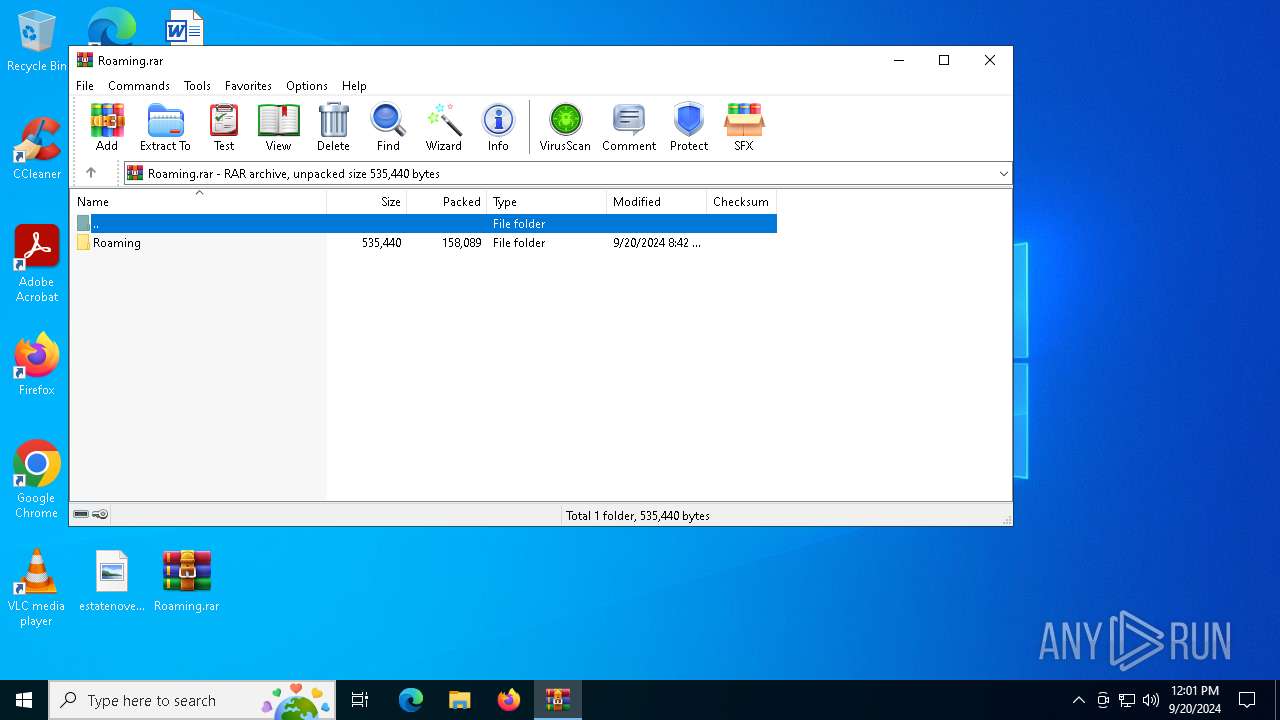
| File name: | Roaming.rar |
| Full analysis: | https://app.any.run/tasks/9d085c02-61d2-479e-9bc8-2e2e04dca31b |
| Verdict: | Malicious activity |
| Analysis date: | September 20, 2024, 12:01:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | B6EAE8A70FA02DA50D75B8C397F26730 |
| SHA1: | B6943B8EFC2FBF410E1ADE270074799027F1AE1D |
| SHA256: | EB2778B970B88C0A44FD439DFD4944CA95263D57268DB83F6E1F08279965A01C |
| SSDEEP: | 6144:IpDuFjeGwpHPQCEr3sLDknw8p+JvgSEwKuY:Ixu9eGwpICW3sLSw0+HEWY |
MALICIOUS
Connects to the CnC server
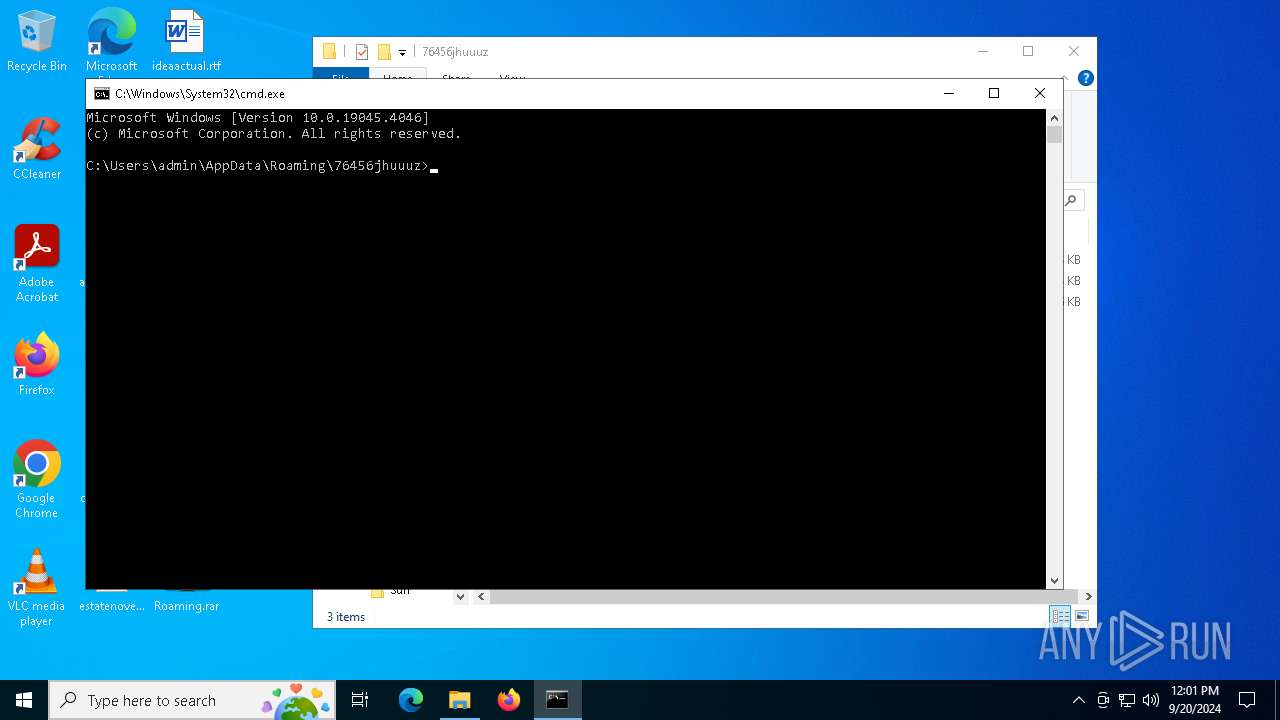
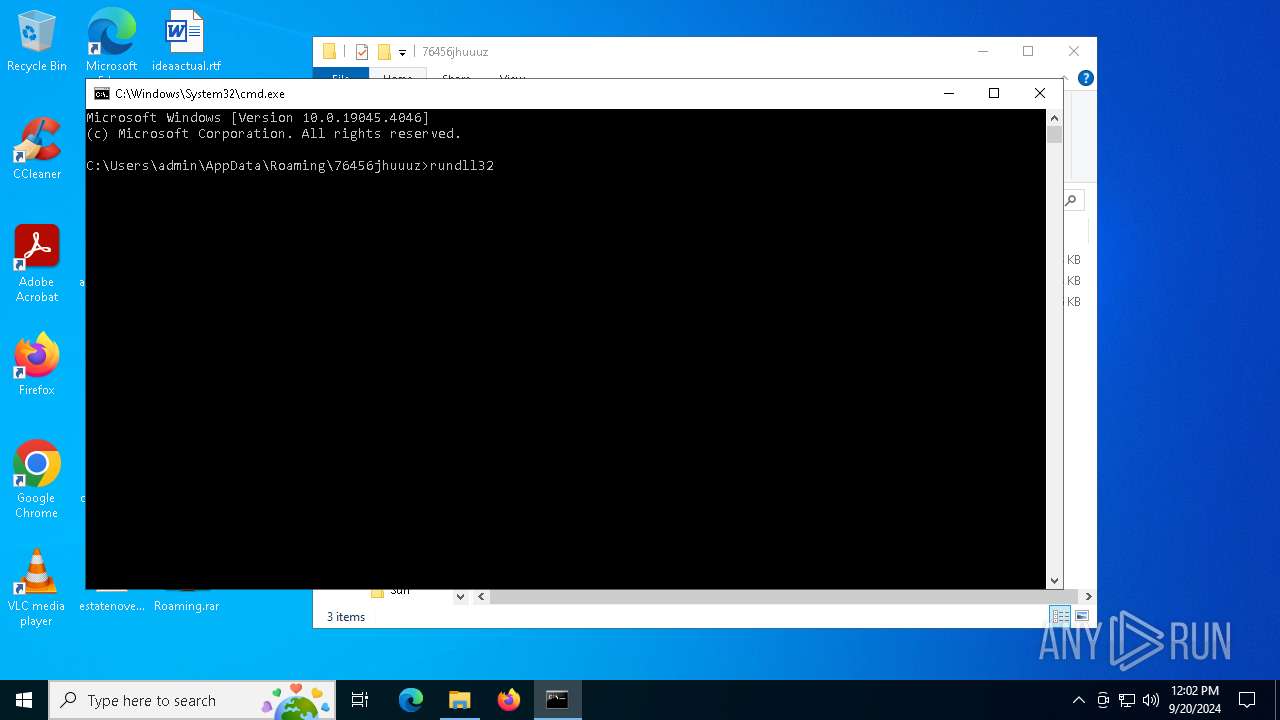
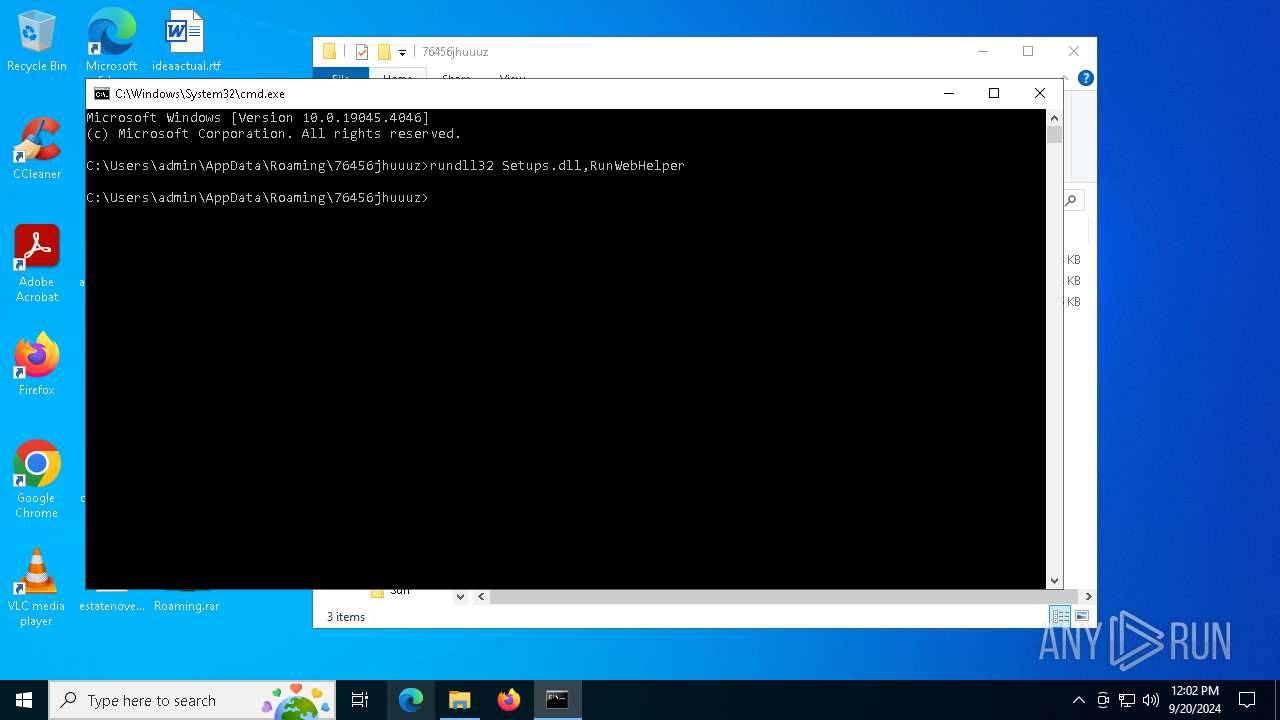
- rundll32.exe (PID: 6108)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 236)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 2608)
The process drops C-runtime libraries
- WinRAR.exe (PID: 236)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 236)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 236)
Manual execution by a user
- cmd.exe (PID: 2608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
133
Monitored processes
7
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Roaming.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2608 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4748 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5248 | rundll32 Setups.dll,RunWebHelper | C:\Windows\System32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6108 | rundll32 Setups.dll,RunWebHelper | C:\Windows\SysWOW64\rundll32.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6332 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 105
Read events
2 085
Write events
20
Delete events
0
Modification events
| (PID) Process: | (236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Roaming.rar | |||
| (PID) Process: | (236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
3
Suspicious files
6
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
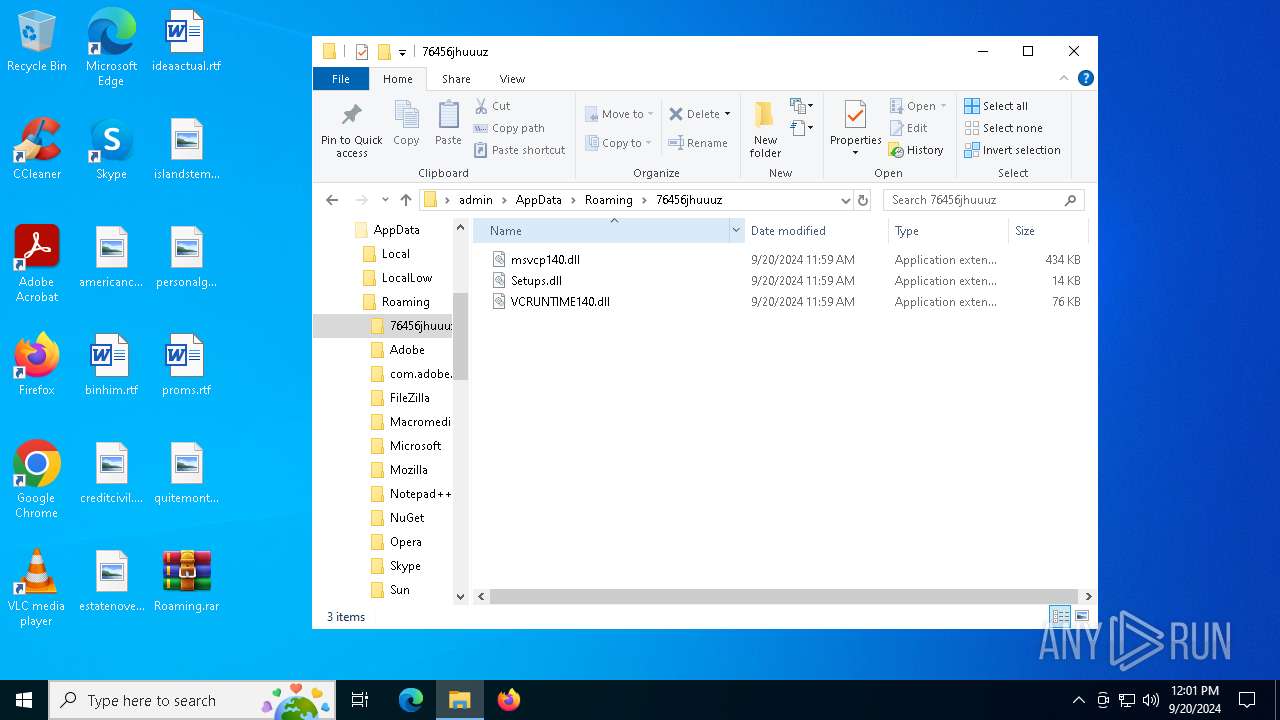
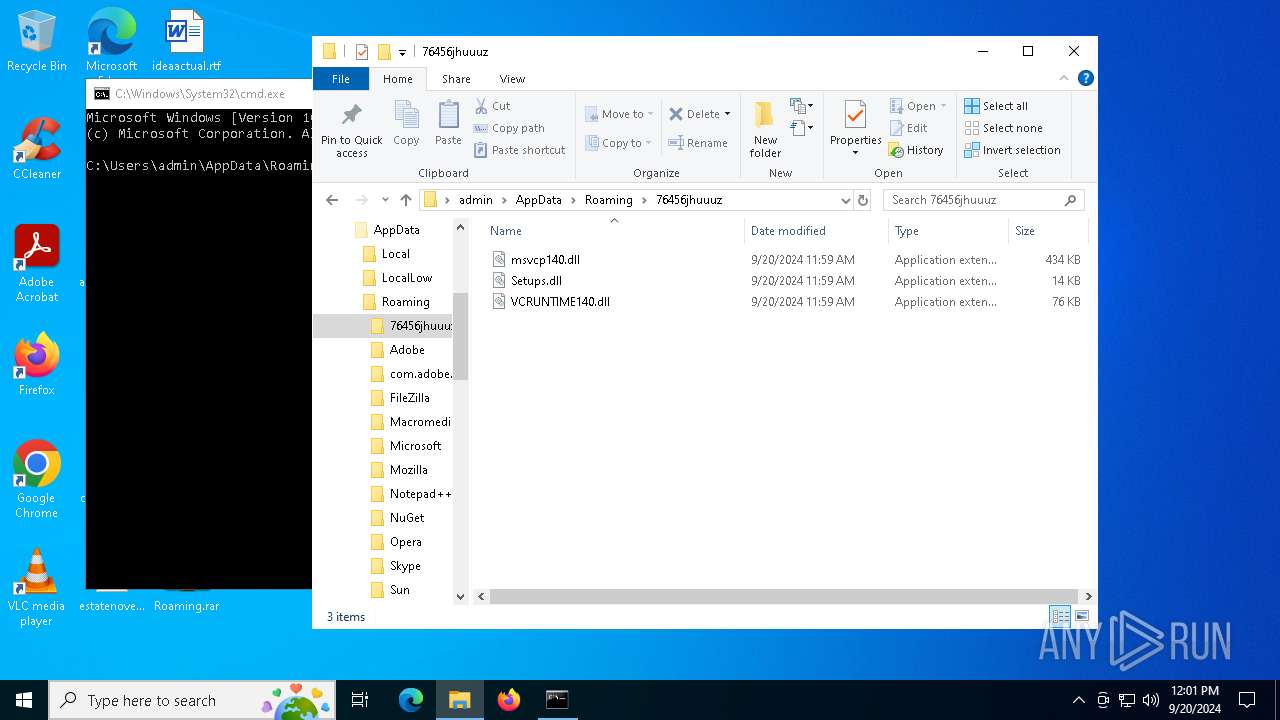
| 236 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa236.256\Roaming\76456jhuuuz\VCRUNTIME140.dll | executable | |
MD5:11528CDF5C8B9FE1651403D5BE5FDEF8 | SHA256:748EC5ED28BC88FCB64A6BA57FDB7F23C8C7DEE6369894F48EAD4959E5C1EA0D | |||
| 6108 | rundll32.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | der | |
MD5:971C514F84BBA0785F80AA1C23EDFD79 | SHA256:F157ED17FCAF8837FA82F8B69973848C9B10A02636848F995698212A08F31895 | |||
| 236 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa236.256\Roaming\76456jhuuuz\Setups.dll | executable | |
MD5:C913934ADE60997D4538FF745A3B22A6 | SHA256:270DBB3CC0211E6EE4C4F349CBD7BE42643C86939EAD34B72FC2328E843CEC3D | |||
| 236 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa236.256\Roaming\76456jhuuuz\msvcp140.dll | executable | |
MD5:F69BA164B2FFA05126CAF0617BD2AB60 | SHA256:9464E6031D1BA955717CC82FB65C25FE9DF02A2E3922CF0DB173271B71B5B808 | |||
| 6108 | rundll32.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:C9B6760436FA682C09BD448E512C3F70 | SHA256:D552FF4726A8FC5CDEE1C4CA545104AD342E2371EA8B92A0930C8D49DB4F3482 | |||
| 6108 | rundll32.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:7EE5BE3B9A51D9B548F9EB108E92AE1A | SHA256:4C3462DEE061F10C5D944EE4527C69C7D03CFB97B032986DBF16BE5AF80151C1 | |||
| 6108 | rundll32.exe | C:\Users\Public\dJbA3VwuqtIG5Tla.log | binary | |
MD5:970537A67A5F4AE3AED165659E06DFE3 | SHA256:C23587B9A3D209229E5519003F5A3B7E96002F121CAF623B901ECC2D2B062B14 | |||
| 6108 | rundll32.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:7FB5FA1534DCF77F2125B2403B30A0EE | SHA256:33A39E9EC2133230533A686EC43760026E014A3828C703707ACBC150FE40FD6F | |||
| 6108 | rundll32.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\k10[1].bin | binary | |
MD5:970537A67A5F4AE3AED165659E06DFE3 | SHA256:C23587B9A3D209229E5519003F5A3B7E96002F121CAF623B901ECC2D2B062B14 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
28
DNS requests
17
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6660 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6120 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6120 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6108 | rundll32.exe | GET | 200 | 172.217.18.3:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
6108 | rundll32.exe | GET | 200 | 172.217.18.3:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6932 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6804 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4324 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6660 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6660 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
www.xyo27b6j.icu |
| unknown |
c.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .icu Domain |
6108 | rundll32.exe | Potentially Bad Traffic | ET INFO Suspicious Domain (*.icu) in TLS SNI |
6108 | rundll32.exe | A Network Trojan was detected | ET MALWARE Win32/Unknown RAT CnC Server Acknowledgement |
6108 | rundll32.exe | A Network Trojan was detected | ET MALWARE Win32/Unknown RAT CnC Server Acknowledgement |