| File name: | _eab74cb48e2926577d16ea10695b75185ca6c4b36f365c117e1cabe4900c6cd2.txt |
| Full analysis: | https://app.any.run/tasks/505813f2-819d-4fab-87a7-f193f96973f8 |
| Verdict: | Malicious activity |
| Analysis date: | August 02, 2025, 04:07:22 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 text, with very long lines (738) |
| MD5: | 1EA32CF0E9D1919FF2BED1E8D79E3BAF |
| SHA1: | C13AA7BAB0AF75936E9CA8D43C97D7020632051C |
| SHA256: | EAB74CB48E2926577D16EA10695B75185CA6C4B36F365C117E1CABE4900C6CD2 |
| SSDEEP: | 192:mkaK9ymziLVWOr2jcyOuME+xOpYGJjxKn60W:mNj0OT9Ox |
MALICIOUS
Deletes shadow copies
- powershell.exe (PID: 1056)
Bypass execution policy to execute commands
- powershell.exe (PID: 1056)
SUSPICIOUS
CSC.EXE is used to compile C# code
- csc.exe (PID: 5236)
- csc.exe (PID: 3052)
Executes as Windows Service
- VSSVC.exe (PID: 4116)
Executable content was dropped or overwritten
- csc.exe (PID: 5236)
- csc.exe (PID: 3052)
Reads security settings of Internet Explorer
- StartMenuExperienceHost.exe (PID: 7008)
Reads the date of Windows installation
- StartMenuExperienceHost.exe (PID: 7008)
- SearchApp.exe (PID: 5676)
Creates new GUID (POWERSHELL)
- powershell.exe (PID: 1056)
Gets path to any of the special folders (POWERSHELL)
- powershell.exe (PID: 1056)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 1056)
INFO
Checks supported languages
- csc.exe (PID: 5236)
- cvtres.exe (PID: 3148)
- TextInputHost.exe (PID: 828)
- StartMenuExperienceHost.exe (PID: 7008)
- cvtres.exe (PID: 6000)
- csc.exe (PID: 3052)
- SearchApp.exe (PID: 5676)
Create files in a temporary directory
- csc.exe (PID: 5236)
- cvtres.exe (PID: 3148)
- csc.exe (PID: 3052)
- cvtres.exe (PID: 6000)
Reads the machine GUID from the registry
- csc.exe (PID: 5236)
- SearchApp.exe (PID: 5676)
- csc.exe (PID: 3052)
Disables trace logs
- powershell.exe (PID: 1056)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 1056)
Checks proxy server information
- powershell.exe (PID: 1056)
- SearchApp.exe (PID: 5676)
- slui.exe (PID: 5308)
Reads the computer name
- StartMenuExperienceHost.exe (PID: 7008)
- TextInputHost.exe (PID: 828)
- SearchApp.exe (PID: 5676)
Process checks computer location settings
- StartMenuExperienceHost.exe (PID: 7008)
- SearchApp.exe (PID: 5676)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1056)
Reads the software policy settings
- SearchApp.exe (PID: 5676)
- slui.exe (PID: 5308)
Reads security settings of Internet Explorer
- notepad.exe (PID: 4820)
Reads Environment values
- SearchApp.exe (PID: 5676)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
153
Monitored processes
15
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 828 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 1056 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\Desktop\_eab74cb48e2926577d16ea10695b75185ca6c4b36f365c117e1cabe4900c6cd2.txt.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1508 | "C:\WINDOWS\system32\vssadmin.exe" delete shadows /all /quiet | C:\Windows\System32\vssadmin.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1592 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | vssadmin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2384 | C:\WINDOWS\System32\mobsync.exe -Embedding | C:\Windows\System32\mobsync.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Sync Center Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3052 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\yoaog0n2.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 3148 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESE990.tmp" "c:\Users\admin\AppData\Local\Temp\CSC259B4C097B44722AB5F43A9371E479F.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 4116 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
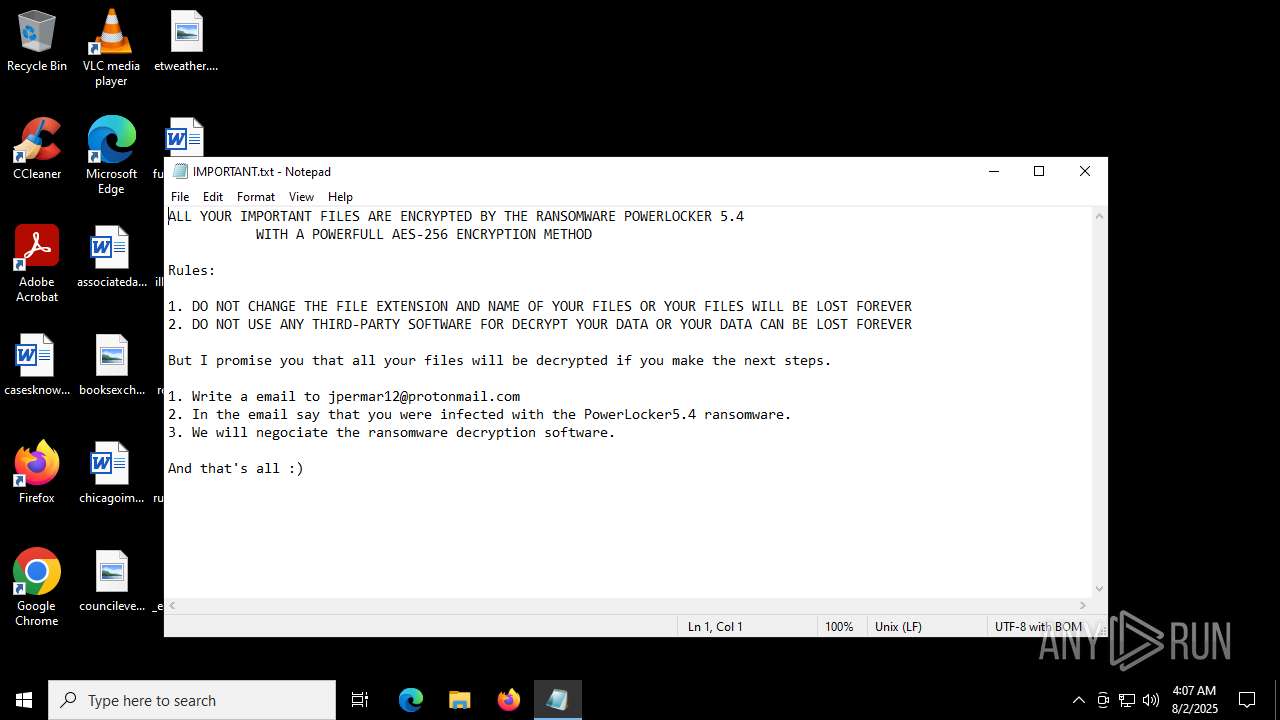
| 4820 | "C:\WINDOWS\system32\notepad.exe" C:\Users\admin\Desktop\IMPORTANT.txt | C:\Windows\System32\notepad.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5236 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\chnzw540.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
Total events
26 570
Read events
26 493
Write events
74
Delete events
3
Modification events
| (PID) Process: | (7008) StartMenuExperienceHost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\TileDataModel\Migration\StartNonLayoutProperties |
| Operation: | write | Name: | Completed |
Value: 1 | |||
| (PID) Process: | (7008) StartMenuExperienceHost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\TileDataModel\Migration\StartNonLayoutProperties_AppUsageData |
| Operation: | write | Name: | Completed |
Value: 1 | |||
| (PID) Process: | (7008) StartMenuExperienceHost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\TileDataModel\Migration\StartNonLayoutProperties_TargetedContentTiles |
| Operation: | write | Name: | Completed |
Value: 1 | |||
| (PID) Process: | (5676) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Flighting |
| Operation: | write | Name: | CachedFeatureString |
Value: | |||
| (PID) Process: | (7008) StartMenuExperienceHost.exe | Key: | \REGISTRY\A\{33d3e75b-3ce0-3cb8-a5e6-26f939fcc9ad}\LocalState\DataCorruptionRecovery |
| Operation: | write | Name: | InitializationAttemptCount |
Value: 01000000B0C3C3FB6203DC01 | |||
| (PID) Process: | (7008) StartMenuExperienceHost.exe | Key: | \REGISTRY\A\{33d3e75b-3ce0-3cb8-a5e6-26f939fcc9ad}\LocalState\DataCorruptionRecovery |
| Operation: | write | Name: | InitializationAttemptCount |
Value: 0000000063F1E9FB6203DC01 | |||
| (PID) Process: | (5676) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | SafeSearchMode |
Value: 1 | |||
| (PID) Process: | (5676) SearchApp.exe | Key: | \REGISTRY\A\{0836b6ad-4f87-ba82-0a59-17a21df12247}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_USEREMAIL |
Value: 0000ED8D06FC6203DC01 | |||
| (PID) Process: | (5676) SearchApp.exe | Key: | \REGISTRY\A\{0836b6ad-4f87-ba82-0a59-17a21df12247}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_ACCOUNTTYPETEXT |
Value: 000015F108FC6203DC01 | |||
| (PID) Process: | (5676) SearchApp.exe | Key: | \REGISTRY\A\{0836b6ad-4f87-ba82-0a59-17a21df12247}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_ACCOUNTTYPE |
Value: 000015F108FC6203DC01 | |||
Executable files
2
Suspicious files
62
Text files
93
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1056 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\EF3SR19WZHVJRQQDPWZQ.temp | binary | |
MD5:AECC159C182B1D1CE9C45E3C76324467 | SHA256:EF506B339BA6C7987F8266FFA1656364ADB2D4E4286F24572973E9362FE92C4D | |||
| 1056 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_cntpxvyb.2dk.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1056 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_v5emcnho.4px.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5676 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\Internet Explorer\DOMStore\ZWUI0EBX\www.bing[1].xml | text | |
MD5:C874A1C6F9110402E921F94E55665B4F | SHA256:8A8680780B0FE29421E300E1A9153504B9545075BF262DDE42995A3F17B0A0C7 | |||
| 1056 | powershell.exe | C:\Users\admin\AppData\Local\Temp\yoaog0n2.cmdline | text | |
MD5:ADA018DD0A316CEA7C771D2E8E1818F7 | SHA256:DA524ABAE9058D618751EBE8E73ED148DD69E33A2B71427B86D9CB19332F8A57 | |||
| 5676 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\TokenBroker\Cache\fbaf94e759052658216786bfbabcdced1b67a5c2.tbres | binary | |
MD5:F6DB36CF724112144FBA4A5237E549F6 | SHA256:2D4C4B5326042D92CE1954C2A3D9172328432517433C8D1CA24E5226D6E357BE | |||
| 5236 | csc.exe | C:\Users\admin\AppData\Local\Temp\chnzw540.dll | executable | |
MD5:A93C15316AEB5AE3DE831F199E7CE1F7 | SHA256:F9F0AFE491C7D18441DCE9F857BC336693DEC57A527ADD45DD7A63E77733A36E | |||
| 1056 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:AECC159C182B1D1CE9C45E3C76324467 | SHA256:EF506B339BA6C7987F8266FFA1656364ADB2D4E4286F24572973E9362FE92C4D | |||
| 5236 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC259B4C097B44722AB5F43A9371E479F.TMP | res | |
MD5:05647F2F184FE79875D9D7DB56579151 | SHA256:8C9CE6989C7EFCF4698EE44EF23AACFBB3063036AE0E60DF67E5D59017CED809 | |||
| 1056 | powershell.exe | C:\Users\admin\AppData\Local\Temp\chnzw540.0.cs | text | |
MD5:01E34DA9E9534A23AC0F14C28EE69ACE | SHA256:E2715D4FC9403E89A2931A24E90278EFDFF72ADC86AD80739FF089A22CEEA467 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
48
TCP/UDP connections
22
DNS requests
9
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3584 | RUXIMICS.exe | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3584 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 404 | 172.66.169.189:443 | https://wallpapercave.com/uwp/uwp4766244.png | unknown | html | 68.5 Kb | whitelisted |
— | — | GET | 200 | 92.123.104.31:443 | https://www.bing.com/manifest/threshold.appcache | unknown | text | 2.97 Kb | whitelisted |
— | — | GET | 200 | 92.123.104.32:443 | https://www.bing.com/rb/18/jnc,nj/6hU_LneafI_NFLeDvM367ebFaKQ.js?bu=DyIrb3t-gQF4cnWyAbUBK6UBK7gB&or=w | unknown | binary | 21.3 Kb | whitelisted |
— | — | GET | 200 | 92.123.104.52:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Init | unknown | html | 132 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3584 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3584 | RUXIMICS.exe | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
wallpapercave.com |
| whitelisted |
www.bing.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |