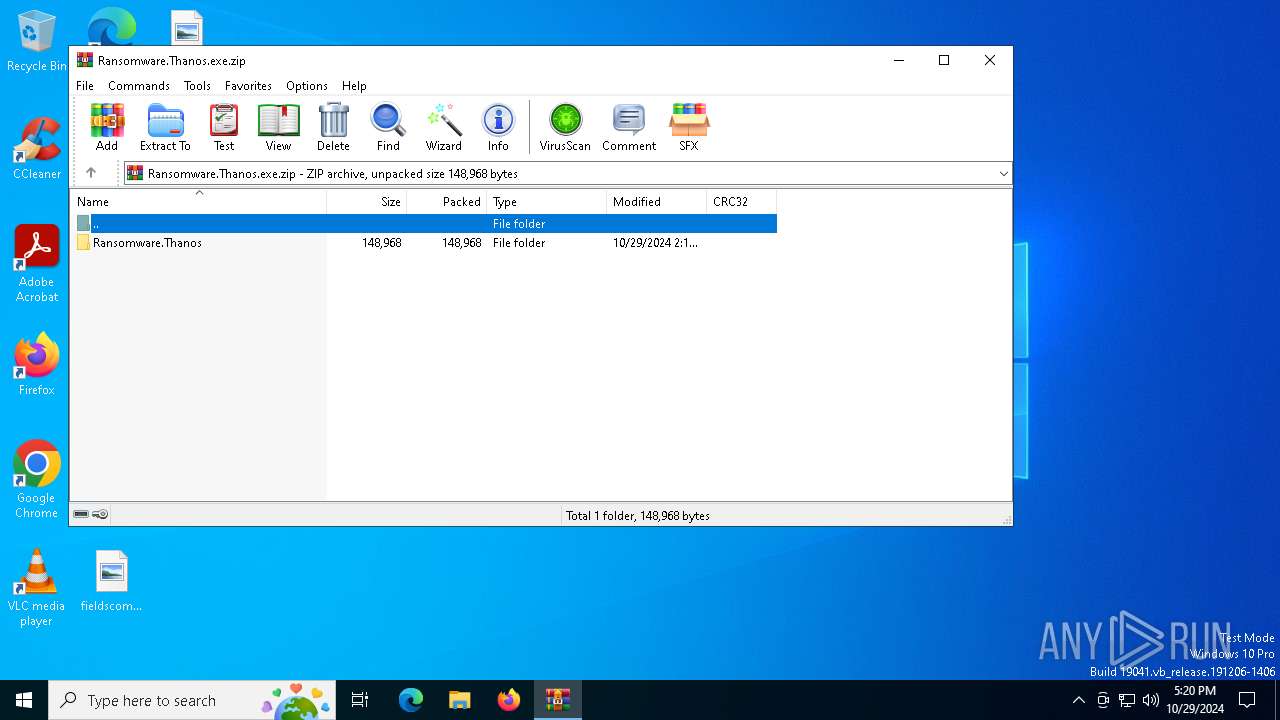
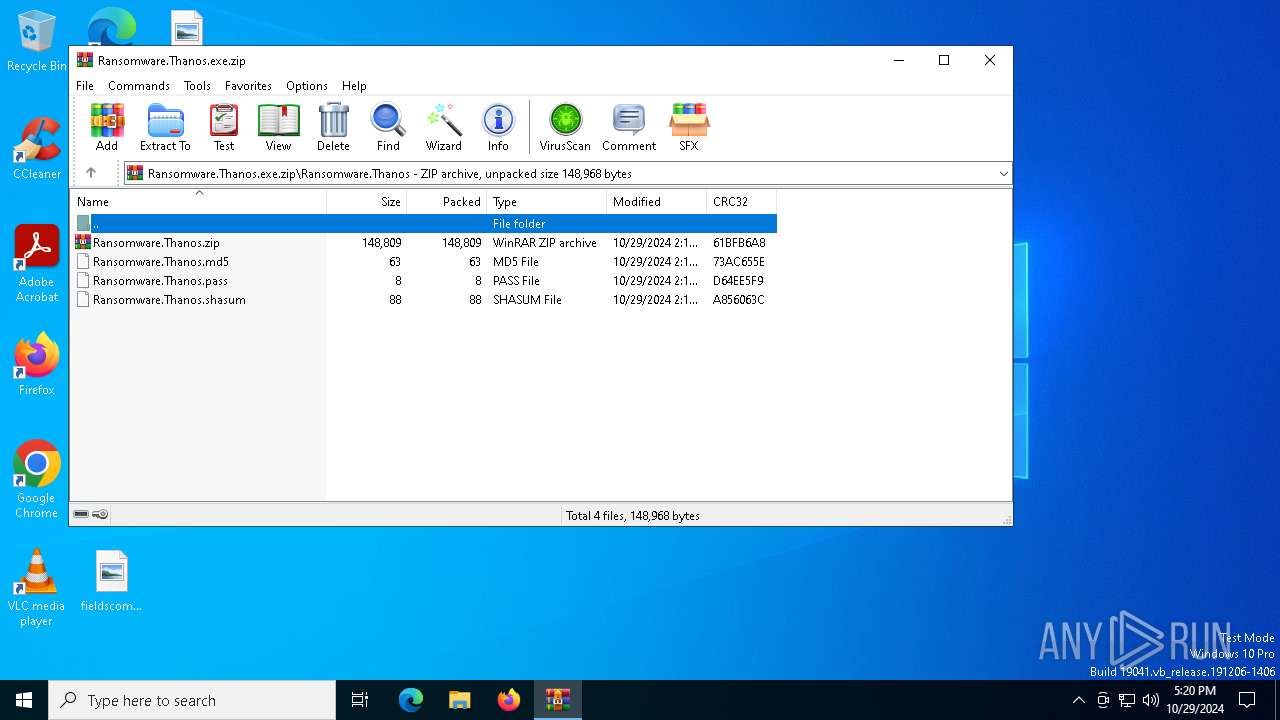
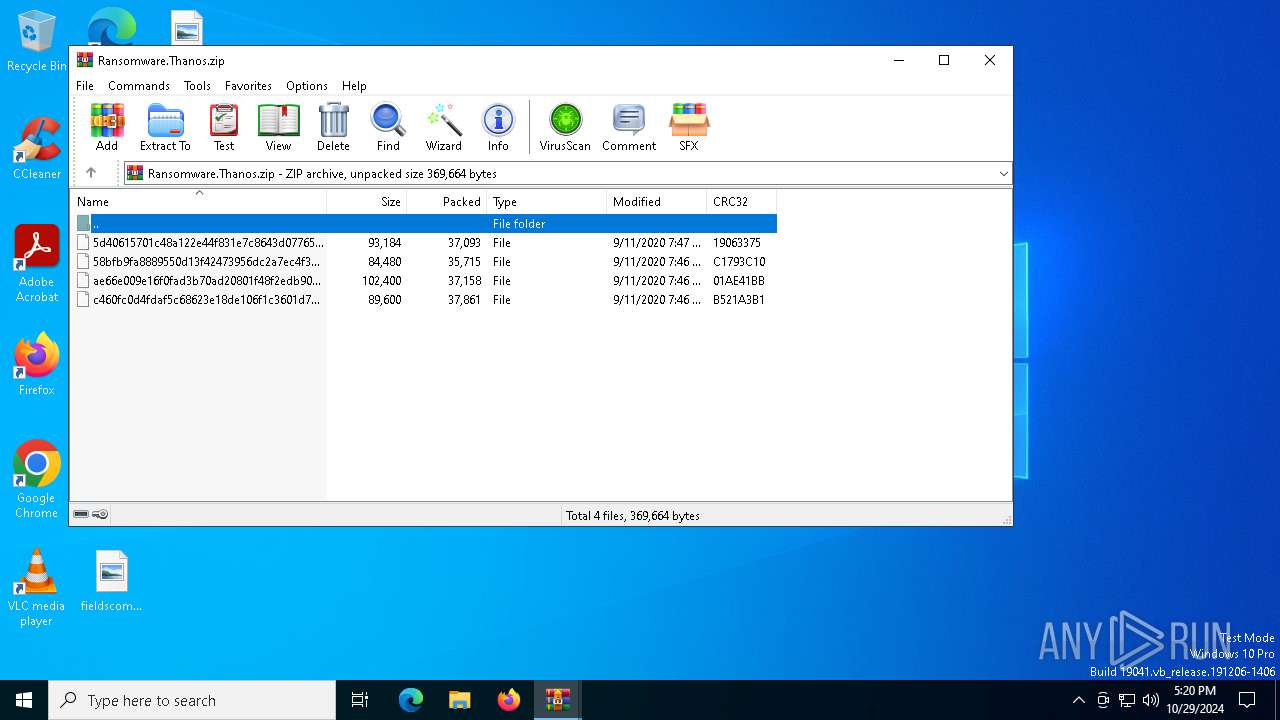
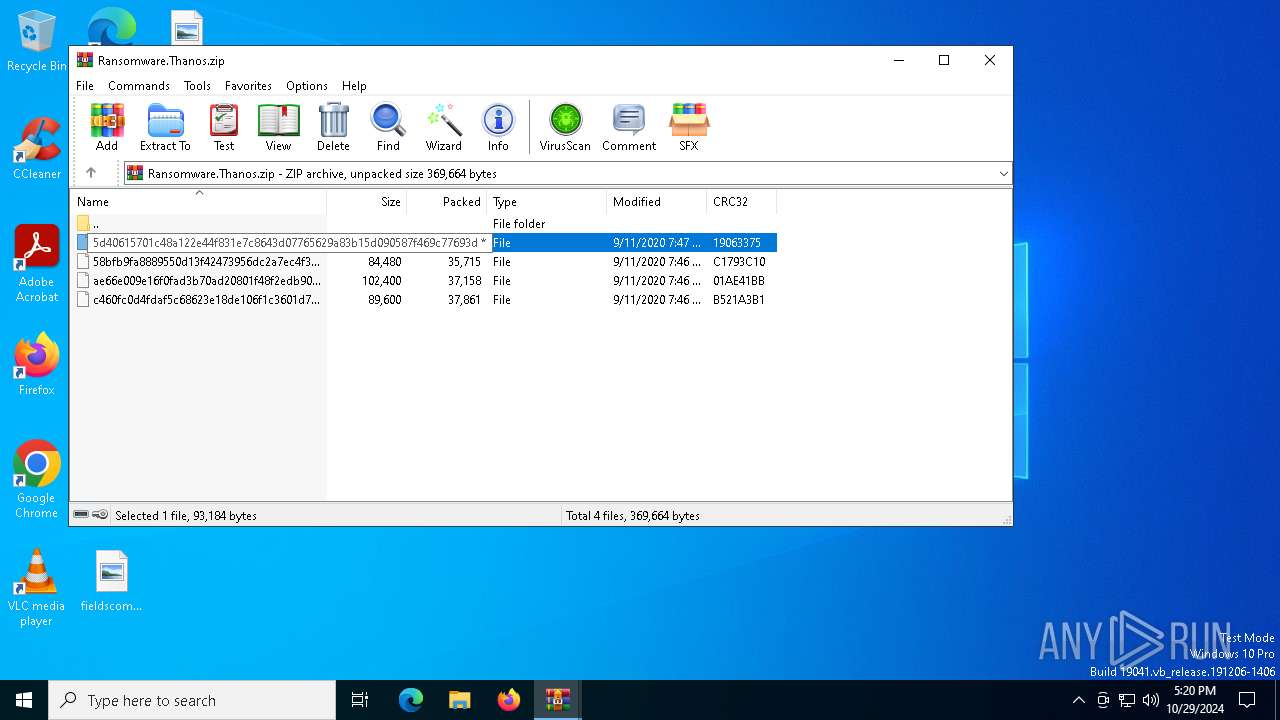
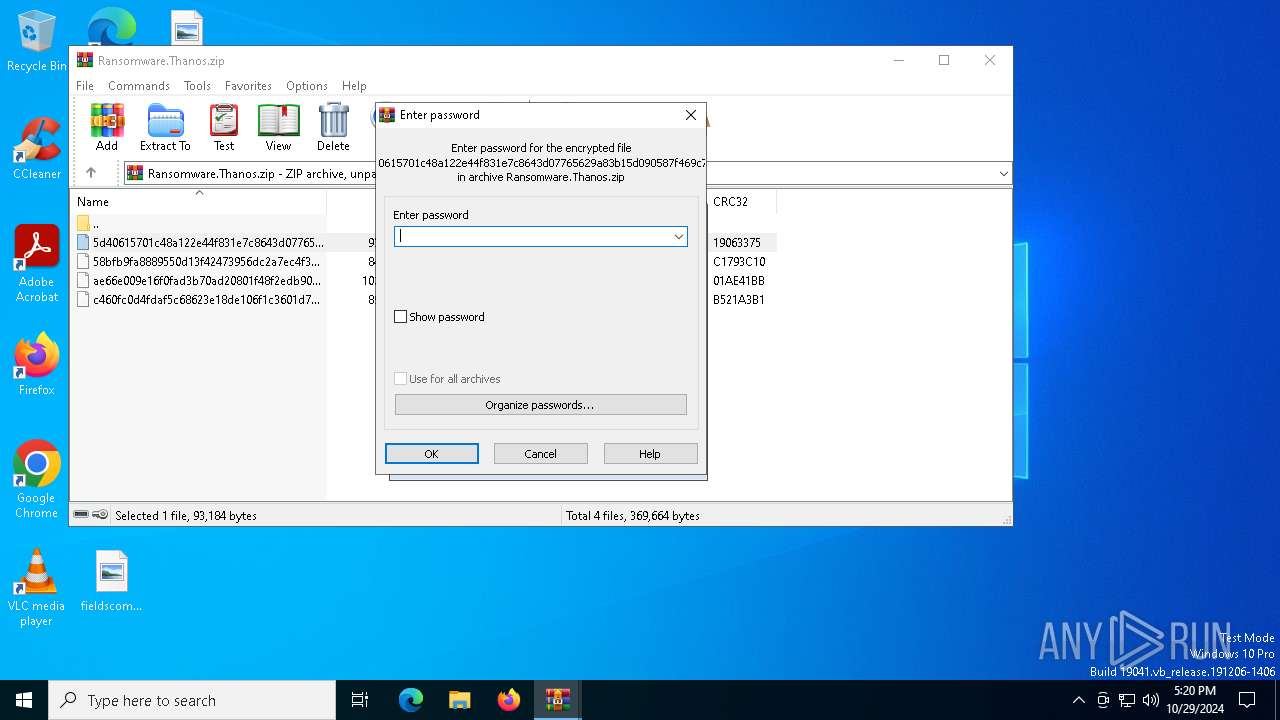
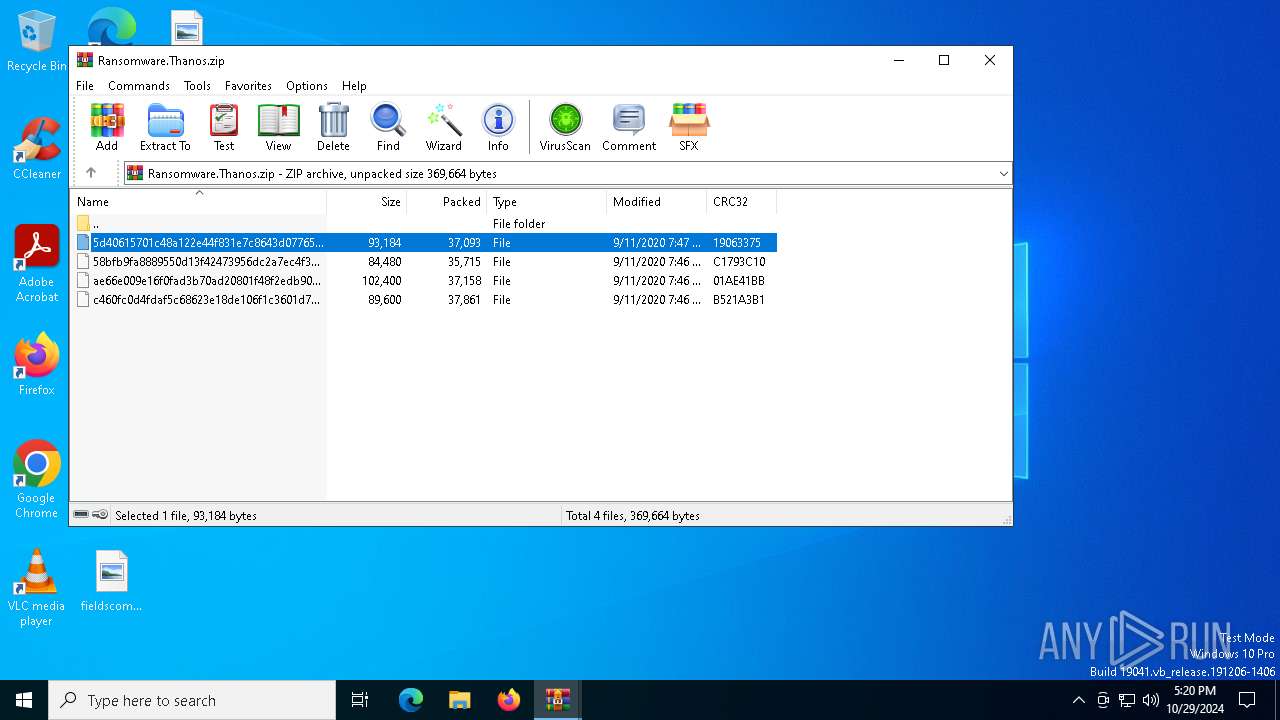
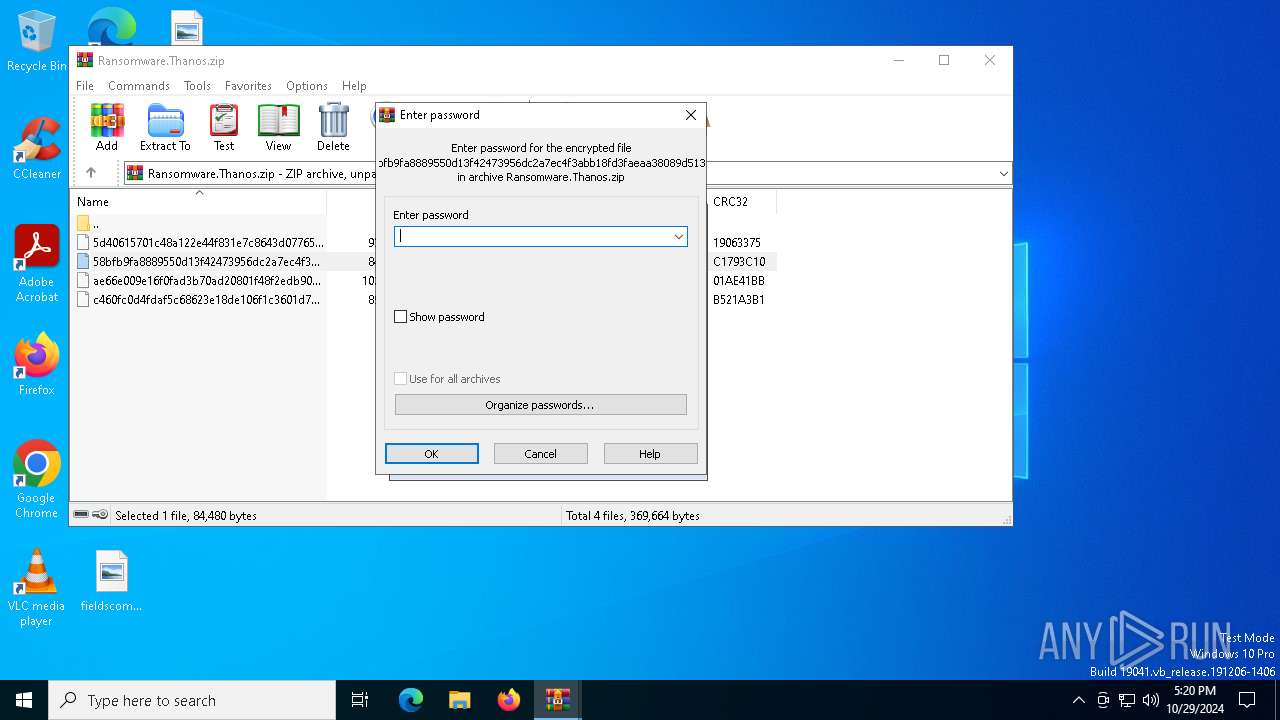
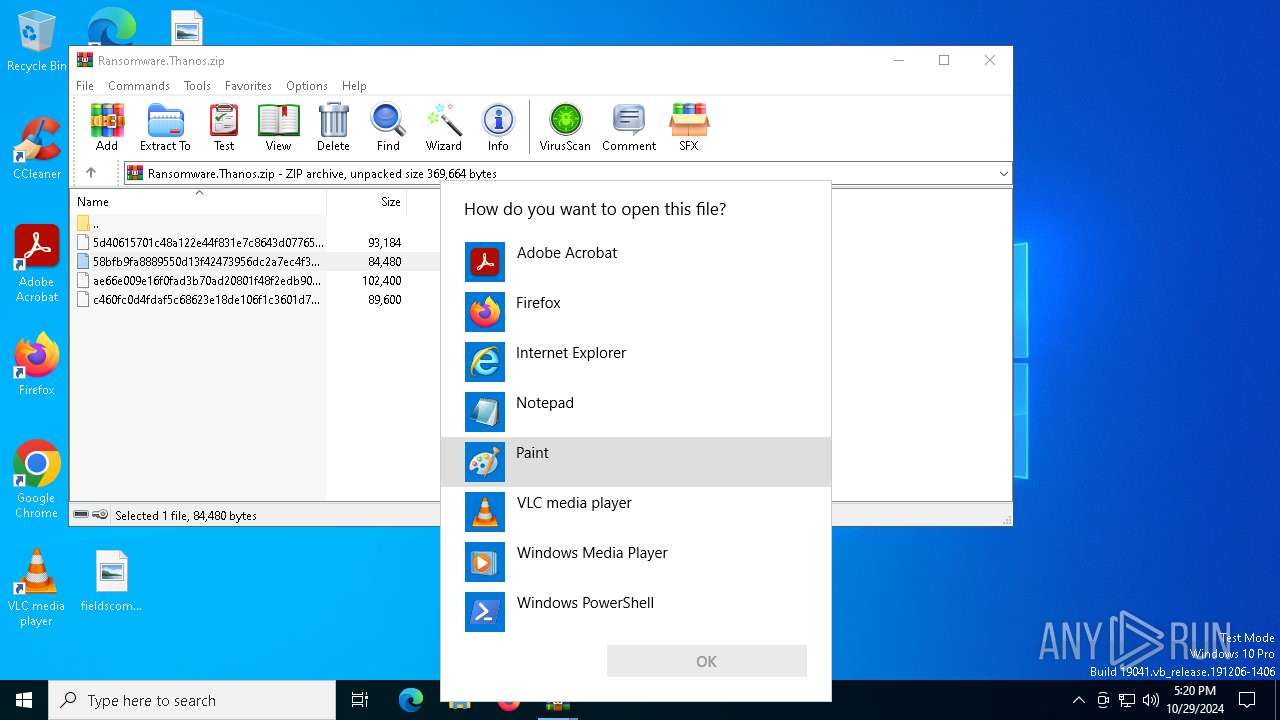
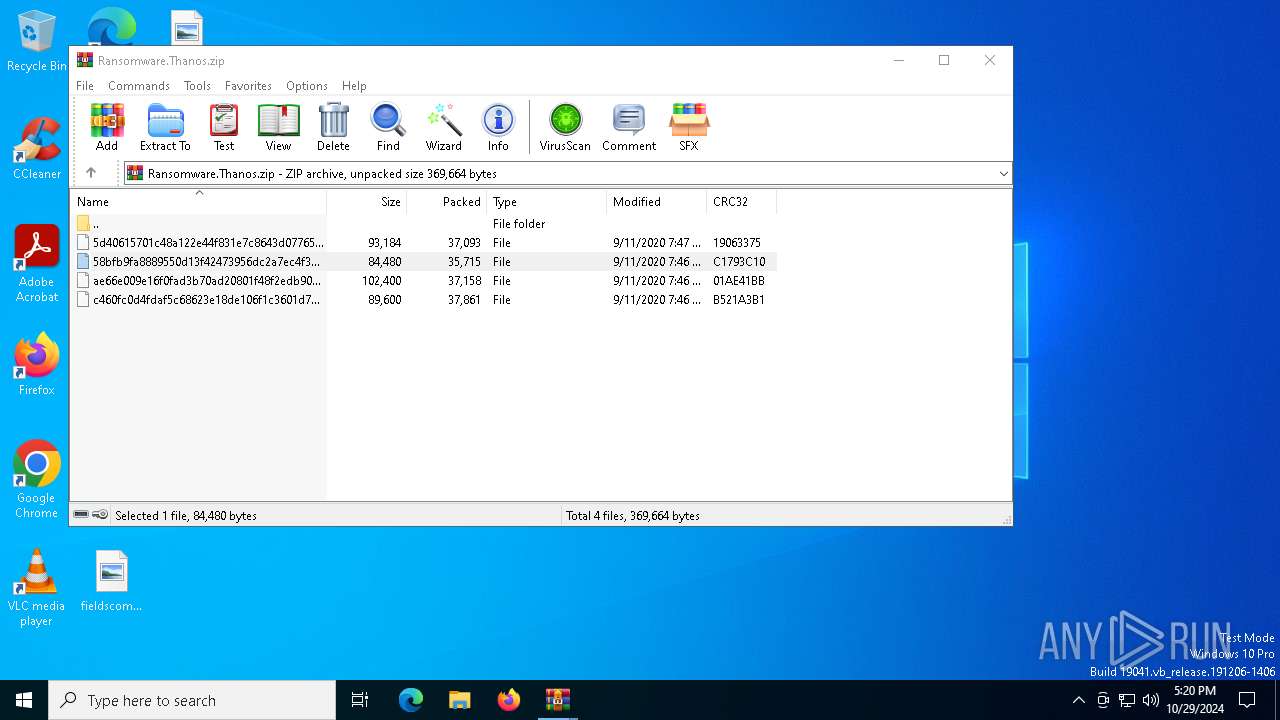
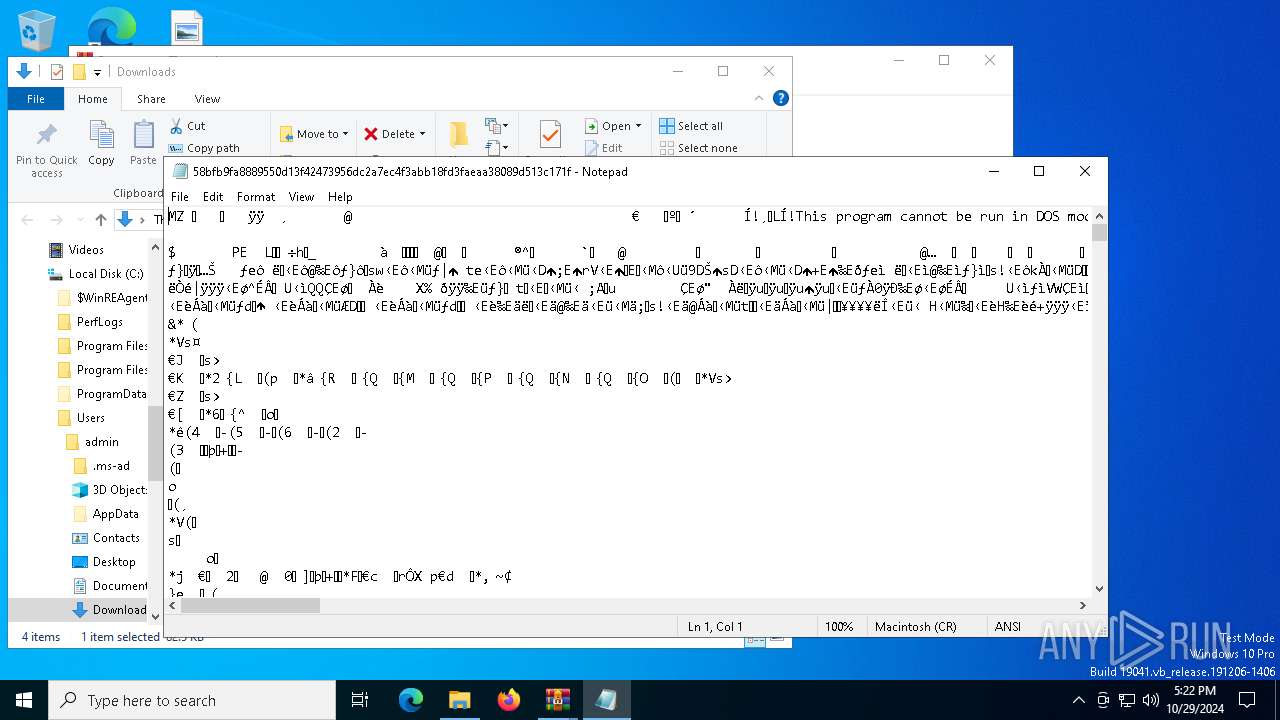
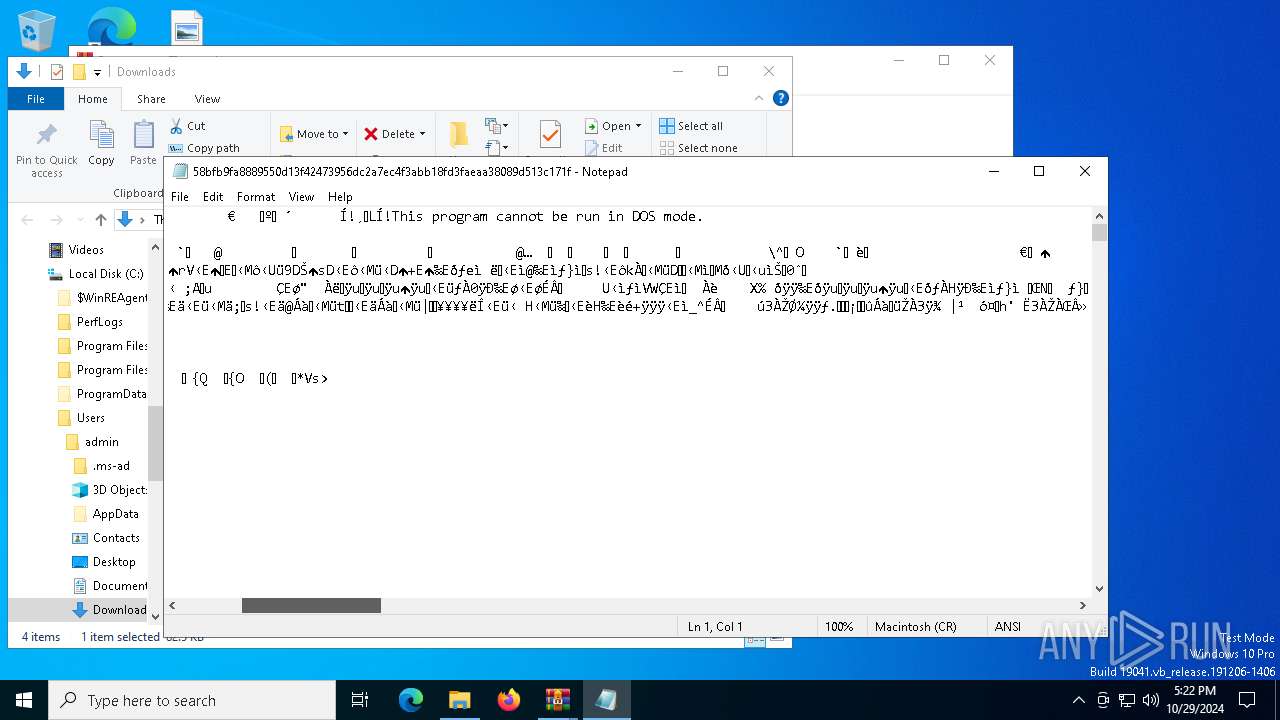
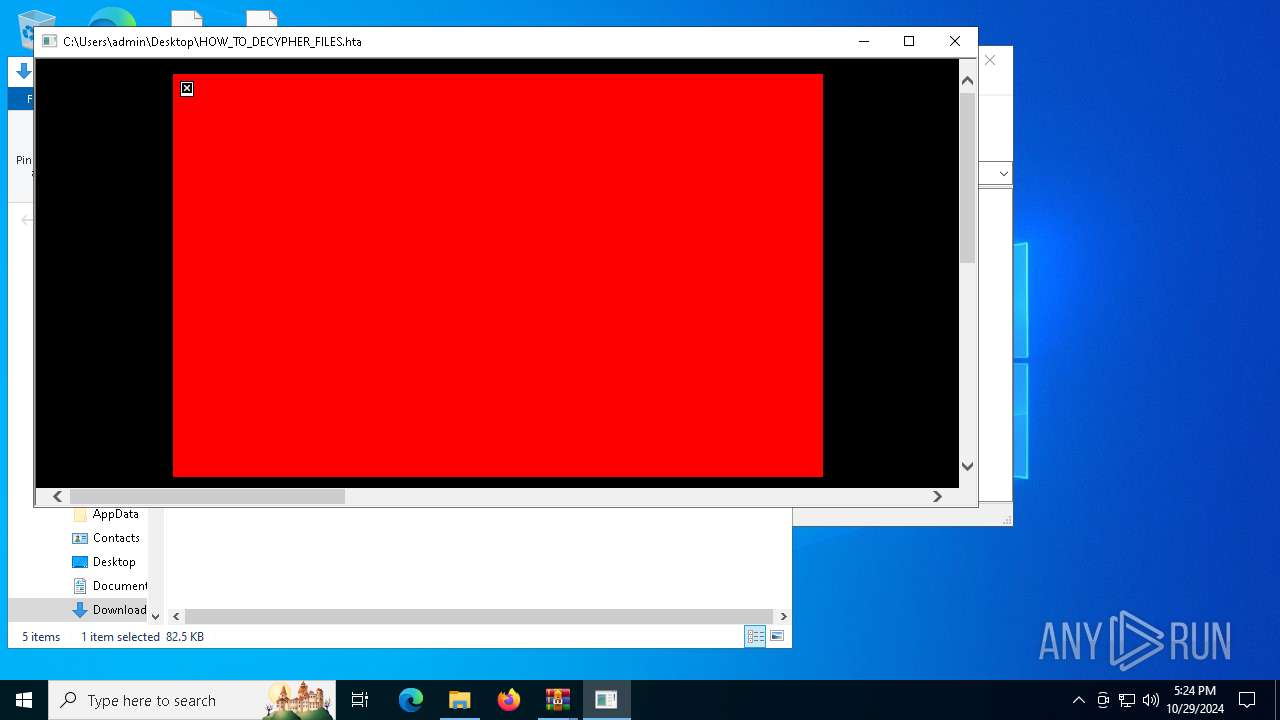
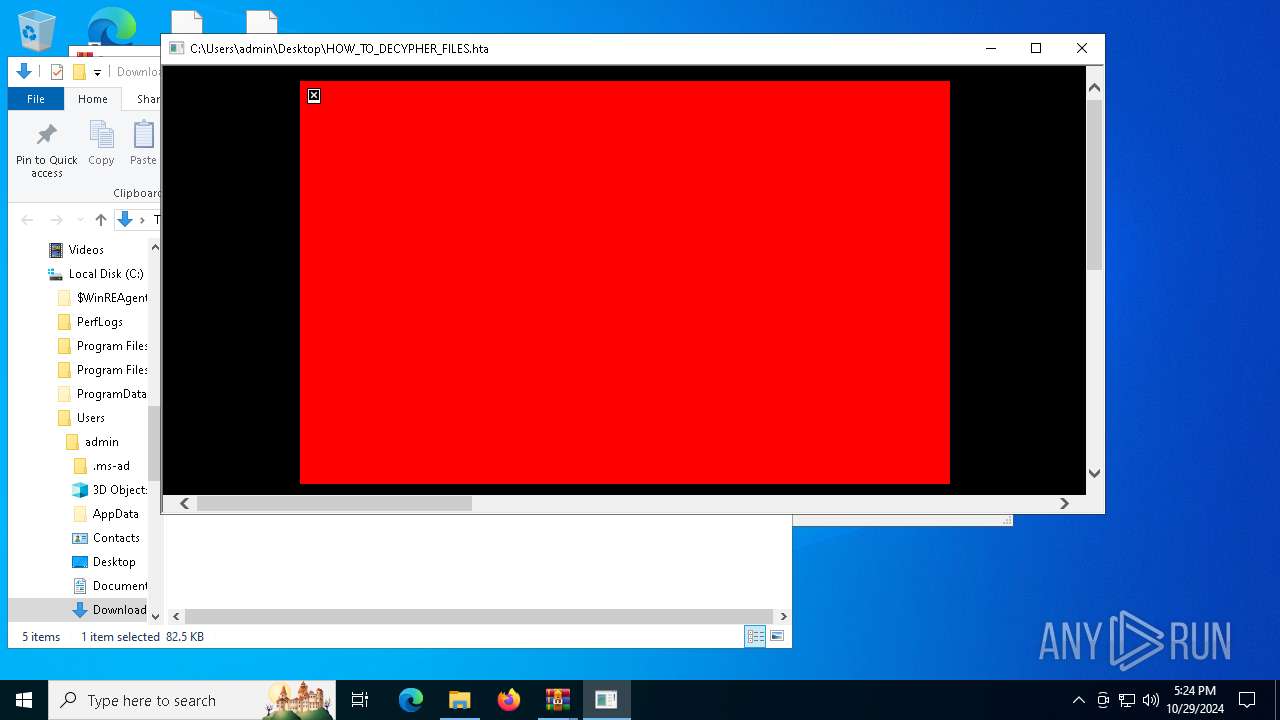
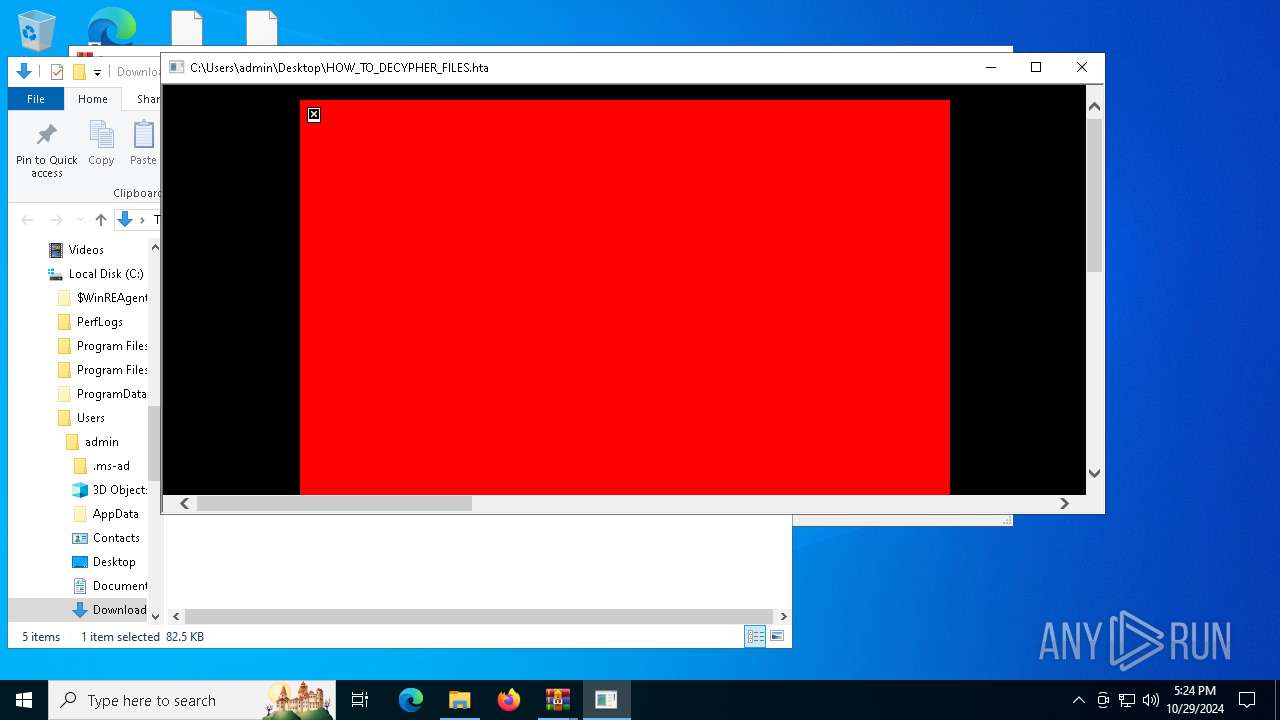
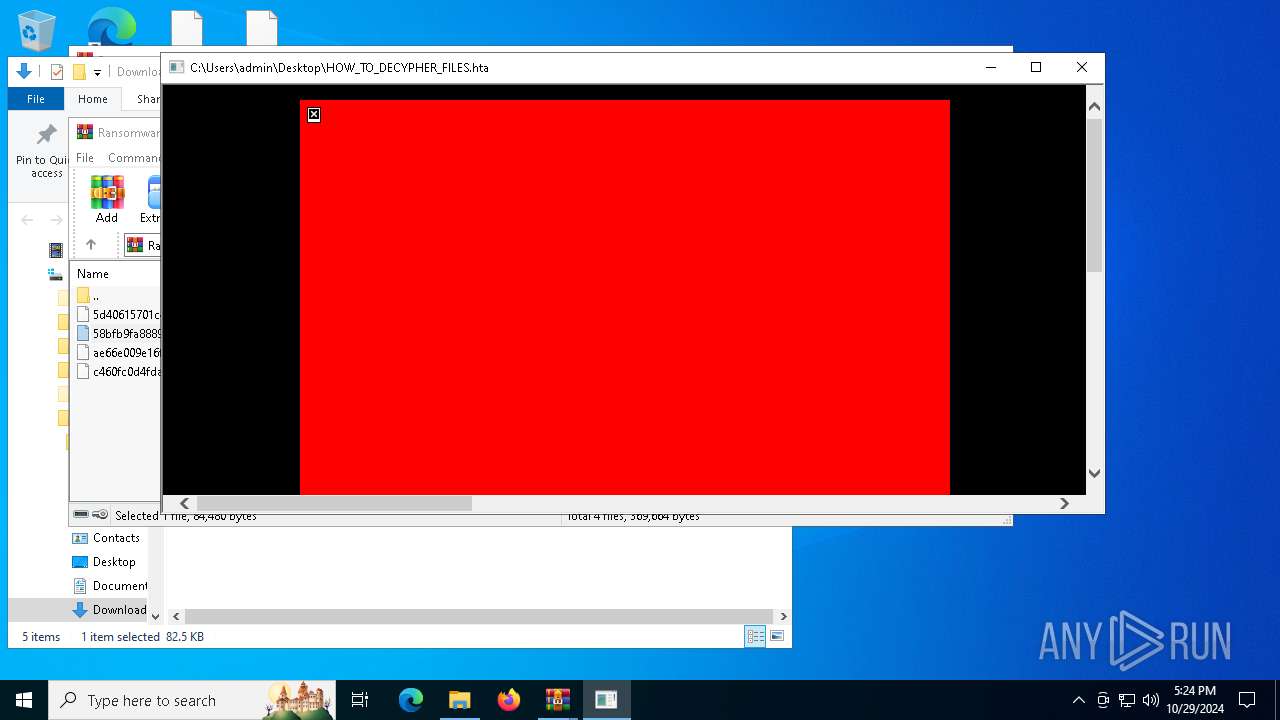
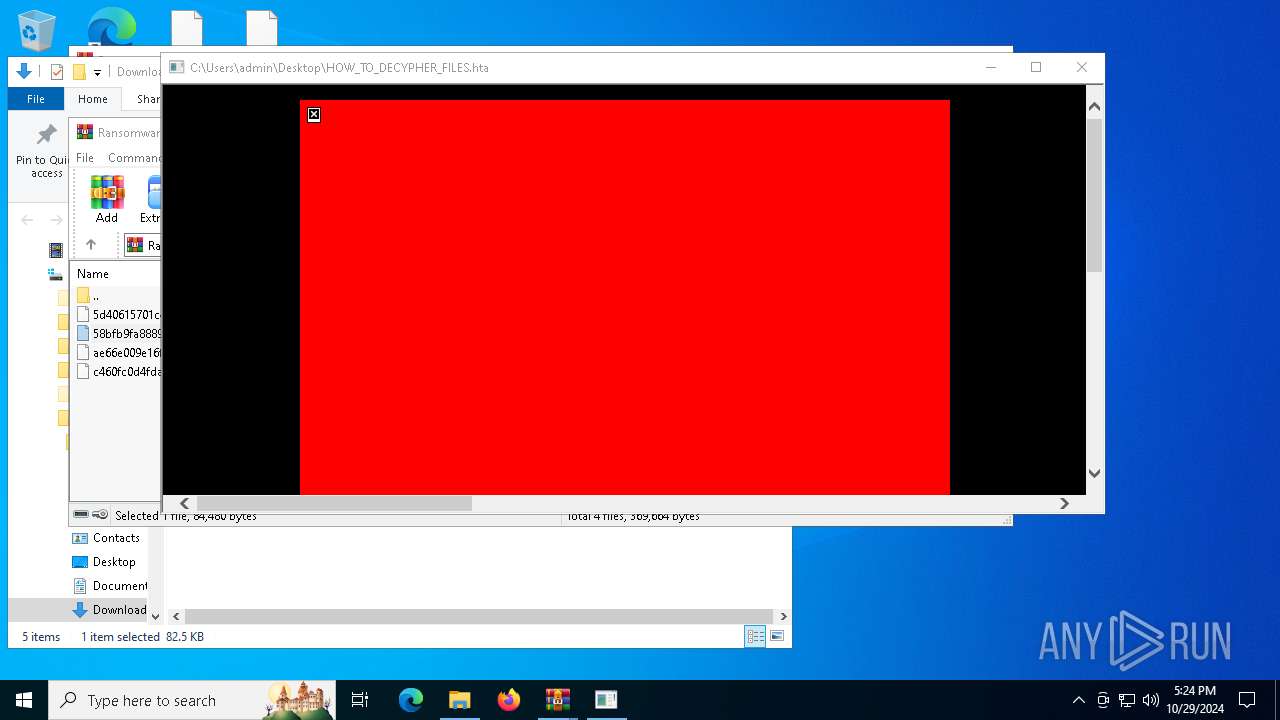
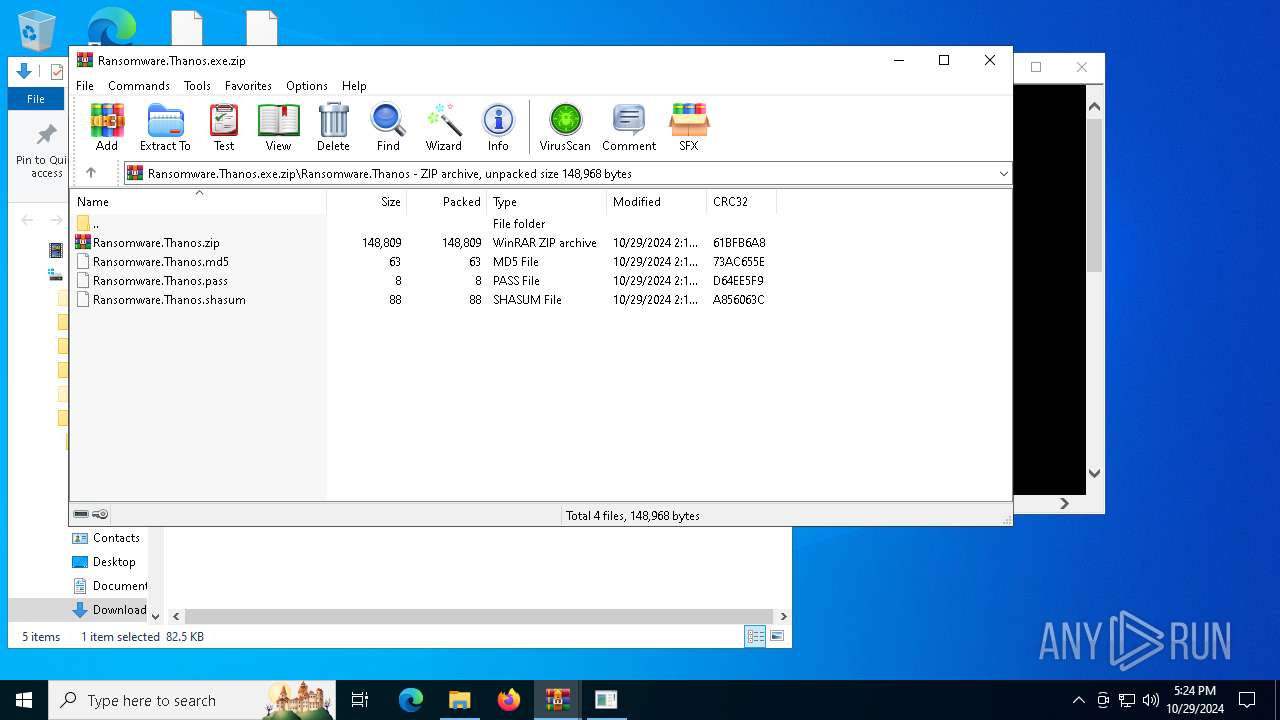
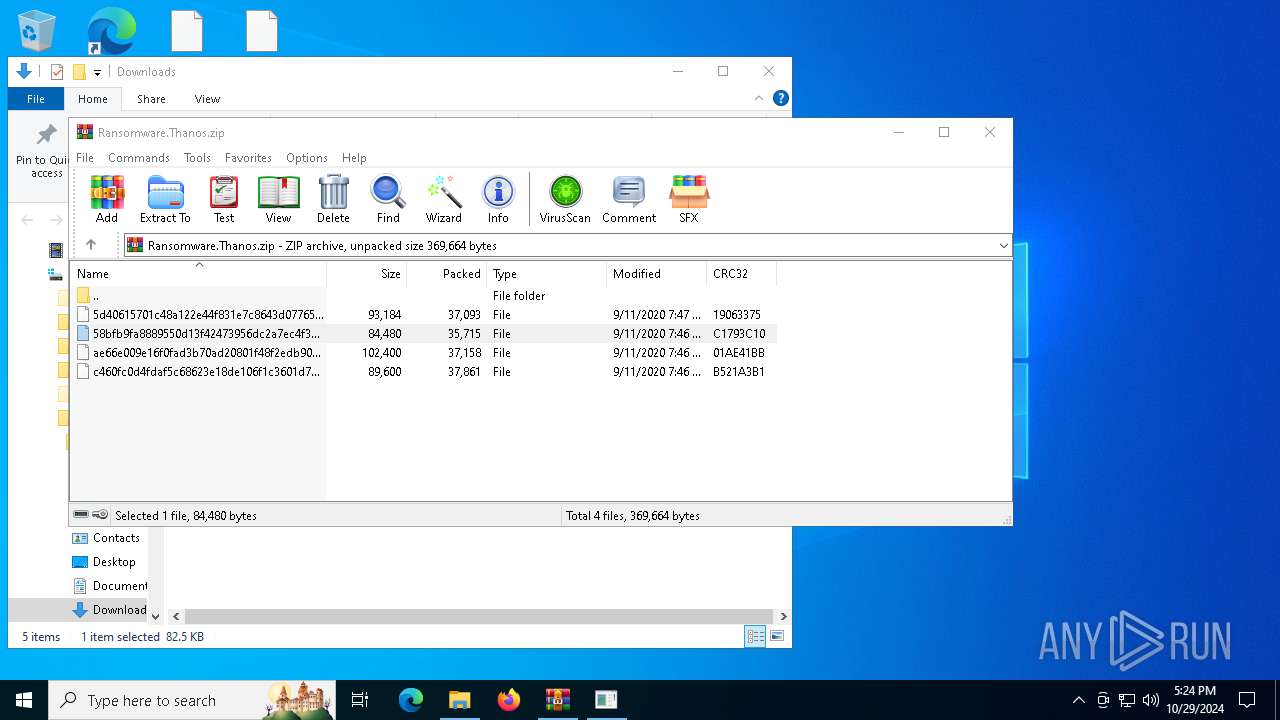
| File name: | Ransomware.Thanos.exe |
| Full analysis: | https://app.any.run/tasks/5cd24147-479a-49ac-9748-7ff7d9986a04 |
| Verdict: | Malicious activity |
| Analysis date: | October 29, 2024, 17:20:00 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 4A52D0A2F4450E97A07BF146777218D6 |
| SHA1: | 5656D5EBD83B42F999EBAF4419C96AB10ADA8F9C |
| SHA256: | EB4E7880BF324A5E22BFA858B9D1BE790D270AEEA8CABF0CCD85F4D9093D362D |
| SSDEEP: | 6144:BW0dXPcx/ybnXBBuROcXlWKoUdAb2Vqle8/gg:BWyXO/y7XBBaOc1WK/dxqlf |
MALICIOUS
Windows Defender preferences modified via 'Set-MpPreference'
- 58bfb9fa8889550d13f42473956dc2a7ec4f3abb18fd3faeaa38089d513c171f.exe (PID: 7688)
Starts NET.EXE for service management
- net.exe (PID: 8060)
- net.exe (PID: 6304)
- net.exe (PID: 6448)
- net.exe (PID: 2236)
- net.exe (PID: 7692)
- net.exe (PID: 8056)
- net.exe (PID: 7936)
- net.exe (PID: 8172)
- 58bfb9fa8889550d13f42473956dc2a7ec4f3abb18fd3faeaa38089d513c171f.exe (PID: 7688)
- net.exe (PID: 7996)
- net.exe (PID: 8028)
- net.exe (PID: 2652)
- net.exe (PID: 5524)
- net.exe (PID: 5036)
- net.exe (PID: 6296)
- net.exe (PID: 7696)
- net.exe (PID: 2280)
- net.exe (PID: 7028)
- net.exe (PID: 7620)
- net.exe (PID: 7924)
- net.exe (PID: 7152)
- net.exe (PID: 6844)
- net.exe (PID: 6660)
- net.exe (PID: 6440)
- net.exe (PID: 6196)
- net.exe (PID: 7660)
- net.exe (PID: 8036)
- net.exe (PID: 7220)
- net.exe (PID: 6632)
- net.exe (PID: 1572)
- net.exe (PID: 2056)
- net.exe (PID: 7236)
- net.exe (PID: 2140)
- net.exe (PID: 7804)
- net.exe (PID: 5756)
- net.exe (PID: 4516)
- net.exe (PID: 7120)
Changes settings for checking scripts for malicious actions
- powershell.exe (PID: 3076)
Deletes shadow copies
- 58bfb9fa8889550d13f42473956dc2a7ec4f3abb18fd3faeaa38089d513c171f.exe (PID: 7688)
Resizes shadow copies
- 58bfb9fa8889550d13f42473956dc2a7ec4f3abb18fd3faeaa38089d513c171f.exe (PID: 7688)
Starts CMD.EXE for self-deleting
- 58bfb9fa8889550d13f42473956dc2a7ec4f3abb18fd3faeaa38089d513c171f.exe (PID: 7688)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 512)
Generic archive extractor
- WinRAR.exe (PID: 512)
Executable content was dropped or overwritten
- 58bfb9fa8889550d13f42473956dc2a7ec4f3abb18fd3faeaa38089d513c171f.exe (PID: 7688)
Query Microsoft Defender preferences
- 58bfb9fa8889550d13f42473956dc2a7ec4f3abb18fd3faeaa38089d513c171f.exe (PID: 7688)
Starts POWERSHELL.EXE for commands execution
- 58bfb9fa8889550d13f42473956dc2a7ec4f3abb18fd3faeaa38089d513c171f.exe (PID: 7688)
Starts CMD.EXE for commands execution
- 58bfb9fa8889550d13f42473956dc2a7ec4f3abb18fd3faeaa38089d513c171f.exe (PID: 7688)
Starts SC.EXE for service management
- 58bfb9fa8889550d13f42473956dc2a7ec4f3abb18fd3faeaa38089d513c171f.exe (PID: 7688)
Uses TASKKILL.EXE to kill process
- 58bfb9fa8889550d13f42473956dc2a7ec4f3abb18fd3faeaa38089d513c171f.exe (PID: 7688)
Hides command output
- cmd.exe (PID: 8792)
Sets range of bytes to zero
- fsutil.exe (PID: 9228)
INFO
Executable content was dropped or overwritten
- msedge.exe (PID: 3396)
- WinRAR.exe (PID: 4236)
- msedge.exe (PID: 7100)
Manual execution by a user
- mspaint.exe (PID: 7880)
- mspaint.exe (PID: 6488)
- 58bfb9fa8889550d13f42473956dc2a7ec4f3abb18fd3faeaa38089d513c171f.exe (PID: 7640)
- 58bfb9fa8889550d13f42473956dc2a7ec4f3abb18fd3faeaa38089d513c171f.exe (PID: 7688)
- mspaint.exe (PID: 7300)
Application launched itself
- msedge.exe (PID: 3396)
- msedge.exe (PID: 6704)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:10:29 14:14:48 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Ransomware.Thanos/ |
Total processes
395
Monitored processes
257
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 512 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Ransomware.Thanos.exe.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 528 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=3404 --field-trial-handle=2332,i,9294564789053002205,13147090834006507576,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 696 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3860 --field-trial-handle=2332,i,9294564789053002205,13147090834006507576,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 864 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5180 --field-trial-handle=2332,i,9294564789053002205,13147090834006507576,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 1236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1248 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x290,0x294,0x298,0x288,0x2a0,0x7ffbcaf05fd8,0x7ffbcaf05fe4,0x7ffbcaf05ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1336 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1336 | "sc.exe" config SQLWriter start= disabled | C:\Windows\System32\sc.exe | — | 58bfb9fa8889550d13f42473956dc2a7ec4f3abb18fd3faeaa38089d513c171f.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1428 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5568 --field-trial-handle=2332,i,9294564789053002205,13147090834006507576,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1552 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
45 146
Read events
44 992
Write events
151
Delete events
3
Modification events
| (PID) Process: | (512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Ransomware.Thanos.exe.zip | |||
| (PID) Process: | (512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (4236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\AppData\Local\Temp\Ransomware.Thanos.exe.zip | |||
| (PID) Process: | (4236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Rar$DIa512.22639\Ransomware.Thanos.zip | |||
| (PID) Process: | (4236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
Executable files
9
Suspicious files
393
Text files
164
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3396 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF961ac.TMP | — | |
MD5:— | SHA256:— | |||
| 3396 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF961ac.TMP | — | |
MD5:— | SHA256:— | |||
| 3396 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3396 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3396 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF961bb.TMP | — | |
MD5:— | SHA256:— | |||
| 3396 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF961bb.TMP | — | |
MD5:— | SHA256:— | |||
| 3396 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3396 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3396 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF961bb.TMP | — | |
MD5:— | SHA256:— | |||
| 3396 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
48
TCP/UDP connections
76
DNS requests
71
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4004 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1200 | svchost.exe | HEAD | 200 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/181d62d0-8e71-4ab0-b6f0-62f746749689?P1=1730381579&P2=404&P3=2&P4=SEeDfLZ5yuUs7fEh8lHGQWMF7cDx%2birDpgSBssTPC8PnH6w%2fM9%2b1aElh8pD8Odpj9HFF2CwdauQ3IiWzx5Ptrg%3d%3d | unknown | — | — | whitelisted |
7164 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4060 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7164 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1200 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/181d62d0-8e71-4ab0-b6f0-62f746749689?P1=1730381579&P2=404&P3=2&P4=SEeDfLZ5yuUs7fEh8lHGQWMF7cDx%2birDpgSBssTPC8PnH6w%2fM9%2b1aElh8pD8Odpj9HFF2CwdauQ3IiWzx5Ptrg%3d%3d | unknown | — | — | whitelisted |
1200 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/181d62d0-8e71-4ab0-b6f0-62f746749689?P1=1730381579&P2=404&P3=2&P4=SEeDfLZ5yuUs7fEh8lHGQWMF7cDx%2birDpgSBssTPC8PnH6w%2fM9%2b1aElh8pD8Odpj9HFF2CwdauQ3IiWzx5Ptrg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3524 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.48.23.147:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4360 | SearchApp.exe | 2.16.110.170:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |