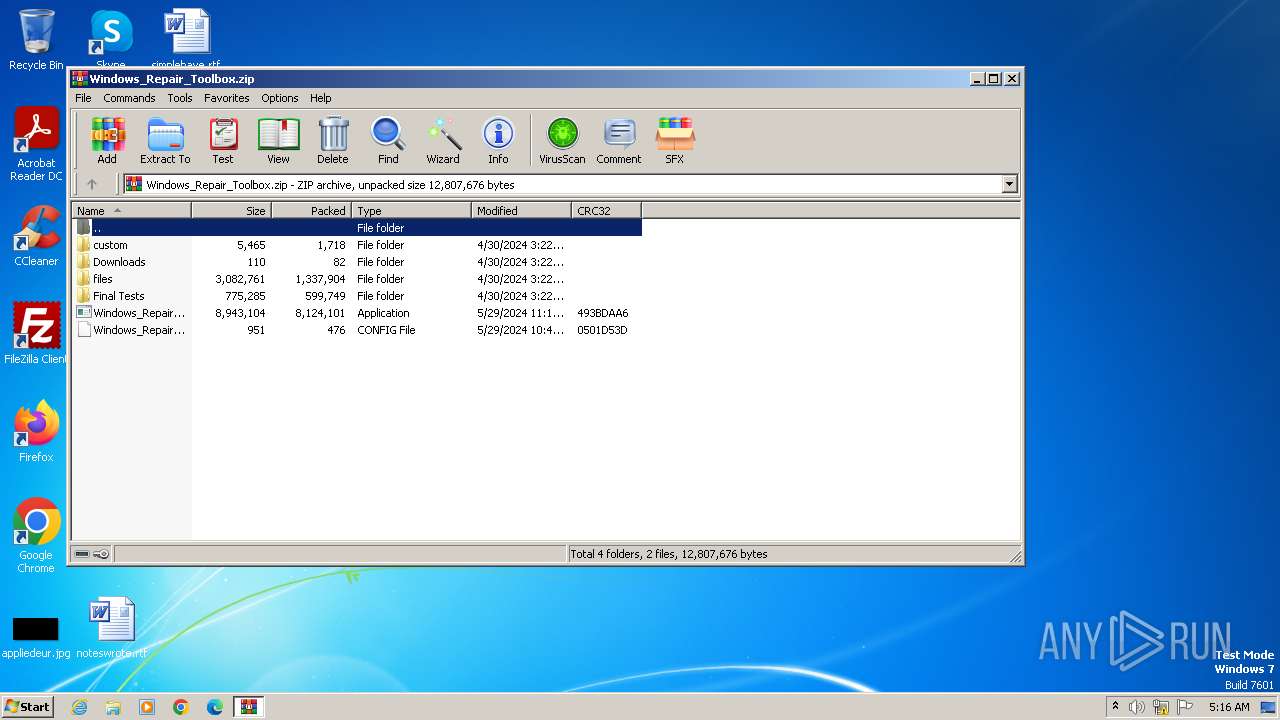
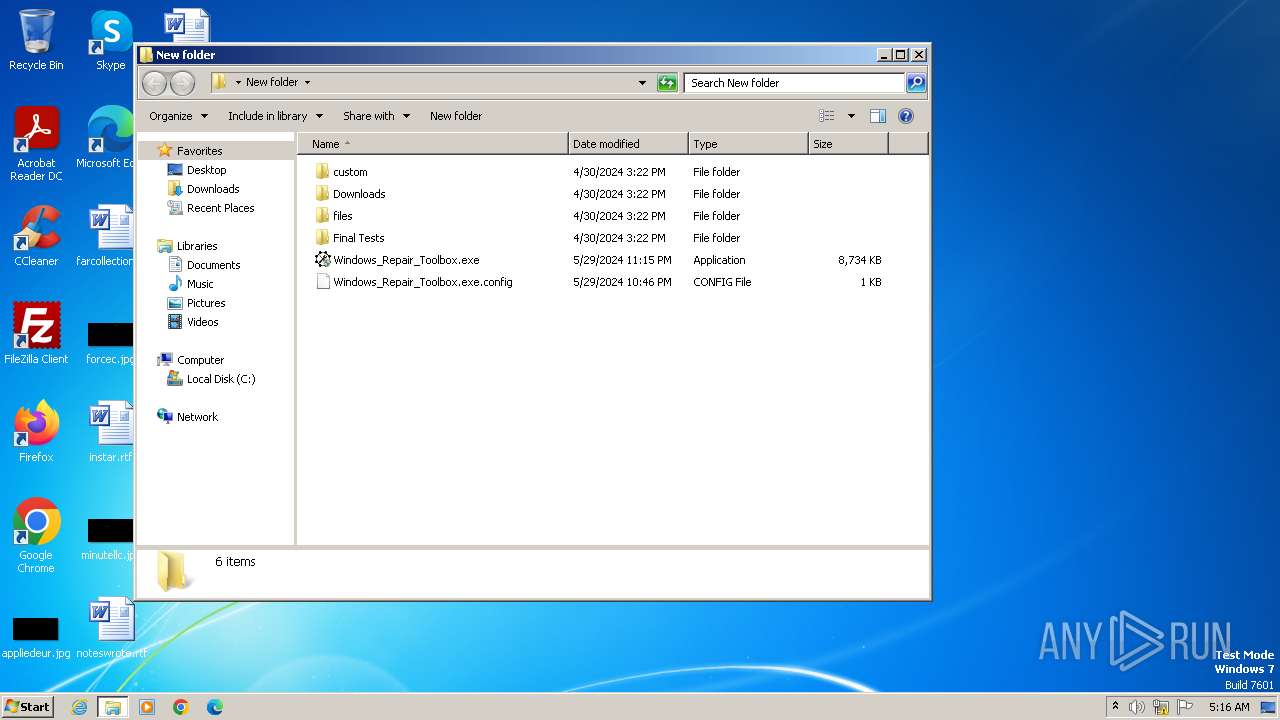
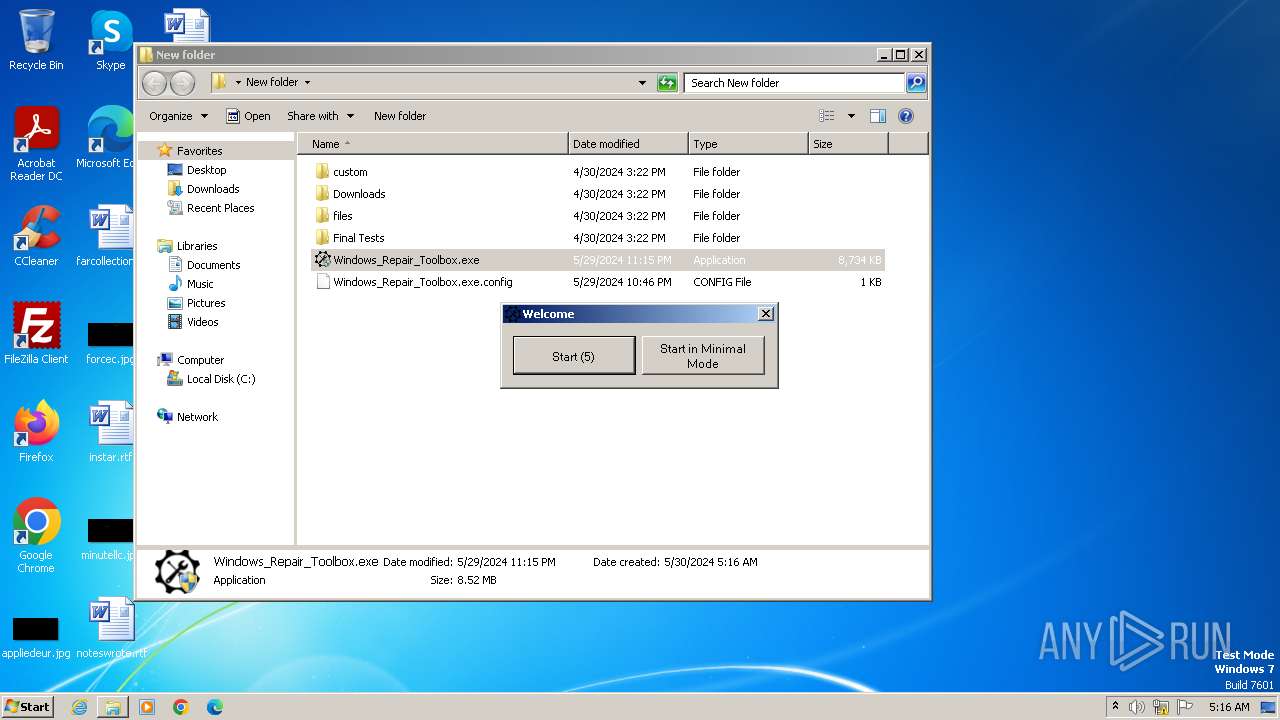
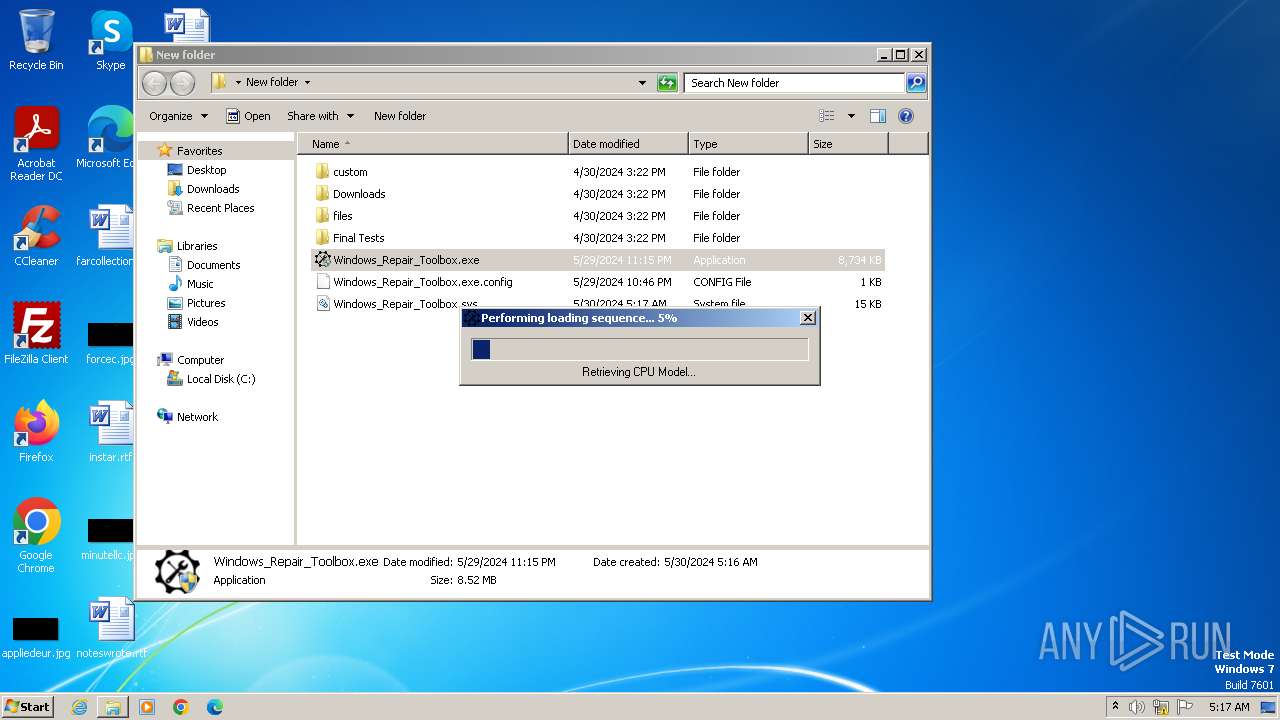
| File name: | Windows_Repair_Toolbox.zip |
| Full analysis: | https://app.any.run/tasks/9e971d8c-2b57-4706-8dfa-a268a8d2f379 |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2024, 04:16:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 54429E32509F99CC3EA2101C9F2EE5A4 |
| SHA1: | AF8AA695E4DA8A9CA5CBF43E8886018901B7B96D |
| SHA256: | EA66156595D4A83BB4715D668D2AFE21EA7D72832077F455DA6C9EA9AC9894F6 |
| SSDEEP: | 98304:7t/mnXbczRzF4+mKbbVkxhkw+mso//cZcwadtjhSHXlyNzWl9auDhk6GDCnoOWVz:M91+VVGIMoN5OfWHRFf2 |
MALICIOUS
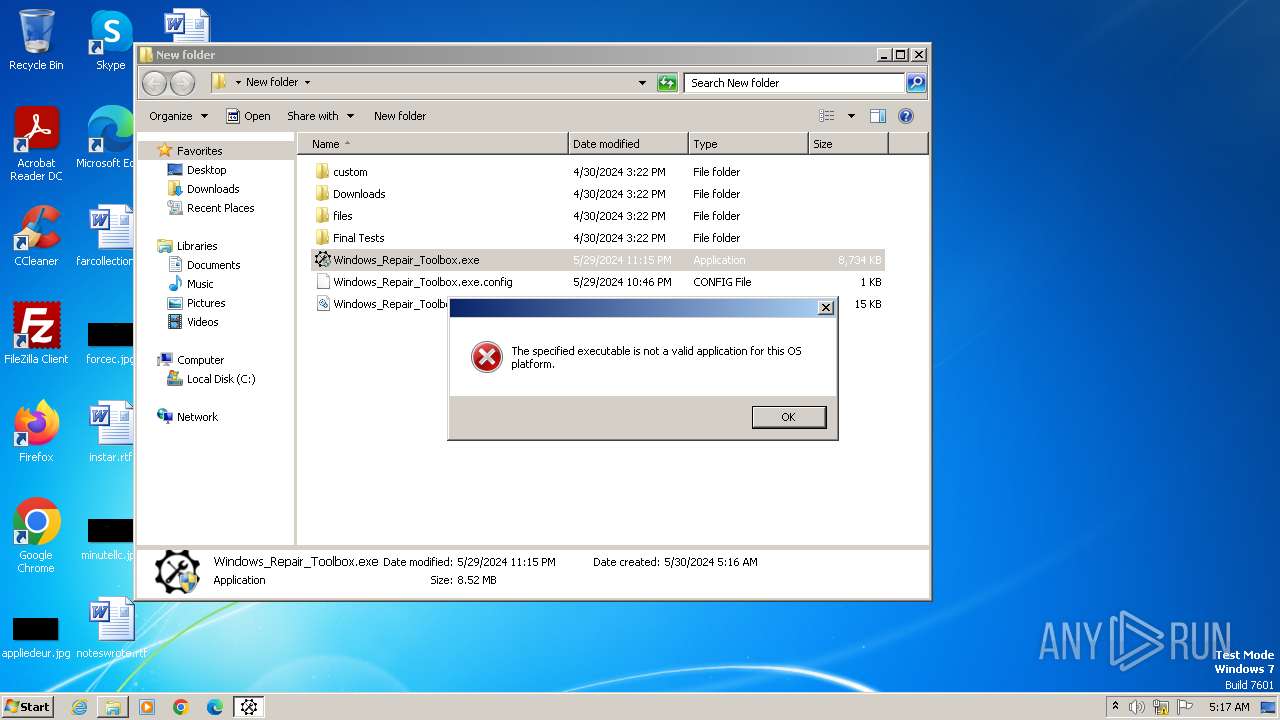
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3992)
- Windows_Repair_Toolbox.exe (PID: 308)
SUSPICIOUS
Drops 7-zip archiver for unpacking
- WinRAR.exe (PID: 3992)
Starts CMD.EXE for commands execution
- Windows_Repair_Toolbox.exe (PID: 308)
Reads the date of Windows installation
- Windows_Repair_Toolbox.exe (PID: 308)
Executable content was dropped or overwritten
- Windows_Repair_Toolbox.exe (PID: 308)
Drops a system driver (possible attempt to evade defenses)
- Windows_Repair_Toolbox.exe (PID: 308)
Reads the Internet Settings
- Windows_Repair_Toolbox.exe (PID: 308)
Reads settings of System Certificates
- Windows_Repair_Toolbox.exe (PID: 308)
Adds/modifies Windows certificates
- Windows_Repair_Toolbox.exe (PID: 308)
Reads Internet Explorer settings
- Windows_Repair_Toolbox.exe (PID: 308)
INFO
Manual execution by a user
- Windows_Repair_Toolbox.exe (PID: 308)
- Windows_Repair_Toolbox.exe (PID: 2040)
- wmpnscfg.exe (PID: 2256)
Checks supported languages
- Windows_Repair_Toolbox.exe (PID: 308)
- wmpnscfg.exe (PID: 2256)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3992)
Reads the computer name
- Windows_Repair_Toolbox.exe (PID: 308)
- wmpnscfg.exe (PID: 2256)
Reads Environment values
- Windows_Repair_Toolbox.exe (PID: 308)
Reads Microsoft Office registry keys
- Windows_Repair_Toolbox.exe (PID: 308)
Create files in a temporary directory
- Windows_Repair_Toolbox.exe (PID: 308)
Reads the machine GUID from the registry
- Windows_Repair_Toolbox.exe (PID: 308)
Disables trace logs
- Windows_Repair_Toolbox.exe (PID: 308)
Reads the software policy settings
- Windows_Repair_Toolbox.exe (PID: 308)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:04:30 15:22:32 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | custom/ |
Total processes
45
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | "C:\Users\admin\Desktop\New folder\Windows_Repair_Toolbox.exe" | C:\Users\admin\Desktop\New folder\Windows_Repair_Toolbox.exe | explorer.exe | ||||||||||||
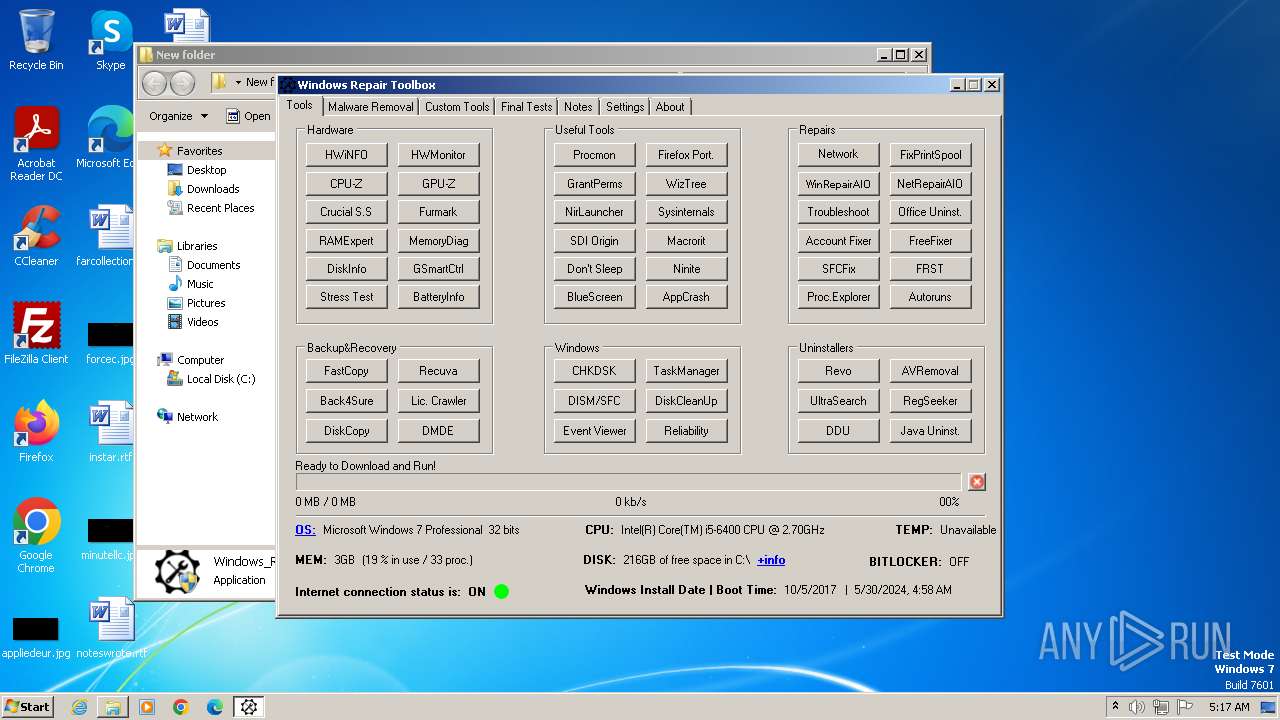
User: admin Company: Alexandre Coelho Integrity Level: HIGH Description: Windows Repair Toolbox Version: 3.0.4.2 Modules
| |||||||||||||||
| 1800 | "CMD.EXE" /C manage-bde -status C: | C:\Windows\System32\cmd.exe | — | Windows_Repair_Toolbox.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1844 | manage-bde -status C: | C:\Windows\System32\manage-bde.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: BitLocker Drive Encryption: Configuration Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2040 | "C:\Users\admin\Desktop\New folder\Windows_Repair_Toolbox.exe" | C:\Users\admin\Desktop\New folder\Windows_Repair_Toolbox.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexandre Coelho Integrity Level: MEDIUM Description: Windows Repair Toolbox Exit code: 3221226540 Version: 3.0.4.2 Modules
| |||||||||||||||
| 2256 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3992 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Windows_Repair_Toolbox.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
11 808
Read events
11 744
Write events
59
Delete events
5
Modification events
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Windows_Repair_Toolbox.zip | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
8
Suspicious files
7
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3992.40987\custom\custom.xml | xml | |
MD5:4117910127395F0C0F747421C90FC440 | SHA256:631B10CE261FDBF8AF53820A6CA3E66674237388D5A9F6C285AAB71E64C00A53 | |||
| 3992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3992.40987\files\ATPad\ATPad.exe | executable | |
MD5:C57409B9D045CFED874F2066D2AD176A | SHA256:532C46592ADE2748803296F6DB29DD323145AA6C925725D2B4BEE0B25205D195 | |||
| 3992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3992.40987\files\7za.exe | executable | |
MD5:9FA07F7B0FFEE060B7ED69F0E028B03F | SHA256:BB6B9F15FF2FC1B938693BE31965D50C23BD79244C013F0223F2E39FE08944CE | |||
| 3992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3992.40987\files\custom.xml | xml | |
MD5:4117910127395F0C0F747421C90FC440 | SHA256:631B10CE261FDBF8AF53820A6CA3E66674237388D5A9F6C285AAB71E64C00A53 | |||
| 3992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3992.40987\files\repair_network.cmd | text | |
MD5:4C147E9ED9A165D2A2275F6852ABEA58 | SHA256:E28CD0A3D9F8C6C9A9225AC37F95E0E64C893C52D0DFBA527251127F7460C5F5 | |||
| 3992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3992.40987\files\hash | text | |
MD5:0A1774F443CDFCF98946FDDEEF3E8F49 | SHA256:CF576BEABEF259E59A498E62D52036F514E0B04FFFDBED422E07F2CE8323A872 | |||
| 3992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3992.40987\files\_files_folder_WRT | text | |
MD5:EEF25A2E07E2975C2708D595243A3AA6 | SHA256:8342C42D28B7F1B95FFF94E0FE95A4BFA451C501C5DE915DED7B8A7182B3E84D | |||
| 3992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3992.40987\files\wrt.ico | image | |
MD5:64574C8DA73FF7064BDEDE895DD24B4B | SHA256:D7E16A1C18CB53AB592C91031A38F77D9421638288CDBC3C133CAB765F7372AC | |||
| 3992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3992.40987\files\CheckDisk.exe | executable | |
MD5:2A87E901BBDBF9102DEEE0C55F7E211B | SHA256:36791524319138B1C14294F723176C514569591808E5E9FC7130B53DE451A709 | |||
| 3992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3992.40987\files\definitions.xml | xml | |
MD5:5A9592656C5DCFEA2812DA83F44DBE60 | SHA256:0663AA049E5EB257E72E37BB6FAE19C63542B86AC9C05B636CA6BC09D6760B4C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
7
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
308 | Windows_Repair_Toolbox.exe | 142.250.185.196:80 | www.google.com | GOOGLE | US | whitelisted |
308 | Windows_Repair_Toolbox.exe | 77.37.53.112:443 | windows-repair-toolbox.com | diva-e Datacenters GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| whitelisted |
windows-repair-toolbox.com |
| unknown |