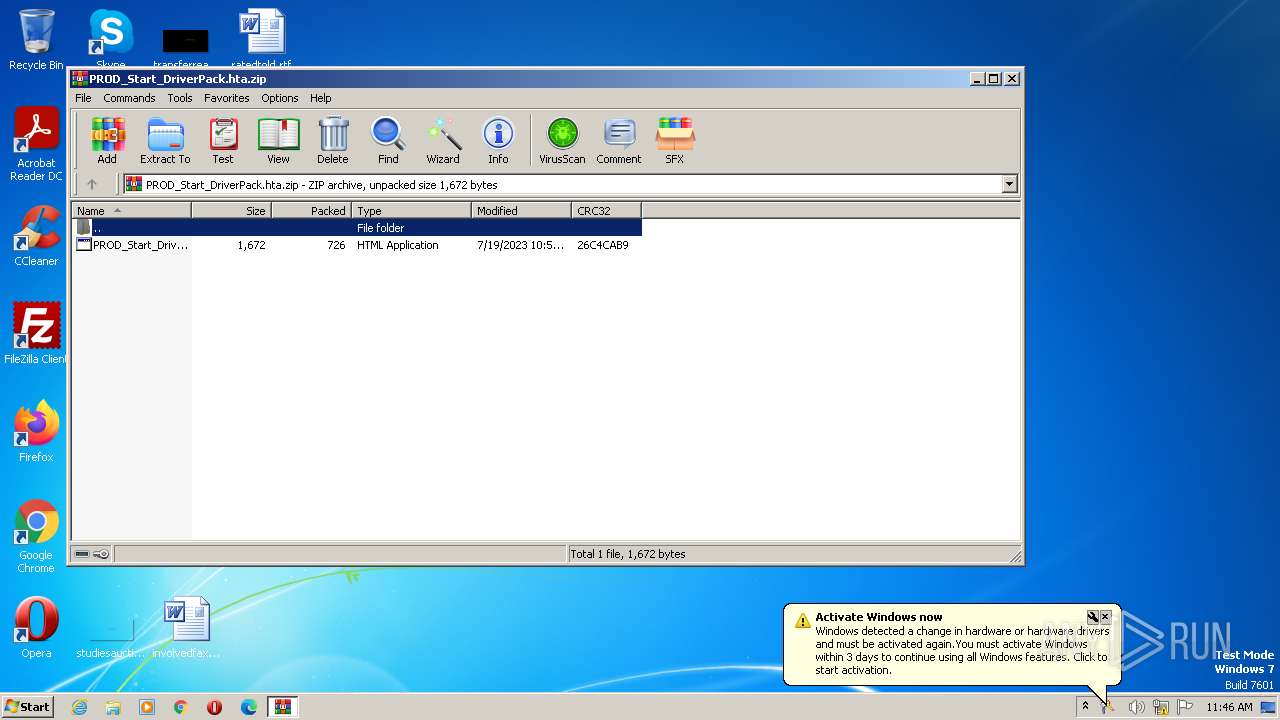
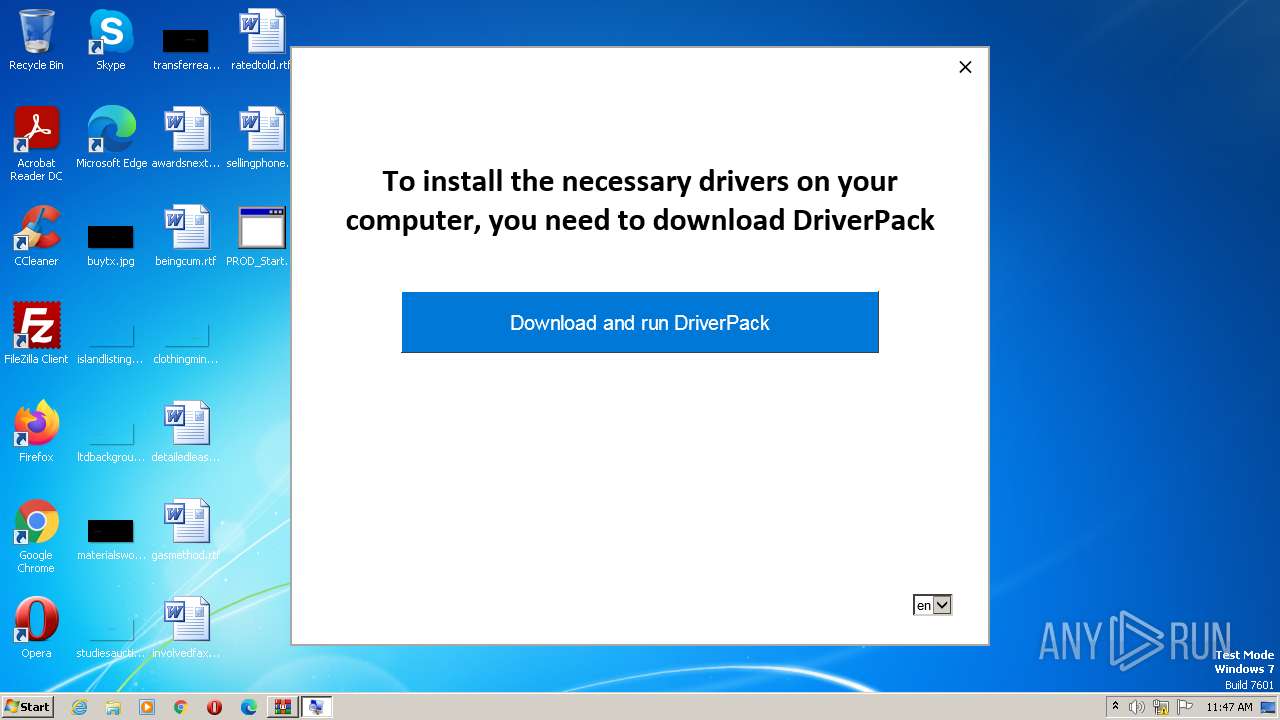
| File name: | PROD_Start_DriverPack.hta.zip |
| Full analysis: | https://app.any.run/tasks/90149905-598a-444d-a385-d217c9f308d6 |
| Verdict: | Malicious activity |
| Analysis date: | July 19, 2023, 10:46:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | F9E5B8C4B36D9AD6E85D4D4B46D642C6 |
| SHA1: | 8D91D7BFE52A10EBC18680730A39490153D890CD |
| SHA256: | EB593312D7A731CF576CA065B5EF3EB44FBEF84C5BE6ED95D3C0E4FD896A116C |
| SSDEEP: | 24:JC+zC0IKLdOgZI6zgQDWKHrBR697HbT0E0baAFfQdCpddp:JCmHXocIwaK9ofybaA6CpN |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Internet Settings
- mshta.exe (PID: 1416)
Process requests binary or script from the Internet
- mshta.exe (PID: 1416)
INFO
Checks proxy server information
- mshta.exe (PID: 1416)
Manual execution by a user
- mshta.exe (PID: 1416)
Reads Internet Explorer settings
- mshta.exe (PID: 1416)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | PROD_Start_DriverPack.hta |
|---|---|
| ZipUncompressedSize: | 1672 |
| ZipCompressedSize: | 726 |
| ZipCRC: | 0x26c4cab9 |
| ZipModifyDate: | 2023:07:19 09:54:52 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0001 |
| ZipRequiredVersion: | 788 |
Total processes
40
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1416 | "C:\Windows\System32\mshta.exe" "C:\Users\admin\Desktop\PROD_Start_DriverPack.hta" | C:\Windows\System32\mshta.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
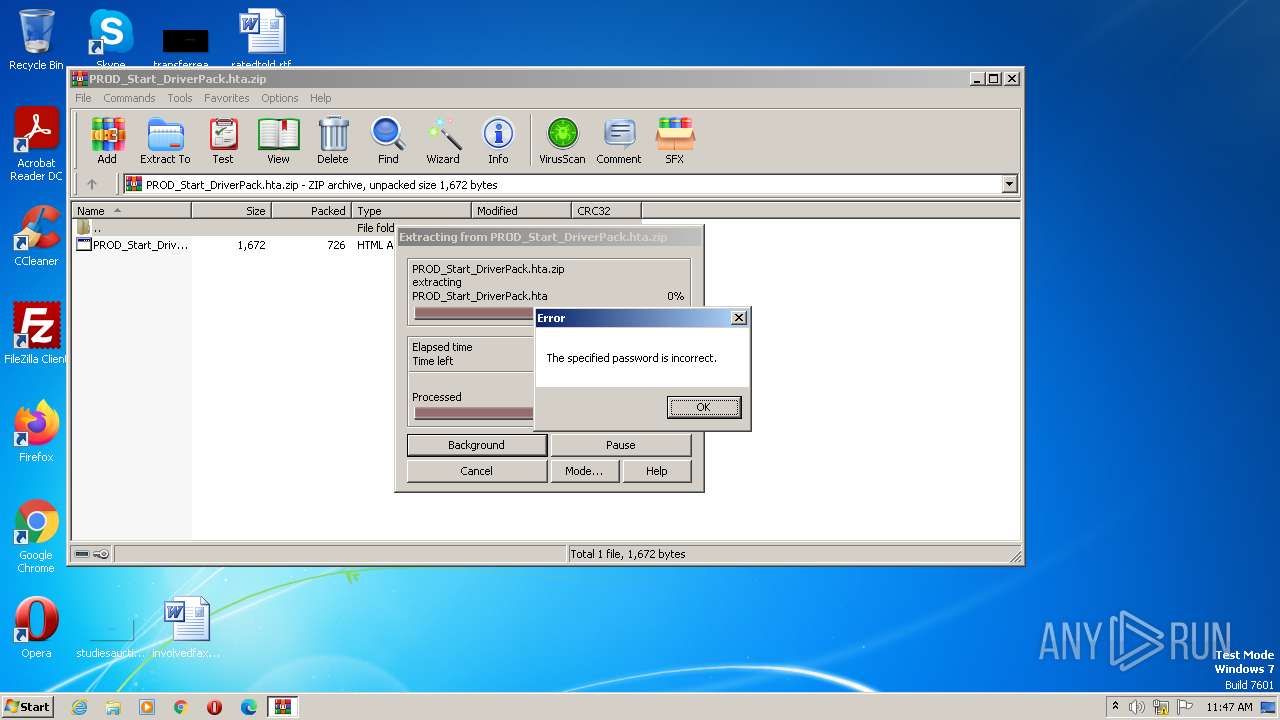
| 3468 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\PROD_Start_DriverPack.hta.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
1 725
Read events
1 692
Write events
33
Delete events
0
Modification events
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (1416) mshta.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
0
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1416 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\2[1].js | text | |
MD5:22D3D08CBEC1245327396FAA5B60725A | SHA256:923CBFF9E47CA64E292A8932A13ED11F9E4A488DC20775181B010231F15E3E26 | |||
| 1416 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\step1_av[1].htm | html | |
MD5:D9C4EDD8648B146931B486C8FC4853F1 | SHA256:C36CFE0BBA2E4B111968E9899B82A5FD6829949D8BA4BF31D0448C86904D7AA0 | |||
| 1416 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\client_ip[1].js | text | |
MD5:611B573CE197EC336B121AD9F8D3D11D | SHA256:2BAF1253F81E8CB5A56DCE73294DAA7C74CDF91BD1B2454F4A8F1423D48C3147 | |||
| 1416 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\4[1].js | text | |
MD5:B21247B2428E6D9F72405EB1A2F5F75C | SHA256:9DDF298484BD63F71CFF04DD81E00913266FA8D71793E2C26F3B7B215067812C | |||
| 1416 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\3[1].js | text | |
MD5:CC9E168614A8D567352E24F970CA21E0 | SHA256:578820B83CD0244FFC068665C531A8C7D633F890A927A682A1708B84B7A08702 | |||
| 1416 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\5[1].js | text | |
MD5:AEEE81BB12D7059393E42828191765C2 | SHA256:F9156E0C0A06207EB66A51AB364A05E37E0273242F9373F8378F6E0DEB705D0B | |||
| 1416 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\lang[1].js | html | |
MD5:0F8AA7C95F02FF49F1FBAE3D5817F2F9 | SHA256:685F7D5BF2AF77F561B24F8E4B2363503A76690D70B179BB55B161317BA47676 | |||
| 1416 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\statistics[1].js | text | |
MD5:B2343F840D0138C1D34648AF653617AF | SHA256:8ECA86E628A4BF5C7CB78DB8654CE749E5BB4A3DAA5FE79ED61045CBF3A97E73 | |||
| 1416 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\style[1].css | text | |
MD5:817F995CDDC5BB427032EB7286FCDA39 | SHA256:F3BDB1D94F79EFD344620028E69EB6BC4AADCA69081E9A9E91D5389E6BFD6DFB | |||
| 1416 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\download_and_av[1].htm | html | |
MD5:DAE972AFAE277C877DBD1373B2202BAB | SHA256:87569B2EEC82C09EB4828761B1B95D58016924EDB54BE2BBD72014E7B3A41EF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
9
DNS requests
2
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1416 | mshta.exe | GET | 200 | 46.137.15.86:80 | http://dwrapper-prod.herokuapp.com/bin/src/script.js | IE | text | 3.47 Kb | malicious |
1416 | mshta.exe | GET | 200 | 46.137.15.86:80 | http://dwrapper-prod.herokuapp.com/bin/step1_av.html | IE | html | 1.42 Kb | malicious |
1416 | mshta.exe | GET | 200 | 46.137.15.86:80 | http://dwrapper-prod.herokuapp.com/bin/src/variables/2.js | IE | text | 4.97 Kb | malicious |
— | — | GET | 200 | 46.137.15.86:80 | http://dwrapper-prod.herokuapp.com/bin/src/variables/1.js | IE | text | 1.27 Kb | malicious |
1416 | mshta.exe | GET | 200 | 46.137.15.86:80 | http://dwrapper-prod.herokuapp.com/bin/src/style.css | IE | text | 2.91 Kb | malicious |
— | — | GET | 200 | 46.137.15.86:80 | http://dwrapper-prod.herokuapp.com/bin/src/variables/3.js | IE | text | 2.48 Kb | malicious |
1416 | mshta.exe | GET | 200 | 46.137.15.86:80 | http://dwrapper-prod.herokuapp.com/client_ip.js | IE | text | 30 b | malicious |
1416 | mshta.exe | GET | 200 | 46.137.15.86:80 | http://dwrapper-prod.herokuapp.com/bin/src/variables/5.js | IE | text | 538 b | malicious |
— | — | GET | 200 | 46.137.15.86:80 | http://dwrapper-prod.herokuapp.com/bin/src/variables/2.js | IE | text | 4.97 Kb | malicious |
1416 | mshta.exe | GET | 200 | 46.137.15.86:80 | http://dwrapper-prod.herokuapp.com/bin/src/variables/4.js | IE | text | 1.13 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2640 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1416 | mshta.exe | 46.137.15.86:80 | dwrapper-prod.herokuapp.com | AMAZON-02 | IE | suspicious |
1416 | mshta.exe | 54.73.53.134:80 | dwrapper-prod.herokuapp.com | AMAZON-02 | IE | suspicious |
1416 | mshta.exe | 18.157.122.248:80 | example-dwrapper.matomo.cloud | AMAZON-02 | DE | suspicious |
1416 | mshta.exe | 3.126.133.169:80 | example-dwrapper.matomo.cloud | AMAZON-02 | DE | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dwrapper-prod.herokuapp.com |
| malicious |
example-dwrapper.matomo.cloud |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1416 | mshta.exe | A Network Trojan was detected | SUSPICIOUS [ANY.RUN] VBS is used to run Shell |
1416 | mshta.exe | A Network Trojan was detected | SUSPICIOUS [ANY.RUN] VBS is used to run Shell |
2 ETPRO signatures available at the full report