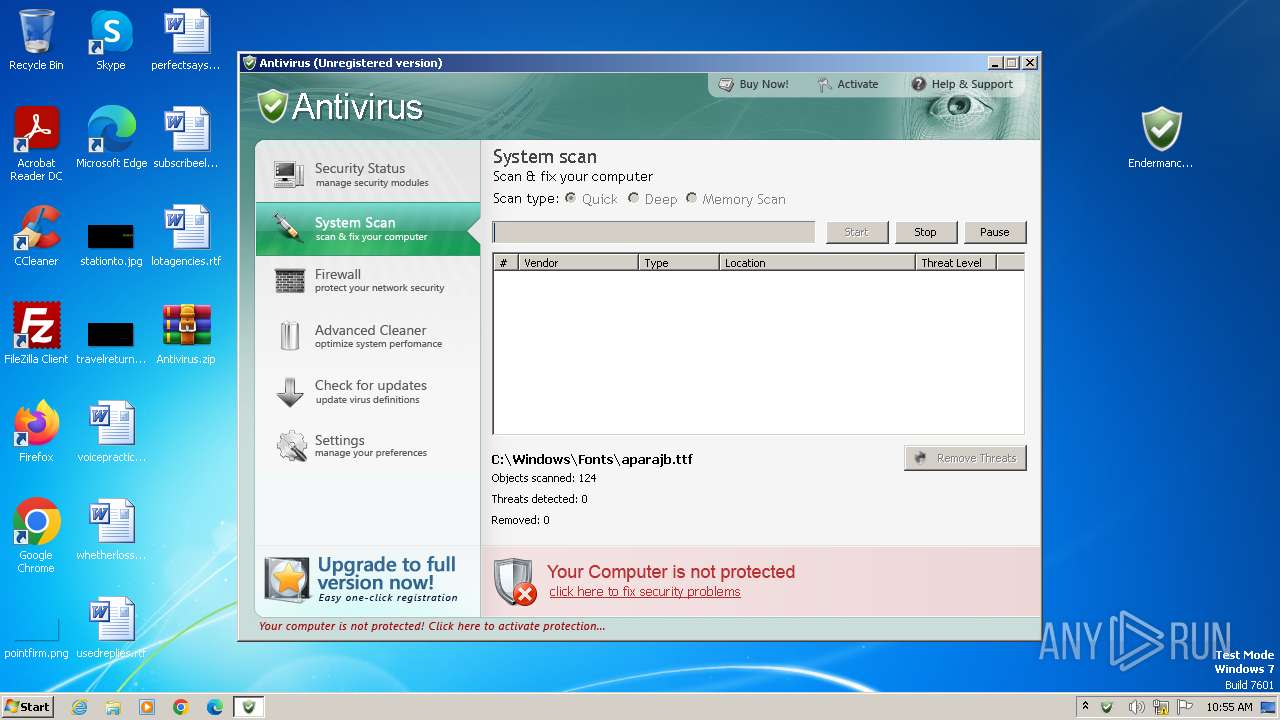
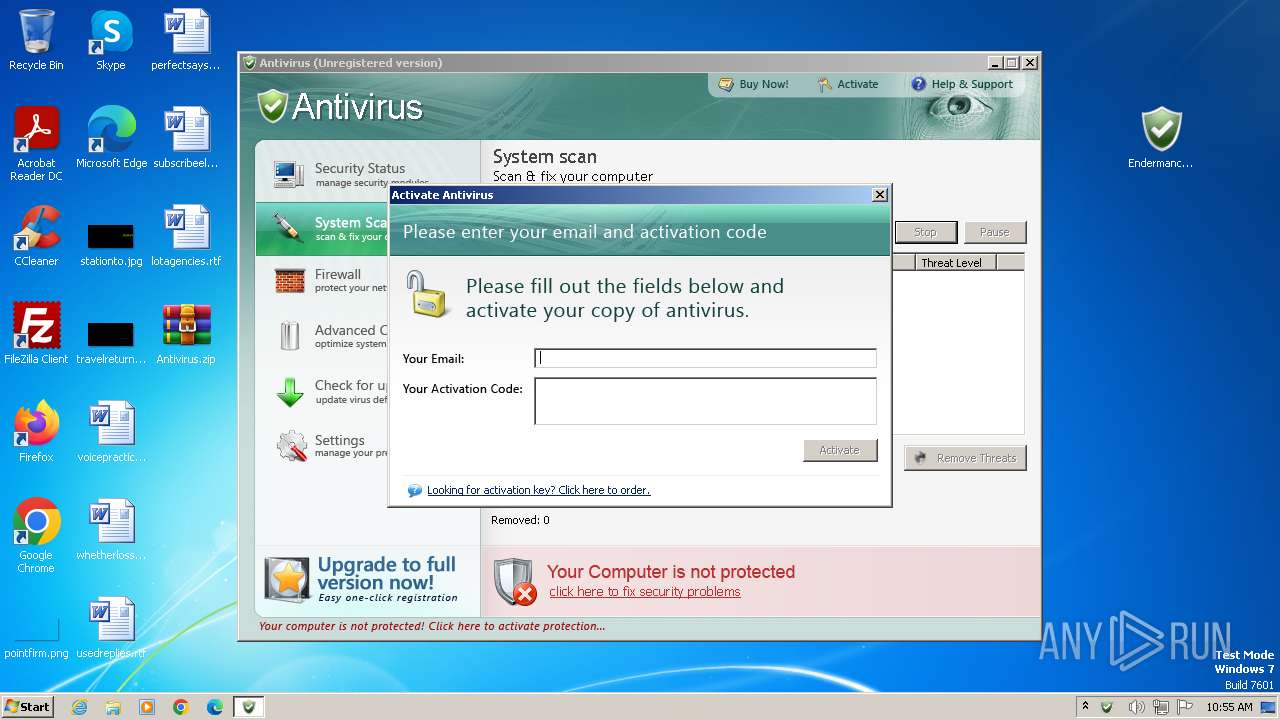
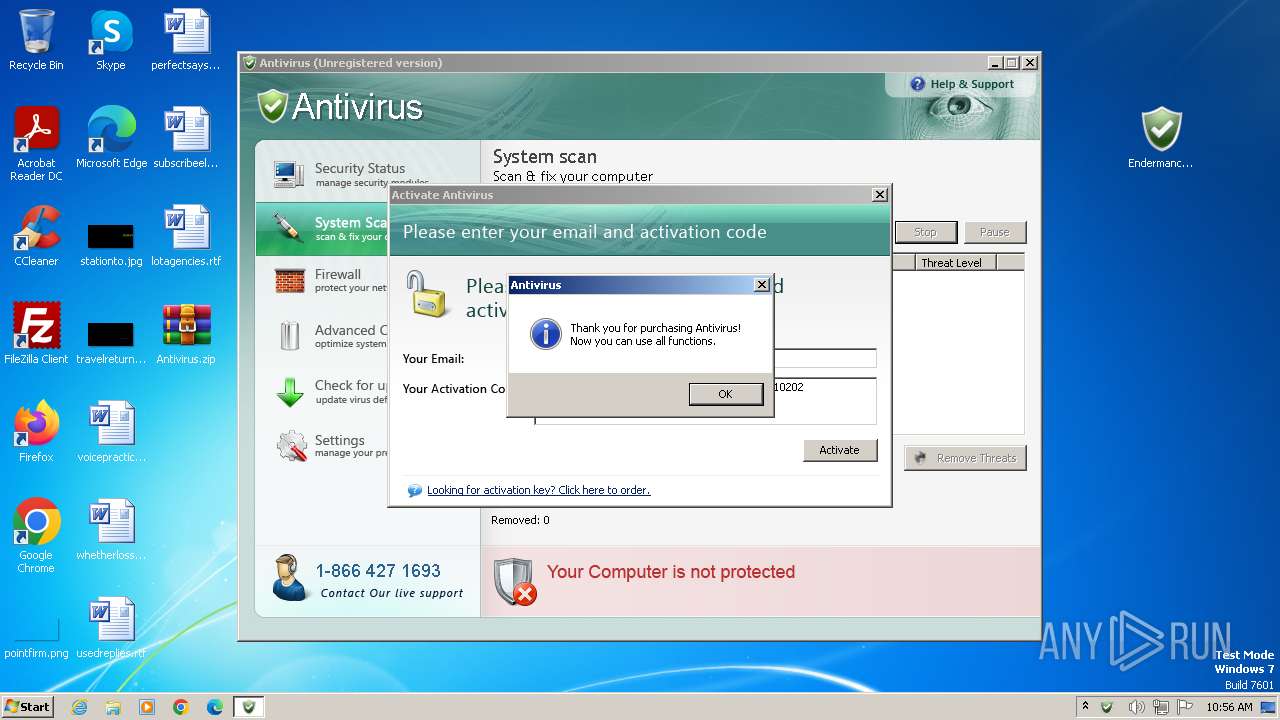
| File name: | Antivirus.zip |
| Full analysis: | https://app.any.run/tasks/8a1268c4-fe93-4cd8-98f8-a93ca613d1bb |
| Verdict: | Malicious activity |
| Analysis date: | May 10, 2024, 09:54:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | E1AC4770F42BAC0E4A6826314331C6EA |
| SHA1: | 66493386AD995819871ACA4C30897B6F29AB358F |
| SHA256: | EABF7FDD31C5838D66CCBC3CA52B0F6EAF8120F83EED43F372F21E4D31734B73 |
| SSDEEP: | 24576:oSL6Ntp05P6ftXeQAPm1sPj54cubcZDUPKrFusldmR8uCbdfxgEgL+xTbQDE5GYJ:oftFtXr85409usl8R8vJgEdCY5n3Rv |
MALICIOUS
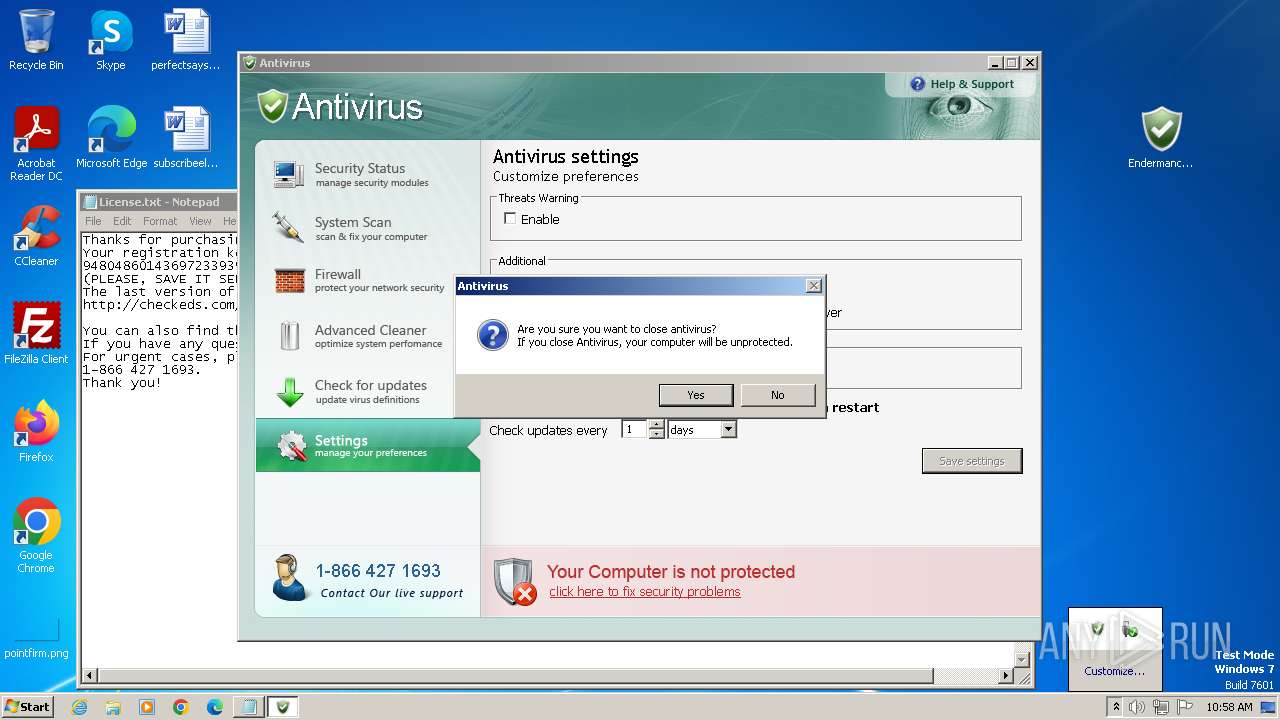
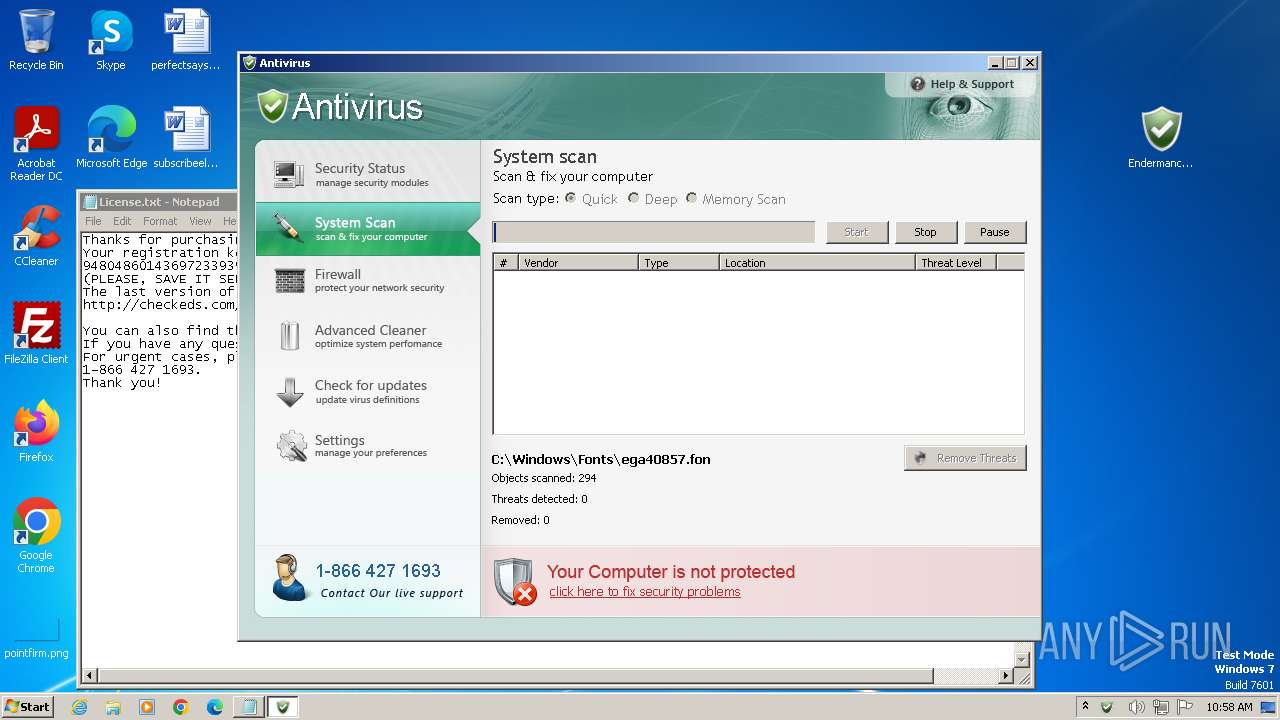
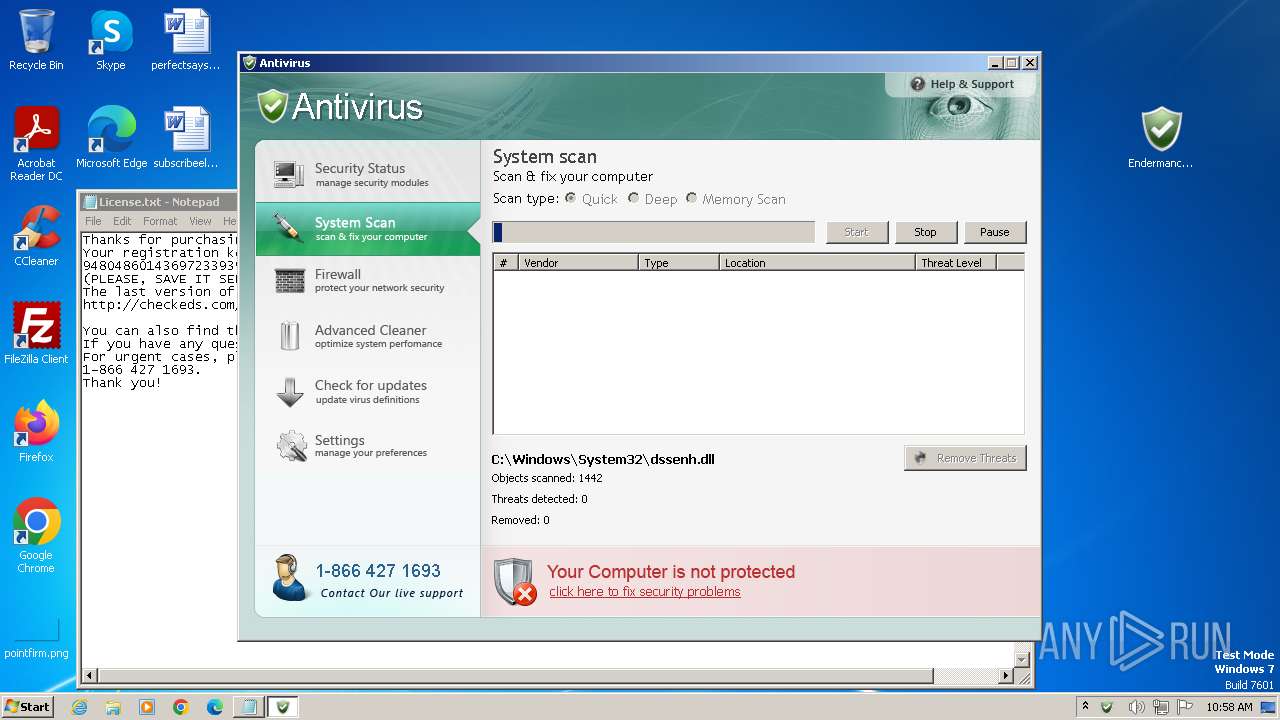
Uses NET.EXE to stop Windows Security Center service
- net.exe (PID: 1764)
- net.exe (PID: 2256)
- Endermanch@Antivirus.exe (PID: 1468)
- net.exe (PID: 2432)
- net.exe (PID: 2736)
- Endermanch@Antivirus.exe (PID: 2840)
- Endermanch@Antivirus.exe (PID: 1116)
Starts NET.EXE for service management
- net.exe (PID: 308)
- net.exe (PID: 1628)
- net.exe (PID: 1764)
- net.exe (PID: 312)
- net.exe (PID: 1596)
- Endermanch@Antivirus.exe (PID: 1116)
- net.exe (PID: 1600)
- net.exe (PID: 2256)
- net.exe (PID: 2196)
- Endermanch@Antivirus.exe (PID: 1468)
- net.exe (PID: 2436)
- net.exe (PID: 2424)
- net.exe (PID: 2432)
- net.exe (PID: 2428)
- net.exe (PID: 2724)
- Endermanch@Antivirus.exe (PID: 2840)
- net.exe (PID: 3176)
- net.exe (PID: 3132)
- net.exe (PID: 2736)
Changes the autorun value in the registry
- Endermanch@Antivirus.exe (PID: 1116)
SUSPICIOUS
Changes internet zones settings
- Endermanch@Antivirus.exe (PID: 1116)
- Endermanch@Antivirus.exe (PID: 1468)
- Endermanch@Antivirus.exe (PID: 2840)
Reads security settings of Internet Explorer
- Endermanch@Antivirus.exe (PID: 1468)
- Endermanch@Antivirus.exe (PID: 2840)
- Endermanch@Antivirus.exe (PID: 1116)
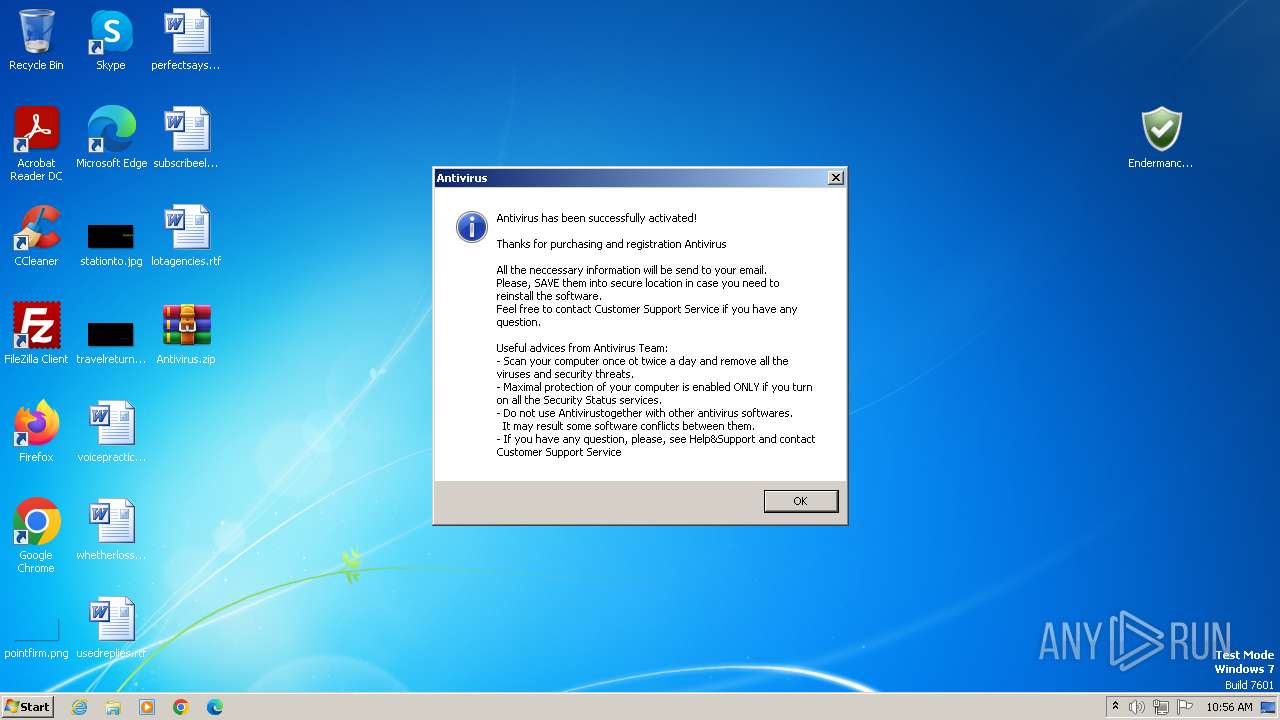
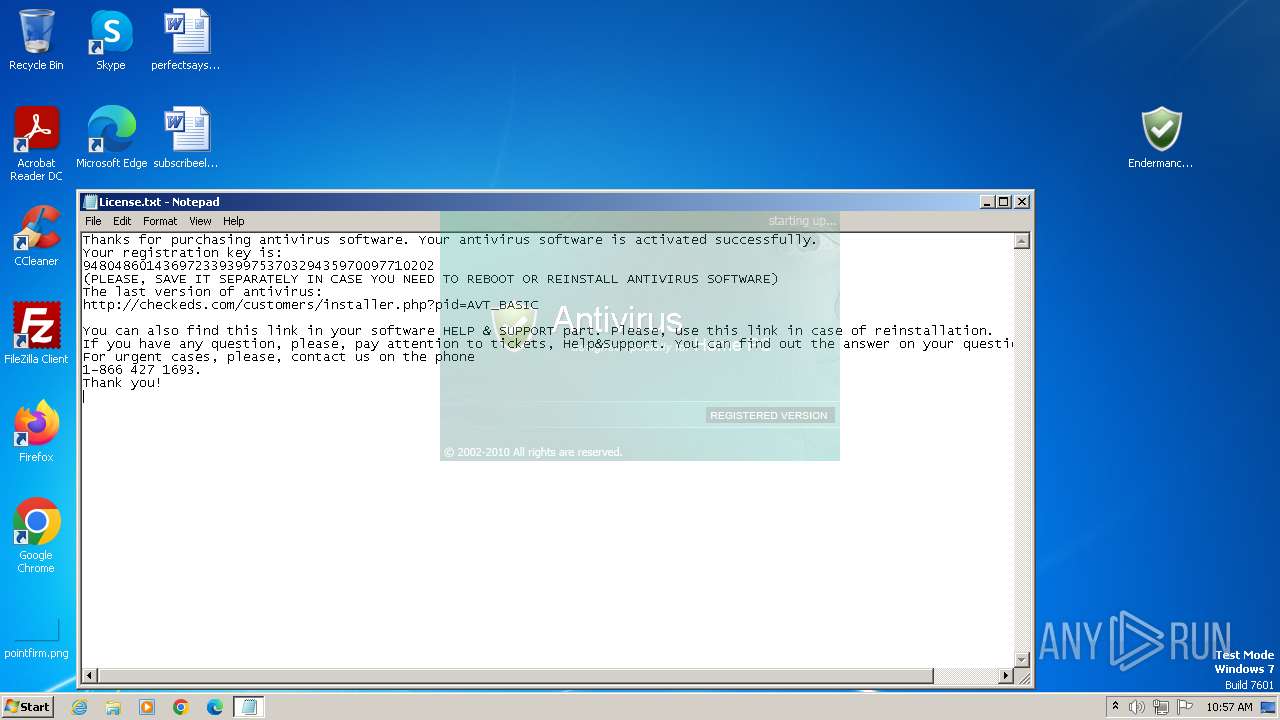
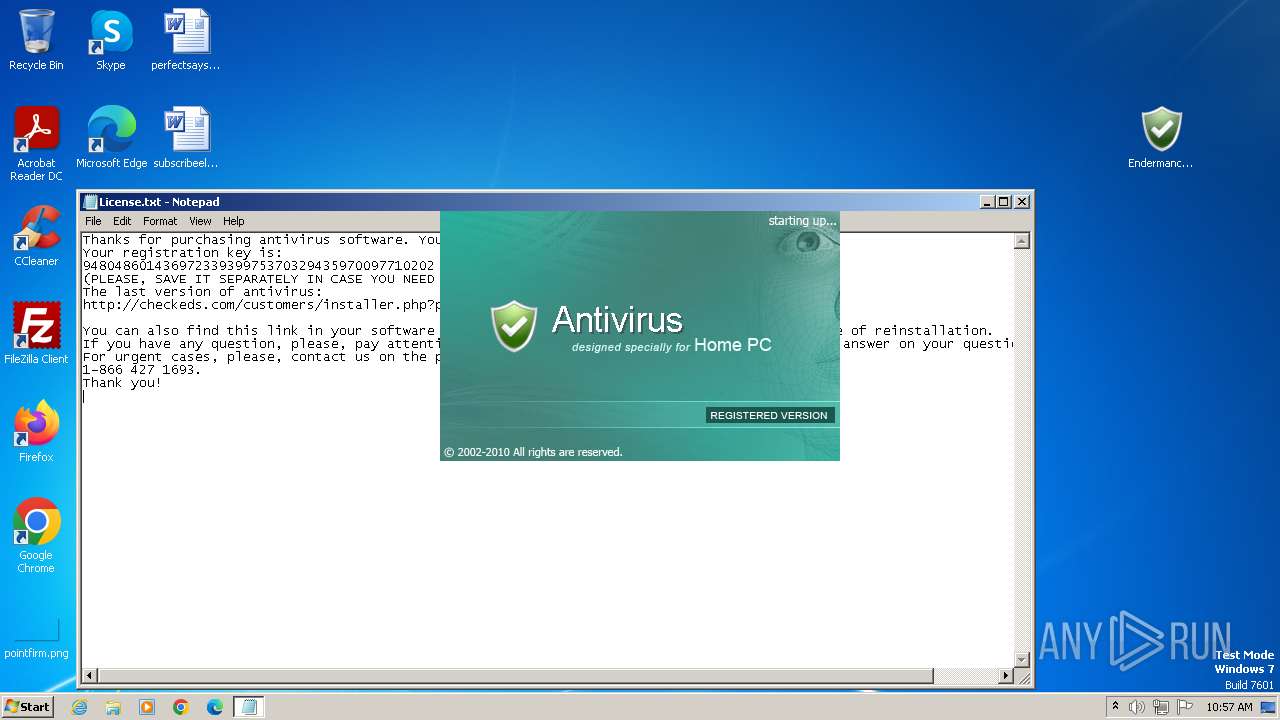
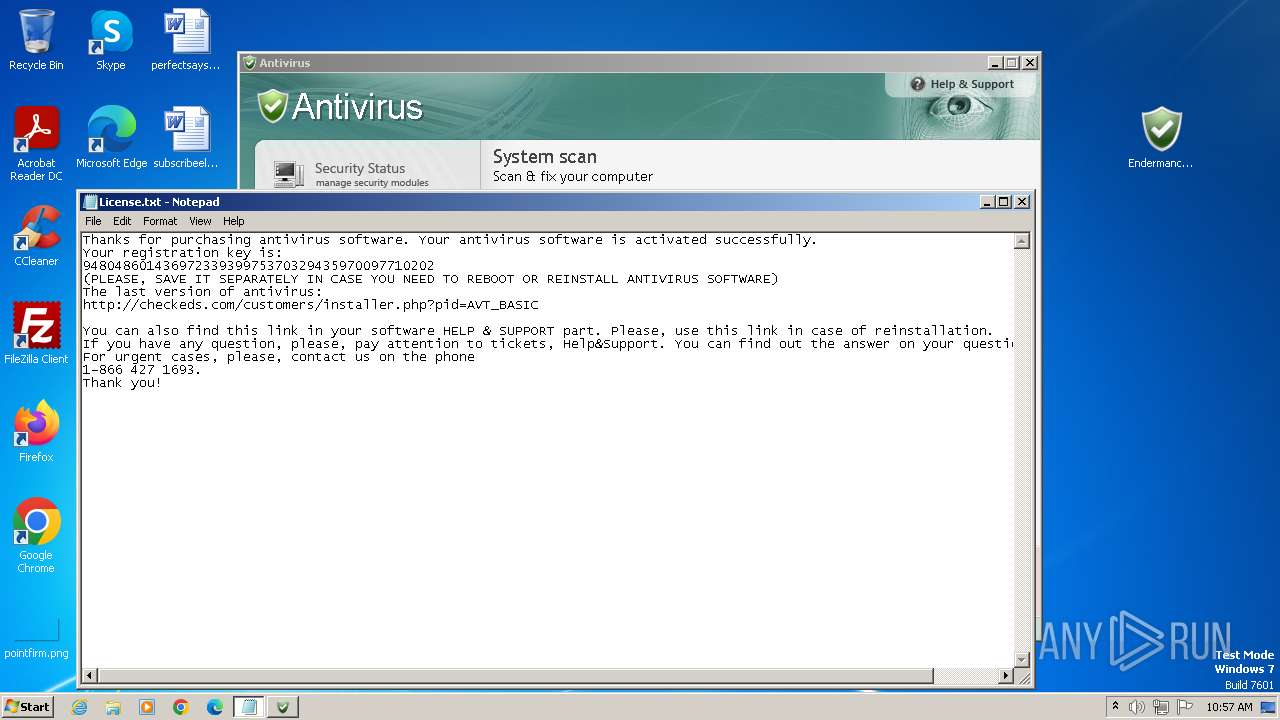
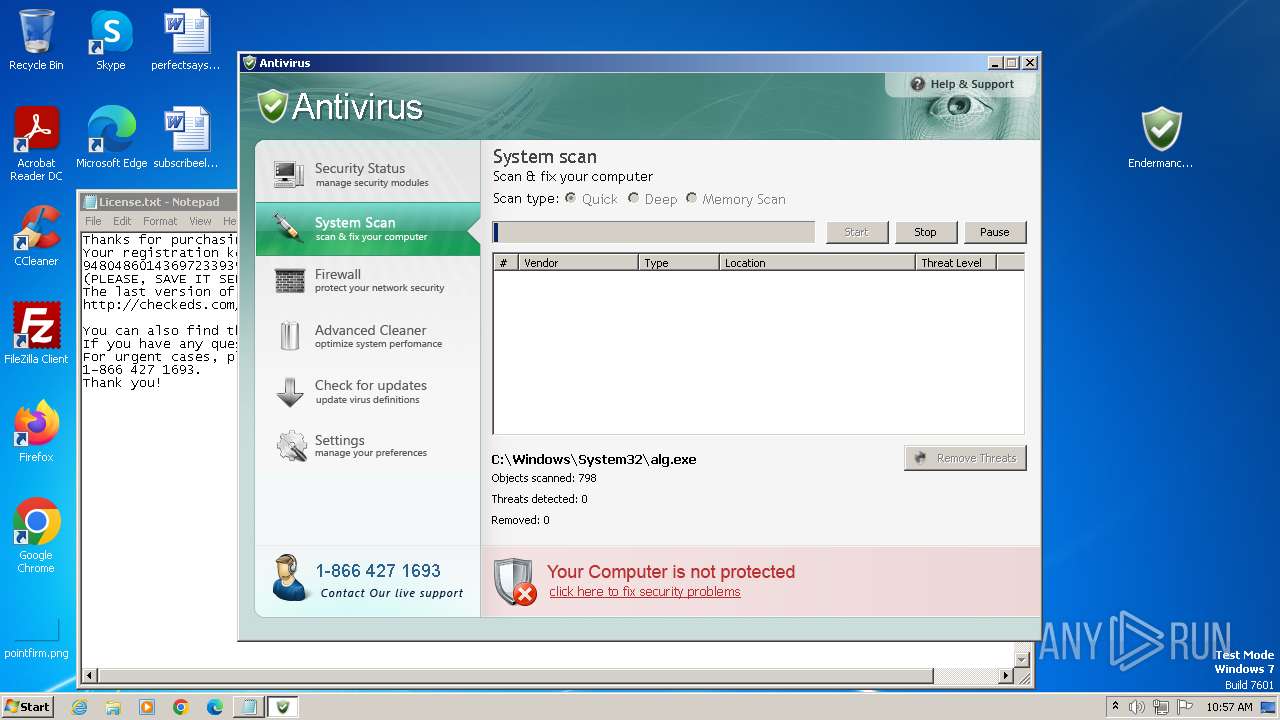
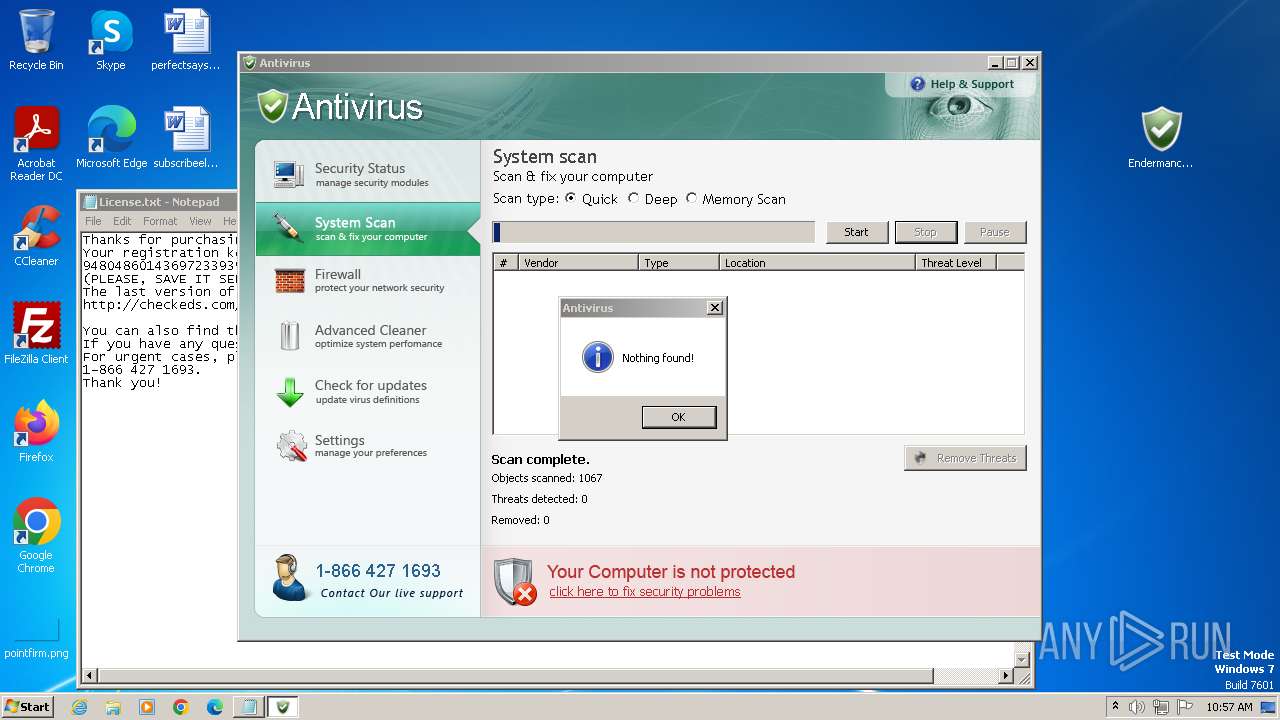
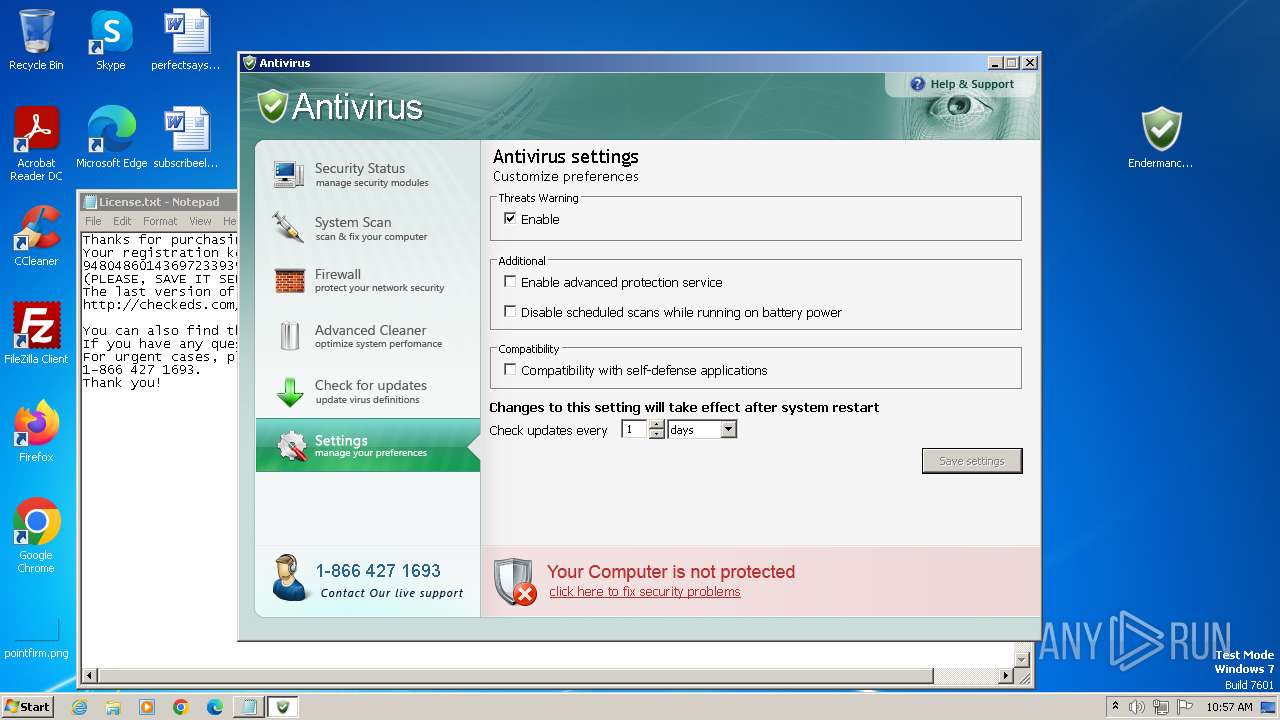
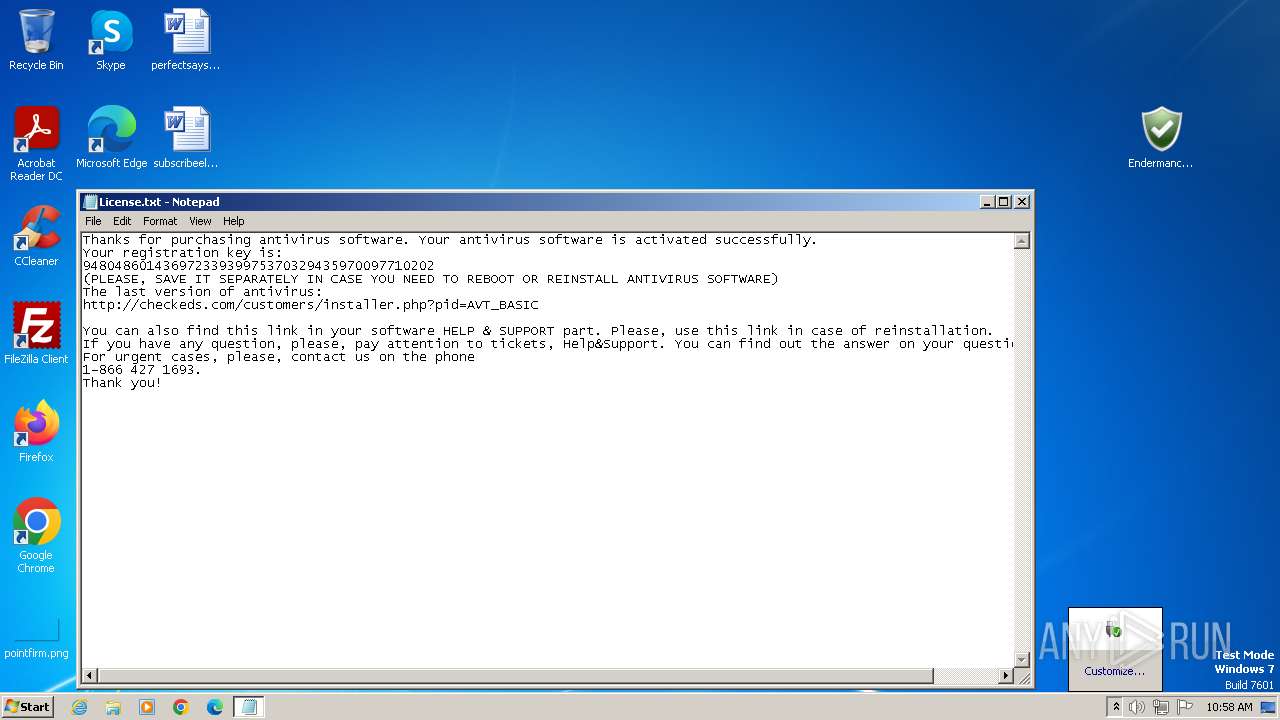
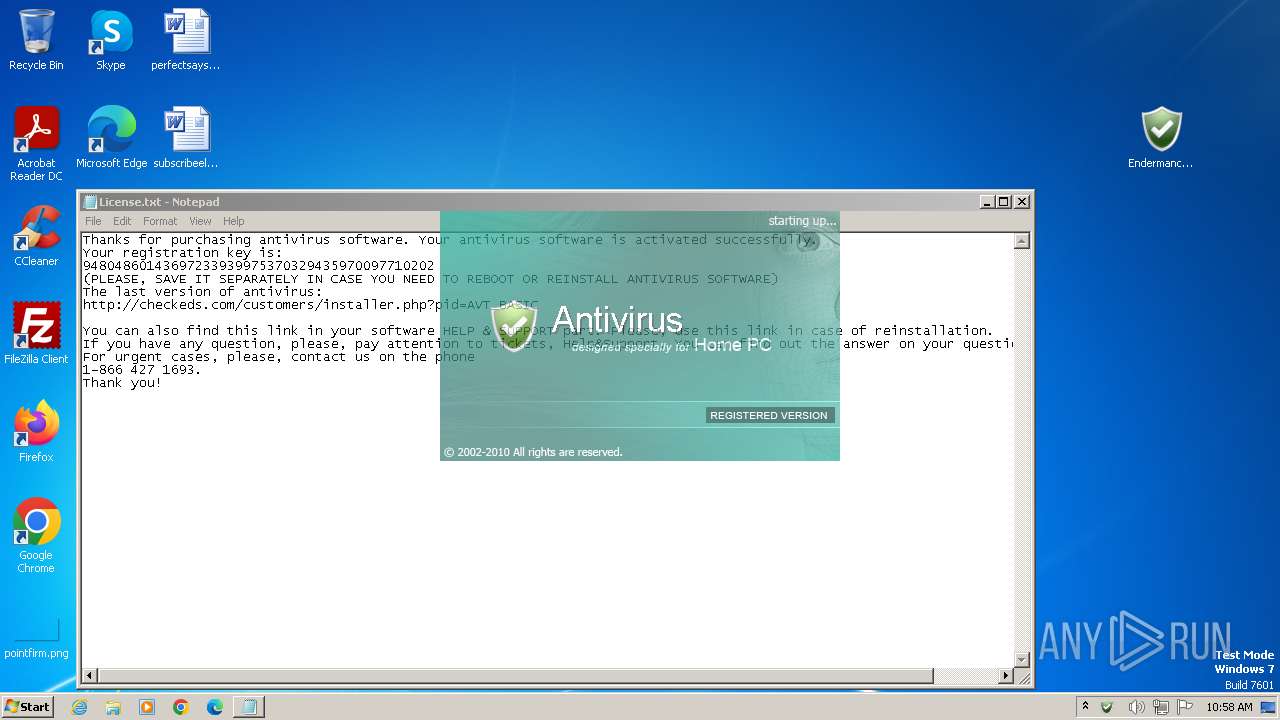
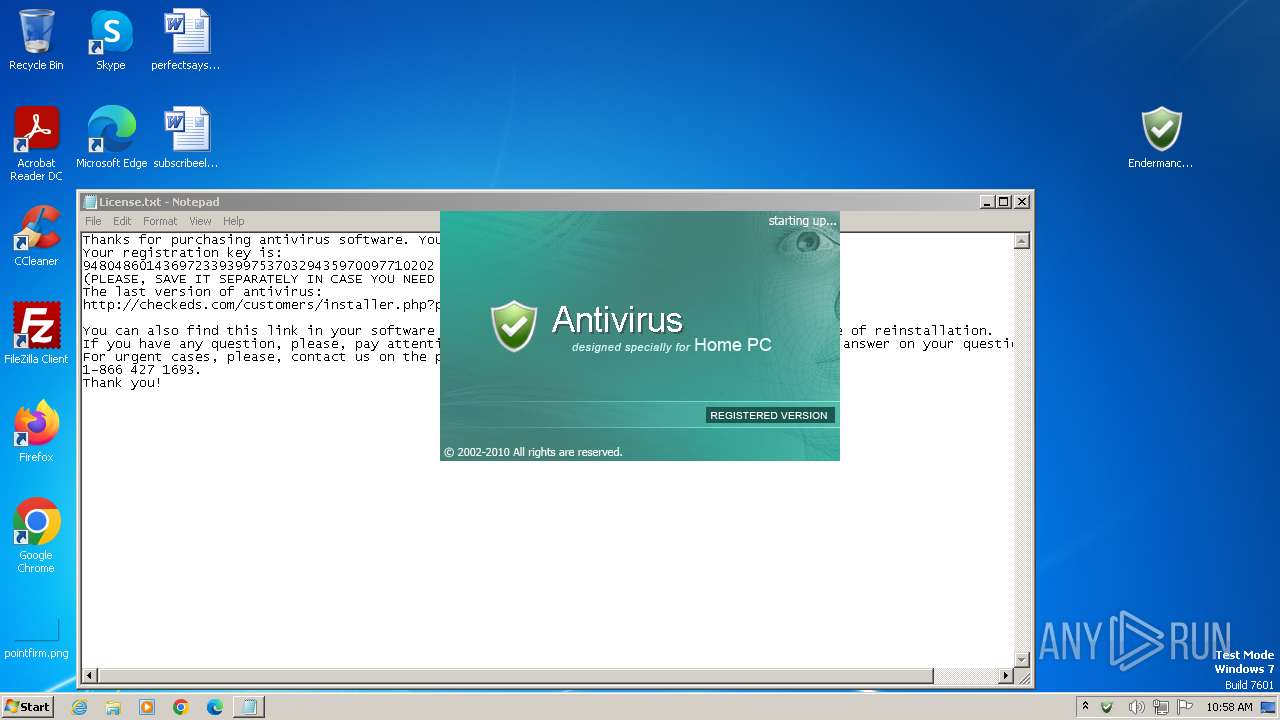
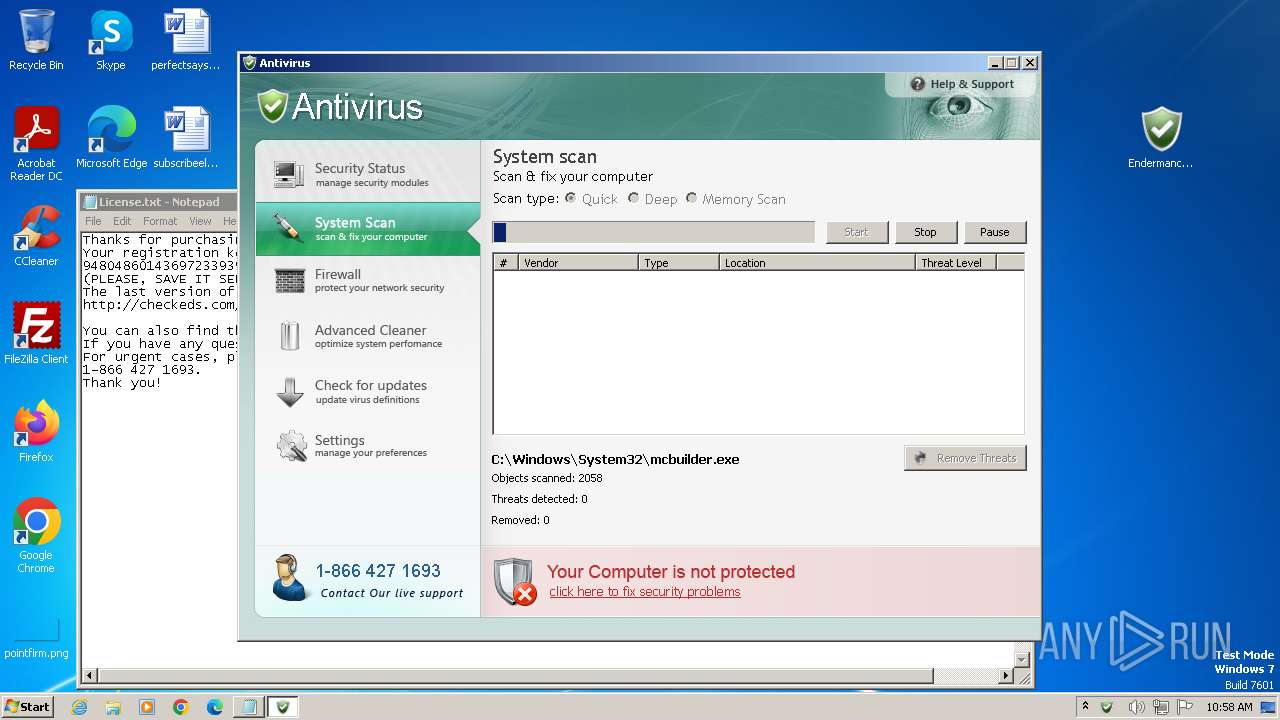
Start notepad (likely ransomware note)
- Endermanch@Antivirus.exe (PID: 1468)
Reads the Internet Settings
- Endermanch@Antivirus.exe (PID: 1468)
- Endermanch@Antivirus.exe (PID: 2840)
- Endermanch@Antivirus.exe (PID: 1116)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3968)
Checks supported languages
- Endermanch@Antivirus.exe (PID: 1116)
- Endermanch@Antivirus.exe (PID: 1468)
- wmpnscfg.exe (PID: 1552)
- Endermanch@Antivirus.exe (PID: 2840)
Reads the computer name
- Endermanch@Antivirus.exe (PID: 1116)
- wmpnscfg.exe (PID: 1552)
- Endermanch@Antivirus.exe (PID: 1468)
- Endermanch@Antivirus.exe (PID: 2840)
Checks proxy server information
- Endermanch@Antivirus.exe (PID: 1116)
- Endermanch@Antivirus.exe (PID: 1468)
- Endermanch@Antivirus.exe (PID: 2840)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3968)
Manual execution by a user
- Endermanch@Antivirus.exe (PID: 1116)
- wmpnscfg.exe (PID: 1552)
- Endermanch@Antivirus.exe (PID: 1468)
- Endermanch@Antivirus.exe (PID: 2840)
Creates files in the program directory
- Endermanch@Antivirus.exe (PID: 1116)
Create files in a temporary directory
- Endermanch@Antivirus.exe (PID: 1116)
- mofcomp.exe (PID: 1856)
- mofcomp.exe (PID: 1072)
- Endermanch@Antivirus.exe (PID: 1468)
- mofcomp.exe (PID: 924)
- mofcomp.exe (PID: 3064)
- Endermanch@Antivirus.exe (PID: 2840)
Reads the machine GUID from the registry
- Endermanch@Antivirus.exe (PID: 1468)
- Endermanch@Antivirus.exe (PID: 2840)
- Endermanch@Antivirus.exe (PID: 1116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2013:12:25 02:24:14 |
| ZipCRC: | 0xd75c0646 |
| ZipCompressedSize: | 1410554 |
| ZipUncompressedSize: | 2066944 |
| ZipFileName: | Endermanch@Antivirus.exe |
Total processes
101
Monitored processes
42
Malicious processes
3
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | net start winmgmt | C:\Windows\System32\net.exe | — | Endermanch@Antivirus.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 312 | net start wscsvc | C:\Windows\System32\net.exe | — | Endermanch@Antivirus.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 916 | C:\Windows\system32\net1 stop wscsvc | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 924 | mofcomp C:\Users\admin\AppData\Local\Temp\4otjesjty.mof | C:\Windows\System32\wbem\mofcomp.exe | — | Endermanch@Antivirus.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: The Managed Object Format (MOF) Compiler Exit code: 3 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1072 | mofcomp C:\Users\admin\AppData\Local\Temp\4otjesjty.mof | C:\Windows\System32\wbem\mofcomp.exe | — | Endermanch@Antivirus.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: The Managed Object Format (MOF) Compiler Exit code: 3 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1080 | C:\Windows\system32\net1 stop wscsvc | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1116 | "C:\Users\admin\Desktop\Endermanch@Antivirus.exe" | C:\Users\admin\Desktop\Endermanch@Antivirus.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225547 Modules
| |||||||||||||||
| 1284 | C:\Windows\system32\net1 stop winmgmt /y | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1344 | notepad.exe "C:\Users\admin\Desktop\License.txt" | C:\Windows\System32\notepad.exe | — | Endermanch@Antivirus.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1468 | "C:\Users\admin\Desktop\Endermanch@Antivirus.exe" | C:\Users\admin\Desktop\Endermanch@Antivirus.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225547 Modules
| |||||||||||||||
Total events
16 424
Read events
16 236
Write events
165
Delete events
23
Modification events
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Antivirus.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
4
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 924 | mofcomp.exe | C:\Users\admin\AppData\Local\Temp\tmp1303.tmp | binary | |
MD5:F99EE9B793E0B063F50D3B4D5D95C026 | SHA256:990113E7452263794B2FD7648FB1304DFDDD541D79B1DBE6D0DA5D8A4D03713A | |||
| 1116 | Endermanch@Antivirus.exe | C:\ProgramData\license.dat | text | |
MD5:692F142CA15552B6F9B8CA74B7E5679F | SHA256:834EB5B9A1F2E30A7E0430365A259E26F98125222A0475E13D17E138BB538FD4 | |||
| 3064 | mofcomp.exe | C:\Users\admin\AppData\Local\Temp\tmp840.tmp | binary | |
MD5:F99EE9B793E0B063F50D3B4D5D95C026 | SHA256:990113E7452263794B2FD7648FB1304DFDDD541D79B1DBE6D0DA5D8A4D03713A | |||
| 1468 | Endermanch@Antivirus.exe | C:\Users\admin\Desktop\License.txt | text | |
MD5:B2B8FB49E4679AF2EC2E39432AC8FA28 | SHA256:AA20F9777786A12F8D1E0CAE3561968D488973F03E1921FC55398F3FF3D89456 | |||
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3968.22634\Endermanch@Antivirus.exe | executable | |
MD5:C7E9746B1B039B8BD1106BCA3038C38F | SHA256:B1369BD254D96F7966047AD4BE06103830136629590182D49E5CB8680529EBD4 | |||
| 1072 | mofcomp.exe | C:\Users\admin\AppData\Local\Temp\tmp5CC3.tmp | binary | |
MD5:F99EE9B793E0B063F50D3B4D5D95C026 | SHA256:990113E7452263794B2FD7648FB1304DFDDD541D79B1DBE6D0DA5D8A4D03713A | |||
| 1856 | mofcomp.exe | C:\Users\admin\AppData\Local\Temp\tmpC584.tmp | binary | |
MD5:3DE4769F0E1EAD866FB009D8B49AA93C | SHA256:976579B449D58CE40B111C782C62571C0137C01577177E638BACA5405835BC57 | |||
| 1116 | Endermanch@Antivirus.exe | C:\Users\admin\AppData\Local\Temp\4otjesjty.mof | text | |
MD5:7FAD92AFDA308DCA8ACFC6FF45C80C24 | SHA256:76E19416EB826A27BDCF626C3877CF7812BBE9B62CC2CCC5C2F65461D644246F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
14
DNS requests
4
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1116 | Endermanch@Antivirus.exe | GET | 404 | 54.39.157.64:80 | http://searchdusty.com/avt/avt_db | unknown | — | — | unknown |
1116 | Endermanch@Antivirus.exe | GET | 404 | 54.39.157.64:80 | http://searchdusty.com/avt/avtr.dat | unknown | — | — | unknown |
1116 | Endermanch@Antivirus.exe | GET | 404 | 54.39.157.64:80 | http://searchdusty.com/avt/avt.dat | unknown | — | — | unknown |
1116 | Endermanch@Antivirus.exe | GET | 200 | 54.39.157.64:80 | http://searchdusty.com/customers/readdatagateway.php?type=notactivation&affid=139&subid=1®key=94804860143697233939975370329435970097710202&email=1&version=4.0 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1116 | Endermanch@Antivirus.exe | 54.39.157.64:80 | searchdusty.com | OVH SAS | CA | unknown |
1116 | Endermanch@Antivirus.exe | 49.13.77.253:80 | frequentwin.com | Hetzner Online GmbH | DE | unknown |
1468 | Endermanch@Antivirus.exe | 49.13.77.253:80 | frequentwin.com | Hetzner Online GmbH | DE | unknown |
2840 | Endermanch@Antivirus.exe | 49.13.77.253:80 | frequentwin.com | Hetzner Online GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
searchdusty.com |
| whitelisted |
frequentwin.com |
| unknown |
fastsofgeld.com |
| unknown |
highway-traffic.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1116 | Endermanch@Antivirus.exe | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
1116 | Endermanch@Antivirus.exe | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
1116 | Endermanch@Antivirus.exe | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
— | — | A Network Trojan was detected | ET MALWARE Fake AV GET |
— | — | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |