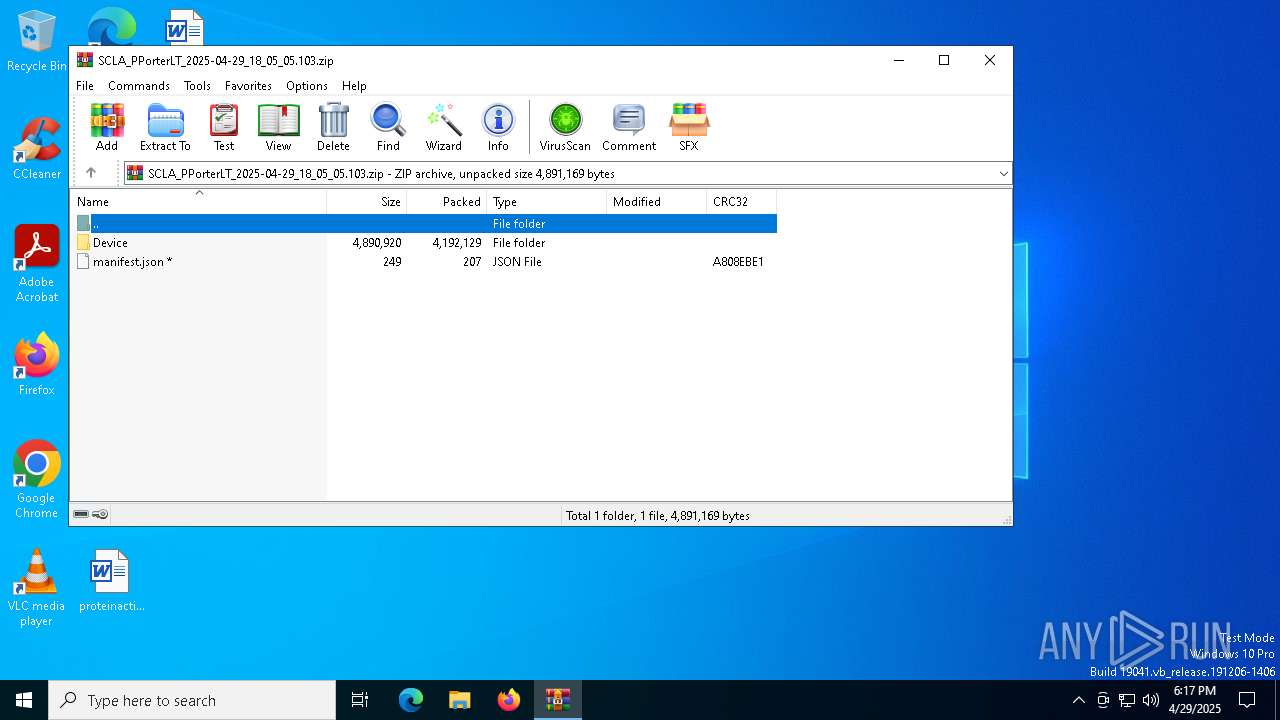
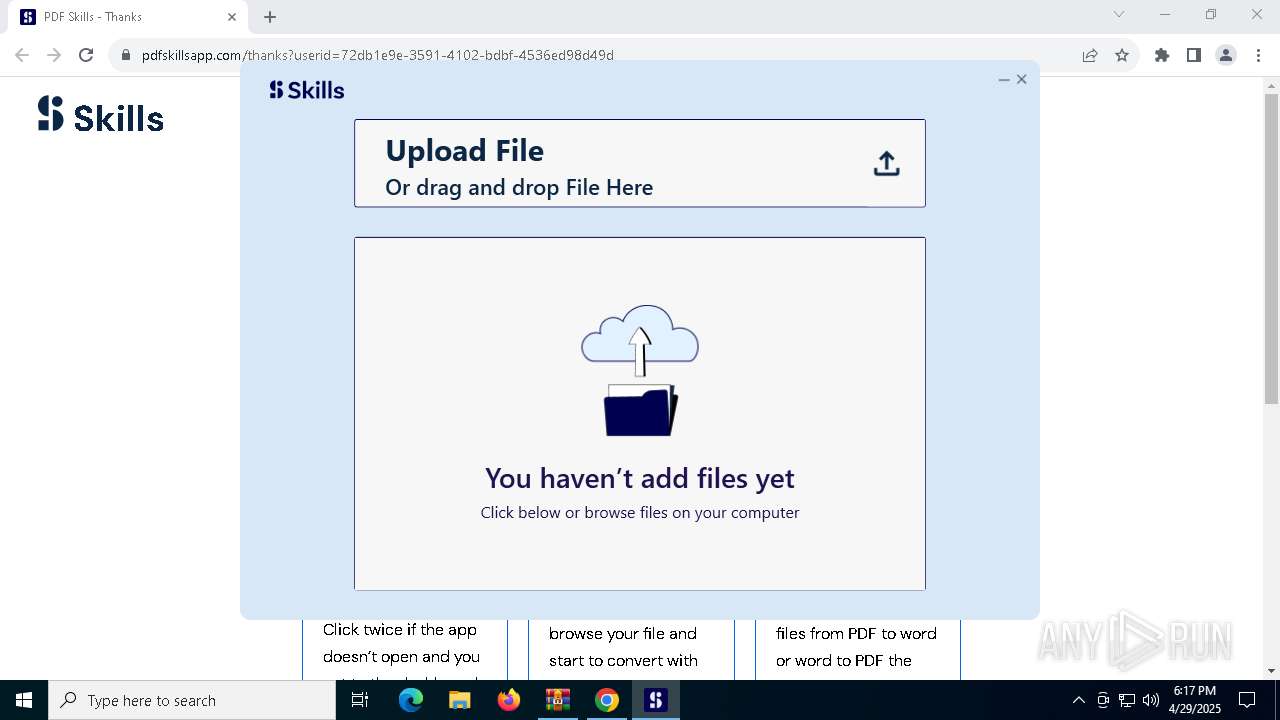
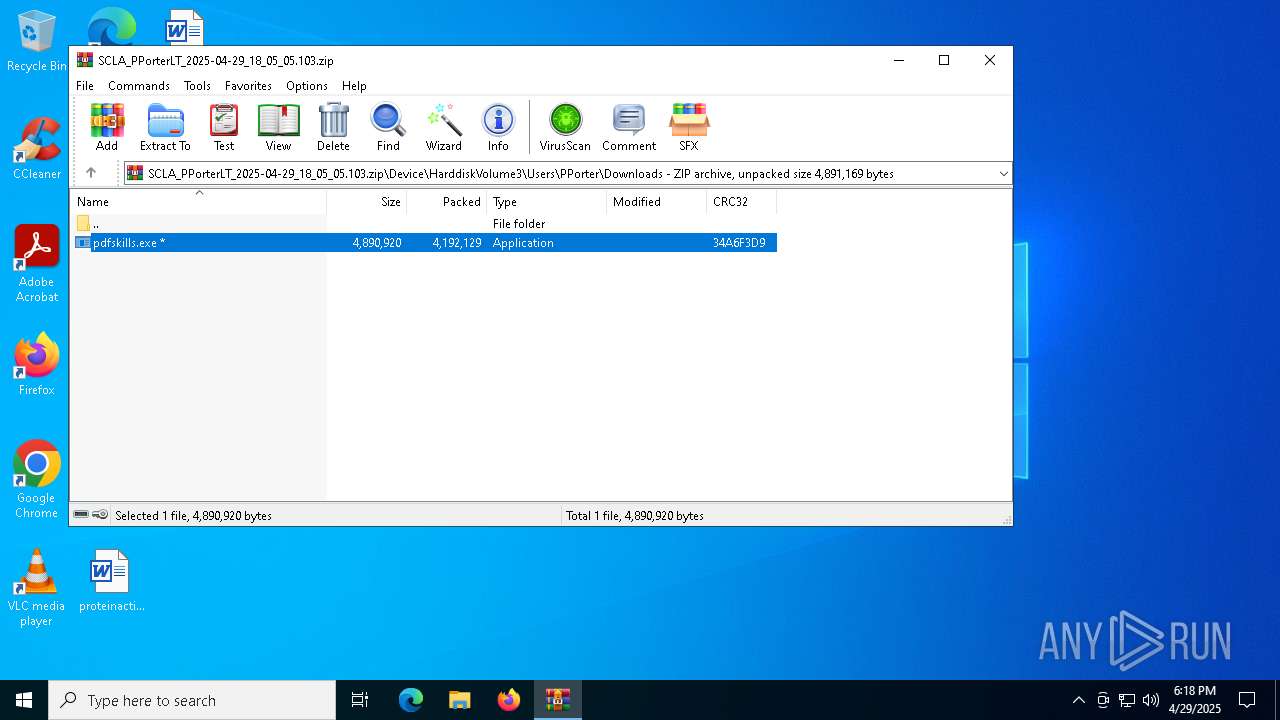
| File name: | SCLA_PPorterLT_2025-04-29_18_05_05.103.zip |
| Full analysis: | https://app.any.run/tasks/b3276667-12d5-4cfd-a2bb-9cd215a885b1 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 18:16:55 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract, compression method=deflate |
| MD5: | F89DF09BCCCEC7E16DA3BB36E469B816 |
| SHA1: | 6C2E9F36B77968F3077546C18B5D7B29422C5EE5 |
| SHA256: | EB300AEE94B17D2D4879C56FB3F1DFA39A67DFD823E0A6353D64E5DBE4BBFC4E |
| SSDEEP: | 98304:k3B1VBUK7yWbiyUXpDsope3AoSu5RtXZI0191n3ya05cfe/cjTzCt3MWbUMCi0dS:KHC9C1ElU1epr |
MALICIOUS
GENERIC has been found (auto)
- WinRAR.exe (PID: 7580)
Changes powershell execution policy (RemoteSigned)
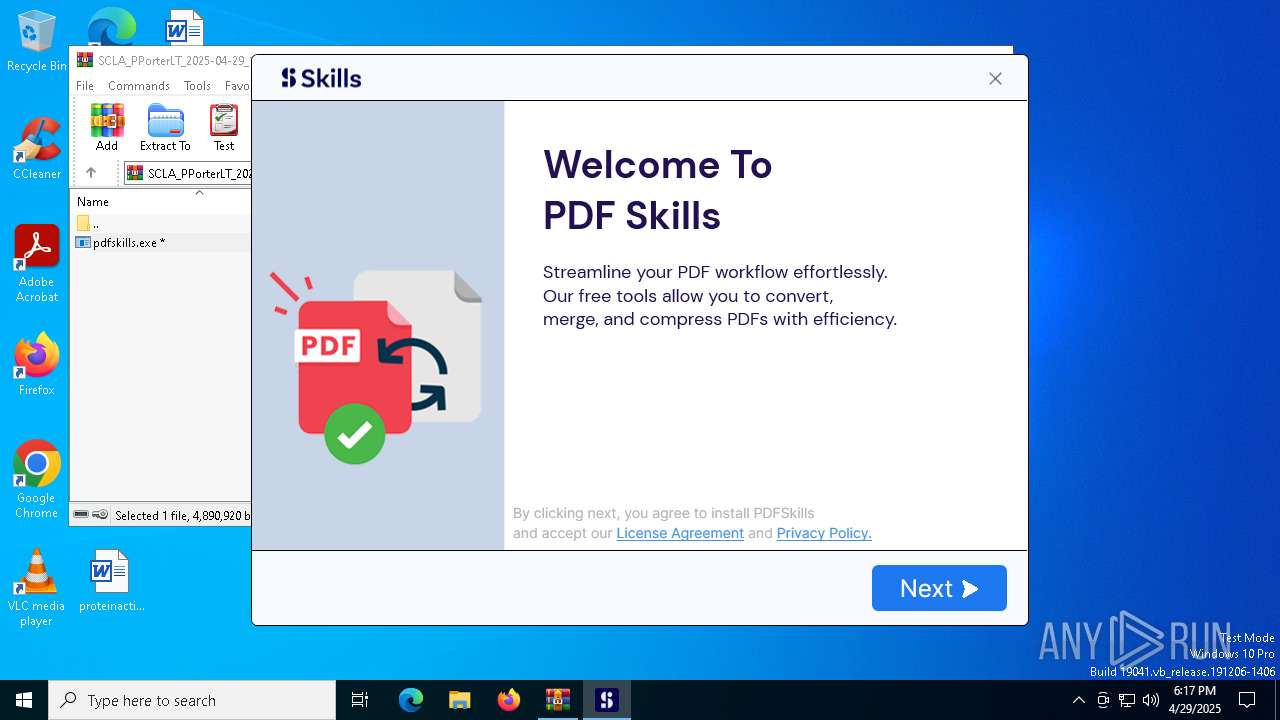
- pdfskills.exe (PID: 8112)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7580)
- pdfskills.exe (PID: 8112)
- PDFSkillsApp.exe (PID: 5048)
- PDFSkillsApp.exe (PID: 8088)
Starts POWERSHELL.EXE for commands execution
- pdfskills.exe (PID: 8112)
Creates a software uninstall entry
- pdfskills.exe (PID: 8112)
Reads the date of Windows installation
- pdfskills.exe (PID: 8112)
The process executes Powershell scripts
- pdfskills.exe (PID: 8112)
Gets path to any of the special folders (POWERSHELL)
- powershell.exe (PID: 2140)
Executable content was dropped or overwritten
- pdfskills.exe (PID: 8112)
Process drops legitimate windows executable
- pdfskills.exe (PID: 8112)
The process drops C-runtime libraries
- pdfskills.exe (PID: 8112)
Searches for installed software
- pdfskills.exe (PID: 8112)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7580)
Reads the computer name
- pdfskills.exe (PID: 8112)
- PDFSkillsApp.exe (PID: 5048)
- PDFSkillsApp.exe (PID: 8088)
Checks supported languages
- pdfskills.exe (PID: 8112)
- PDFSkillsApp.exe (PID: 5048)
- PDFSkillsApp.exe (PID: 8088)
Reads the machine GUID from the registry
- pdfskills.exe (PID: 8112)
- PDFSkillsApp.exe (PID: 5048)
- PDFSkillsApp.exe (PID: 8088)
Disables trace logs
- pdfskills.exe (PID: 8112)
Creates files or folders in the user directory
- pdfskills.exe (PID: 8112)
Checks proxy server information
- pdfskills.exe (PID: 8112)
Reads Environment values
- pdfskills.exe (PID: 8112)
Reads the software policy settings
- pdfskills.exe (PID: 8112)
- slui.exe (PID: 7804)
Process checks computer location settings
- pdfskills.exe (PID: 8112)
Application launched itself
- chrome.exe (PID: 2088)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 2140)
The sample compiled with english language support
- pdfskills.exe (PID: 8112)
Manual execution by a user
- PDFSkillsApp.exe (PID: 8088)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0801 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x34a6f3d9 |
| ZipCompressedSize: | 4192129 |
| ZipUncompressedSize: | 4890920 |
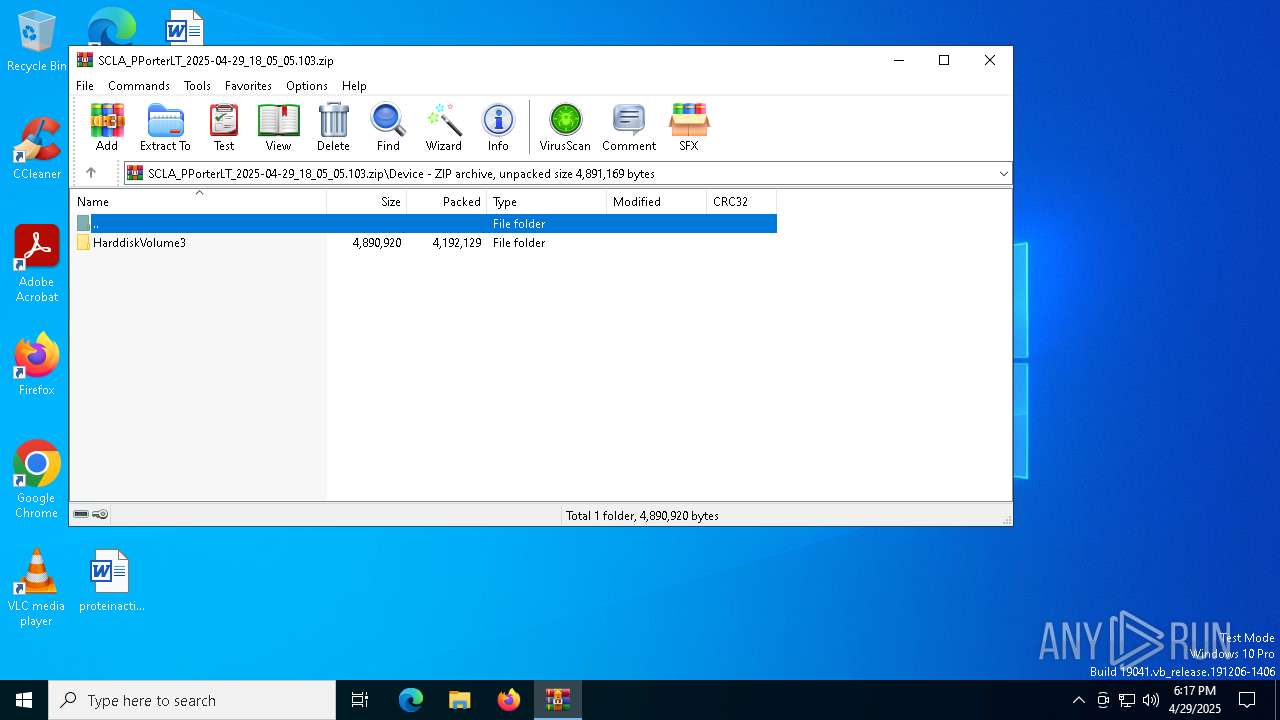
| ZipFileName: | Device/HarddiskVolume3/Users/PPorter/Downloads/pdfskills.exe |
Total processes
172
Monitored processes
33
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1012 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5088 --field-trial-handle=1948,i,11427939027252705621,2183154238266631758,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1168 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4880 --field-trial-handle=1948,i,11427939027252705621,2183154238266631758,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1616 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --extension-process --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=3748 --field-trial-handle=1948,i,11427939027252705621,2183154238266631758,262144 --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
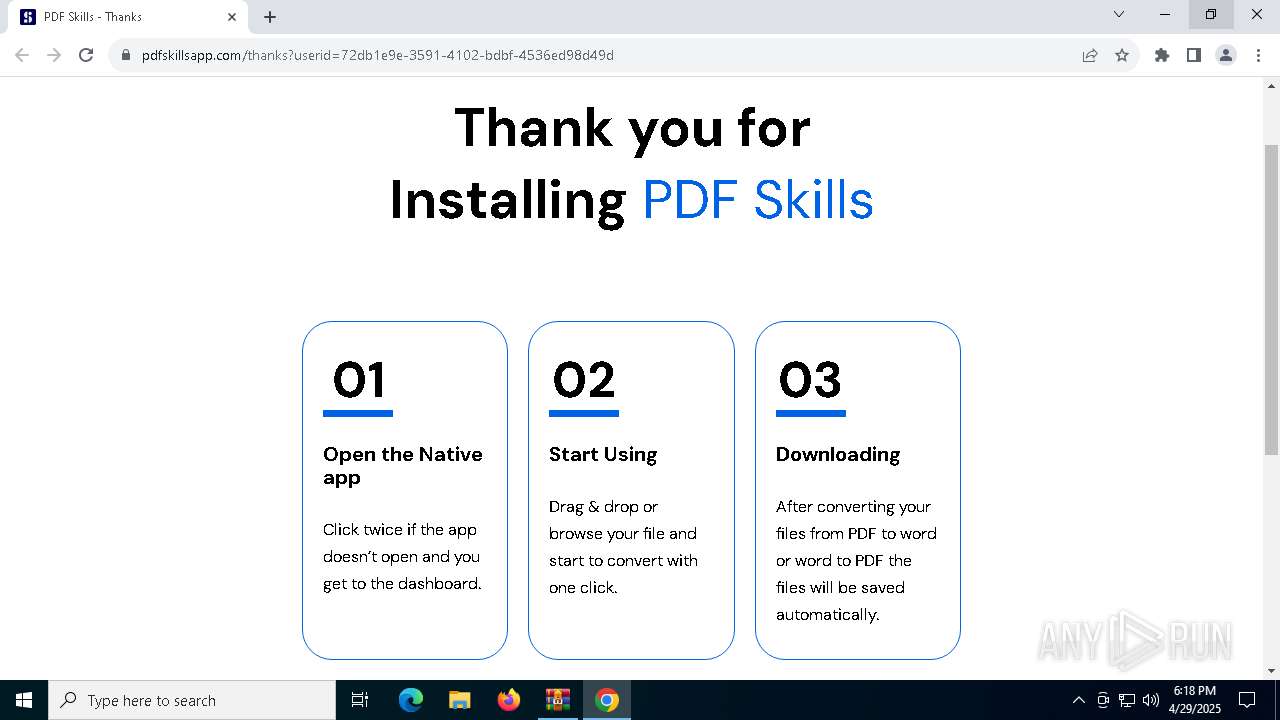
| 2088 | "C:\Program Files\Google\Chrome\Application\chrome.exe" https://www.pdfskillsapp.com/thanks?userid=72db1e9e-3591-4102-bdbf-4536ed98d49d | C:\Program Files\Google\Chrome\Application\chrome.exe | pdfskills.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2136 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2140 | "powershell.exe" -ep RemoteSigned -File "C:\Users\admin\AppData\Local\PDFSkills\update_task_ad.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | pdfskills.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2284 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5916 --field-trial-handle=1948,i,11427939027252705621,2183154238266631758,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2616 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4848 --field-trial-handle=1948,i,11427939027252705621,2183154238266631758,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2656 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5712 --field-trial-handle=1948,i,11427939027252705621,2183154238266631758,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 4996 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x21c,0x220,0x224,0x1f8,0x228,0x7ffc843bdc40,0x7ffc843bdc4c,0x7ffc843bdc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
28 679
Read events
28 542
Write events
131
Delete events
6
Modification events
| (PID) Process: | (7580) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7580) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7580) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7580) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SCLA_PPorterLT_2025-04-29_18_05_05.103.zip | |||
| (PID) Process: | (7580) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7580) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7580) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7580) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7580) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (8112) pdfskills.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\pdfskills_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
25
Suspicious files
127
Text files
41
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 8112 | pdfskills.exe | C:\Users\admin\AppData\Local\PDFSkills\update_task_ad.ps1 | text | |
MD5:303E2E6AD62BDBC4AB32F6041FEA897A | SHA256:5FDF76A78556E479E41422D577F6FC7B672CBC9C131721B725FEA765E288EED9 | |||
| 8112 | pdfskills.exe | C:\Users\admin\AppData\Local\PDFSkills\msvcp140.dll | executable | |
MD5:C3D497B0AFEF4BD7E09C7559E1C75B05 | SHA256:1E57A6DF9E3742E31A1C6D9BFF81EBEEAE8A7DE3B45A26E5079D5E1CCE54CD98 | |||
| 7580 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7580.44323\manifest.json | text | |
MD5:C92B20B045B6091E0C0ECBBF3D51E300 | SHA256:E28E44C0C3E453CAEB1FC53569AD52027ADE38921DD8686F08FF318DC9A497BF | |||
| 8112 | pdfskills.exe | C:\Users\admin\AppData\Local\PDFSkills\skillsUserId.txt | text | |
MD5:509E3B8DFB4FCAB23950F196AB80BB08 | SHA256:71B0368717AC678E97F403C99DDEC9425C7090C5CC0A099C6E7603D61EE07FA0 | |||
| 8112 | pdfskills.exe | C:\Users\admin\AppData\Local\PDFSkills\Update_files.zip | compressed | |
MD5:6F3E6D28273C0E8BF8E0A80DE5B0A5BE | SHA256:1E537133A195CF64EE9979800DBFB2D74E0BBAA9367FEABEB4AC7C7F9610B938 | |||
| 8112 | pdfskills.exe | C:\Users\admin\AppData\Local\PDFSkills\vcomp140.dll | executable | |
MD5:EF76327FF132A48F3BAC24598C99B373 | SHA256:D49B394DE1154176B39611C37C669EBFF50AA5A818DBD5FF3D2214A299368DDD | |||
| 8112 | pdfskills.exe | C:\Users\admin\AppData\Roaming\SMCR\userId.txt | text | |
MD5:509E3B8DFB4FCAB23950F196AB80BB08 | SHA256:71B0368717AC678E97F403C99DDEC9425C7090C5CC0A099C6E7603D61EE07FA0 | |||
| 2140 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_dacyidpw.uvp.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 8112 | pdfskills.exe | C:\Users\admin\AppData\Local\PDFSkills\msvcp140_atomic_wait.dll | executable | |
MD5:6722344B74084D0AF629283060716BAE | SHA256:C9FD25862B1B8B2977BF188A4E0C4460DADE43C31710283C2B42DBD3B15B4317 | |||
| 8112 | pdfskills.exe | C:\Users\admin\AppData\Local\PDFSkills\Libraries.dll | executable | |
MD5:08B1B14B4573E95BDB5E6DDCA74D2513 | SHA256:EE803D254AF9E2FE4781E3335164D24BEC31512A229E607A3A93254D47177F52 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
55
DNS requests
65
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.30:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5728 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5728 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4024 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.30:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
val.skillcli.com |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7224 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7224 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |