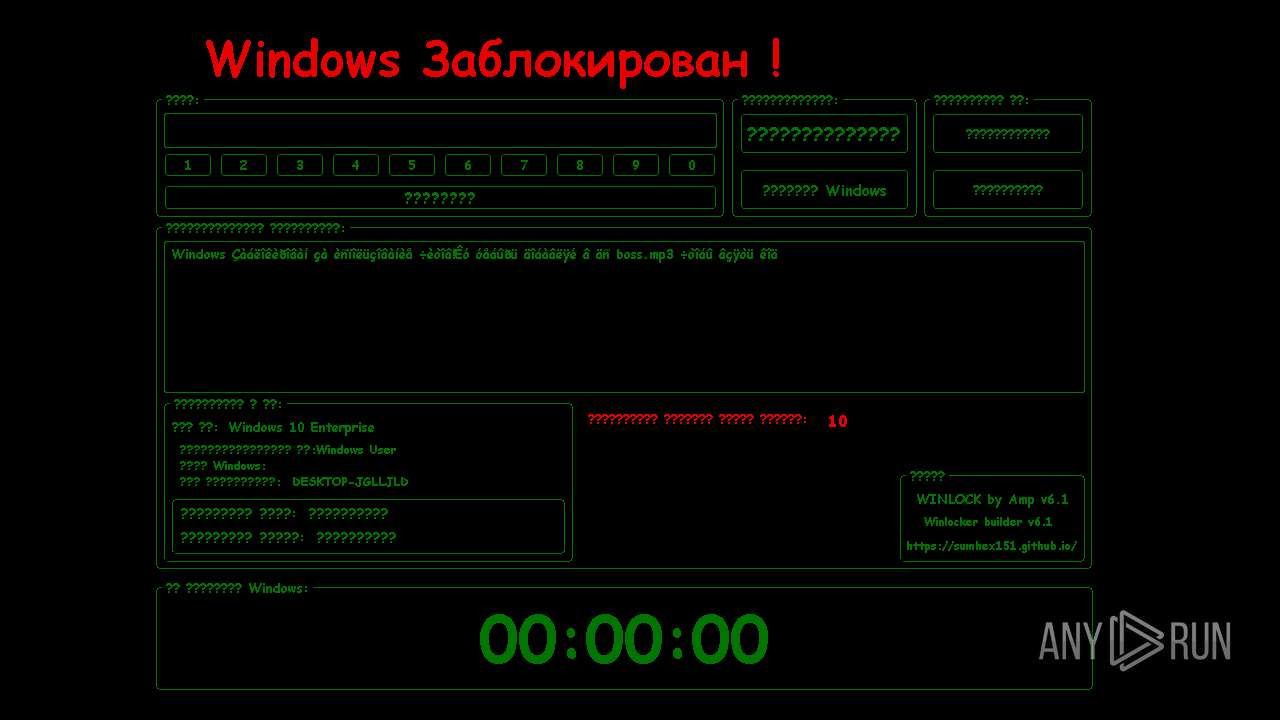
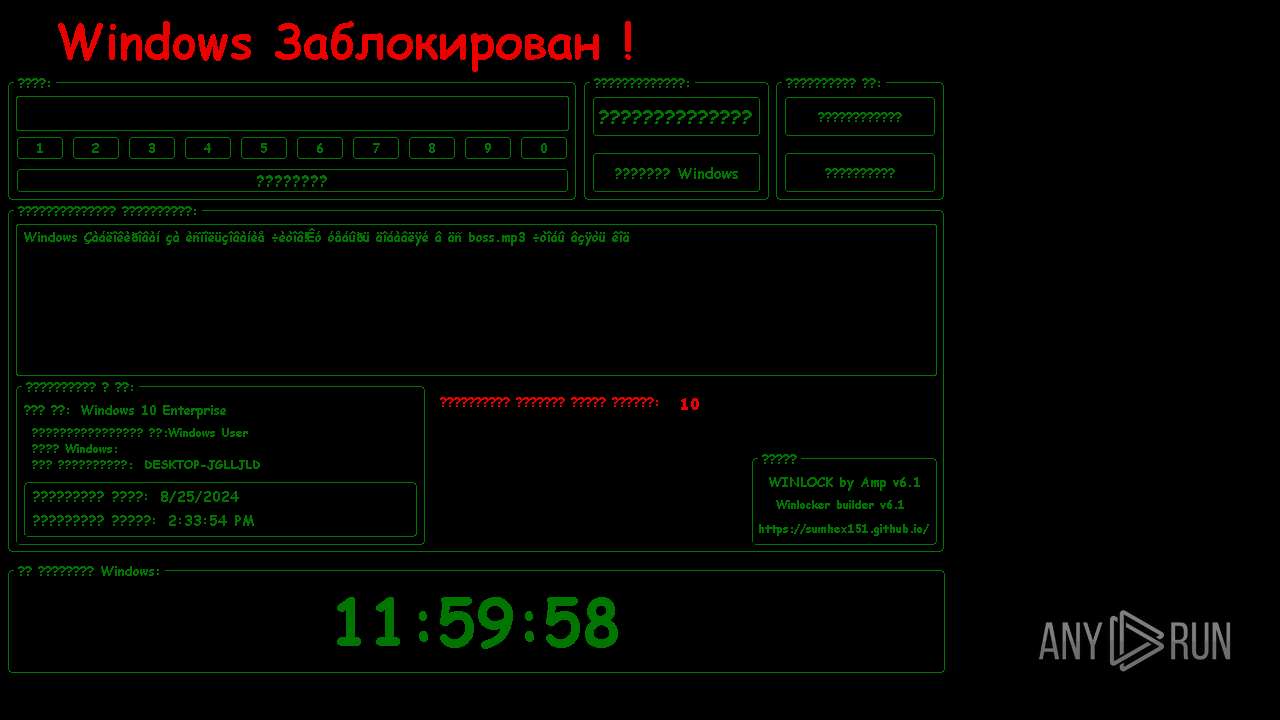
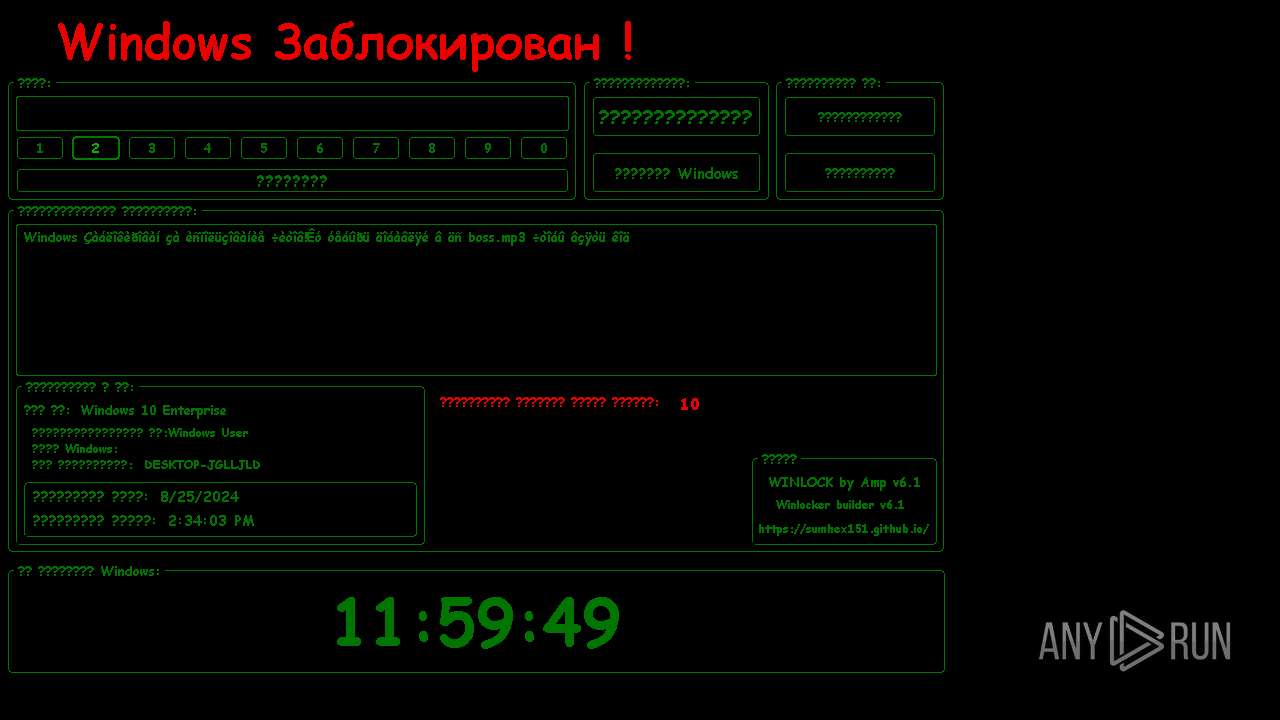
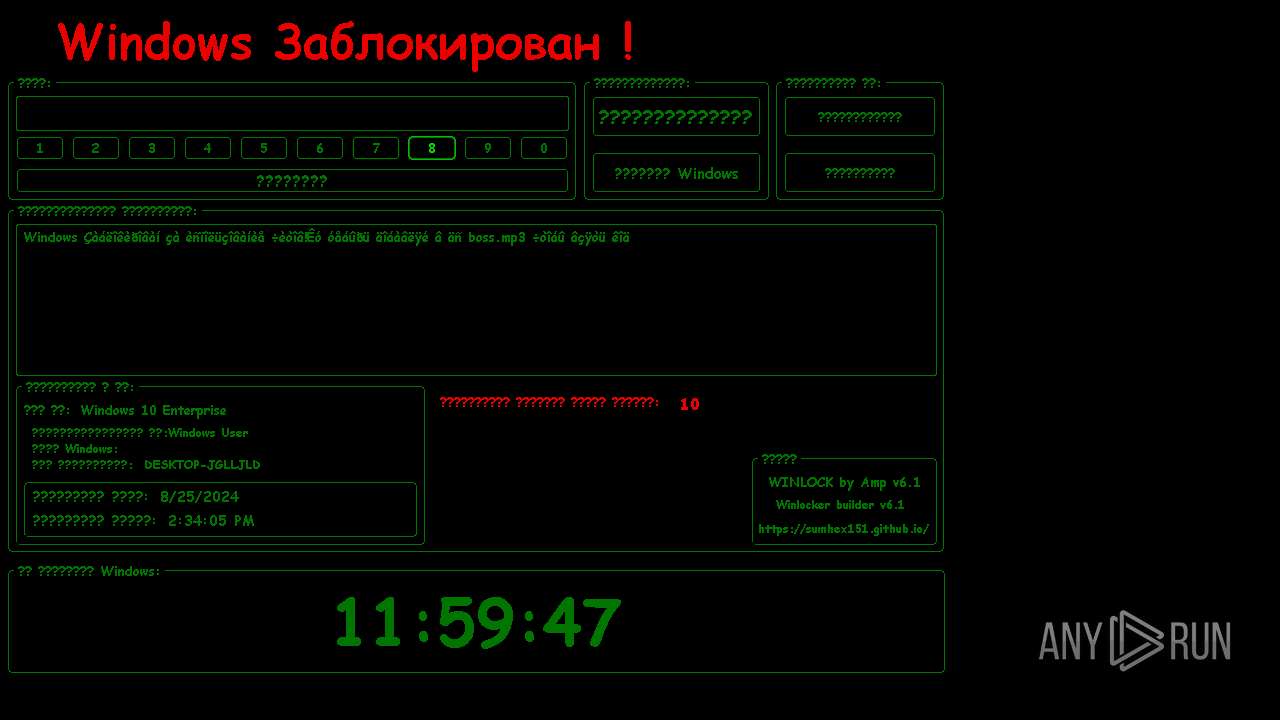
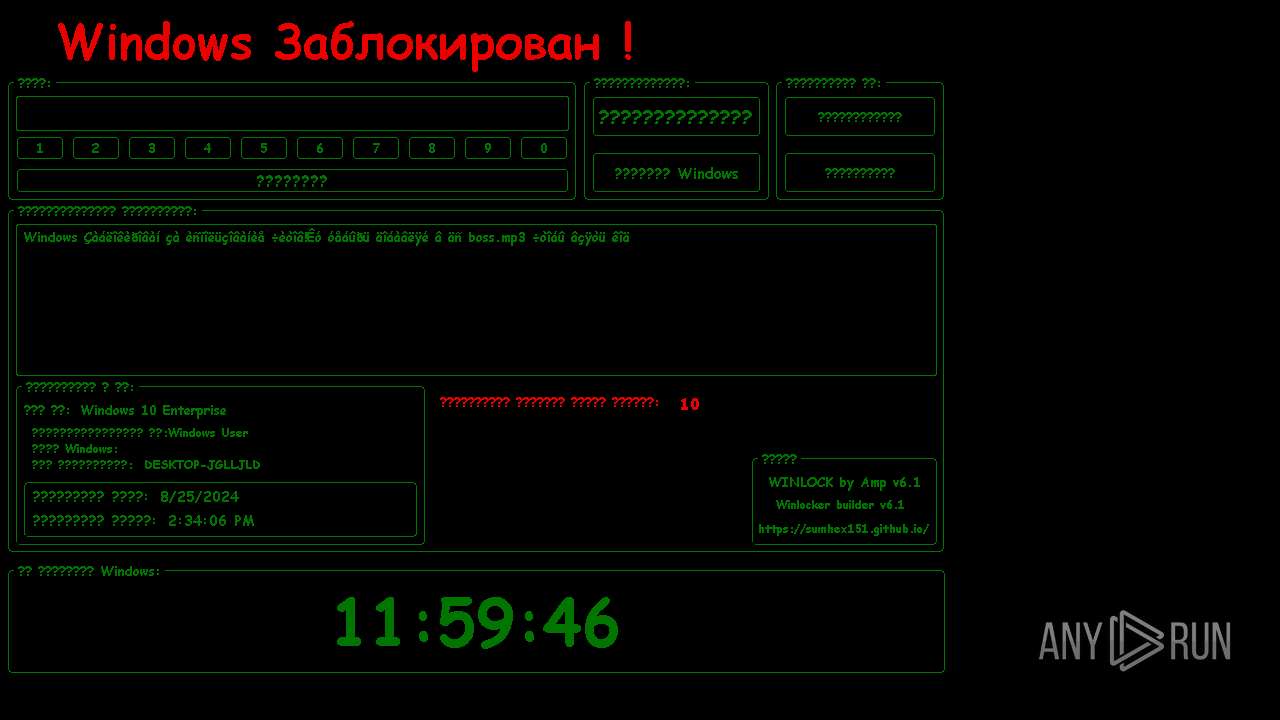
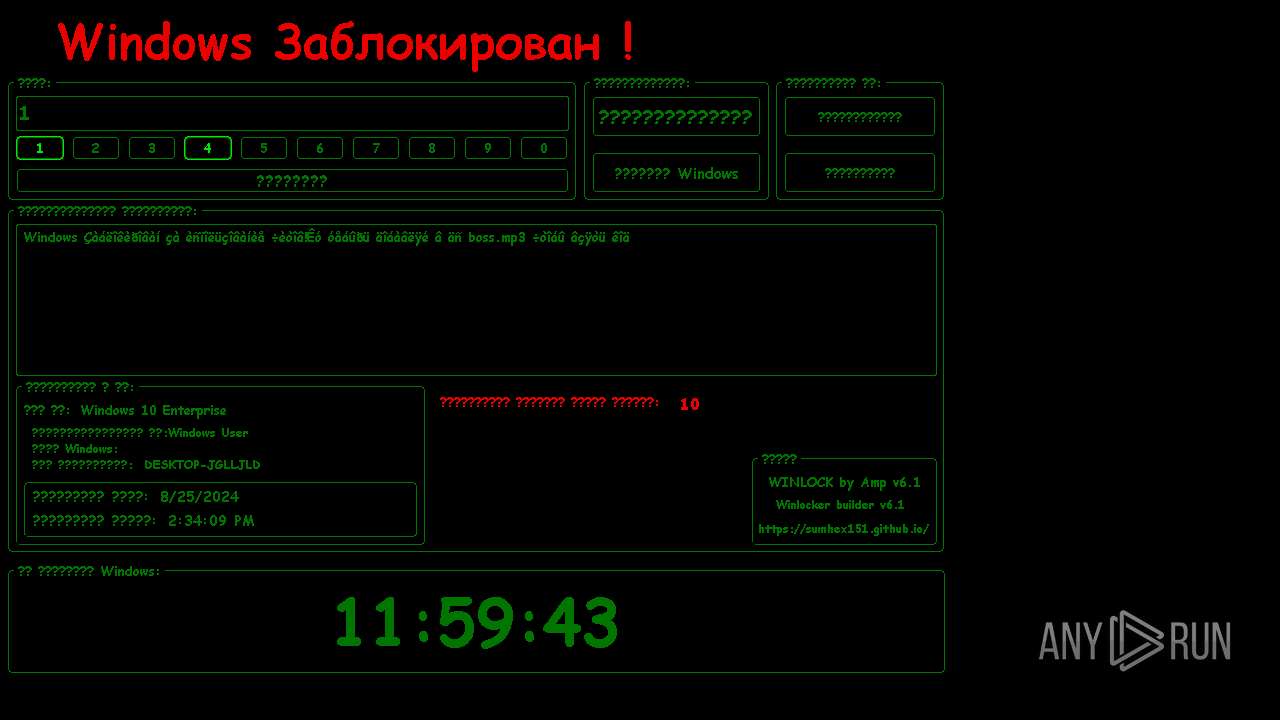
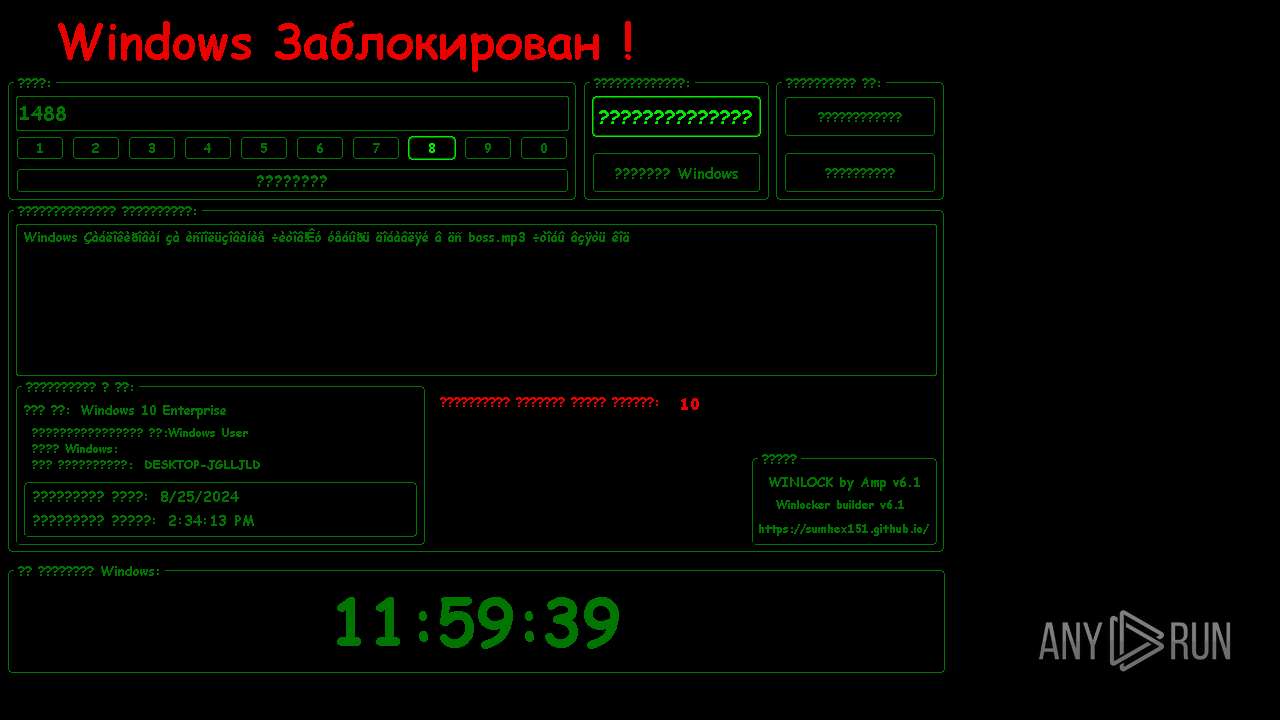
| File name: | WinLocker.exe |
| Full analysis: | https://app.any.run/tasks/2246047f-d7b1-4166-9944-00c5786876d2 |
| Verdict: | Malicious activity |
| Analysis date: | August 25, 2024, 14:33:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 88C574CE28B1FEEAB4C6C1CBB781F421 |
| SHA1: | EA6AB2E1EE21BCEC0B23ABCCD2221D69A5013A2C |
| SHA256: | EAA737ADA3D93DBCE50FD1251F6AADEE1CC3221C0389E58F1745B35AB5EA278B |
| SSDEEP: | 98304:9cCyub1kqAzajfr/qSRmkgT9908yj2fBRhdLfCdat6zcMlU3UJfdA48X6GM+l:Grj |
MALICIOUS
Changes the autorun value in the registry
- WinLocker.exe (PID: 6692)
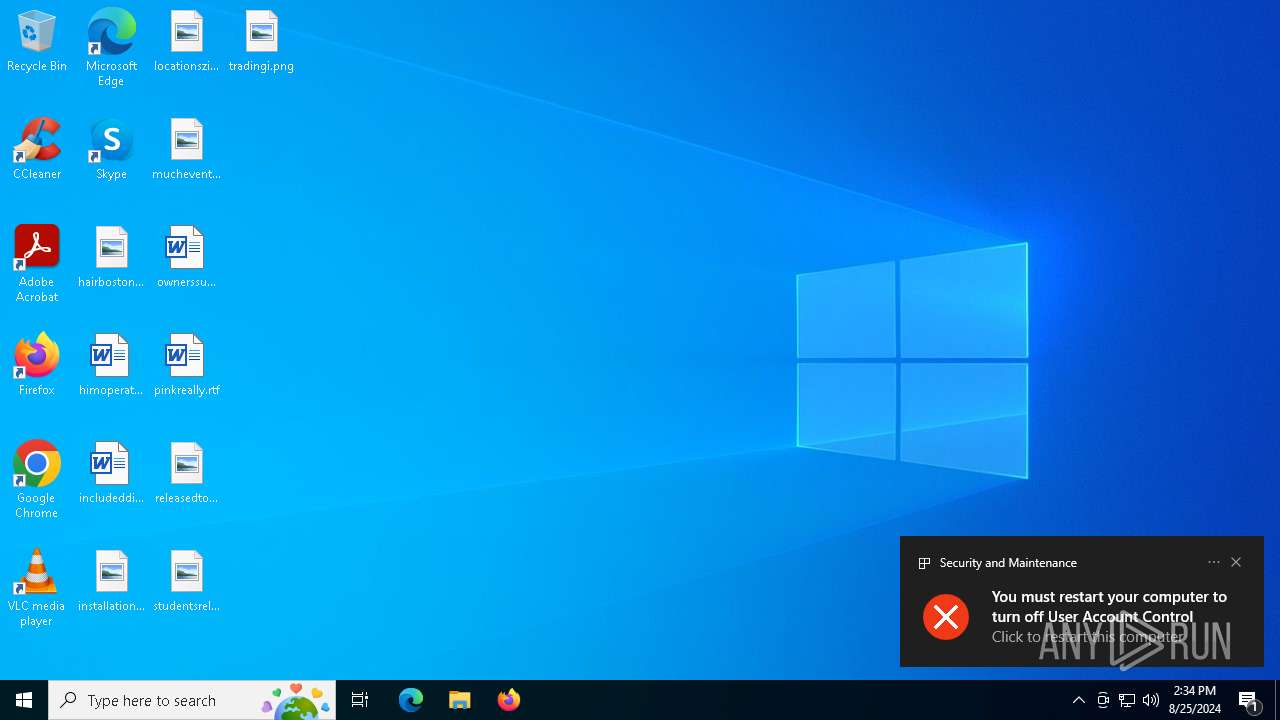
UAC/LUA settings modification
- WinLocker.exe (PID: 6692)
Disables the LogOff the Start menu
- WinLocker.exe (PID: 6692)
Disables the Find the Start menu
- WinLocker.exe (PID: 6692)
Disables the Run the Start menu
- WinLocker.exe (PID: 6692)
Changes image file execution options
- WinLocker.exe (PID: 6692)
Disables the Shutdown in the Start menu
- WinLocker.exe (PID: 6692)
SUSPICIOUS
Drops the executable file immediately after the start
- WinLocker.exe (PID: 6692)
Reads the Windows owner or organization settings
- WinLocker.exe (PID: 6692)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 6788)
- GameBar.exe (PID: 6632)
- WinLocker.exe (PID: 6692)
- StartMenuExperienceHost.exe (PID: 6920)
- ShellExperienceHost.exe (PID: 5720)
There is functionality for taking screenshot (YARA)
- WinLocker.exe (PID: 6692)
Reads the date of Windows installation
- WinLocker.exe (PID: 6692)
- StartMenuExperienceHost.exe (PID: 6920)
The process executes via Task Scheduler
- explorer.exe (PID: 1292)
INFO
Checks supported languages
- WinLocker.exe (PID: 6692)
- ShellExperienceHost.exe (PID: 6788)
- GameBar.exe (PID: 6632)
- TextInputHost.exe (PID: 6760)
- ShellExperienceHost.exe (PID: 5720)
- StartMenuExperienceHost.exe (PID: 6920)
- SearchApp.exe (PID: 3144)
Reads Windows Product ID
- WinLocker.exe (PID: 6692)
Reads the computer name
- WinLocker.exe (PID: 6692)
- ShellExperienceHost.exe (PID: 6788)
- GameBar.exe (PID: 6632)
- ShellExperienceHost.exe (PID: 5720)
- TextInputHost.exe (PID: 6760)
- StartMenuExperienceHost.exe (PID: 6920)
- SearchApp.exe (PID: 3144)
Reads Environment values
- WinLocker.exe (PID: 6692)
- SearchApp.exe (PID: 3144)
Create files in a temporary directory
- WinLocker.exe (PID: 6692)
Reads security settings of Internet Explorer
- explorer.exe (PID: 1292)
Reads Microsoft Office registry keys
- explorer.exe (PID: 1292)
Process checks computer location settings
- WinLocker.exe (PID: 6692)
- SearchApp.exe (PID: 3144)
- StartMenuExperienceHost.exe (PID: 6920)
Checks proxy server information
- explorer.exe (PID: 1292)
- SearchApp.exe (PID: 3144)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 3144)
Process checks Internet Explorer phishing filters
- SearchApp.exe (PID: 3144)
Reads the software policy settings
- SearchApp.exe (PID: 3144)
Creates files or folders in the user directory
- explorer.exe (PID: 1292)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Borland Delphi 7 (94.6) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (2) |
| .scr | | | Windows screen saver (1.8) |
| .exe | | | Win32 Executable (generic) (0.6) |
| .exe | | | Win16/32 Executable Delphi generic (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 1146368 |
| InitializedDataSize: | 1500160 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x118d94 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
142
Monitored processes
12
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1128 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | WinLocker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 2 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1292 | "C:\Windows\explorer.exe" /NoUACCheck | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3144 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4892 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5720 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6032 | C:\WINDOWS\System32\mobsync.exe -Embedding | C:\Windows\System32\mobsync.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Sync Center Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6632 | "C:\Program Files\WindowsApps\Microsoft.XboxGamingOverlay_2.34.28001.0_x64__8wekyb3d8bbwe\GameBar.exe" -ServerName:App.AppXbdkk0yrkwpcgeaem8zk81k8py1eaahny.mca | C:\Program Files\WindowsApps\Microsoft.XboxGamingOverlay_2.34.28001.0_x64__8wekyb3d8bbwe\GameBar.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 6644 | "C:\Users\admin\AppData\Local\Temp\WinLocker.exe" | C:\Users\admin\AppData\Local\Temp\WinLocker.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6692 | "C:\Users\admin\AppData\Local\Temp\WinLocker.exe" | C:\Users\admin\AppData\Local\Temp\WinLocker.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 6760 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
Total events
46 044
Read events
45 735
Write events
265
Delete events
44
Modification events
| (PID) Process: | (6692) WinLocker.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Windows\System |
| Operation: | write | Name: | DisableCMD |
Value: 2 | |||
| (PID) Process: | (6692) WinLocker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (6692) WinLocker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Java |
Value: C:\Users\admin\AppData\Local\Temp\WinLocker.exe | |||
| (PID) Process: | (6692) WinLocker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\explorer.exe |
| Operation: | write | Name: | Debugger |
Value: C:\Users\admin\AppData\Local\Temp\WinLocker.exe | |||
| (PID) Process: | (6692) WinLocker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\taskmgr.exe |
| Operation: | write | Name: | Debugger |
Value: C:\Users\admin\AppData\Local\Temp\WinLocker.exe | |||
| (PID) Process: | (6692) WinLocker.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Uninstall |
| Operation: | write | Name: | NoAddRemovePrograms |
Value: 1 | |||
| (PID) Process: | (6692) WinLocker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | HideFastUserSwitching |
Value: 1 | |||
| (PID) Process: | (6692) WinLocker.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Advanced |
| Operation: | write | Name: | NoClose |
Value: 1 | |||
| (PID) Process: | (6692) WinLocker.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableLockWorkstation |
Value: 1 | |||
| (PID) Process: | (6692) WinLocker.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableChangePassword |
Value: 1 | |||
Executable files
2
Suspicious files
13
Text files
152
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6692 | WinLocker.exe | C:\Users\admin\AppData\Local\Temp\Time.ini | text | |
MD5:EB13B7EAF7F30D348E471F0907B31AAC | SHA256:94BA214735774FB4E68BE906C3E181D29C71DBBCD10540E70BA7021FCF5EA3AA | |||
| 3144 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\64\UOY0_NvaNmYOaPCm0BTcnmMvX60[1].css | text | |
MD5:0FF1F38355538E225067A8B7C2BB1A05 | SHA256:E4F9D9E92CB3B6C0C44514EEF214F436ED3D5EB048FA2480DE059A82BD1B00D1 | |||
| 3144 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\64\CYGXBN1kkA_ojDY5vKbCoG4Zy0E[1].css | text | |
MD5:DF25912CCFEE50A9E57BC97B4D05B5C0 | SHA256:3CA3D1262A62E919C72A641F7491B38769CFB8149704E69CB6C960836DD9C6F8 | |||
| 3144 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:85770E04C47BBC69B9EF0065BFC13A70 | SHA256:70561937109CAF210C0B3D7C7C361C5A3D362895BAB381C2AF5B9FBDC6D087FC | |||
| 3144 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\64\4-xJy3tX6bM2BGl5zKioiEcQ1TU[1].css | text | |
MD5:B8C89E50D1A8DF3954C30836B80AFA47 | SHA256:F63656D5FE0A12D00F9FD662236FE996E18F036435781B1824F51C5B2BA935EC | |||
| 3144 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\Internet Explorer\DOMStore\ZWUI0EBX\www.bing[1].xml | text | |
MD5:ABB149ECECF385A201A69AAA2A6B2402 | SHA256:60DF762B2681FEEB0C7F0BEE3472C0406B993E08C7040D03F3511B4AA1634AC5 | |||
| 4892 | TiWorker.exe | C:\Windows\Logs\CBS\CBS.log | text | |
MD5:3C59445785D7107AD887453F665BDDB5 | SHA256:DD36690DDAF032984FBBC87B921A0169E7481FFD6A312AF8112B4B682488F0E7 | |||
| 3144 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\INetCache\M8N5R19A\th[1].svg | image | |
MD5:48E632A133BAE466E88AD5B3D0117000 | SHA256:2BC5C4074744AC3C2D4FD718ED8E5B804E61E9108E940BF86E79CAB0BD05C096 | |||
| 3144 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\64\oT6Um3bDKq3bSDJ4e0e-YJ5MXCI[1].css | text | |
MD5:212CA645026552E6E0430DD815E209A8 | SHA256:C7DE31F7449EB7373452E3F942A2B070BC5893087C5BB2BC50E565244DA70CD3 | |||
| 3144 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\INetCache\P26HLZ9S\th[2].svg | image | |
MD5:EE5331E5BFCC9D2451F74B9EDA5C56FF | SHA256:97E59357EC4E81097F5C3713E55377AFD0144358C41746A4ED5951E840CDD592 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
27
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
812 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3144 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5876 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5876 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1344 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1432 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1432 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
812 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
r.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |
www.microsoft.com |
| whitelisted |