| download: | /MSI.msi |
| Full analysis: | https://app.any.run/tasks/56cafb5b-f5bb-45c3-8abc-d17993a489c9 |
| Verdict: | Malicious activity |
| Analysis date: | May 11, 2024, 04:49:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Last Printed: Fri Dec 11 11:47:44 2009, Create Time/Date: Fri Dec 11 11:47:44 2009, Last Saved Time/Date: Fri Sep 18 14:06:51 2020, Security: 0, Code page: 1252, Revision Number: {5079DED0-A577-44C9-A041-A291BC53658D}, Number of Words: 10, Subject: DavinciSoft, Author: Ciguru LLC, Name of Creating Application: DavinciSoft, Template: ;1033, Comments: This installer database contains the logic and data required to install DavinciSoft., Title: Installation Database, Keywords: Installer, MSI, Database, Number of Pages: 200 |
| MD5: | B4A482A7E96CFDEF632A7AF286120156 |
| SHA1: | 73E3639A9388AF84B9C0F172B3AEAF3823014596 |
| SHA256: | EAD5EBF464C313176174FF0FDC3360A3477F6361D0947221D31287EEB04691B3 |
| SSDEEP: | 49152:K449IfHgoHxmbqD+/GKIikt698ta5Q1FTeor8trZe96S2gzgdDcAmEYpbNMZWlMV:o9IIoHWkt698tPTeorH6IzghNmEYpbNs |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 4012)
- msiexec.exe (PID: 3976)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 2108)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 4012)
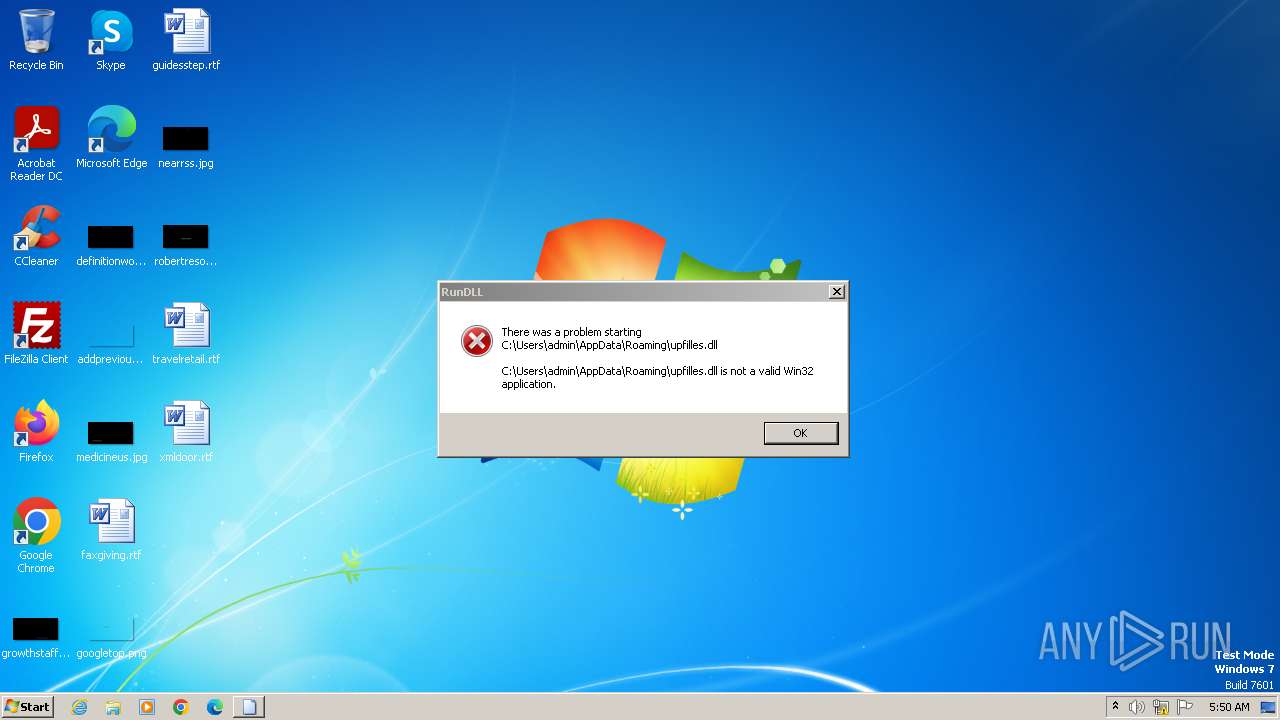
Uses RUNDLL32.EXE to load library
- MSI5F3C.tmp (PID: 2068)
Reads the Internet Settings
- MSI5F3C.tmp (PID: 2068)
Reads security settings of Internet Explorer
- MSI5F3C.tmp (PID: 2068)
INFO
Reads the computer name
- msiexec.exe (PID: 4012)
- msiexec.exe (PID: 4056)
- msiexec.exe (PID: 1588)
- MSI5F3C.tmp (PID: 2068)
Reads the machine GUID from the registry
- msiexec.exe (PID: 4012)
- msiexec.exe (PID: 4056)
- msiexec.exe (PID: 1588)
Checks supported languages
- msiexec.exe (PID: 4056)
- msiexec.exe (PID: 4012)
- MSI5F3C.tmp (PID: 2068)
- msiexec.exe (PID: 1588)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4012)
- msiexec.exe (PID: 3976)
Starts application with an unusual extension
- msiexec.exe (PID: 4012)
Application launched itself
- msiexec.exe (PID: 4012)
Create files in a temporary directory
- msiexec.exe (PID: 4012)
Creates files or folders in the user directory
- msiexec.exe (PID: 4012)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (81.9) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.2) |
| .msp | | | Windows Installer Patch (7.6) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| LastPrinted: | 2009:12:11 11:47:44 |
|---|---|
| CreateDate: | 2009:12:11 11:47:44 |
| ModifyDate: | 2020:09:18 14:06:51 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {5079DED0-A577-44C9-A041-A291BC53658D} |
| Words: | 10 |
| Subject: | DavinciSoft |
| Author: | Ciguru LLC |
| LastModifiedBy: | - |
| Software: | DavinciSoft |
| Template: | ;1033 |
| Comments: | This installer database contains the logic and data required to install DavinciSoft. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| Pages: | 200 |
Total processes
39
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1588 | C:\Windows\system32\MsiExec.exe -Embedding FD8153A8AAA727A8E974C72ED7E1DCCC | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1800 | "C:\Windows\System32\rundll32.exe" C:\Users\admin\AppData\Roaming\upfilles.dll, stow | C:\Windows\System32\rundll32.exe | — | MSI5F3C.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2068 | "C:\Windows\Installer\MSI5F3C.tmp" C:/Windows/System32/rundll32.exe C:\Users\admin\AppData\Roaming\upfilles.dll, stow | C:\Windows\Installer\MSI5F3C.tmp | — | msiexec.exe | |||||||||||
User: admin Company: Caphyon LTD Integrity Level: MEDIUM Description: File that launches another file Exit code: 0 Version: 19.1.0.0 Modules
| |||||||||||||||
