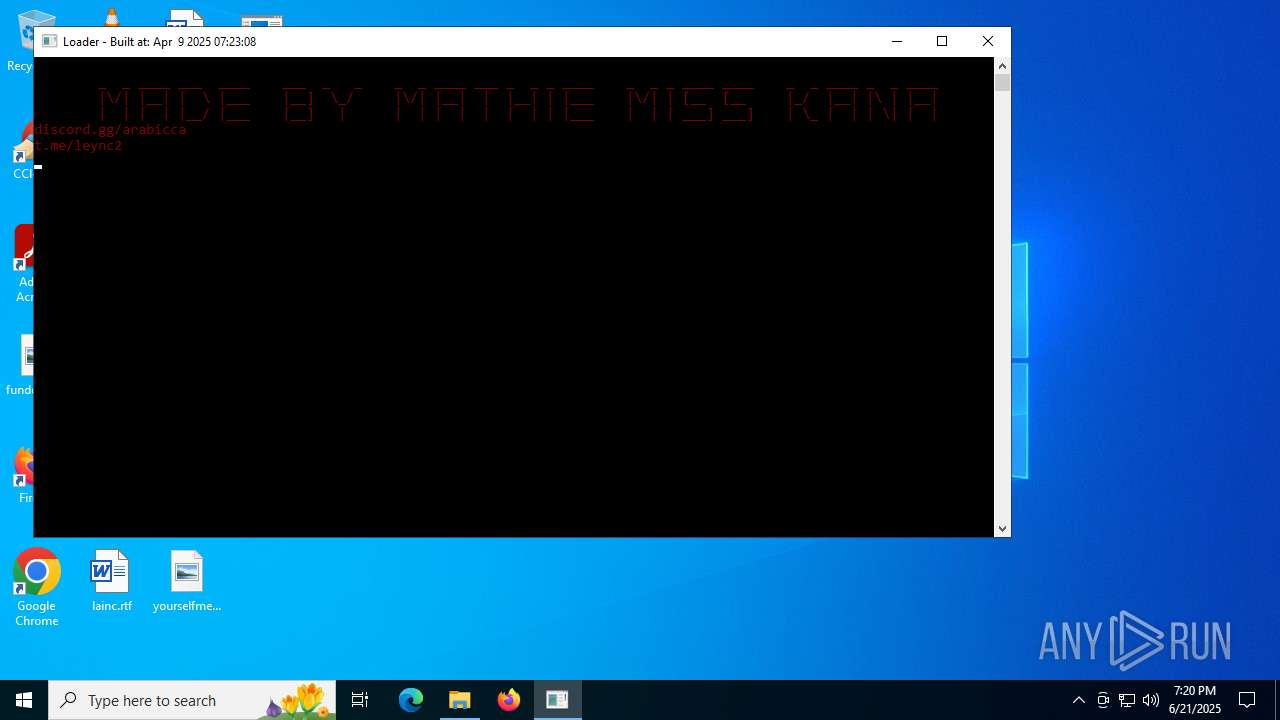
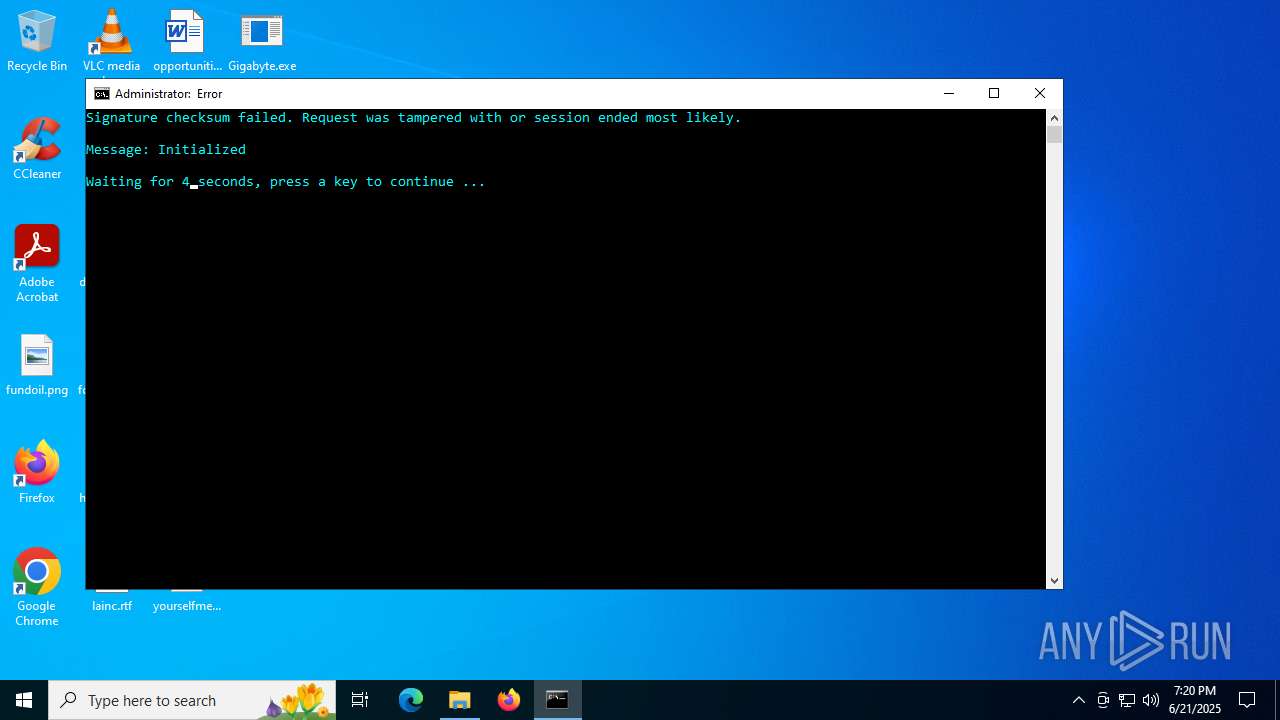
| File name: | Gigabyte.exe |
| Full analysis: | https://app.any.run/tasks/648dbc27-5407-45e1-946e-4bb3d9ac9ec3 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 19:18:38 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | 936E50665D8AB942A57A491AF7D14815 |
| SHA1: | D695D317E4867DEB29D11F3B0E491D273589BE3D |
| SHA256: | EACF0DCC6014BC800F6D212F999F2A1F9889D71E5BFFF12567F7E42E70F0D6C0 |
| SSDEEP: | 24576:urhlcH6Ovl+3+0ORw4VBFJxPdOfOSddLYQUNS:QcBl+3+0ORw8BFzPdxSddLRUNS |
MALICIOUS
No malicious indicators.SUSPICIOUS
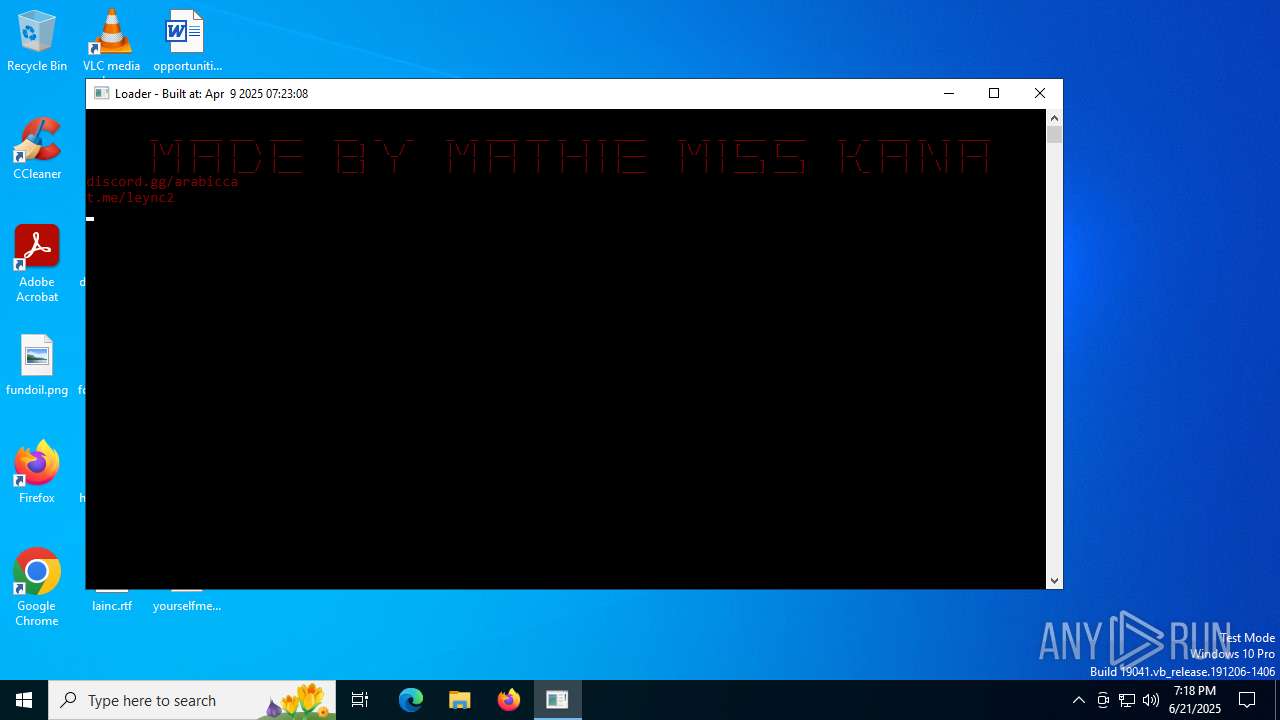
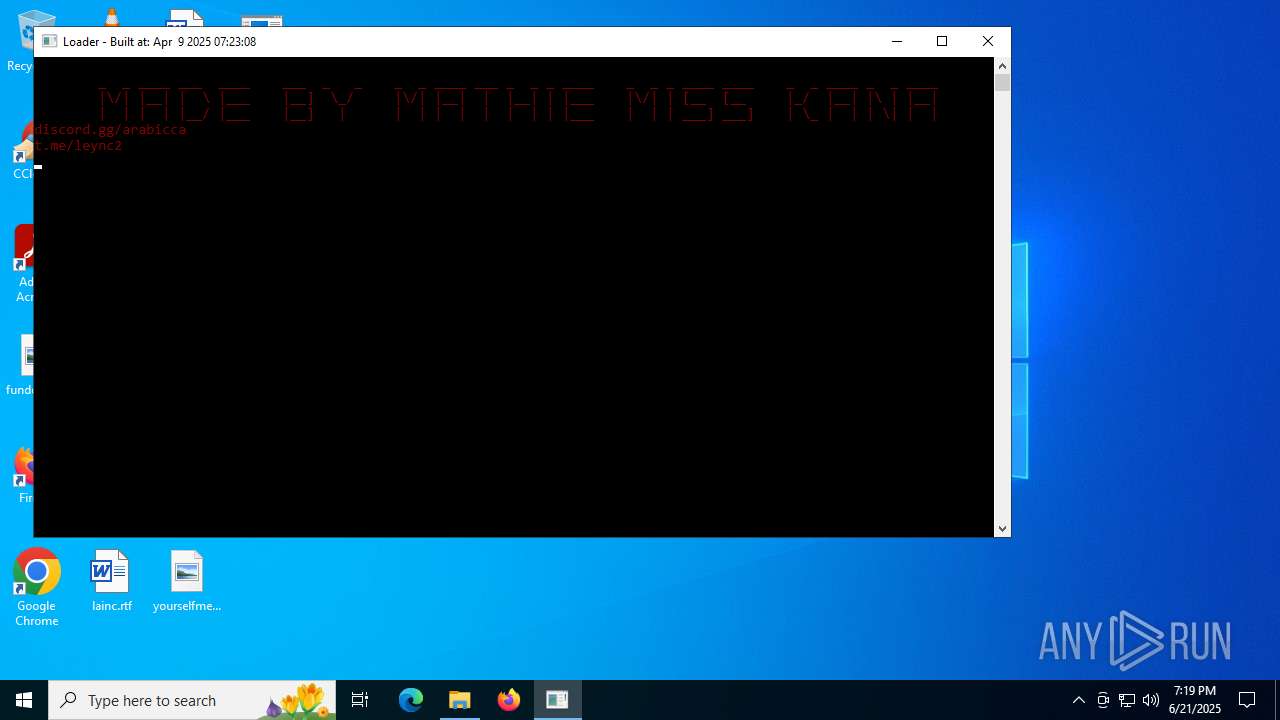
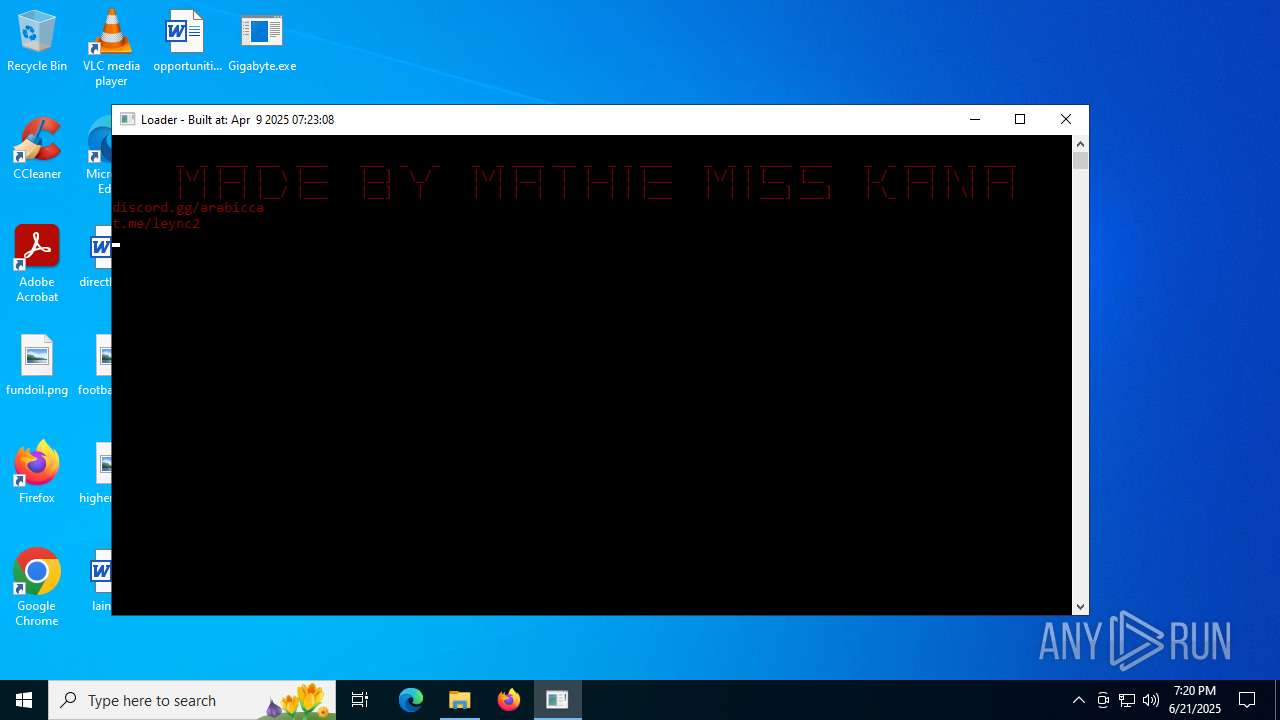
Starts CMD.EXE for commands execution
- Gigabyte.exe (PID: 1720)
- cmd.exe (PID: 6896)
- Gigabyte.exe (PID: 4808)
- cmd.exe (PID: 4520)
- Gigabyte.exe (PID: 6516)
- Gigabyte.exe (PID: 6336)
- cmd.exe (PID: 2076)
- cmd.exe (PID: 7080)
- Gigabyte.exe (PID: 4372)
- cmd.exe (PID: 6836)
- Gigabyte.exe (PID: 888)
- cmd.exe (PID: 5432)
Application launched itself
- cmd.exe (PID: 6896)
- cmd.exe (PID: 4520)
- cmd.exe (PID: 7080)
- cmd.exe (PID: 2076)
- cmd.exe (PID: 5432)
- cmd.exe (PID: 6836)
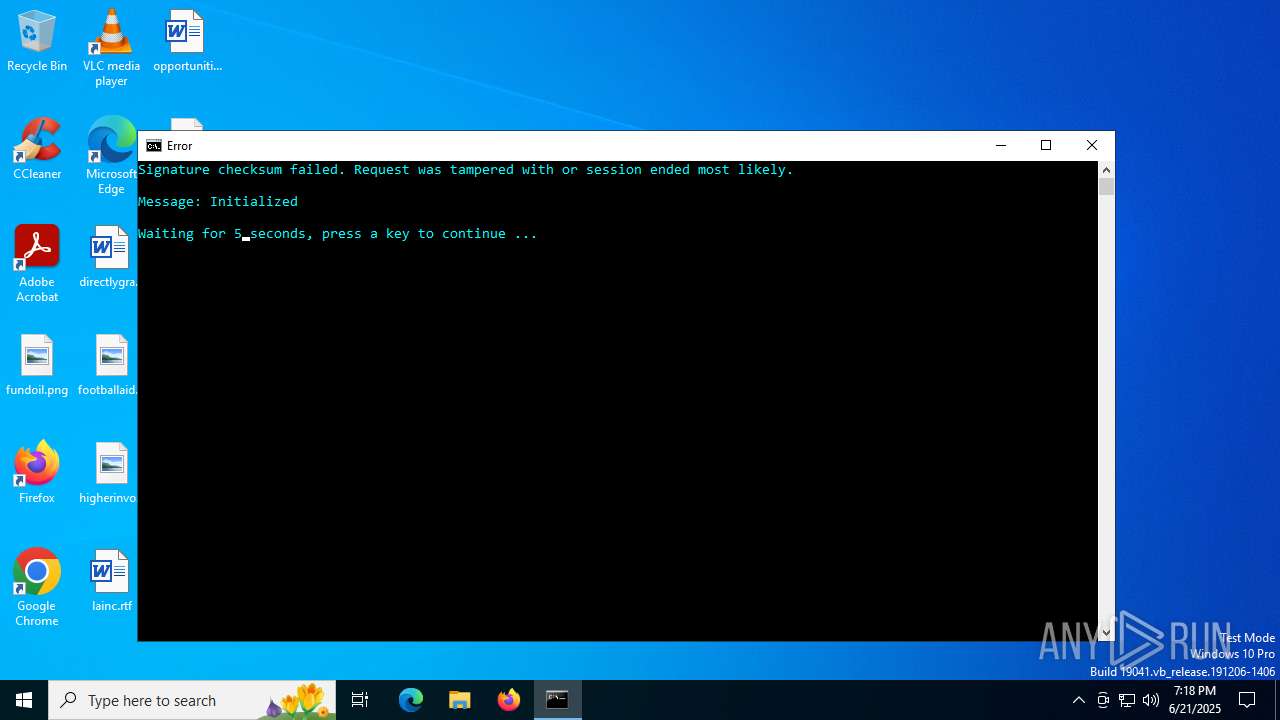
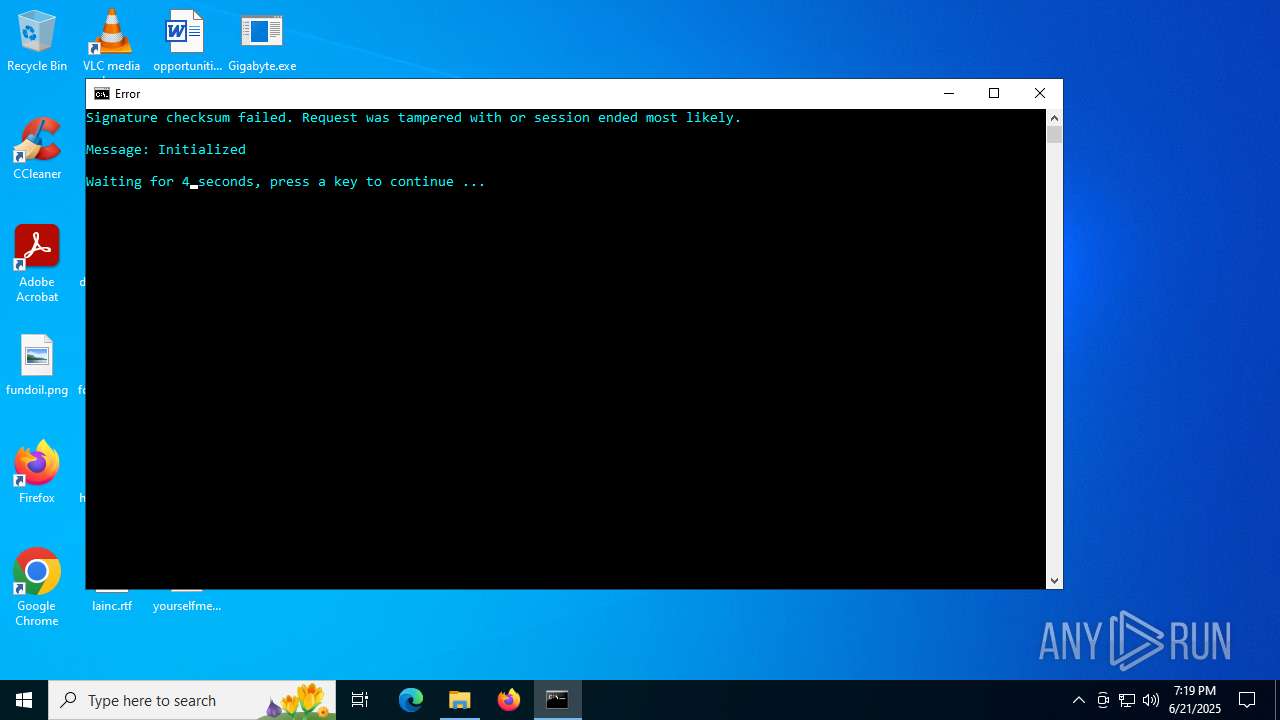
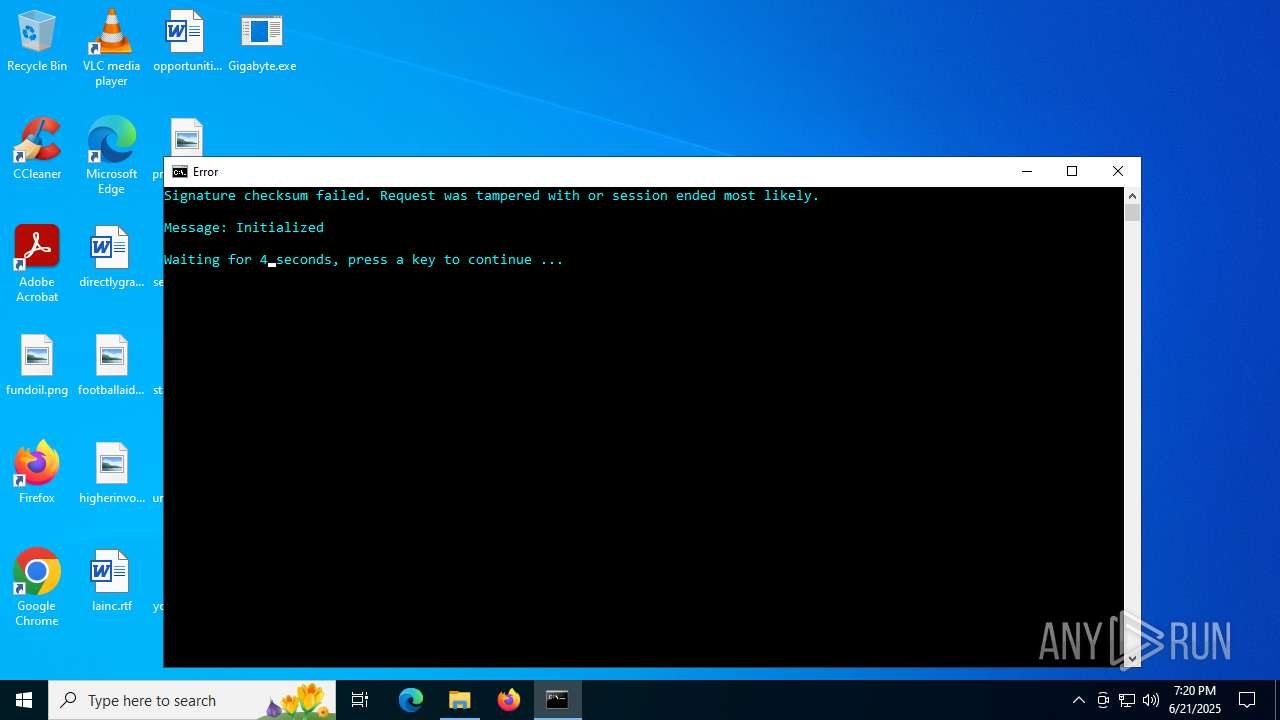
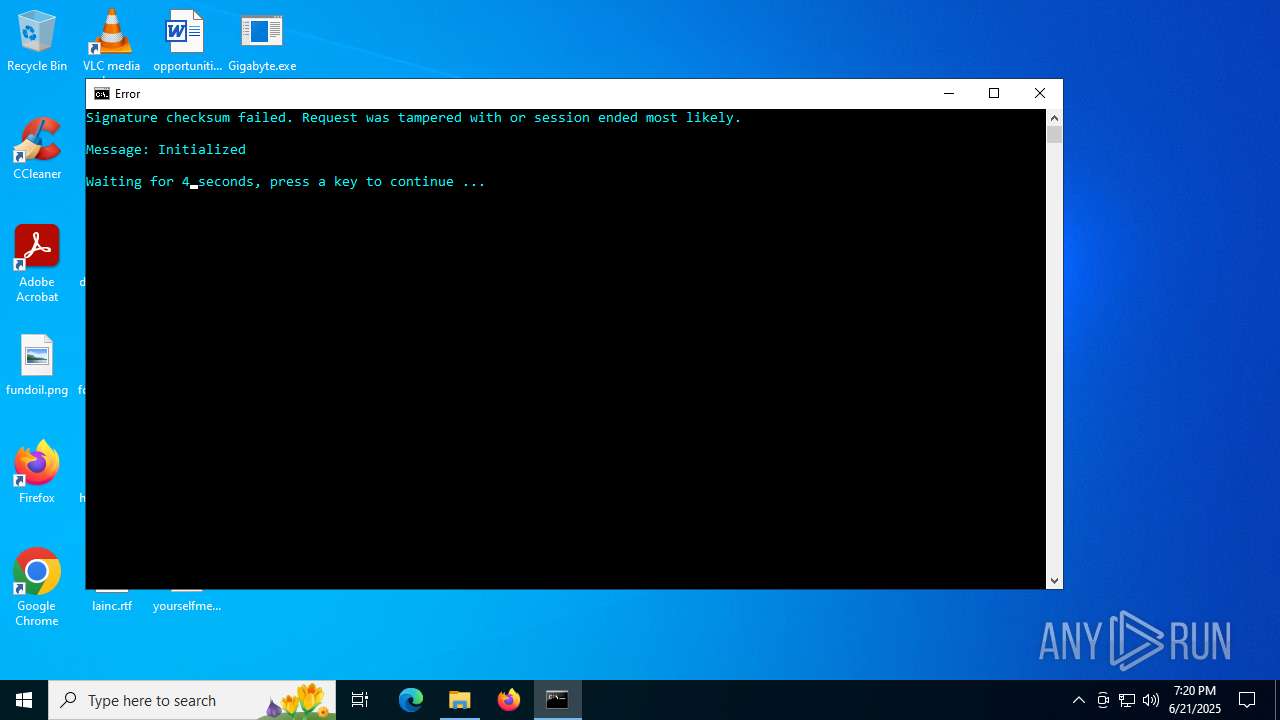
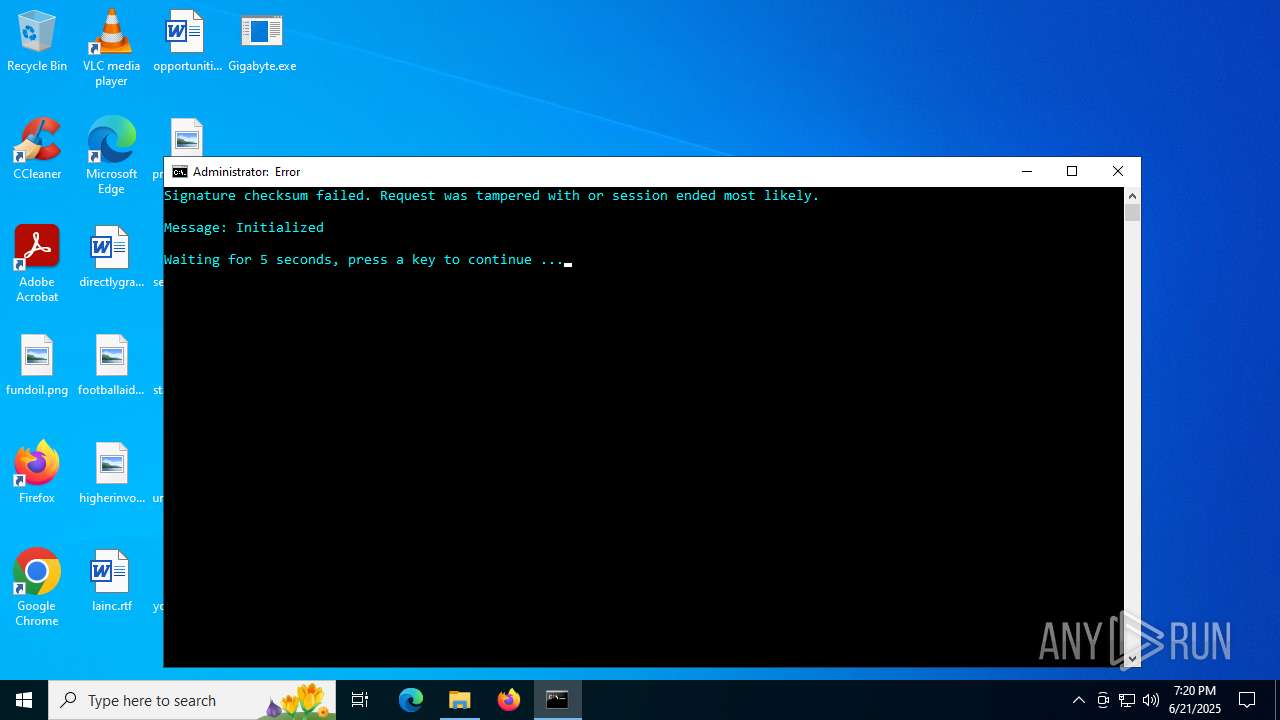
Executes application which crashes
- Gigabyte.exe (PID: 1720)
- Gigabyte.exe (PID: 4808)
- Gigabyte.exe (PID: 6516)
- Gigabyte.exe (PID: 6336)
- Gigabyte.exe (PID: 888)
- Gigabyte.exe (PID: 4372)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5708)
- cmd.exe (PID: 6620)
- cmd.exe (PID: 5744)
- cmd.exe (PID: 4800)
- cmd.exe (PID: 6676)
- cmd.exe (PID: 6140)
INFO
Gets the hash of the file via CERTUTIL.EXE
- certutil.exe (PID: 5712)
- certutil.exe (PID: 6672)
- certutil.exe (PID: 2276)
- certutil.exe (PID: 2132)
- certutil.exe (PID: 864)
- certutil.exe (PID: 1740)
Reads the computer name
- Gigabyte.exe (PID: 1720)
- Gigabyte.exe (PID: 4808)
- Gigabyte.exe (PID: 6516)
- Gigabyte.exe (PID: 6336)
- Gigabyte.exe (PID: 4372)
- Gigabyte.exe (PID: 888)
Checks supported languages
- Gigabyte.exe (PID: 1720)
- Gigabyte.exe (PID: 4808)
- Gigabyte.exe (PID: 6516)
- Gigabyte.exe (PID: 6336)
- Gigabyte.exe (PID: 888)
- Gigabyte.exe (PID: 4372)
Creates files in the program directory
- Gigabyte.exe (PID: 1720)
Manual execution by a user
- Gigabyte.exe (PID: 4808)
- Gigabyte.exe (PID: 6516)
- Gigabyte.exe (PID: 6336)
- Gigabyte.exe (PID: 4372)
- Gigabyte.exe (PID: 888)
Checks proxy server information
- slui.exe (PID: 5476)
Reads the software policy settings
- slui.exe (PID: 5476)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:04:08 23:23:12+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.42 |
| CodeSize: | 564224 |
| InitializedDataSize: | 163328 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x86c10 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
221
Monitored processes
69
Malicious processes
0
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 620 | find /i /v "md5" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | certutil -hashfile "C:\Users\admin\Desktop\Gigabyte.exe" MD5 | C:\Windows\System32\certutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 888 | "C:\Users\admin\Desktop\Gigabyte.exe" | C:\Users\admin\Desktop\Gigabyte.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221226505 Modules
| |||||||||||||||
| 1052 | find /i /v "certutil" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1488 | C:\WINDOWS\system32\WerFault.exe -u -p 4372 -s 804 | C:\Windows\System32\WerFault.exe | — | Gigabyte.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 2147942405 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1704 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Gigabyte.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1712 | find /i /v "certutil" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1720 | "C:\Users\admin\AppData\Local\Temp\Gigabyte.exe" | C:\Users\admin\AppData\Local\Temp\Gigabyte.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226505 Modules
| |||||||||||||||
| 1740 | certutil -hashfile "C:\Users\admin\Desktop\Gigabyte.exe" MD5 | C:\Windows\System32\certutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 714
Read events
5 711
Write events
3
Delete events
0
Modification events
| (PID) Process: | (1740) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.1!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_AUTO_UPDATE_CA_REVOCATION | |||
| (PID) Process: | (1740) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.2!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_AUTO_UPDATE_END_REVOCATION | |||
| (PID) Process: | (1740) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.3!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_NO_OCSP_FAILOVER_TO_CRL | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
37
DNS requests
22
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
764 | lsass.exe | GET | 200 | 104.18.21.213:80 | http://e6.c.lencr.org/19.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.24.77.37:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
3148 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
436 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3148 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2664 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1440 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4236 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1720 | Gigabyte.exe | 104.26.1.5:443 | keyauth.win | CLOUDFLARENET | US | malicious |
764 | lsass.exe | 104.18.21.213:80 | e6.c.lencr.org | CLOUDFLARENET | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 184.24.77.37:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
keyauth.win |
| malicious |
e6.c.lencr.org |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain in DNS Lookup (keyauth .win) |
1720 | Gigabyte.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain (keyauth .win) in TLS SNI |
4808 | Gigabyte.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain (keyauth .win) in TLS SNI |
6516 | Gigabyte.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain (keyauth .win) in TLS SNI |
6336 | Gigabyte.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain (keyauth .win) in TLS SNI |
888 | Gigabyte.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain (keyauth .win) in TLS SNI |
4372 | Gigabyte.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain (keyauth .win) in TLS SNI |