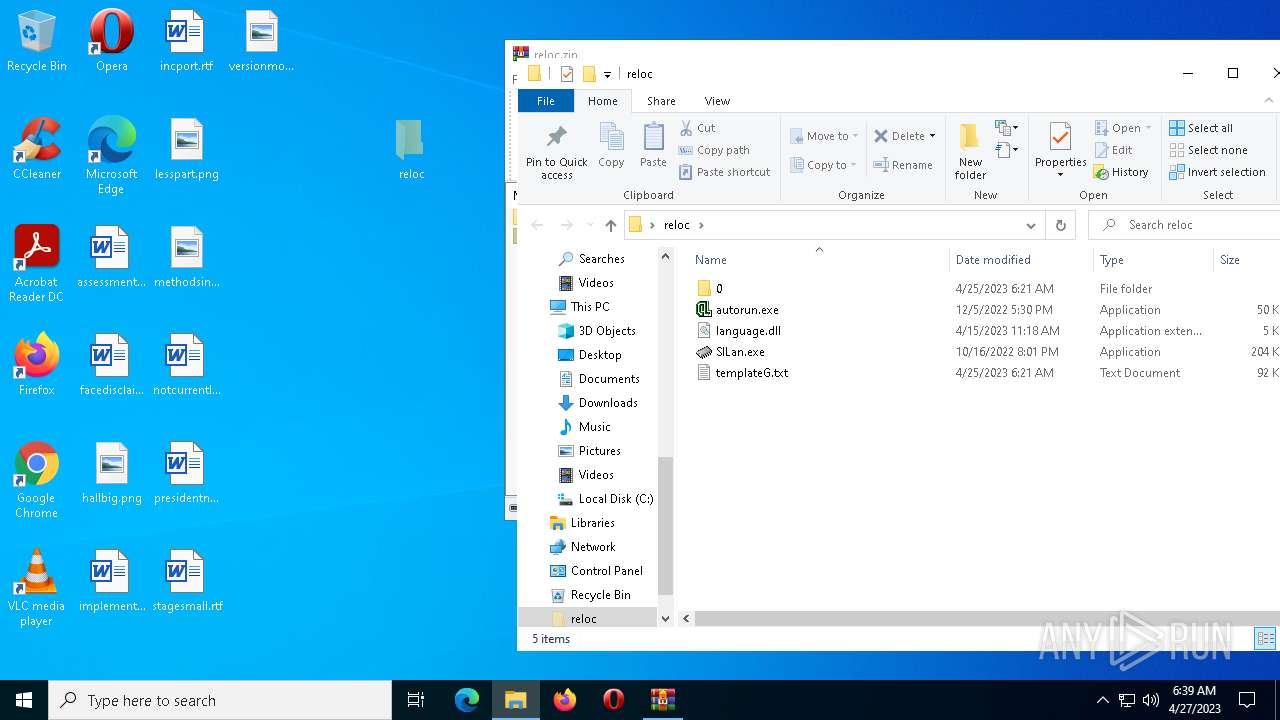
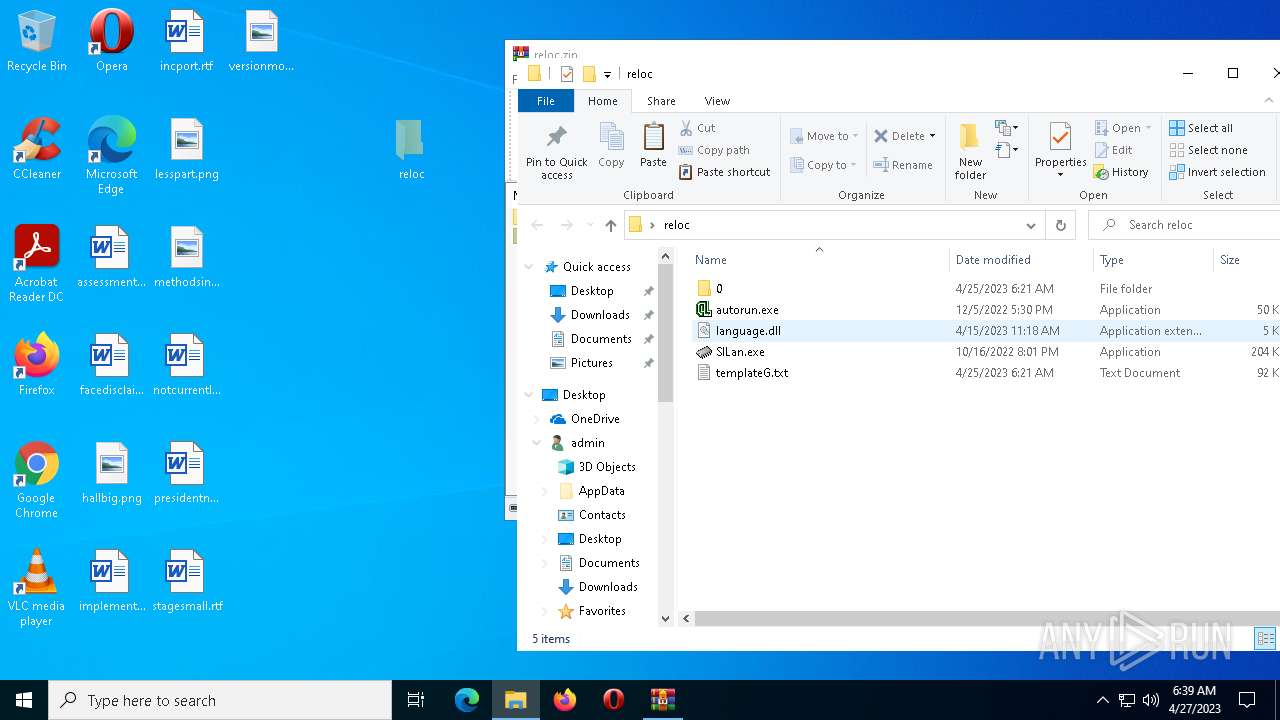
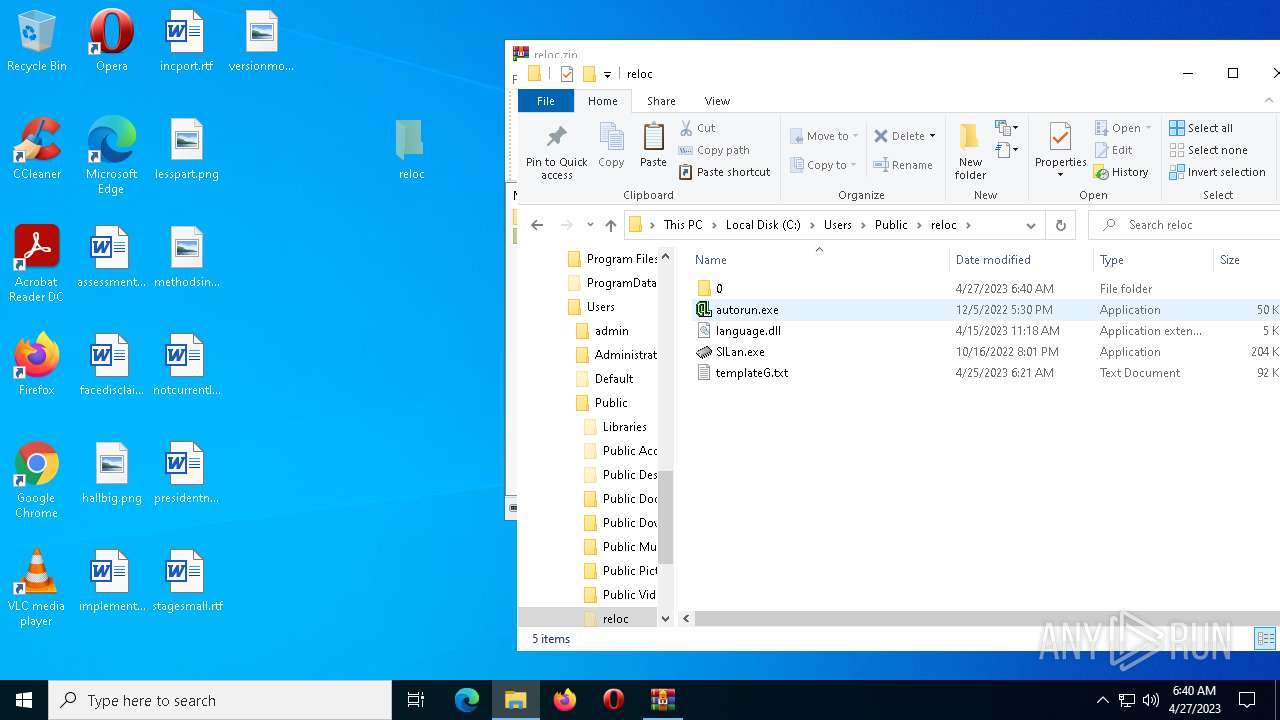
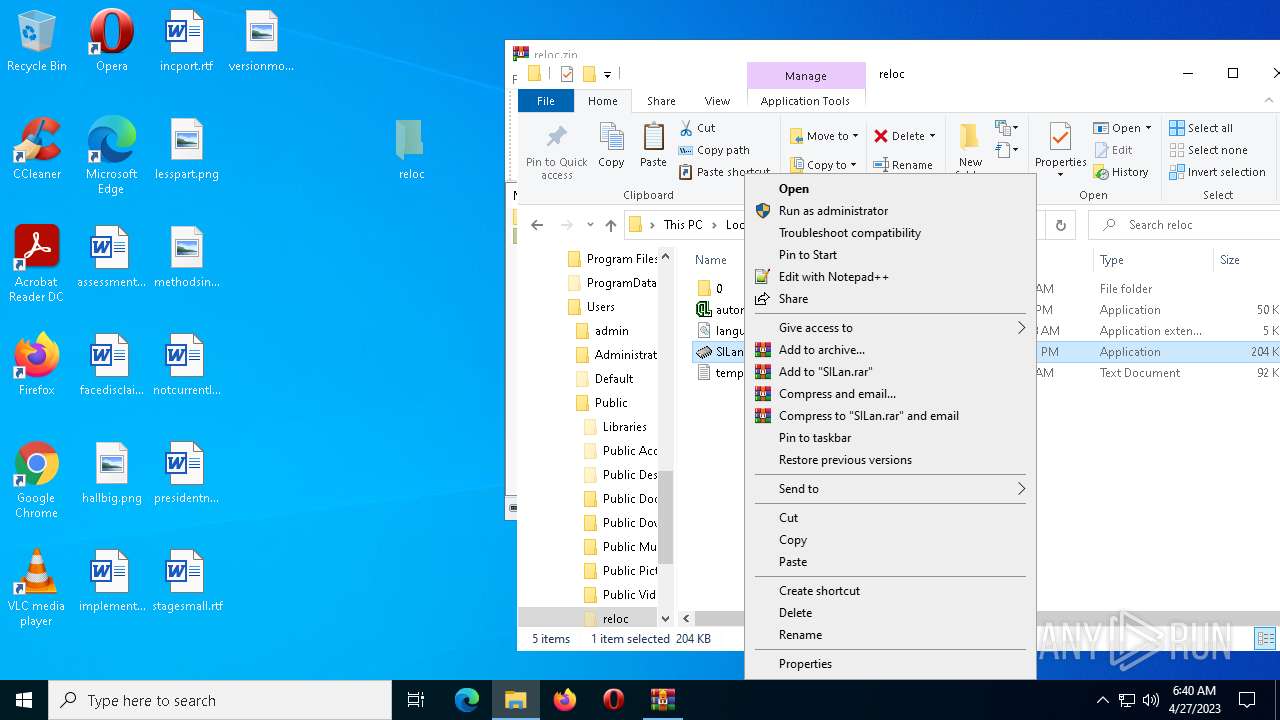
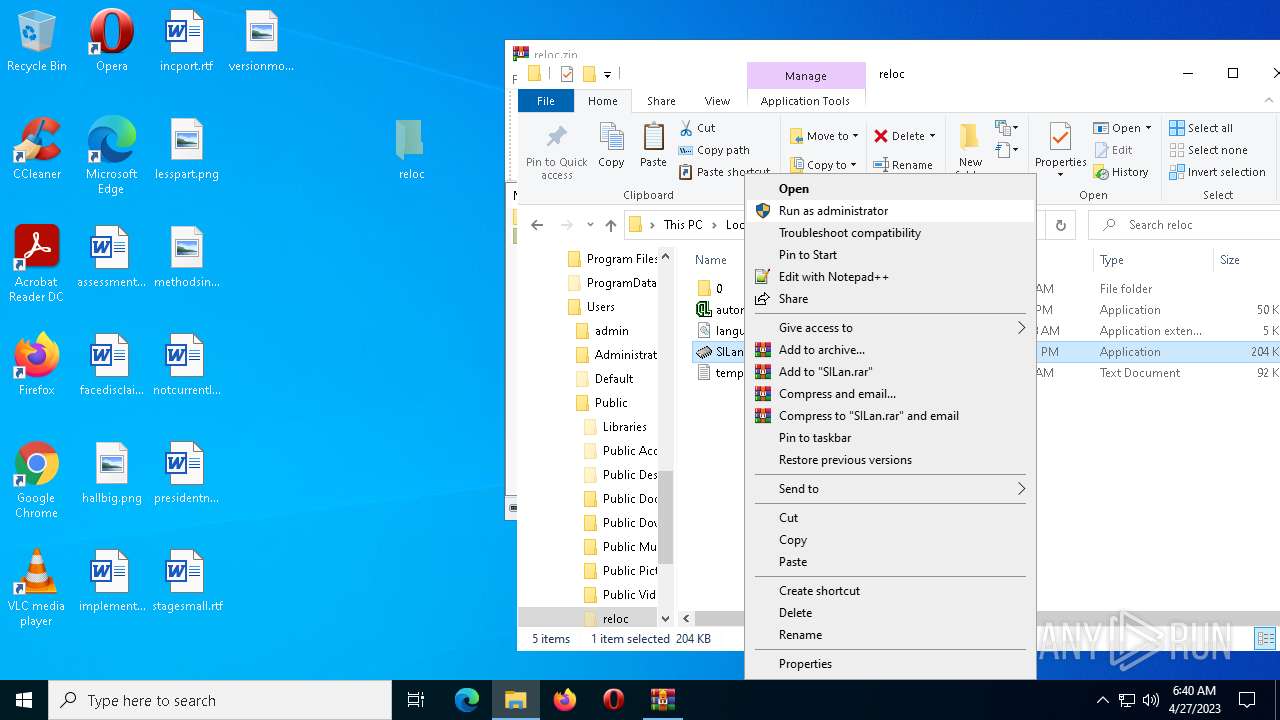
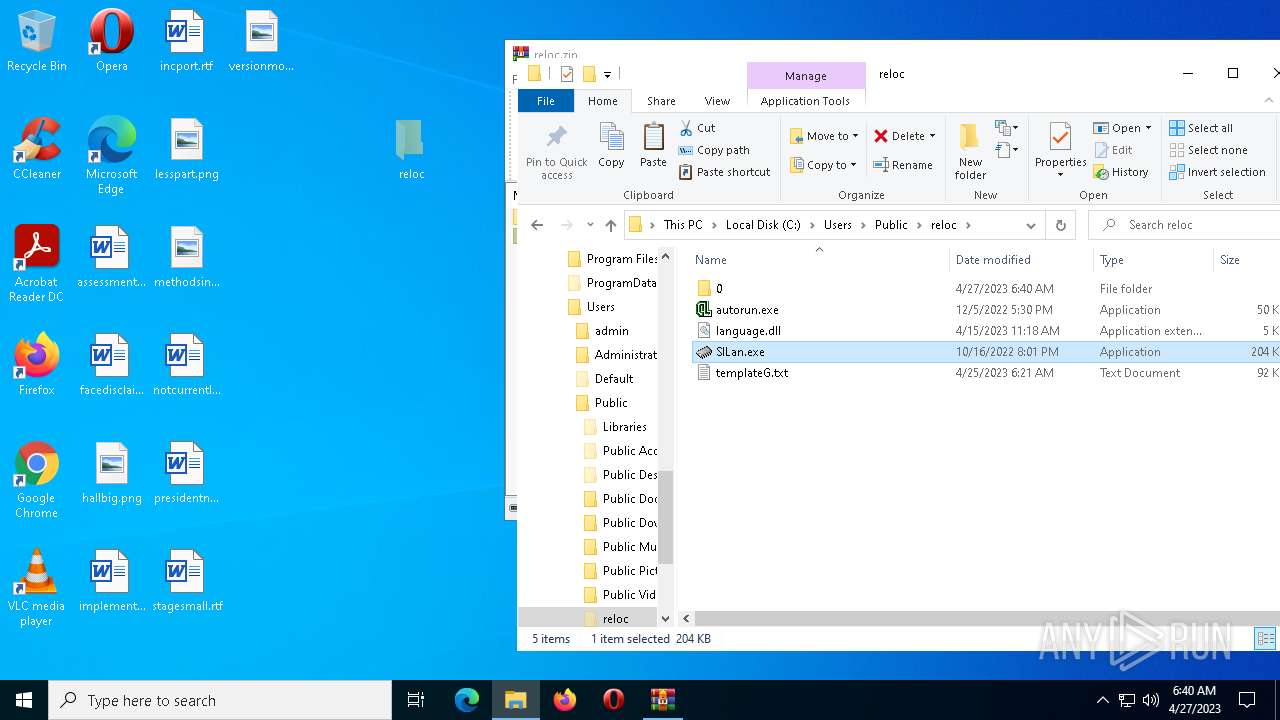
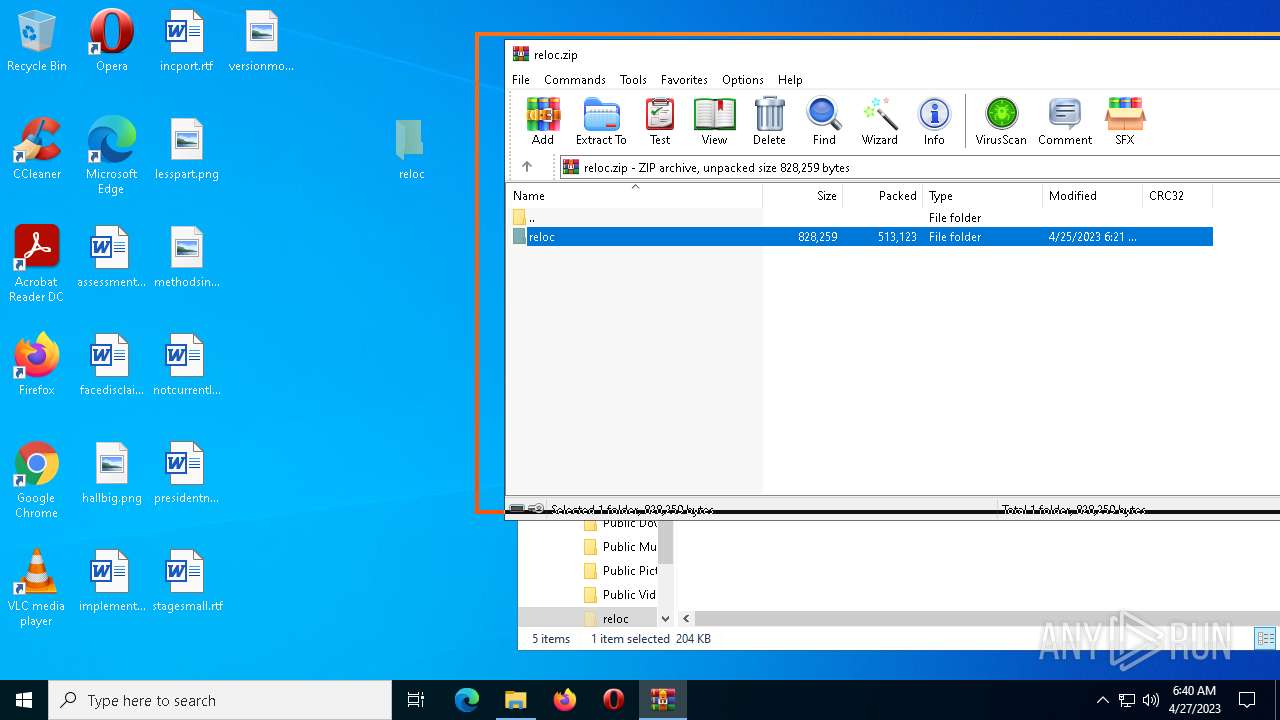
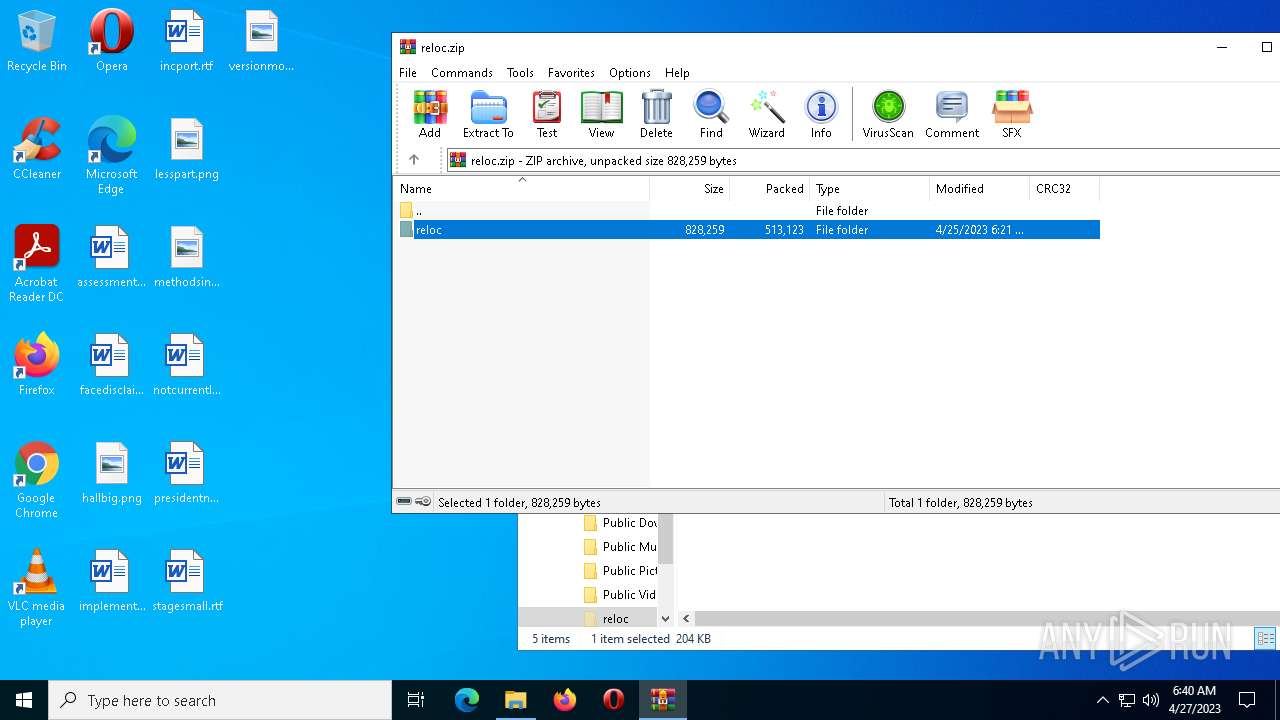
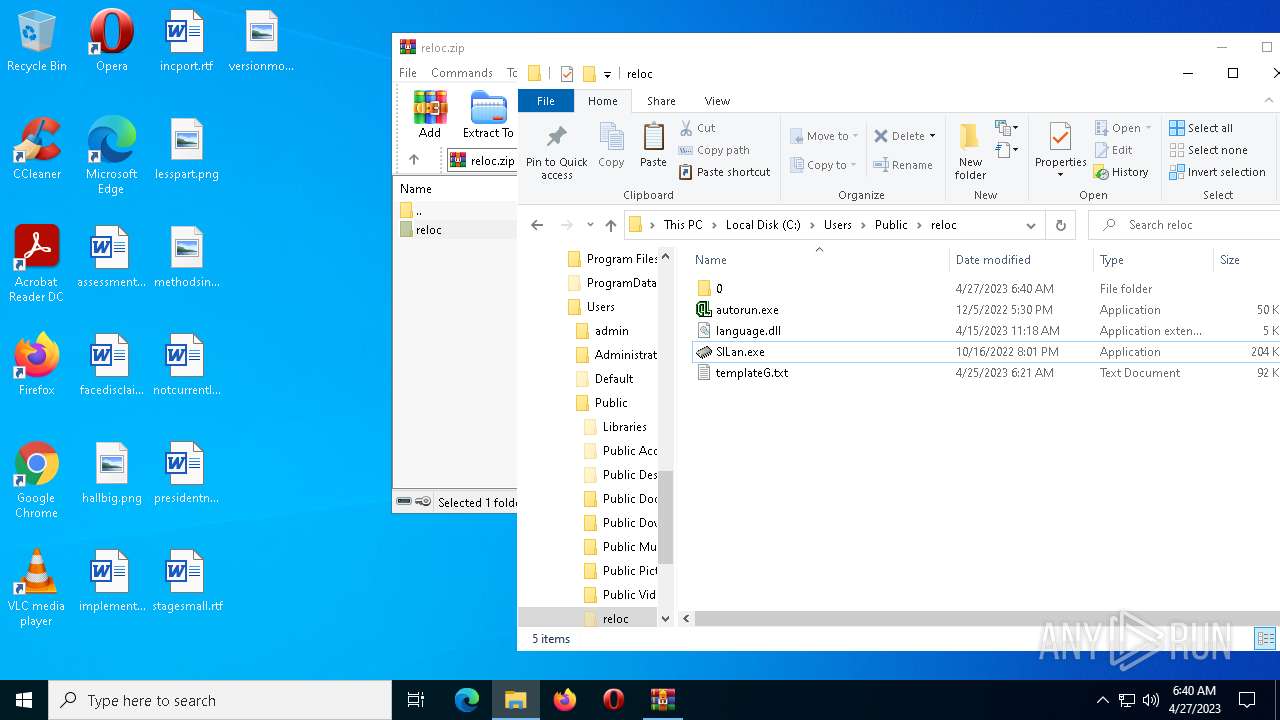
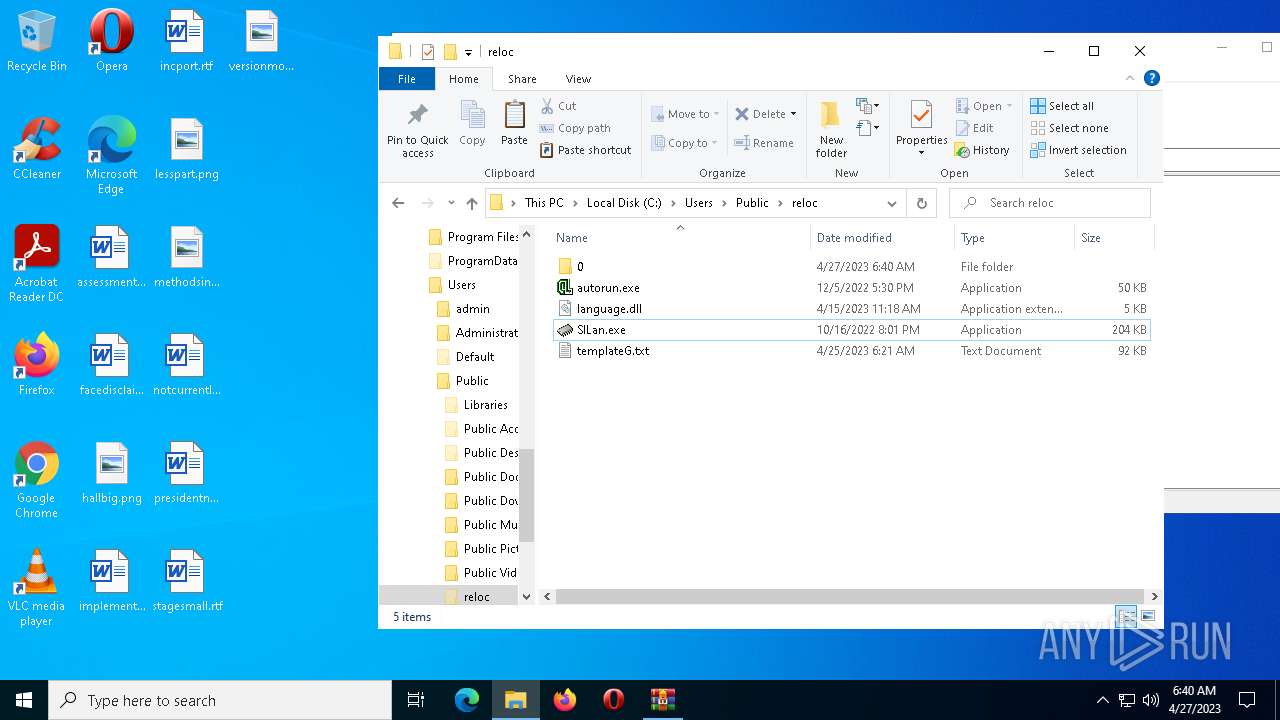
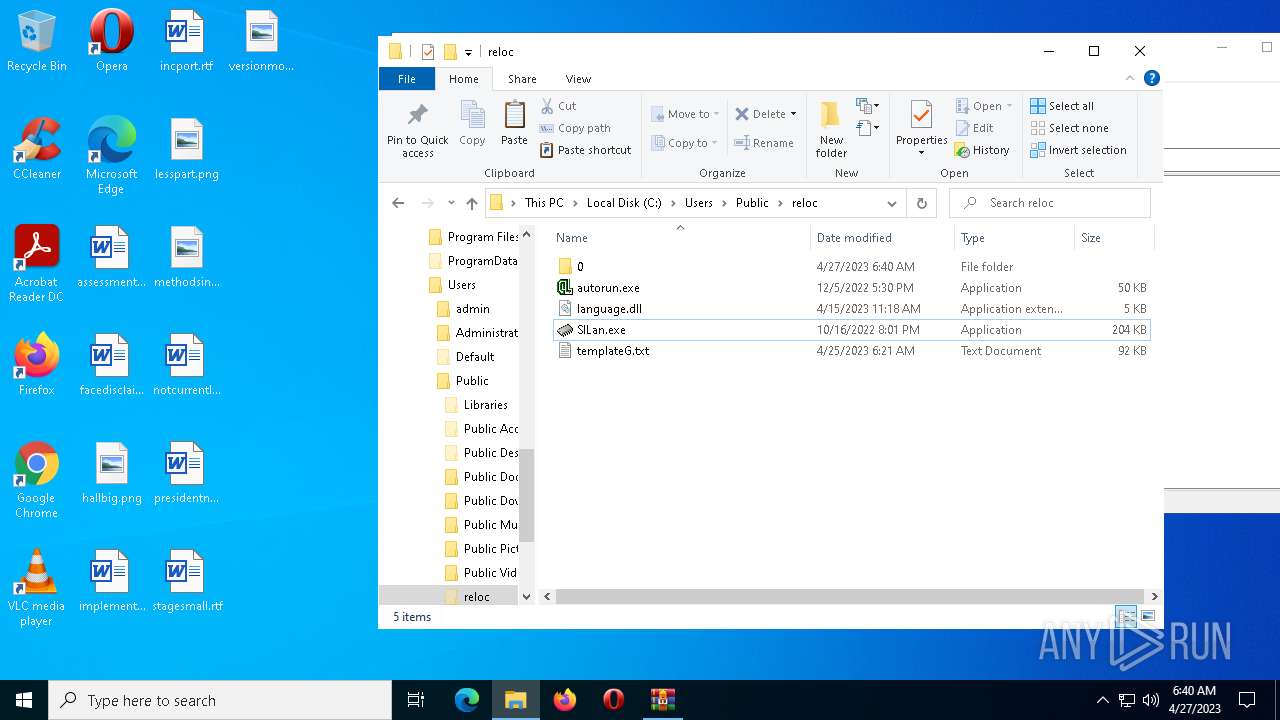
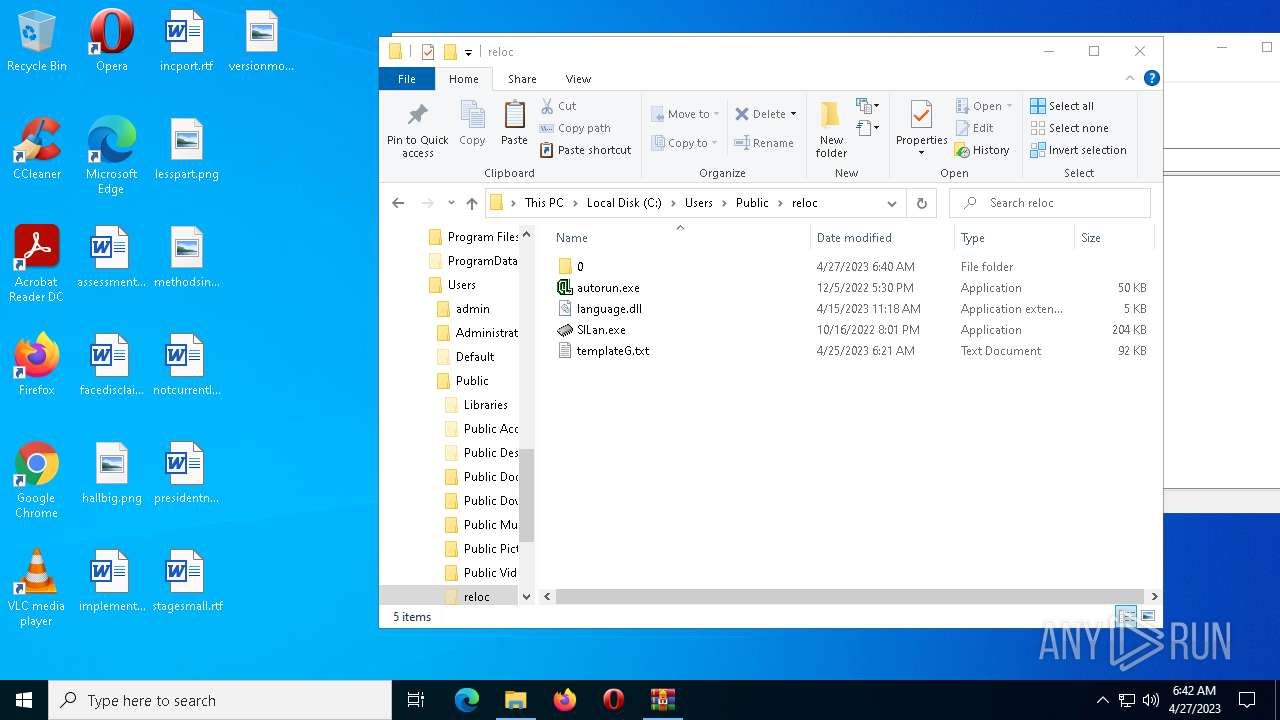
| File name: | reloc.zip |
| Full analysis: | https://app.any.run/tasks/114766d9-a37e-4021-9799-30eafcc112aa |
| Verdict: | Malicious activity |
| Analysis date: | April 27, 2023, 06:39:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 8DFE899B30B8D2F7DD00913FFA5EB832 |
| SHA1: | 22D686BEE3871CAD53431477754BA0F699D961AD |
| SHA256: | EABC6724A7EF0793C73F78B427E940C63551896FE84F3AA83630581973D614CA |
| SSDEEP: | 12288:BsUnvOi5J43tB4wbe2LOVDGbKapJZTwFsUnvOi5J43to4e1rDoNk:eUl5JwB4OeLyp8CUl5Jwo4e1HB |
MALICIOUS
Runs injected code in another process
- SystemSettings.exe (PID: 1204)
Application was injected by another process
- msedge.exe (PID: 6628)
SUSPICIOUS
Reads settings of System Certificates
- SystemSettings.exe (PID: 1204)
Connects to unusual port
- autorun.exe (PID: 6600)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2732)
The process checks LSA protection
- slui.exe (PID: 5172)
- SystemSettings.exe (PID: 1204)
- autorun.exe (PID: 6600)
- conhost.exe (PID: 5088)
- autorun.exe (PID: 5224)
- autorun.exe (PID: 4712)
- notepad.exe (PID: 5780)
Checks supported languages
- autorun.exe (PID: 6600)
- SILan.exe (PID: 3344)
- SILan.exe (PID: 6404)
- autorun.exe (PID: 4712)
- SystemSettings.exe (PID: 1204)
- SILan.exe (PID: 1916)
- autorun.exe (PID: 5224)
Manual execution by a user
- SILan.exe (PID: 3344)
- cmd.exe (PID: 4224)
- SILan.exe (PID: 6404)
- notepad.exe (PID: 5780)
- SILan.exe (PID: 1916)
Reads the computer name
- autorun.exe (PID: 6600)
- SystemSettings.exe (PID: 1204)
- autorun.exe (PID: 4712)
- autorun.exe (PID: 5224)
Process checks computer location settings
- SystemSettings.exe (PID: 1204)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | reloc/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2023:04:25 14:21:52 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
149
Monitored processes
14
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1204 | "C:\Windows\ImmersiveControlPanel\SystemSettings.exe" -ServerName:microsoft.windows.immersivecontrolpanel | C:\Windows\ImmersiveControlPanel\SystemSettings.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Settings Exit code: 0 Version: 10.0.19041.1266 (WinBuild.160101.0800) Modules
| |||||||||||||||
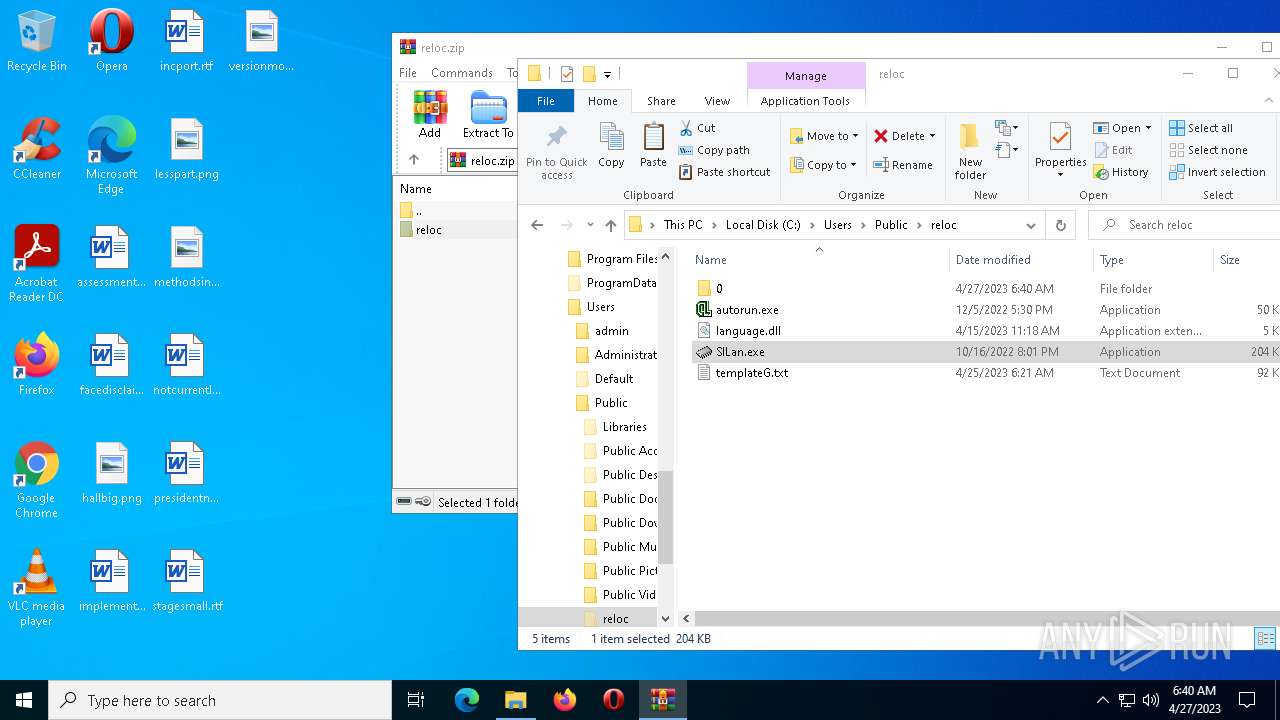
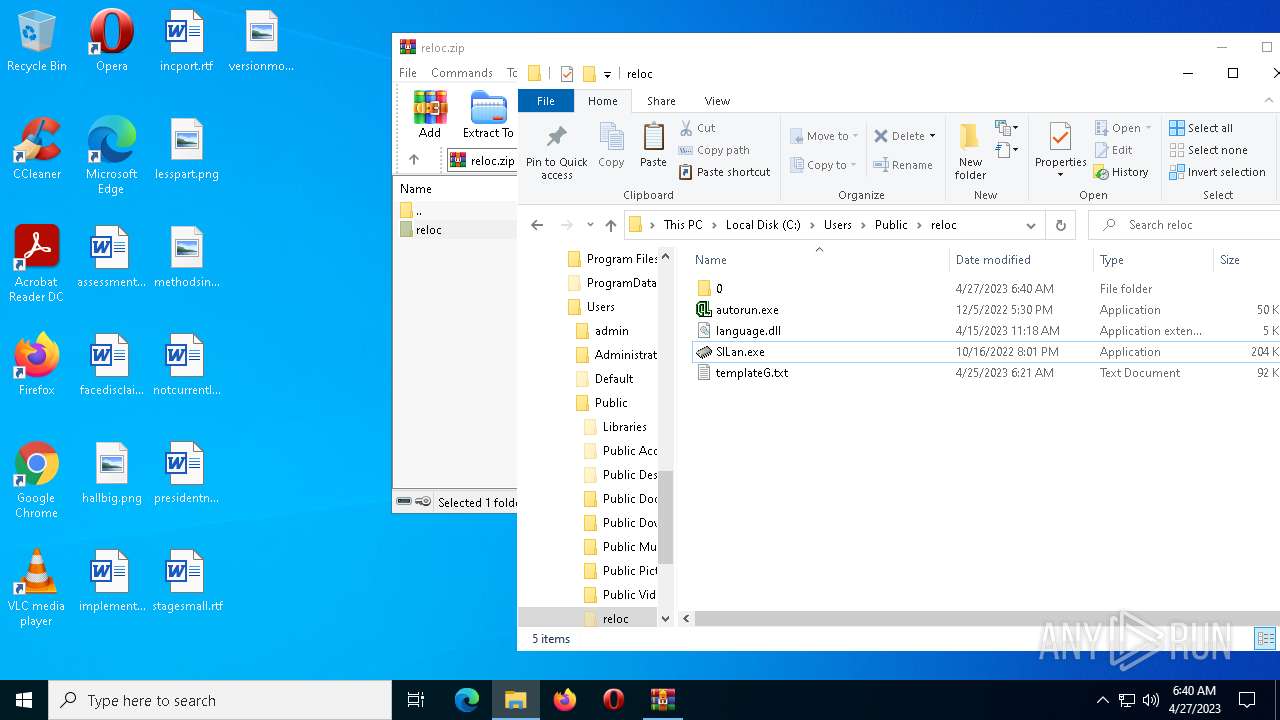
| 1916 | "C:\Users\Public\reloc\SILan.exe" | C:\Users\Public\reloc\SILan.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: SILan MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 2732 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\reloc.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3344 | "C:\Users\Public\reloc\SILan.exe" | C:\Users\Public\reloc\SILan.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: SILan MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 4180 | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe -Embedding | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneDriveFile Co-Authoring Executable Exit code: 0 Version: 19.043.0304.0013 Modules
| |||||||||||||||
| 4224 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4712 | C:\Users\Public\reloc\autorun.exe | C:\Users\Public\reloc\autorun.exe | — | SILan.exe | |||||||||||
User: admin Company: CyberLink Corp. Integrity Level: MEDIUM Description: PowerDVD Language Application Exit code: 0 Version: 1.00.3413 Modules
| |||||||||||||||
| 5088 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5172 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5224 | C:\Users\Public\reloc\autorun.exe | C:\Users\Public\reloc\autorun.exe | — | SILan.exe | |||||||||||
User: admin Company: CyberLink Corp. Integrity Level: MEDIUM Description: PowerDVD Language Application Exit code: 0 Version: 1.00.3413 Modules
| |||||||||||||||
Total events
10 060
Read events
9 992
Write events
68
Delete events
0
Modification events
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | VerInfo |
Value: 003C050012F8FE6A437AD701 | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\SpybotAntiBeaconPortable-safer-networking.org_3.7.0.paf.zip | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\MicrosoftEdgePolicyTemplates.cab | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\MicrosoftEdgePolicyTemplates.zip | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1204) SystemSettings.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\ContentDeliveryManager\Subscriptions\88000105 |
| Operation: | write | Name: | HasValidContent |
Value: 0 | |||
| (PID) Process: | (1204) SystemSettings.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\ContentDeliveryManager\Subscriptions\88000105 |
| Operation: | write | Name: | SubscriptionContext |
Value: sc-allCompleted=0 | |||
Executable files
12
Suspicious files
18
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2732 | WinRAR.exe | C:\Users\admin\AppData\Roaming\WinRAR\version.dat | binary | |
MD5:079A7B8D6BBB85E385C4BD12B9778BFB | SHA256:B0167362415EDF4A985C5D67C32463ED5D19DFADD03DE604C6AB9C223B38B848 | |||
| 2732 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2732.6073\reloc\0\templateG.txt | binary | |
MD5:369EA122D4E29F06E088FA0A59B5DD3B | SHA256:CB5D8215B6372D25DC8F690993BE661A98C4AB3771DF4903ABE440516D568C10 | |||
| 1204 | SystemSettings.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\f18460fded109990.customDestinations-ms | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 1204 | SystemSettings.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\4AD11DW7GGAFTLNVN1JY.temp | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 2732 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2732.6073\reloc\templateG.txt | binary | |
MD5:83CF3F61C69BBCD1076DBC806758D9ED | SHA256:DD49D899381088D086A7A43DFB338DF57204D3A70DF9333FDF9C79F0D94F07F3 | |||
| 4180 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Common\FileCoAuth-2023-04-27.0642.4180.1.aodl | binary | |
MD5:923BF0E545D9C37CA8874C8D6C4A30E6 | SHA256:AB32C675D35DDBEBFCF8B11720C3E550024E8D0DF557838F17186377E3D0FE65 | |||
| 2732 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2732.6073\reloc\autorun.exe | executable | |
MD5:86810E2D993F7327EB5B25B5D17D21C1 | SHA256:63636CEC408ACBBC4D04C01F9EFDBE4B9B08FA0C4390EC8729B9FF0C8BE9D246 | |||
| 4180 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Common\FileCoAuth-2023-04-27.0642.4180.1.odl | binary | |
MD5:1EF798032E6679CD6B8169EE56FF230D | SHA256:39015E15C34C61E9C66A0E5AFAC41B9FA3B740C6BB424A37E8E4F99348CC43FE | |||
| 6628 | msedge.exe | C:\USERS\ADMIN\APPDATA\LOCAL\MICROSOFT\EDGE\USER DATA\VARIATIONS | binary | |
MD5:11B5180FA66C3FA16144BA6D52303FE2 | SHA256:B077B9DB281ED58008156216E7706EEBDF11CD570A943995CBFFA4F88CE80A51 | |||
| 6628 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\777a2b85-19e8-435f-a25b-22c6d47fdbf9.tmp | text | |
MD5:75F04DBAE225F24516B7AEEBFA6D9424 | SHA256:4980E1EAAB806970CA4EC5467267D66ACC13AA141A45618EC9DE28875C1AEDFD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
75
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5756 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
5952 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | der | 814 b | whitelisted |
4736 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | US | der | 471 b | whitelisted |
6400 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | der | 418 b | whitelisted |
5952 | MoUsoCoreWorker.exe | GET | 200 | 95.101.54.128:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | DE | der | 1.11 Kb | whitelisted |
6400 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | der | 409 b | whitelisted |
4736 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://crl3.digicert.com/Omniroot2025.crl | US | der | 7.78 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5952 | MoUsoCoreWorker.exe | 95.101.54.122:80 | — | Akamai International B.V. | DE | suspicious |
4736 | SearchApp.exe | 2.16.186.203:443 | — | Akamai International B.V. | DE | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | suspicious |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 95.101.54.128:80 | — | Akamai International B.V. | DE | suspicious |
5756 | svchost.exe | 20.190.159.75:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 20.190.159.0:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | suspicious |
6400 | SIHClient.exe | 20.114.59.183:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6400 | SIHClient.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officeclient.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
licensing.mp.microsoft.com |
| whitelisted |
l2.pic447.com |
| unknown |