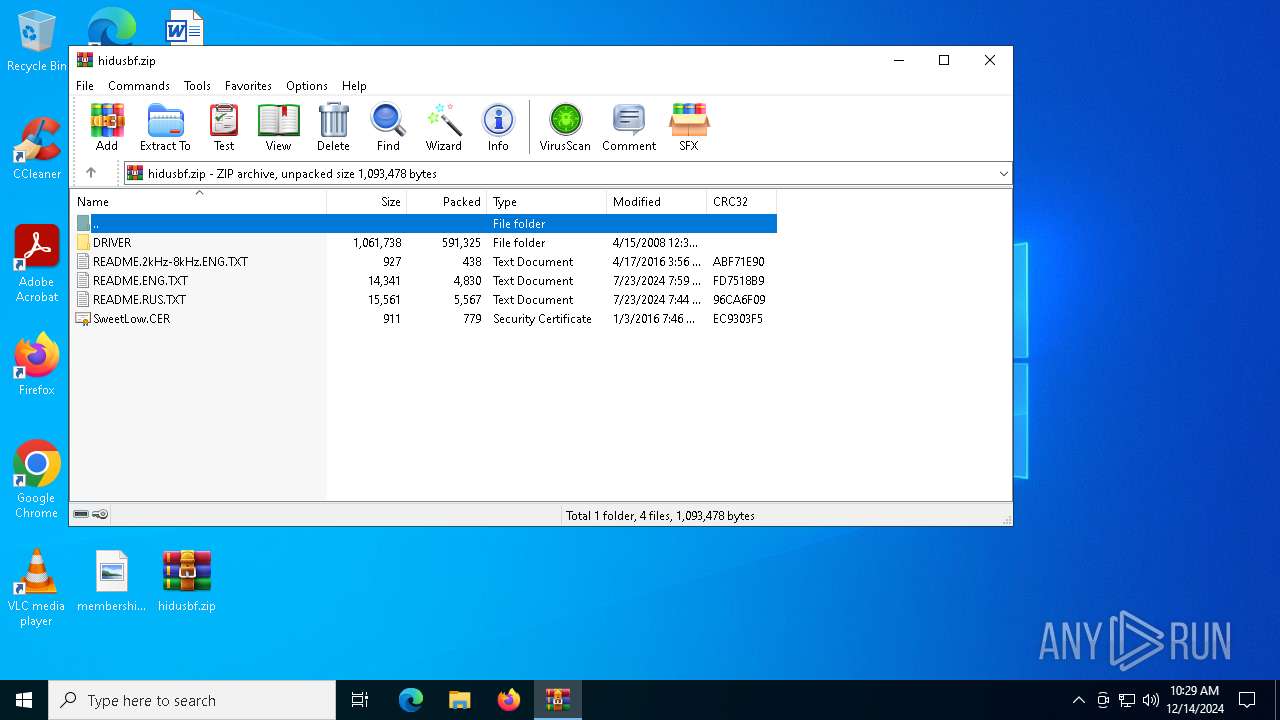
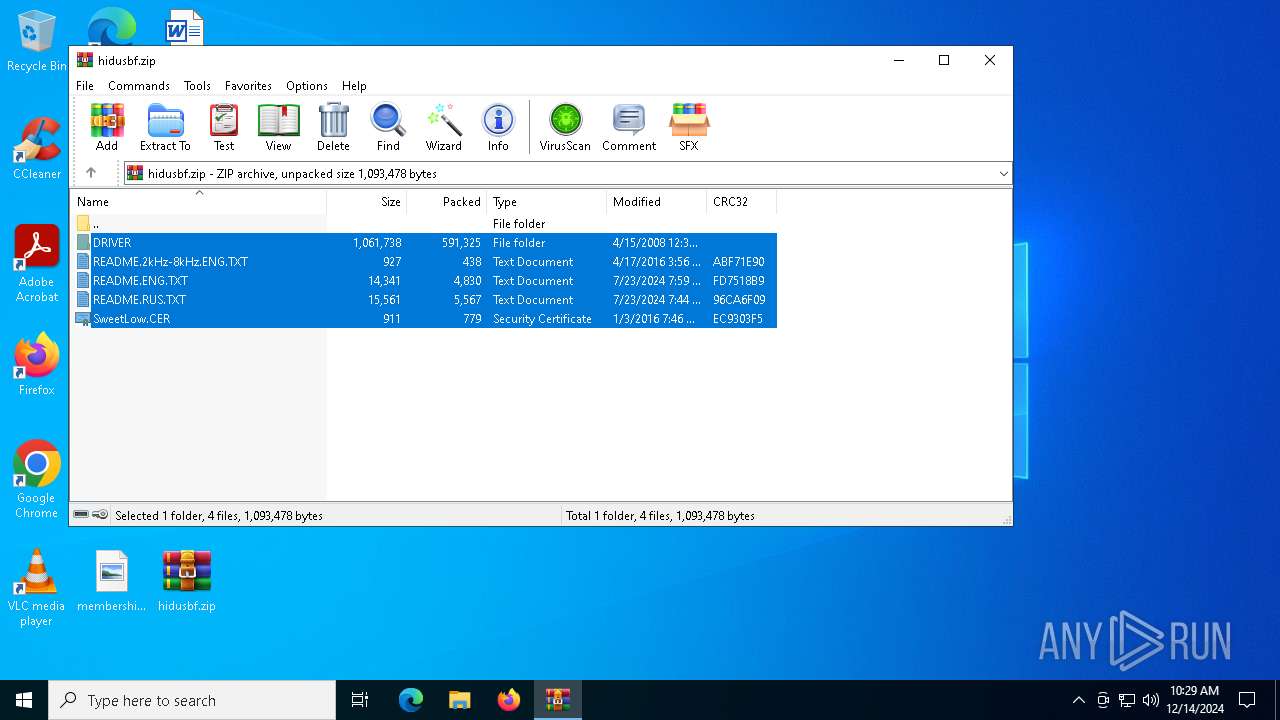
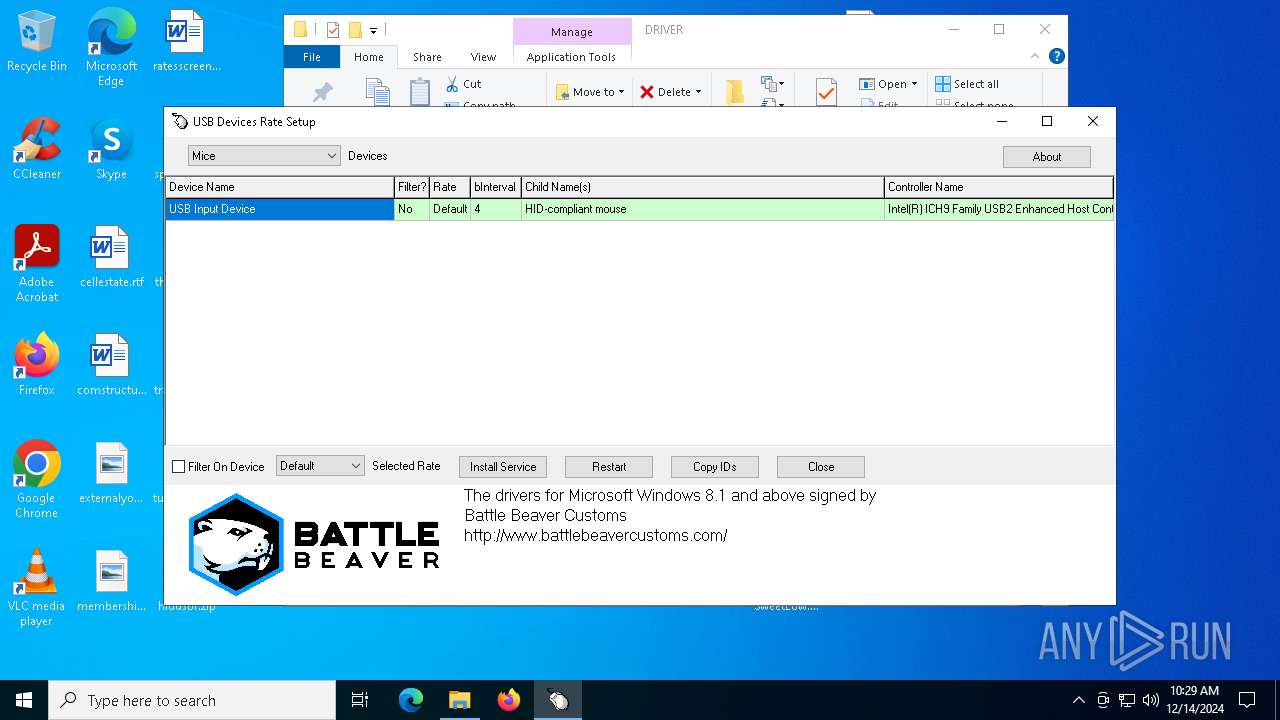
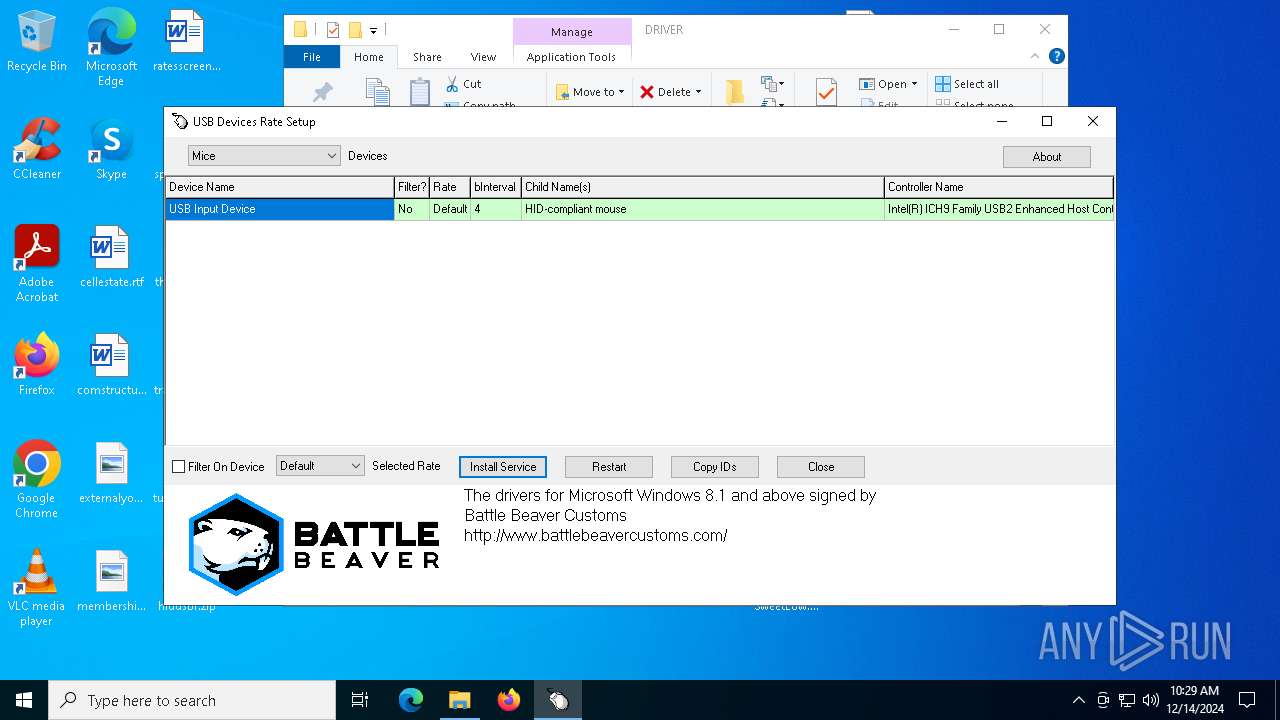
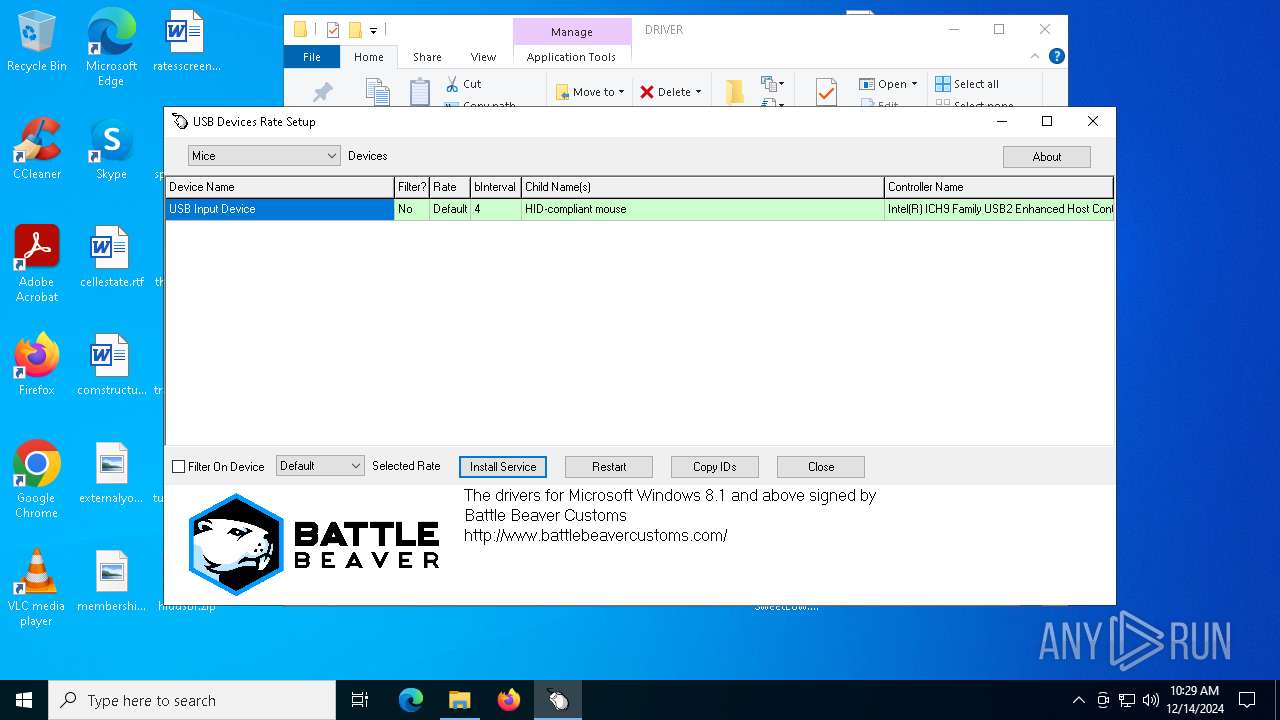
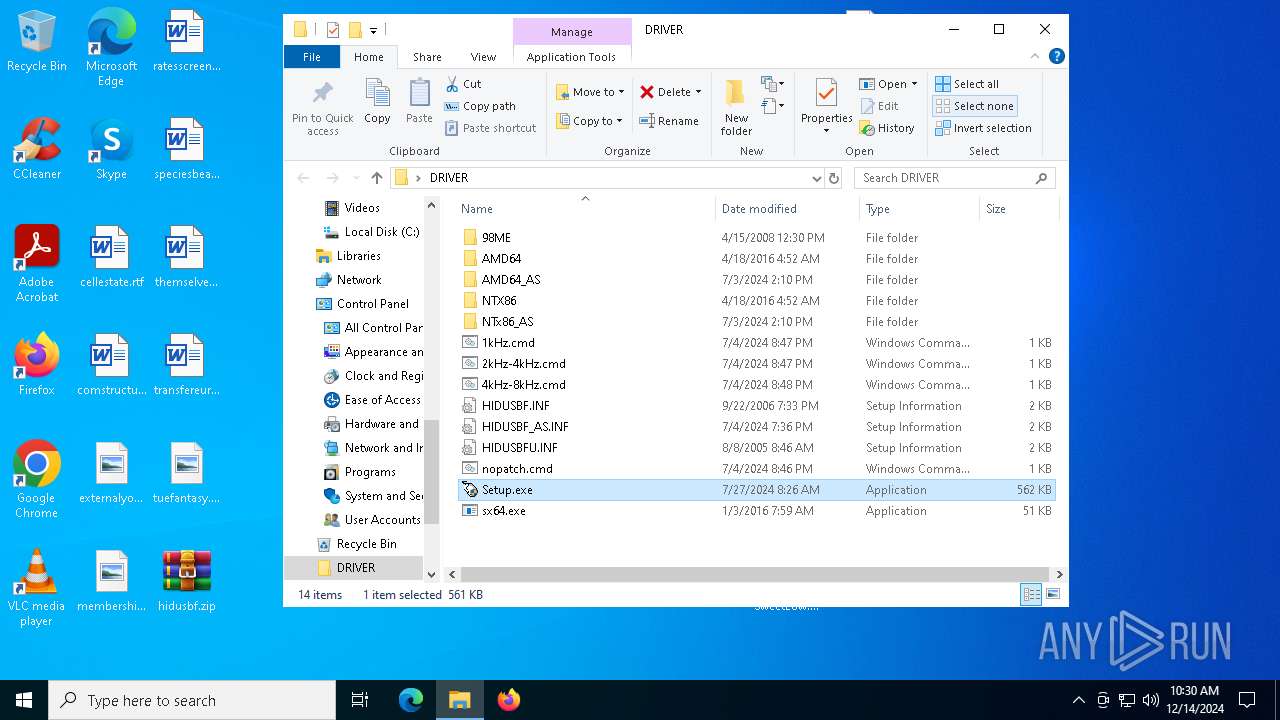
| File name: | hidusbf.zip |
| Full analysis: | https://app.any.run/tasks/1025fa58-d5c6-4af1-aed4-317438b2b4f1 |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2024, 10:29:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 91F9D7834431CCDB8640E6514413BB2E |
| SHA1: | 99E180FABED3F805D4A09E3121DBB53D56883051 |
| SHA256: | EA74EAE4F4F074DEF0328ADE4F2414C3090F34E35226D1FDEC07DCE90F2DA7E3 |
| SSDEEP: | 24576:kuG6O+oo1+oorQ2Yh/QwTj7xKceaaj/HWS4OXQ4euMSZMBi0BHu/jy:kD6O+oo1+oorQ2Yh/QwTj7xKceaaj/H6 |
MALICIOUS
Executing a file with an untrusted certificate
- Setup.exe (PID: 6860)
- Setup.exe (PID: 6808)
- sx64.exe (PID: 7000)
Changes the autorun value in the registry
- InfDefaultInstall.exe (PID: 7048)
SUSPICIOUS
Reads security settings of Internet Explorer
- Setup.exe (PID: 6860)
- sx64.exe (PID: 7000)
Reads the date of Windows installation
- sx64.exe (PID: 7000)
Drops a system driver (possible attempt to evade defenses)
- InfDefaultInstall.exe (PID: 7048)
- WinRAR.exe (PID: 772)
Executable content was dropped or overwritten
- InfDefaultInstall.exe (PID: 7048)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 772)
Manual execution by a user
- Setup.exe (PID: 6808)
- Setup.exe (PID: 6860)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 772)
Checks supported languages
- Setup.exe (PID: 6860)
- sx64.exe (PID: 7000)
Process checks computer location settings
- Setup.exe (PID: 6860)
- sx64.exe (PID: 7000)
Reads the computer name
- sx64.exe (PID: 7000)
- Setup.exe (PID: 6860)
Reads Microsoft Office registry keys
- sx64.exe (PID: 7000)
The process uses the downloaded file
- sx64.exe (PID: 7000)
- runonce.exe (PID: 7092)
- WinRAR.exe (PID: 772)
- Setup.exe (PID: 6860)
Creates files in the driver directory
- InfDefaultInstall.exe (PID: 7048)
Reads the time zone
- runonce.exe (PID: 7092)
Reads security settings of Internet Explorer
- runonce.exe (PID: 7092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2008:04:15 15:30:18 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | DRIVER/ |
Total processes
135
Monitored processes
8
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 772 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\hidusbf.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6772 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6808 | "C:\Users\admin\Desktop\DRIVER\Setup.exe" | C:\Users\admin\Desktop\DRIVER\Setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6860 | "C:\Users\admin\Desktop\DRIVER\Setup.exe" | C:\Users\admin\Desktop\DRIVER\Setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 7000 | "C:\Users\admin\Desktop\DRIVER\sx64.exe" e install hidusbf_as.inf | C:\Users\admin\Desktop\DRIVER\sx64.exe | — | Setup.exe | |||||||||||
User: admin Company: SweetLow Integrity Level: HIGH Description: SETUP x64 Helper Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
| 7048 | "C:\WINDOWS\System32\InfDefaultInstall.exe" "C:\Users\admin\Desktop\DRIVER\HIDUSBF_AS.INF" | C:\Windows\System32\InfDefaultInstall.exe | sx64.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: INF Default Install Exit code: 0 Version: 5.2.3668.0 Modules
| |||||||||||||||
| 7092 | "C:\WINDOWS\system32\runonce.exe" -r | C:\Windows\System32\runonce.exe | — | InfDefaultInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7136 | "C:\Windows\System32\grpconv.exe" -o | C:\Windows\System32\grpconv.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 874
Read events
2 849
Write events
24
Delete events
1
Modification events
| (PID) Process: | (772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\hidusbf.zip | |||
| (PID) Process: | (772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
25
Suspicious files
4
Text files
7
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa772.48520\DRIVER\AMD64\4khz-8khz\hidusbf.sys | executable | |
MD5:DFE3AEEA9E6C889698FE12F5308C810F | SHA256:889241E792A3E58673EB98D4D1815C8073A6BCFA0ABC6C3AF060C5C6E7B94302 | |||
| 772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa772.48520\DRIVER\NTX86\nopatch\hidusbf.sys | executable | |
MD5:2122564C266A79E73FA73A44523783DC | SHA256:A3CBA51DC28B10F7BE1A232BE0D6CEC6D734B6753AB7054169A04CE22335F7D8 | |||
| 772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa772.48520\DRIVER\NTX86\4khz-8khz\hidusbf.sys | executable | |
MD5:E20703C1C2A2AA94E6D5EEB48BAB62FD | SHA256:377D2BBC879759260A66D937D3C80E2C2B4BAD08D6ED36A0CF93873B7B38A9CE | |||
| 772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa772.48520\DRIVER\sx64.exe | executable | |
MD5:722C4801D445CB49477A6A60AFF8E6E8 | SHA256:B0DF95C336A135B3F0D61DFB4914FAD4C0288EA4527D71F514FE7016ED331053 | |||
| 772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa772.48520\DRIVER\NTX86\2khz-4khz\hidusbf.sys | executable | |
MD5:2EAA8605C6F9F511BB28B16F3626C609 | SHA256:3273A052E5A54F0270168CEE156B7B27B22B59E122B94922A801DD7CDB8BF6B5 | |||
| 772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa772.48520\DRIVER\2kHz-4kHz.cmd | text | |
MD5:CFA099C407DCC29C80DF3CC485EB428A | SHA256:766954A41C08E210FD5B7A31968CC3F6CD3D86227D0C35A1F1CC2FECF89B233A | |||
| 772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa772.48520\DRIVER\NTX86\1khz\hidusbf.sys | executable | |
MD5:40047C4BBD53B7383134E92175F24296 | SHA256:E753BF75D6D8AF04E409D6797DDDDDD287A952070A3779C6D6354623E71A2EEC | |||
| 772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa772.48520\DRIVER\AMD64\1khz\hidusbf.sys | executable | |
MD5:C0C8BDFA88BFAF4552B1C50BEDB2E20D | SHA256:EC97D9C203B6FC47605027DE2E65891C63C8088230F5F8B59E705F40E0BD860A | |||
| 772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa772.48520\DRIVER\1kHz.cmd | text | |
MD5:0E5DFCAAF161C50462DF12B8372E87CB | SHA256:4153A509905F2AE92EEE1578E7E2D0EC8FC734C24A6B6F7ED07F6DFE142724C3 | |||
| 772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa772.48520\DRIVER\HIDUSBF.INF | binary | |
MD5:8EAD6929CA01C948532FC16CEF6B8591 | SHA256:9F98870BA3CBF2B992C848BC7447685B70C0A06D2DD31975CBD8CE3E8235E5A5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
33
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
712 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6208 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
712 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2632 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.170:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |