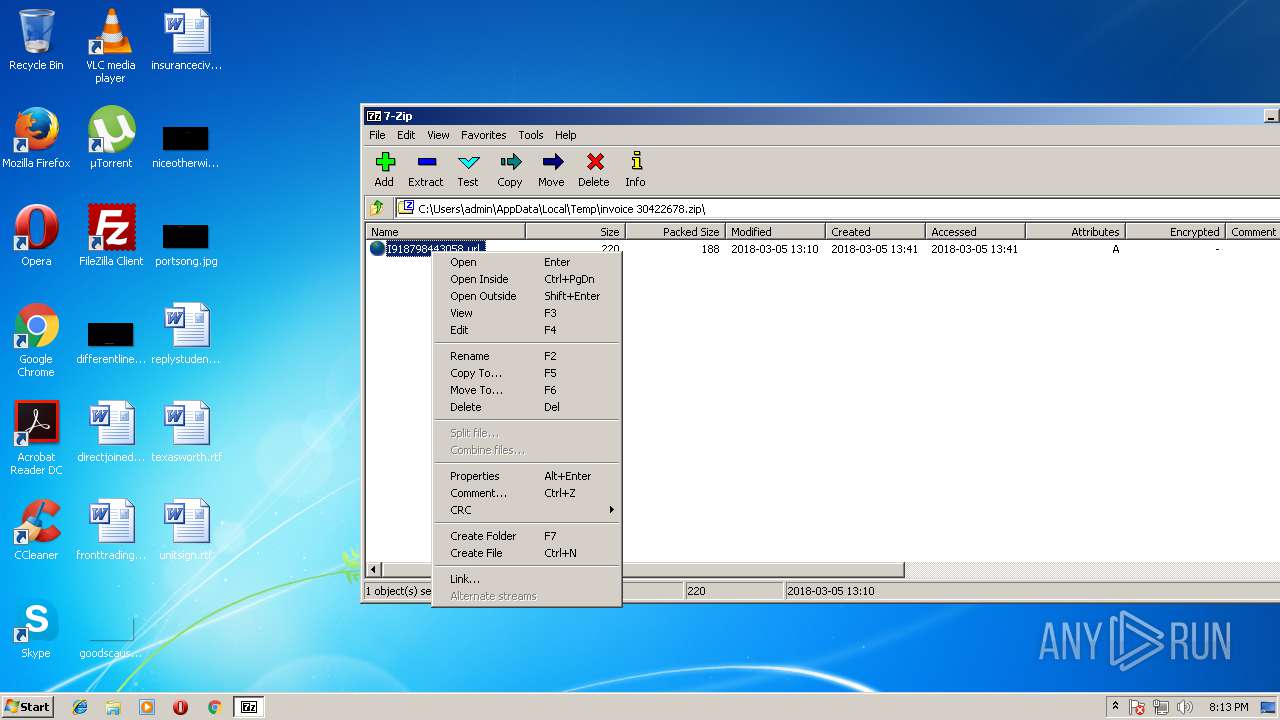
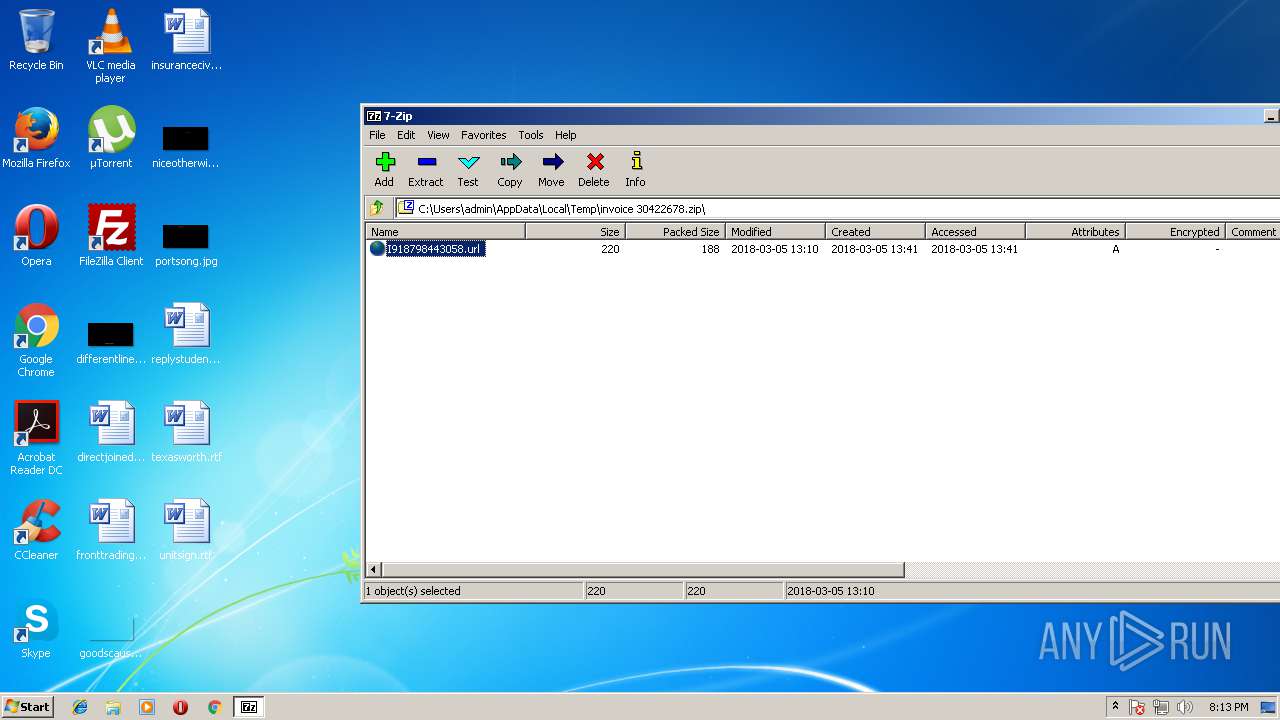
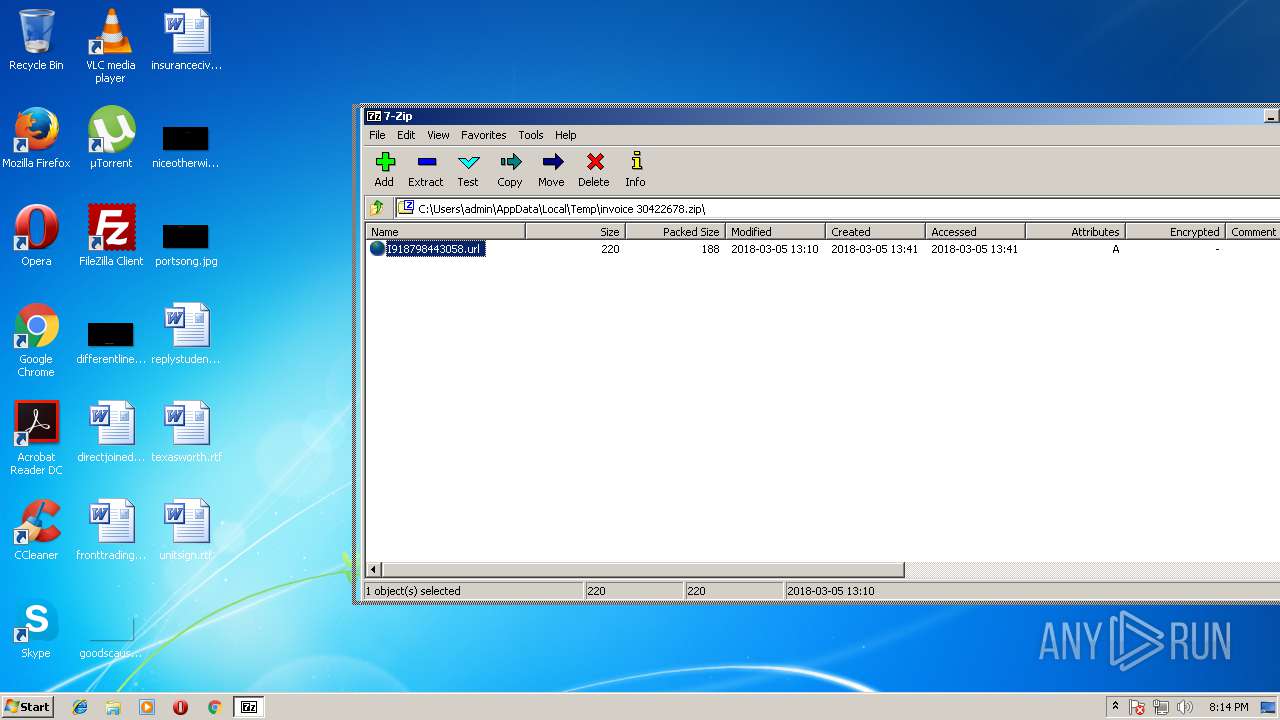
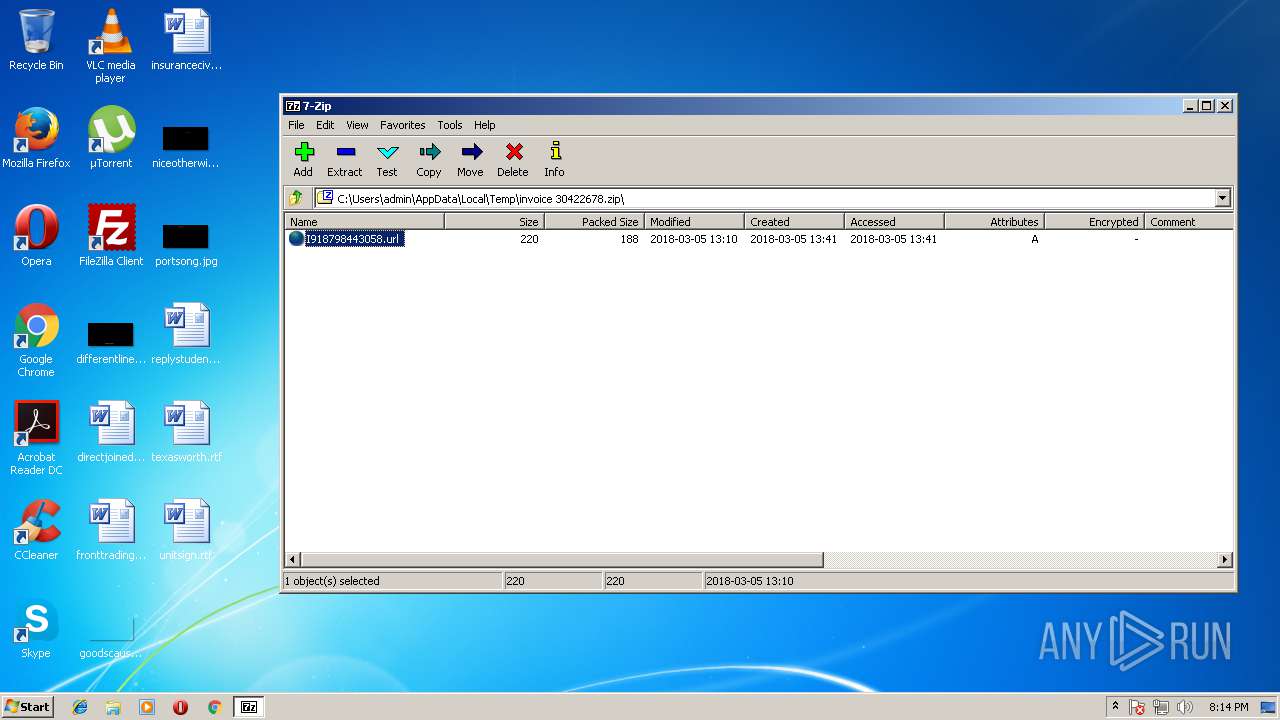
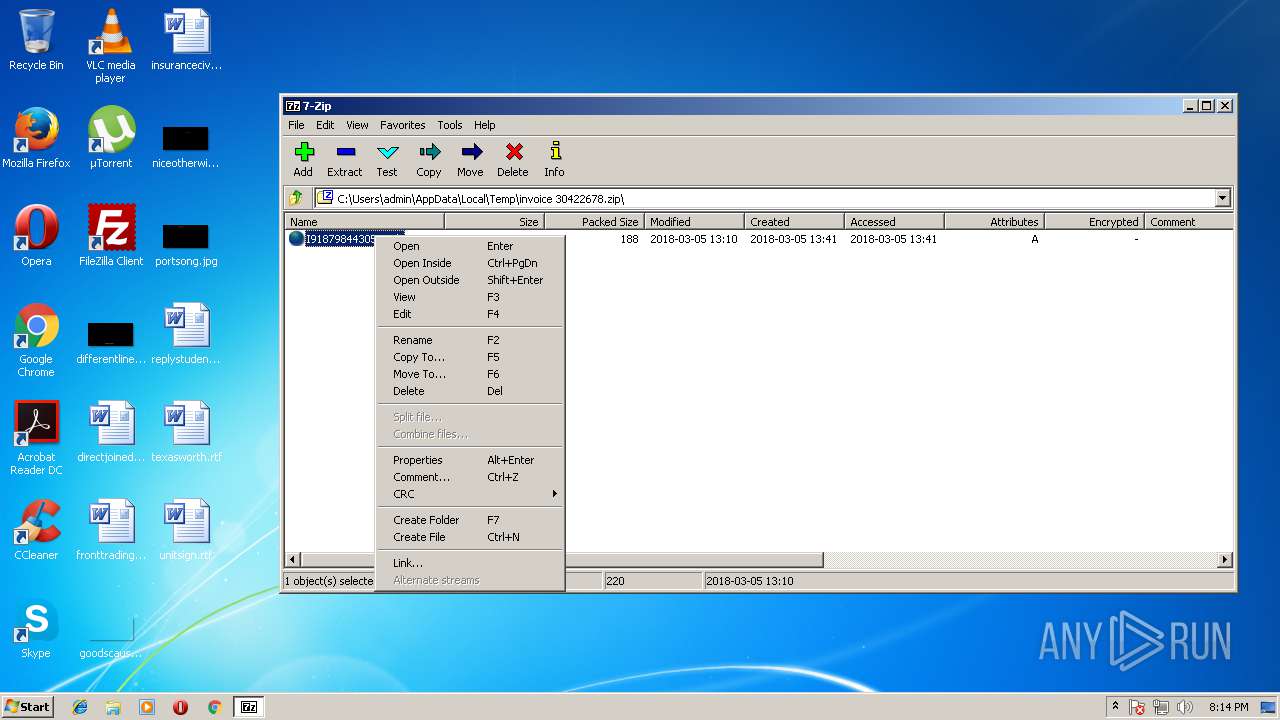
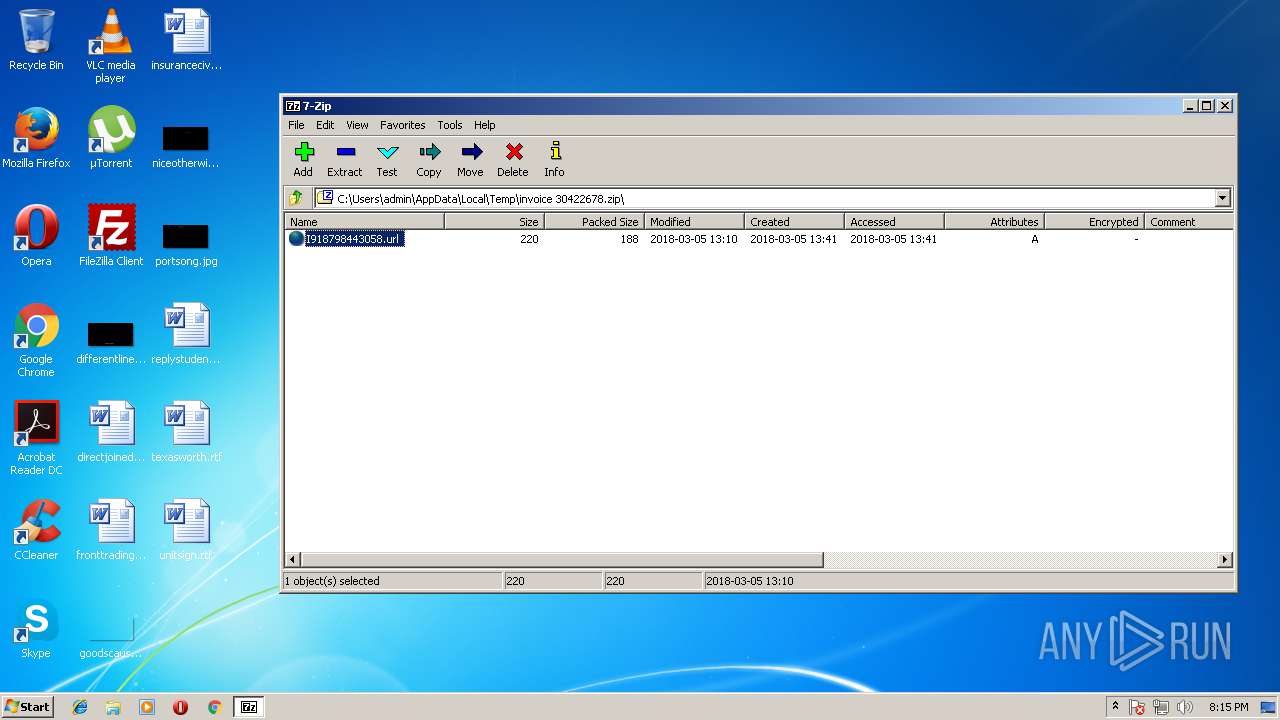
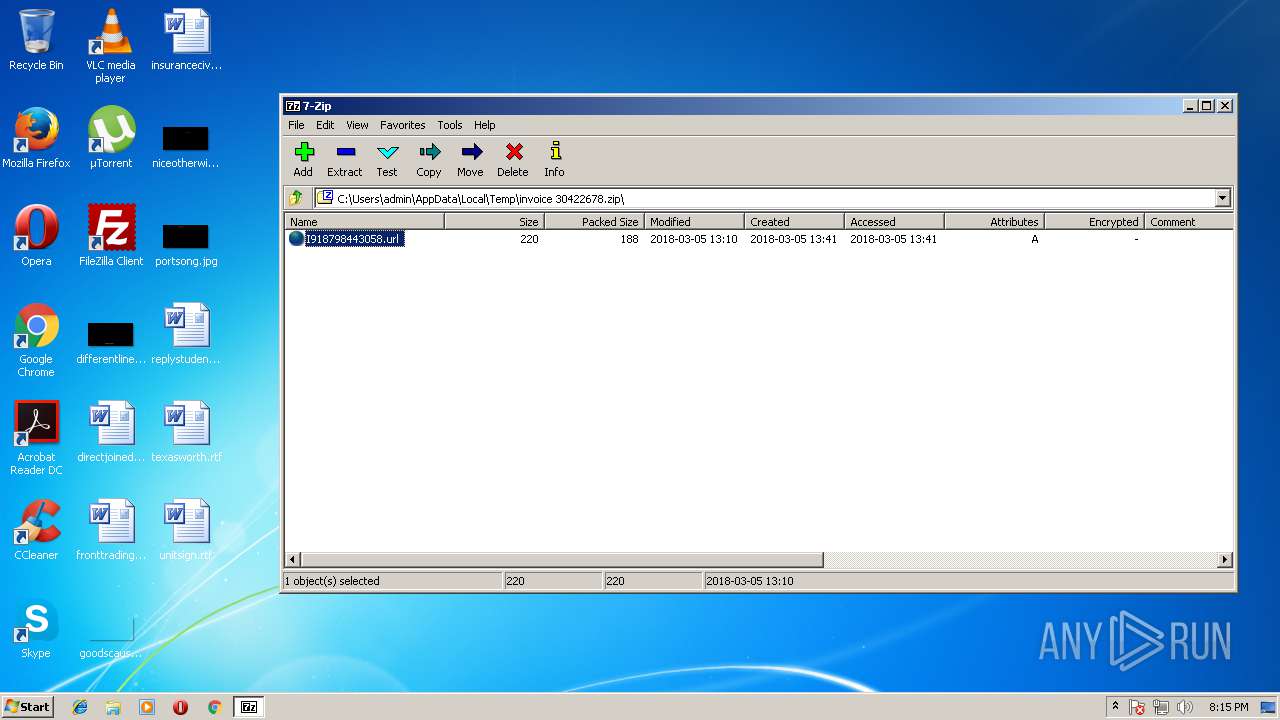
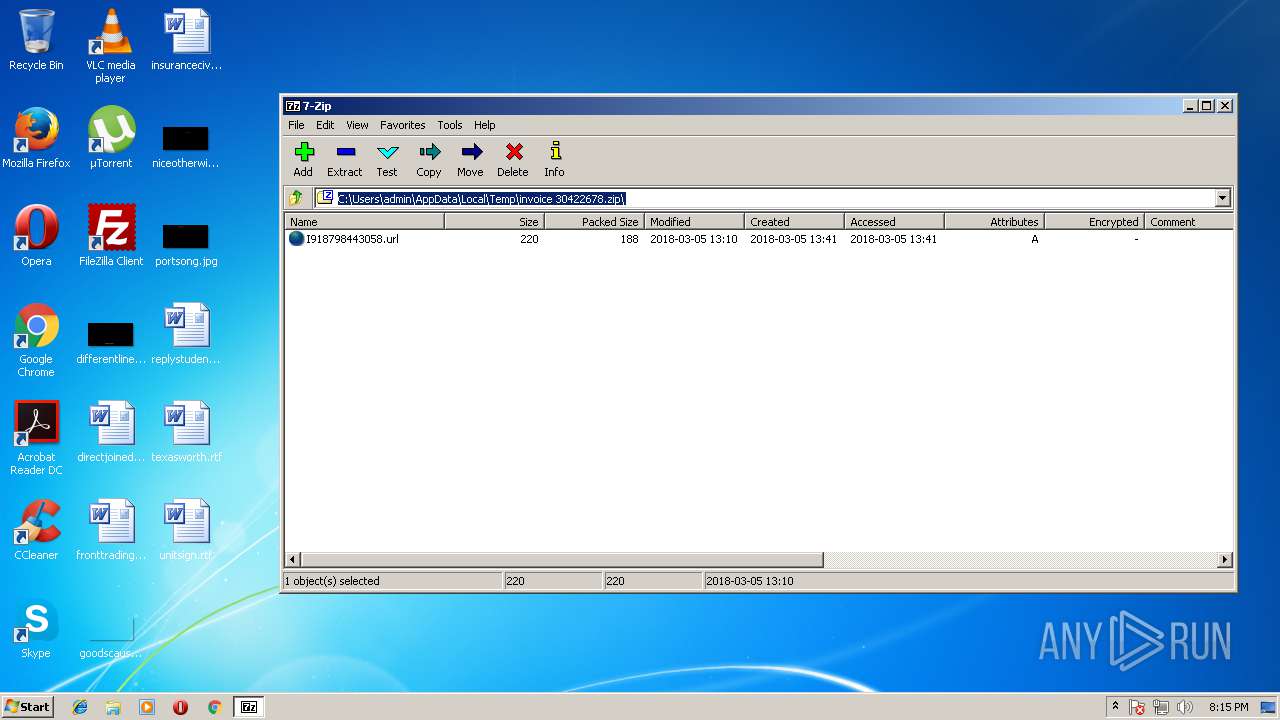
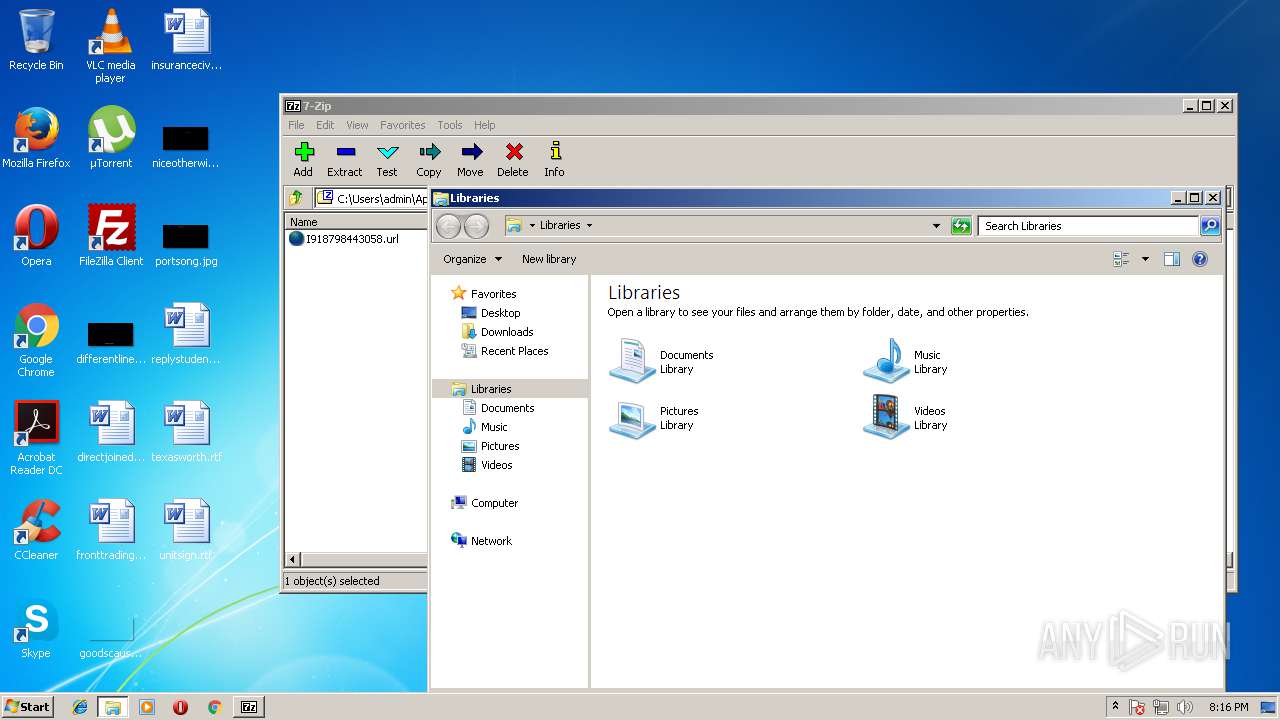
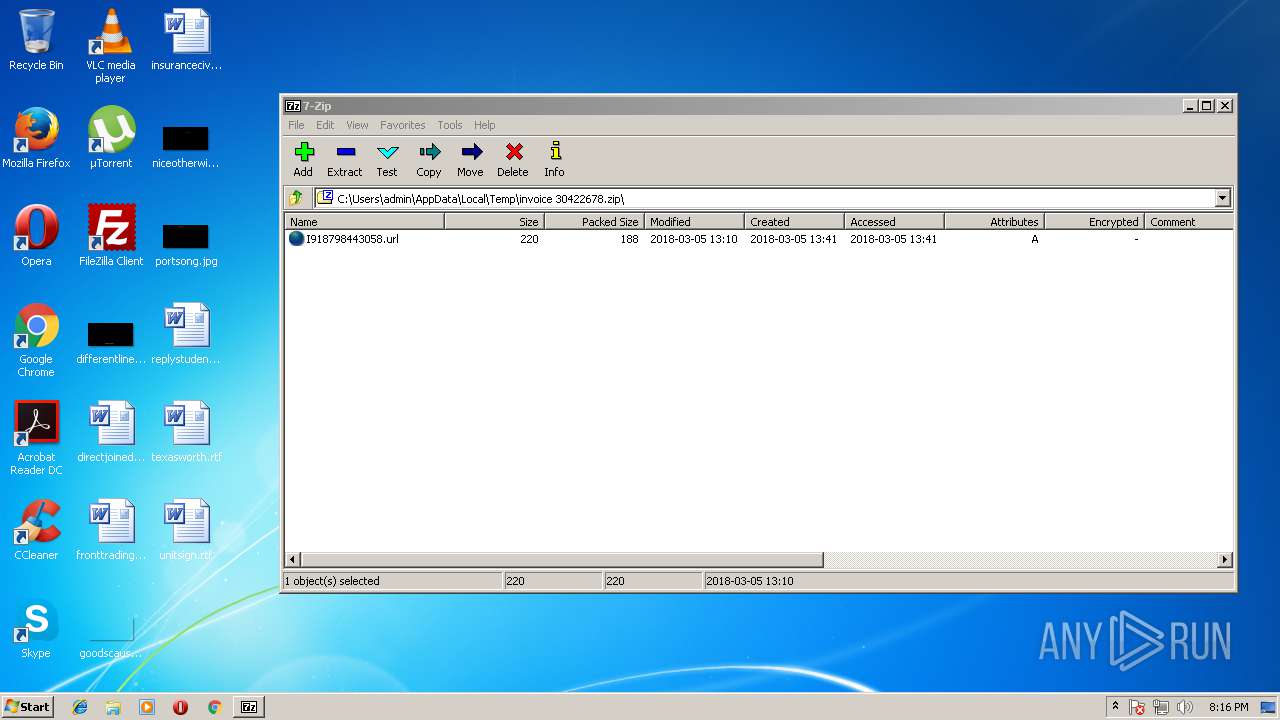
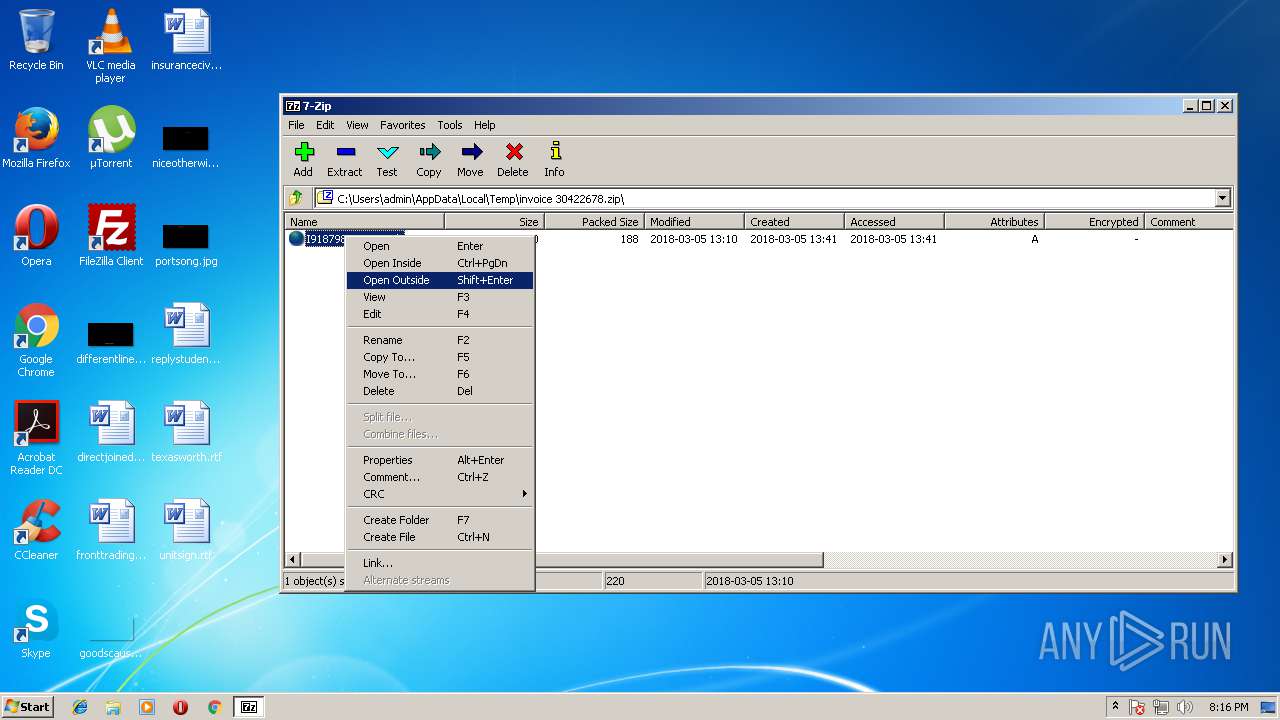
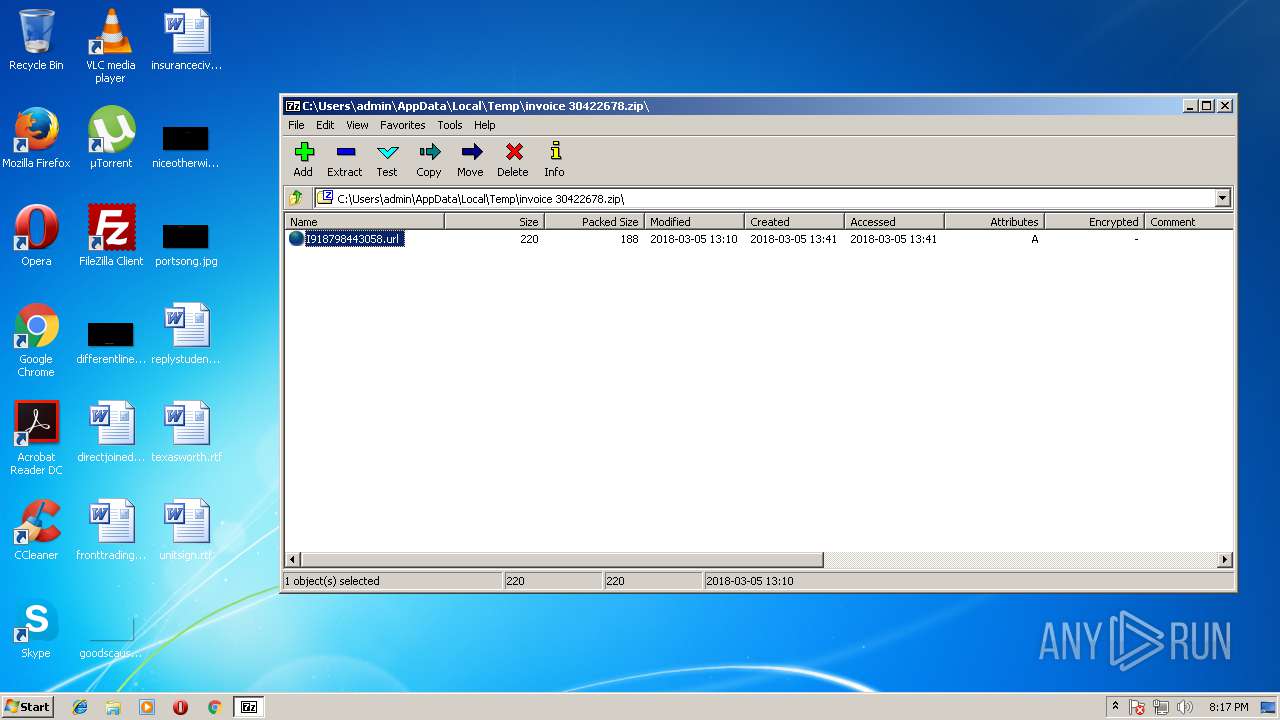
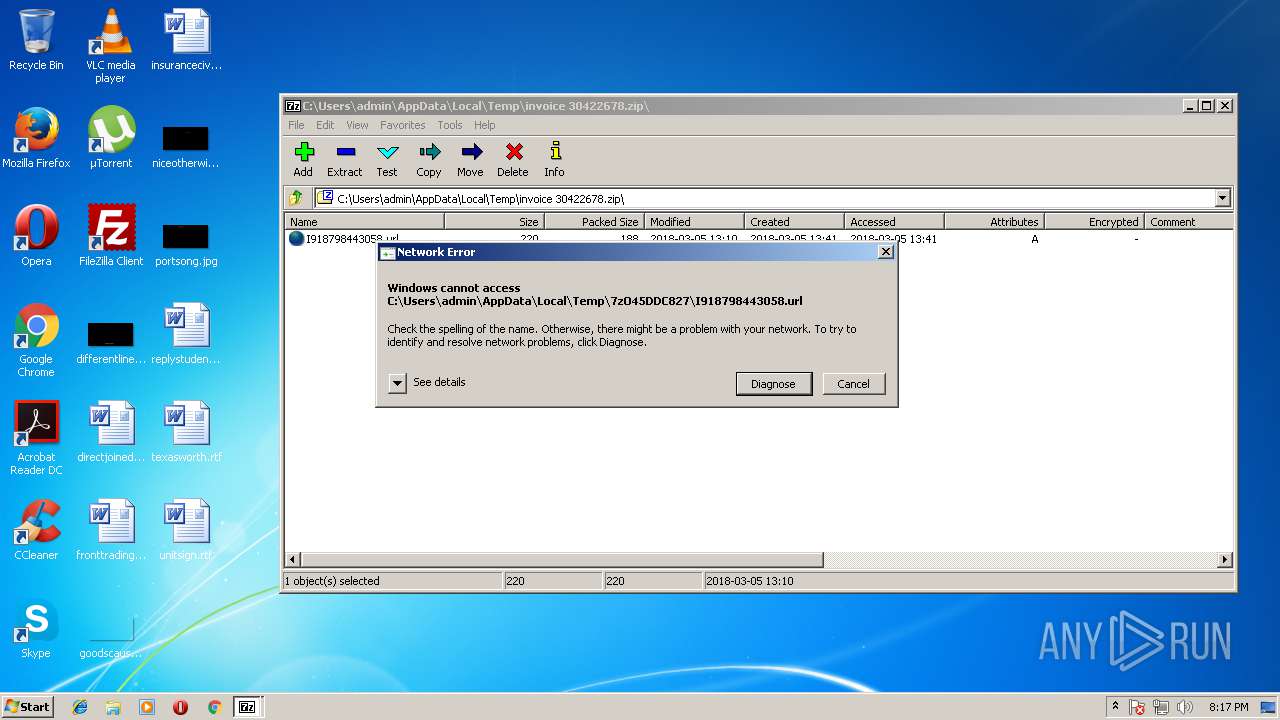
| File name: | invoice 30422678.zip |
| Full analysis: | https://app.any.run/tasks/8216e7db-246c-4f79-bb05-a6a04695e213 |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2018, 19:12:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 436DAF137D6294209163670BE88C0F85 |
| SHA1: | 7F0CFE6402C2CDE47C0233CC3FE25E673477D1C3 |
| SHA256: | EA1E873D574B82111C1A17E8DF31FAC0F31A5487264CB398243D8674A2B3F3F8 |
| SSDEEP: | 6:5jHQtzZ8/s2D/QMTCwVxaHs3vV25WUHRXj5T1p9/o7I97AJQB7ZnzbMyP+l0:5jv/s2D7aM0oq5Bbo7wzoUa0 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- msdt.exe (PID: 1352)
- msdt.exe (PID: 3796)
- msdt.exe (PID: 2780)
Application launched itself
- msdt.exe (PID: 1352)
Creates files in the Windows directory
- msdt.exe (PID: 2780)
Removes files from Windows directory
- msdt.exe (PID: 2780)
INFO
Dropped object may contain URL's
- msdt.exe (PID: 1352)
- msdt.exe (PID: 3796)
- msdt.exe (PID: 2780)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
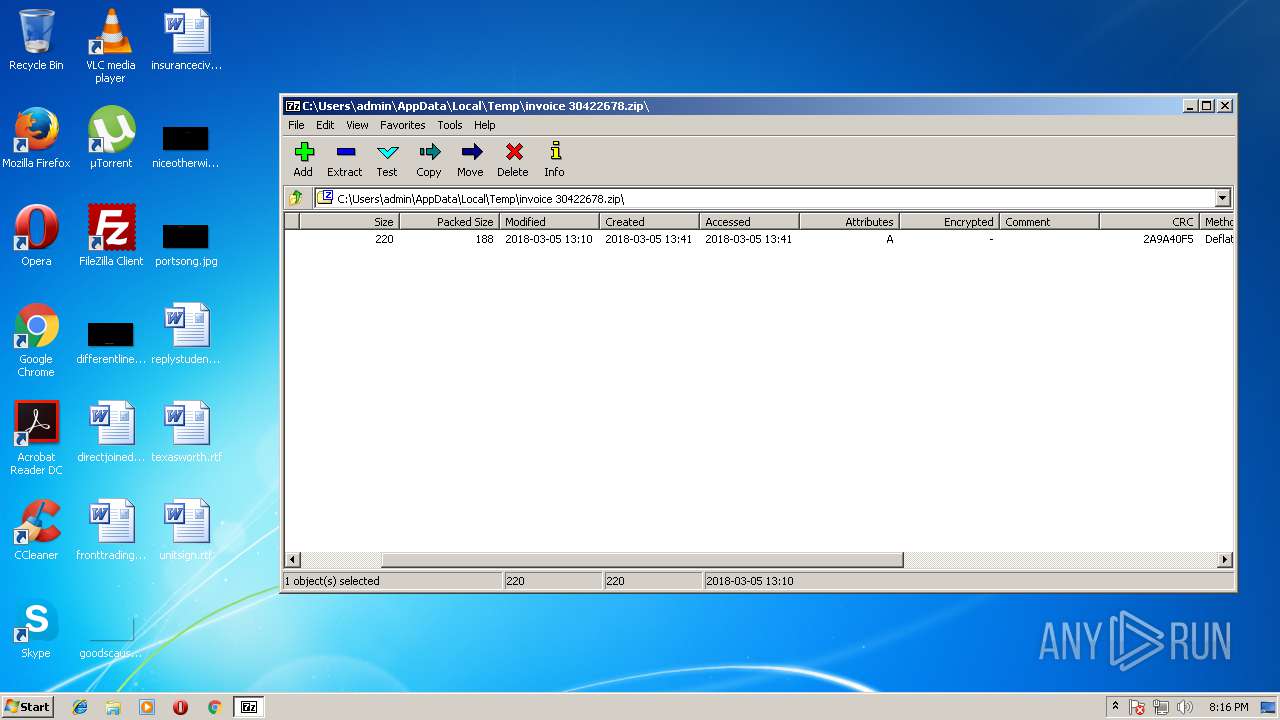
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:03:05 15:10:15 |
| ZipCRC: | 0x2a9a40f5 |
| ZipCompressedSize: | 188 |
| ZipUncompressedSize: | 220 |
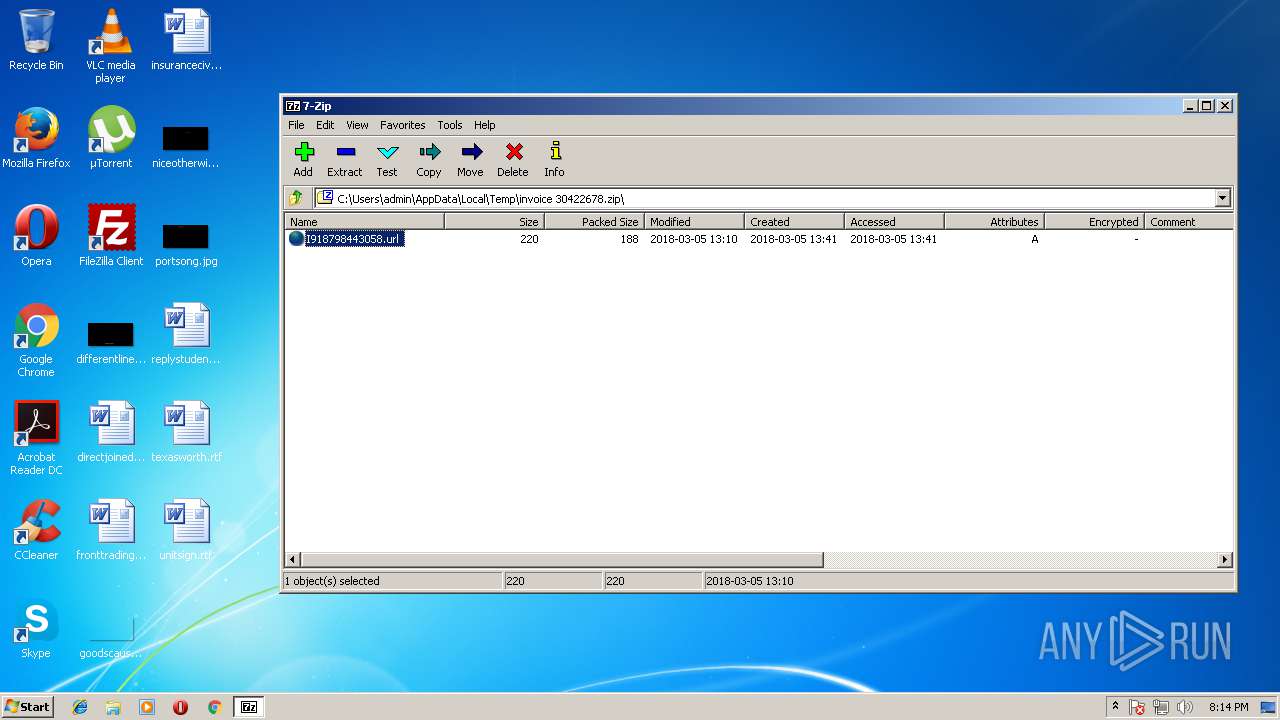
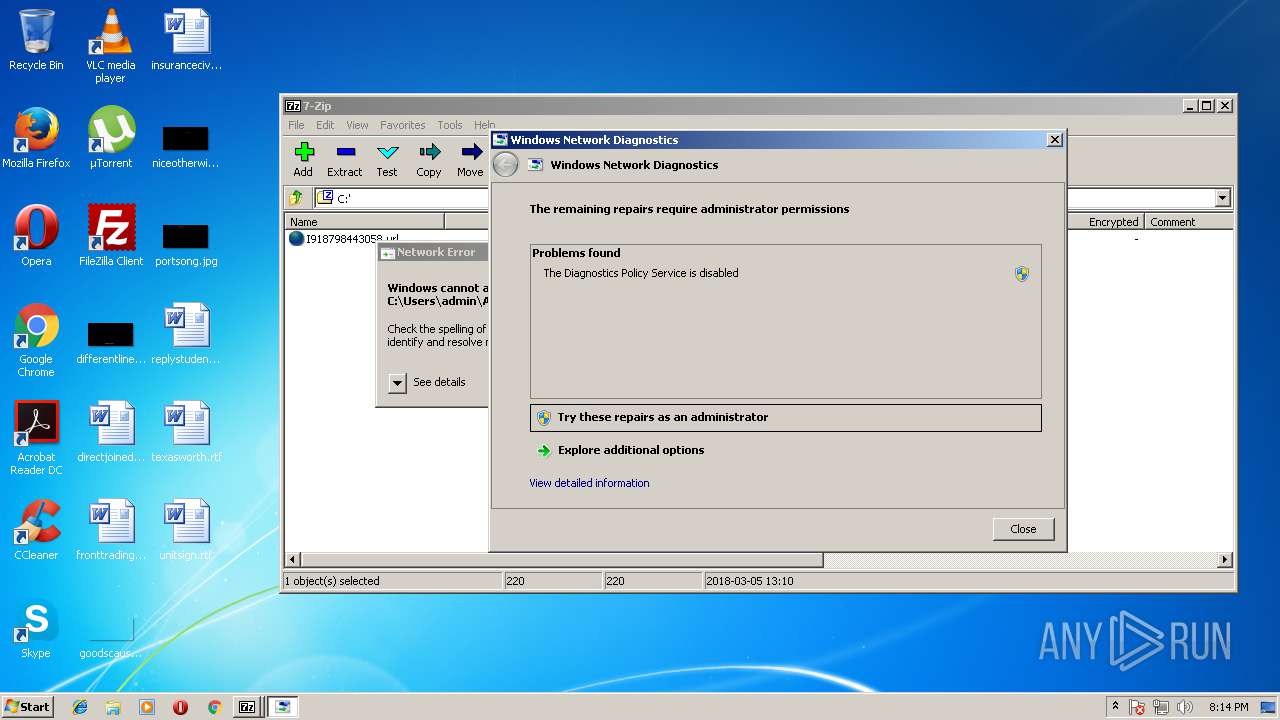
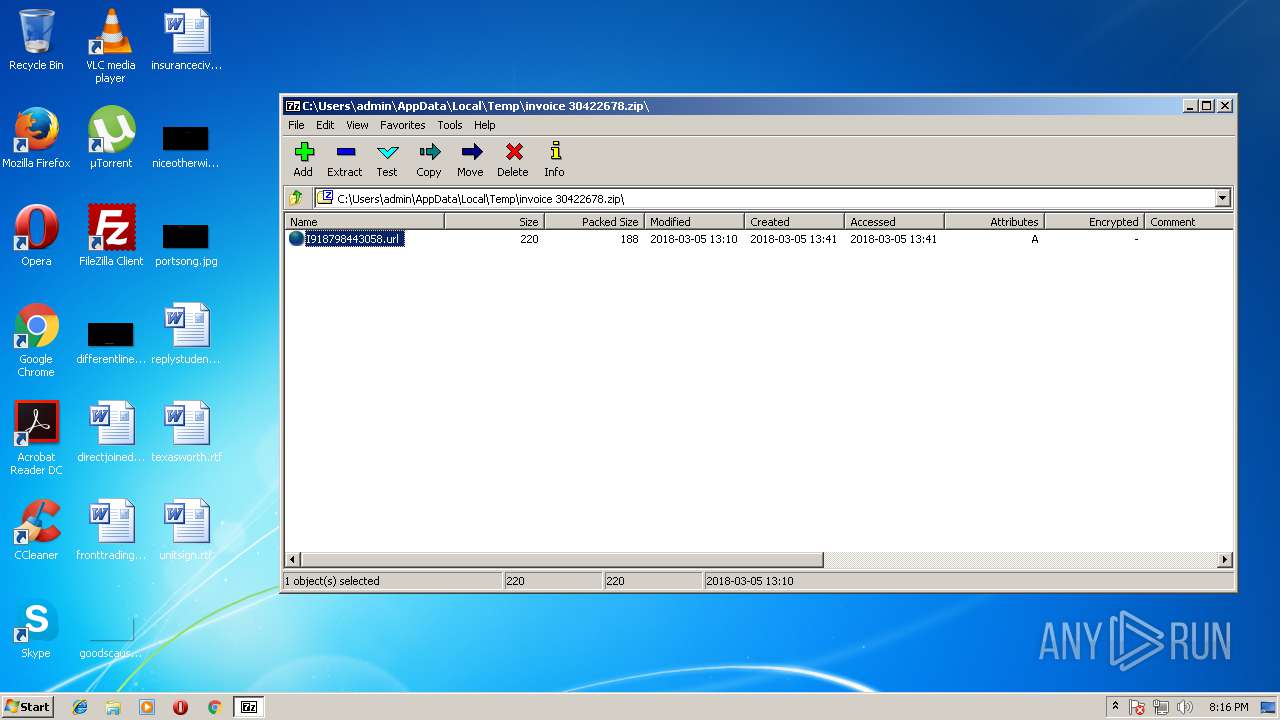
| ZipFileName: | I918798443058.url |
Total processes
50
Monitored processes
11
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
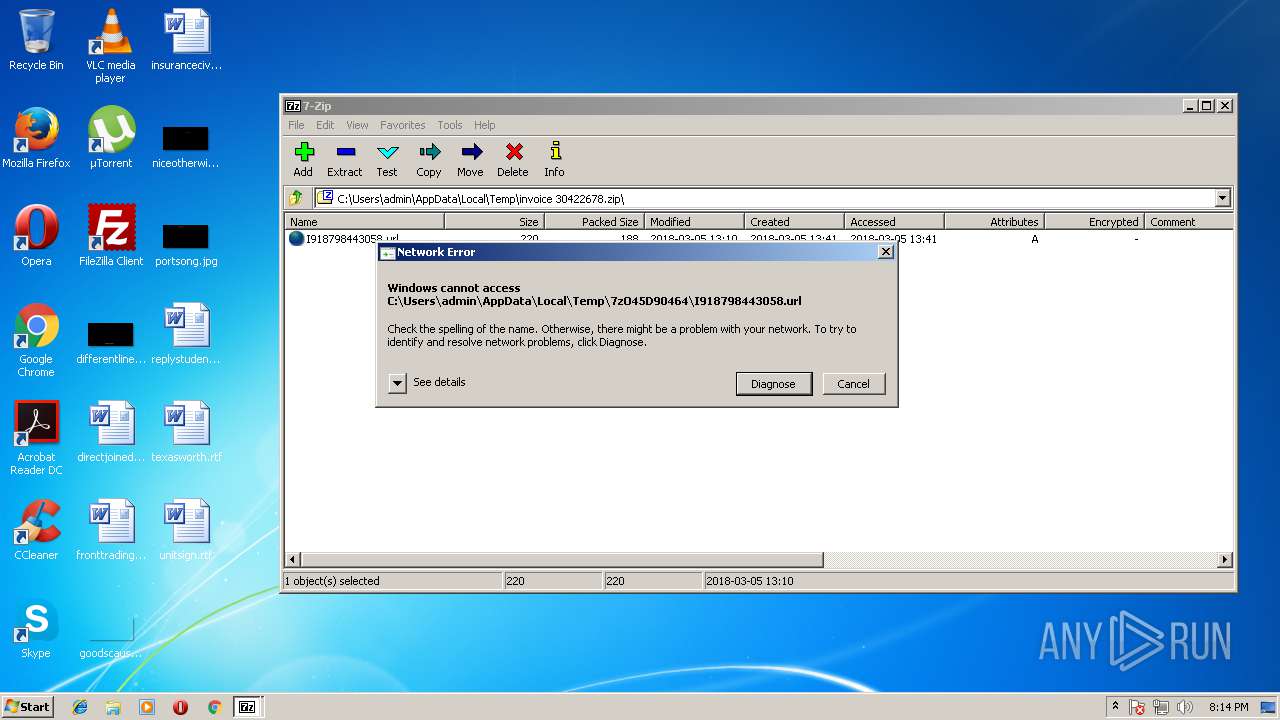
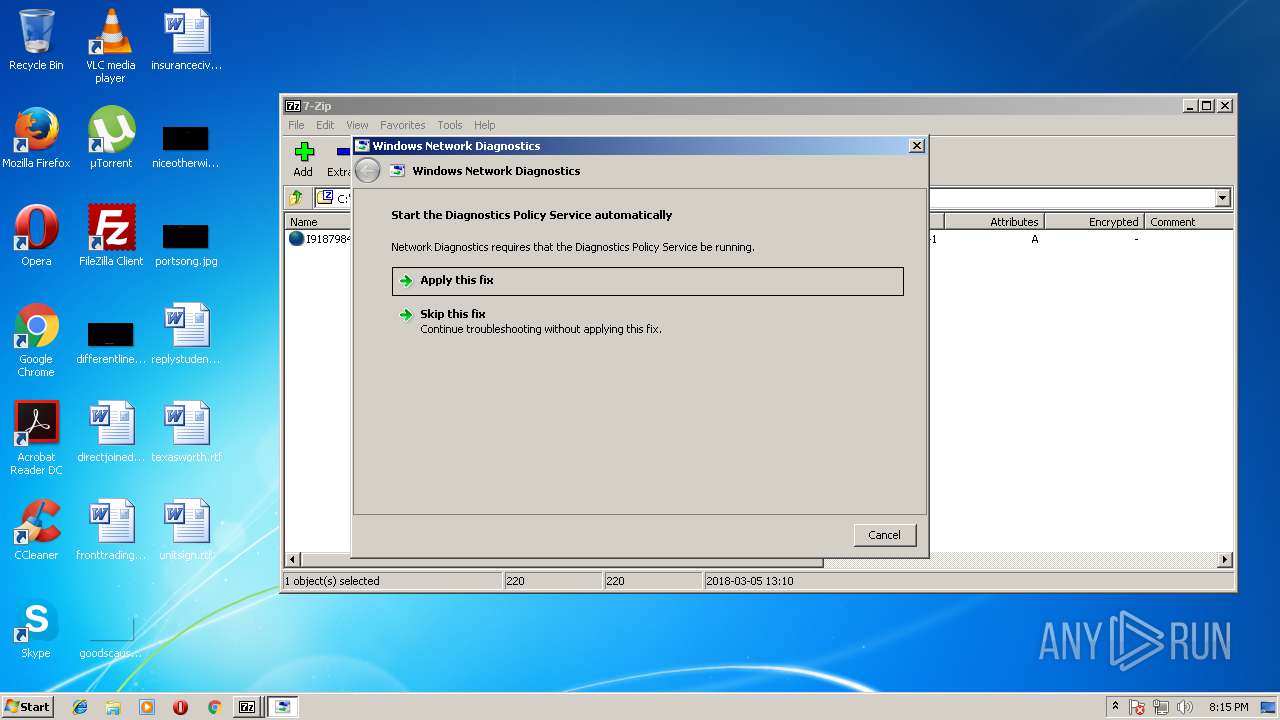
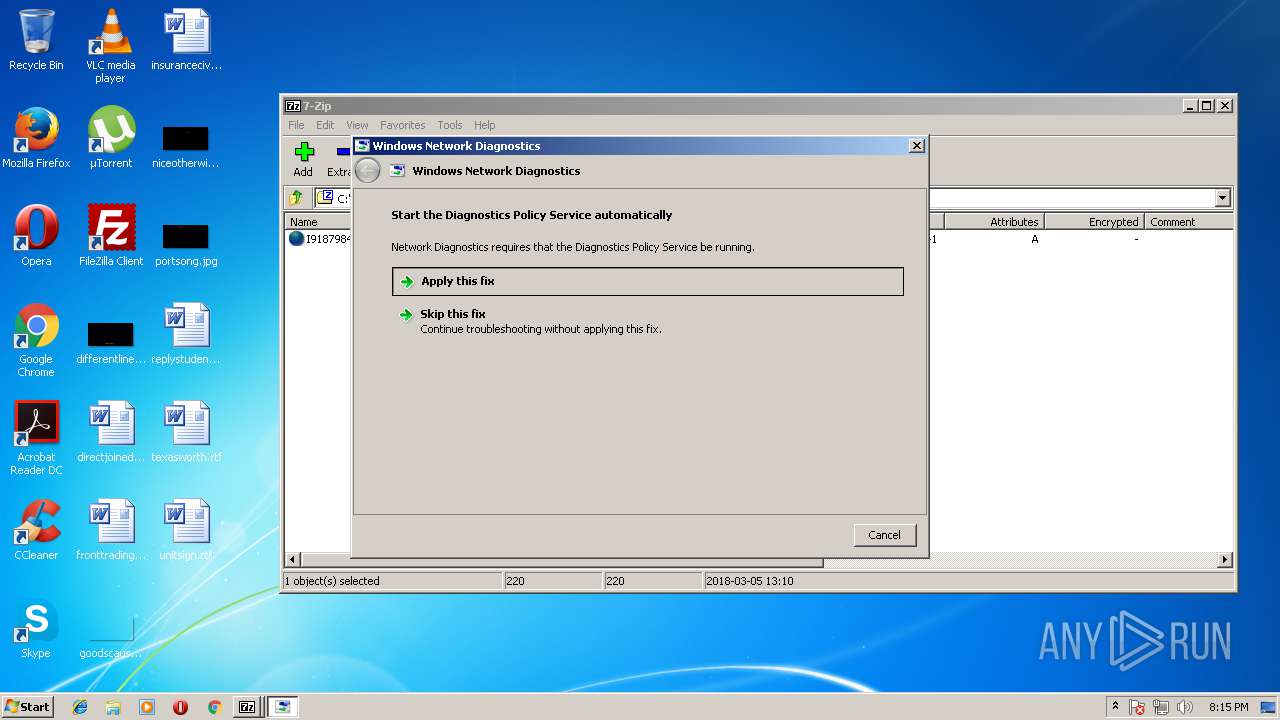
| 688 | "C:\Windows\system32\rundll32.exe" ndfapi.dll,NdfRunDllDiagnoseWithAnswerFile NetworkDiagnosticsSharing C:\Users\admin\AppData\Local\Temp\NDF4225.tmp | C:\Windows\system32\rundll32.exe | — | 7zFM.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
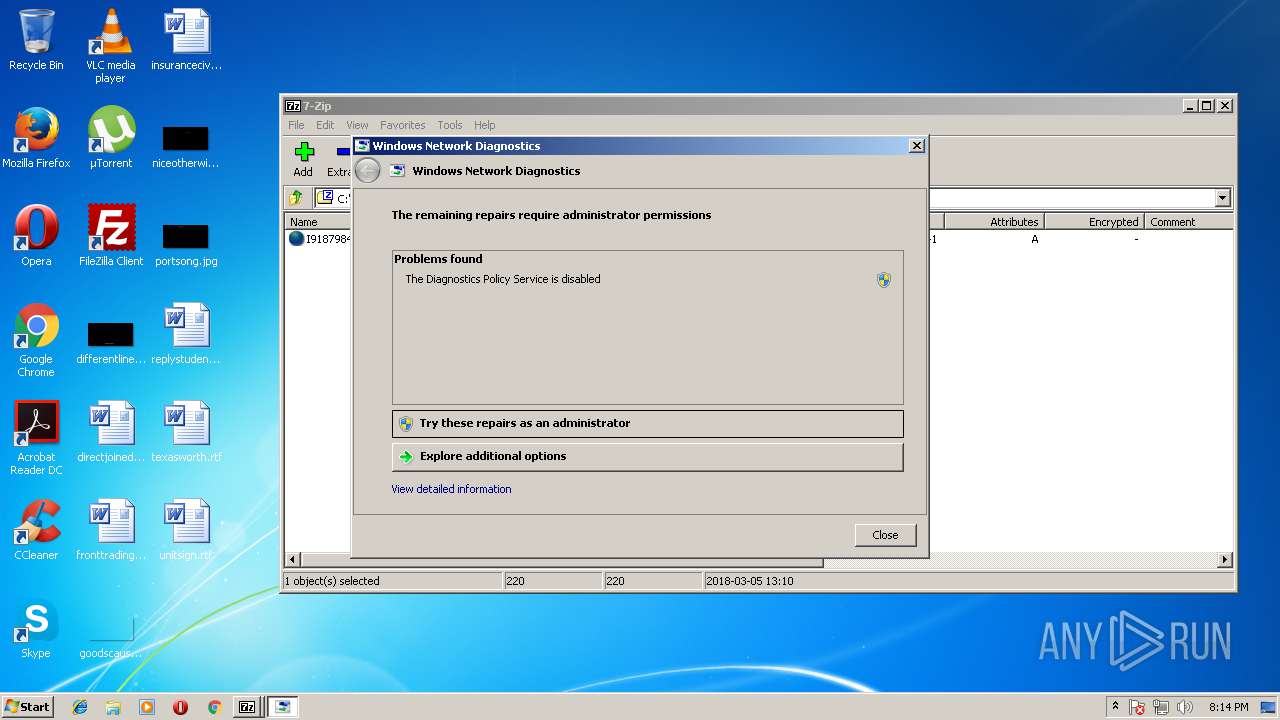
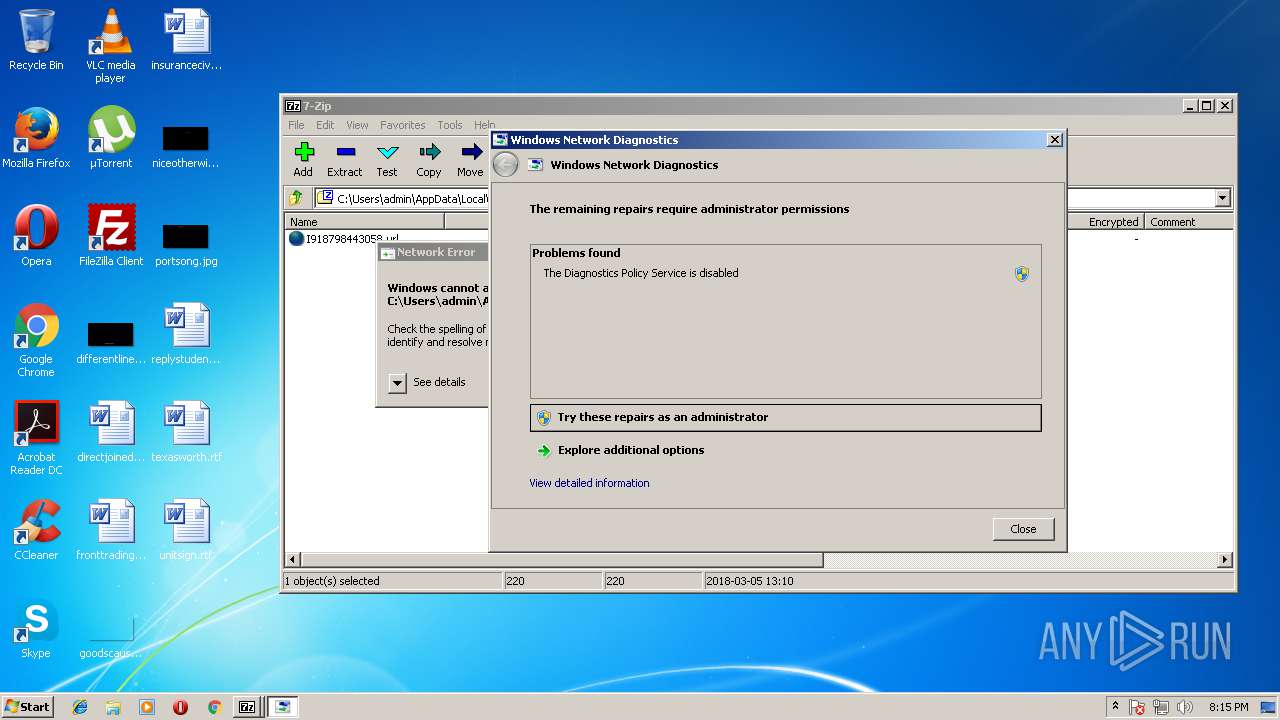
| 1352 | -skip TRUE -path C:\Windows\diagnostics\system\networking -af C:\Users\admin\AppData\Local\Temp\NDF8FD6.tmp -ep NetworkDiagnosticsSharing | C:\Windows\system32\msdt.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Diagnostics Troubleshooting Wizard Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1516 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Scripted Diagnostics Native Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
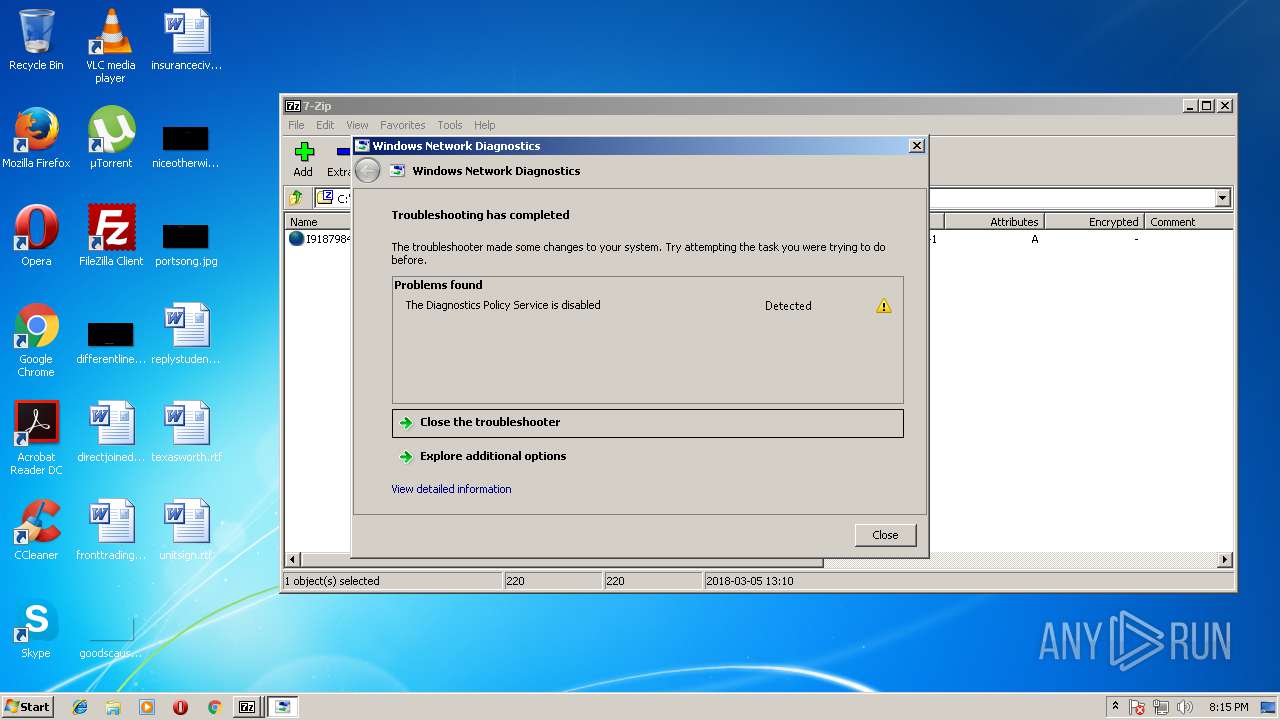
| 2780 | "C:\Windows\system32\msdt.exe" -path "C:\Windows\diagnostics\system\networking" -skip force -af "C:\Users\admin\AppData\Local\Temp\NDF8FD6.tmp" -ep NetworkDiagnosticsSharing -elevated yes | C:\Windows\system32\msdt.exe | msdt.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Diagnostics Troubleshooting Wizard Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2916 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2952 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Scripted Diagnostics Native Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3204 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Scripted Diagnostics Native Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3404 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Scripted Diagnostics Native Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
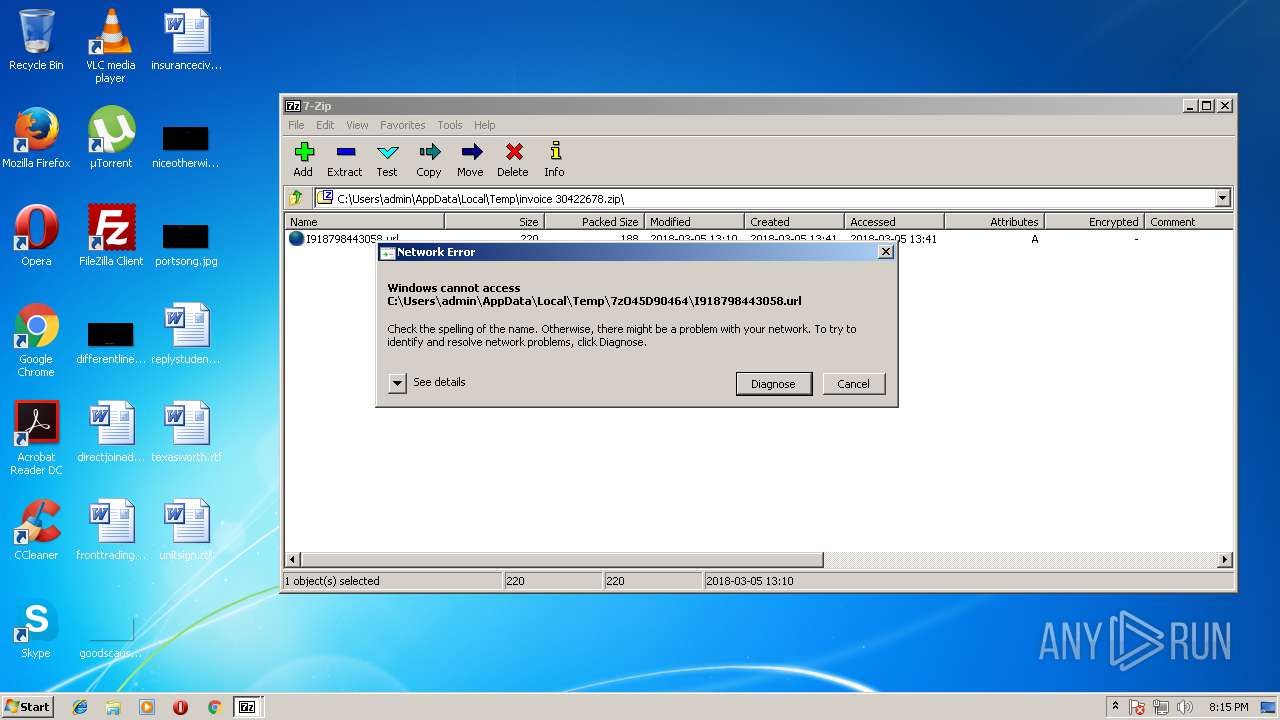
| 3412 | "C:\Program Files\7-Zip\7zFM.exe" "C:\Users\admin\AppData\Local\Temp\invoice 30422678.zip" | C:\Program Files\7-Zip\7zFM.exe | explorer.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip File Manager Exit code: 0 Version: 16.04 Modules
| |||||||||||||||
| 3612 | "C:\Windows\system32\rundll32.exe" ndfapi.dll,NdfRunDllDiagnoseWithAnswerFile NetworkDiagnosticsSharing C:\Users\admin\AppData\Local\Temp\NDF8FD6.tmp | C:\Windows\system32\rundll32.exe | — | 7zFM.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
776
Read events
715
Write events
61
Delete events
0
Modification events
| (PID) Process: | (3412) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {FBF23B40-E3F0-101B-8488-00AA003E56F8} {000214E4-0000-0000-C000-000000000046} 0xFFFF |
Value: 0100000000000000A06E8A1C13EED301 | |||
| (PID) Process: | (1352) msdt.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\93\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3412) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3412) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3204) sdiagnhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3204) sdiagnhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (1352) msdt.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1352) msdt.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2780) msdt.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\93\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3404) sdiagnhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
8
Suspicious files
9
Text files
80
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1352 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_ff9a166f-694d-407b-85e3-a8e2797f00d9\result\DebugReport.xml | — | |
MD5:— | SHA256:— | |||
| 1352 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_ff9a166f-694d-407b-85e3-a8e2797f00d9\result\ResultReport.xml | — | |
MD5:— | SHA256:— | |||
| 1352 | msdt.exe | C:\Users\admin\AppData\Local\Diagnostics\460911090\2018051719.000\DebugReport.xml | — | |
MD5:— | SHA256:— | |||
| 3412 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\NDF8FD6.tmp | binary | |
MD5:— | SHA256:— | |||
| 1352 | msdt.exe | C:\Users\admin\AppData\Local\Diagnostics\460911090\2018051719.000\ResultReport.xml | xml | |
MD5:— | SHA256:— | |||
| 1352 | msdt.exe | C:\Users\admin\AppData\Local\Diagnostics\460911090\2018051719.000\NetworkDiagnostics.0.debugreport.xml | xml | |
MD5:— | SHA256:— | |||
| 1352 | msdt.exe | C:\Users\admin\AppData\Local\Temp\PLA769B.tmp | — | |
MD5:— | SHA256:— | |||
| 1352 | msdt.exe | C:\Users\admin\AppData\Local\Temp\PLA6848.tmp | — | |
MD5:— | SHA256:— | |||
| 1352 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_ff9a166f-694d-407b-85e3-a8e2797f00d9\InteractiveRes.ps1 | text | |
MD5:25B8543DBF571F040118423BC3C7A75E | SHA256:D78E6291D6F27AC6FEBDCF0A4D5A34521E7F033AF8875E026DF21BA7513AB64A | |||
| 1352 | msdt.exe | C:\Users\admin\AppData\Local\Temp\PLA3F96.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
10
DNS requests
7
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 91.102.153.90:445 | buyviagraoverthecounterusabb.net | Limited Liability Company NTCOM | RU | unknown |
4 | System | 91.102.153.90:139 | buyviagraoverthecounterusabb.net | Limited Liability Company NTCOM | RU | unknown |
3412 | 7zFM.exe | 91.102.153.90:80 | buyviagraoverthecounterusabb.net | Limited Liability Company NTCOM | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
buyviagraoverthecounterusabb.net |
| unknown |
dns.msftncsi.com |
| shared |