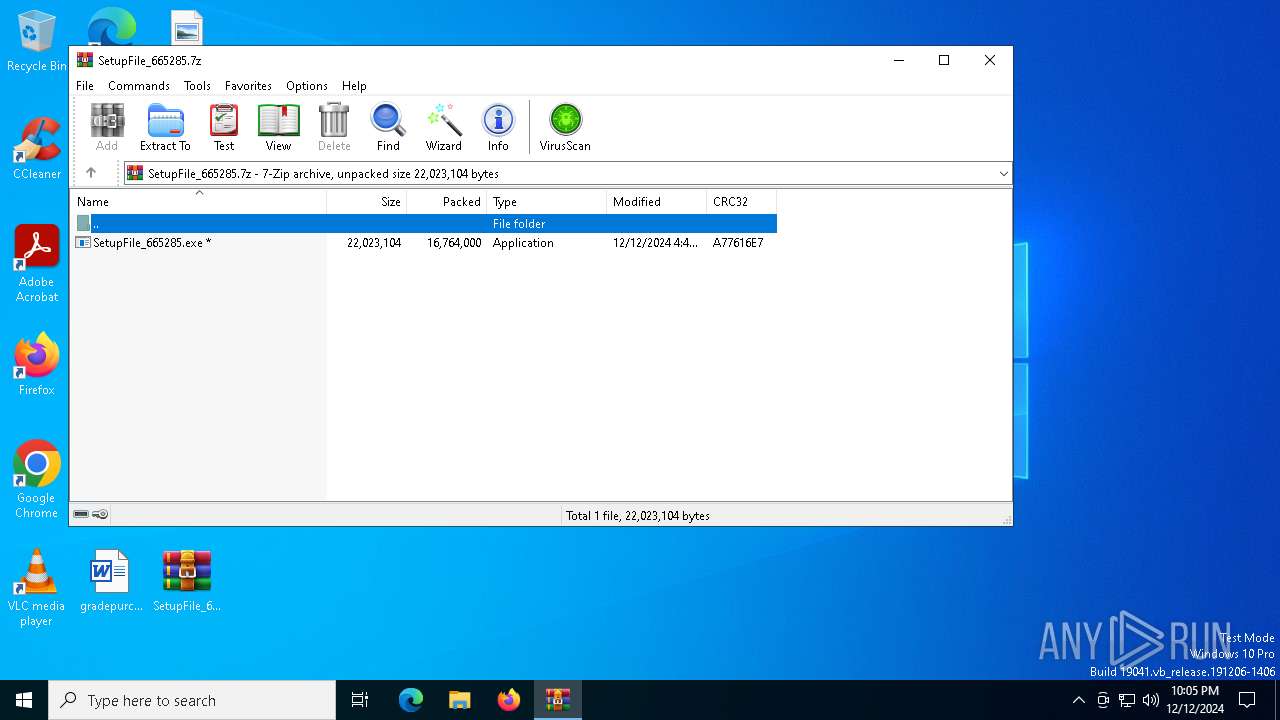
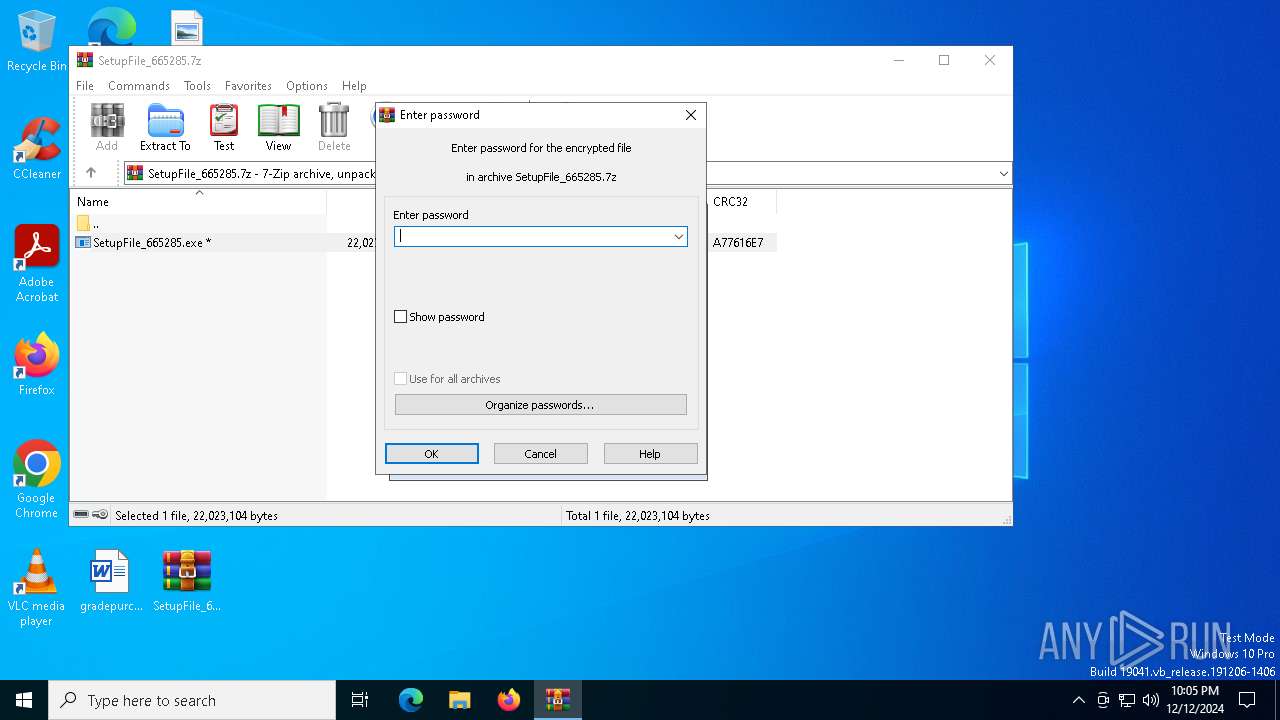
| File name: | SetupFile_665285.7z |
| Full analysis: | https://app.any.run/tasks/43364f14-3146-4a5c-b57b-18866b3acb62 |
| Verdict: | Malicious activity |
| Analysis date: | December 12, 2024, 22:05:37 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 097A0038BB3ECDB6A43CCDAEF3C88123 |
| SHA1: | D7E1A3F66D321AAFAF0292C9ADD74D37CA11A083 |
| SHA256: | EAE6DCF39F681DD2800D4C14CCEB6C5E6B55769A6C7711FC3C7B5BA4CBBCB2F9 |
| SSDEEP: | 196608:aP+bvtqdwFLxNI/v5+guO+5itl6Uroy2vMGHh4ROAp:mw1GwFLxMvJVRrovXKkAp |
MALICIOUS
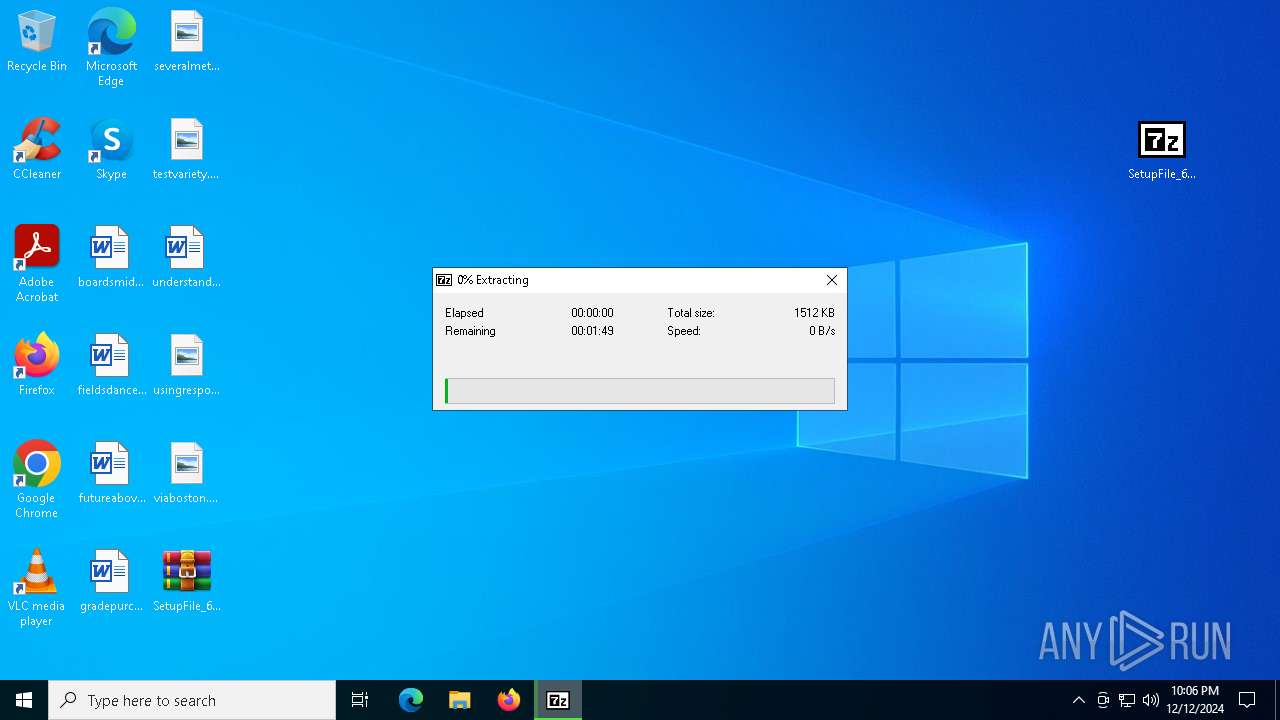
Generic archive extractor
- WinRAR.exe (PID: 6292)
SUSPICIOUS
Searches for installed software
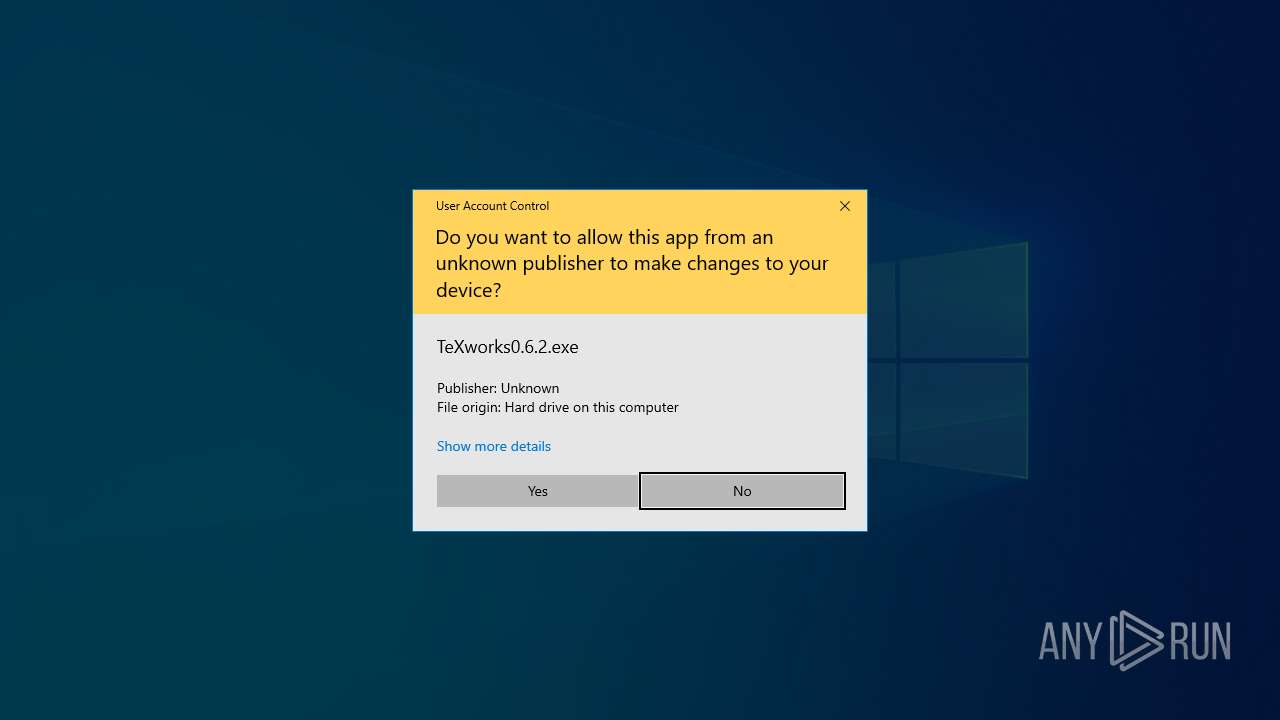
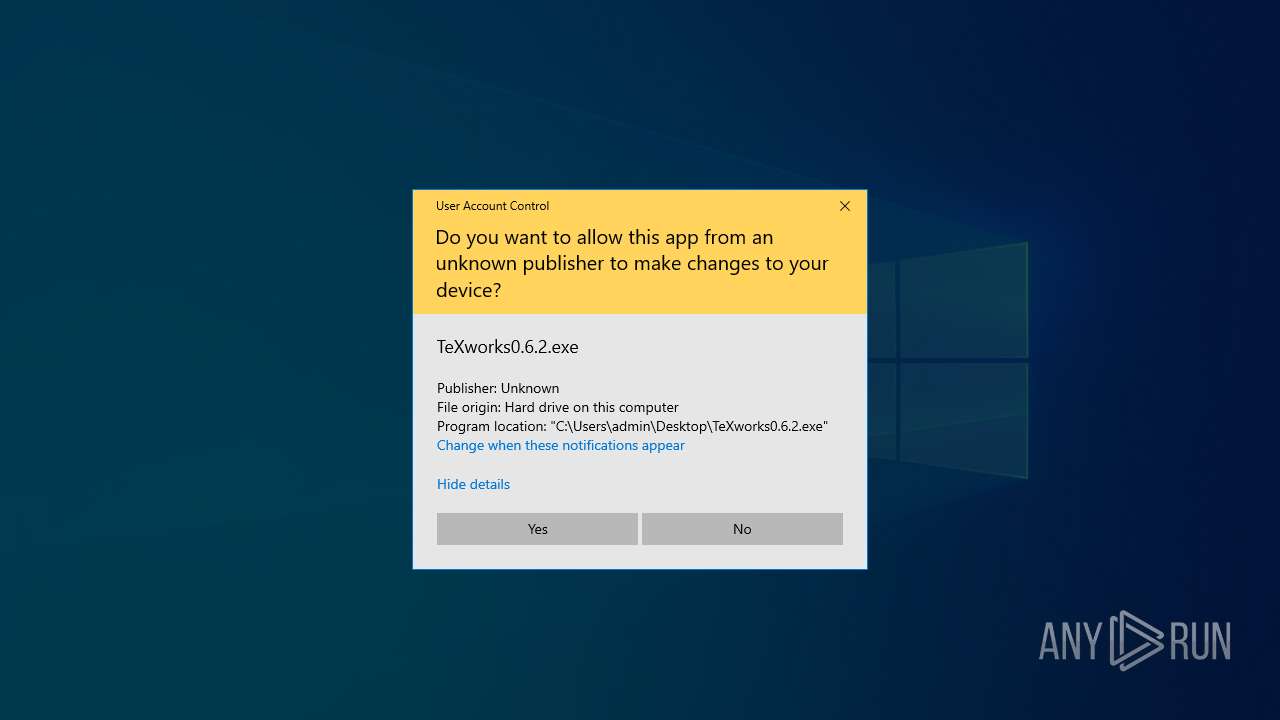
- SetupFile_665285.exe (PID: 7100)
Executable content was dropped or overwritten
- SetupFile_665285.exe (PID: 7100)
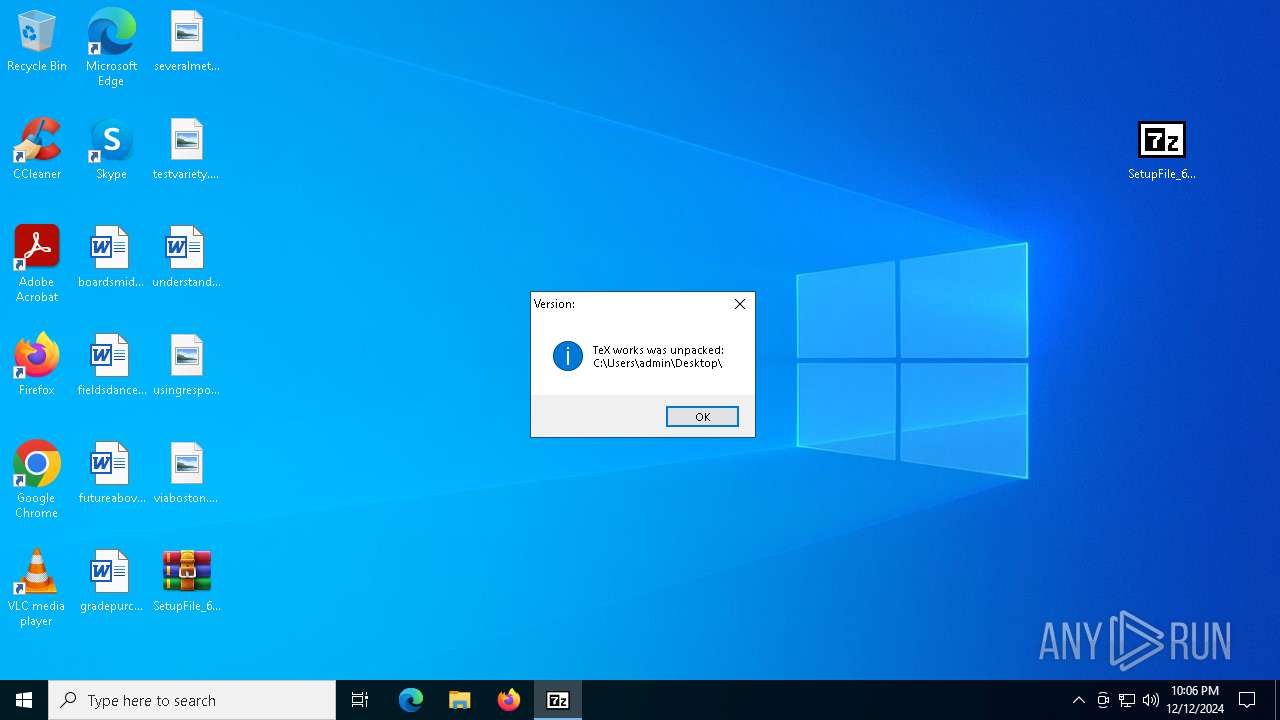
- TeXworks0.6.2.exe (PID: 2216)
- TeXworks0.6.2.tmp (PID: 3080)
Reads the Windows owner or organization settings
- TeXworks0.6.2.tmp (PID: 3080)
INFO
Checks supported languages
- SetupFile_665285.exe (PID: 7100)
- TeXworks0.6.2.exe (PID: 2216)
- TeXworks0.6.2.tmp (PID: 3080)
- TeXworks.exe (PID: 6552)
The process uses the downloaded file
- WinRAR.exe (PID: 6292)
Manual execution by a user
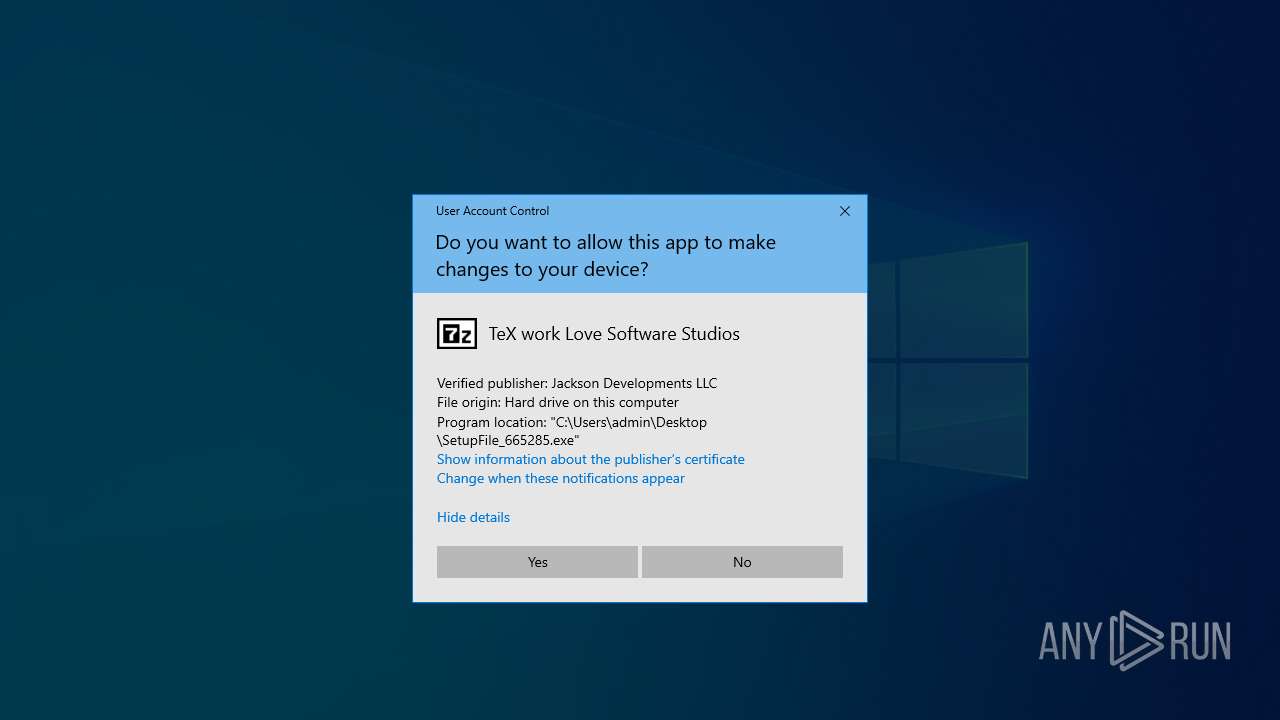
- SetupFile_665285.exe (PID: 7100)
- TeXworks0.6.2.exe (PID: 2216)
The sample compiled with english language support
- WinRAR.exe (PID: 6292)
- TeXworks0.6.2.tmp (PID: 3080)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6292)
Reads the computer name
- SetupFile_665285.exe (PID: 7100)
- TeXworks0.6.2.tmp (PID: 3080)
- TeXworks.exe (PID: 6552)
Create files in a temporary directory
- TeXworks0.6.2.exe (PID: 2216)
- TeXworks0.6.2.tmp (PID: 3080)
Creates files in the program directory
- TeXworks0.6.2.tmp (PID: 3080)
Creates a software uninstall entry
- TeXworks0.6.2.tmp (PID: 3080)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2024:12:12 16:46:23+00:00 |
| ArchivedFileName: | SetupFile_665285.exe |
Total processes
132
Monitored processes
5
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2216 | "C:\Users\admin\Desktop\TeXworks0.6.2.exe" | C:\Users\admin\Desktop\TeXworks0.6.2.exe | explorer.exe | ||||||||||||
User: admin Company: TeX Users Group Integrity Level: HIGH Description: TeXworks Setup Exit code: 0 Version: 0.6.2.0 Modules
| |||||||||||||||
| 3080 | "C:\Users\admin\AppData\Local\Temp\is-SO4S6.tmp\TeXworks0.6.2.tmp" /SL5="$902BA,15119424,227840,C:\Users\admin\Desktop\TeXworks0.6.2.exe" | C:\Users\admin\AppData\Local\Temp\is-SO4S6.tmp\TeXworks0.6.2.tmp | TeXworks0.6.2.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 6292 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\SetupFile_665285.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6552 | "C:\Program Files (x86)\TeXworks\TeXworks.exe" | C:\Program Files (x86)\TeXworks\TeXworks.exe | — | TeXworks0.6.2.tmp | |||||||||||
User: admin Company: TeX Users Group Integrity Level: HIGH Description: TeXworks editor & previewer Version: 0.6.2-r.7ecce17 Modules
| |||||||||||||||
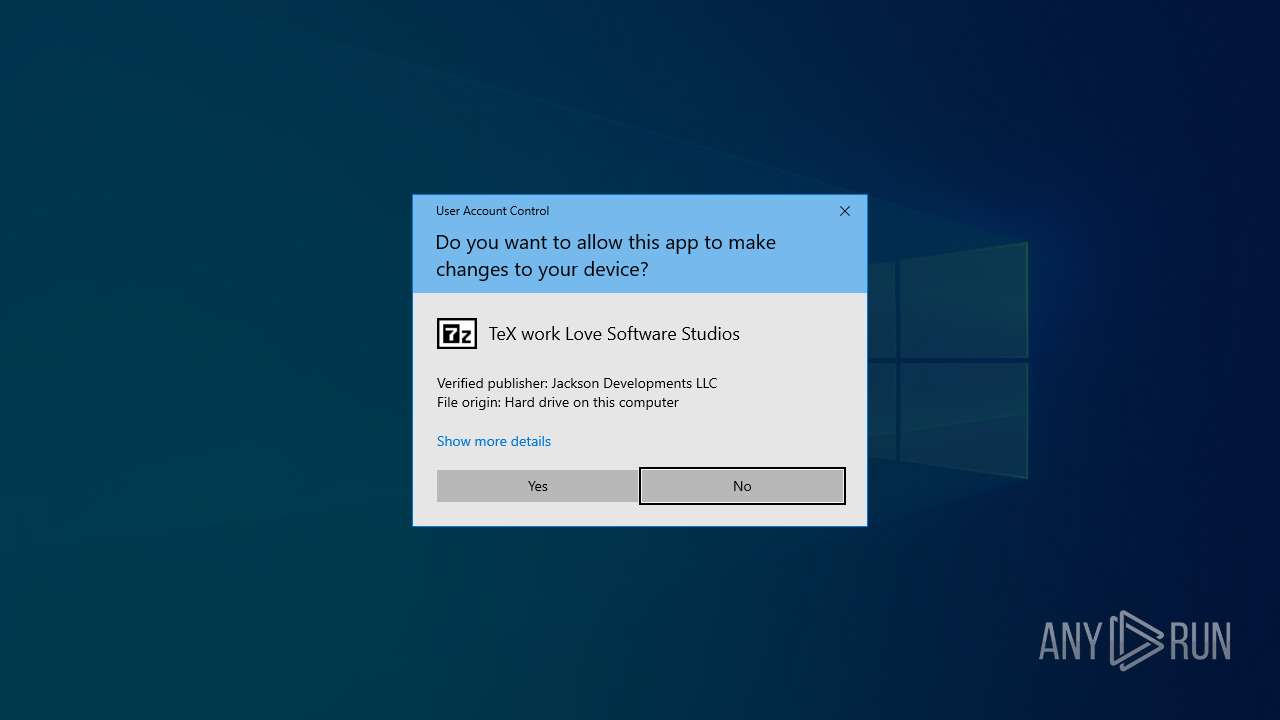
| 7100 | "C:\Users\admin\Desktop\SetupFile_665285.exe" | C:\Users\admin\Desktop\SetupFile_665285.exe | explorer.exe | ||||||||||||
User: admin Company: Love Software Studios Integrity Level: HIGH Description: TeX work Love Software Studios Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
2 108
Read events
2 063
Write events
44
Delete events
1
Modification events
| (PID) Process: | (6292) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6292) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6292) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6292) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\SetupFile_665285.7z | |||
| (PID) Process: | (6292) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6292) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6292) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6292) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6292) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6292) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
8
Suspicious files
216
Text files
457
Unknown types
249
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3080 | TeXworks0.6.2.tmp | C:\Users\admin\AppData\Local\Temp\is-MN9FR.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 3080 | TeXworks0.6.2.tmp | C:\Program Files (x86)\TeXworks\is-6LA7K.tmp | text | |
MD5:751419260AA954499F7ABAABAA882BBE | SHA256:AB15FD526BD8DD18A9E77EBC139656BF4D33E97FC7238CD11BF60E2B9B8666C6 | |||
| 3080 | TeXworks0.6.2.tmp | C:\Program Files (x86)\TeXworks\is-QVI9J.tmp | text | |
MD5:BC3F46D5C147A18EB25404D15C500F89 | SHA256:97613F18BB8FE1C815131F1D4795BD6C45B13FB881FDBDFA5C981E926AD93641 | |||
| 3080 | TeXworks0.6.2.tmp | C:\Program Files (x86)\TeXworks\is-2QB9J.tmp | executable | |
MD5:3925E61E1F5A16CF9AA5E3F0981B2F46 | SHA256:8E76D071DE97C42D6715A31EF6705958EF497C484FFC8D83F181B9CD1554CA7B | |||
| 3080 | TeXworks0.6.2.tmp | C:\Program Files (x86)\TeXworks\README.txt | text | |
MD5:BC3F46D5C147A18EB25404D15C500F89 | SHA256:97613F18BB8FE1C815131F1D4795BD6C45B13FB881FDBDFA5C981E926AD93641 | |||
| 7100 | SetupFile_665285.exe | C:\Users\admin\Desktop\TeXworks0.6.2.exe | executable | |
MD5:DADEC2CE17A256082B1AB0ECC92A01E8 | SHA256:E5847ADB23DFB0944D20890CF0F027A322BCEF323CC98F658D89A16F9CB22AB7 | |||
| 3080 | TeXworks0.6.2.tmp | C:\Program Files (x86)\TeXworks\is-FVBH3.tmp | executable | |
MD5:264E63F2DD7A323A884D004DD3F9D263 | SHA256:5E966F7CD63CB15A989BEBB4FC5A24DABE07CEFD4F288E0F59D9F6643EA38DB1 | |||
| 3080 | TeXworks0.6.2.tmp | C:\Program Files (x86)\TeXworks\share\fonts\is-043OS.tmp | pfb | |
MD5:6DFCB282CF470CEB18D57D017B7898D6 | SHA256:1ED716566691399AAEE420B07FB18CE0AFFBD883091862C68184997A8D6F1A7A | |||
| 3080 | TeXworks0.6.2.tmp | C:\Program Files (x86)\TeXworks\unins000.exe | executable | |
MD5:264E63F2DD7A323A884D004DD3F9D263 | SHA256:5E966F7CD63CB15A989BEBB4FC5A24DABE07CEFD4F288E0F59D9F6643EA38DB1 | |||
| 3080 | TeXworks0.6.2.tmp | C:\Program Files (x86)\TeXworks\share\fonts\d050000l.pfb | pfb | |
MD5:6DFCB282CF470CEB18D57D017B7898D6 | SHA256:1ED716566691399AAEE420B07FB18CE0AFFBD883091862C68184997A8D6F1A7A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
33
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
448 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
448 | svchost.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2136 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5640 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5640 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1344 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
448 | svchost.exe | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
448 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.209.133:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
appstalation.com |
| unknown |
arc.msn.com |
| whitelisted |