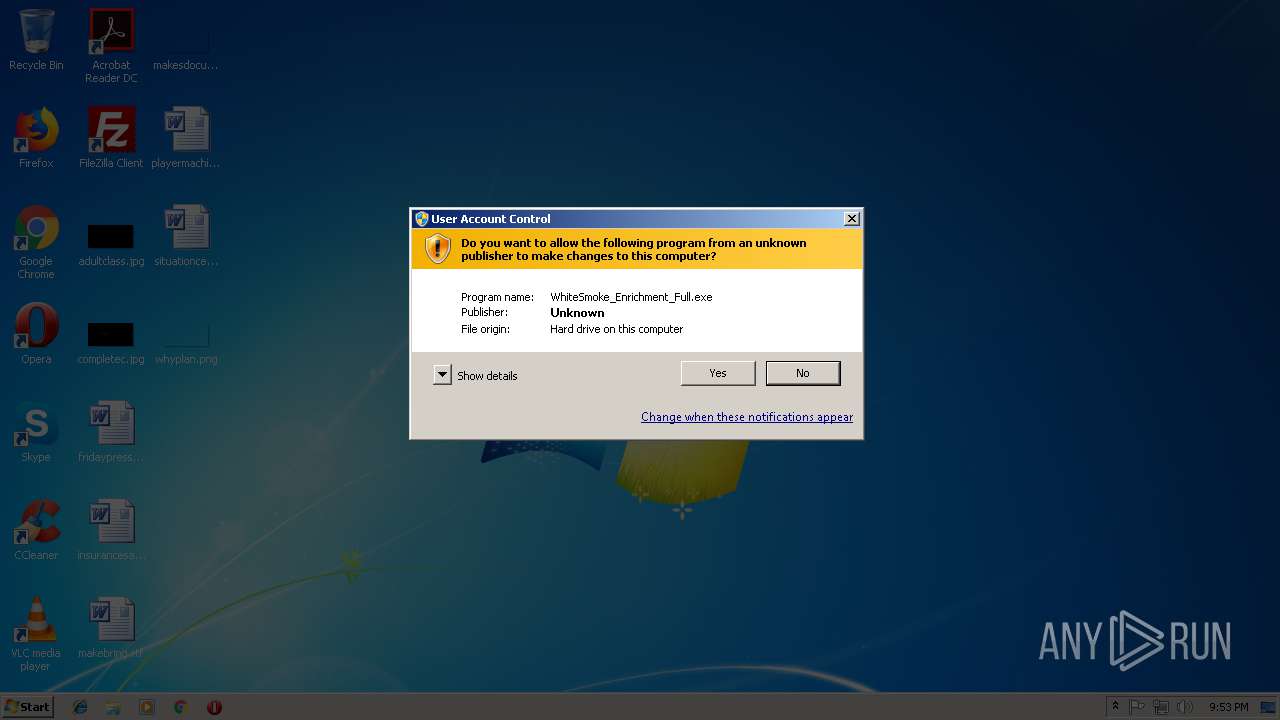
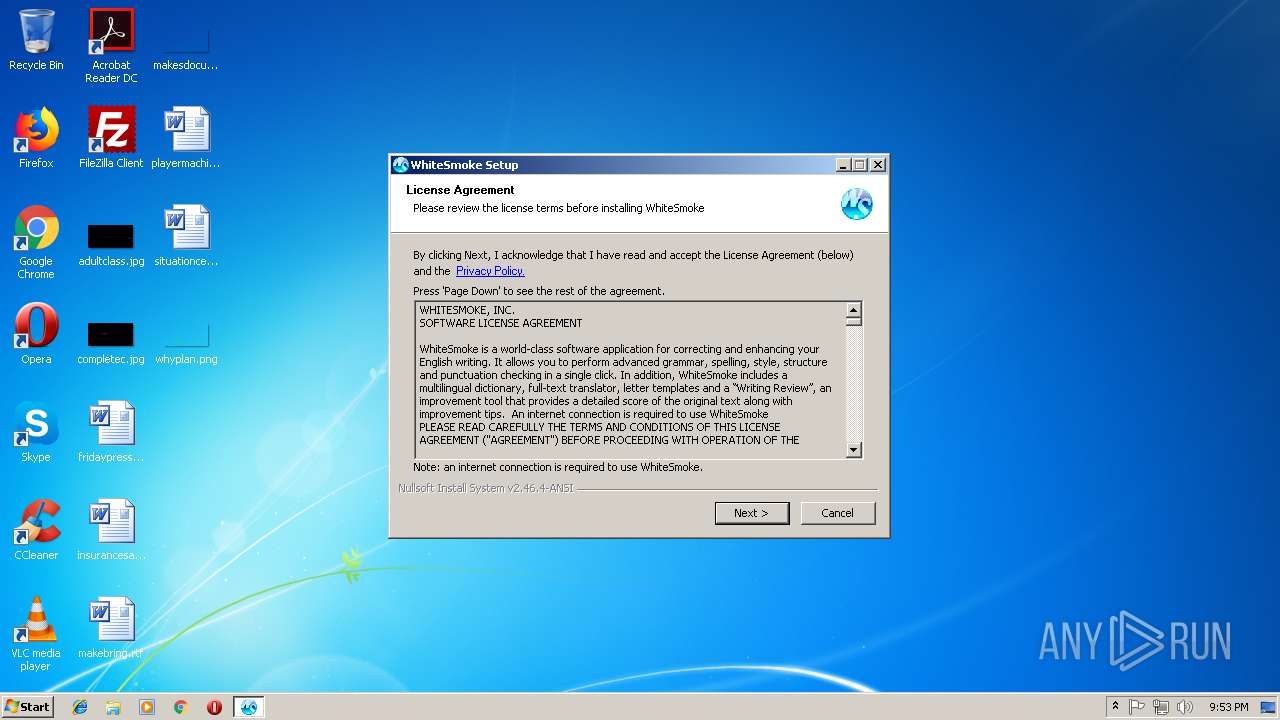
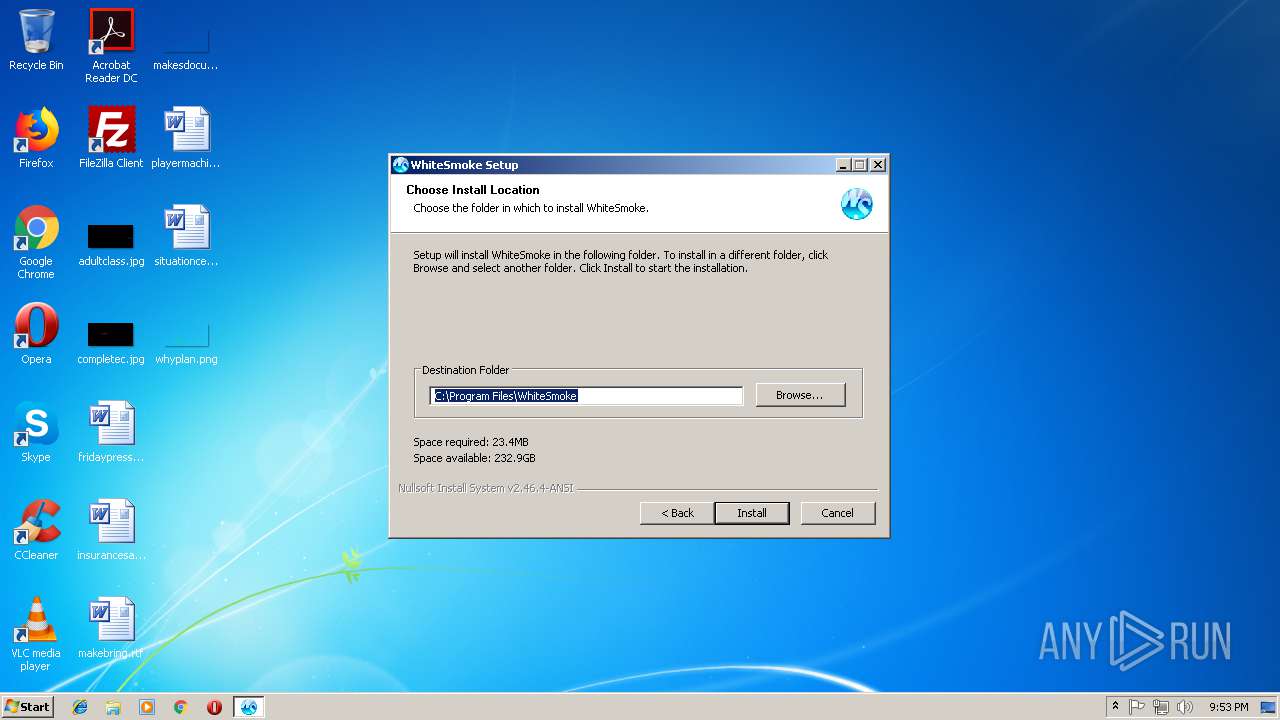
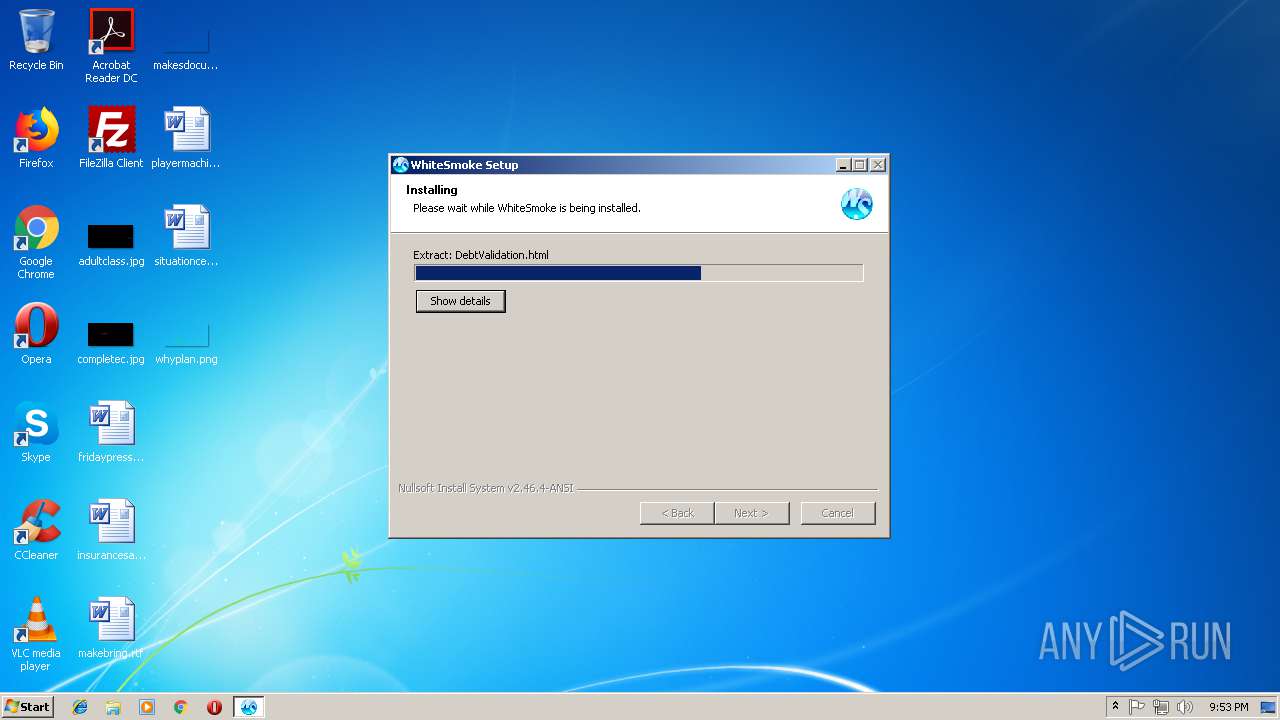
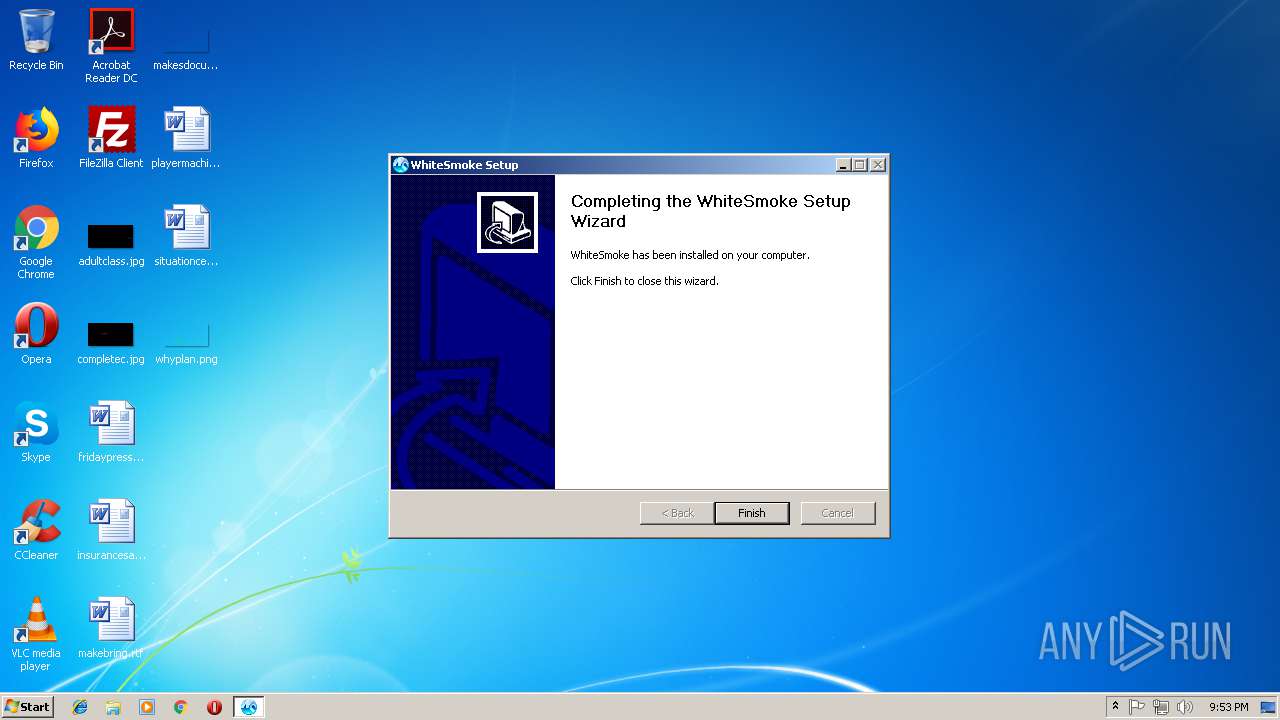
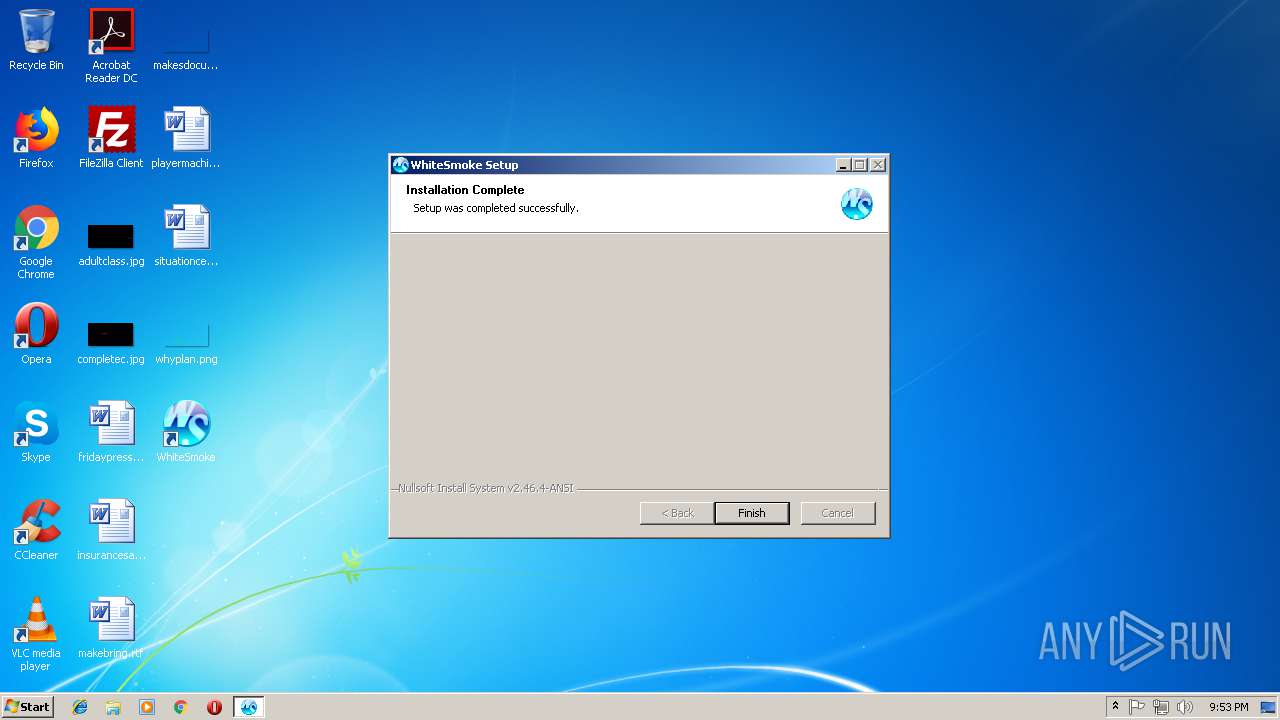
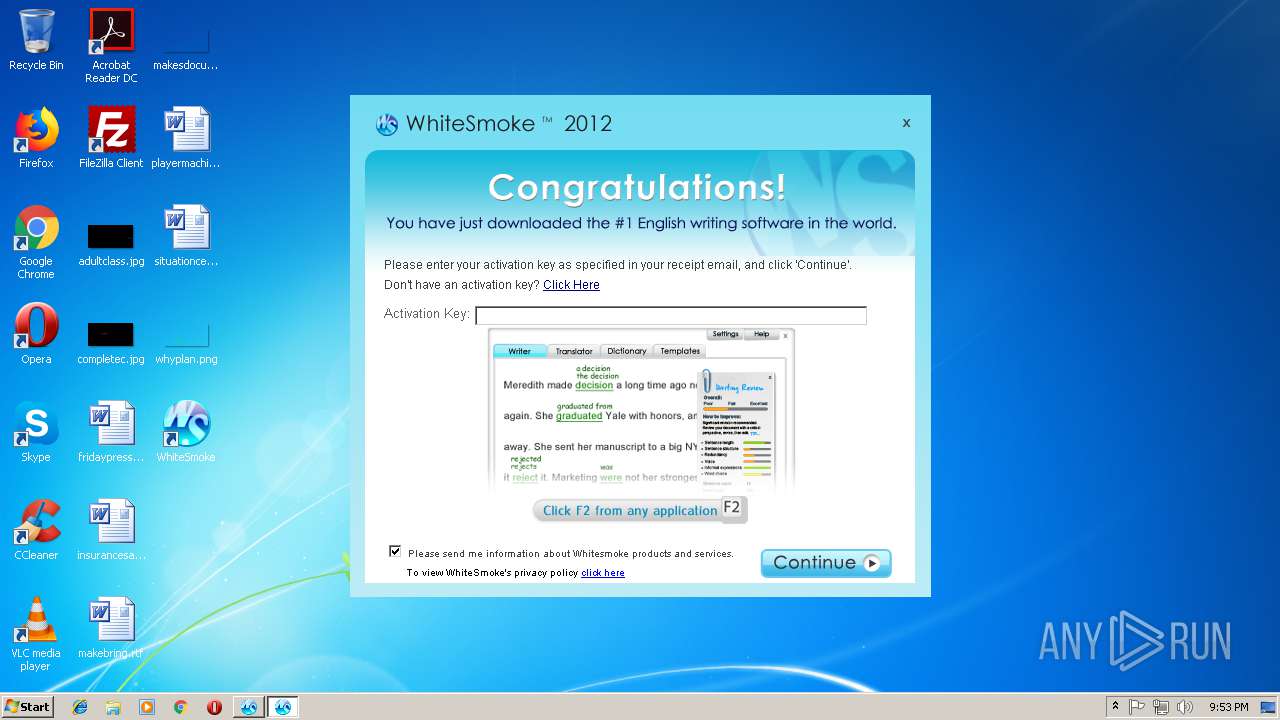
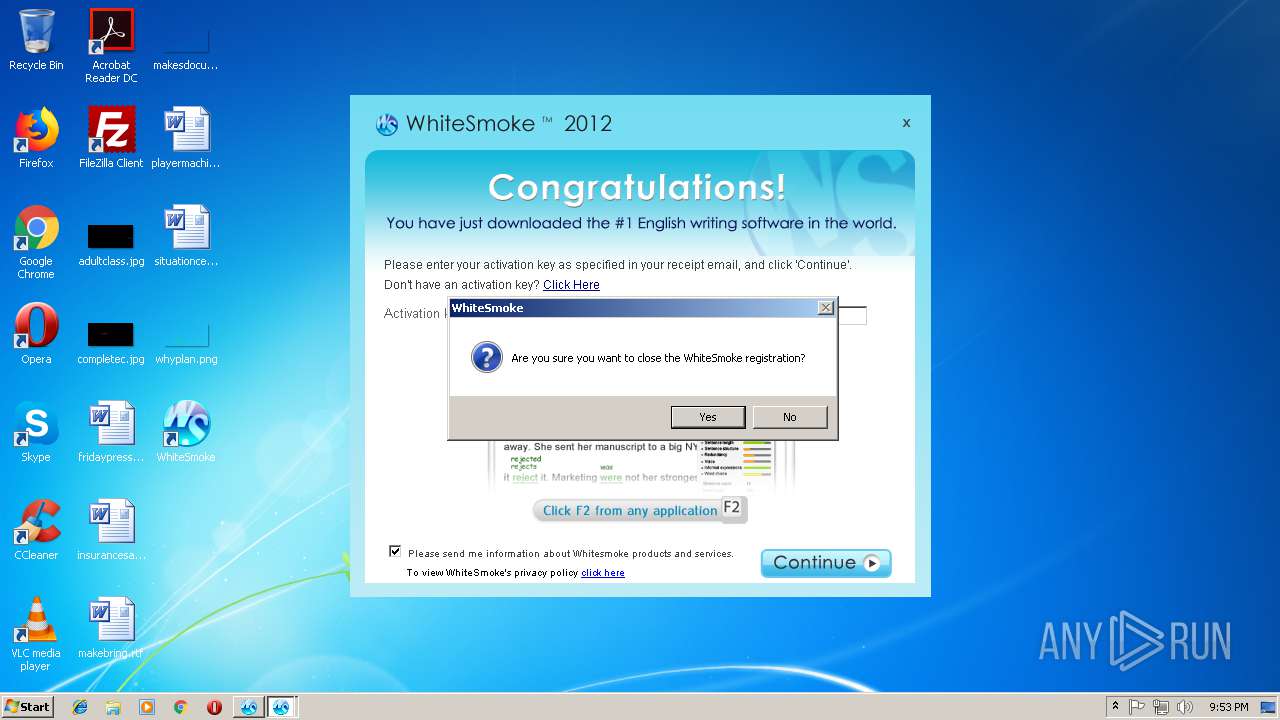
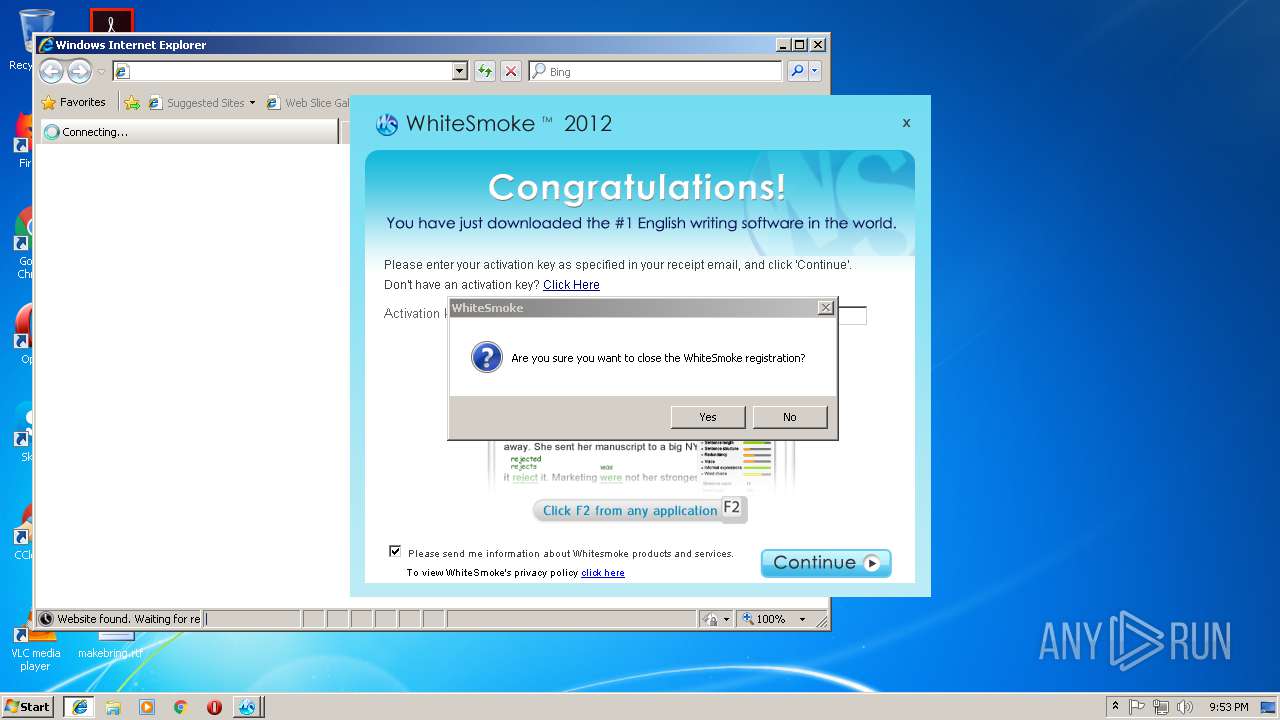
| File name: | WhiteSmoke_Enrichment_Full.exe |
| Full analysis: | https://app.any.run/tasks/906086b5-46bd-49de-bca0-f666b6560622 |
| Verdict: | Malicious activity |
| Analysis date: | October 18, 2018, 20:53:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 118DA020F80B3E71C94150D39490C6B1 |
| SHA1: | E31E793779779EFA0A32E25A0A6275749E3ECC69 |
| SHA256: | EB4B3F628CA13BACACA041D83586BC471A8835CC7130F93AB72A208FF9AFF25A |
| SSDEEP: | 196608:mptmloewsPB519N4YL/n542i66nqUSxdvAHhyKmBgT0z56V:mqoewGBfnL/nDVUSxdq9mBdI |
MALICIOUS
Application was dropped or rewritten from another process
- CheckLockedWSFiles.exe (PID: 3656)
- WSTray.exe (PID: 2372)
- CheckLockedWSFiles.exe (PID: 1840)
- WSRegistration.exe (PID: 2208)
- WSRegistration.exe (PID: 2828)
- WSTray.exe (PID: 944)
Loads dropped or rewritten executable
- CheckLockedWSFiles.exe (PID: 3656)
- CheckLockedWSFiles.exe (PID: 1840)
- WhiteSmoke_Enrichment_Full.exe (PID: 3128)
- WSRegistration.exe (PID: 2208)
- WSTray.exe (PID: 2372)
- csrss.exe (PID: 400)
- csrss.exe (PID: 344)
- WSTray.exe (PID: 944)
- WSRegistration.exe (PID: 2828)
Writes to a start menu file
- WhiteSmoke_Enrichment_Full.exe (PID: 3128)
SUSPICIOUS
Executable content was dropped or overwritten
- WhiteSmoke_Enrichment_Full.exe (PID: 3128)
Creates a software uninstall entry
- WhiteSmoke_Enrichment_Full.exe (PID: 3128)
Creates COM task schedule object
- WhiteSmoke_Enrichment_Full.exe (PID: 3128)
Reads internet explorer settings
- WSRegistration.exe (PID: 2208)
- WSRegistration.exe (PID: 2828)
Creates files in the user directory
- WhiteSmoke_Enrichment_Full.exe (PID: 3128)
Starts Internet Explorer
- WhiteSmoke_Enrichment_Full.exe (PID: 3128)
Creates files in the program directory
- WhiteSmoke_Enrichment_Full.exe (PID: 3128)
INFO
Dropped object may contain Bitcoin addresses
- WhiteSmoke_Enrichment_Full.exe (PID: 3128)
Changes internet zones settings
- iexplore.exe (PID: 3992)
Reads internet explorer settings
- iexplore.exe (PID: 1732)
Creates files in the user directory
- iexplore.exe (PID: 1732)
Reads Internet Cache Settings
- iexplore.exe (PID: 1732)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (91.9) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.3) |
| .exe | | | Win64 Executable (generic) (3) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:02:24 20:21:56+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 27648 |
| InitializedDataSize: | 272896 |
| UninitializedDataSize: | 8704 |
| EntryPoint: | 0x3814 |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.6034.13130 |
| ProductVersionNumber: | 1.0.6034.13130 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | ASCII |
| FileDescription: | - |
| FileVersion: | 1.00.6034.13130 |
| LegalCopyright: | - |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 24-Feb-2012 19:21:56 |
| Detected languages: |
|
| FileDescription: | - |
| FileVersion: | 1.00.6034.13130 |
| LegalCopyright: | - |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000E0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 24-Feb-2012 19:21:56 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00006B32 | 0x00006C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.47711 |
.rdata | 0x00008000 | 0x00001EFE | 0x00002000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.35432 |
.data | 0x0000A000 | 0x0003E95C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.44337 |
.ndata | 0x00049000 | 0x0005D000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x000A6000 | 0x00003210 | 0x00003400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.38484 |
.reloc | 0x000AA000 | 0x00000D92 | 0x00000E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 5.76775 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.22656 | 965 | UNKNOWN | English - United States | RT_MANIFEST |
103 | 1.91924 | 20 | UNKNOWN | English - United States | RT_GROUP_ICON |
105 | 2.73893 | 514 | UNKNOWN | English - United States | RT_DIALOG |
106 | 2.91148 | 248 | UNKNOWN | English - United States | RT_DIALOG |
111 | 2.92787 | 238 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
VERSION.dll |
ole32.dll |
Total processes
45
Monitored processes
12
Malicious processes
5
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 344 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,12288,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\System32\csrss.exe | — | — | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 400 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,12288,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\System32\csrss.exe | — | — | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 944 | "C:\Program Files\WhiteSmoke\WSTray.exe" | C:\Program Files\WhiteSmoke\WSTray.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1732 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3992 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1840 | "C:\Users\admin\AppData\Local\Temp\WhiteSmoke\CheckLockedWSFiles.exe" targetdir="C:\Program Files\WhiteSmoke" silent | C:\Users\admin\AppData\Local\Temp\WhiteSmoke\CheckLockedWSFiles.exe | — | WhiteSmoke_Enrichment_Full.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1872 | "C:\Users\admin\AppData\Local\Temp\WhiteSmoke_Enrichment_Full.exe" | C:\Users\admin\AppData\Local\Temp\WhiteSmoke_Enrichment_Full.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.00.6034.13130 Modules
| |||||||||||||||
| 2208 | "C:\Program Files\WhiteSmoke\WSRegistration.exe" | C:\Program Files\WhiteSmoke\WSRegistration.exe | — | WSTray.exe | |||||||||||
User: admin Company: WhiteSmoke Integrity Level: HIGH Description: WhiteSmoke Registration App Exit code: 0 Version: 1.0.6034.0 Modules
| |||||||||||||||
| 2372 | "C:\Program Files\WhiteSmoke\WSTray.exe" | C:\Program Files\WhiteSmoke\WSTray.exe | — | WhiteSmoke_Enrichment_Full.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2828 | "C:\Program Files\WhiteSmoke\WSRegistration.exe" | C:\Program Files\WhiteSmoke\WSRegistration.exe | — | WSTray.exe | |||||||||||
User: admin Company: WhiteSmoke Integrity Level: MEDIUM Description: WhiteSmoke Registration App Exit code: 0 Version: 1.0.6034.0 Modules
| |||||||||||||||
| 3128 | "C:\Users\admin\AppData\Local\Temp\WhiteSmoke_Enrichment_Full.exe" | C:\Users\admin\AppData\Local\Temp\WhiteSmoke_Enrichment_Full.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00.6034.13130 Modules
| |||||||||||||||
Total events
1 050
Read events
775
Write events
273
Delete events
2
Modification events
| (PID) Process: | (3128) WhiteSmoke_Enrichment_Full.exe | Key: | HKEY_CURRENT_USER\Software\WhiteSmoke |
| Operation: | write | Name: | Promotion |
Value: 1 | |||
| (PID) Process: | (3128) WhiteSmoke_Enrichment_Full.exe | Key: | HKEY_CURRENT_USER\Software\WhiteSmoke |
| Operation: | write | Name: | ShowRegistration |
Value: 1 | |||
| (PID) Process: | (3128) WhiteSmoke_Enrichment_Full.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\AppID\{5C731C2A-6ADF-487E-99A2-7291BF794A14} |
| Operation: | write | Name: | |
Value: osmax | |||
| (PID) Process: | (3128) WhiteSmoke_Enrichment_Full.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\AppID\osmax.ocx |
| Operation: | write | Name: | AppID |
Value: {5C731C2A-6ADF-487E-99A2-7291BF794A14} | |||
| (PID) Process: | (3128) WhiteSmoke_Enrichment_Full.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\AddInExpress.OutlookSecurityManager.1 |
| Operation: | write | Name: | |
Value: OutlookSecMan Control | |||
| (PID) Process: | (3128) WhiteSmoke_Enrichment_Full.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\AddInExpress.OutlookSecurityManager.1\CLSID |
| Operation: | write | Name: | |
Value: {20E1481B-E285-4ABC-ADC7-AE24842B81CD} | |||
| (PID) Process: | (3128) WhiteSmoke_Enrichment_Full.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\AddInExpress.OutlookSecurityManager |
| Operation: | write | Name: | |
Value: OutlookSecMan Control | |||
| (PID) Process: | (3128) WhiteSmoke_Enrichment_Full.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\AddInExpress.OutlookSecurityManager\CLSID |
| Operation: | write | Name: | |
Value: {20E1481B-E285-4ABC-ADC7-AE24842B81CD} | |||
| (PID) Process: | (3128) WhiteSmoke_Enrichment_Full.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\AddInExpress.OutlookSecurityManager\CurVer |
| Operation: | write | Name: | |
Value: AddInExpress.OutlookSecurityManager.1 | |||
| (PID) Process: | (3128) WhiteSmoke_Enrichment_Full.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{20E1481B-E285-4ABC-ADC7-AE24842B81CD} |
| Operation: | write | Name: | |
Value: Add-in Express Outlook Security Manager | |||
Executable files
42
Suspicious files
5
Text files
874
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3128 | WhiteSmoke_Enrichment_Full.exe | C:\Users\admin\AppData\Local\Temp\WhiteSmoke\CheckLockedWsFiles.exe | executable | |
MD5:— | SHA256:— | |||
| 3128 | WhiteSmoke_Enrichment_Full.exe | C:\Users\admin\AppData\Local\Temp\WhiteSmoke\Microsoft.VC80.CRT.manifest | xml | |
MD5:188E68005ED62F32248032C65CB4DE96 | SHA256:AA8E944ADFEED4B29CC9262C63F43ED752F8EF44D52FD868E41BDF1EA974D1B0 | |||
| 3128 | WhiteSmoke_Enrichment_Full.exe | C:\Users\admin\AppData\Local\Temp\nse3B94.tmp\ioSpecial.ini | text | |
MD5:— | SHA256:— | |||
| 3128 | WhiteSmoke_Enrichment_Full.exe | C:\Program Files\WhiteSmoke\ComVistaElevator.dll | executable | |
MD5:— | SHA256:— | |||
| 3128 | WhiteSmoke_Enrichment_Full.exe | C:\Program Files\WhiteSmoke\WSMouseHook.dll | executable | |
MD5:— | SHA256:— | |||
| 3128 | WhiteSmoke_Enrichment_Full.exe | C:\Users\admin\AppData\Local\Temp\nse3B94.tmp\Whitesmoke_EULA.txt | text | |
MD5:— | SHA256:— | |||
| 3128 | WhiteSmoke_Enrichment_Full.exe | C:\Program Files\WhiteSmoke\WSEngine.dll | executable | |
MD5:— | SHA256:— | |||
| 3128 | WhiteSmoke_Enrichment_Full.exe | C:\Program Files\WhiteSmoke\WSTray.exe | executable | |
MD5:— | SHA256:— | |||
| 3128 | WhiteSmoke_Enrichment_Full.exe | C:\Program Files\WhiteSmoke\WSKeyboardHook.dll | executable | |
MD5:— | SHA256:— | |||
| 3128 | WhiteSmoke_Enrichment_Full.exe | C:\Users\admin\AppData\Local\Temp\nse3B94.tmp\System.dll | executable | |
MD5:A78507EA1078CADAA8B2EC1A2E1D874F | SHA256:93D1E681DAEBFD24FF9FAB3952E8AE94EDDBDFB3650937988C1FD8085991610E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
7
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1732 | iexplore.exe | GET | 301 | 54.149.187.185:80 | http://www.whitesmoke.com/promotions/popups/popup_writer_funnel_external.php?user_id=&dist_id=0&installOption=0&offer=0& | US | — | — | malicious |
1732 | iexplore.exe | GET | 301 | 54.149.187.185:80 | http://www.whitesmoke.com/promotions/popups/directpostinstallation.php?user_id=&dist_id=0&installOption=0&offer=0 | US | — | — | malicious |
3992 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
1732 | iexplore.exe | GET | 200 | 172.217.23.170:80 | http://fonts.googleapis.com/css?family=Open+Sans | US | text | 167 b | whitelisted |
1732 | iexplore.exe | GET | 200 | 54.149.187.185:80 | http://www.whitesmoke.com/postInstallation/?user_id=&dist_id=0&installOption=0&offer=0& | US | html | 15.1 Kb | malicious |
1732 | iexplore.exe | GET | 200 | 54.149.187.185:80 | http://www.whitesmoke.com/website2016/css/bxslider/jquery.bxslider.css | US | text | 3.75 Kb | malicious |
1732 | iexplore.exe | GET | 200 | 172.217.23.170:80 | http://fonts.googleapis.com/css?family=Scada:400,700,400italic | US | text | 156 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1732 | iexplore.exe | 54.149.187.185:80 | www.whitesmoke.com | Amazon.com, Inc. | US | unknown |
3992 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1732 | iexplore.exe | 172.217.23.170:80 | fonts.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.whitesmoke.com |
| malicious |
www.bing.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |