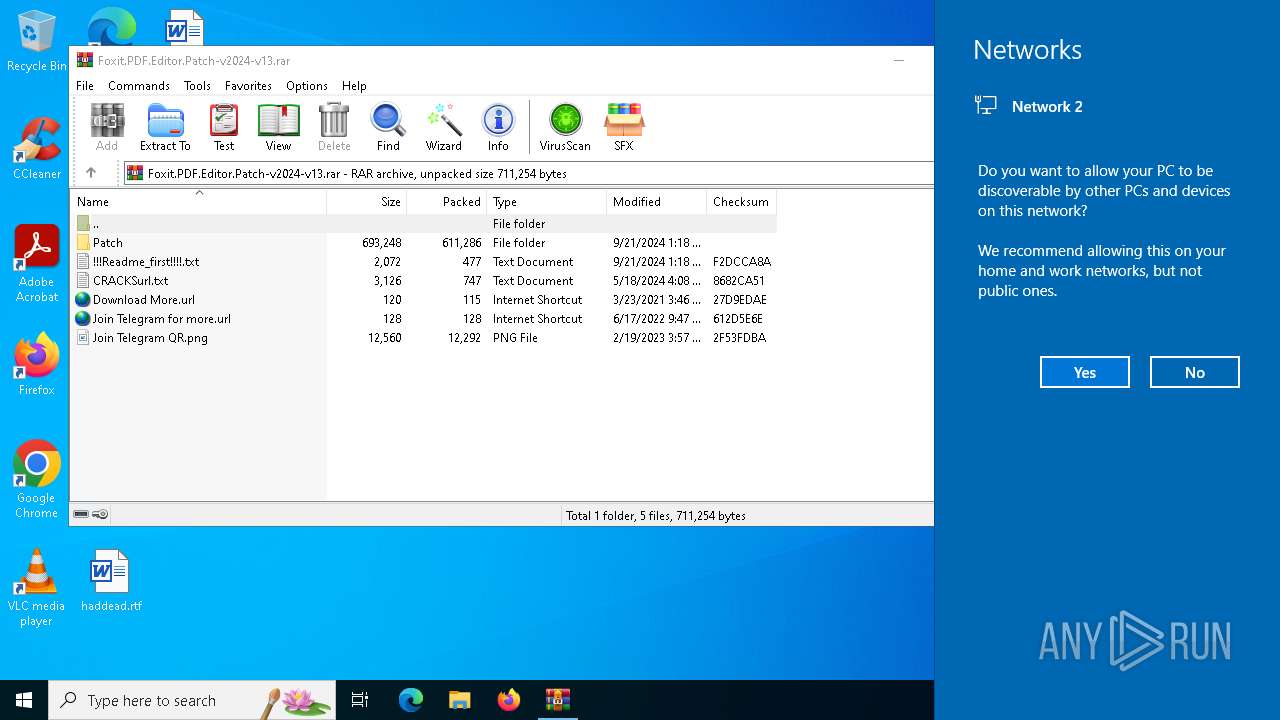
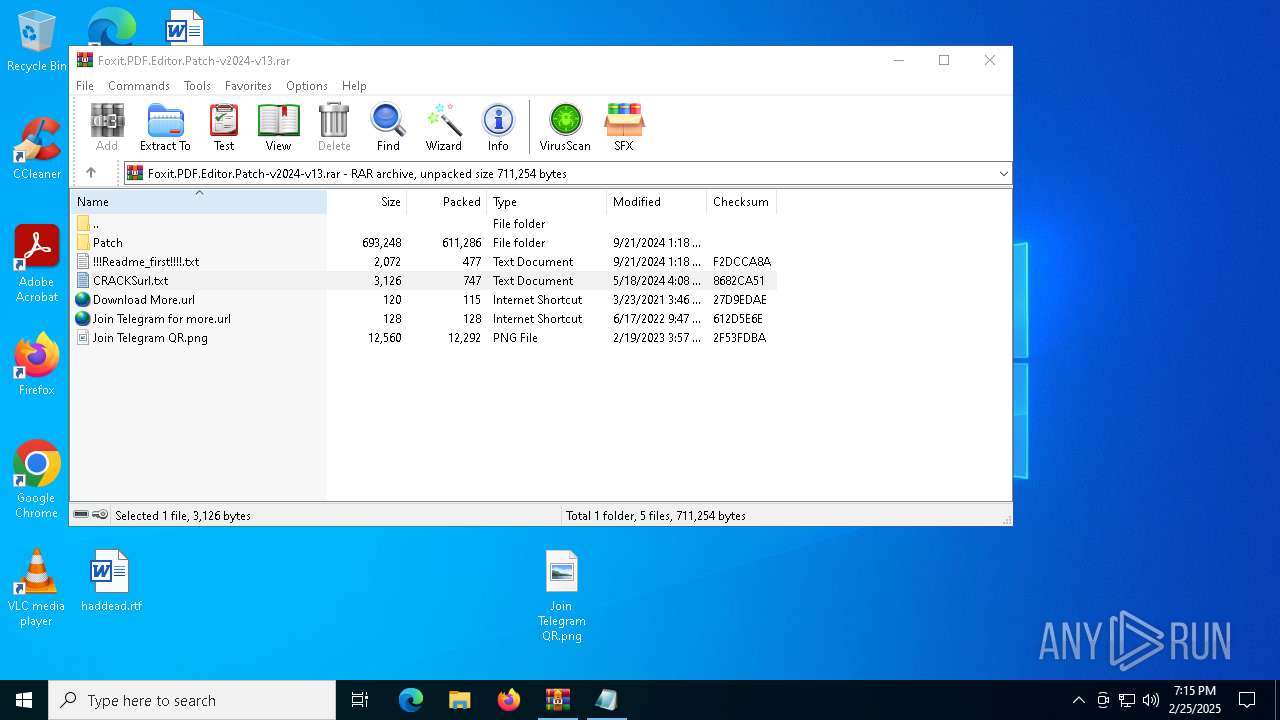
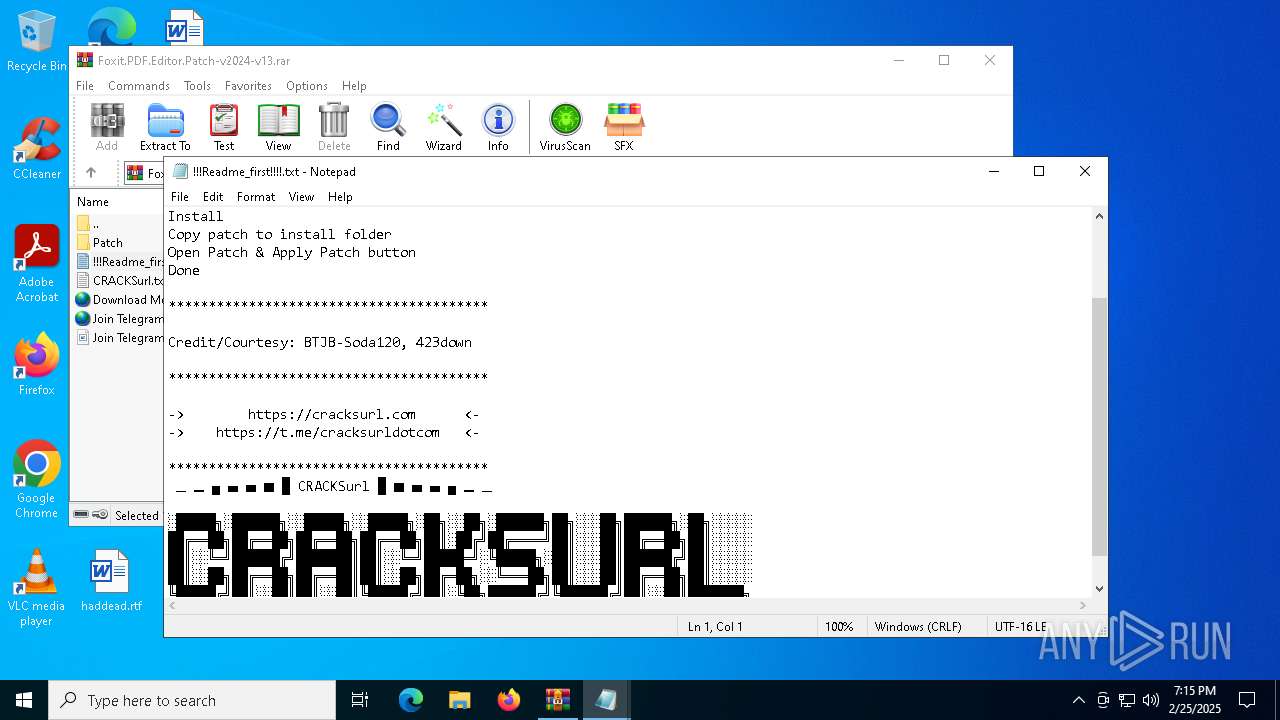
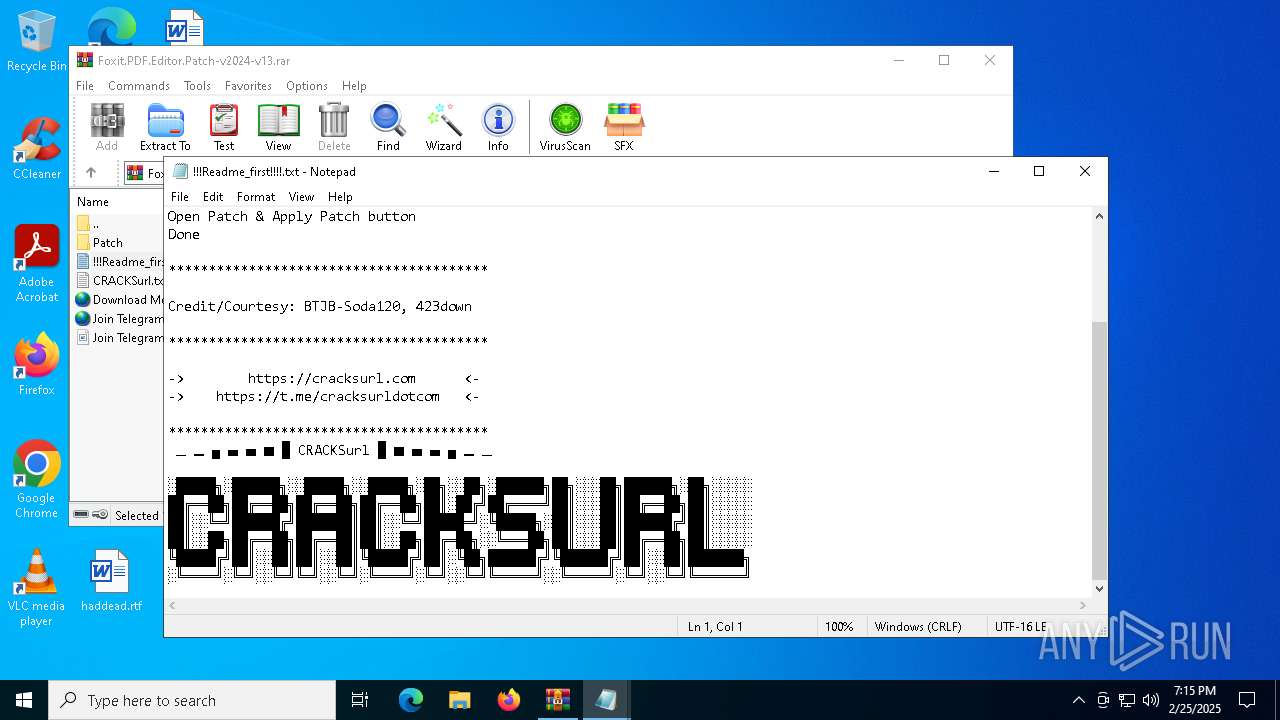
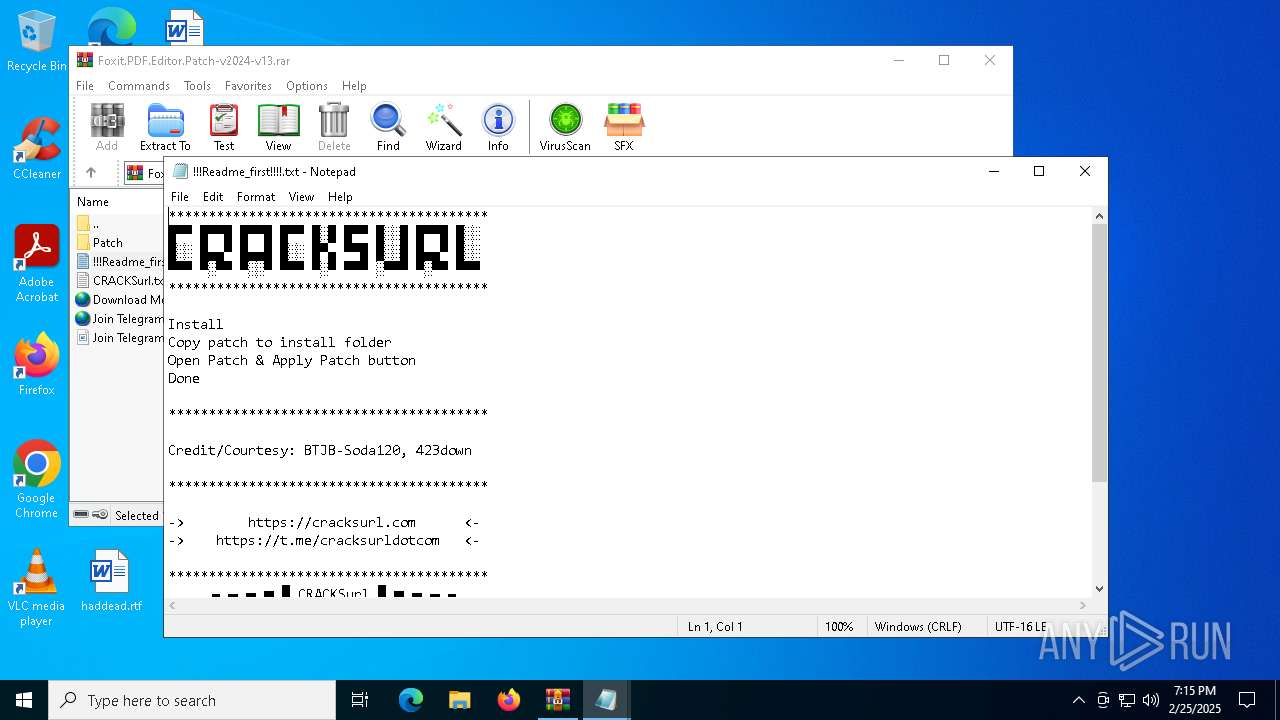
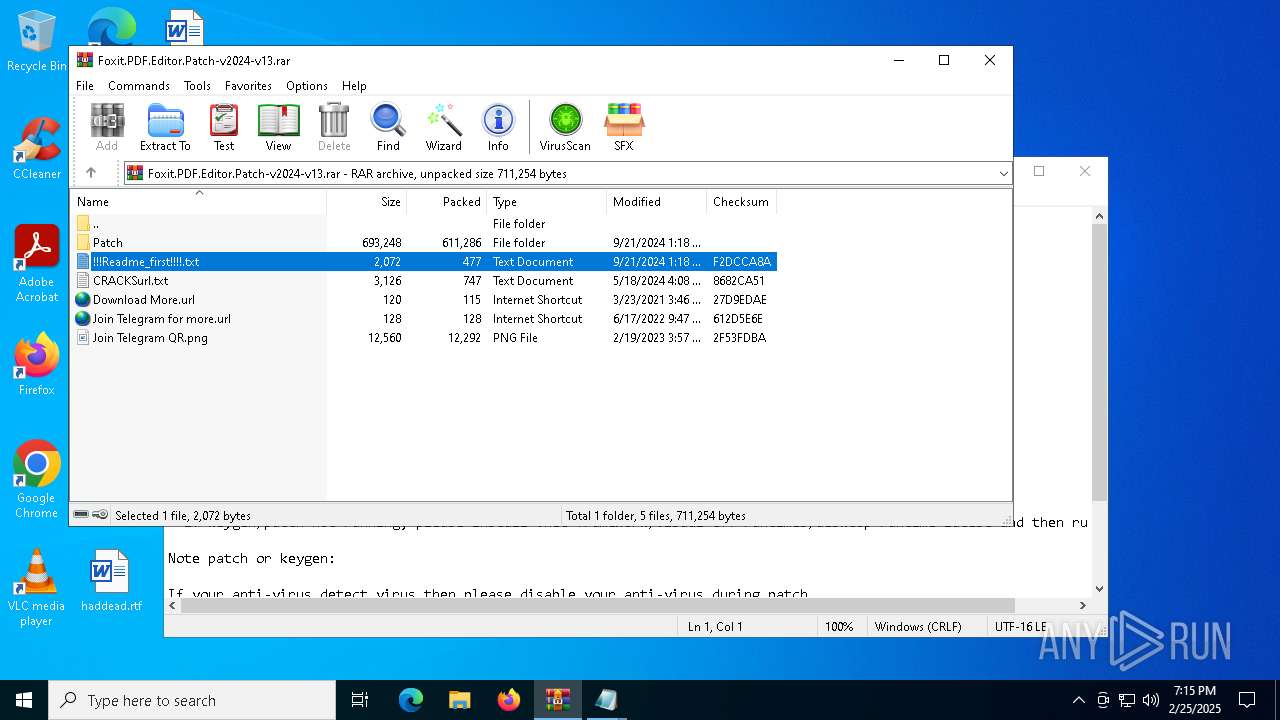
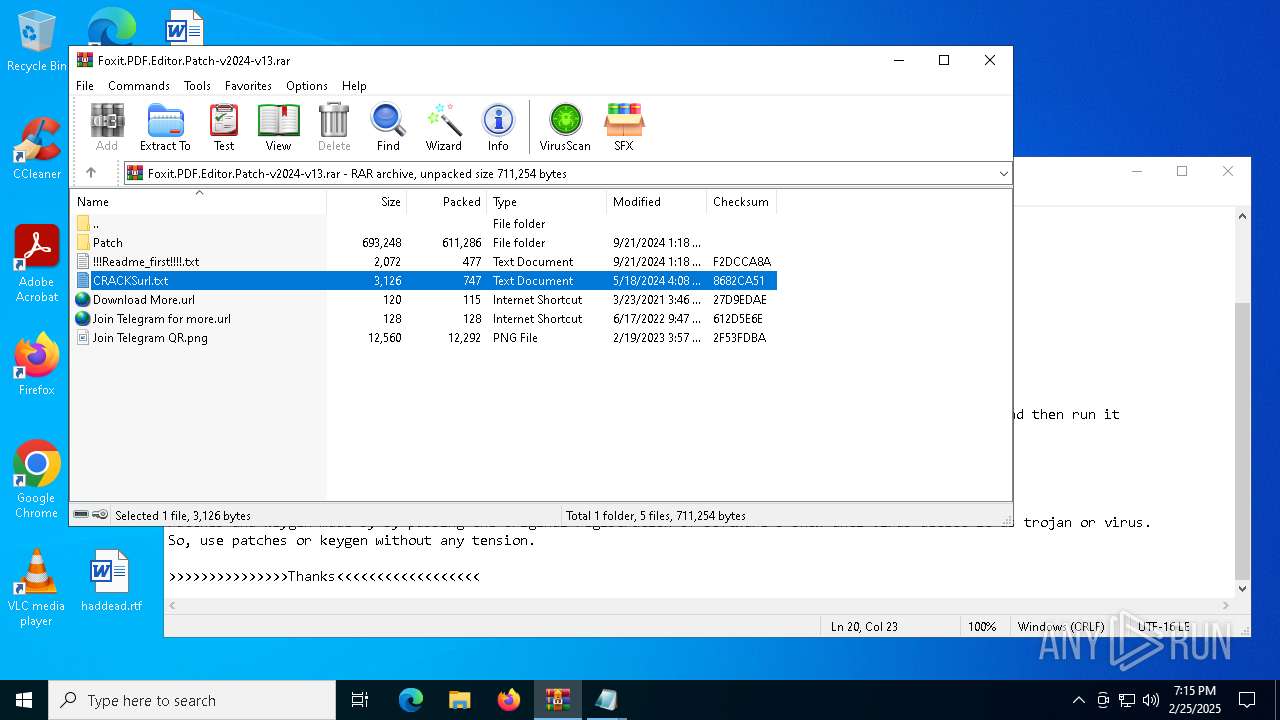
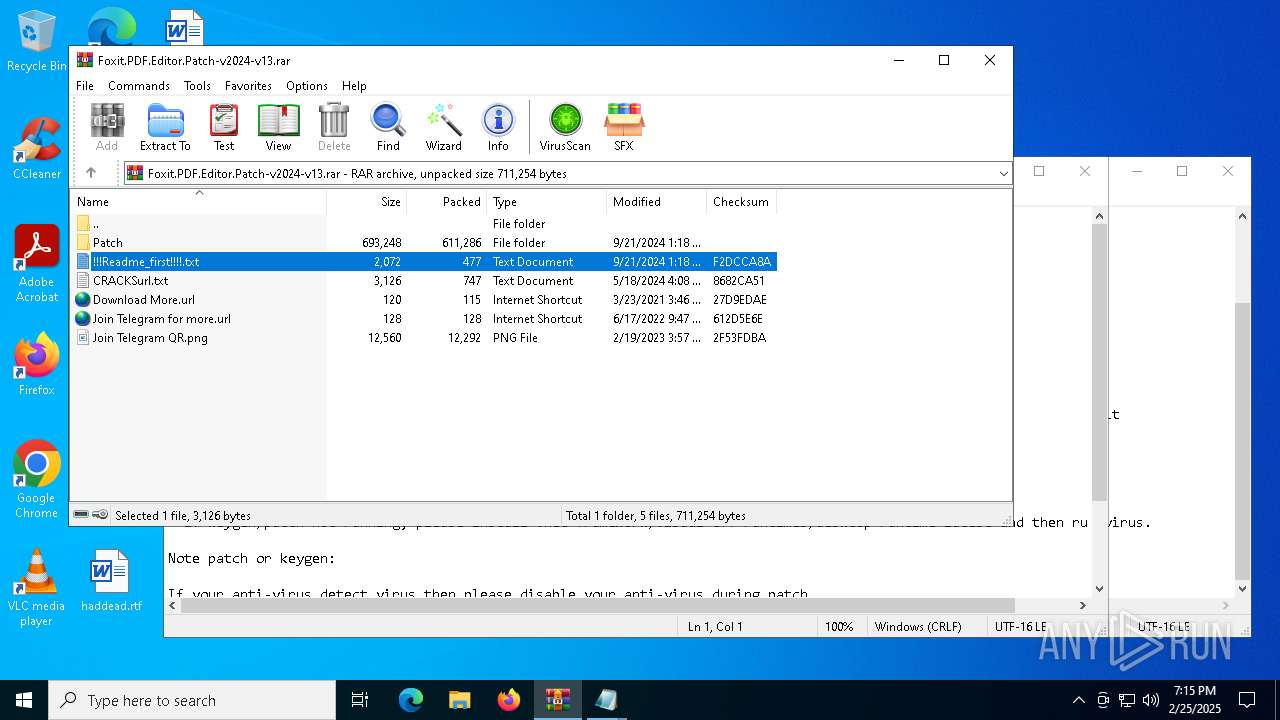
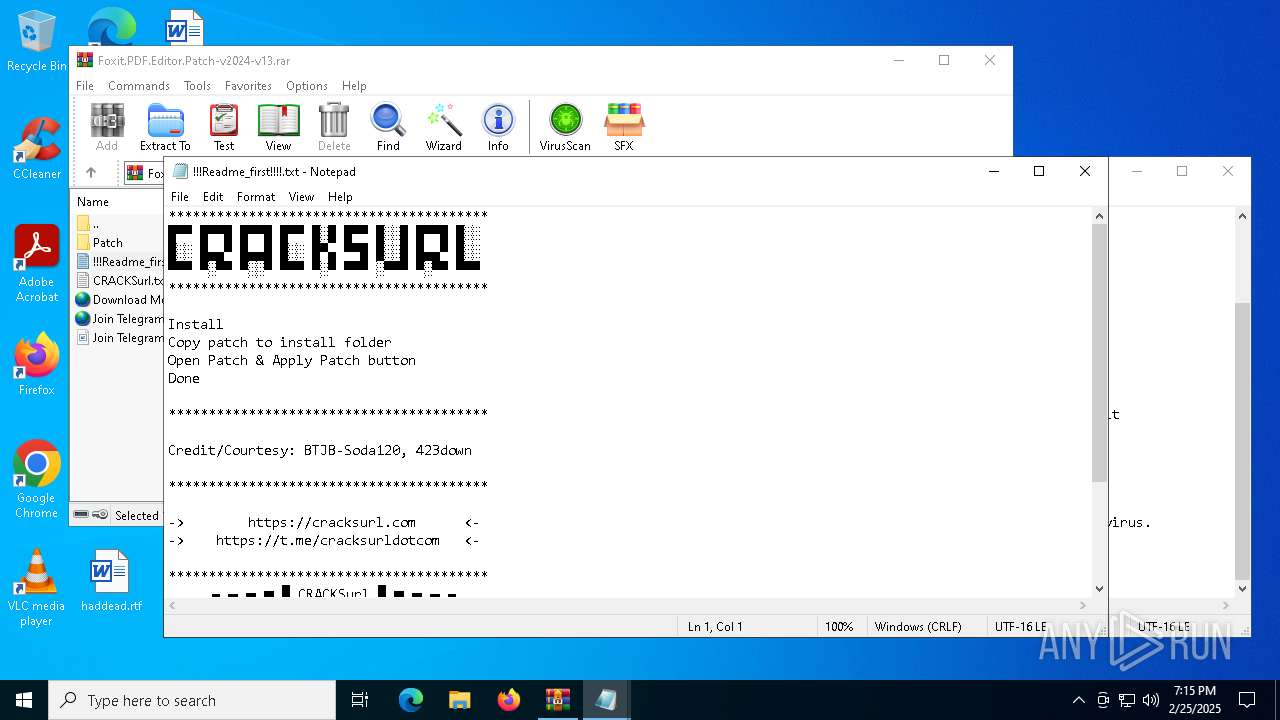
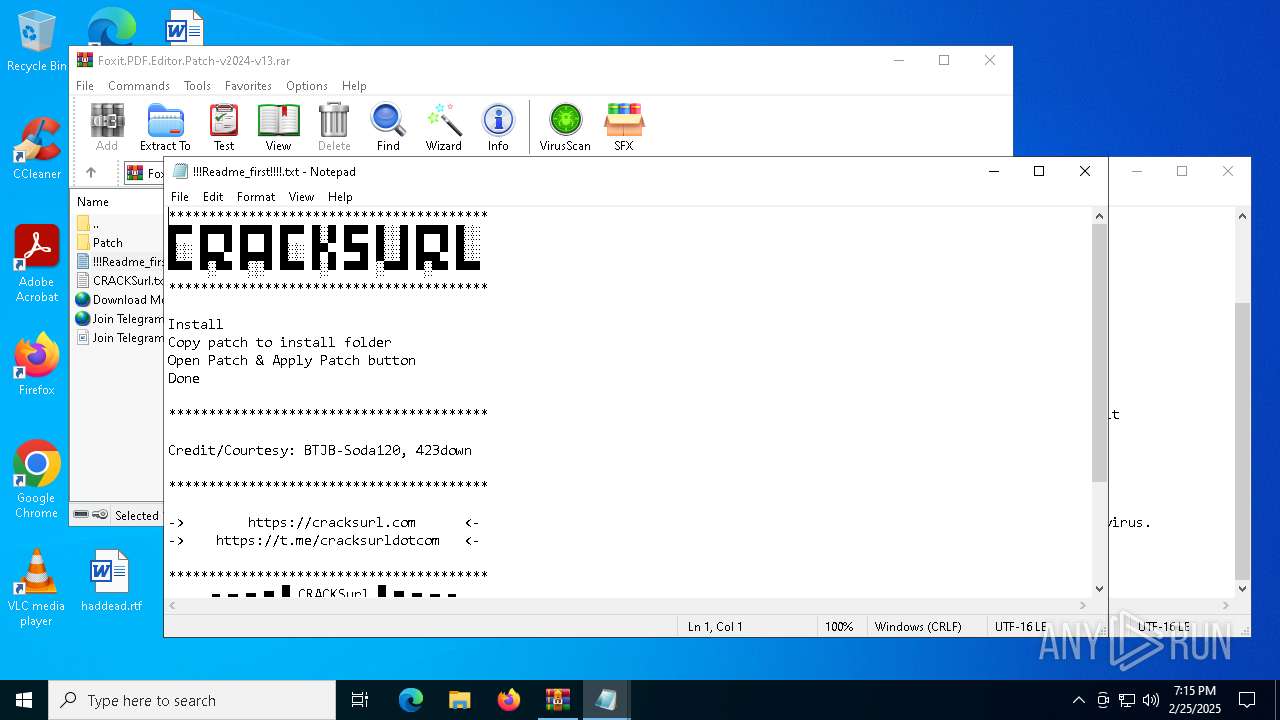
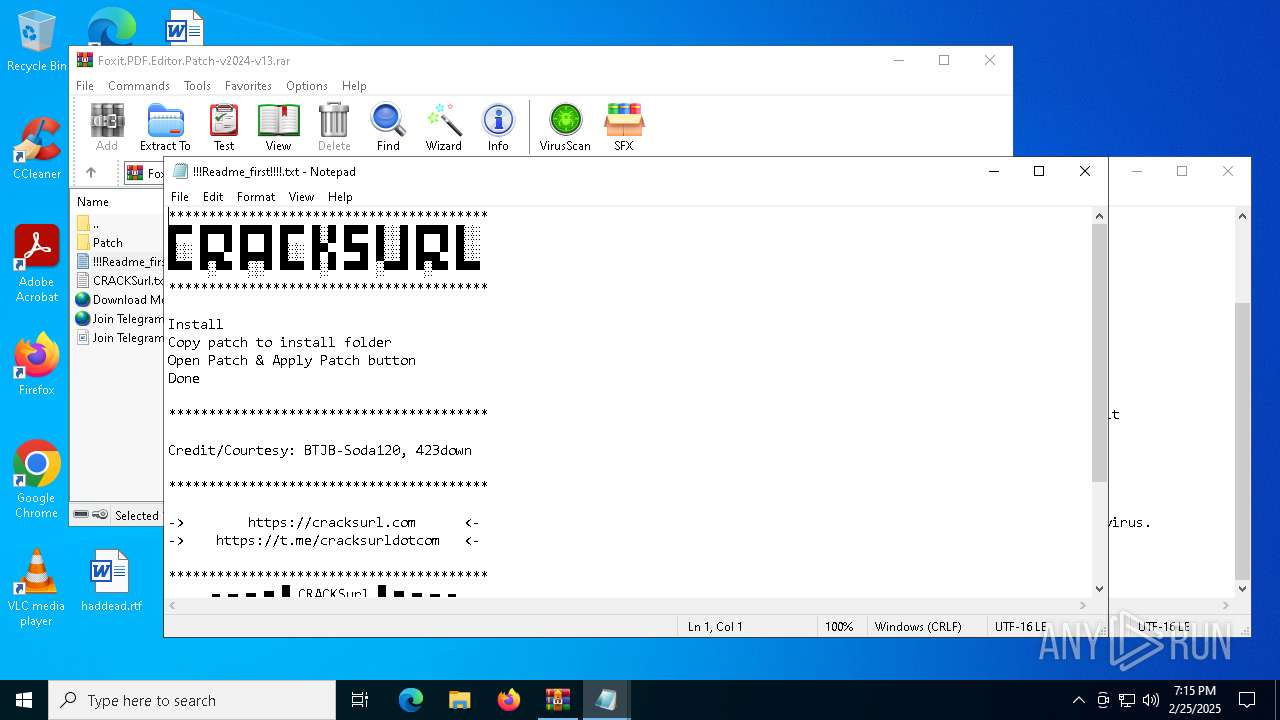
| File name: | Foxit.PDF.Editor.Patch-v2024-v13.rar |
| Full analysis: | https://app.any.run/tasks/19e3a0d6-62c3-4c1d-bc3b-c9f7ab0b81b2 |
| Verdict: | Malicious activity |
| Analysis date: | February 25, 2025, 19:13:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 6F8FE04933C88323B46042448C0C6932 |
| SHA1: | 9D5FB8B0CA8F9253B3641046AF928AB84711B277 |
| SHA256: | EAA6910D6AE5EB8E044F0E46FE73002EF0264273D800865B6D43DB18AC45D0C5 |
| SSDEEP: | 24576:3bVpBcFvBLZd6/c9juCFU8Y70Lp7coOdVwg07ut3zuyB:3bVpBcJBLZd6/c9juCFU8Y70Lp7coOfV |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 3560)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3560)
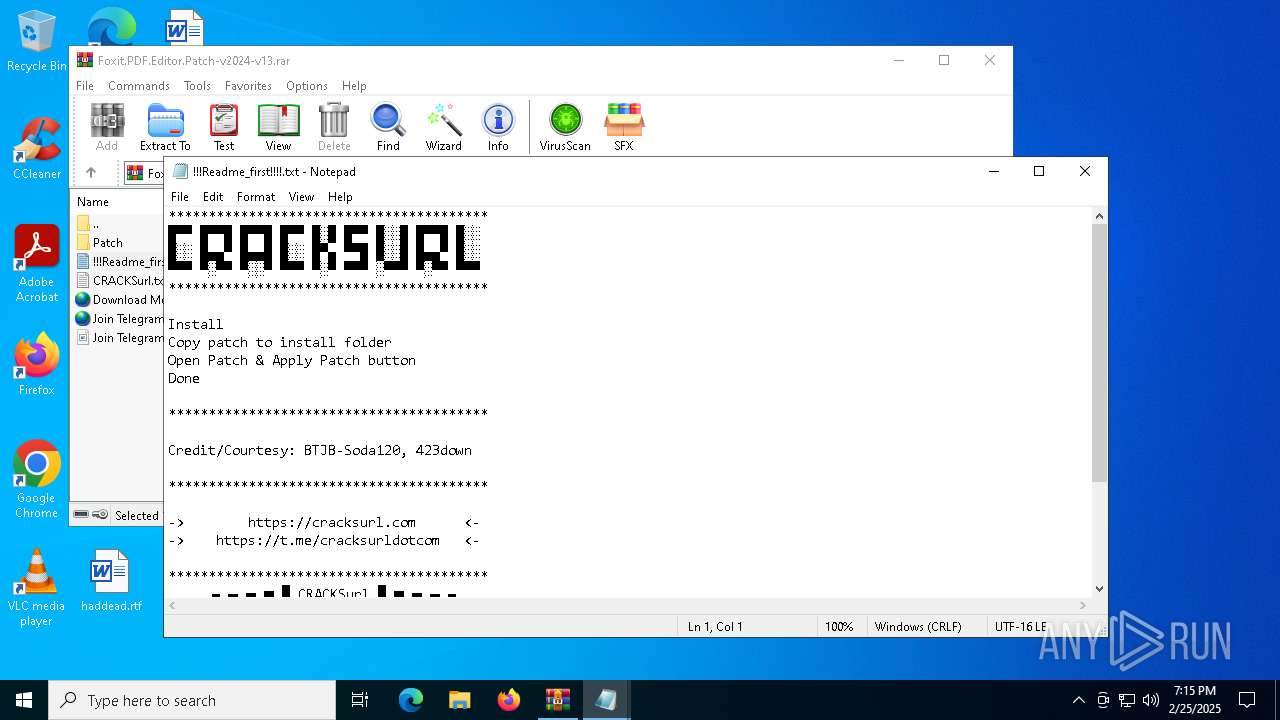
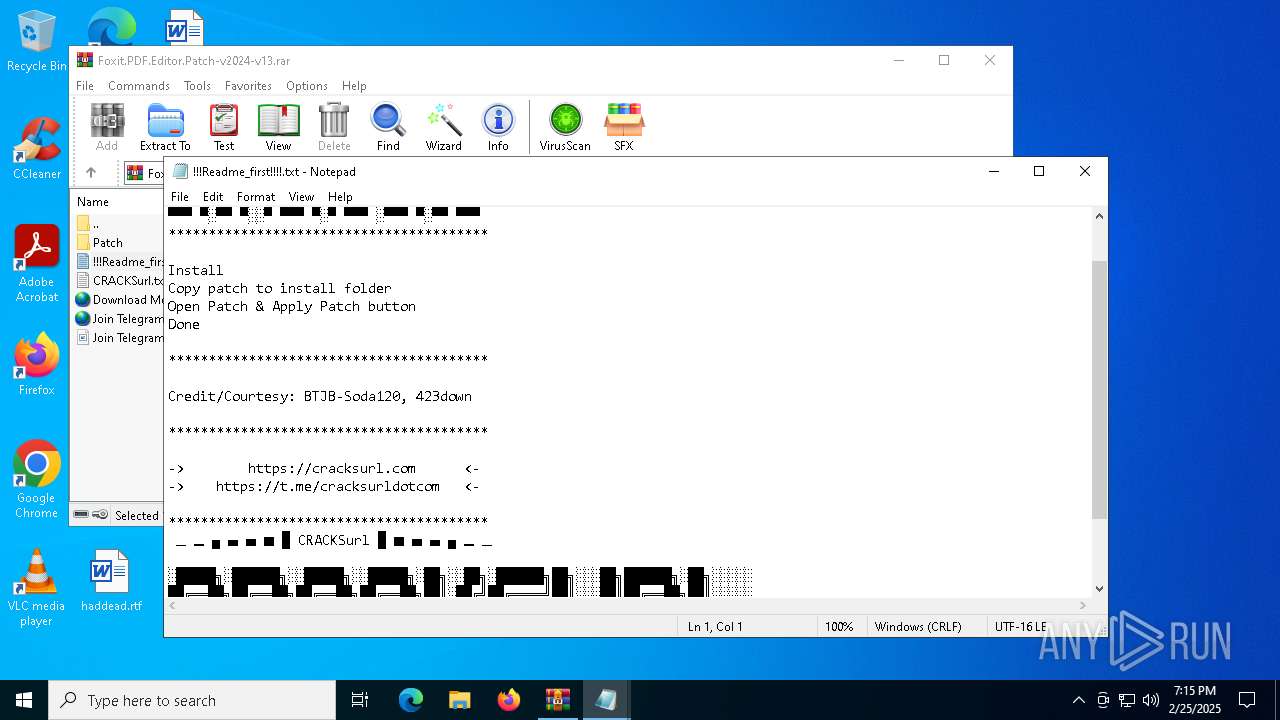
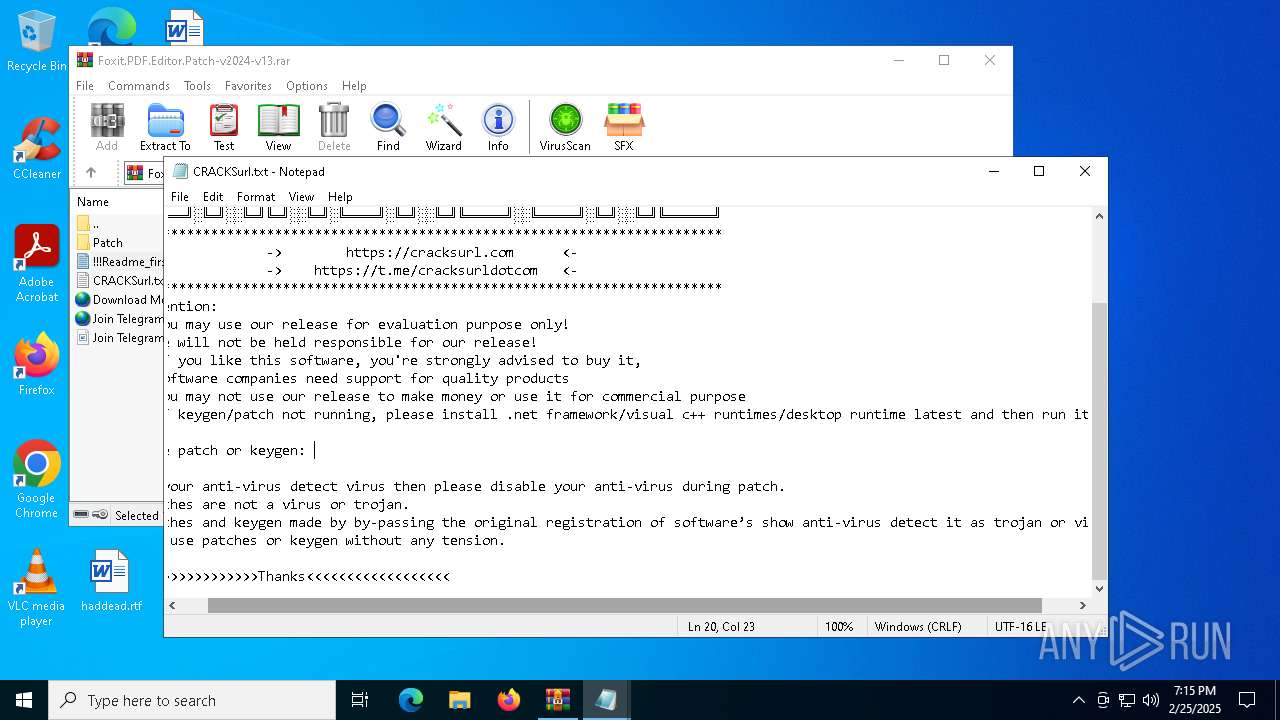
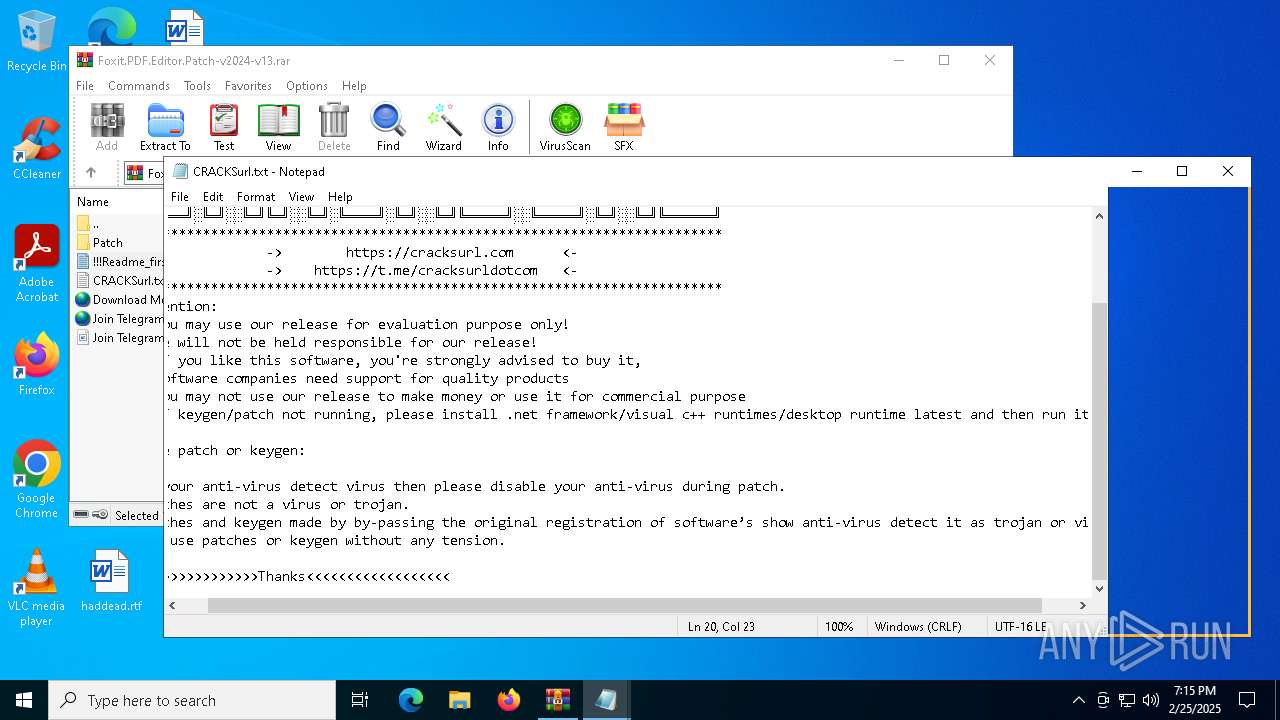
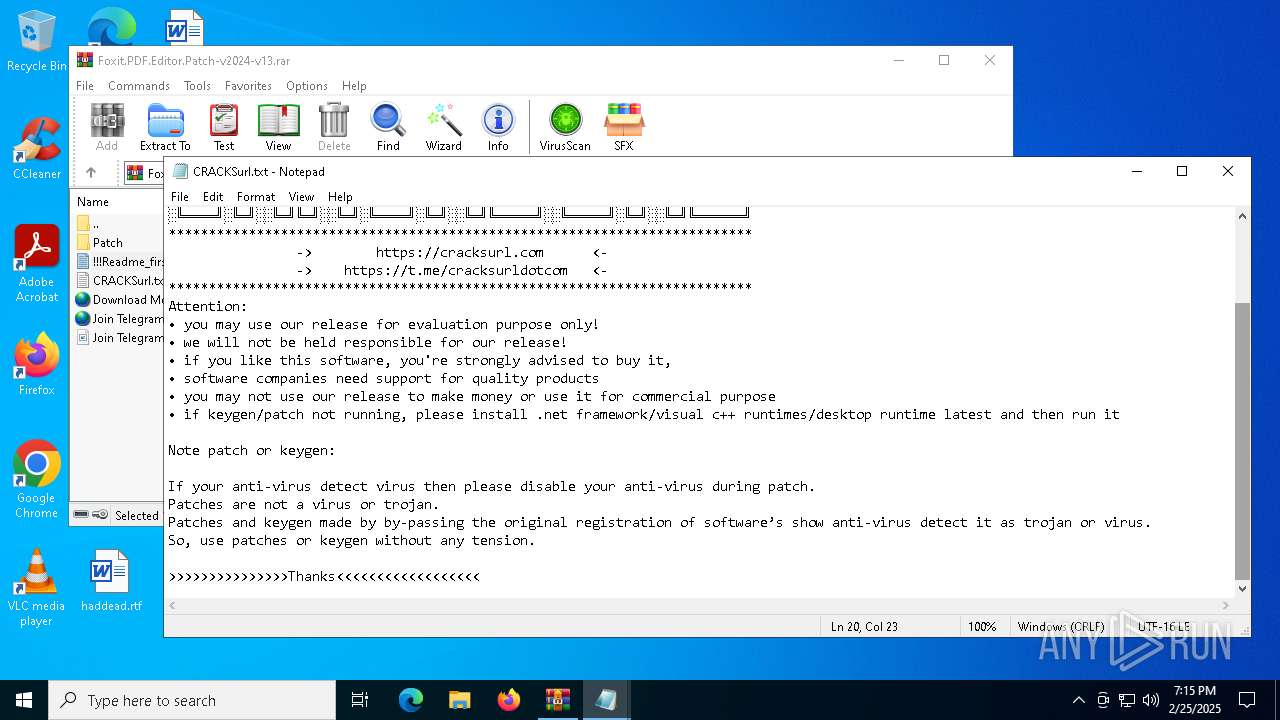
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 3560)
INFO
Reads security settings of Internet Explorer
- notepad.exe (PID: 4320)
- notepad.exe (PID: 3260)
- notepad.exe (PID: 1732)
- notepad.exe (PID: 4592)
- notepad.exe (PID: 5560)
Local mutex for internet shortcut management
- WinRAR.exe (PID: 3560)
Manual execution by a user
- mspaint.exe (PID: 6940)
- mspaint.exe (PID: 4668)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 3560)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 542291 |
| UncompressedSize: | 620544 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | Patch/Foxit.PDF.Editor.2024-Patch.exe |
Total processes
134
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1732 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa3560.21846\!!!Readme_first!!!!.txt | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3260 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa3560.21760\CRACKSurl.txt | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3560 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Foxit.PDF.Editor.Patch-v2024-v13.rar | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4320 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa3560.17530\CRACKSurl.txt | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4592 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa3560.25352\CRACKSurl.txt | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
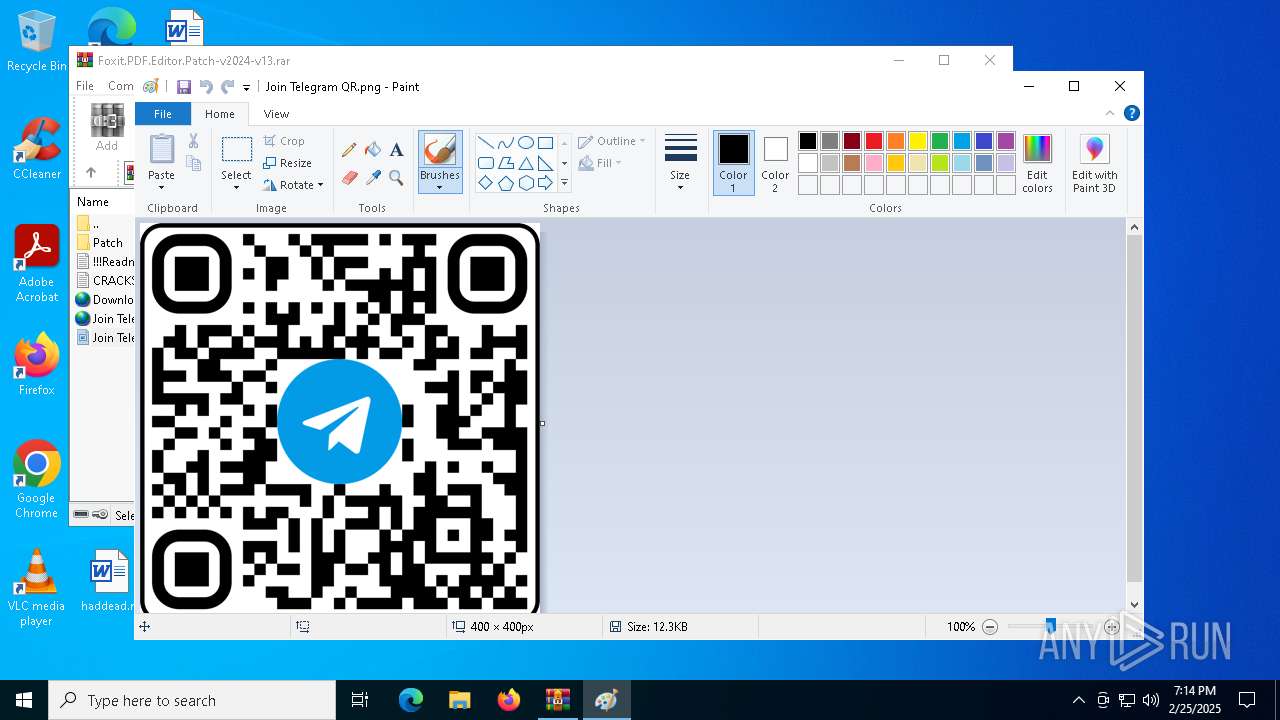
| 4668 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Desktop\Join Telegram QR.png" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5560 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa3560.25461\!!!Readme_first!!!!.txt | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6940 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Desktop\Join Telegram QR.png" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 568
Read events
5 497
Write events
69
Delete events
2
Modification events
| (PID) Process: | (3560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Foxit.PDF.Editor.Patch-v2024-v13.rar | |||
| (PID) Process: | (3560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6940) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | WindowPlacement |
Value: 2C00000000000000010000000000000000000000FFFFFFFFFFFFFFFF7F000000470000007F04000087020000 | |||
| (PID) Process: | (6940) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ShowThumbnail |
Value: 0 | |||
Executable files
0
Suspicious files
0
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3560.21846\!!!Readme_first!!!!.txt | text | |
MD5:B0E4F3FD30785B8944D966668245D450 | SHA256:254206EA7639F25DE177AE133D16EE49ECAB381A4AF057C0CFF4185BAA56EFF8 | |||
| 3560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3560.25461\!!!Readme_first!!!!.txt | text | |
MD5:B0E4F3FD30785B8944D966668245D450 | SHA256:254206EA7639F25DE177AE133D16EE49ECAB381A4AF057C0CFF4185BAA56EFF8 | |||
| 3560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3560.25352\CRACKSurl.txt | text | |
MD5:E99959E0D9E3F3EF08252B78B9F860F9 | SHA256:798B0622C7E8DC82BD80A19E54E87AF38C118BF7C96963619E6A215493777080 | |||
| 3560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3560.21760\CRACKSurl.txt | text | |
MD5:E99959E0D9E3F3EF08252B78B9F860F9 | SHA256:798B0622C7E8DC82BD80A19E54E87AF38C118BF7C96963619E6A215493777080 | |||
| 3560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3560.17530\CRACKSurl.txt | text | |
MD5:E99959E0D9E3F3EF08252B78B9F860F9 | SHA256:798B0622C7E8DC82BD80A19E54E87AF38C118BF7C96963619E6A215493777080 | |||
| 3560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3560.15600\Join Telegram QR.png | image | |
MD5:484407264E37BE1EE4266BAD02A7474C | SHA256:6410F1B81043EAFDDAD750345986726C2AC6313D38AA7290CCFEEAB93992C87F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
30
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.140:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7104 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6632 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7104 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.140:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4672 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 184.86.251.24:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 20.190.159.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |