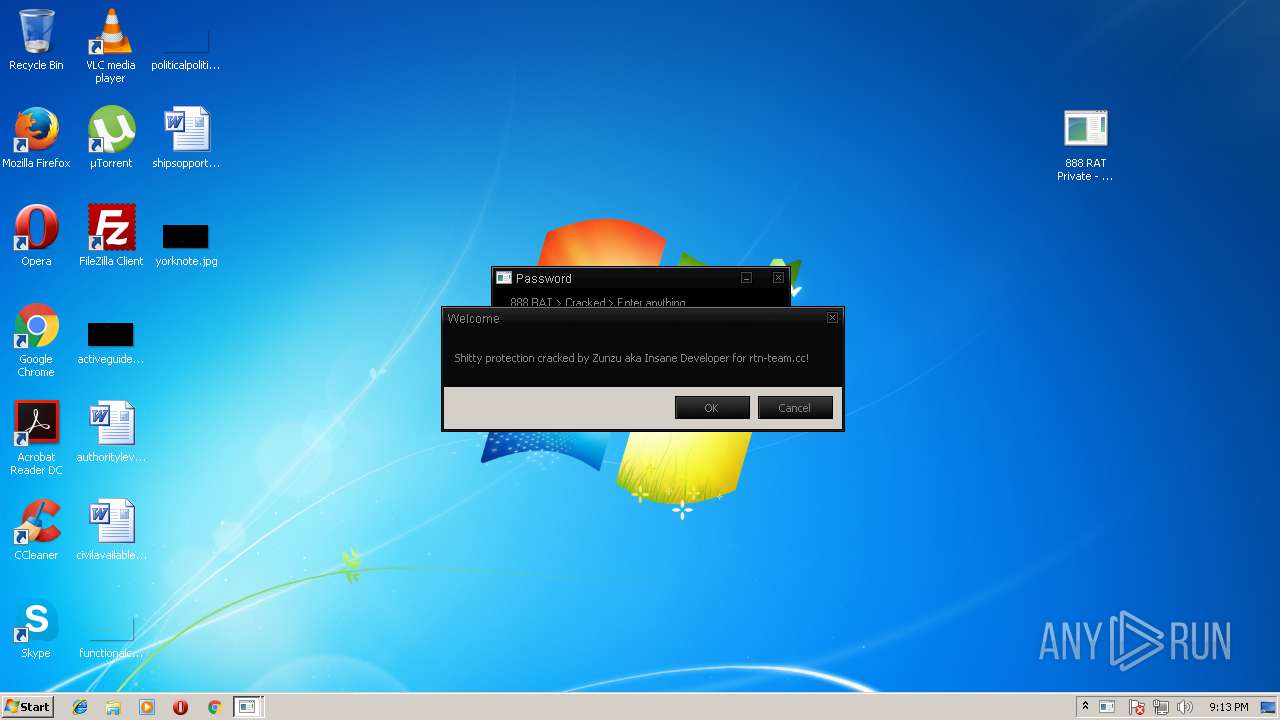
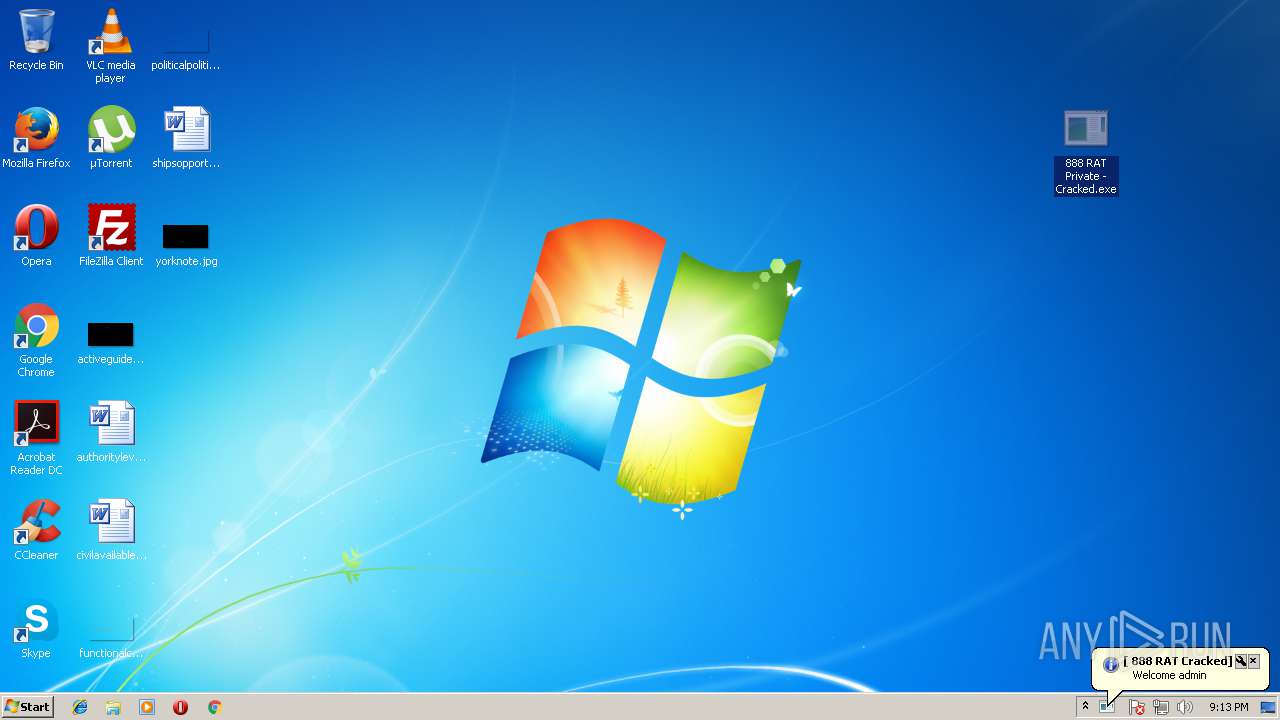
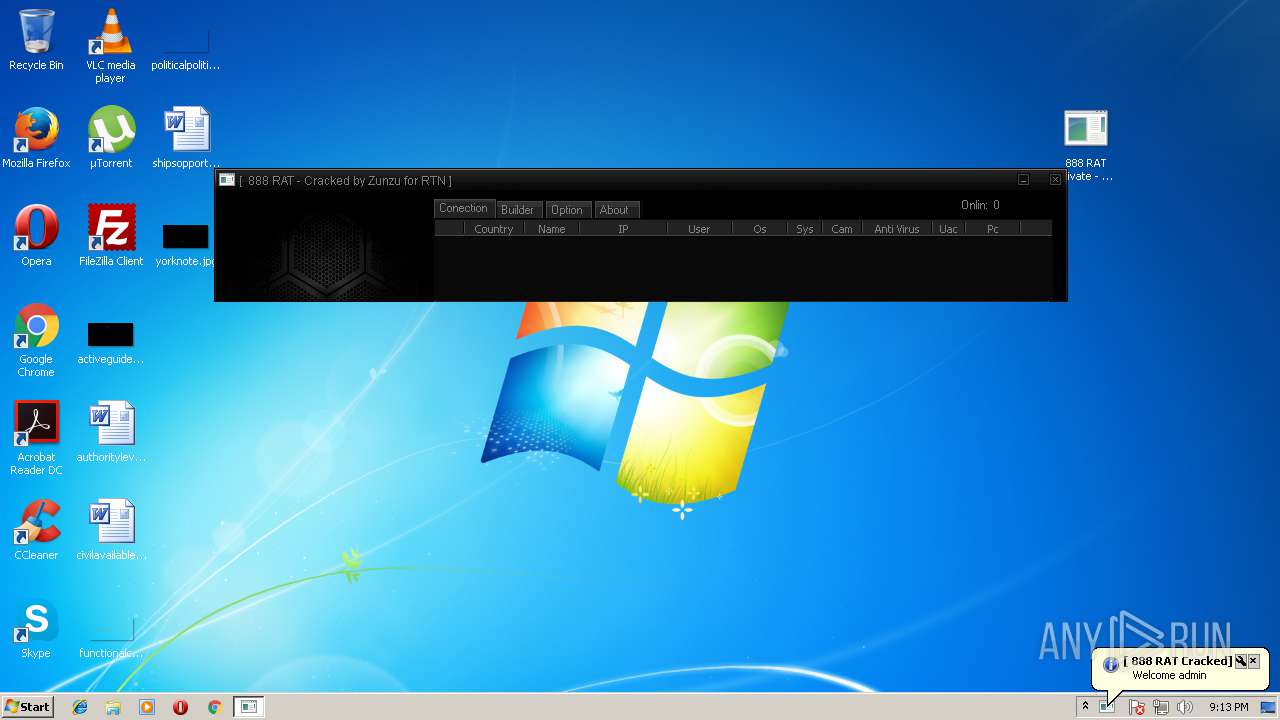
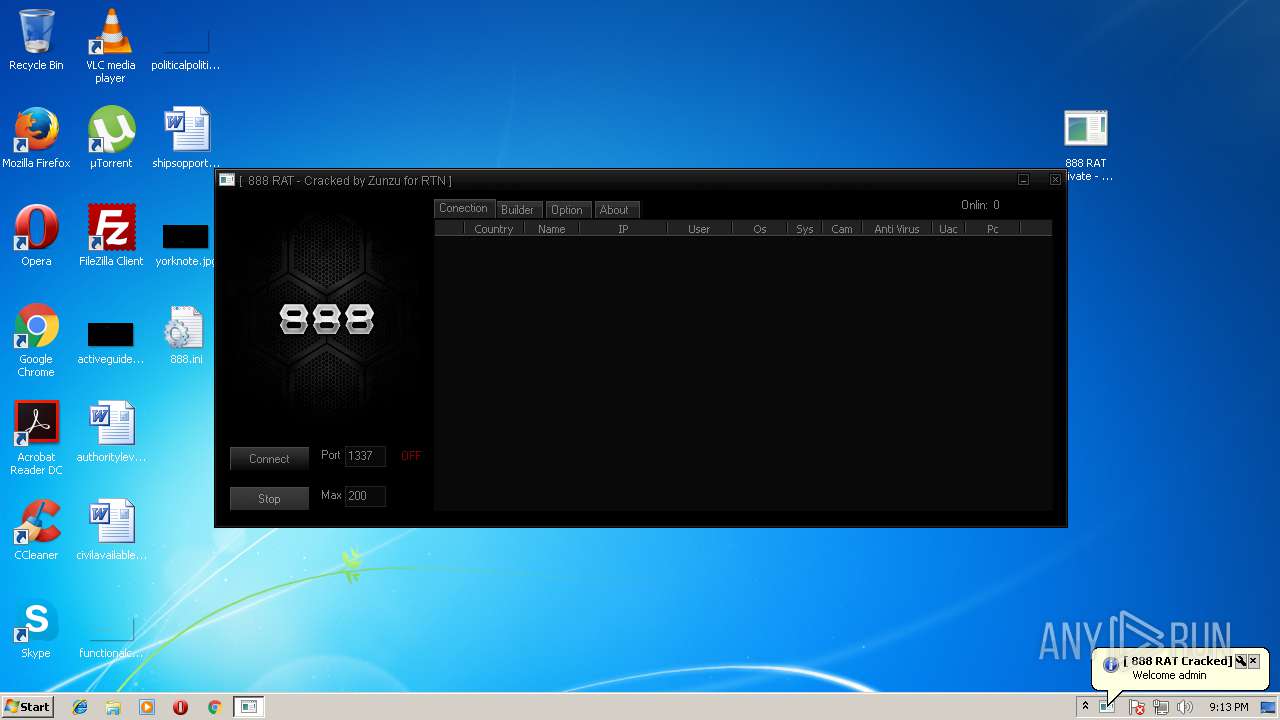
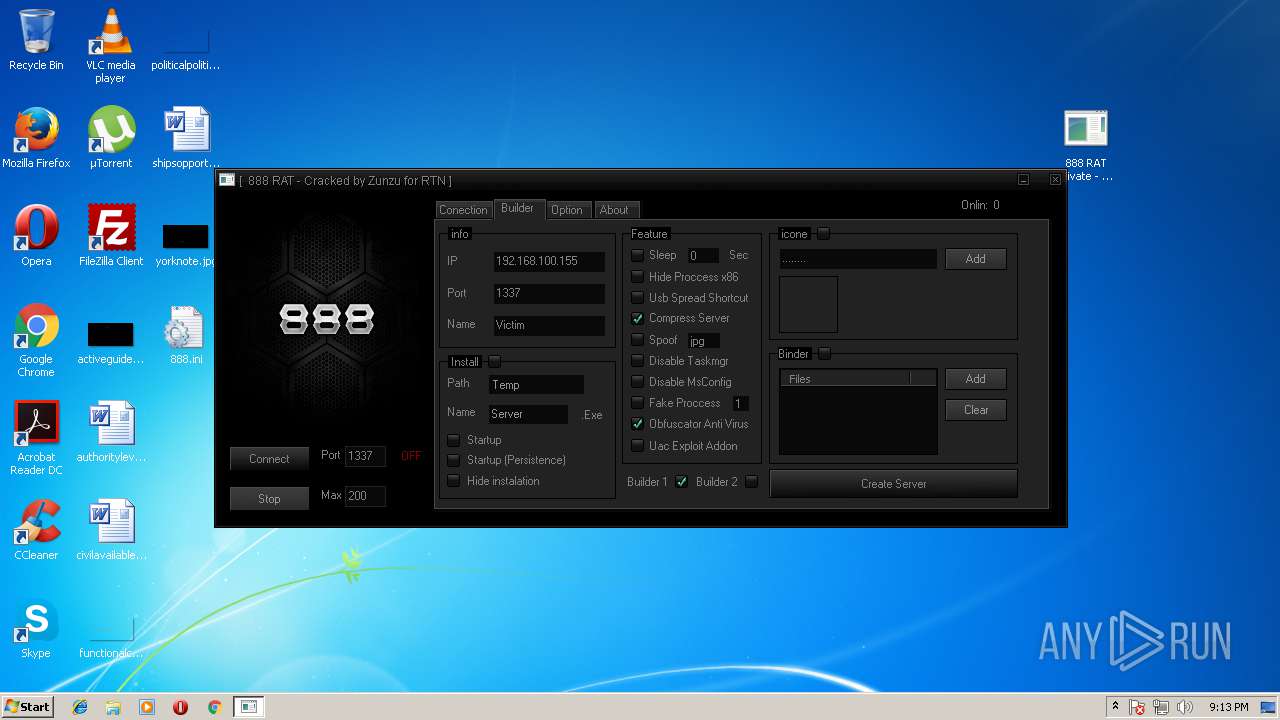
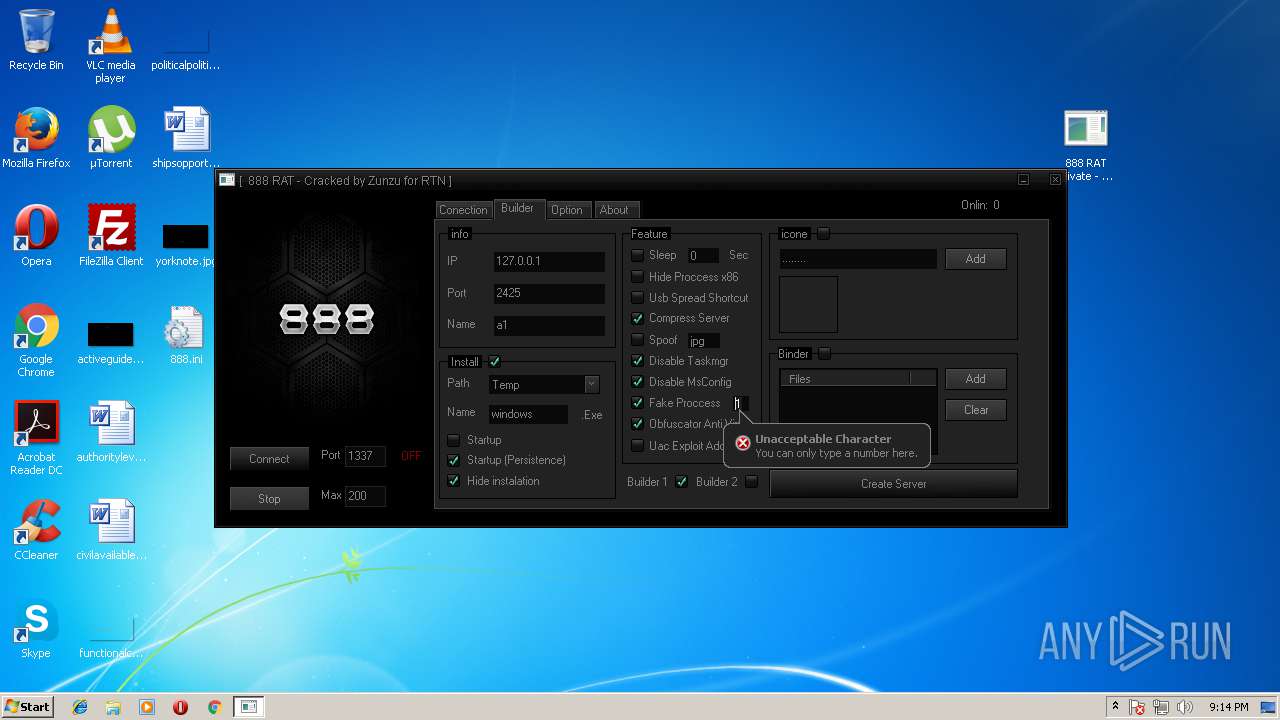
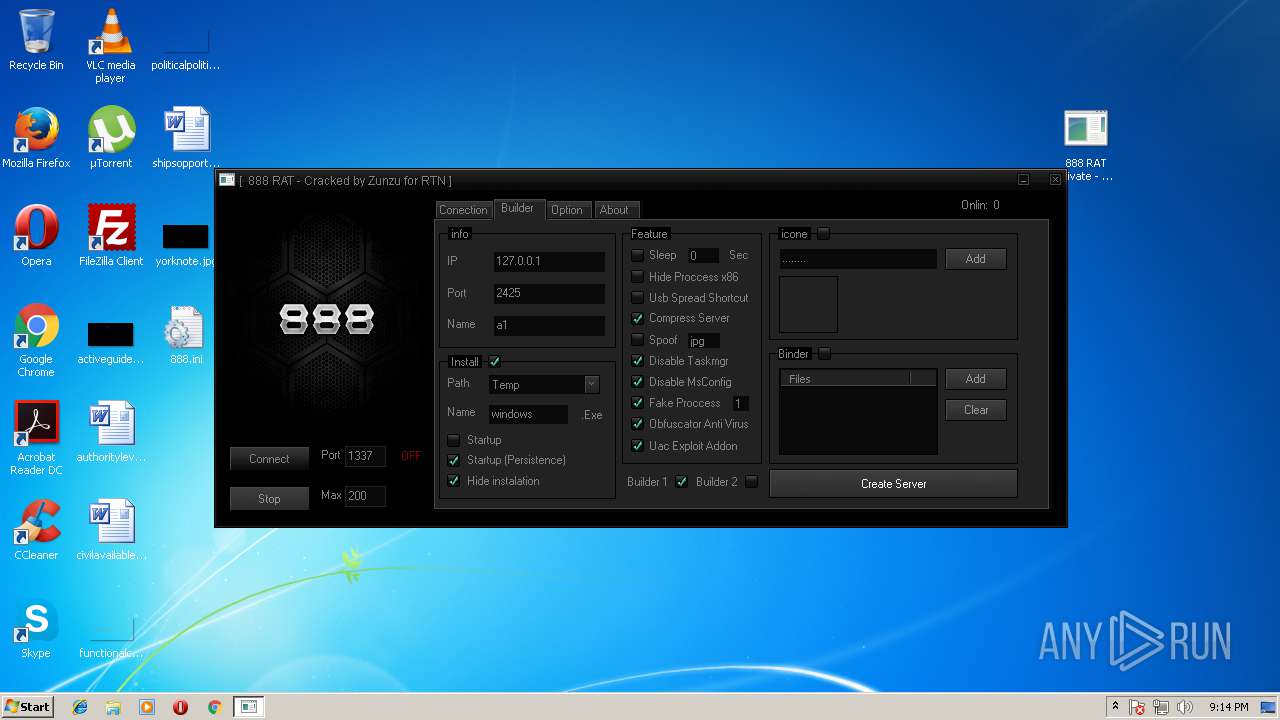
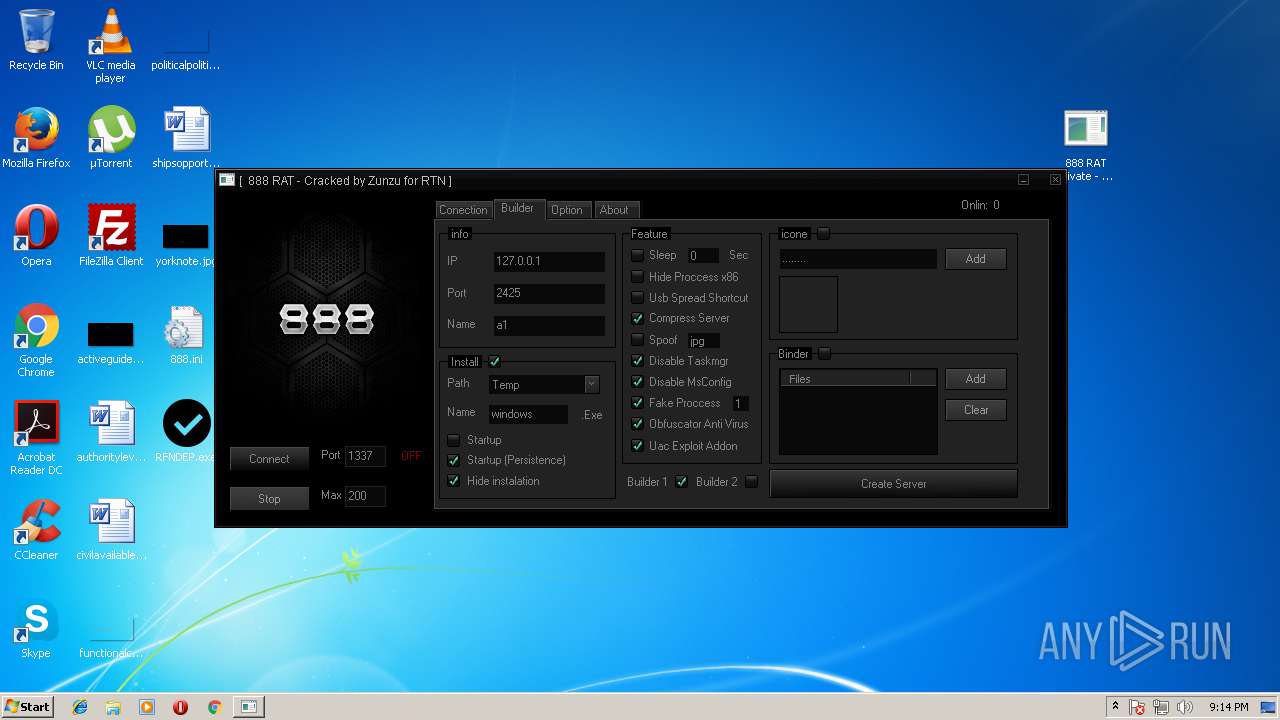
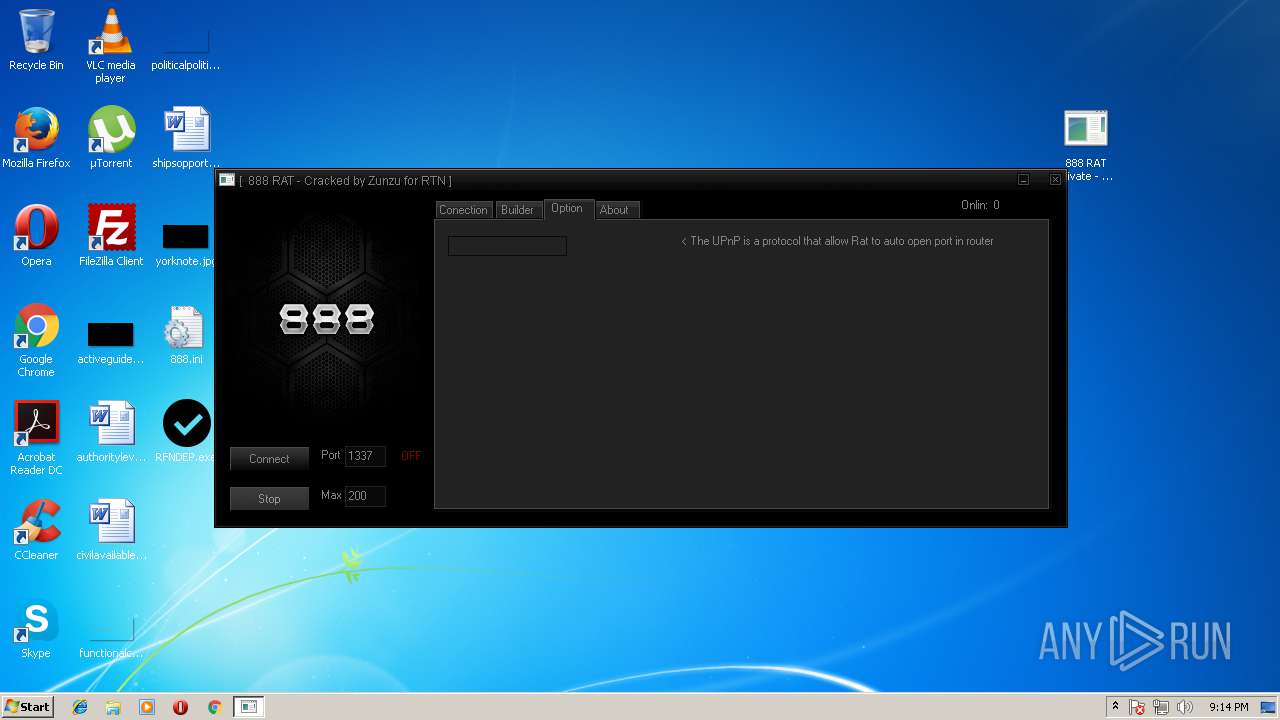
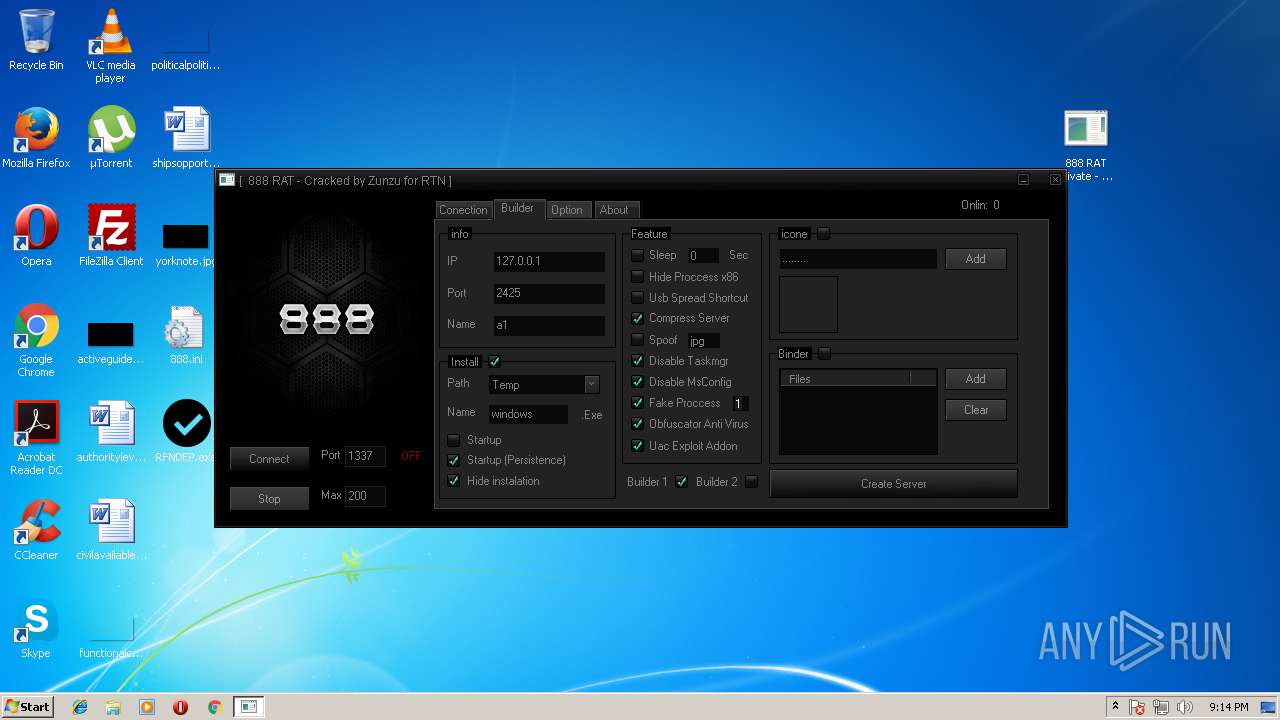
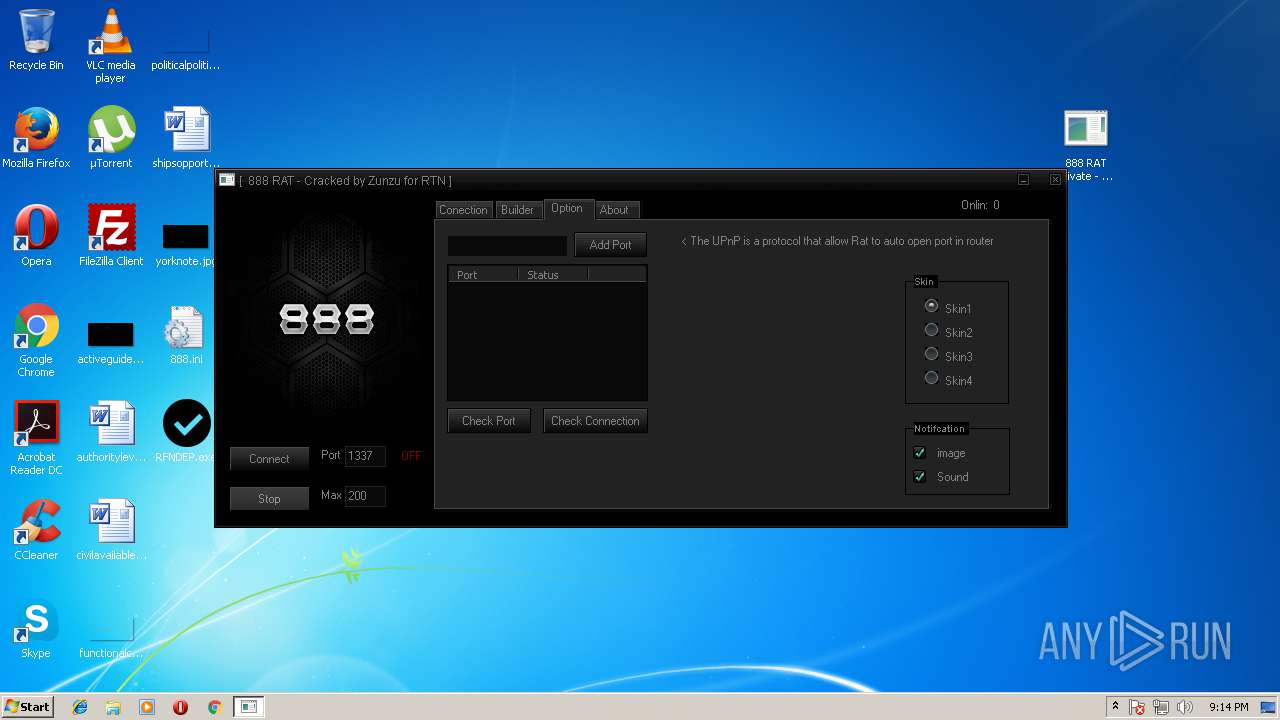
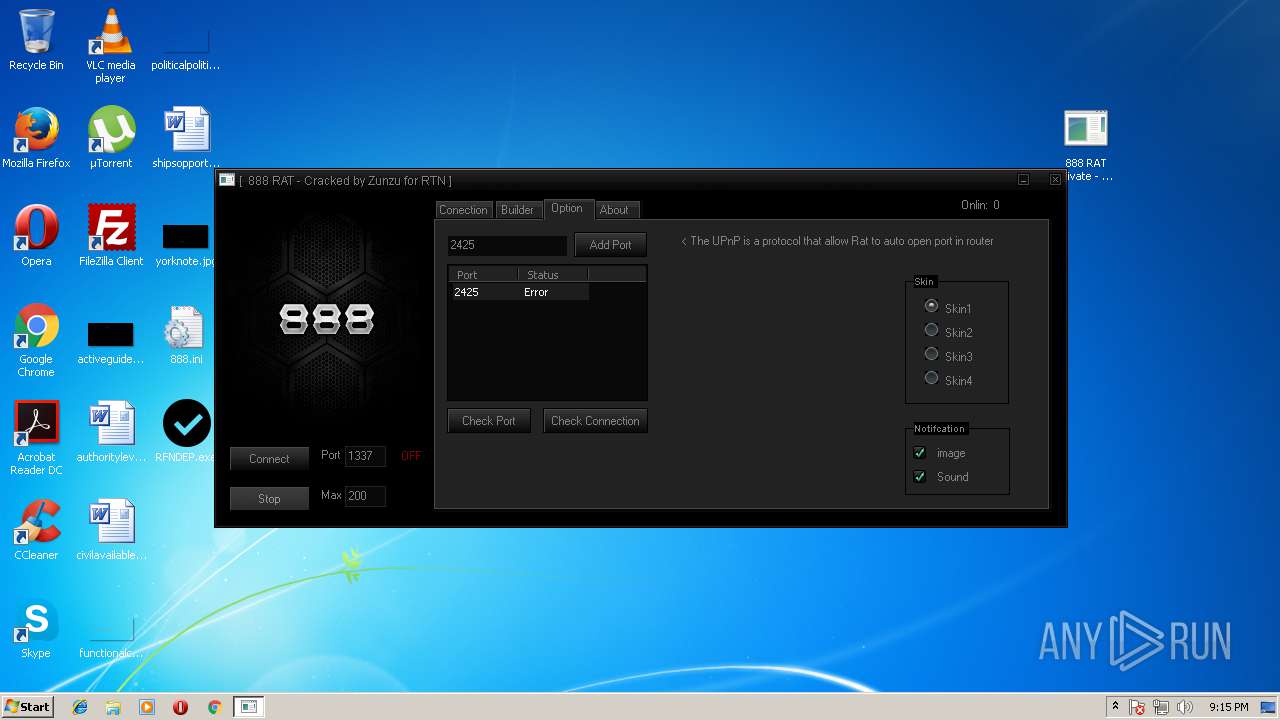
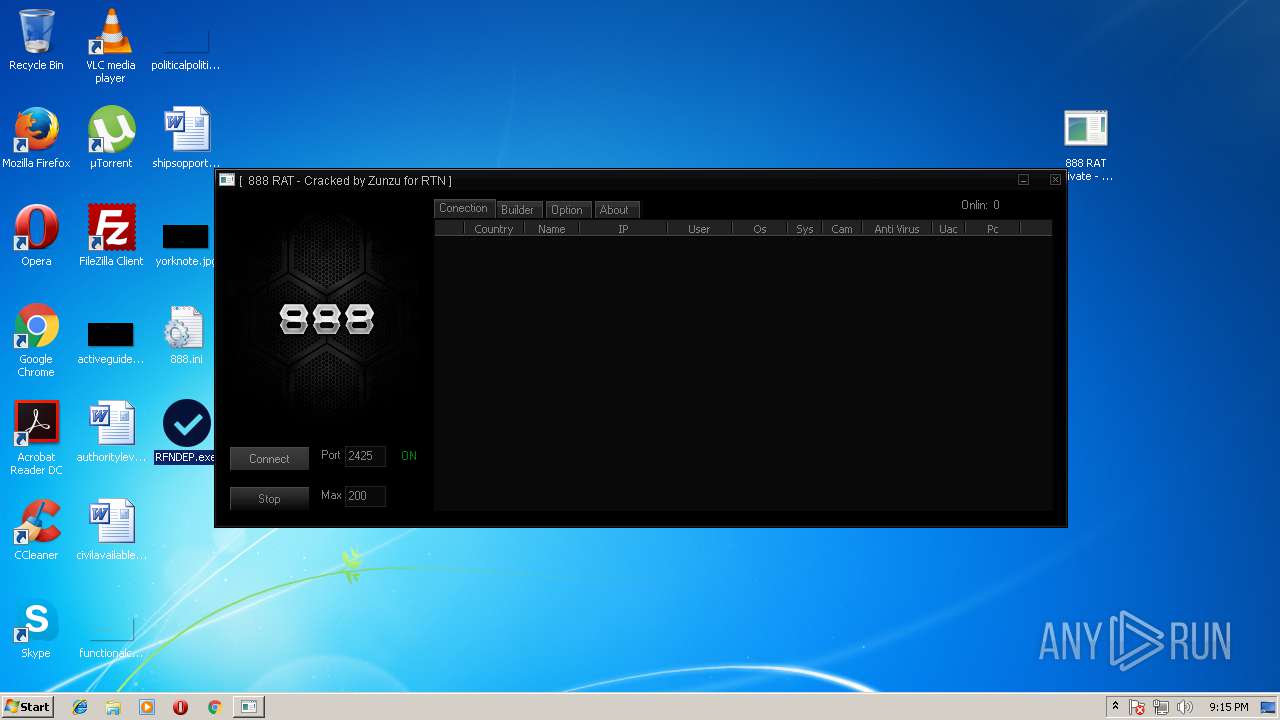
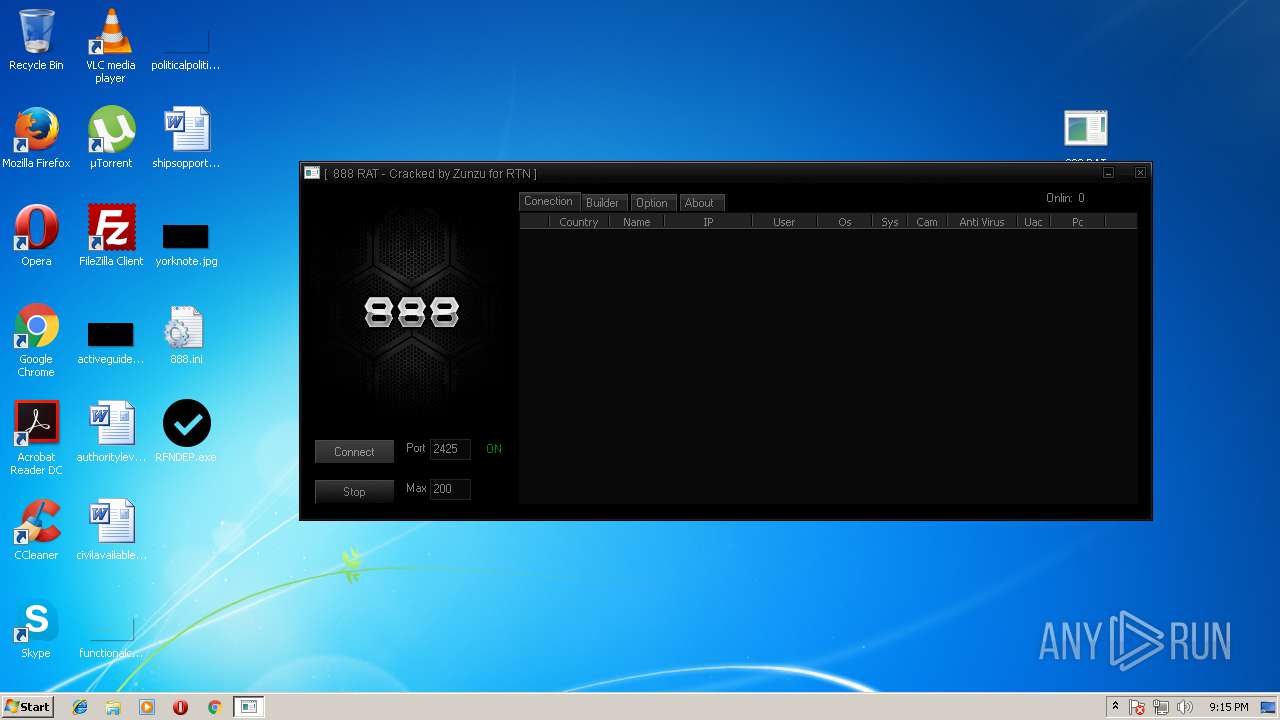
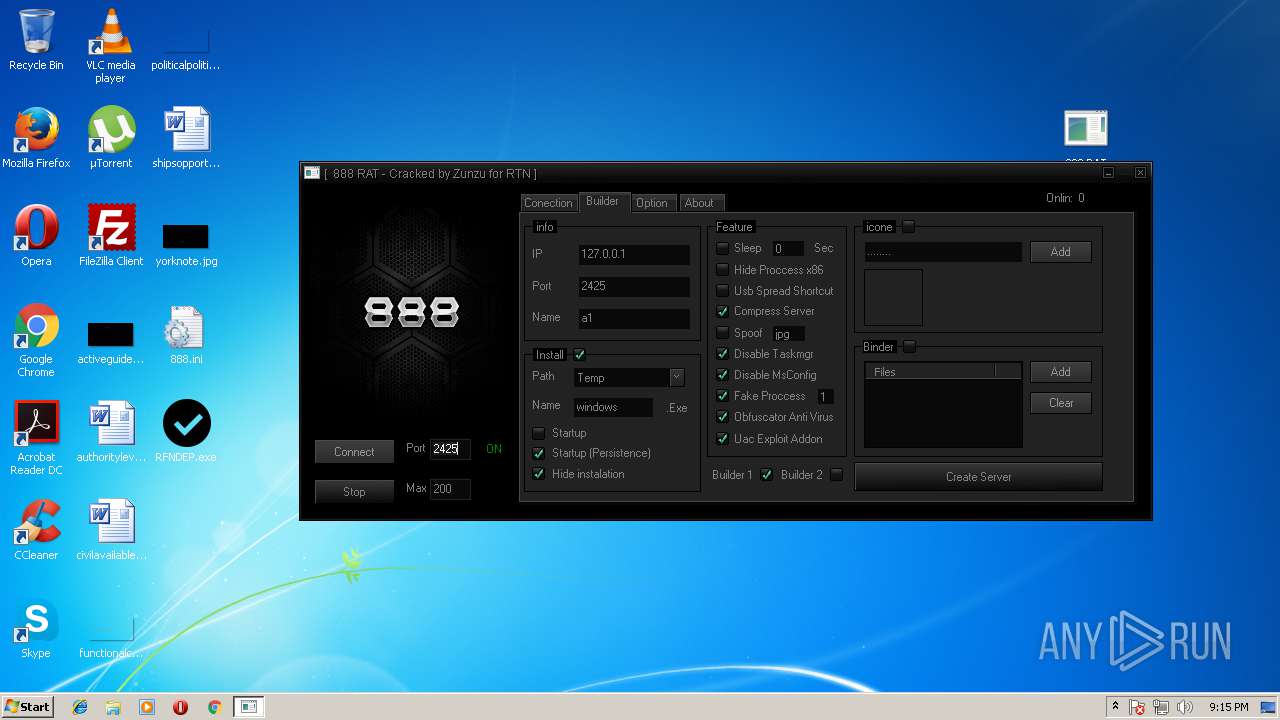
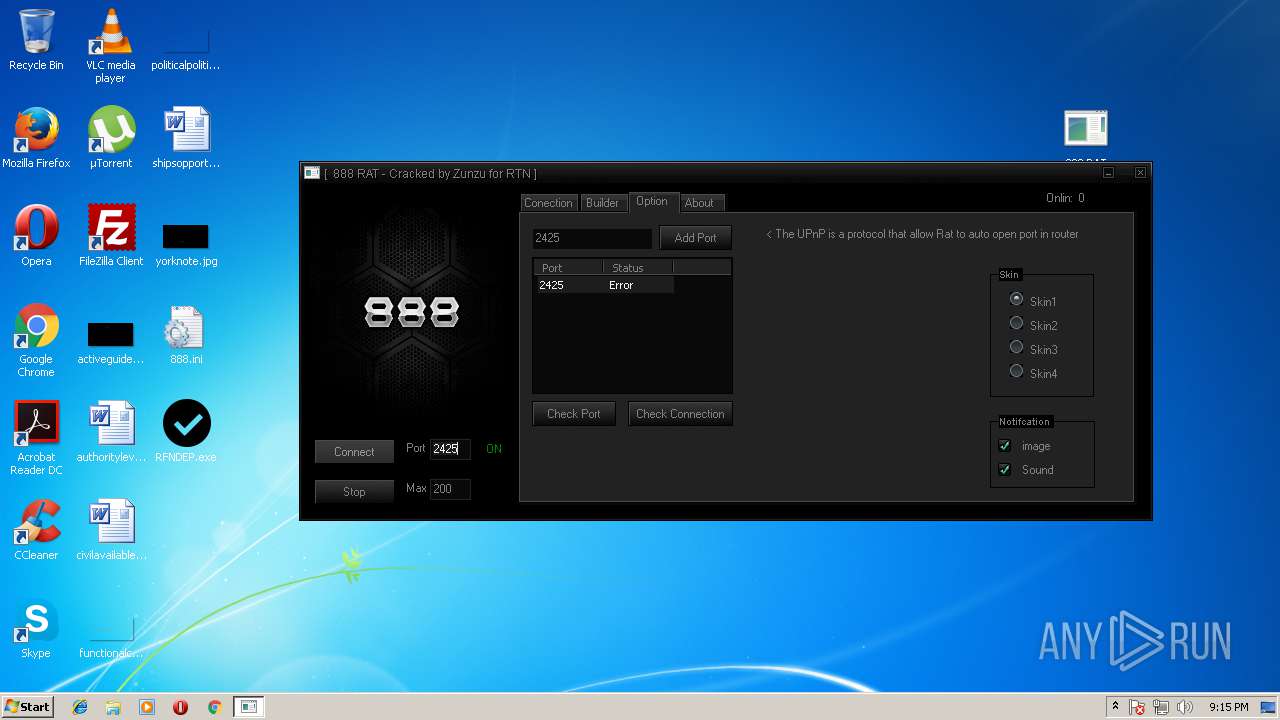
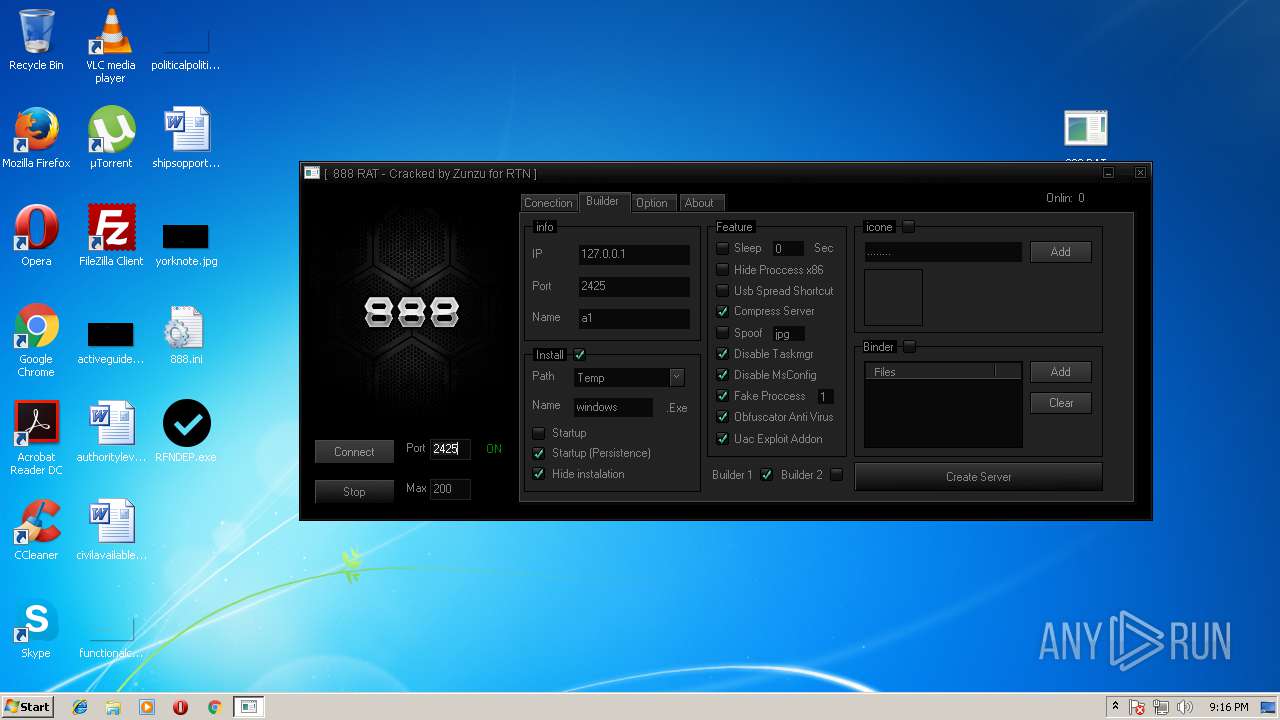
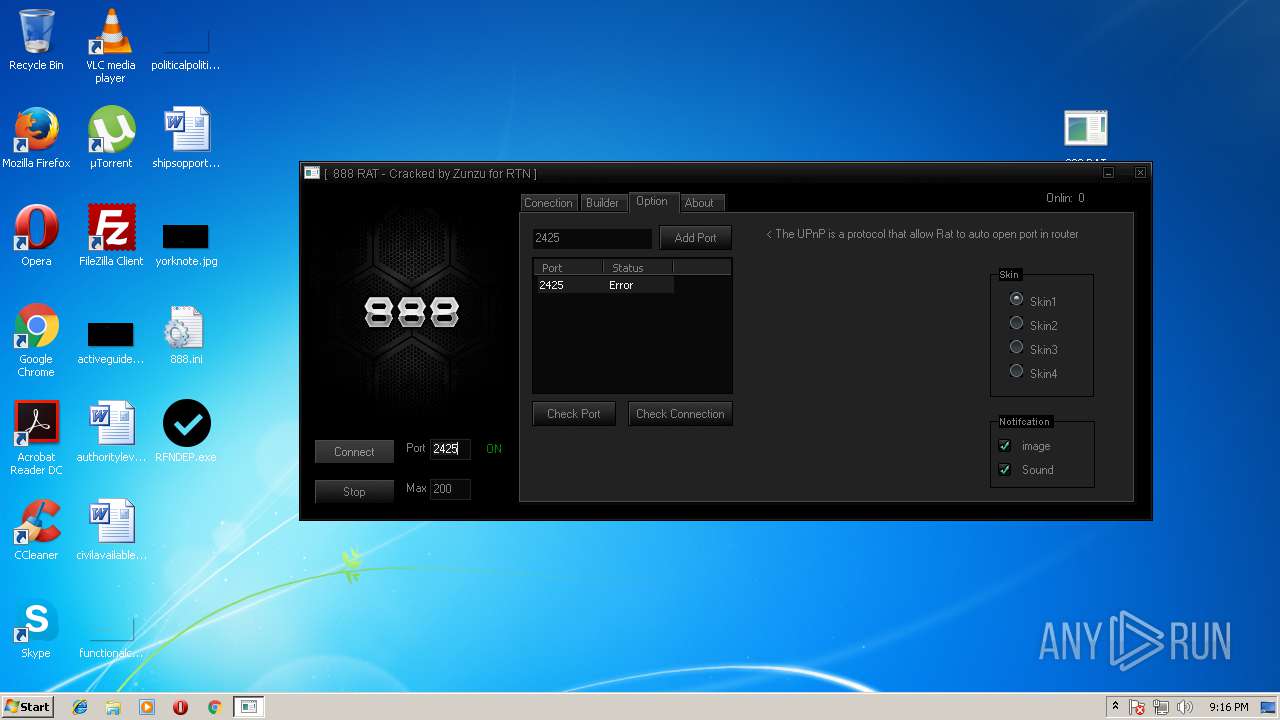
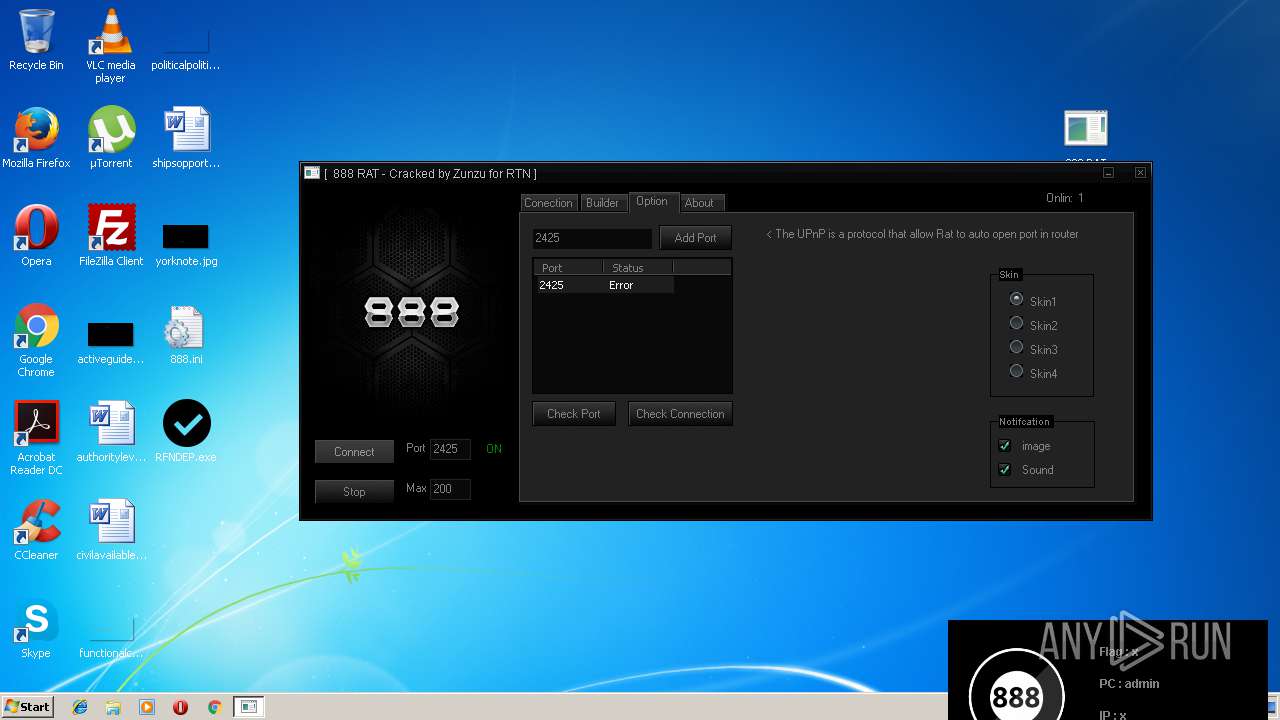
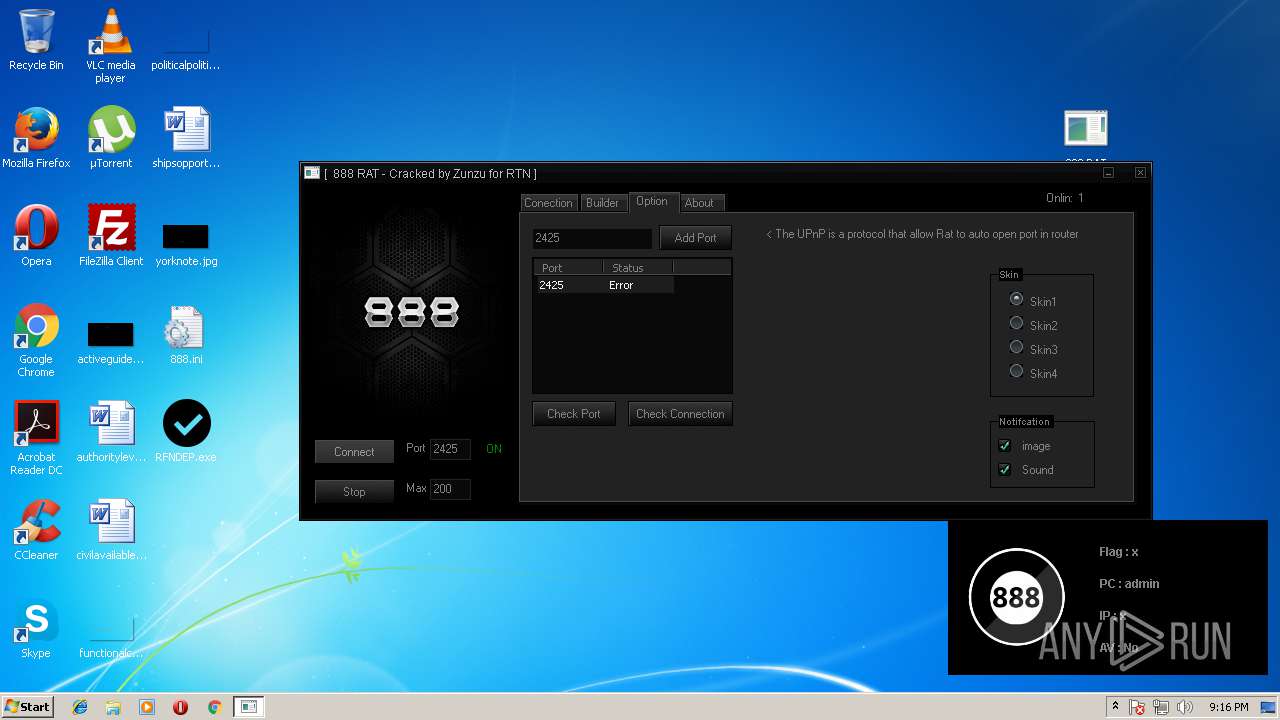
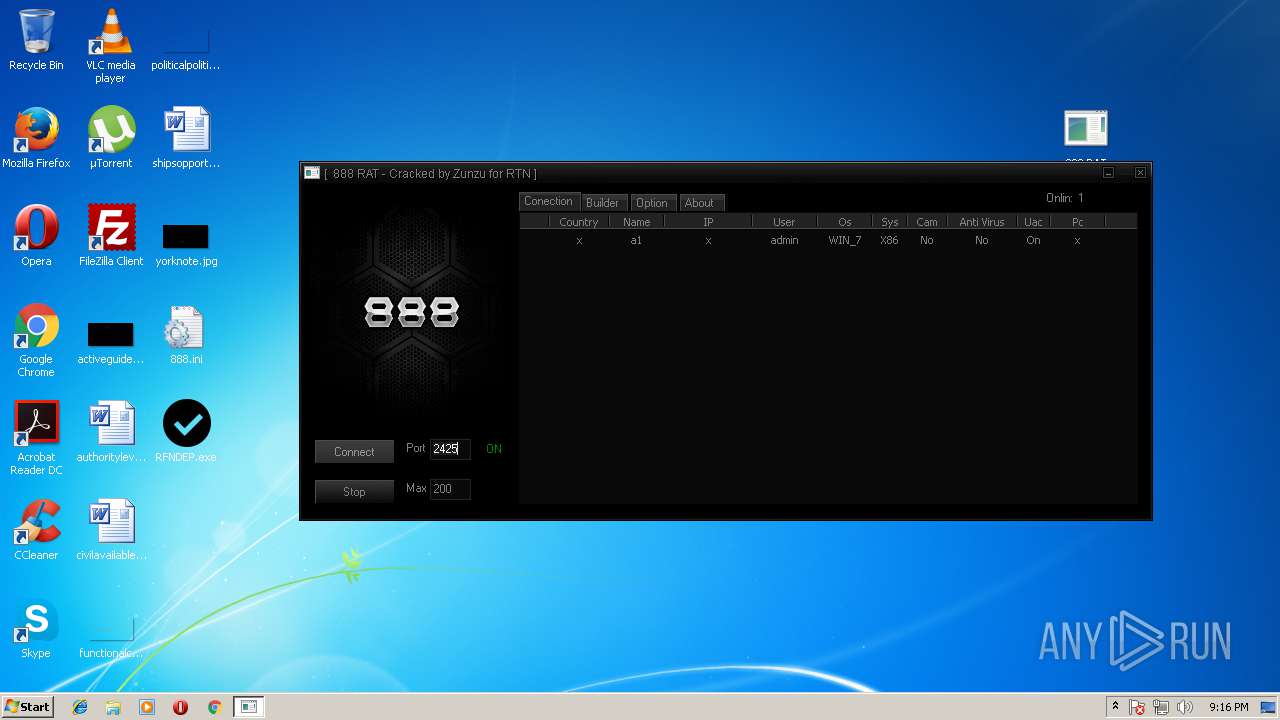
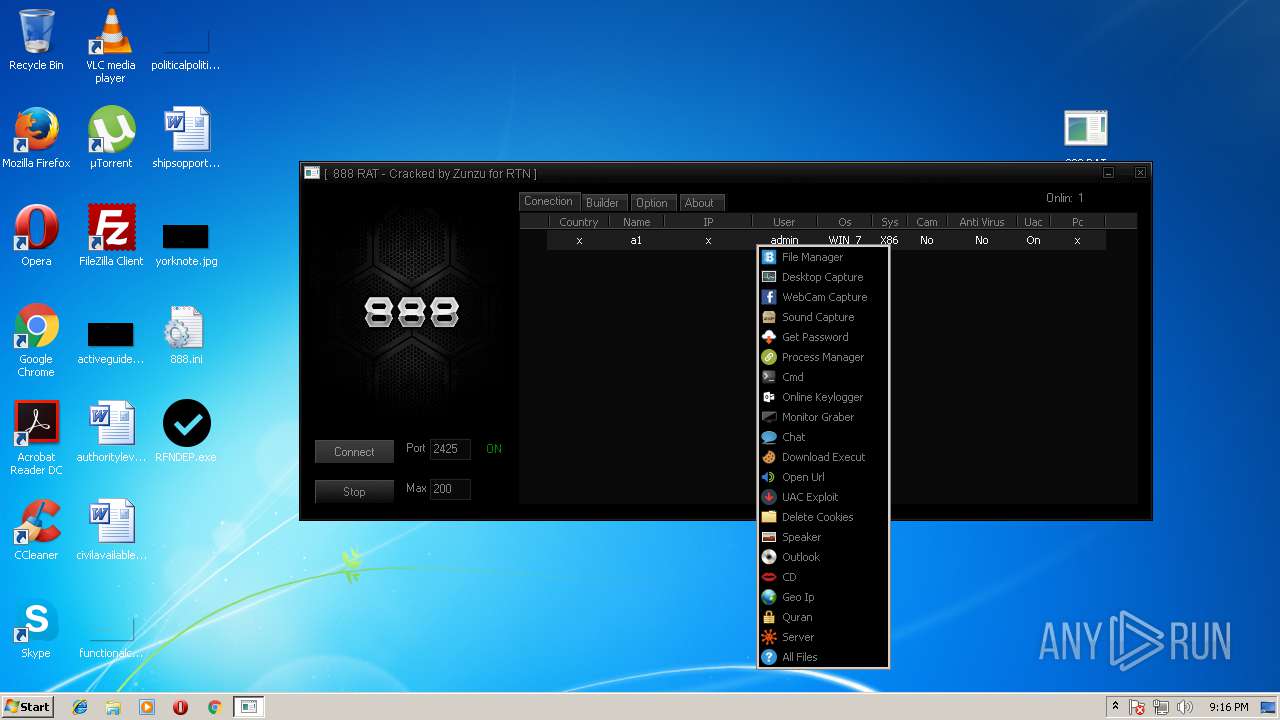
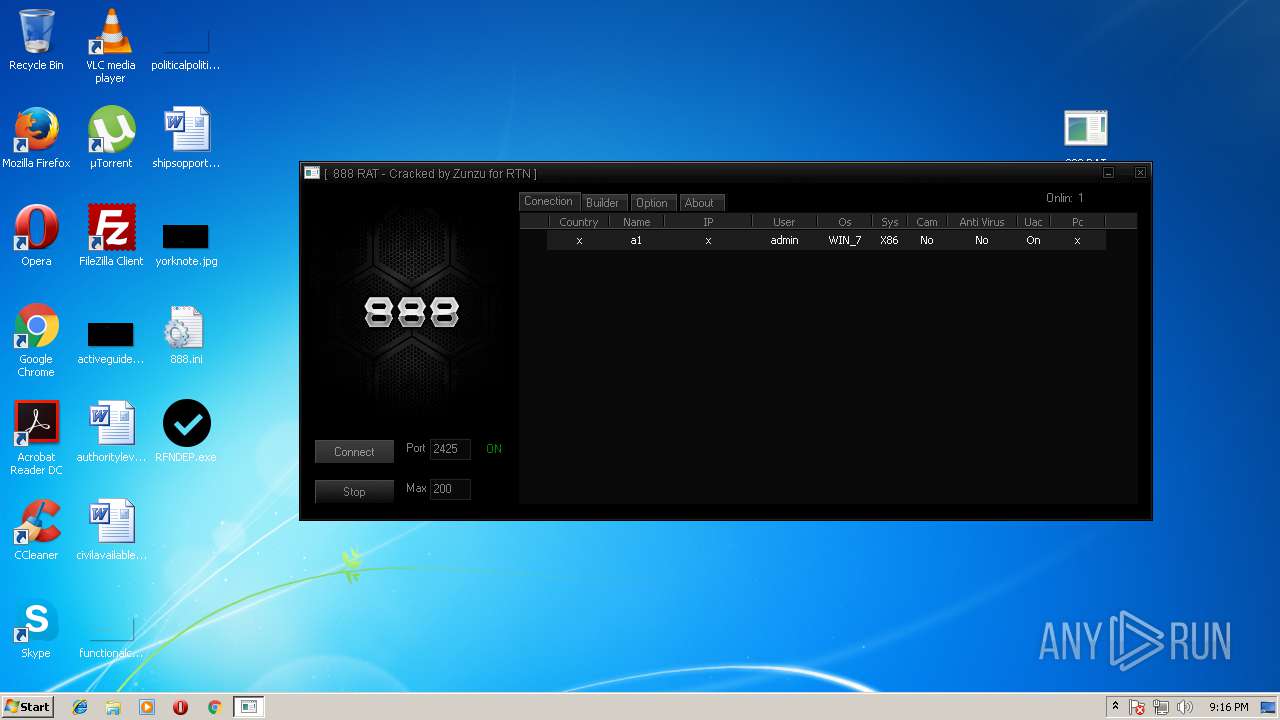
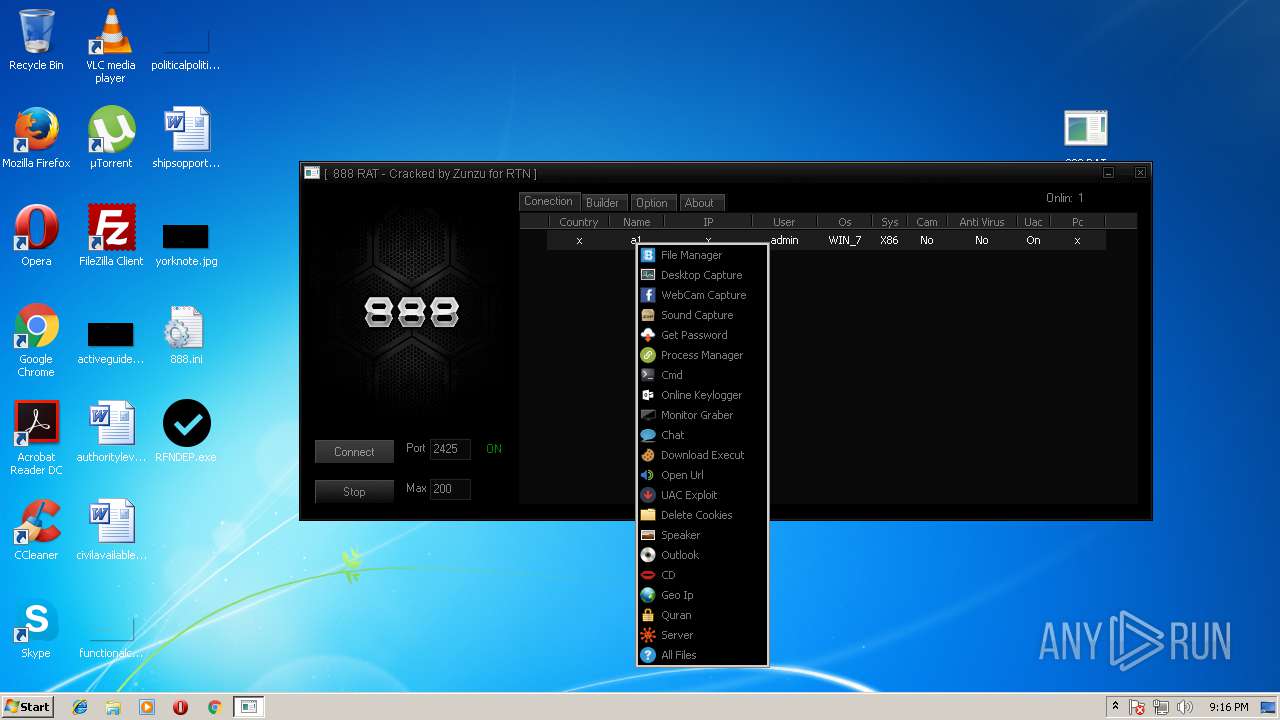
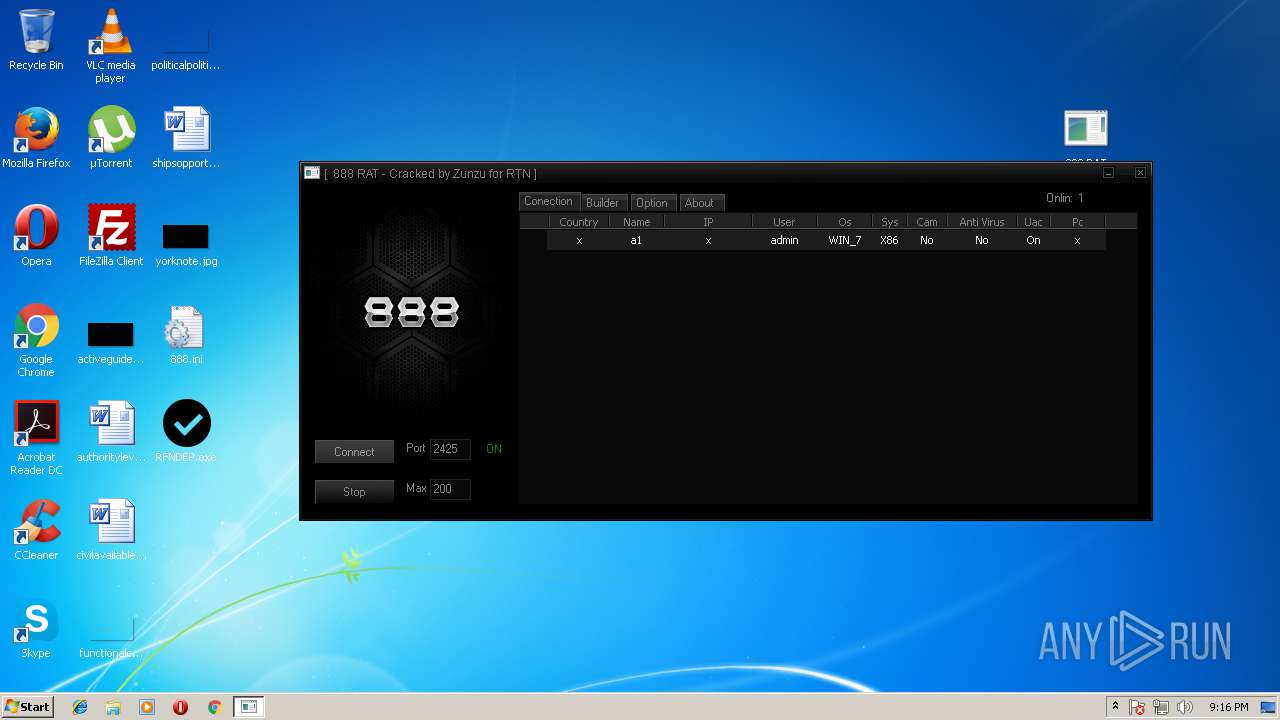
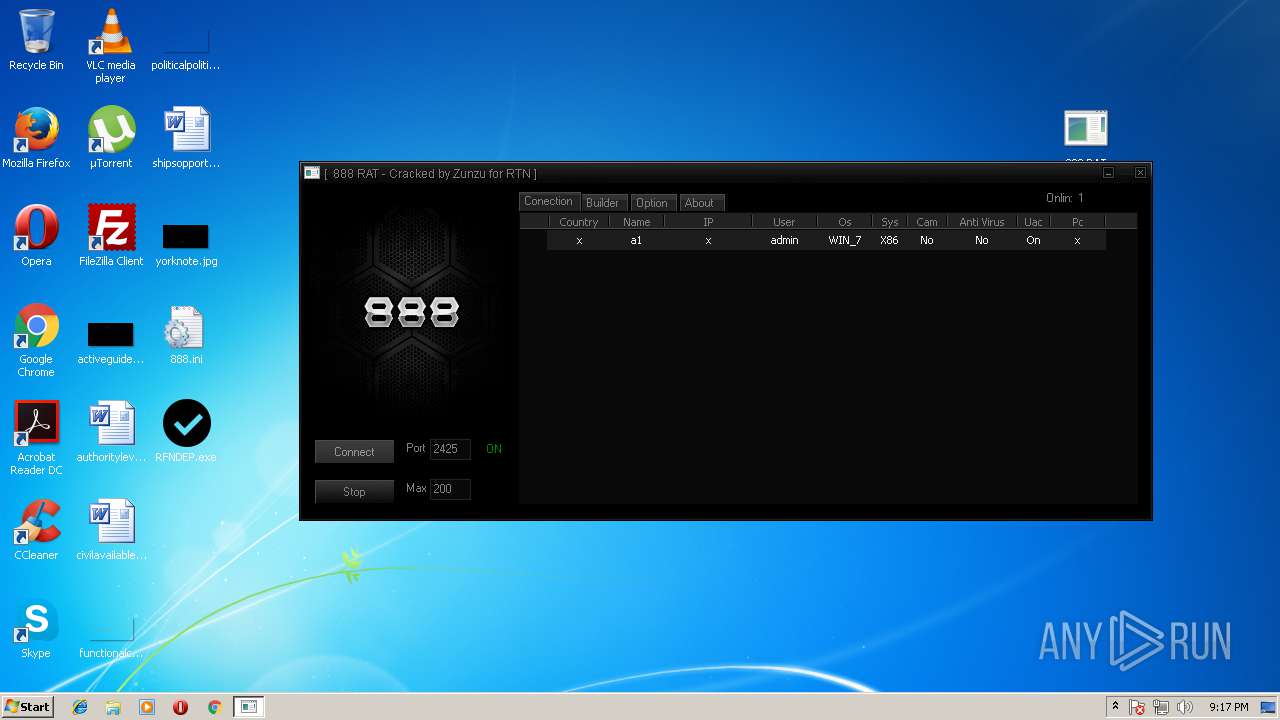
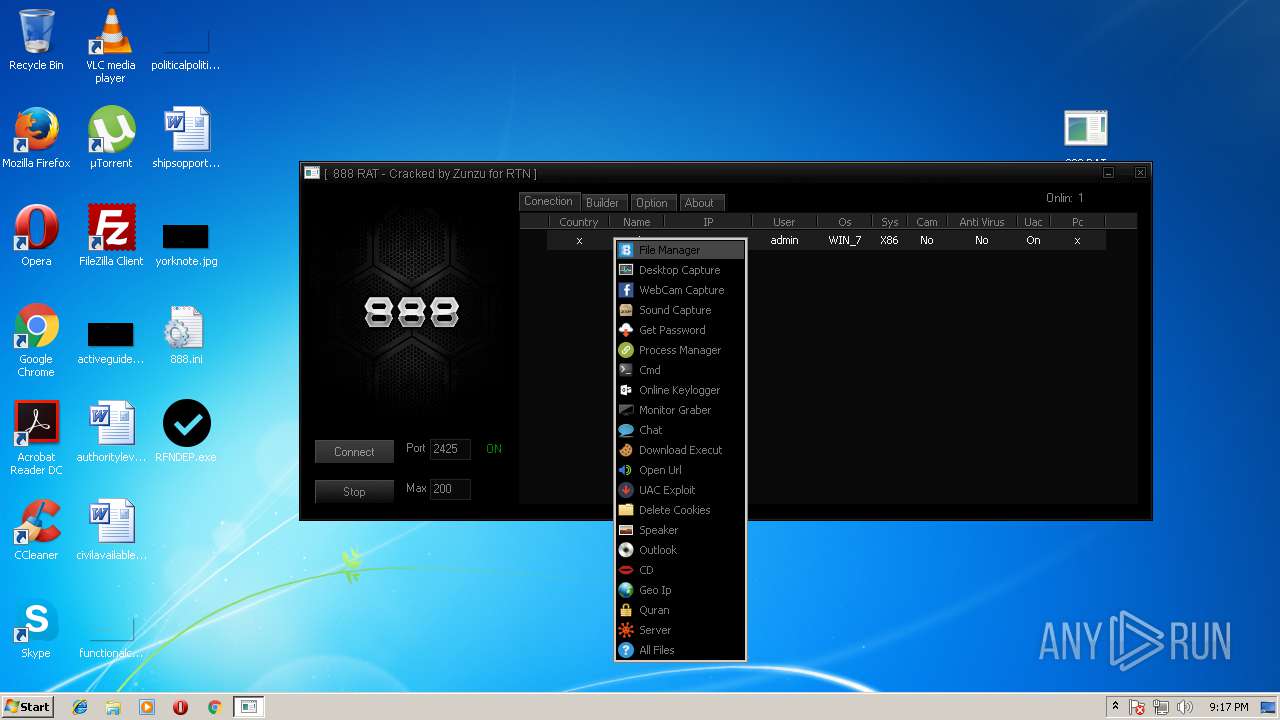
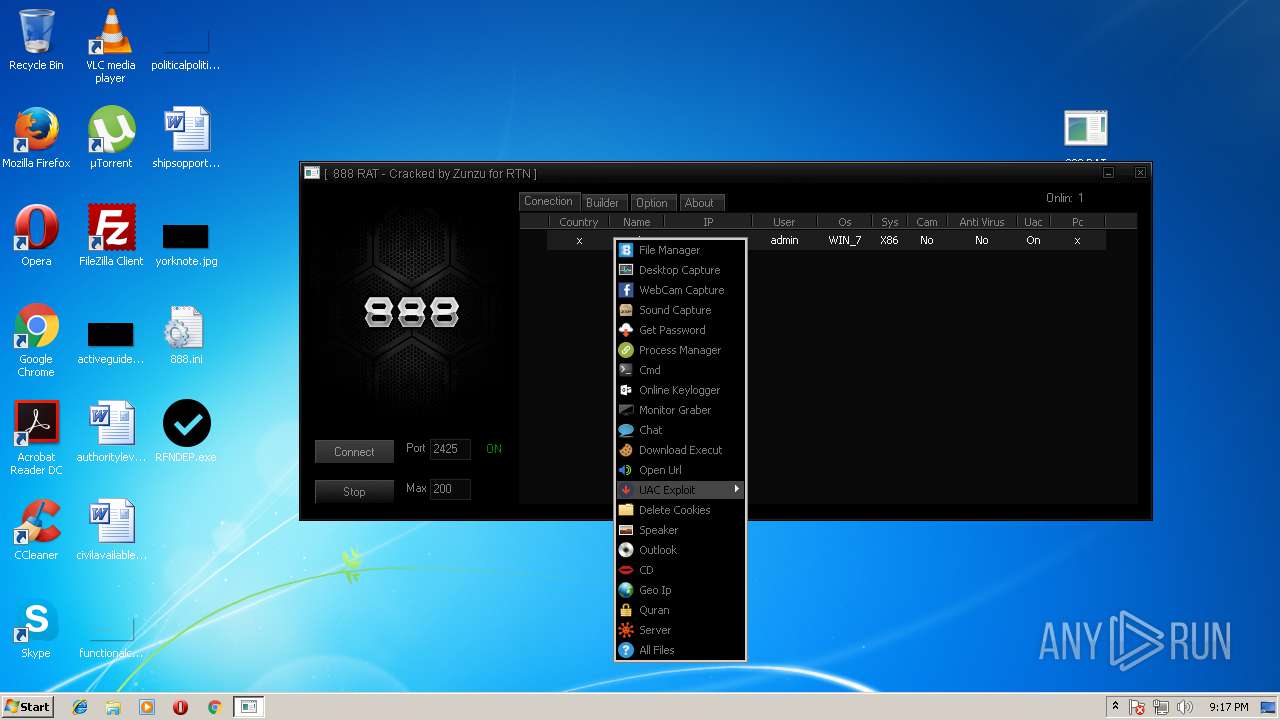
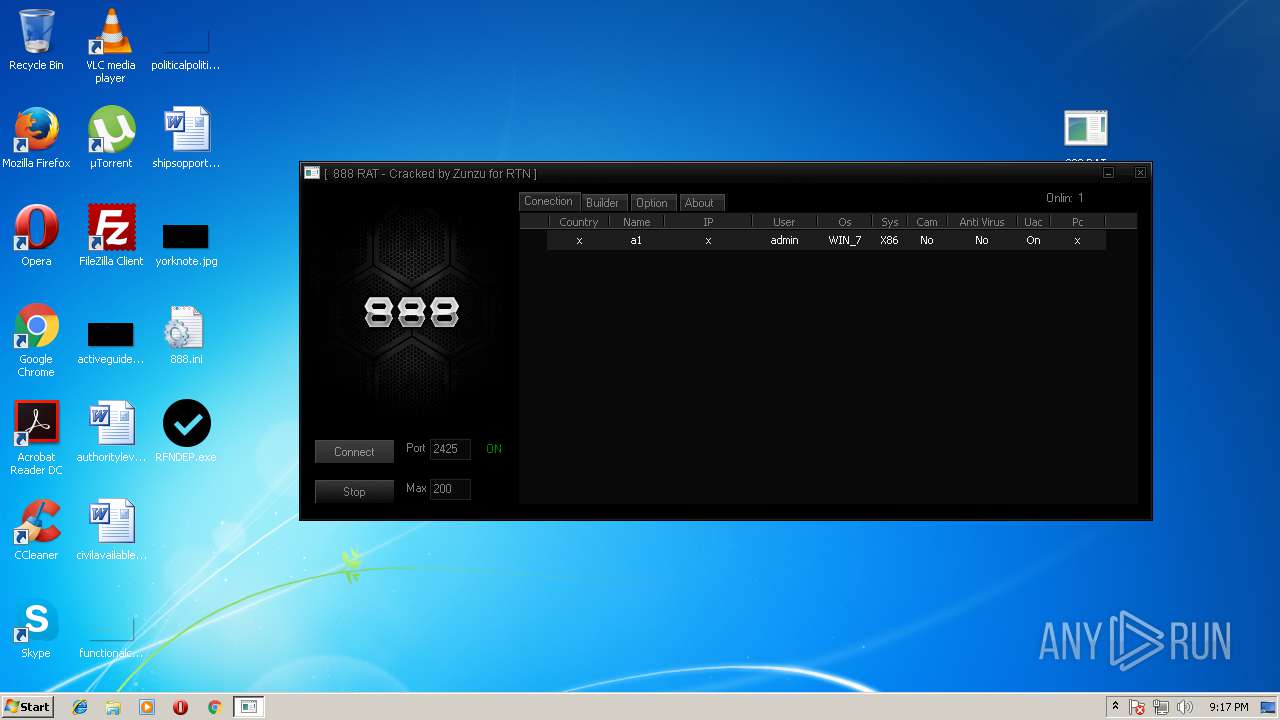
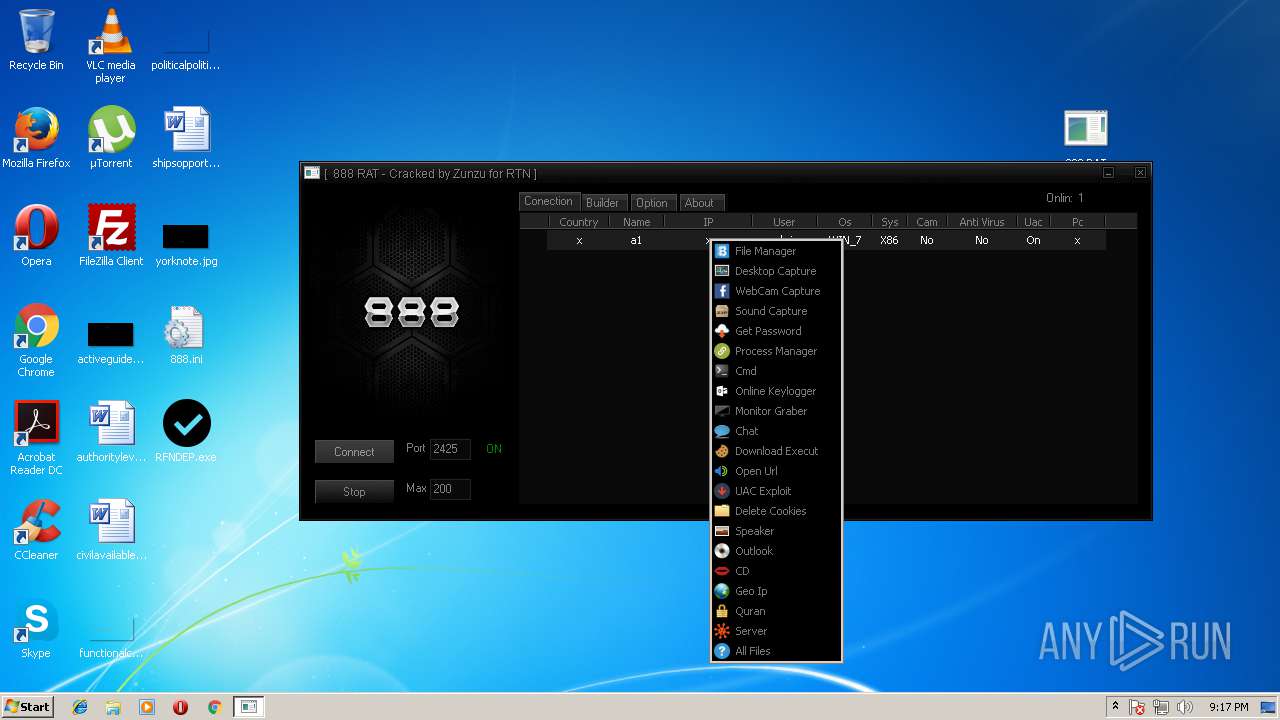
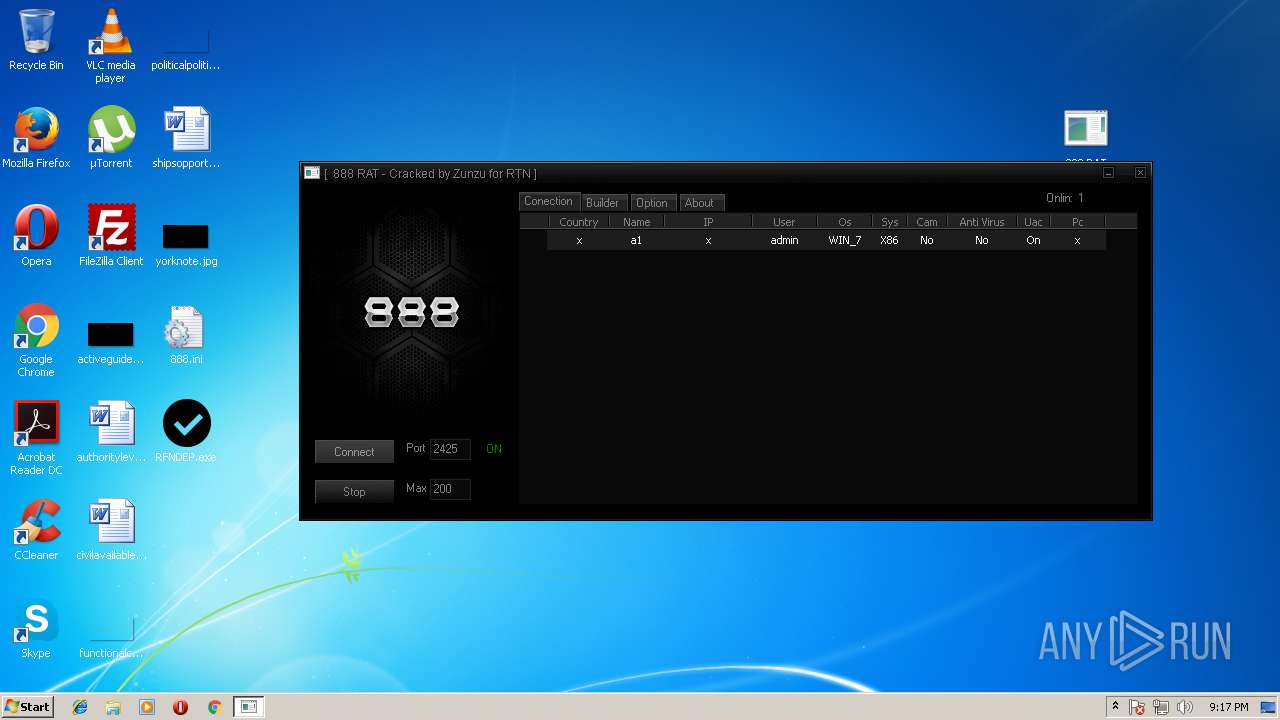
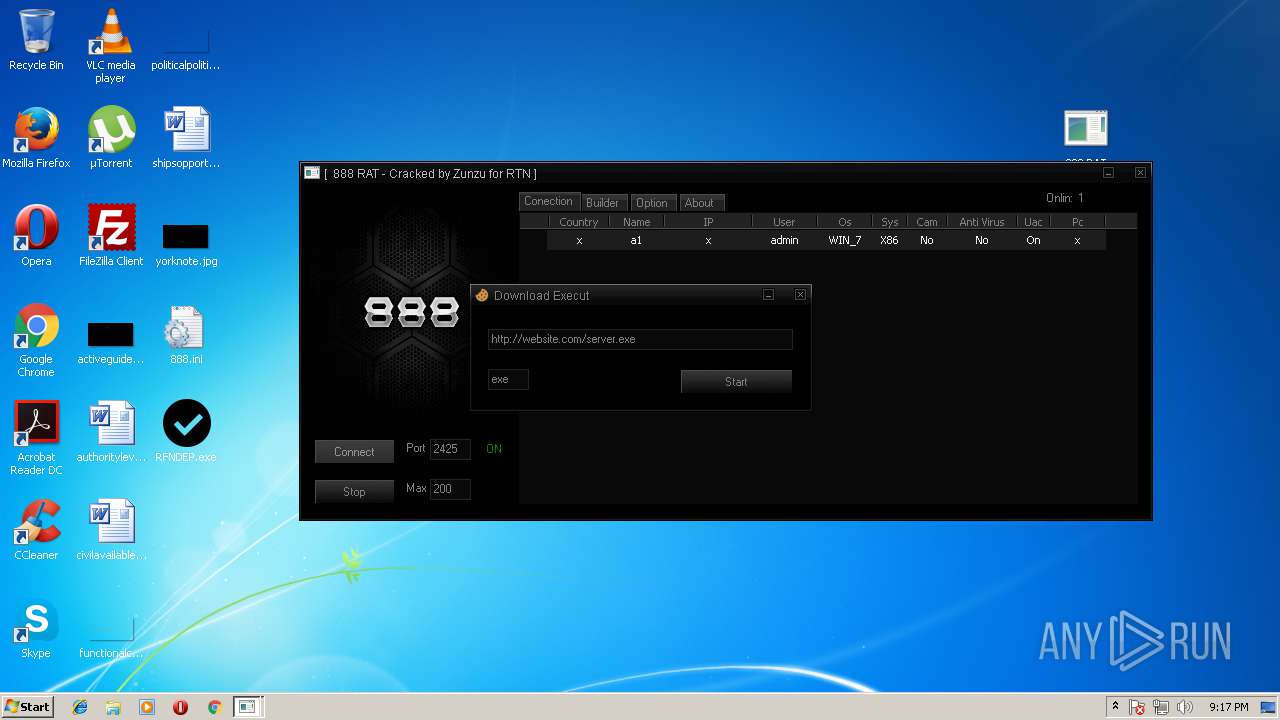
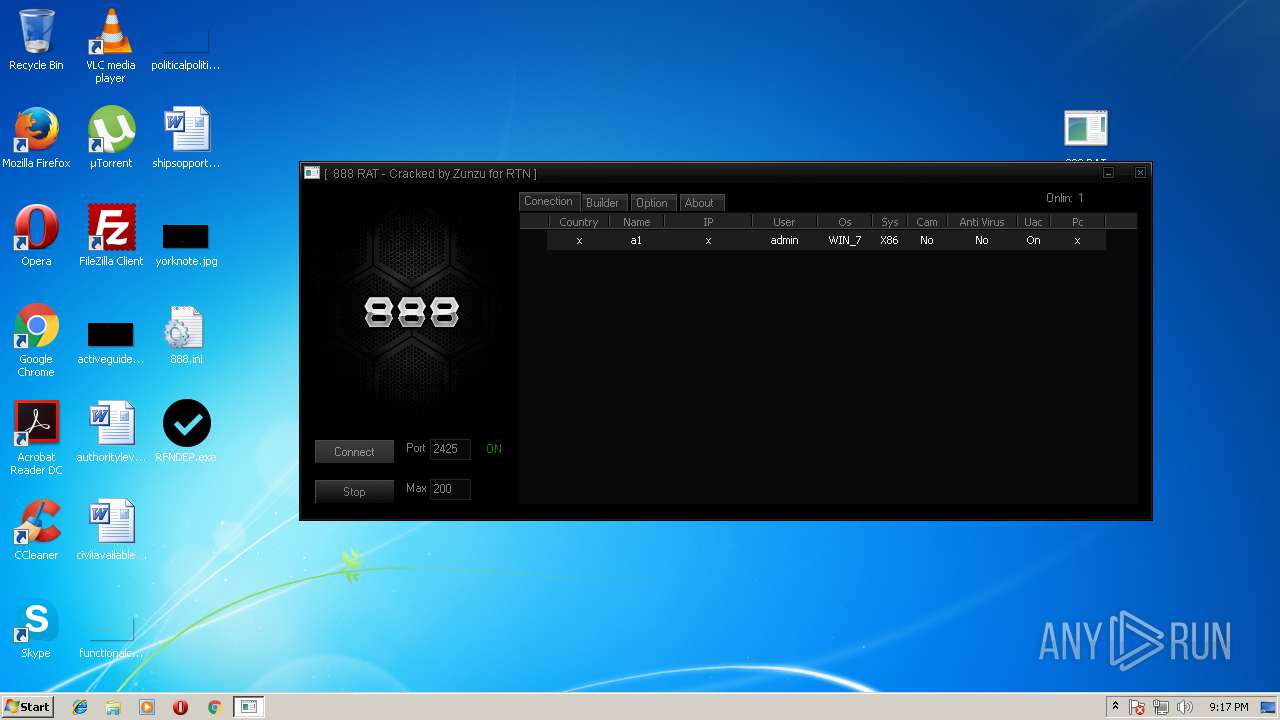
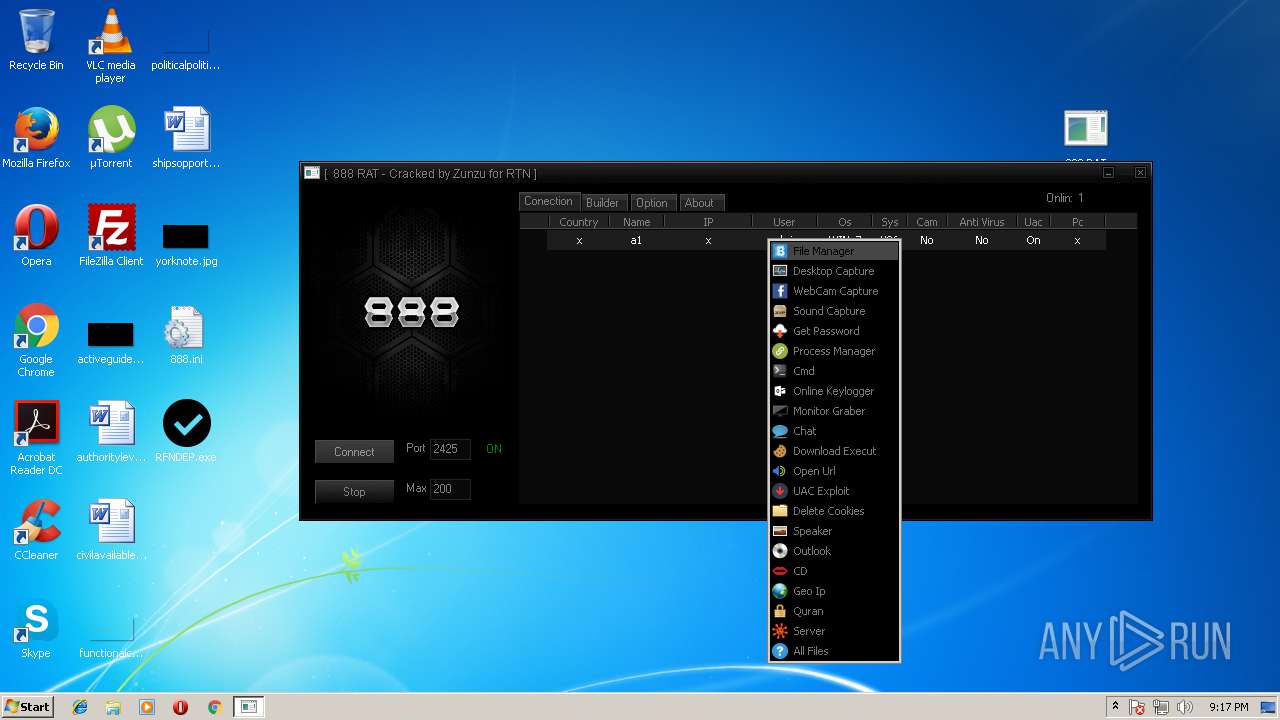
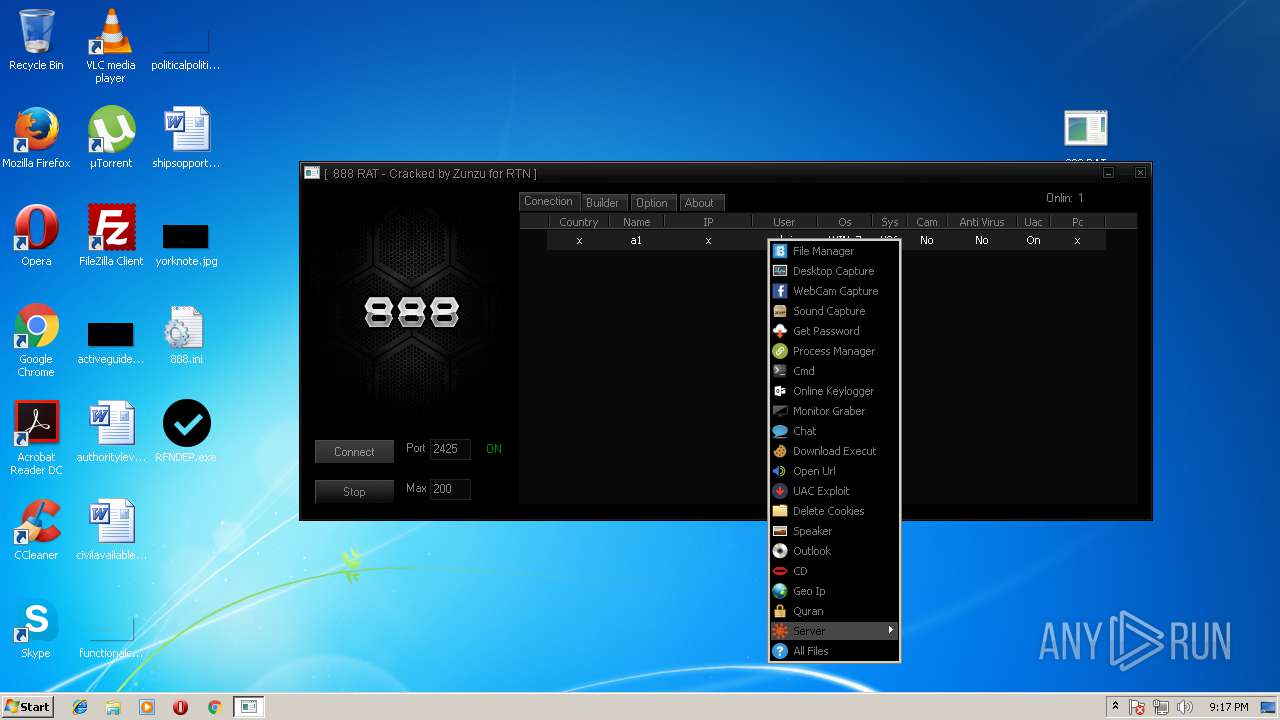
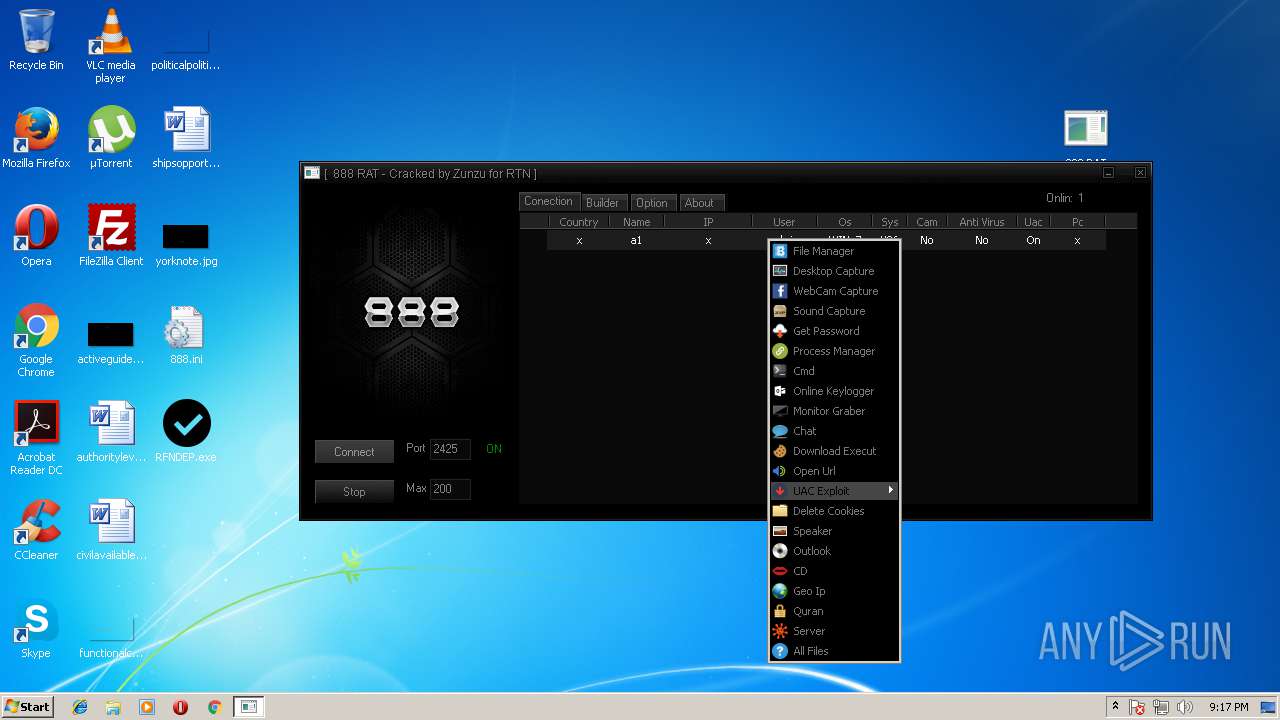
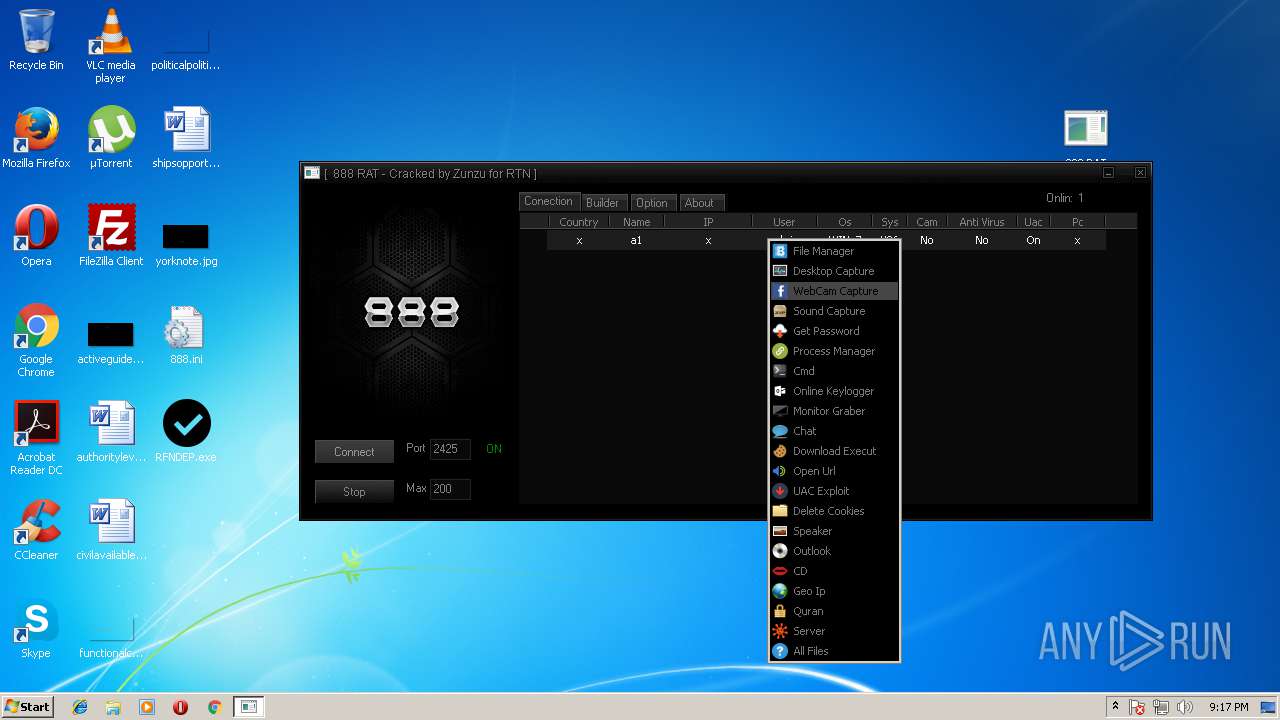
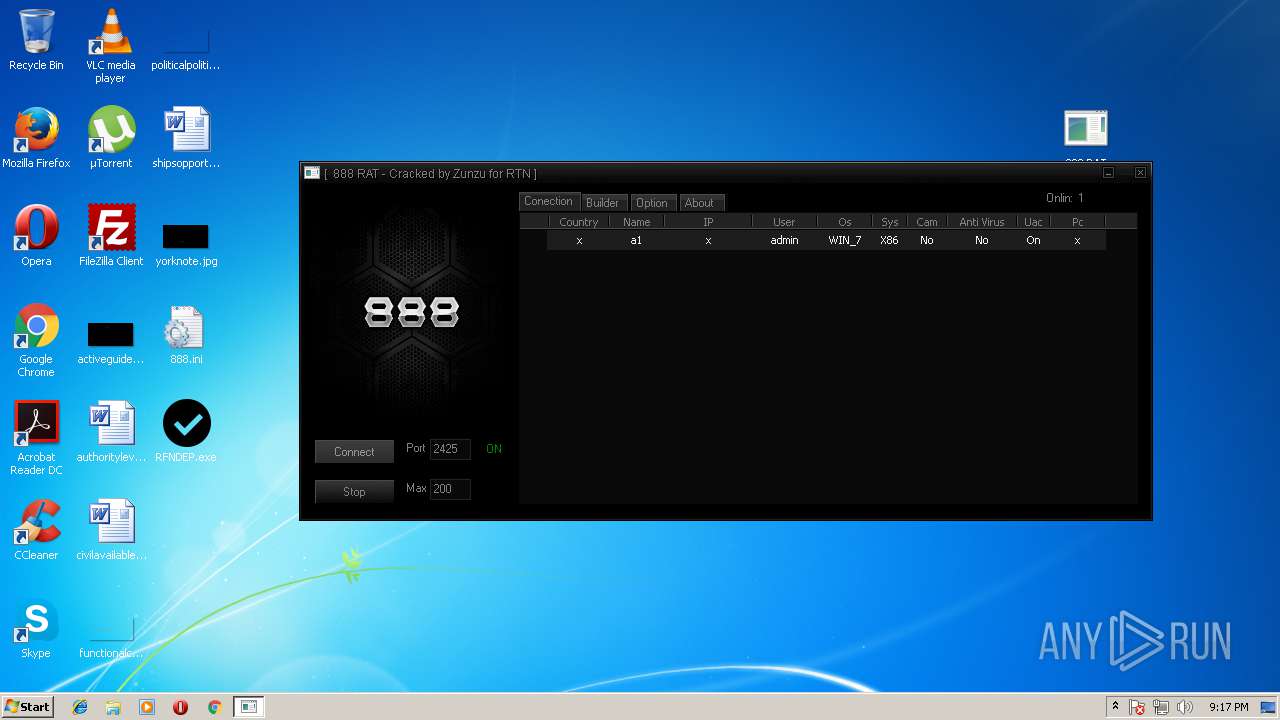
| File name: | 888 rat private - cracked.rar |
| Full analysis: | https://app.any.run/tasks/3f87f9bd-20ac-453d-b804-deef0680ee4a |
| Verdict: | Malicious activity |
| Analysis date: | July 06, 2018, 20:12:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | B2B5165B14BBD5FF613FC41C5378662F |
| SHA1: | 69A1F13F316AFF35CBD9F0C7FA1FA880F03C7092 |
| SHA256: | EACEFBA7832A2E27ED5341B8693002821CE7A20DFFE86C169DC05FE18F7024E0 |
| SSDEEP: | 196608:hH+UaisCDdKWoNhX++nNiDDTGwWxG3HlzXeQOjAZvCvo:h+u7IWoNhu0gyM3HlzXreAvCvo |
MALICIOUS
Application was dropped or rewritten from another process
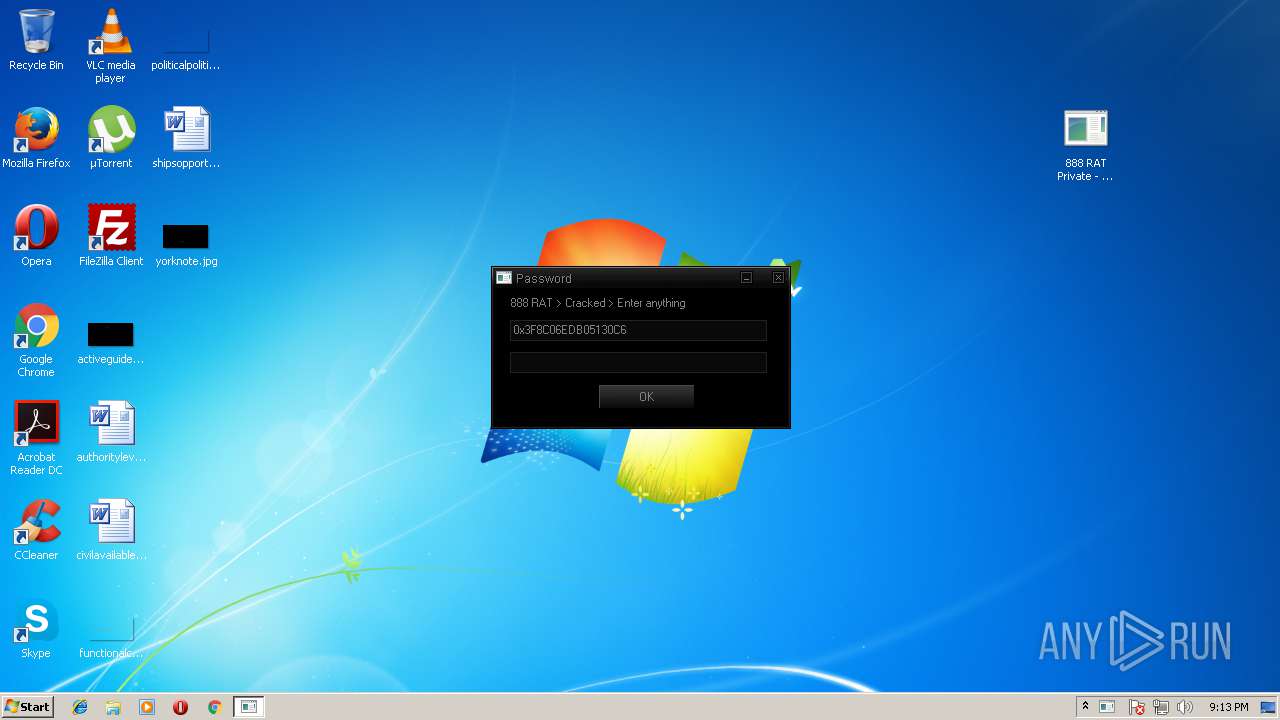
- 888 RAT Private - Cracked.exe (PID: 2572)
- flagx.exe (PID: 2992)
- Obfuscator.exe (PID: 3976)
- upx.exe (PID: 2716)
- Aut2exe.exe (PID: 2148)
- RFNDEP.exe (PID: 2304)
- 1.exe (PID: 788)
- RFNDEP.exe (PID: 2408)
Loads dropped or rewritten executable
- 888 RAT Private - Cracked.exe (PID: 2572)
Writes to a start menu file
- RFNDEP.exe (PID: 2304)
Runs app for hidden code execution
- RFNDEP.exe (PID: 2304)
SUSPICIOUS
Executable content was dropped or overwritten
- 888 RAT Private - Cracked.exe (PID: 2572)
- upx.exe (PID: 2716)
- Aut2exe.exe (PID: 2148)
- RFNDEP.exe (PID: 2304)
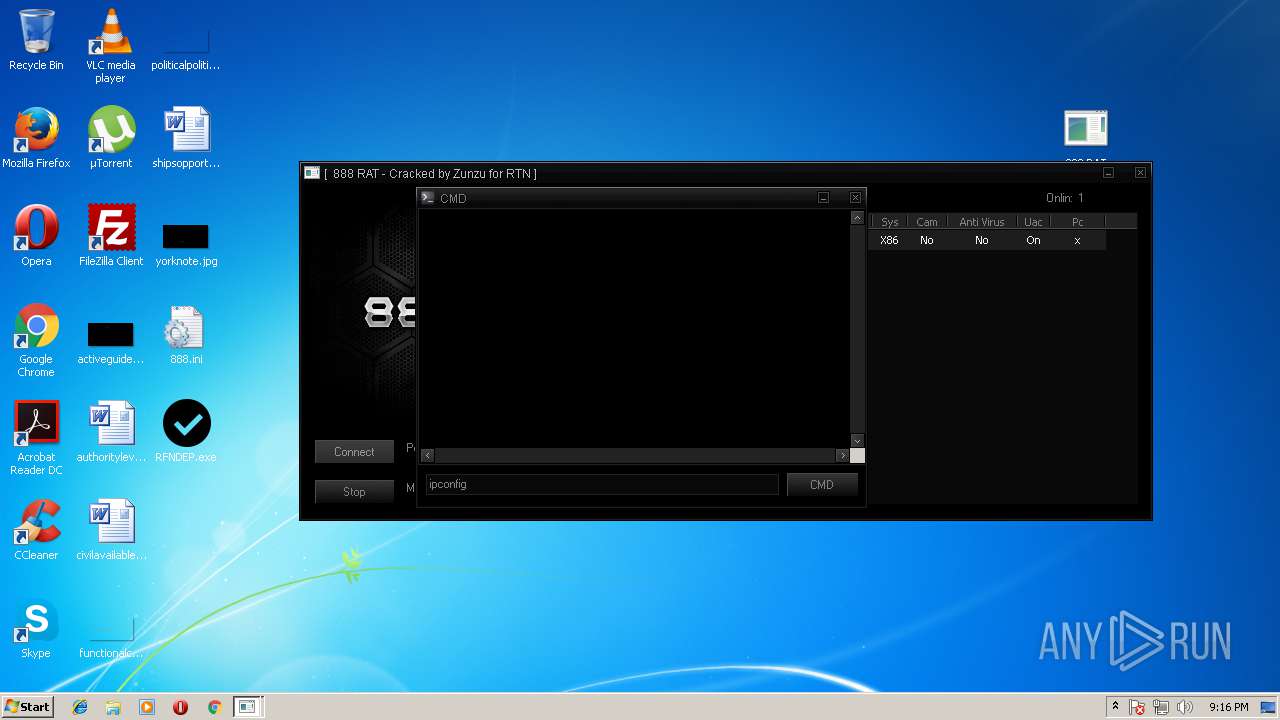
Starts CMD.EXE for commands execution
- 888 RAT Private - Cracked.exe (PID: 2572)
- RFNDEP.exe (PID: 2304)
Starts Internet Explorer
- 888 RAT Private - Cracked.exe (PID: 2572)
Application launched itself
- RFNDEP.exe (PID: 2304)
Reads Internet Cache Settings
- rundll32.exe (PID: 2240)
- rundll32.exe (PID: 588)
Checks for external IP
- RFNDEP.exe (PID: 2304)
Creates files in the user directory
- RFNDEP.exe (PID: 2304)
INFO
Dropped object may contain URL's
- Obfuscator.exe (PID: 3976)
- 888 RAT Private - Cracked.exe (PID: 2572)
- iexplore.exe (PID: 3564)
Application launched itself
- iexplore.exe (PID: 3924)
Creates files in the user directory
- iexplore.exe (PID: 3564)
Reads Internet Cache Settings
- iexplore.exe (PID: 3564)
- iexplore.exe (PID: 3056)
Changes internet zones settings
- iexplore.exe (PID: 3924)
- iexplore.exe (PID: 3492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 6899998 |
|---|---|
| UncompressedSize: | 7395840 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2016:12:23 13:10:27 |
| PackingMethod: | Normal |
| ArchivedFileName: | 888 RAT Private - Cracked.exe |
Total processes
62
Monitored processes
19
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | "C:\Program Files\7-Zip\7zFM.exe" "C:\Users\admin\AppData\Local\Temp\888 rat private - cracked.rar" | C:\Program Files\7-Zip\7zFM.exe | — | explorer.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip File Manager Exit code: 0 Version: 16.04 Modules
| |||||||||||||||
| 588 | "C:\Windows\system32\rundll32.exe" "C:\Windows\system32\WININET.dll",DispatchAPICall 1 | C:\Windows\system32\rundll32.exe | — | RFNDEP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
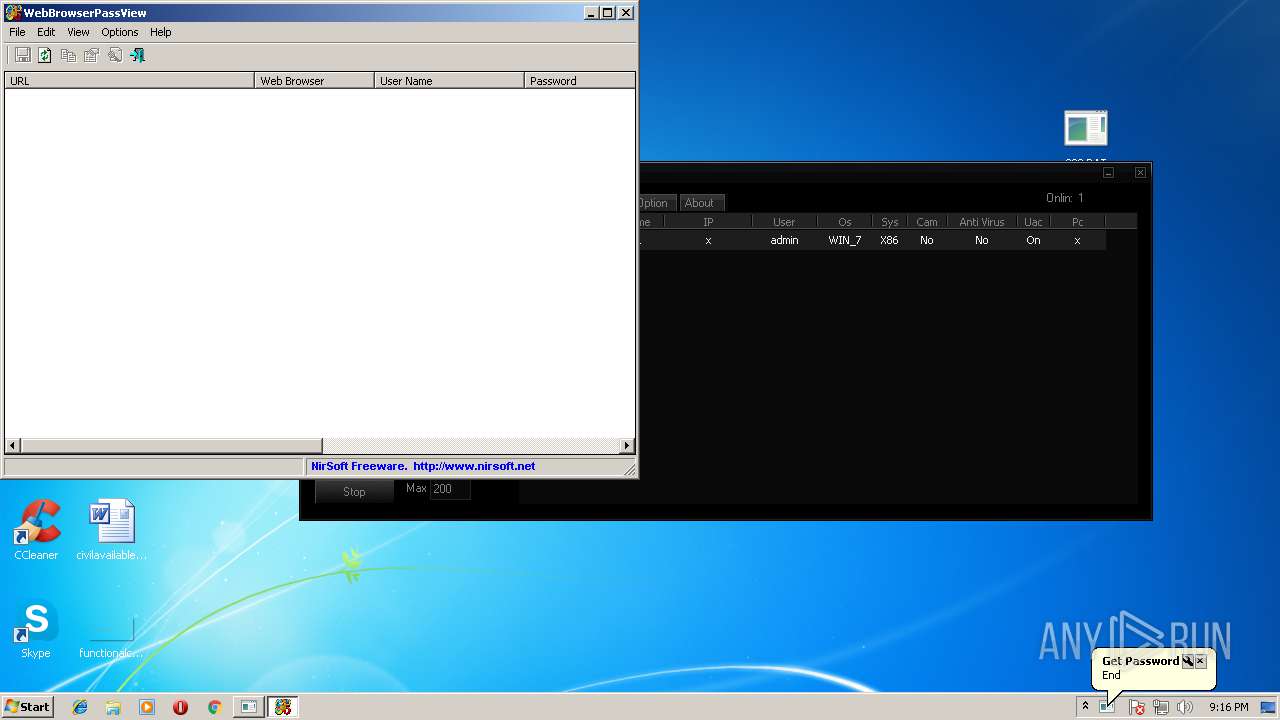
| 788 | 1.exe /LoadPasswordsIE 0 /LoadPasswordsOpera 0 /LoadPasswordsFirefox 1 /LoadPasswordsChrome 1 /LoadPasswordsSafari 0 /UseChromeProfileFolder 1 /ChromeProfileFolder "C:\Users\admin\AppData\Local\Temp\Pass\DD" /UseFirefoxProfileFolder 1 /FirefoxProfileFolder "C:\Users\admin\AppData\Local\Temp\Pass\DD" | C:\Users\admin\AppData\Local\Temp\1.exe | — | cmd.exe | |||||||||||
User: admin Company: NirSoft Integrity Level: MEDIUM Description: WebBrowserPassView Exit code: 0 Version: 1.70 Modules
| |||||||||||||||
| 1132 | C:\Windows\system32\cmd.exe | C:\Windows\system32\cmd.exe | — | RFNDEP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1828 | ipconfig | C:\Windows\system32\ipconfig.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2148 | C:\Users\admin\AppData\Local\Temp\Aut2exe.exe /in C:\Users\admin\AppData\Local\Temp/Server.au3 /out C:\Users\admin\AppData\Local\Temp/RFNDEP.exe /icon C:\Users\admin\AppData\Local\Temp\ssc.ico /comp 2 /pack /Unicode | C:\Users\admin\AppData\Local\Temp\Aut2exe.exe | 888 RAT Private - Cracked.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: Aut2Exe Exit code: 0 Version: 3, 3, 8, 1 Modules
| |||||||||||||||
| 2240 | "C:\Windows\system32\rundll32.exe" "C:\Windows\system32\WININET.dll",DispatchAPICall 1 | C:\Windows\system32\rundll32.exe | — | RFNDEP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2304 | "C:\Users\admin\Desktop\RFNDEP.exe" | C:\Users\admin\Desktop\RFNDEP.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 3, 3, 8, 1 Modules
| |||||||||||||||
| 2408 | "C:\Users\admin\Desktop\RFNDEP.exe" | C:\Users\admin\Desktop\RFNDEP.exe | — | RFNDEP.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 3, 3, 8, 1 | |||||||||||||||
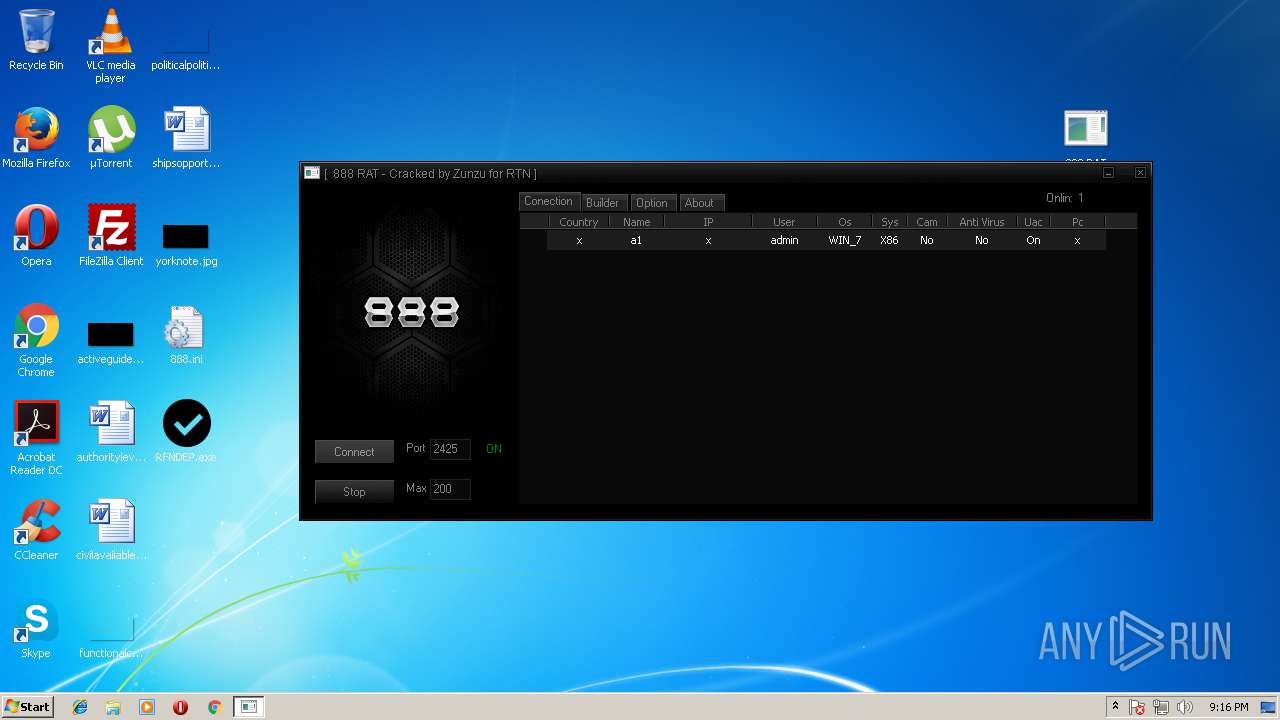
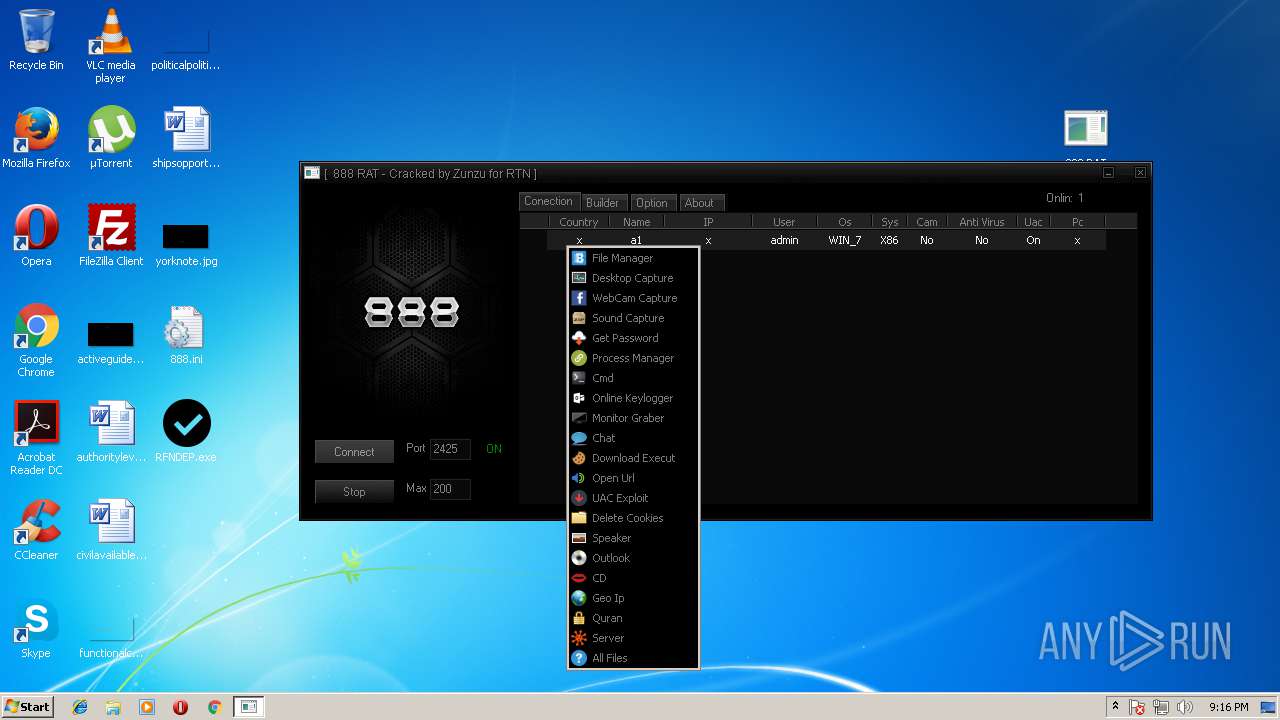
| 2572 | "C:\Users\admin\Desktop\888 RAT Private - Cracked.exe" | C:\Users\admin\Desktop\888 RAT Private - Cracked.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 635
Read events
1 527
Write events
106
Delete events
2
Modification events
| (PID) Process: | (292) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FolderShortcuts |
Value: | |||
| (PID) Process: | (292) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FolderHistory |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C0038003800380020007200610074002000700072006900760061007400650020002D00200063007200610063006B00650064002E007200610072005C000000 | |||
| (PID) Process: | (292) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | PanelPath0 |
Value: C:\Users\admin\AppData\Local\Temp\ | |||
| (PID) Process: | (292) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FlatViewArc0 |
Value: 0 | |||
| (PID) Process: | (292) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | PanelPath1 |
Value: | |||
| (PID) Process: | (292) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FlatViewArc1 |
Value: 0 | |||
| (PID) Process: | (292) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | ListMode |
Value: 771 | |||
| (PID) Process: | (292) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | Position |
Value: 1600000016000000D60300000B02000000000000 | |||
| (PID) Process: | (292) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | Panels |
Value: 0100000000000000DA010000 | |||
| (PID) Process: | (292) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM\Columns |
| Operation: | write | Name: | 7-Zip.Rar |
Value: 0100000004000000010000000400000001000000A00000000700000001000000640000000800000001000000640000000C00000001000000640000000A00000001000000640000000B00000001000000640000000900000001000000640000000F00000001000000640000000D00000001000000640000000E00000001000000640000001000000001000000640000001100000001000000640000001300000001000000640000001700000001000000640000001600000001000000640000002100000001000000640000001F0000000100000064000000200000000100000064000000 | |||
Executable files
20
Suspicious files
11
Text files
480
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 292 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE4215EFAA\888 RAT Private - Cracked.exe | — | |
MD5:— | SHA256:— | |||
| 2572 | 888 RAT Private - Cracked.exe | C:\Users\admin\AppData\Local\Temp\autC4A9.tmp | — | |
MD5:— | SHA256:— | |||
| 2572 | 888 RAT Private - Cracked.exe | C:\Users\admin\AppData\Local\Temp\geykhoj | — | |
MD5:— | SHA256:— | |||
| 2572 | 888 RAT Private - Cracked.exe | C:\Users\admin\AppData\Local\Temp\autC565.tmp | — | |
MD5:— | SHA256:— | |||
| 2572 | 888 RAT Private - Cracked.exe | C:\Users\admin\AppData\Local\Temp\autC586.tmp | — | |
MD5:— | SHA256:— | |||
| 2572 | 888 RAT Private - Cracked.exe | C:\Users\admin\AppData\Local\Temp\autC5C6.tmp | — | |
MD5:— | SHA256:— | |||
| 2572 | 888 RAT Private - Cracked.exe | C:\Users\admin\AppData\Local\Temp\autC5D7.tmp | — | |
MD5:— | SHA256:— | |||
| 2572 | 888 RAT Private - Cracked.exe | C:\Users\admin\AppData\Local\Temp\autD9CD.tmp | — | |
MD5:— | SHA256:— | |||
| 2572 | 888 RAT Private - Cracked.exe | C:\Users\admin\AppData\Local\Temp\autD9DE.tmp | — | |
MD5:— | SHA256:— | |||
| 2572 | 888 RAT Private - Cracked.exe | C:\Users\admin\AppData\Local\Temp\autD9DF.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
8
DNS requests
6
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
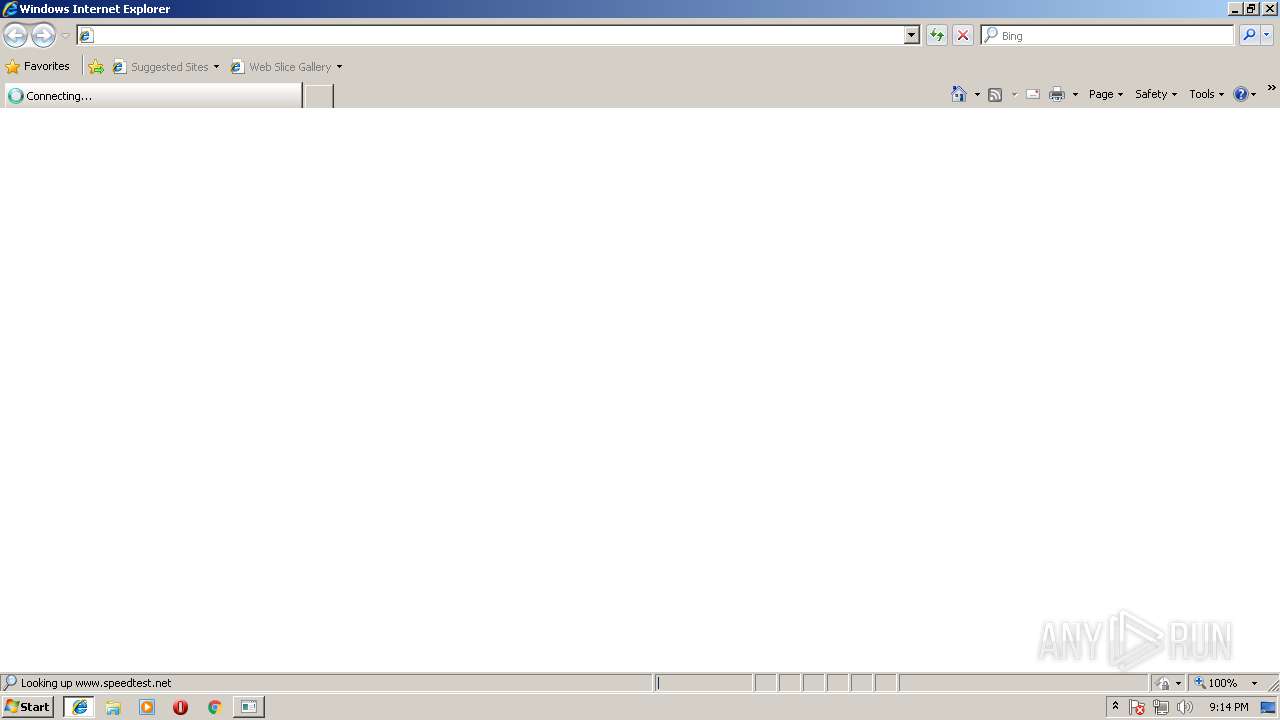
3564 | iexplore.exe | GET | 302 | 151.101.194.219:80 | http://www.speedtest.net/ | US | text | 50 b | whitelisted |
2304 | RFNDEP.exe | GET | — | 95.211.125.236:80 | http://ip-score.com/checkip/ | NL | — | — | shared |
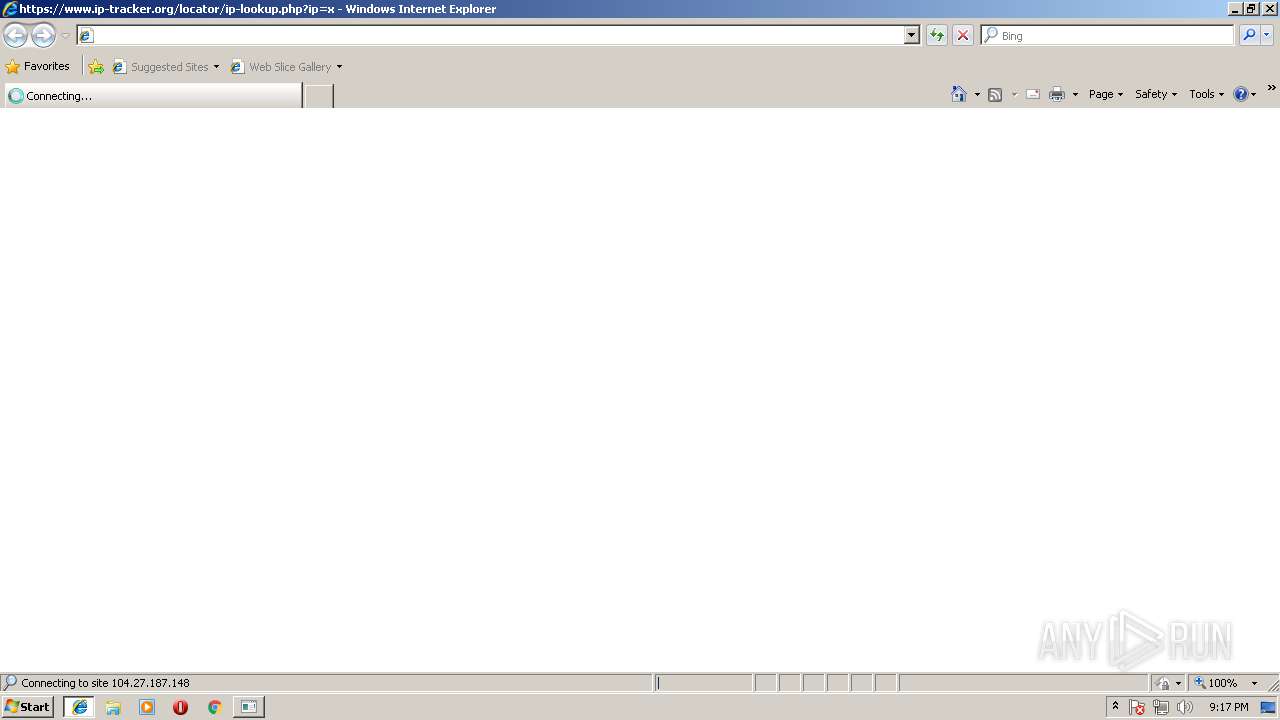
3056 | iexplore.exe | GET | 301 | 104.27.187.148:80 | http://www.ip-tracker.org/locator/ip-lookup.php?ip=x | US | — | — | suspicious |
3924 | iexplore.exe | GET | 200 | 13.107.21.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
3492 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
2304 | RFNDEP.exe | GET | — | 95.211.125.236:80 | http://ip-score.com/checkip/ | NL | — | — | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3924 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3564 | iexplore.exe | 151.101.194.219:80 | www.speedtest.net | Fastly | US | suspicious |
3564 | iexplore.exe | 151.101.2.219:80 | www.speedtest.net | Fastly | US | suspicious |
2304 | RFNDEP.exe | 95.211.125.236:80 | ip-score.com | LeaseWeb Netherlands B.V. | NL | malicious |
3492 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3056 | iexplore.exe | 104.27.187.148:80 | www.ip-tracker.org | Cloudflare Inc | US | shared |
3056 | iexplore.exe | 104.27.187.148:443 | www.ip-tracker.org | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
www.speedtest.net |
| whitelisted |
legacy.speedtest.net |
| whitelisted |
ip-score.com |
| shared |
www.ip-tracker.org |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2304 | RFNDEP.exe | Potential Corporate Privacy Violation | ET POLICY Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
2304 | RFNDEP.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-score.com |
2304 | RFNDEP.exe | Potential Corporate Privacy Violation | ET POLICY Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
2304 | RFNDEP.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-score.com |