| 2108 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3976 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\MSI.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4012 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4056 | C:\Windows\system32\MsiExec.exe -Embedding 0086B6120381CF1CAD57A7DFF451B25E C | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 574
Read events
5 397
Write events
165
Delete events
12
Modification events
| (PID) Process: | (4012) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000E23D8FA95EA3DA01AC0F000060040000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4012) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000E23D8FA95EA3DA01AC0F000060040000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4012) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 75 | |||
| (PID) Process: | (4012) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4000000000000000C4E559AA5EA3DA01AC0F000060040000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4012) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000001E485CAA5EA3DA01AC0F000074010000E80300000100000000000000000000007533668F9B99C64DB66399535A48C6B30000000000000000 | |||
| (PID) Process: | (2108) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000E03368AA5EA3DA013C08000090060000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2108) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000E03368AA5EA3DA013C08000084080000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2108) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000E03368AA5EA3DA013C0800000C040000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2108) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000E03368AA5EA3DA013C08000060030000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2108) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 400000000000000094F86CAA5EA3DA013C0800000C040000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
9
Suspicious files
8
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4012 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{8f663375-999b-4dc6-b663-99535a48c6b3}_OnDiskSnapshotProp | — | |
MD5:— | SHA256:— | |||
| 4012 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3976 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI3A0D.tmp | executable | |
MD5:475D20C0EA477A35660E3F67ECF0A1DF | SHA256:426E6CF199A8268E8A7763EC3A4DD7ADD982B28C51D89EBEA90CA792CBAE14DD | |||
| 4012 | msiexec.exe | C:\Windows\Installer\105882.msi | executable | |
MD5:B4A482A7E96CFDEF632A7AF286120156 | SHA256:EAD5EBF464C313176174FF0FDC3360A3477F6361D0947221D31287EEB04691B3 | |||
| 3976 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI3ABD.tmp | executable | |
MD5:475D20C0EA477A35660E3F67ECF0A1DF | SHA256:426E6CF199A8268E8A7763EC3A4DD7ADD982B28C51D89EBEA90CA792CBAE14DD | |||
| 4012 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF3980774851C71C93.TMP | gmc | |
MD5:3E7877412860E83A99415F4F6CEE0FBB | SHA256:AD0B5C1B0C72FD4D7A6E2727487A0D9819540F1808613B3DC6C7CB1B62109E77 | |||
| 4012 | msiexec.exe | C:\Config.Msi\105884.rbs | binary | |
MD5:D2A957D0D05C776E51FFD44F01EDC52D | SHA256:4D0649C12685ECA09DE3ACE4D9ECB2B7089A7C3C96EAE2692686536969C2ACDA | |||
| 4012 | msiexec.exe | C:\Users\admin\AppData\Roaming\upfilles.dll | executable | |
MD5:CCB6D3CB020F56758622911DDD2F1FCB | SHA256:F4CB6B684EA097F867D406A978B3422BBF2ECFEA39236BF3AB99340996B825DE | |||
| 4012 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF93E5AC7DCA726F65.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 4012 | msiexec.exe | C:\Windows\Installer\MSI5E6F.tmp | binary | |
MD5:B54DA1FE7947D6006C5B8C7752A54E95 | SHA256:84FE22F9F06D09E9B32470F461EA265CA18382C027292E4064A86B56B8CCDA30 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |