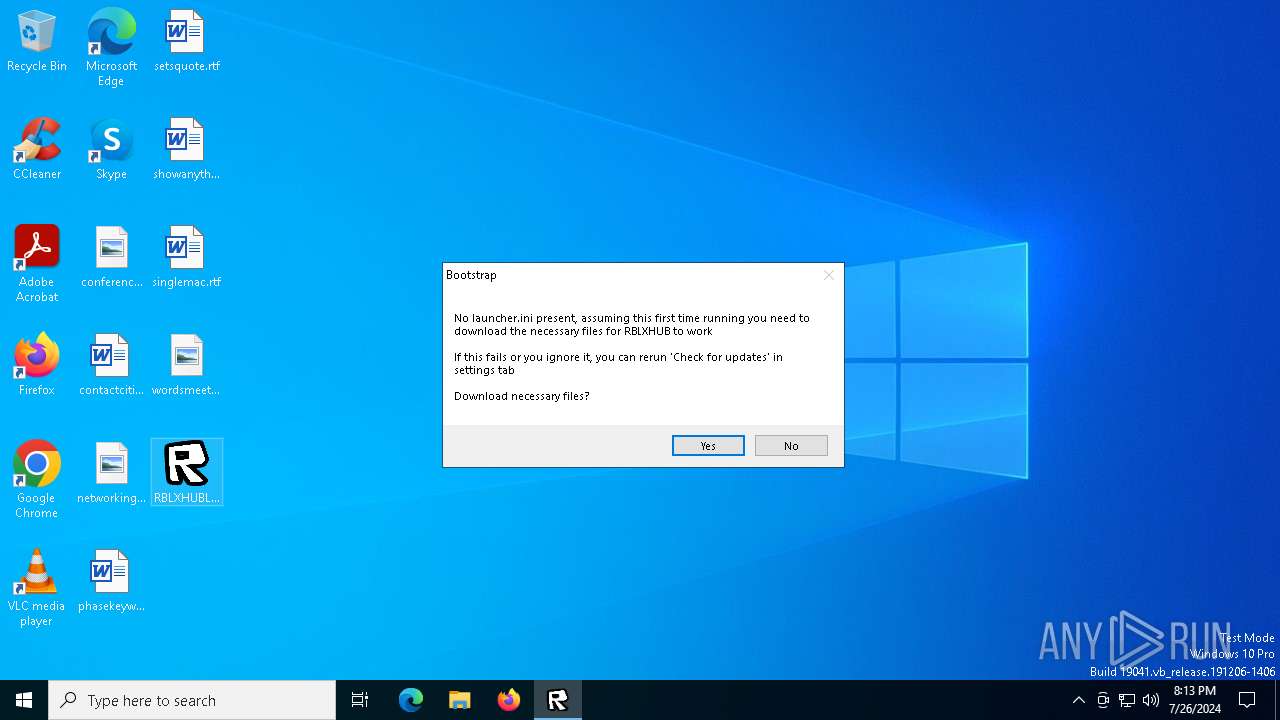
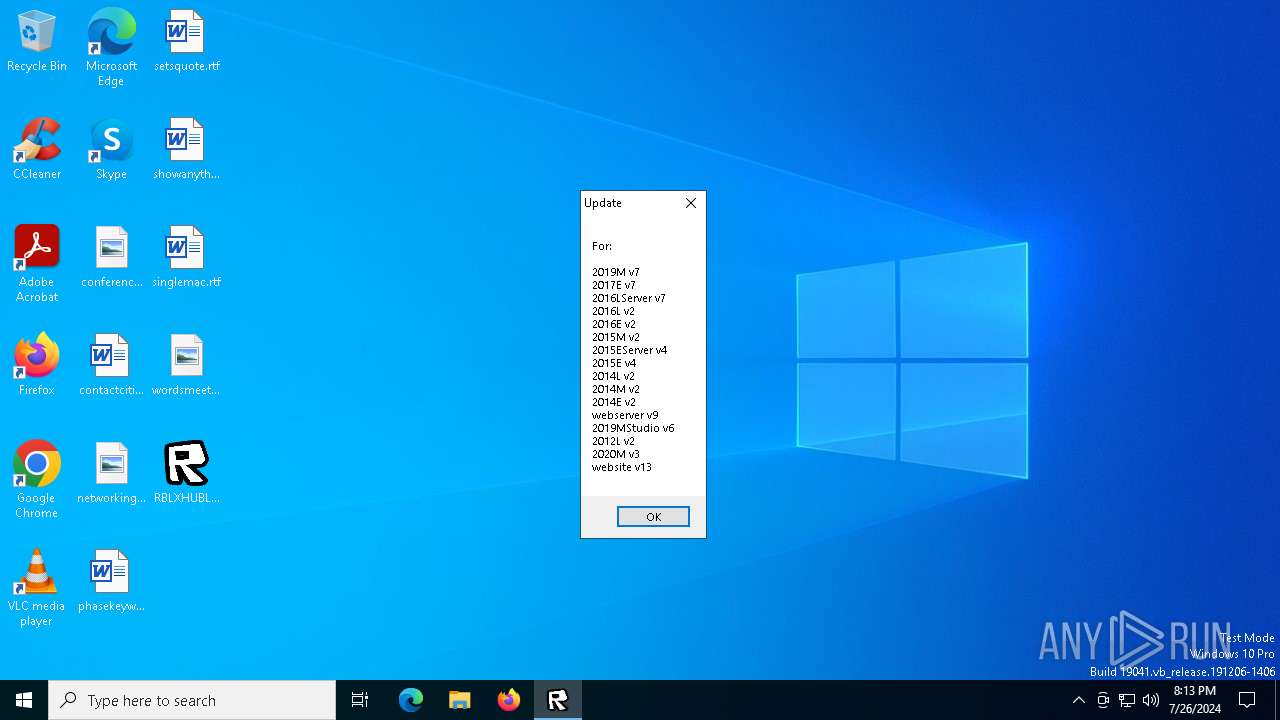
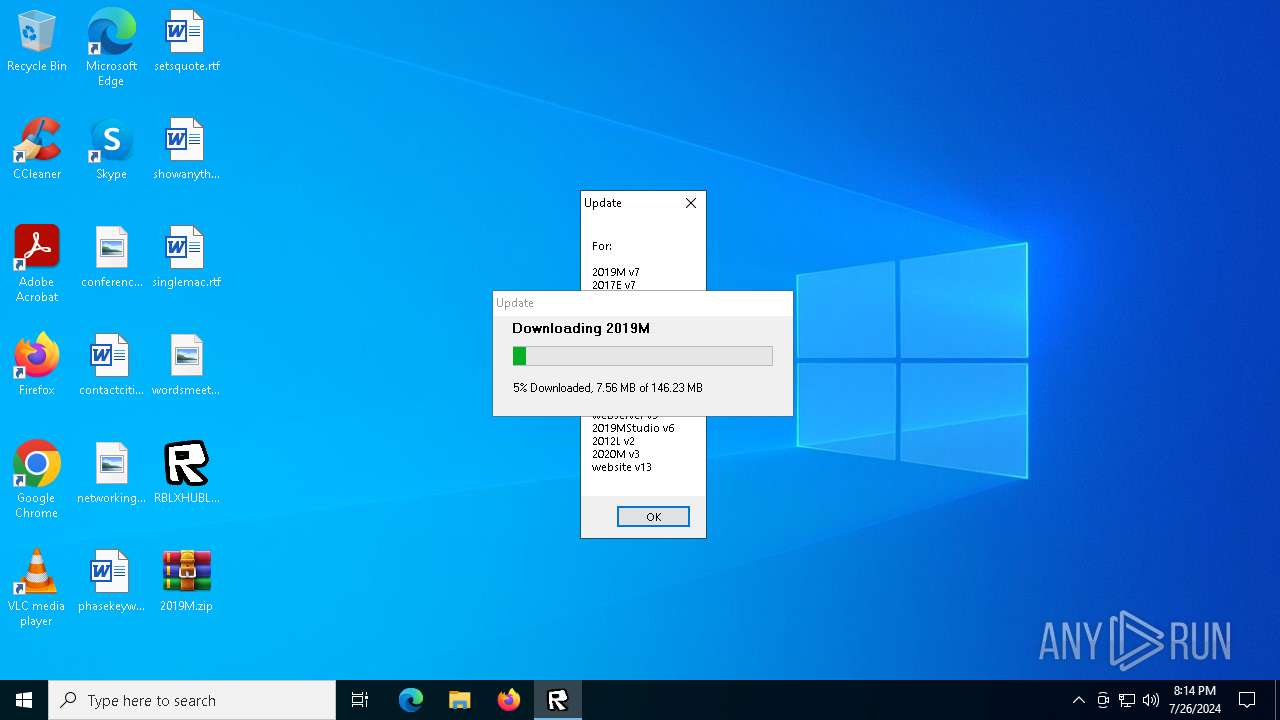
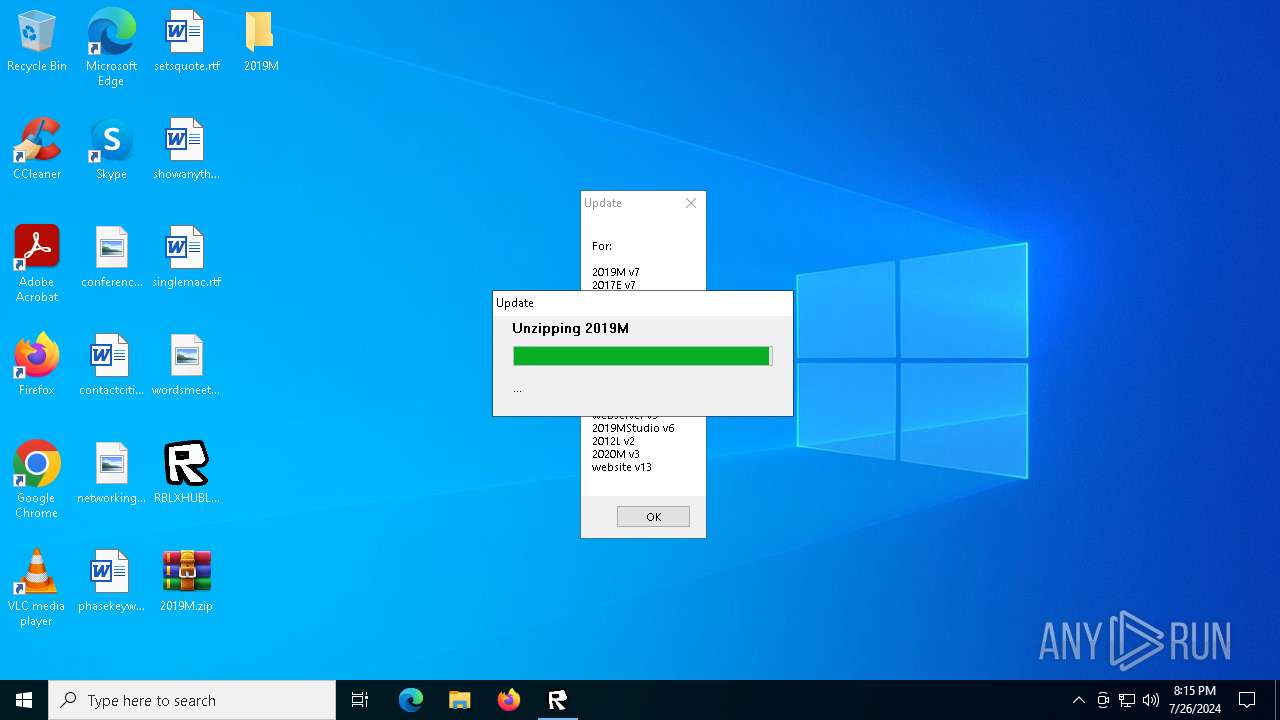
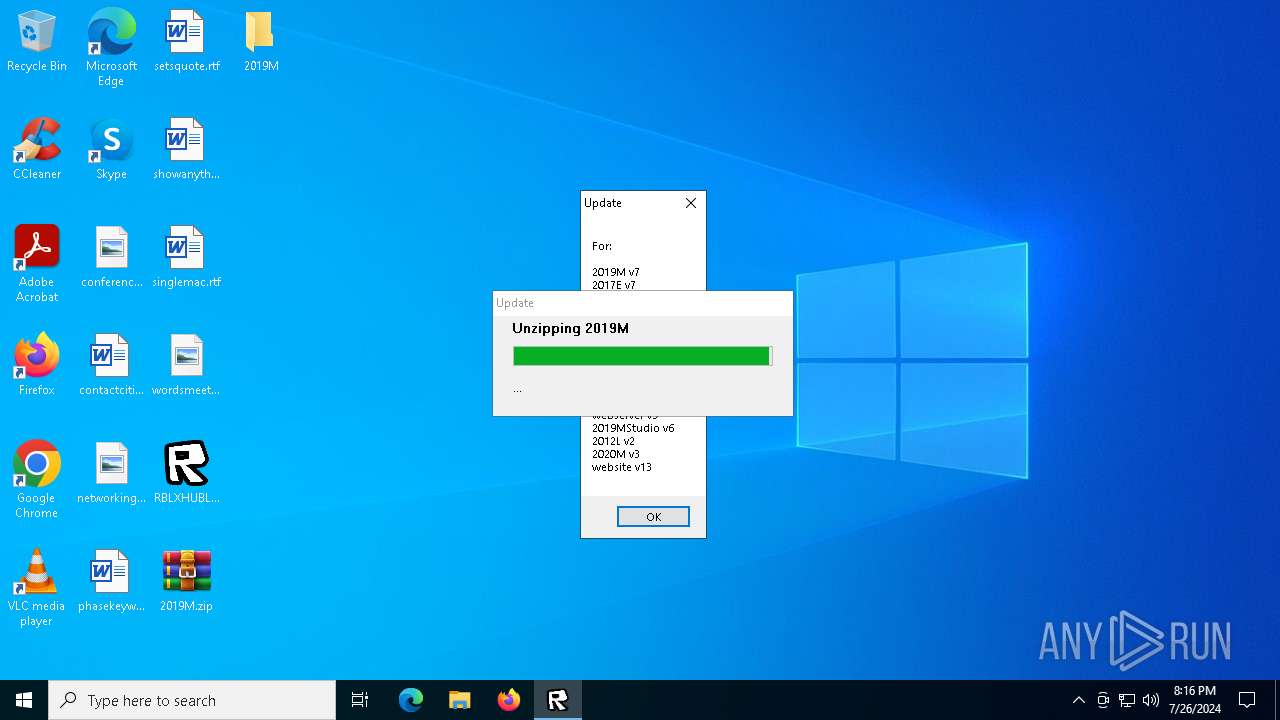
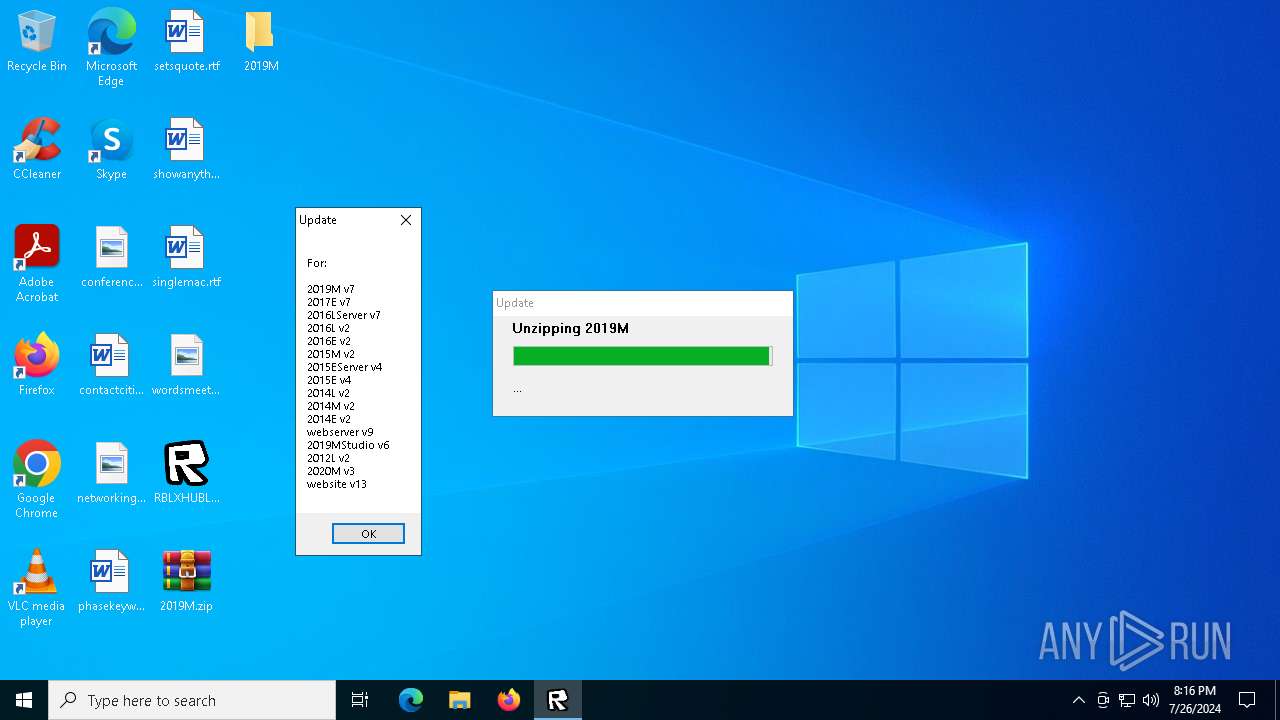
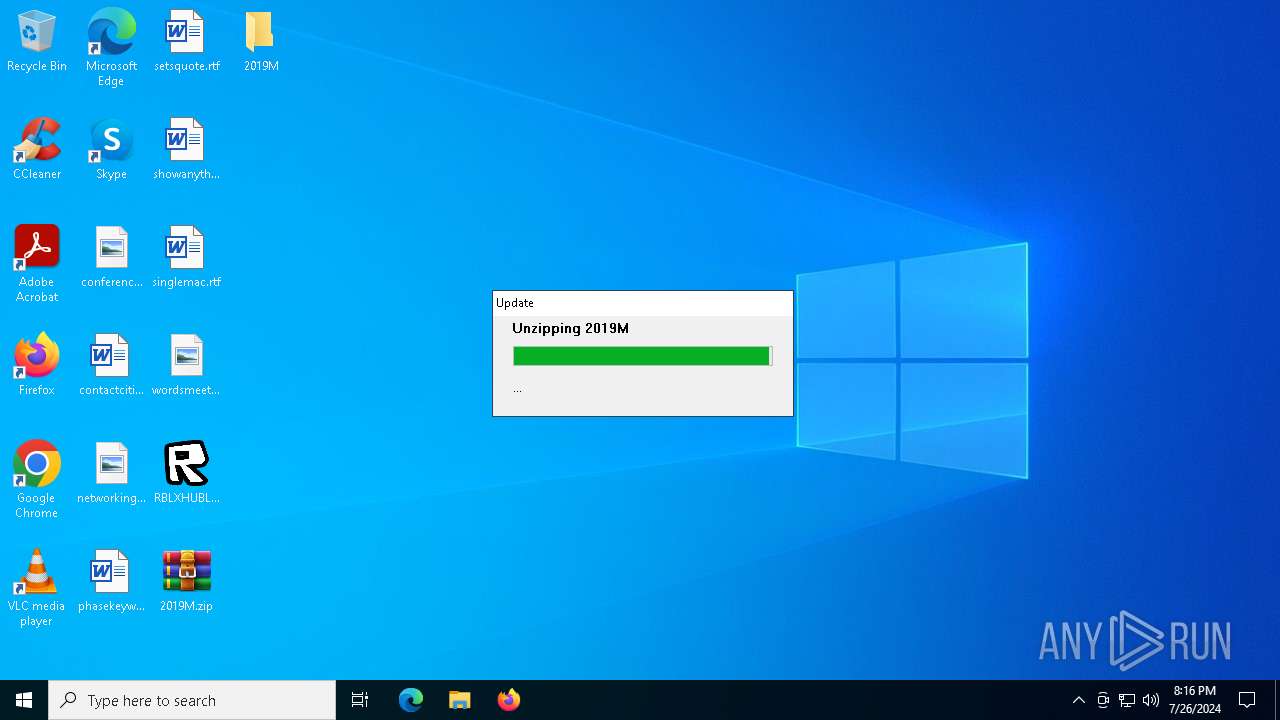
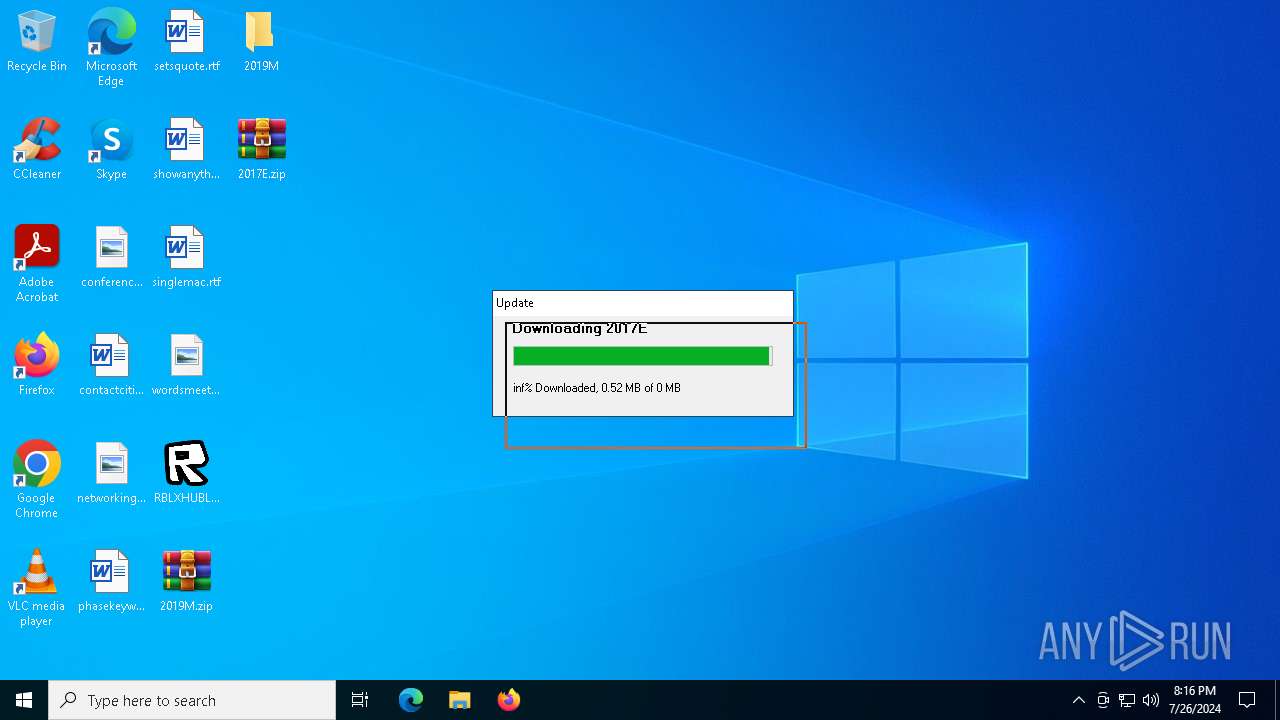
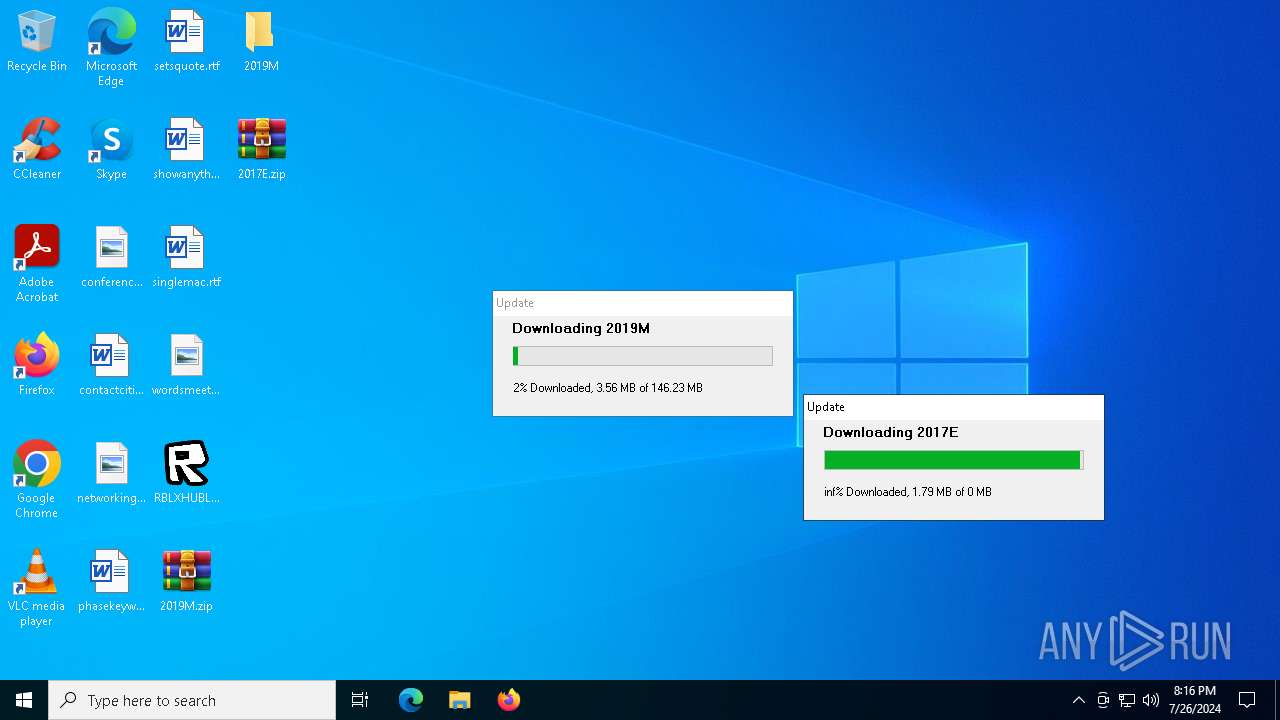
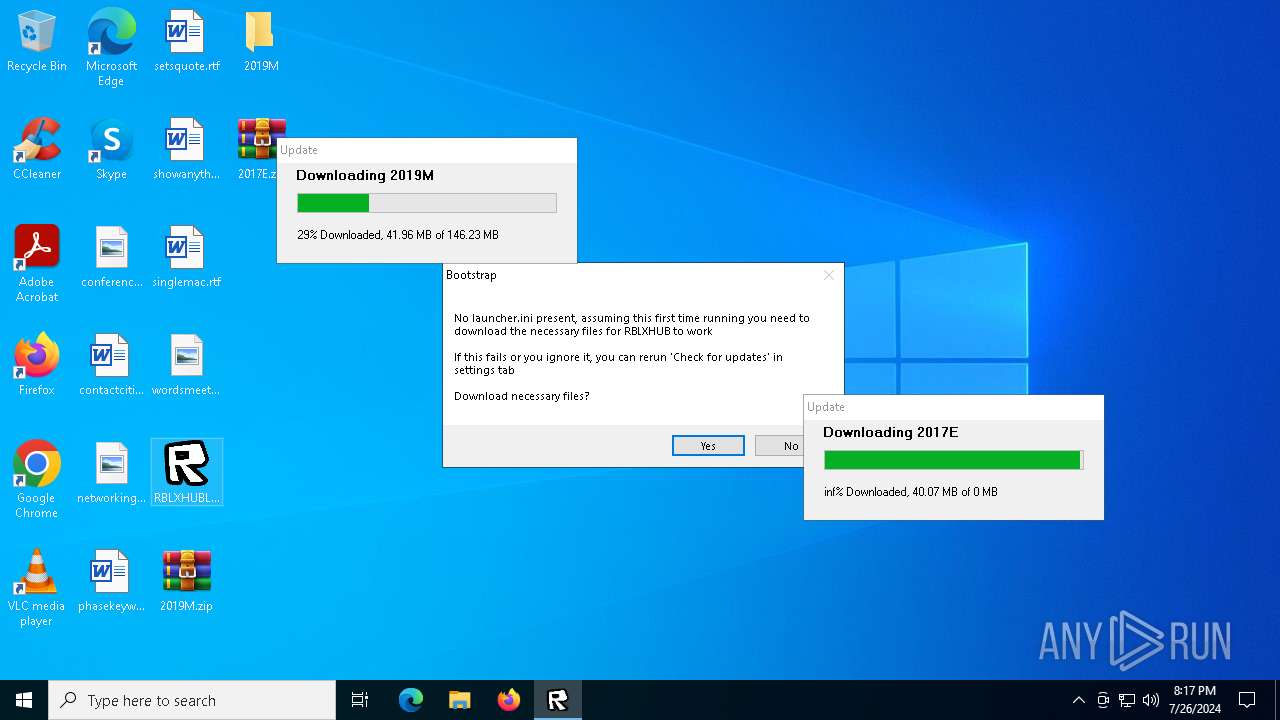
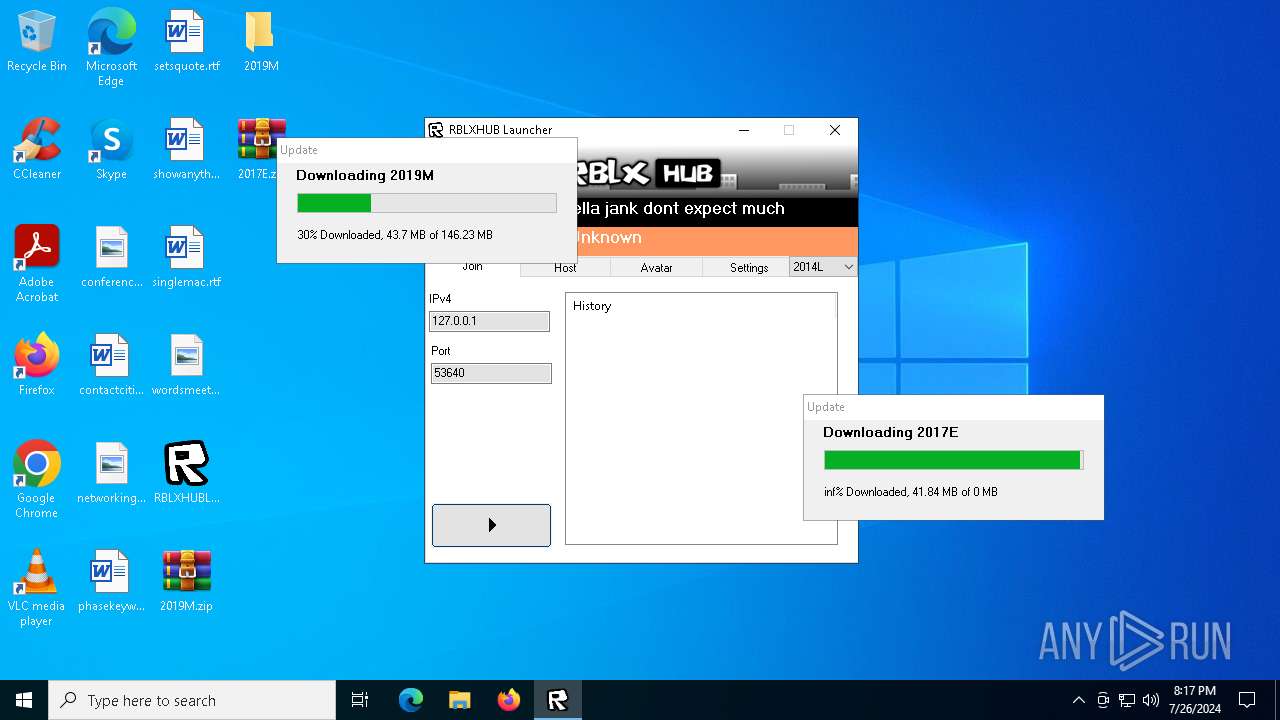
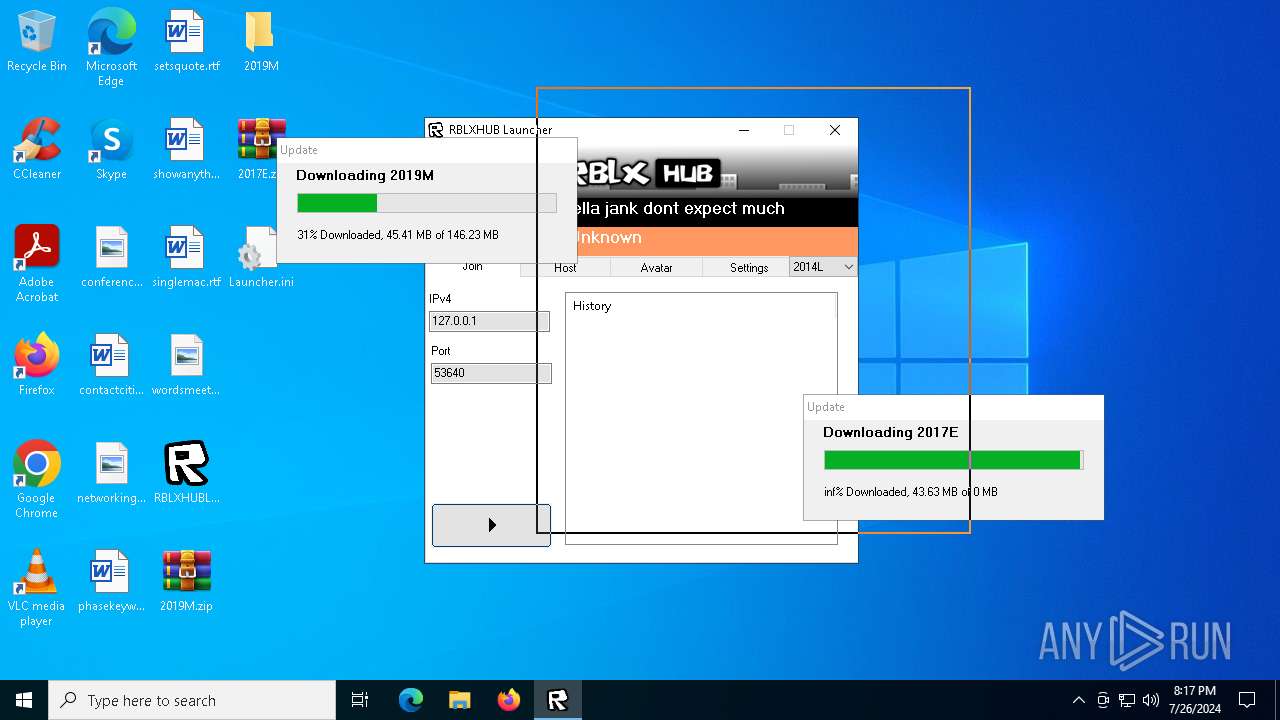
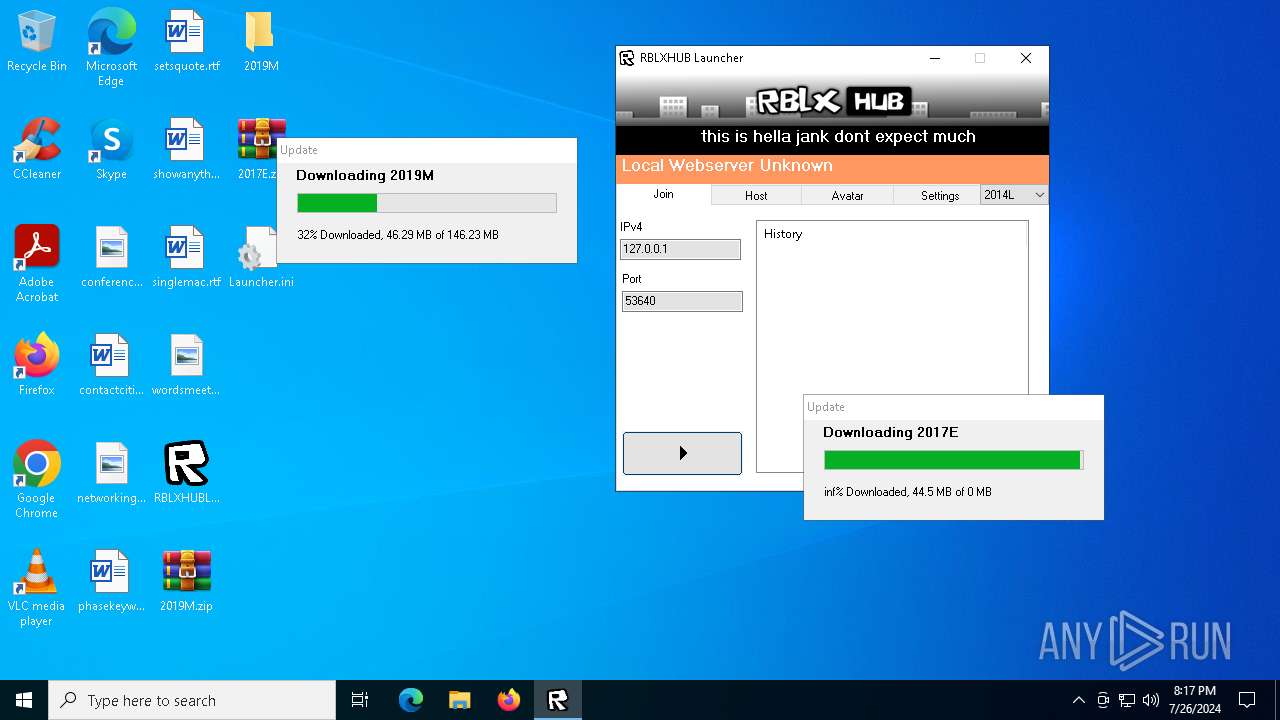
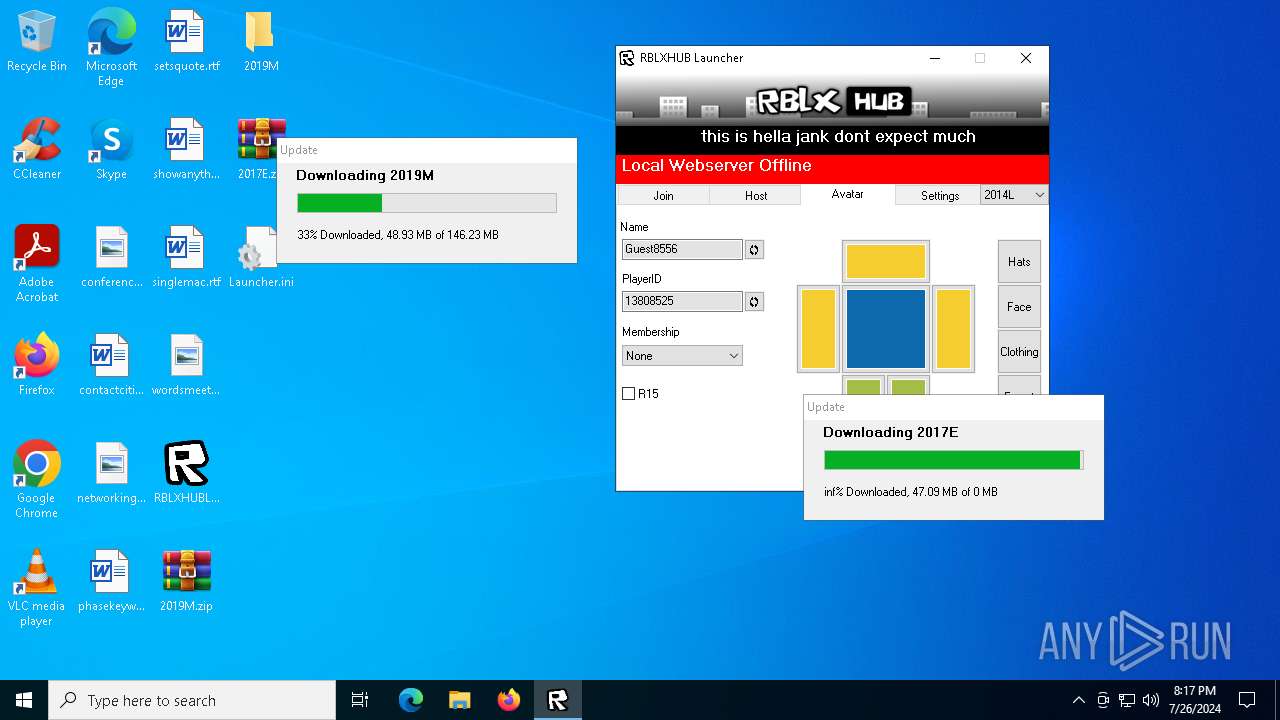
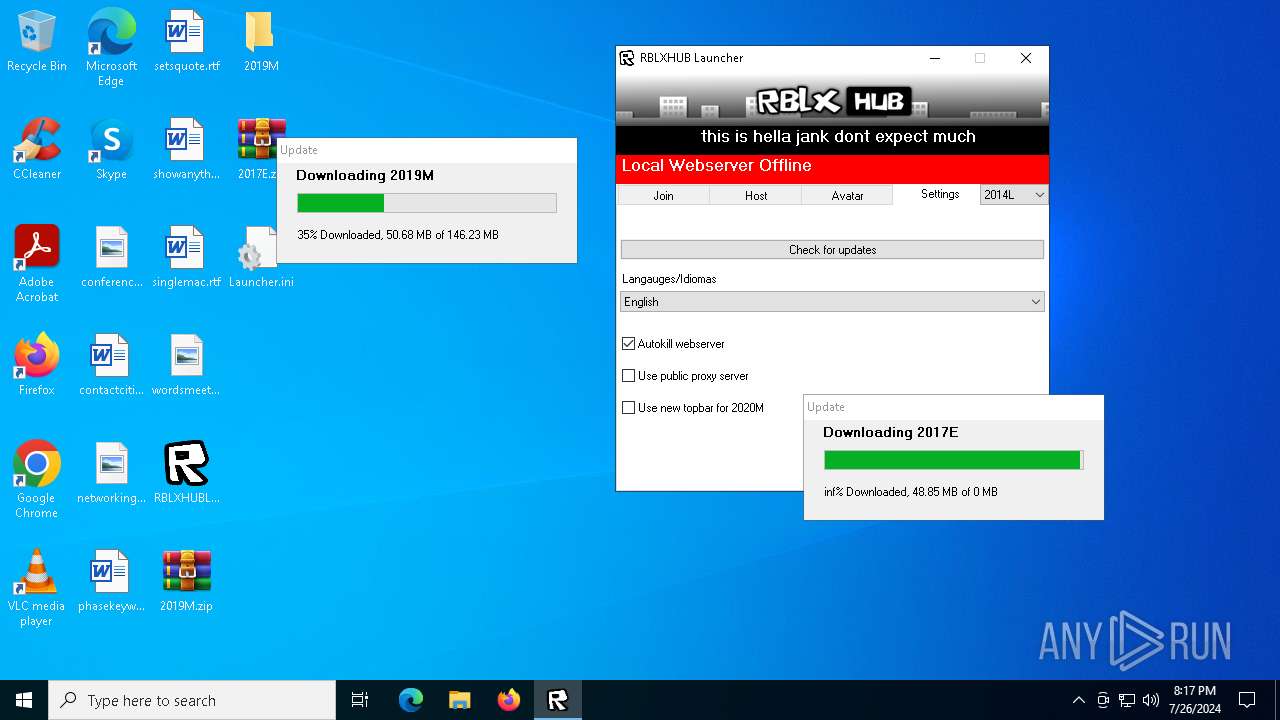
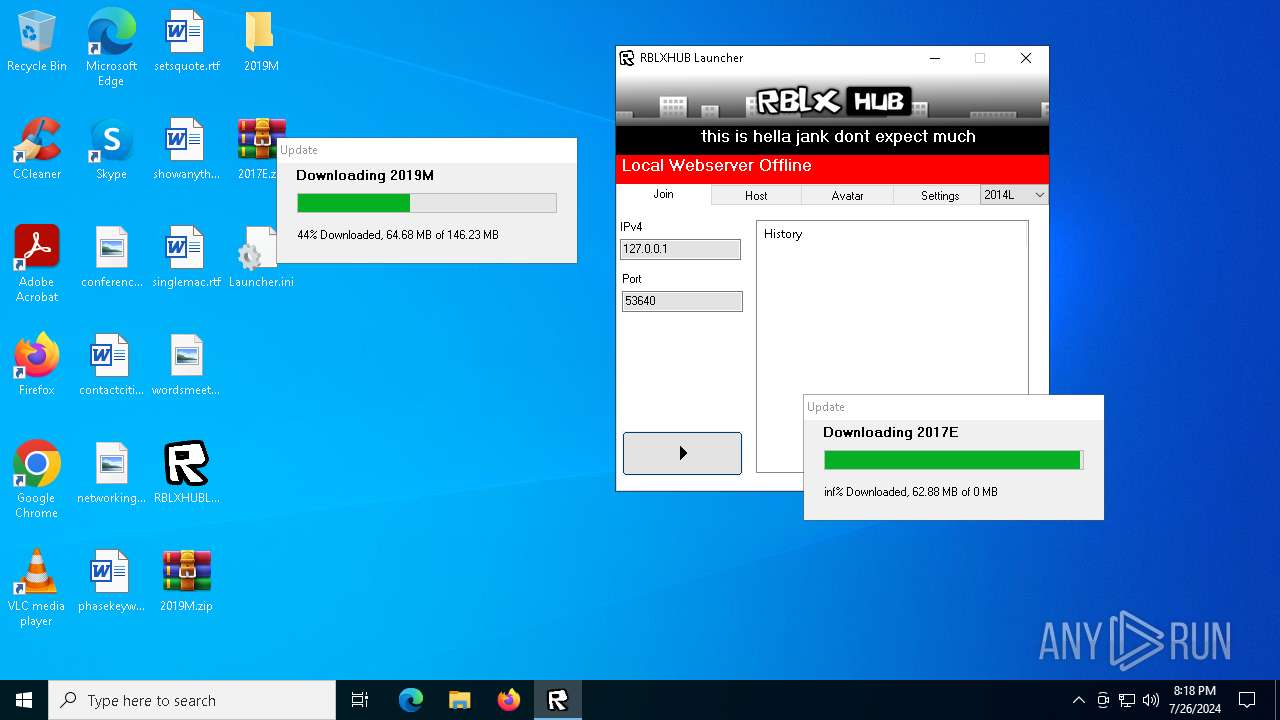
| File name: | RBLXHUBLauncher.exe |
| Full analysis: | https://app.any.run/tasks/b5b40ca5-e80d-4d39-972a-0559910a4406 |
| Verdict: | Malicious activity |
| Analysis date: | July 26, 2024, 20:13:09 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | B4463809F314A236C031C5005CF88D2F |
| SHA1: | 75CACA1A36410CA730D1DB7A51EEFD2AAA20684A |
| SHA256: | EB58958B80E3E519339B125AC0B294911566E1636D0E167116E7971650CF9DD1 |
| SSDEEP: | 49152:0PPkzemqoSut3Jh4+QQ/btosJwIA4hHmZlKH2Tw/Pq83zw0bCjvk9G661QGtpjXi:+P/mp7t3T4+B/btosJwIA4hHmZlKH2Ts |
MALICIOUS
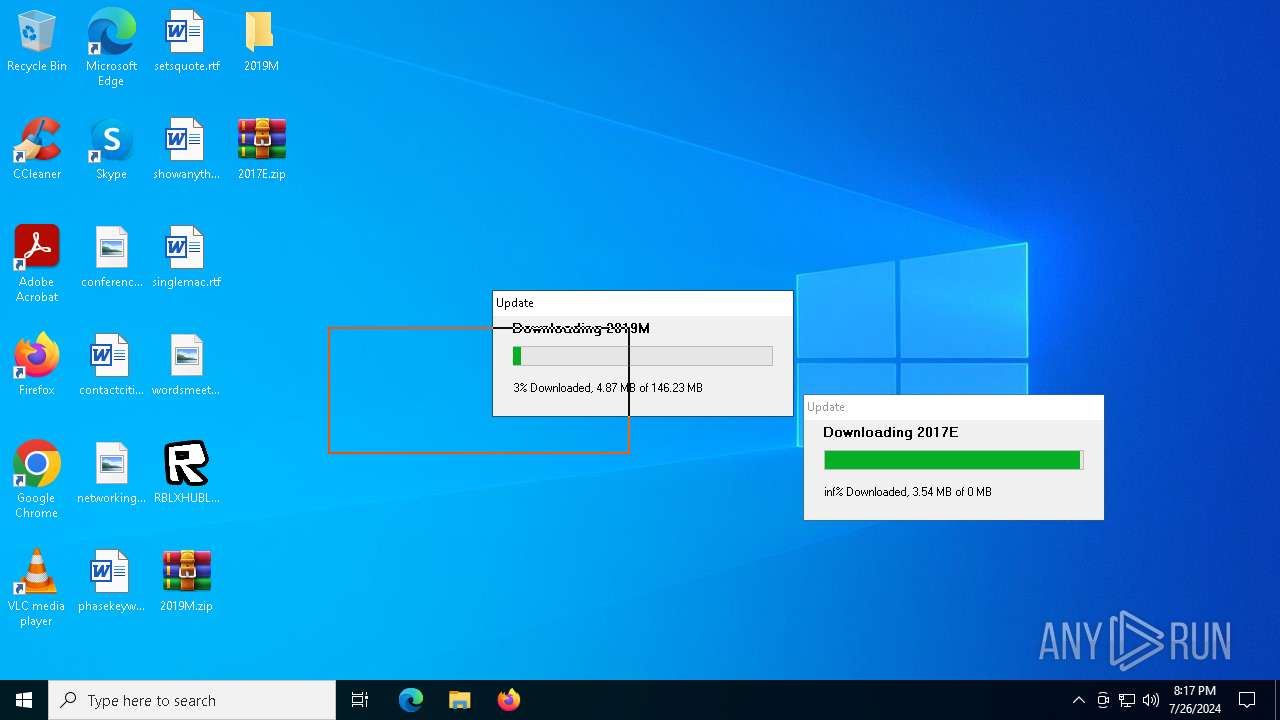
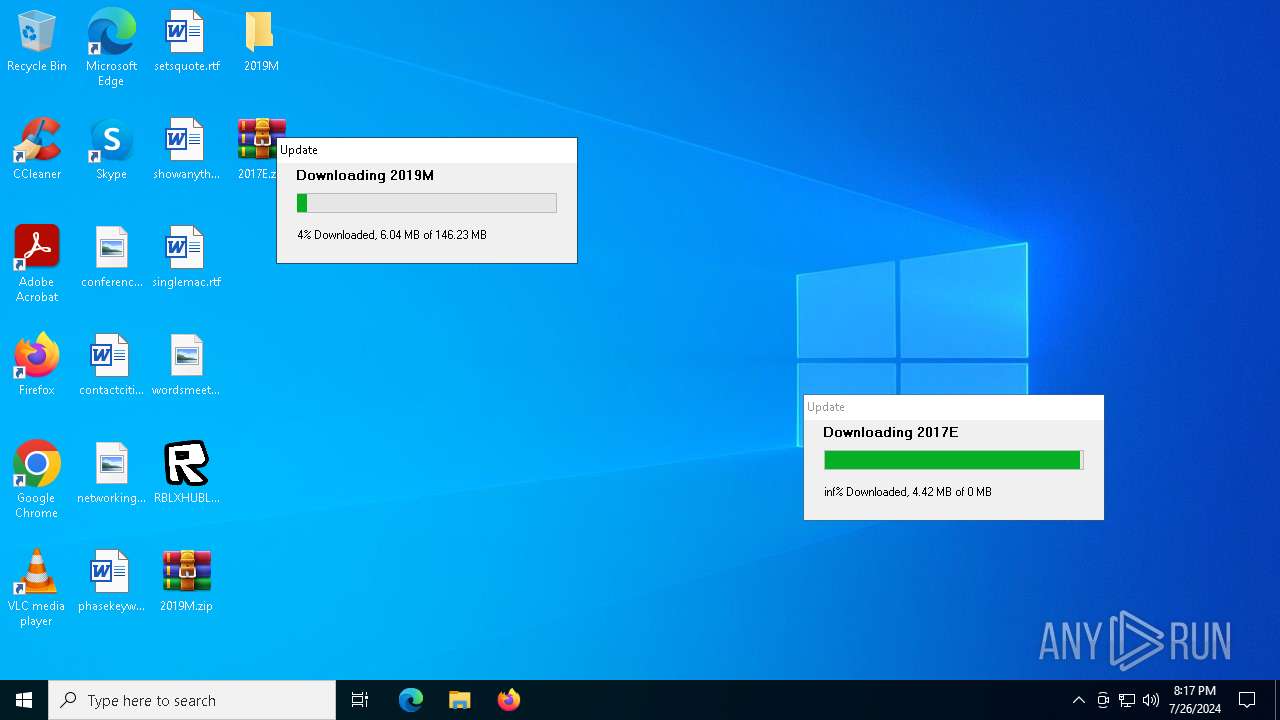
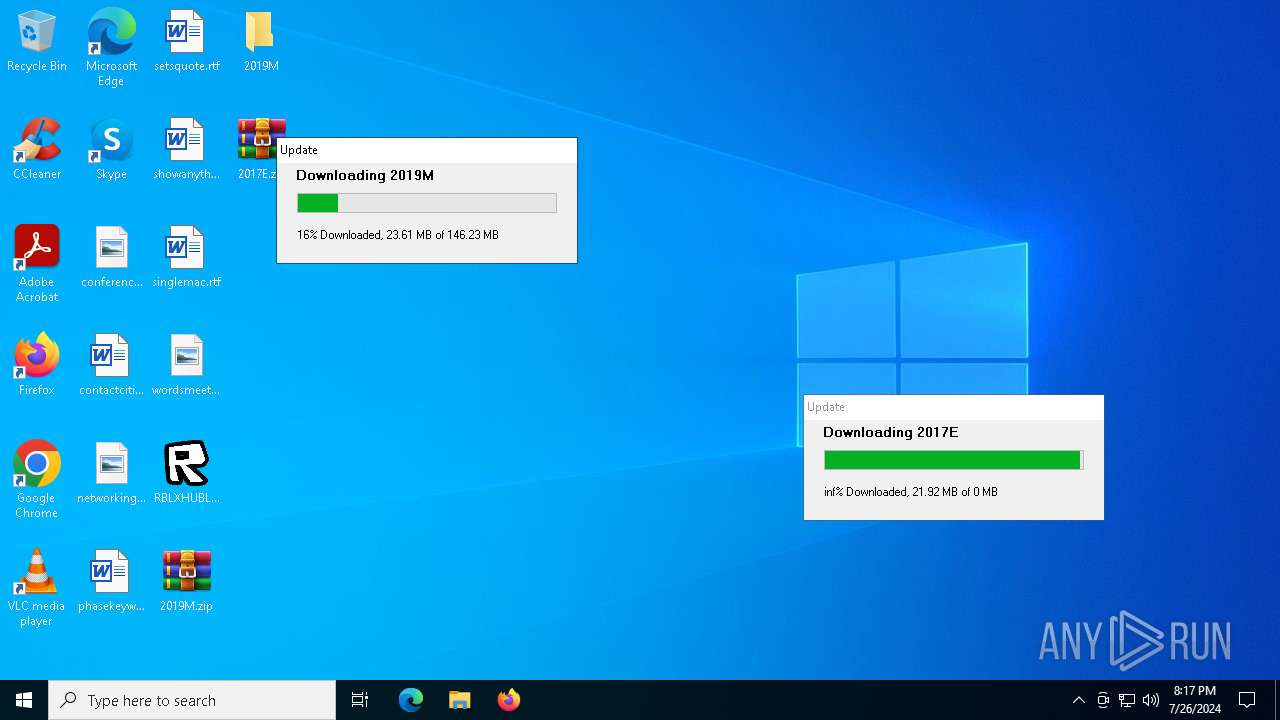
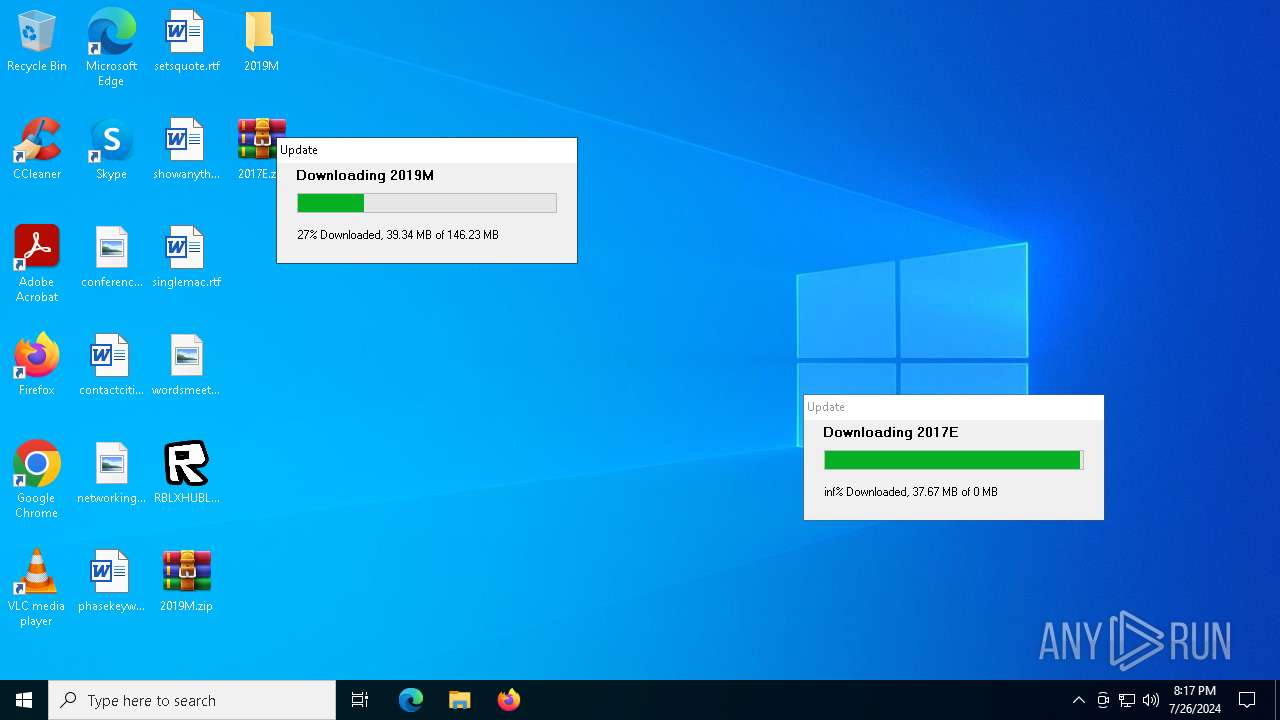
Drops the executable file immediately after the start
- RBLXHUBLauncher.exe (PID: 396)
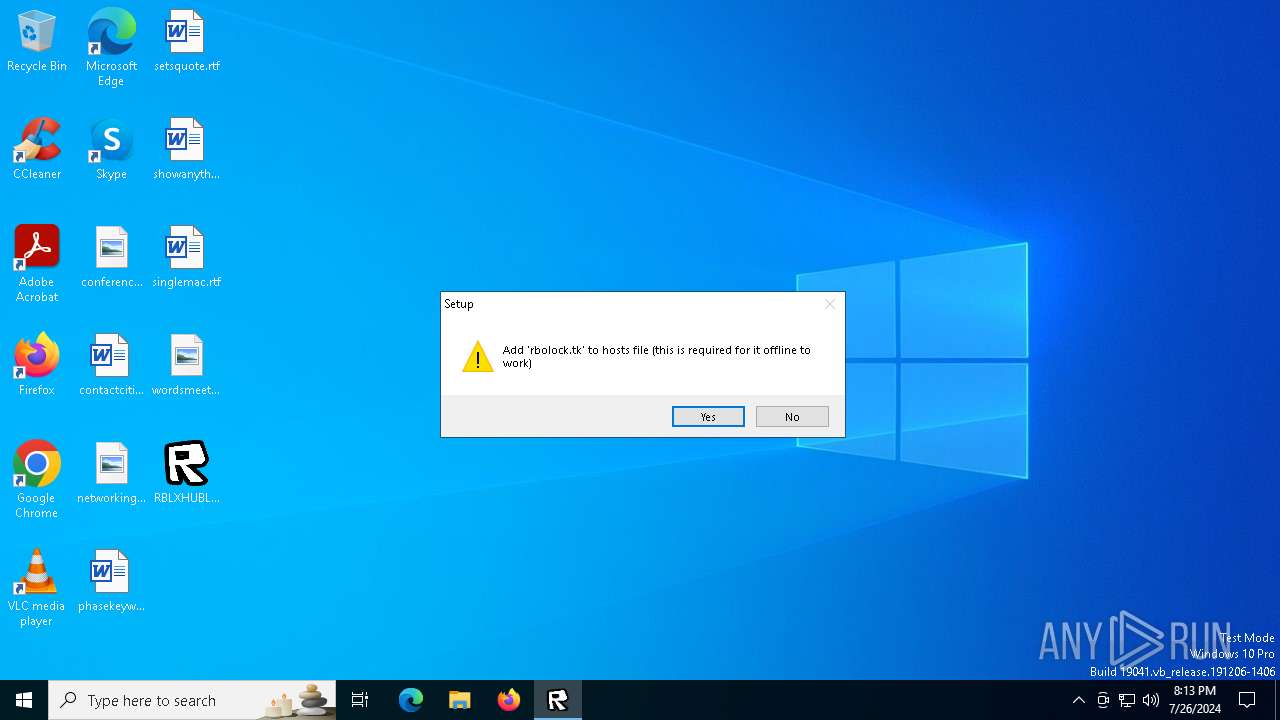
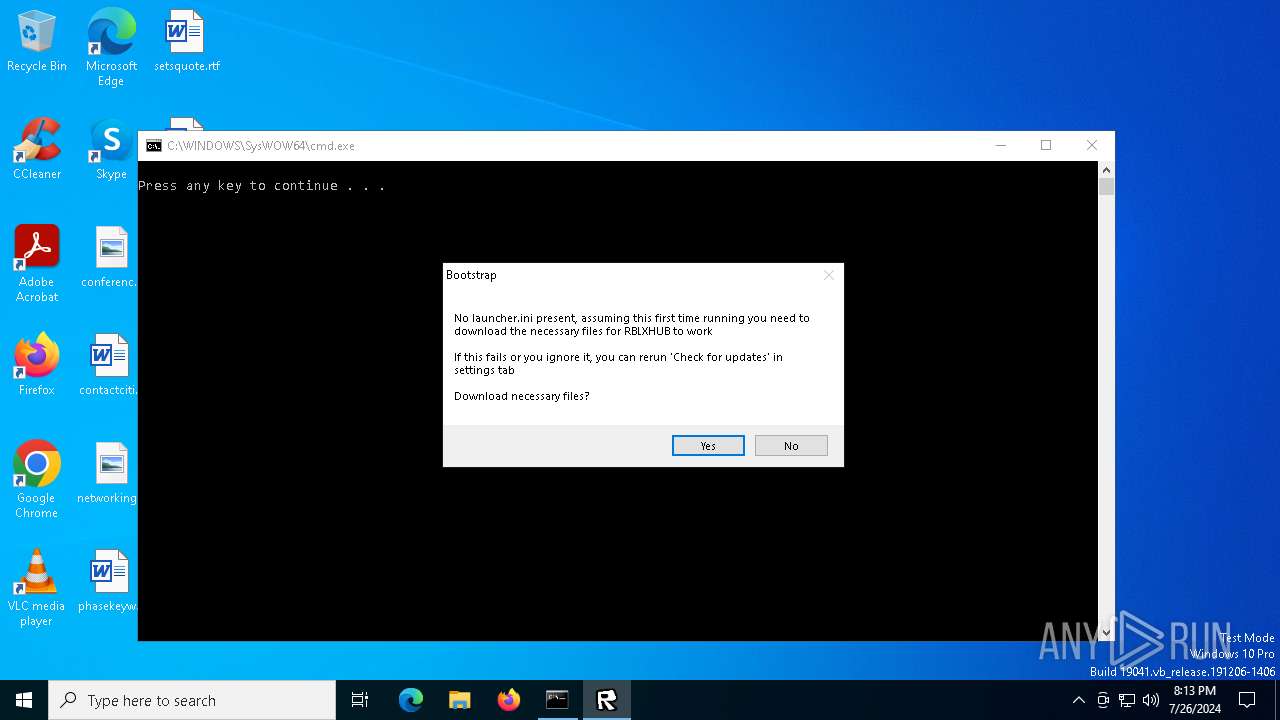
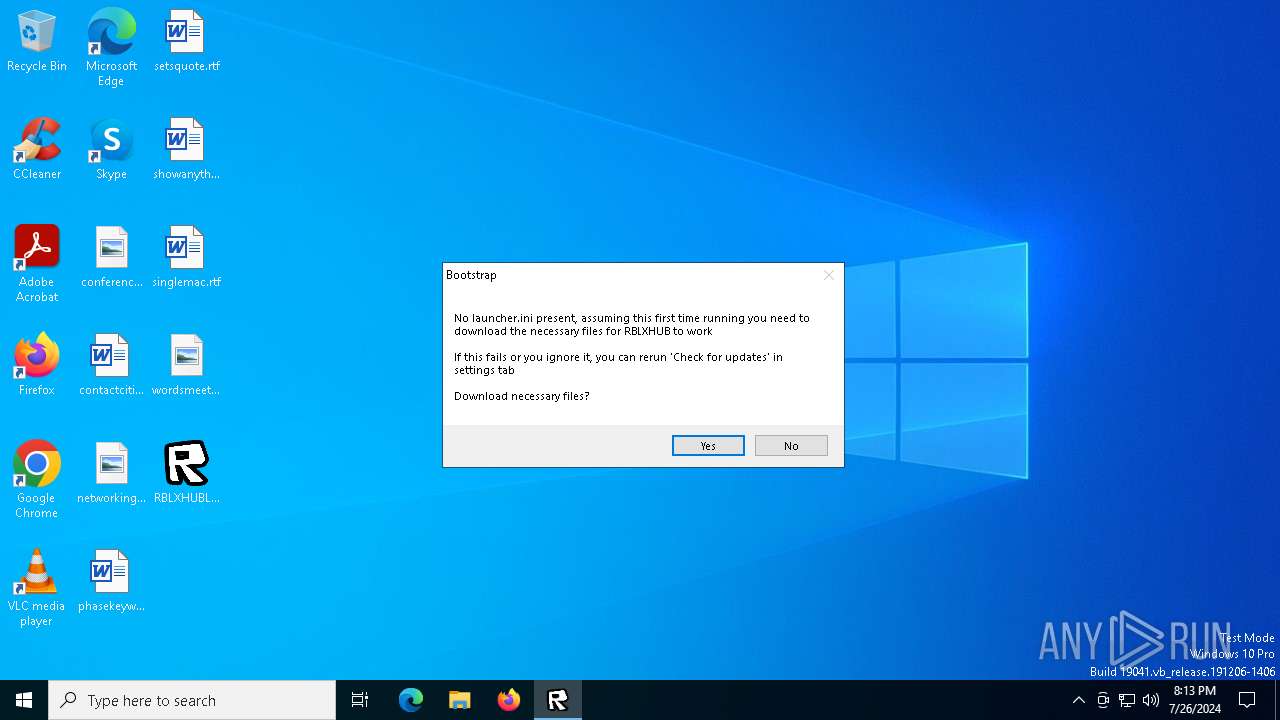
Modifies hosts file to block updates
- cmd.exe (PID: 236)
SUSPICIOUS
Reads security settings of Internet Explorer
- RBLXHUBLauncher.exe (PID: 396)
- RBLXHUBLauncher.exe (PID: 2124)
- RBLXHUBLauncher.exe (PID: 1180)
Reads the date of Windows installation
- RBLXHUBLauncher.exe (PID: 396)
Powershell scripting: start process
- RBLXHUBLauncher.exe (PID: 396)
Starts POWERSHELL.EXE for commands execution
- RBLXHUBLauncher.exe (PID: 396)
Found IP address in command line
- powershell.exe (PID: 2132)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 2132)
Potential Corporate Privacy Violation
- RBLXHUBLauncher.exe (PID: 396)
- RBLXHUBLauncher.exe (PID: 2124)
INFO
Reads the software policy settings
- slui.exe (PID: 6480)
- slui.exe (PID: 6308)
Reads mouse settings
- RBLXHUBLauncher.exe (PID: 396)
- RBLXHUBLauncher.exe (PID: 2124)
- RBLXHUBLauncher.exe (PID: 1180)
Reads the computer name
- RBLXHUBLauncher.exe (PID: 396)
- RBLXHUBLauncher.exe (PID: 2124)
- RBLXHUBLauncher.exe (PID: 1180)
Checks proxy server information
- slui.exe (PID: 6480)
- RBLXHUBLauncher.exe (PID: 396)
- RBLXHUBLauncher.exe (PID: 2124)
- slui.exe (PID: 6308)
- RBLXHUBLauncher.exe (PID: 1180)
Checks supported languages
- RBLXHUBLauncher.exe (PID: 396)
- RBLXHUBLauncher.exe (PID: 2124)
- RBLXHUBLauncher.exe (PID: 1180)
Process checks computer location settings
- RBLXHUBLauncher.exe (PID: 396)
Create files in a temporary directory
- RBLXHUBLauncher.exe (PID: 396)
- RBLXHUBLauncher.exe (PID: 2124)
Manual execution by a user
- RBLXHUBLauncher.exe (PID: 2124)
- RBLXHUBLauncher.exe (PID: 1180)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:07:23 11:42:28+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 633856 |
| InitializedDataSize: | 783872 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x20577 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
| FileVersion: | 0.0.0.0 |
| Comments: | RBLXHub |
| FileDescription: | RBLXHub Launcher |
| ProductName: | RBLXHub Launcher |
| ProductVersion: | 1 |
| CompanyName: | RBLXHub |
| LegalCopyright: | Made by Alienwy and randomdude744 |
Total processes
155
Monitored processes
9
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\WINDOWS\SysWOW64\cmd.exe" /c echo. && echo 127.0.0.1 rbolock.tk >>c:\Windows\System32\Drivers\etc\hosts && echo 127.0.0.1 www.rbolock.tk >>c:\Windows\System32\Drivers\etc\hosts && echo 127.0.0.1 api.rbolock.tk >>c:\Windows\System32\Drivers\etc\hosts && echo 127.0.0.1 assetgame.rbolock.tk >>c:\Windows\System32\Drivers\etc\hosts && echo 127.0.0.1 assetdelivery.rbolock.tk >>c:\Windows\System32\Drivers\etc\hosts && echo 127.0.0.1 clientsettingscdn.rbolock.tk >>c:\Windows\System32\Drivers\etc\hosts && pause | C:\Windows\SysWOW64\cmd.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
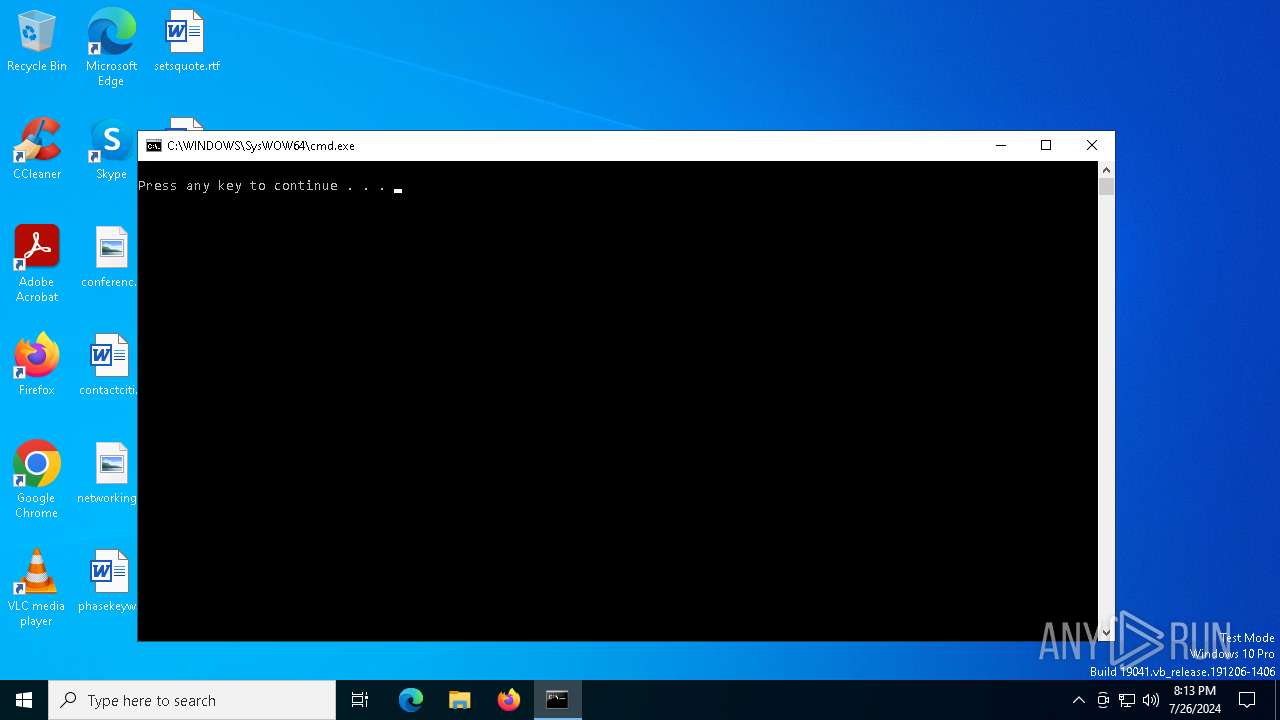
| 396 | "C:\Users\admin\Desktop\RBLXHUBLauncher.exe" | C:\Users\admin\Desktop\RBLXHUBLauncher.exe | explorer.exe | ||||||||||||
User: admin Company: RBLXHub Integrity Level: MEDIUM Description: RBLXHub Launcher Version: 0.0.0.0 Modules
| |||||||||||||||
| 1180 | "C:\Users\admin\Desktop\RBLXHUBLauncher.exe" | C:\Users\admin\Desktop\RBLXHUBLauncher.exe | — | explorer.exe | |||||||||||
User: admin Company: RBLXHub Integrity Level: MEDIUM Description: RBLXHub Launcher Version: 0.0.0.0 Modules
| |||||||||||||||
| 2124 | "C:\Users\admin\Desktop\RBLXHUBLauncher.exe" | C:\Users\admin\Desktop\RBLXHUBLauncher.exe | explorer.exe | ||||||||||||
User: admin Company: RBLXHub Integrity Level: MEDIUM Description: RBLXHub Launcher Version: 0.0.0.0 Modules
| |||||||||||||||
| 2132 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" start-process -verb runas 'cmd.exe' -argumentlist ' /c echo. && echo 127.0.0.1 rbolock.tk >>c:\Windows\System32\Drivers\etc\hosts && echo 127.0.0.1 www.rbolock.tk >>c:\Windows\System32\Drivers\etc\hosts && echo 127.0.0.1 api.rbolock.tk >>c:\Windows\System32\Drivers\etc\hosts && echo 127.0.0.1 assetgame.rbolock.tk >>c:\Windows\System32\Drivers\etc\hosts && echo 127.0.0.1 assetdelivery.rbolock.tk >>c:\Windows\System32\Drivers\etc\hosts && echo 127.0.0.1 clientsettingscdn.rbolock.tk >>c:\Windows\System32\Drivers\etc\hosts && pause ' | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | RBLXHUBLauncher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3848 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4324 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6308 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6480 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
92 425
Read events
92 384
Write events
41
Delete events
0
Modification events
| (PID) Process: | (396) RBLXHUBLauncher.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (396) RBLXHUBLauncher.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (396) RBLXHUBLauncher.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (396) RBLXHUBLauncher.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2132) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2132) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2132) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2132) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (396) RBLXHUBLauncher.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (396) RBLXHUBLauncher.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
6
Suspicious files
229
Text files
1 186
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2132 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:88A9811FC2E7C0A50D13BD39D4D1E520 | SHA256:74CB2D34A50D69D3B35F3C1FFA5D05E47ADB146D8B5BDF2A5528393A7F474991 | |||
| 2132 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_fhp3solt.pug.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2124 | RBLXHUBLauncher.exe | C:\Users\admin\AppData\Local\Temp\A10F.tmp | ini | |
MD5:87479499BB892874A6C59ADA845DFC6D | SHA256:625F2616438C8BA94299565C5DFC380925E2DE942968CA609553D905CC0D0E31 | |||
| 2132 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\R6KWQN54FMHT6LHSX3CG.temp | binary | |
MD5:88A9811FC2E7C0A50D13BD39D4D1E520 | SHA256:74CB2D34A50D69D3B35F3C1FFA5D05E47ADB146D8B5BDF2A5528393A7F474991 | |||
| 2132 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_mt15yvbq.ffx.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 396 | RBLXHUBLauncher.exe | C:\Users\admin\AppData\Local\Temp\435B.tmp | ini | |
MD5:C6DBFAF3F4D59FD6C17E7623C9C3FE84 | SHA256:D3DB4EE3A2400602AF1F24845F0DFBADFFCF35AEDB6D3DEF1F3975AA9920F717 | |||
| 2124 | RBLXHUBLauncher.exe | C:\Users\admin\AppData\Local\Temp\9C97.tmp | ini | |
MD5:CF6E4FD4C1E5289840C345D61CE87D3D | SHA256:338EB529238055483789ADEF0818143EB0166E2C118B40938FCF1A13FF58D1FF | |||
| 2124 | RBLXHUBLauncher.exe | C:\Users\admin\AppData\Local\Temp\A382.tmp | ini | |
MD5:88643CA5D632E70DB63F0F4D031A24FD | SHA256:08905CA14E493537734C5FF18B487ECABA9A110834262887C217359D96CE9287 | |||
| 2132 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:289B1B0F266DEAD61B3B7459AFBBDA0A | SHA256:2C083A6A6ED19F559E5BE583CA1D505CF79C466C4719127CF5293D539D00CD60 | |||
| 2124 | RBLXHUBLauncher.exe | C:\Users\admin\AppData\Local\Temp\A248.tmp | text | |
MD5:2857A79A2BA970C716E280F7D5C3EF1E | SHA256:313DB37144EDCB97404159BD46A242C15808F6C134F9D18259EFF7354471425C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
66
TCP/UDP connections
50
DNS requests
28
Threats
64
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
396 | RBLXHUBLauncher.exe | GET | 200 | 188.114.96.3:80 | http://rblxhubdeploytest.rand744.nl/latestver | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3676 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
396 | RBLXHUBLauncher.exe | GET | 200 | 188.114.96.3:80 | http://rblxhubdeploytest.rand744.nl/ver2-requiredupdates | unknown | — | — | whitelisted |
396 | RBLXHUBLauncher.exe | GET | 200 | 188.114.96.3:80 | http://rblxhubdeploytest.rand744.nl/ver2-requiredupdates | unknown | — | — | whitelisted |
396 | RBLXHUBLauncher.exe | GET | 200 | 188.114.96.3:80 | http://rblxhubdeploytest.rand744.nl/latestver | unknown | — | — | whitelisted |
396 | RBLXHUBLauncher.exe | GET | 200 | 188.114.96.3:80 | http://rblxhubdeploytest.rand744.nl/ver3-requiredupdates | unknown | — | — | whitelisted |
4132 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1256 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1028 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 2.20.142.145:443 | www.bing.com | Akamai International B.V. | DE | unknown |
6012 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1272 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2616 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1044 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6480 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
t-ring-fdv2.msedge.net |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
a-ring-fallback.msedge.net |
| unknown |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
fp-afd-nocache-ccp.azureedge.net |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
396 | RBLXHUBLauncher.exe | Potential Corporate Privacy Violation | ET POLICY Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
396 | RBLXHUBLauncher.exe | Potential Corporate Privacy Violation | ET POLICY Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
396 | RBLXHUBLauncher.exe | Potential Corporate Privacy Violation | ET POLICY Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
396 | RBLXHUBLauncher.exe | Potential Corporate Privacy Violation | ET POLICY Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
396 | RBLXHUBLauncher.exe | Potential Corporate Privacy Violation | ET POLICY Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
2124 | RBLXHUBLauncher.exe | Potential Corporate Privacy Violation | ET POLICY Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
2124 | RBLXHUBLauncher.exe | Potential Corporate Privacy Violation | ET POLICY Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
2124 | RBLXHUBLauncher.exe | Potential Corporate Privacy Violation | ET POLICY Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
2124 | RBLXHUBLauncher.exe | Potential Corporate Privacy Violation | ET POLICY Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
2124 | RBLXHUBLauncher.exe | Potential Corporate Privacy Violation | ET POLICY Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |