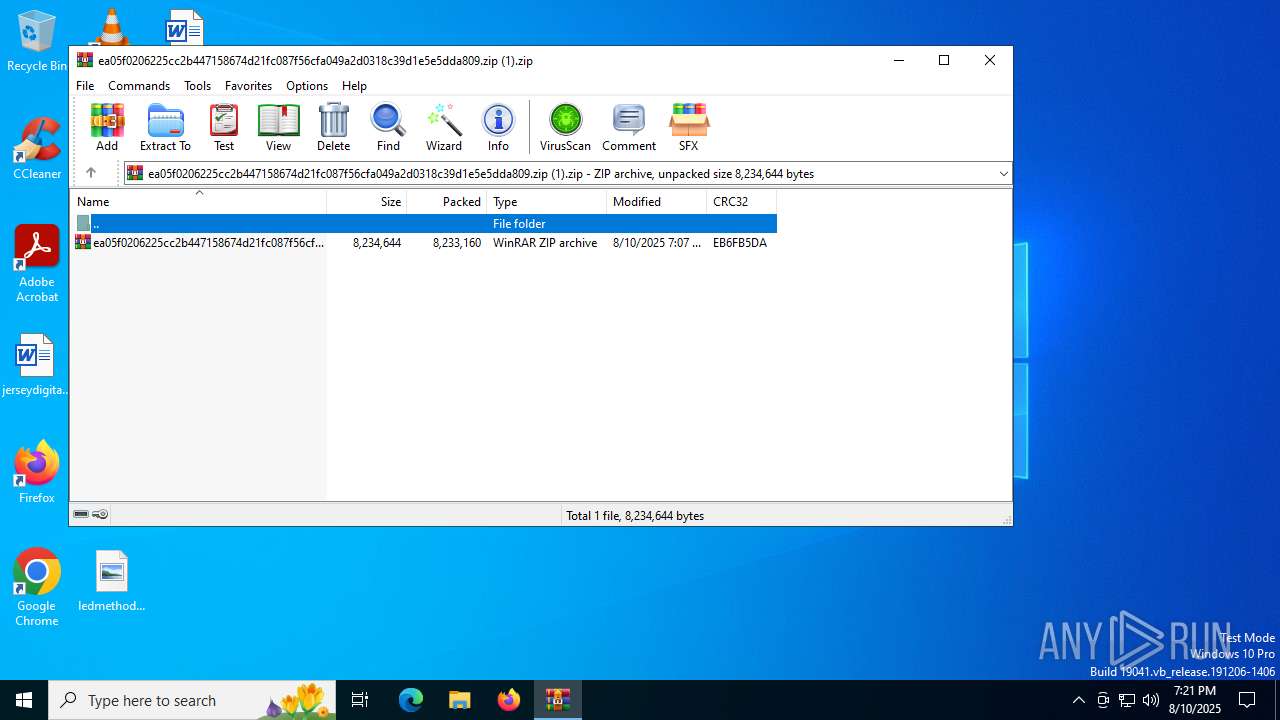
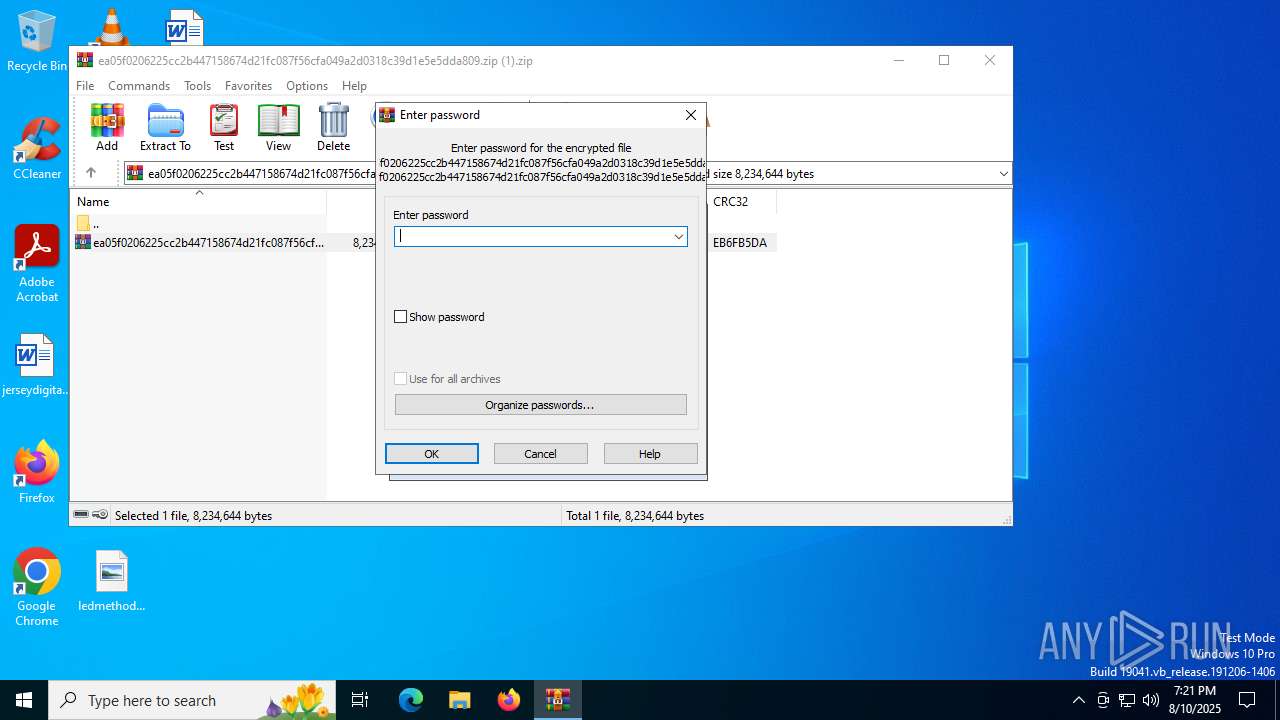
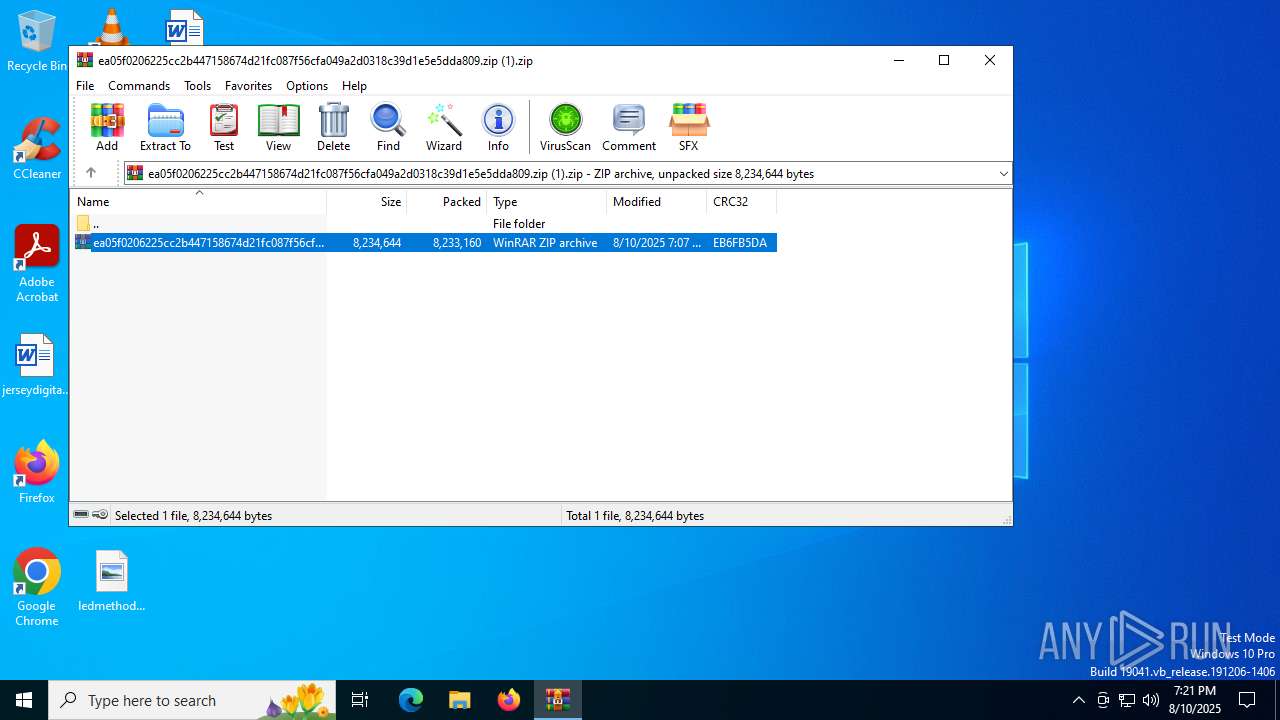
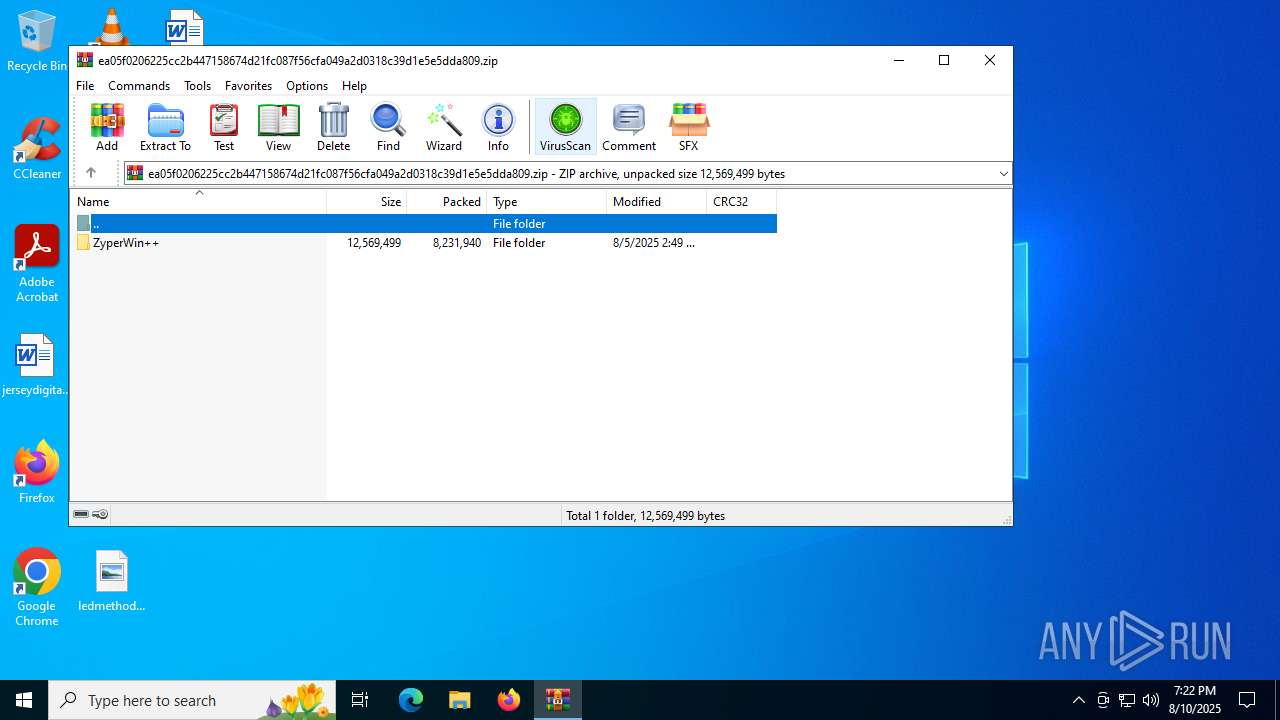
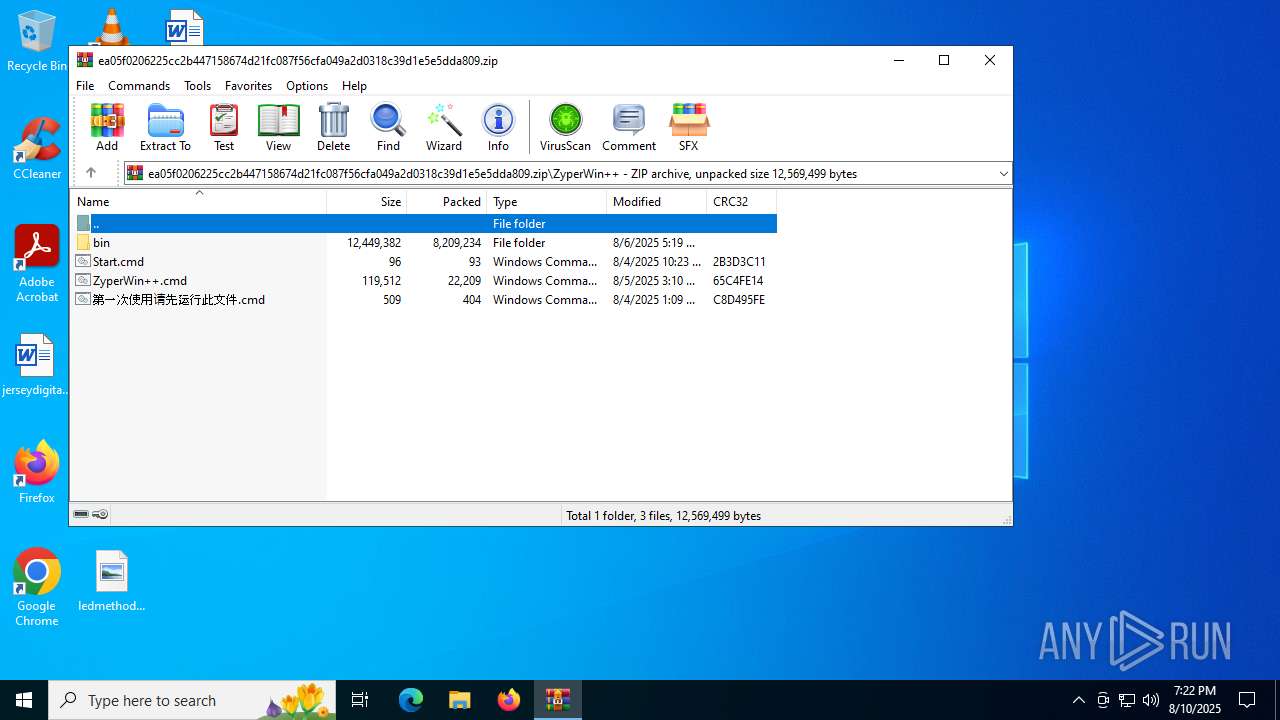
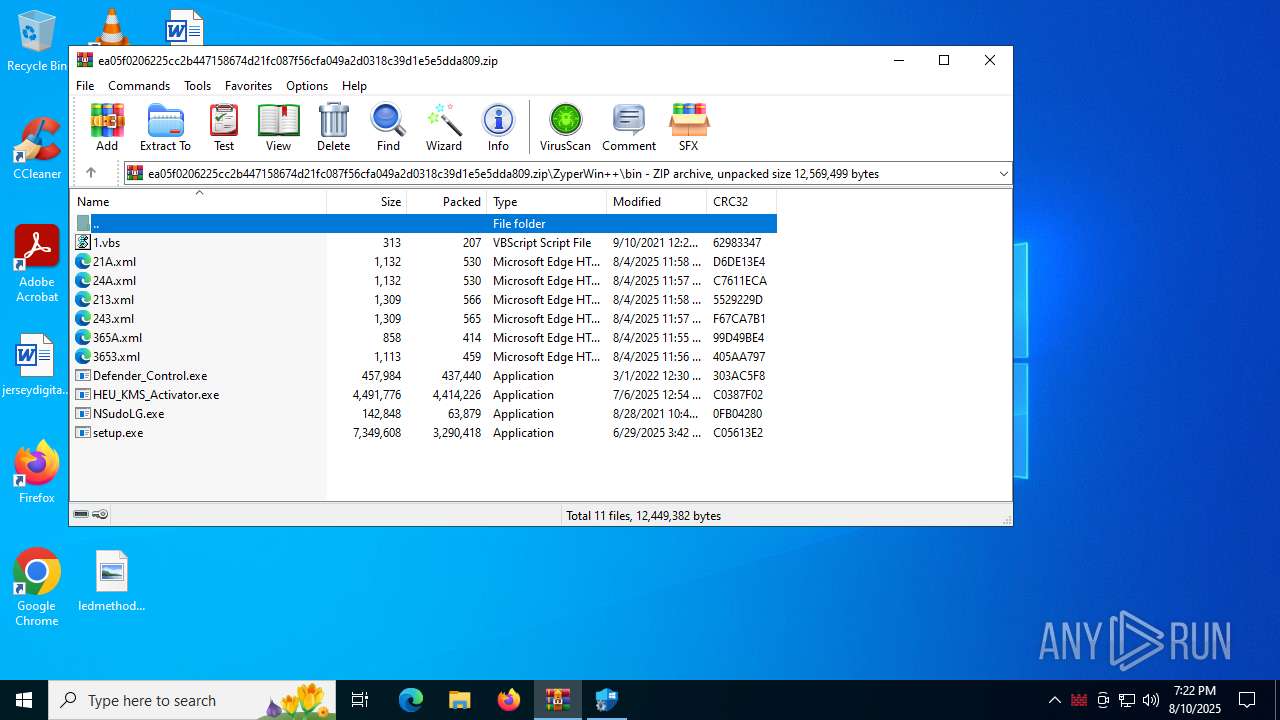
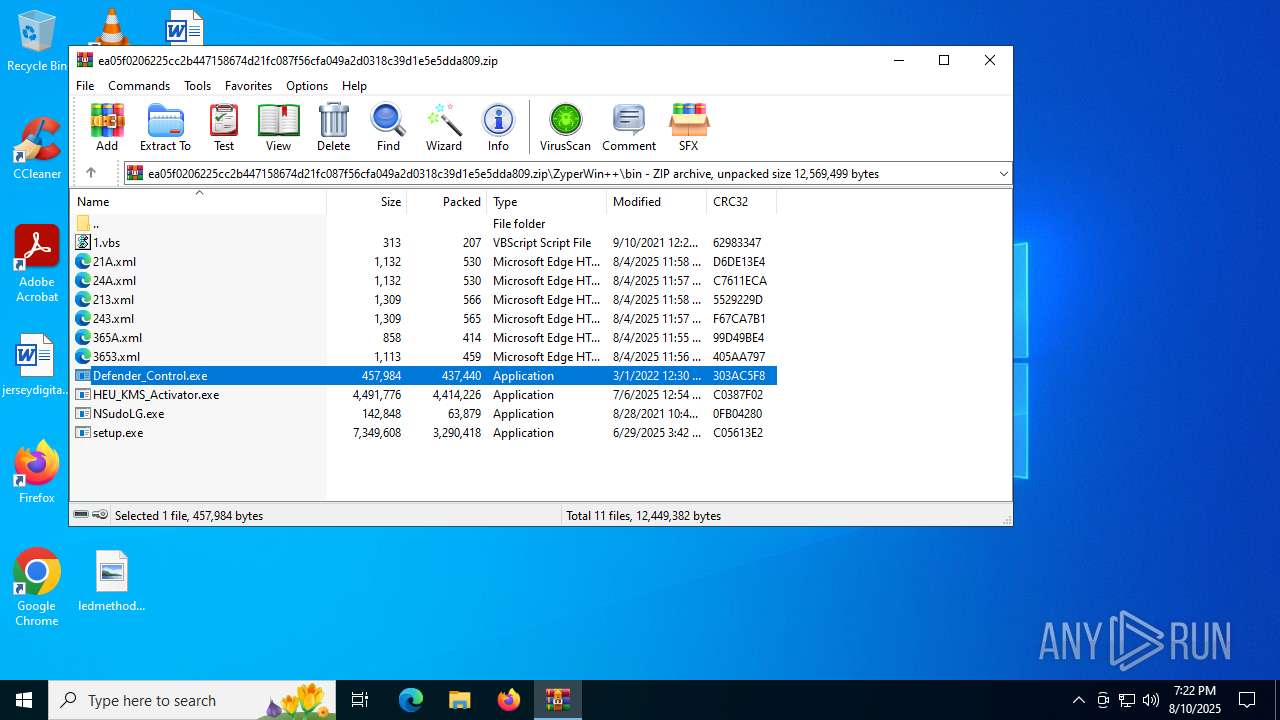
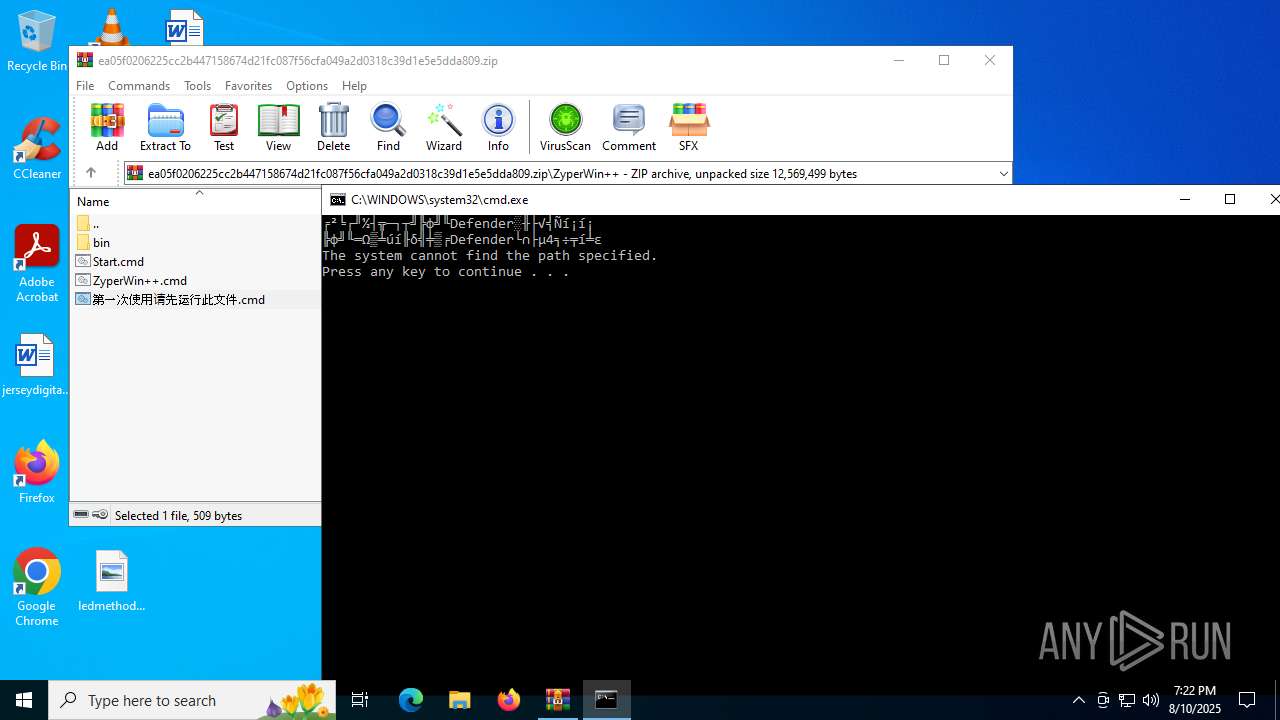
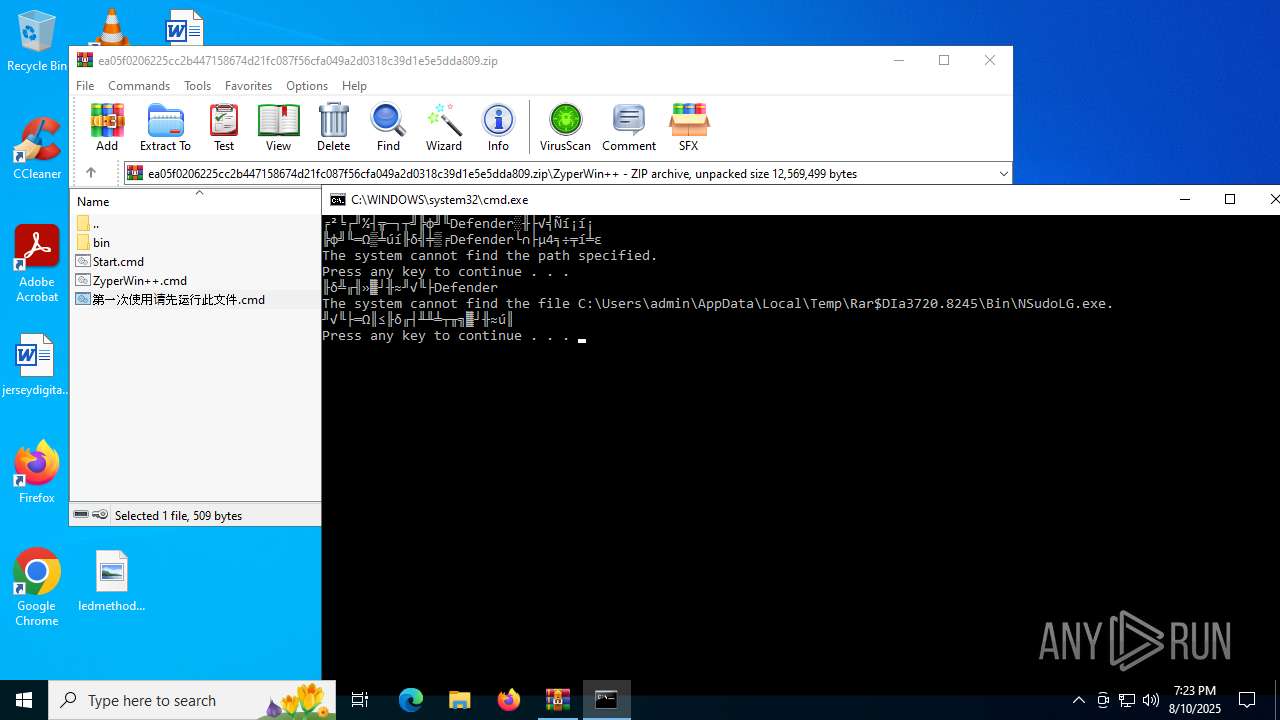
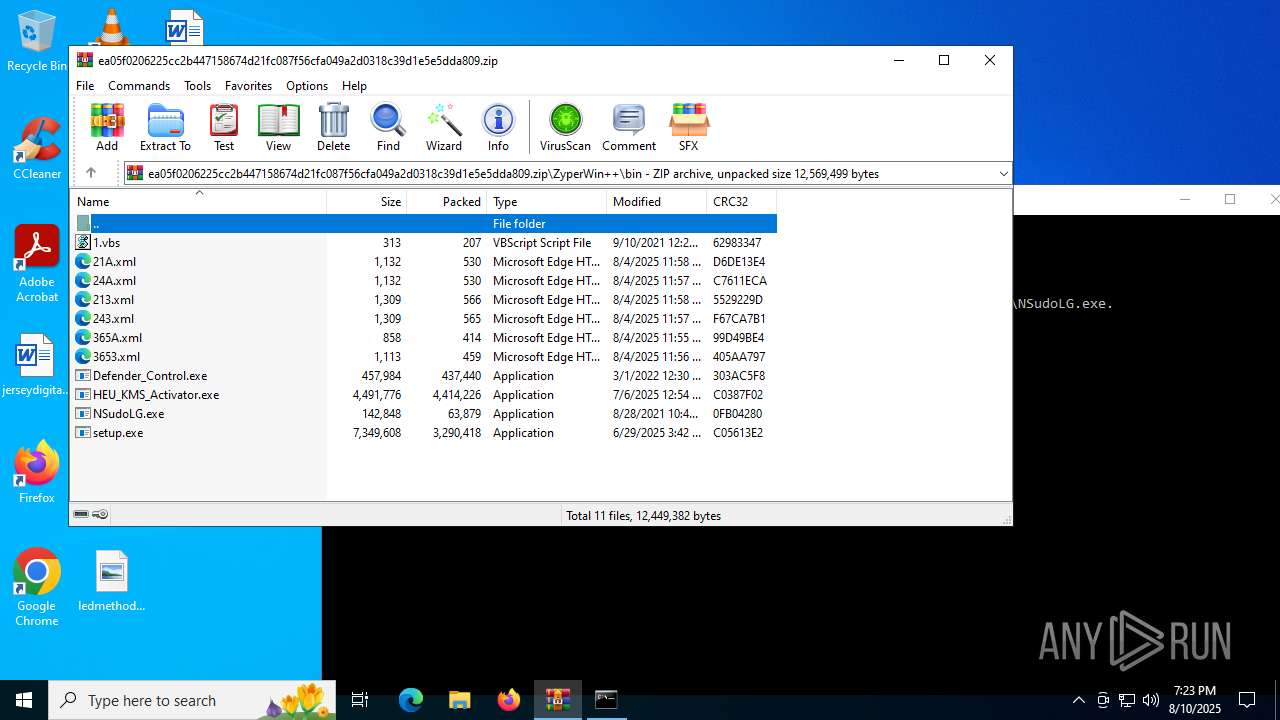
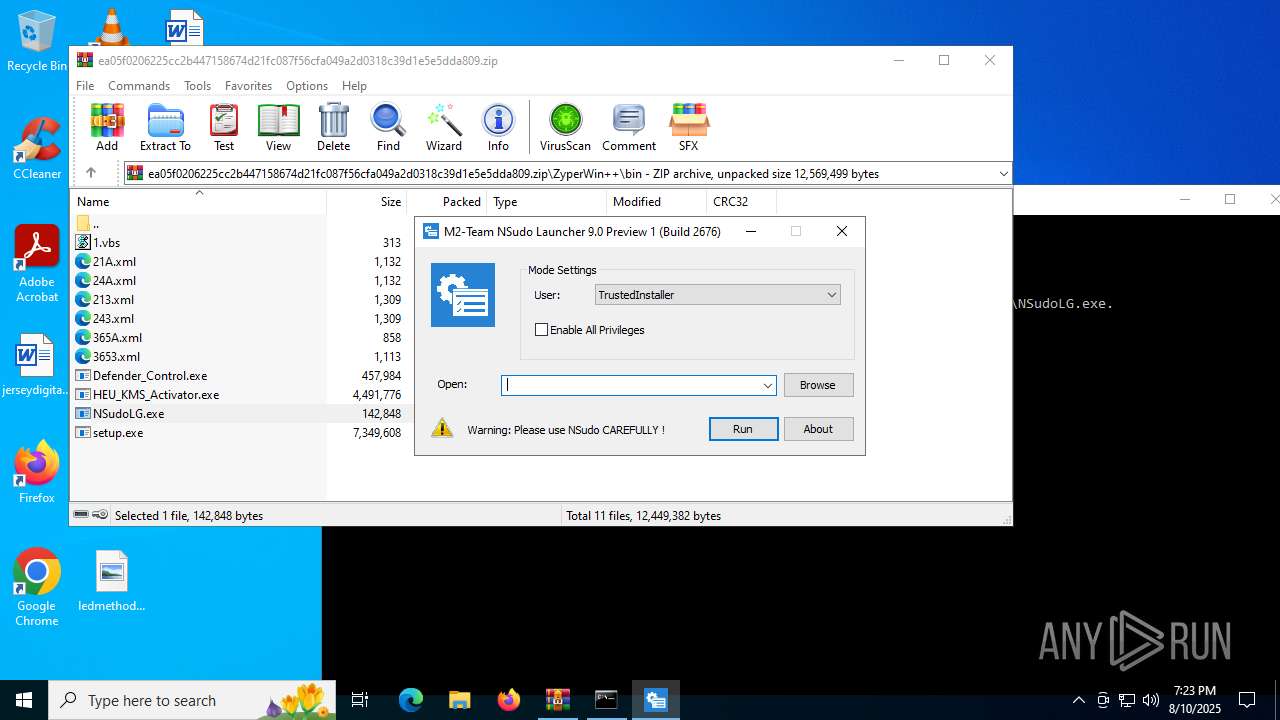
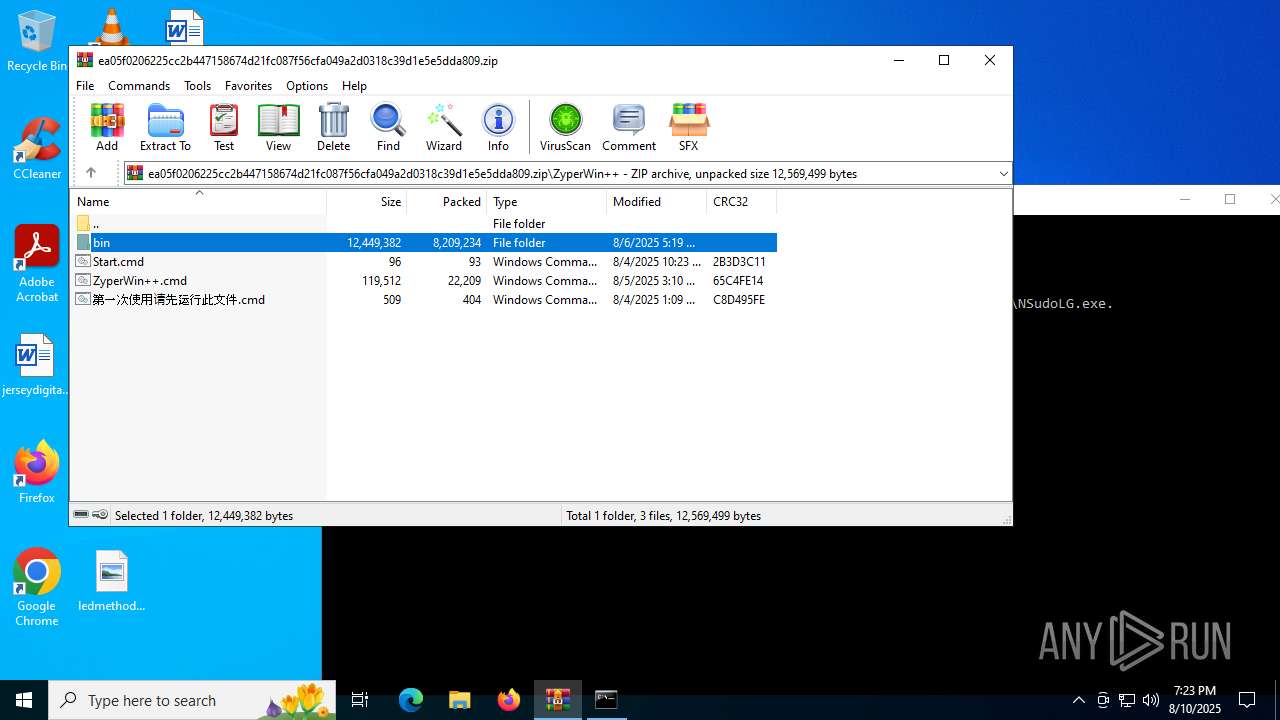
| File name: | ea05f0206225cc2b447158674d21fc087f56cfa049a2d0318c39d1e5e5dda809.zip (1).zip |
| Full analysis: | https://app.any.run/tasks/f82cdecd-f008-4ddf-9d91-69e13ae274a2 |
| Verdict: | Malicious activity |
| Analysis date: | August 10, 2025, 19:21:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | C8D96E52E9EC4E751C0064F6283CEBA8 |
| SHA1: | 0829E67A475876D9A20B53CBF286739A2D82E30F |
| SHA256: | EA5C62936156ED3157B163680FC7097F3CFC9DC129794EE92946BAF6945938C3 |
| SSDEEP: | 98304:nr7Mzz76wm7IL1g45QPr9z1zlhtH0+SFxcQTp+vpuWlARcr4k8keM0CDdD4PpzVX:4madFQKDZK443pim7gz |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4320)
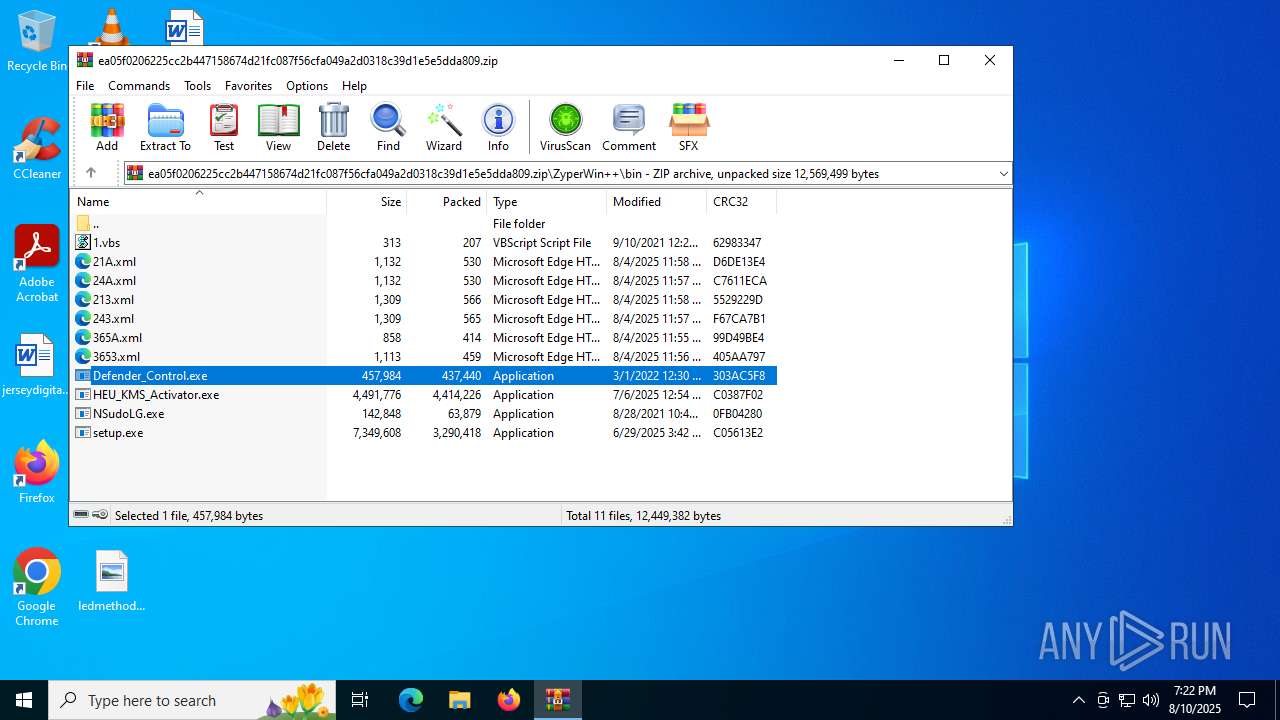
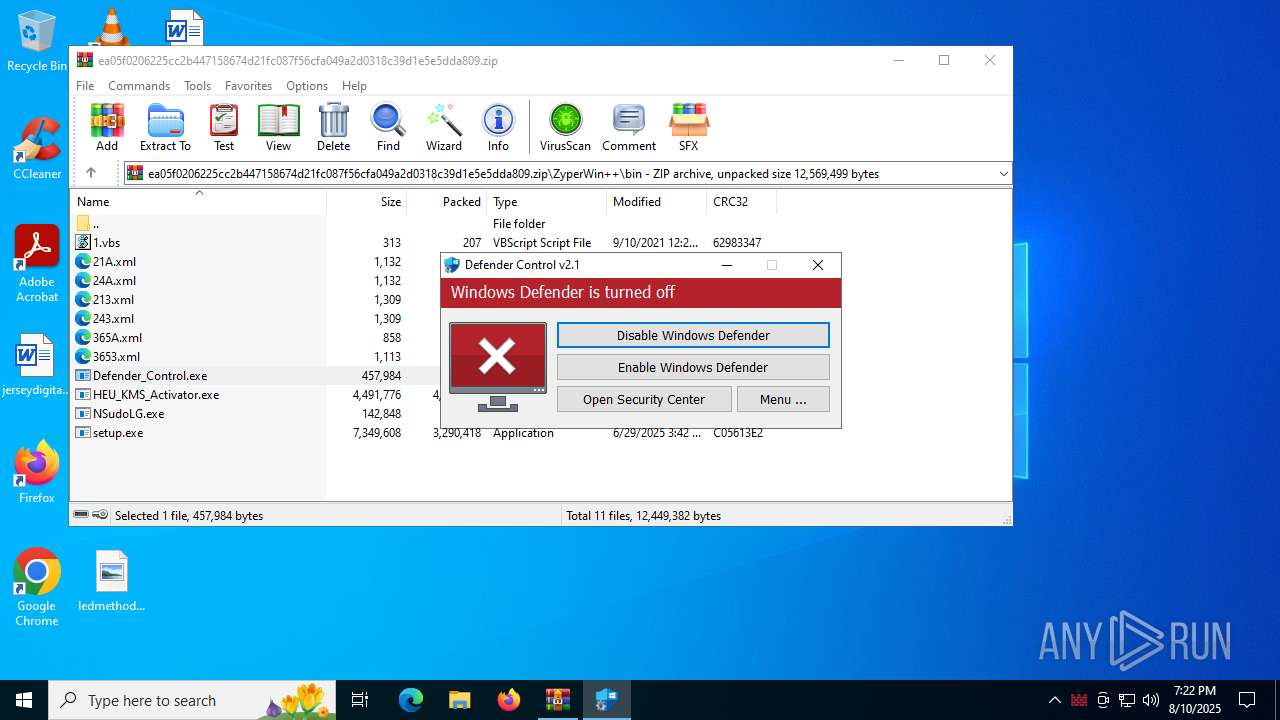
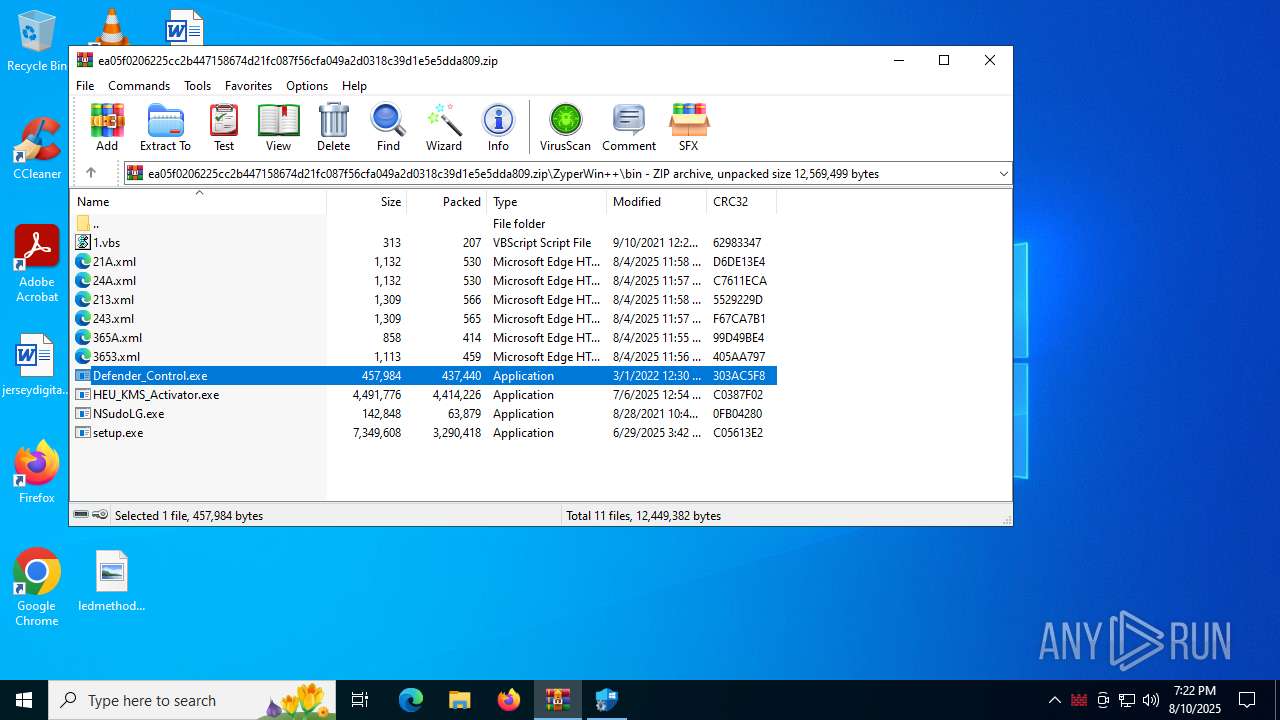
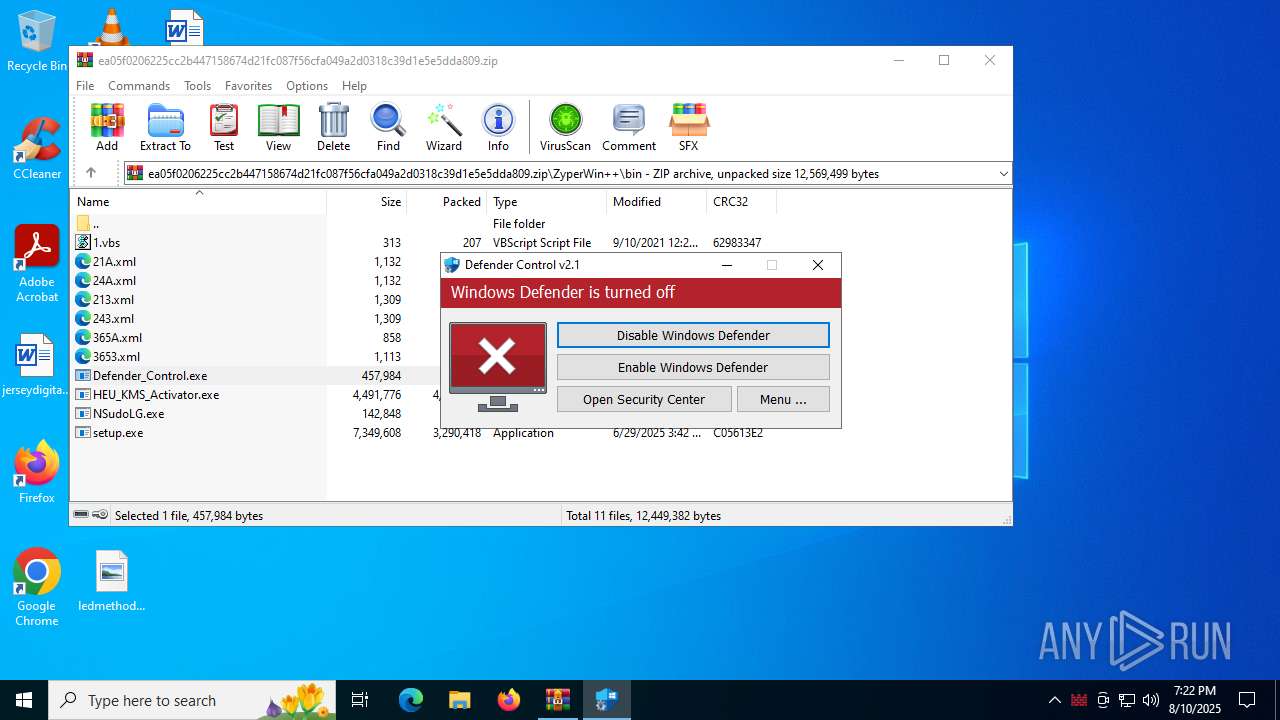
Disables Windows Defender
- Defender_Control.exe (PID: 4024)
Changes image file execution options
- Defender_Control.exe (PID: 4024)
Creates or modifies Windows services
- Defender_Control.exe (PID: 4024)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3720)
- WinRAR.exe (PID: 4320)
Application launched itself
- Defender_Control.exe (PID: 3624)
- Defender_Control.exe (PID: 3160)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3720)
Creates or modifies Windows services
- Defender_Control.exe (PID: 4024)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 3720)
Executing commands from ".cmd" file
- WinRAR.exe (PID: 3720)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4984)
INFO
Reads mouse settings
- Defender_Control.exe (PID: 3624)
- Defender_Control.exe (PID: 3160)
- Defender_Control.exe (PID: 4024)
- Defender_Control.exe (PID: 6668)
The sample compiled with english language support
- WinRAR.exe (PID: 4320)
- WinRAR.exe (PID: 3720)
Reads the computer name
- Defender_Control.exe (PID: 3624)
- Defender_Control.exe (PID: 3160)
- Defender_Control.exe (PID: 4024)
- Defender_Control.exe (PID: 6668)
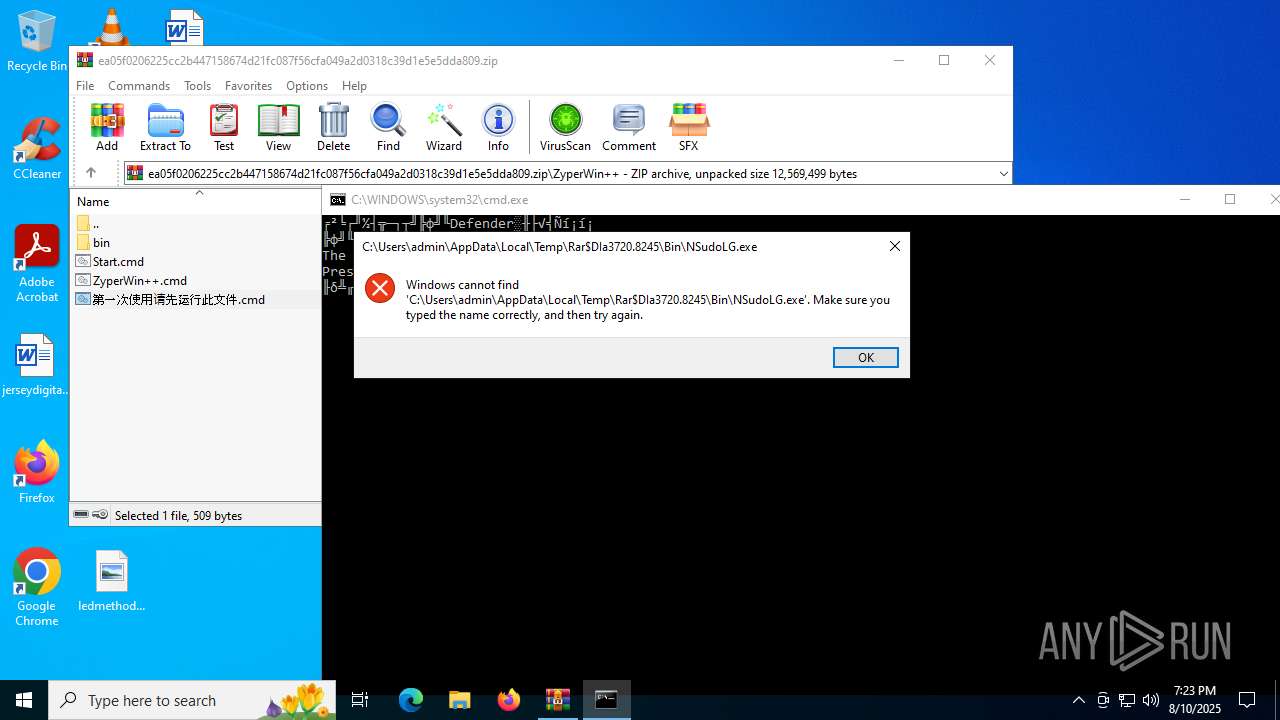
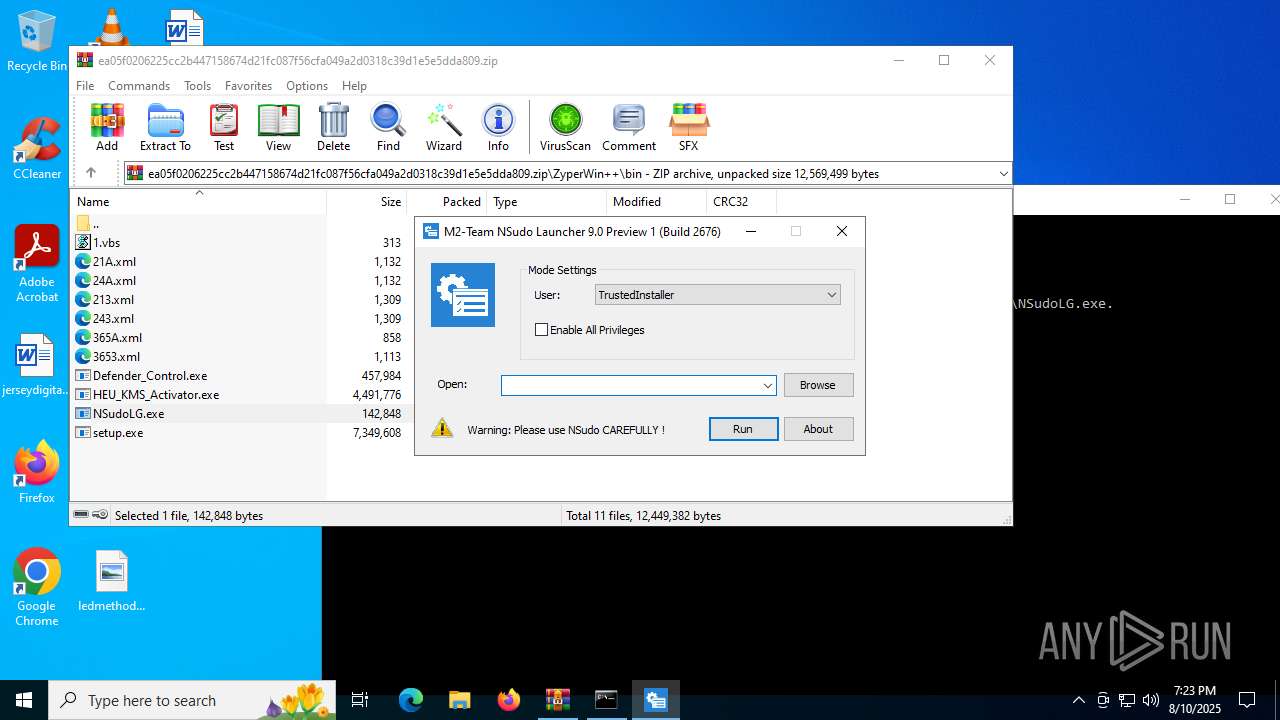
- NSudoLG.exe (PID: 3288)
The sample compiled with chinese language support
- WinRAR.exe (PID: 4320)
- WinRAR.exe (PID: 3720)
DEFENDERCONTROL has been detected
- Defender_Control.exe (PID: 3624)
- WinRAR.exe (PID: 3720)
- Defender_Control.exe (PID: 3160)
Create files in a temporary directory
- Defender_Control.exe (PID: 3624)
- Defender_Control.exe (PID: 4024)
- Defender_Control.exe (PID: 6668)
Checks supported languages
- Defender_Control.exe (PID: 3624)
- Defender_Control.exe (PID: 3160)
- Defender_Control.exe (PID: 4024)
- Defender_Control.exe (PID: 6668)
- NSudoLG.exe (PID: 3288)
Manual execution by a user
- WinRAR.exe (PID: 3720)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3720)
Reads the software policy settings
- slui.exe (PID: 2076)
Checks proxy server information
- slui.exe (PID: 2076)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:08:10 19:07:26 |
| ZipCRC: | 0xeb6fb5da |
| ZipCompressedSize: | 8233160 |
| ZipUncompressedSize: | 8234644 |
| ZipFileName: | ea05f0206225cc2b447158674d21fc087f56cfa049a2d0318c39d1e5e5dda809.zip |
Total processes
164
Monitored processes
17
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | powershell "try {$null = icim MSFT_MpPreference @{ExclusionPath = @('C:\Users\admin\AppData\Local\Temp\Rar$DIa3720.8245\'); Force = $True} Add -Namespace root/Microsoft/Windows/Defender -EA 1} catch {$host.SetShouldExit($_.Exception.HResult)}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 2148734208 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
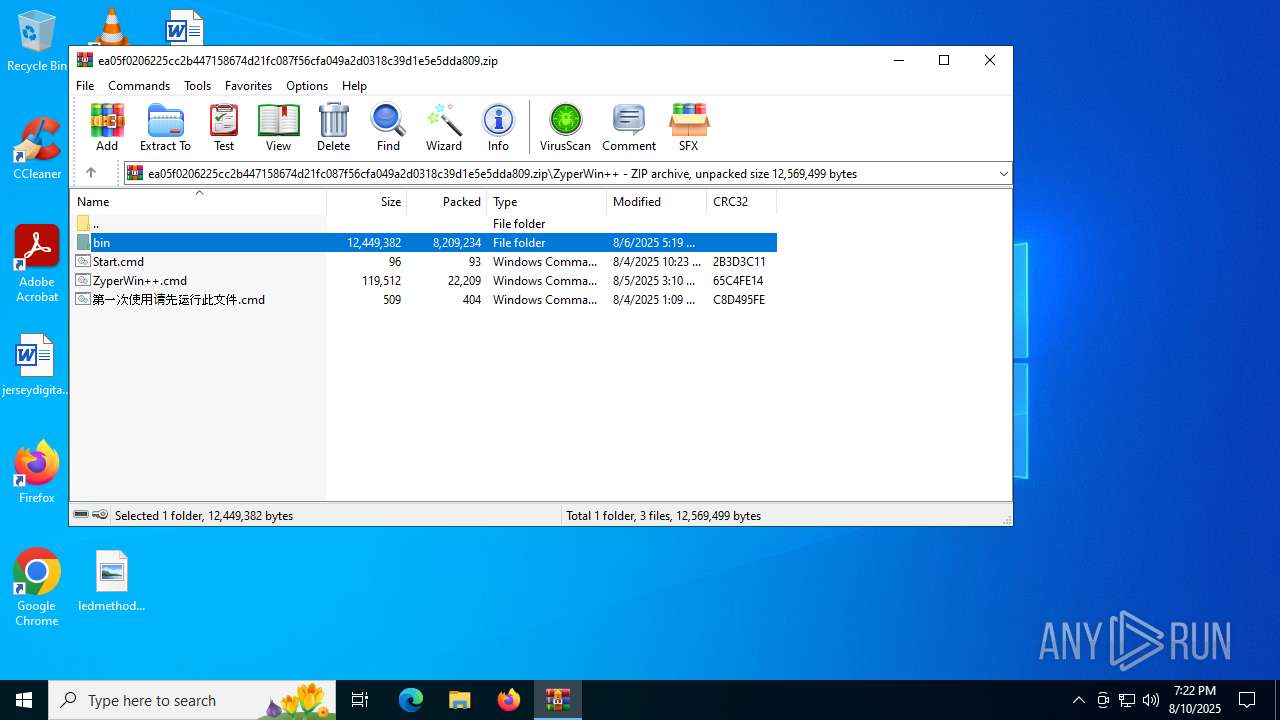
| 888 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.6469\ZyperWin++\bin\Defender_Control.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.6469\ZyperWin++\bin\Defender_Control.exe | — | WinRAR.exe | |||||||||||
User: admin Company: www.sordum.org Integrity Level: MEDIUM Description: dControl v2.1 Exit code: 3221226540 Version: 2.1.0.0 Modules
| |||||||||||||||
| 1056 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.3995\ZyperWin++\bin\Defender_Control.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.3995\ZyperWin++\bin\Defender_Control.exe | — | WinRAR.exe | |||||||||||
User: admin Company: www.sordum.org Integrity Level: MEDIUM Description: dControl v2.1 Exit code: 3221226540 Version: 2.1.0.0 Modules
| |||||||||||||||
| 1932 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.9763\ZyperWin++\bin\NSudoLG.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.9763\ZyperWin++\bin\NSudoLG.exe | — | WinRAR.exe | |||||||||||
User: admin Company: M2-Team Integrity Level: MEDIUM Description: NSudo Launcher Exit code: 3221226540 Version: 9.0.2676.0 Modules
| |||||||||||||||
| 2076 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2760 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2848 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3160 | C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.3995\ZyperWin++\bin\Defender_Control.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.3995\ZyperWin++\bin\Defender_Control.exe | Defender_Control.exe | ||||||||||||
User: SYSTEM Company: www.sordum.org Integrity Level: SYSTEM Description: dControl v2.1 Exit code: 0 Version: 2.1.0.0 Modules
| |||||||||||||||
| 3288 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.9763\ZyperWin++\bin\NSudoLG.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.9763\ZyperWin++\bin\NSudoLG.exe | WinRAR.exe | ||||||||||||
User: admin Company: M2-Team Integrity Level: HIGH Description: NSudo Launcher Exit code: 0 Version: 9.0.2676.0 Modules
| |||||||||||||||
| 3624 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.3995\ZyperWin++\bin\Defender_Control.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.3995\ZyperWin++\bin\Defender_Control.exe | WinRAR.exe | ||||||||||||
User: admin Company: www.sordum.org Integrity Level: HIGH Description: dControl v2.1 Exit code: 0 Version: 2.1.0.0 Modules
| |||||||||||||||
Total events
10 401
Read events
10 350
Write events
50
Delete events
1
Modification events
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\ea05f0206225cc2b447158674d21fc087f56cfa049a2d0318c39d1e5e5dda809.zip (1).zip | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
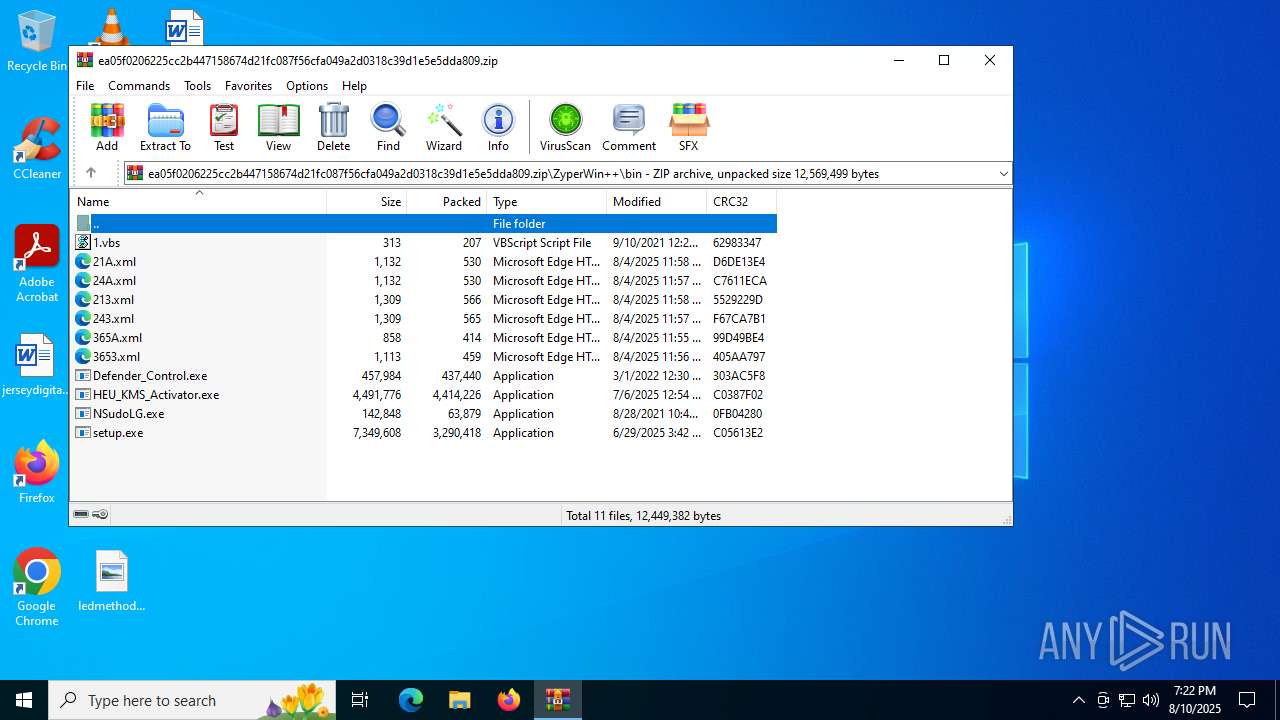
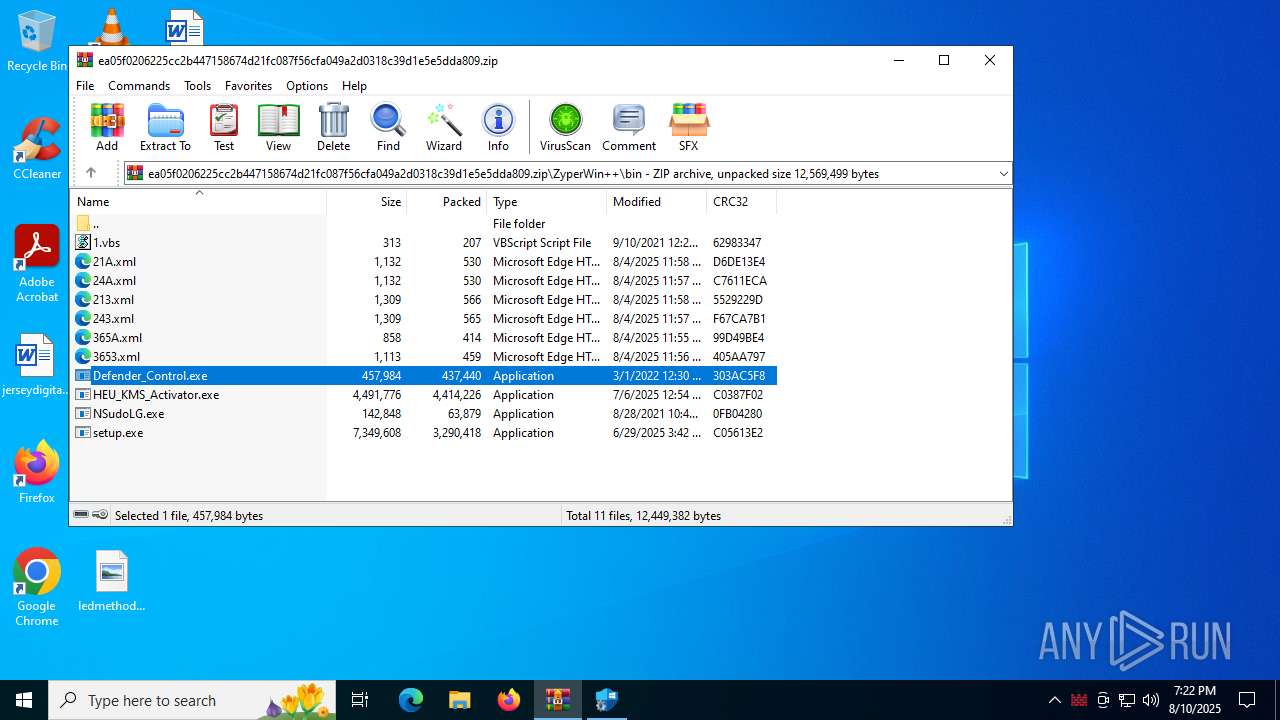
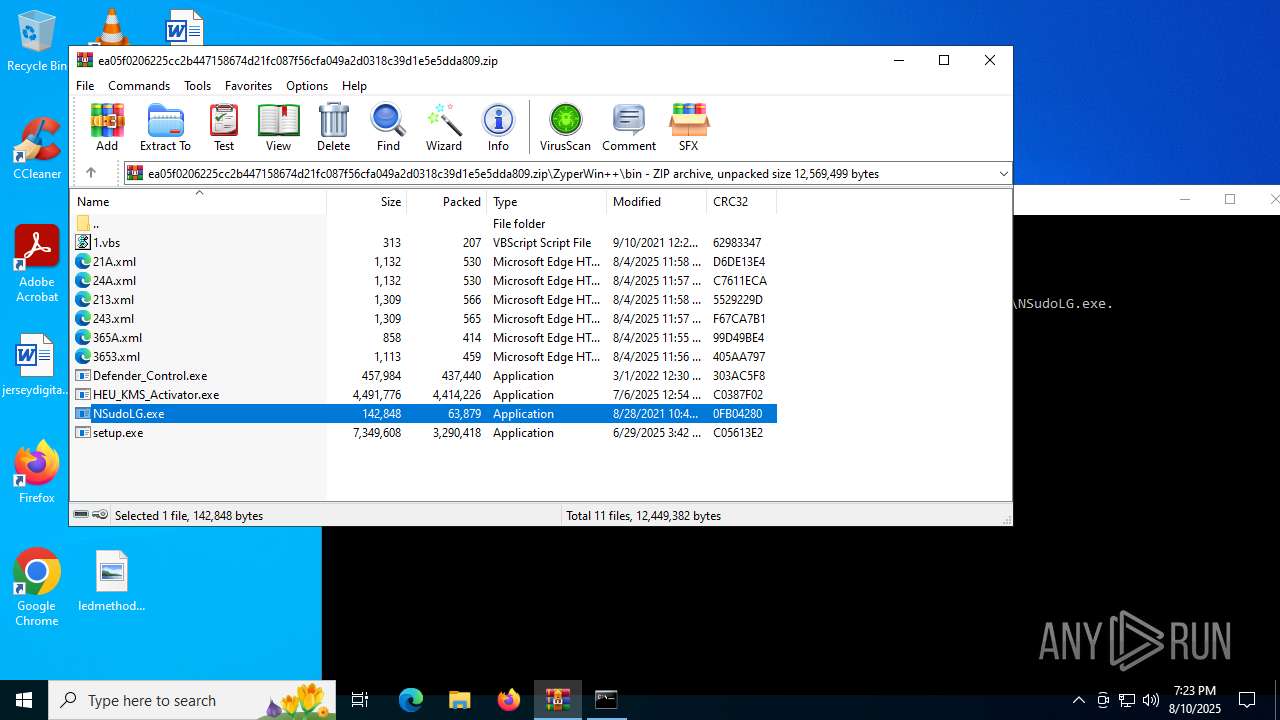
Executable files
12
Suspicious files
15
Text files
42
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.3995\ZyperWin++\bin\213.xml | text | |
MD5:52B197A0698E66A5B011AC873840325B | SHA256:A264221C9C11C6EA0932FF351E871D62C296EDF6AF623295FB94438B11ACB7FA | |||
| 3720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.3995\ZyperWin++\bin\24A.xml | text | |
MD5:6796421675756C9CA6AB09D4226833BA | SHA256:91A32E26AF1CA2EE56492D0BCD0C1F6EDDB7479A72D80209C5ECA42AC3EA7AE9 | |||
| 3720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.3995\ZyperWin++\bin\21A.xml | text | |
MD5:6156067FC6671DADB7525DEFF5AC7870 | SHA256:2438383E4C0DE3417177B55D513A8A8722EC44607458998BBDA8F69E0EC38214 | |||
| 3720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.3995\ZyperWin++\bin\setup.exe | executable | |
MD5:B88216E9727418C74C3E9EBA7AAB7979 | SHA256:AB55449661354567539CE611B7DA6BEE90444F7D4C417A685E39B7F415F8C1B9 | |||
| 3720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.3995\ZyperWin++\bin\243.xml | text | |
MD5:A5646C12BFCD01710D167913991ED646 | SHA256:5EA3141EA3C6ED88C71B35E5FD60EF8E3FC102149358CB5F1D8EC7030EA9FD35 | |||
| 3720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.3995\ZyperWin++\bin\NSudoLG.exe | executable | |
MD5:44BE11477673BAA42C7FA7423E8F4604 | SHA256:BDD9286EAEFC70E313748693A0372EAA18DE535FFEBFAE0EF658F88F53073E6F | |||
| 3720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.3995\ZyperWin++\bin\3653.xml | text | |
MD5:E06B266C17236054F64B5CE2CF886364 | SHA256:CDD993EC0C491795DE7649F62257C0E3CACCFDFF53799DF1A31C6F801421AE12 | |||
| 3720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.3995\ZyperWin++\Start.cmd | text | |
MD5:AAAB185C5B24985092AA3D3DF6F5C8A8 | SHA256:7157C78D71E906328184F031D7AE60076BB1122F8F0ECE40079A824ADF7C8CBA | |||
| 3720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.3995\ZyperWin++\bin\Defender_Control.exe | executable | |
MD5:58008524A6473BDF86C1040A9A9E39C3 | SHA256:1EF6C1A4DFDC39B63BFE650CA81AB89510DE6C0D3D7C608AC5BE80033E559326 | |||
| 3624 | Defender_Control.exe | C:\Users\admin\AppData\Local\Temp\3o6f2h4n.tmp | text | |
MD5:E00DCC76E4DCD90994587375125DE04B | SHA256:C8709F5A8B971D136E2273D66E65449791CA8EBA1F47DD767733EA52EE635447 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
25
DNS requests
21
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.29:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.32.97.216:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
504 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2604 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2604 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6312 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.216.77.29:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.32.97.216:80 | www.microsoft.com | AKAMAI-AS | SE | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
504 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |