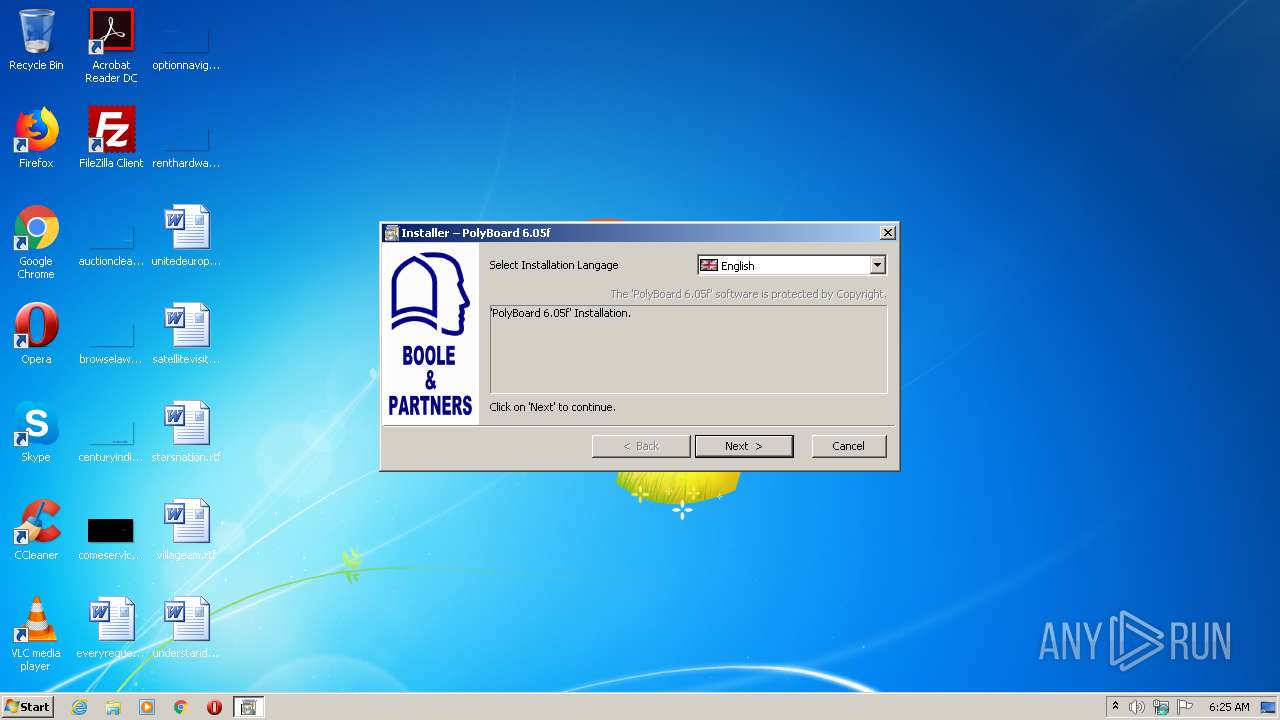
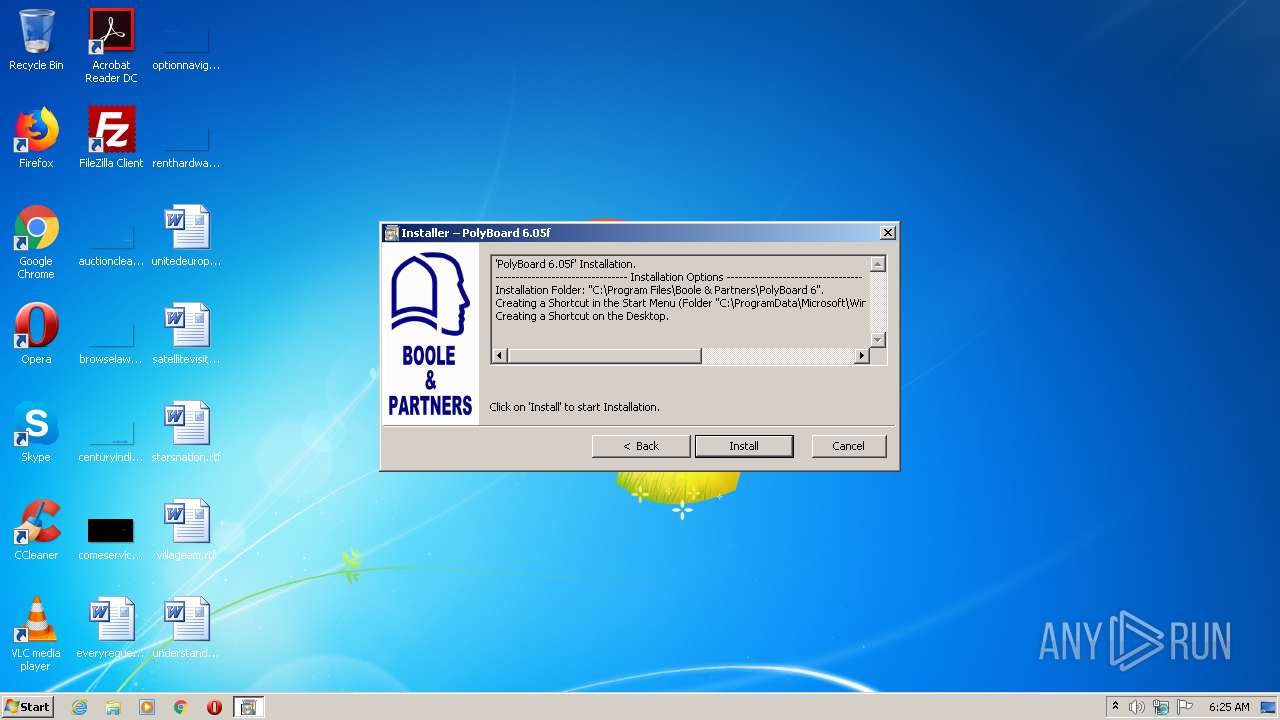
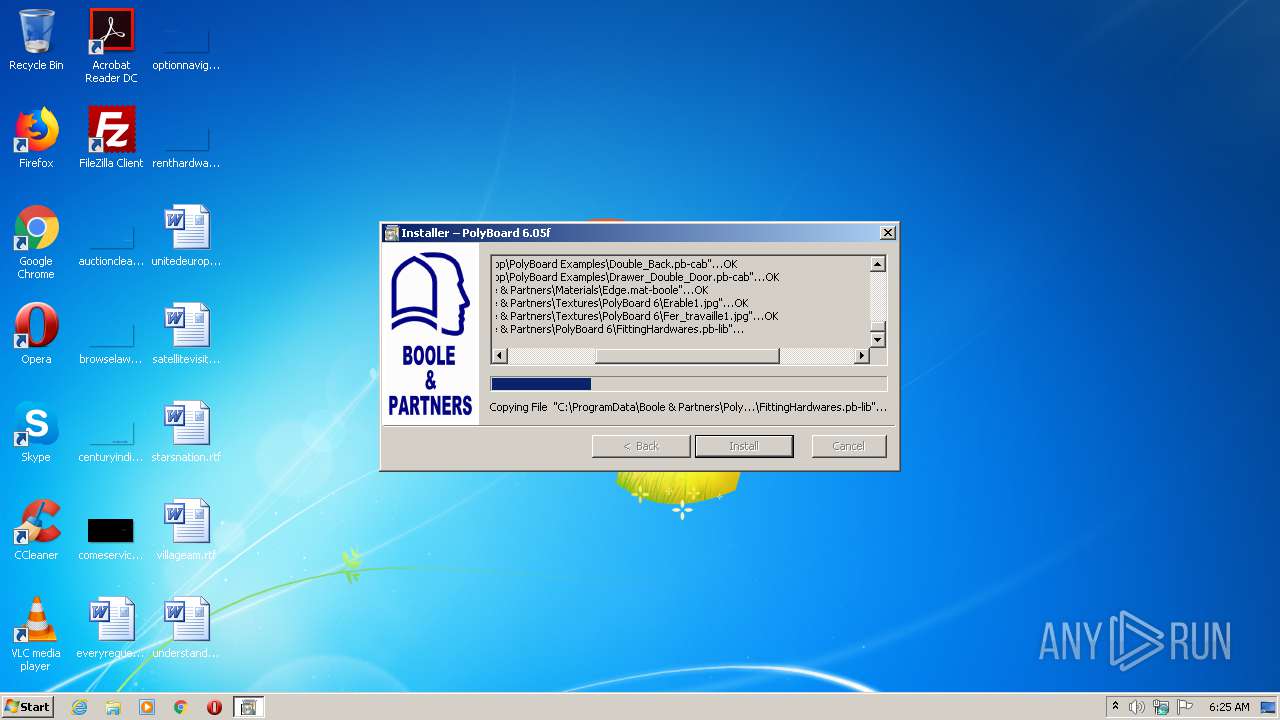
| File name: | installpolyboard.exe |
| Full analysis: | https://app.any.run/tasks/a3959119-1a80-4427-98c0-01fe9352c60d |
| Verdict: | Malicious activity |
| Analysis date: | February 26, 2021, 06:24:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 610A68D796F444219470C2DEE295C327 |
| SHA1: | 318C3634C19CBA3EB3AECC49A144276E02E8A50A |
| SHA256: | EA17BD026EF22D98978F859AB1BB696B2ED4A21A443D020A5722F9243B0798FD |
| SSDEEP: | 196608:yrRGdG2xHgjk3seMk8BlBS+cySha6b5rsOtknCyJCC/yGC9cfjto:yrRWG2tgjpkkTS+gLbJWVp5j |
MALICIOUS
Changes settings of System certificates
- installpolyboard.exe (PID: 1672)
Loads dropped or rewritten executable
- installpolyboard.exe (PID: 1672)
- Polyboard.exe (PID: 3112)
Application was dropped or rewritten from another process
- Polyboard.exe (PID: 3112)
- Polyboard.exe (PID: 1900)
SUSPICIOUS
Creates files in the Windows directory
- installpolyboard.exe (PID: 1672)
Creates files in the user directory
- installpolyboard.exe (PID: 1672)
Creates a directory in Program Files
- installpolyboard.exe (PID: 1672)
Creates files in the program directory
- installpolyboard.exe (PID: 1672)
Executable content was dropped or overwritten
- installpolyboard.exe (PID: 1672)
Executed via COM
- DllHost.exe (PID: 1748)
Drops a file that was compiled in debug mode
- installpolyboard.exe (PID: 1672)
Searches for installed software
- installpolyboard.exe (PID: 1672)
Adds / modifies Windows certificates
- installpolyboard.exe (PID: 1672)
Removes files from Windows directory
- installpolyboard.exe (PID: 1672)
Creates a software uninstall entry
- installpolyboard.exe (PID: 1672)
Changes default file association
- Polyboard.exe (PID: 3112)
INFO
Dropped object may contain Bitcoin addresses
- installpolyboard.exe (PID: 1672)
Reads settings of System Certificates
- installpolyboard.exe (PID: 1672)
Manual execution by user
- Polyboard.exe (PID: 1900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:01:16 12:25:35+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 2005504 |
| InitializedDataSize: | 9426432 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x194680 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.2.0.3 |
| ProductVersionNumber: | 2.2.0.3 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Process default |
| CharacterSet: | Unicode |
| ProductName: | Install |
| ProductVersion: | 2.02 |
| FileVersion: | 2.2.0.3 |
| FileDescription: | Installeur PolyBoard 6.05f |
| CompanyName: | Boole & Partners |
| LegalCopyright: | Copyright © Boole & Partners 2004-2018 |
| InternalName: | Install |
| OriginalFileName: | InstallPolyBoard6.05f.exe |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 16-Jan-2018 11:25:35 |
| Detected languages: |
|
| ProductName: | Install |
| ProductVersion: | 2.02 |
| FileVersion: | 2.2.0.3 |
| FileDescription: | Installeur PolyBoard 6.05f |
| CompanyName: | Boole & Partners |
| LegalCopyright: | Copyright © Boole & Partners 2004-2018 |
| InternalName: | Install |
| OriginalFilename: | InstallPolyBoard6.05f.exe |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000128 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 8 |
| Time date stamp: | 16-Jan-2018 11:25:35 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x001E986F | 0x001E9A00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.57603 |
.rdata | 0x001EB000 | 0x0006B702 | 0x0006B800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.06782 |
.data | 0x00257000 | 0x0001359C | 0x00009A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.07069 |
.gfids | 0x0026B000 | 0x00016EC4 | 0x00017000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.2152 |
.giats | 0x00282000 | 0x00000010 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0.155178 |
.tls | 0x00283000 | 0x00000009 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.0203931 |
.rsrc | 0x00284000 | 0x00841590 | 0x00841600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.99565 |
.reloc | 0x00AC6000 | 0x00025C5C | 0x00025E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.50179 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.16876 | 1985 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 3.15864 | 744 | UNKNOWN | Process Default Language | RT_ICON |
3 | 3.50949 | 296 | UNKNOWN | Process Default Language | RT_ICON |
4 | 5.56662 | 3752 | UNKNOWN | Process Default Language | RT_ICON |
5 | 5.94251 | 2216 | UNKNOWN | Process Default Language | RT_ICON |
6 | 3.37828 | 1384 | UNKNOWN | Process Default Language | RT_ICON |
7 | 7.98515 | 55762 | UNKNOWN | Process Default Language | RT_ICON |
8 | 5.33023 | 9640 | UNKNOWN | Process Default Language | RT_ICON |
9 | 5.61313 | 4264 | UNKNOWN | Process Default Language | RT_ICON |
10 | 4.85349 | 1128 | UNKNOWN | Process Default Language | RT_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
IMM32.dll |
KERNEL32.dll |
MSIMG32.dll |
OLEACC.dll |
OLEAUT32.dll |
SHELL32.dll |
SHLWAPI.dll |
Total processes
47
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1672 | "C:\Users\admin\AppData\Local\Temp\installpolyboard.exe" | C:\Users\admin\AppData\Local\Temp\installpolyboard.exe | explorer.exe | ||||||||||||
User: admin Company: Boole & Partners Integrity Level: HIGH Description: Installeur PolyBoard 6.05f Exit code: 0 Version: 2.2.0.3 Modules
| |||||||||||||||
| 1748 | C:\Windows\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1900 | "C:\Program Files\Boole & Partners\PolyBoard 6\Polyboard.exe" | C:\Program Files\Boole & Partners\PolyBoard 6\Polyboard.exe | — | explorer.exe | |||||||||||
User: admin Company: Boole & Partners Integrity Level: MEDIUM Description: PolyBoard Exit code: 0 Version: 6.5.6.3 Modules
| |||||||||||||||
| 2768 | "C:\Users\admin\AppData\Local\Temp\installpolyboard.exe" | C:\Users\admin\AppData\Local\Temp\installpolyboard.exe | — | explorer.exe | |||||||||||
User: admin Company: Boole & Partners Integrity Level: MEDIUM Description: Installeur PolyBoard 6.05f Exit code: 3221226540 Version: 2.2.0.3 Modules
| |||||||||||||||
| 3112 | "C:\Program Files\Boole & Partners\PolyBoard 6\Polyboard.exe" /Register /Background | C:\Program Files\Boole & Partners\PolyBoard 6\Polyboard.exe | — | installpolyboard.exe | |||||||||||
User: admin Company: Boole & Partners Integrity Level: HIGH Description: PolyBoard Exit code: 4294967286 Version: 6.5.6.3 Modules
| |||||||||||||||
Total events
395
Read events
297
Write events
98
Delete events
0
Modification events
| (PID) Process: | (1672) installpolyboard.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 400000000000000008AF7C2A080CD701880600003C050000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1672) installpolyboard.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 400000000000000008AF7C2A080CD701880600003C050000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1748) DllHost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 400000000000000078E7B52A080CD701D406000034080000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1748) DllHost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 45 | |||
| (PID) Process: | (1748) DllHost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4000000000000000860EBD2A080CD701D406000034080000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1748) DllHost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000E070BF2A080CD701D40600008C090000E8030000010000000000000000000000F7741AB3B223834C8471F63DA83C2B2E0000000000000000 | |||
| (PID) Process: | (1672) installpolyboard.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 44 | |||
| (PID) Process: | (1672) installpolyboard.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 400000000000000016D6832A080CD701880600003C050000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1672) installpolyboard.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000007038862A080CD7018806000020060000E8030000010000000000000000000000BA48606BD6ED934E954F38752D738CB30000000000000000 | |||
| (PID) Process: | (1672) installpolyboard.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 40000000000000004E72A02A080CD7018806000020060000E8030000000000000000000000000000BA48606BD6ED934E954F38752D738CB30000000000000000 | |||
Executable files
18
Suspicious files
39
Text files
306
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1672 | installpolyboard.exe | C:\Windows\inf\sdatabl.sav.bin | binary | |
MD5:— | SHA256:— | |||
| 1672 | installpolyboard.exe | C:\Users\admin\AppData\Local\Temp\boole_{e2a60823-78bf-457f-8e88-b8c405478a78}\dxdllreg_x86.cab | compressed | |
MD5:A025C67403DC2C2BCD709AA9435FAEB1 | SHA256:8AD77A4D9C76F65CD62337588F847CC1E0CA6CA9735937F3A781F7395E9566A1 | |||
| 1672 | installpolyboard.exe | C:\Users\admin\AppData\Local\Temp\boole_{e2a60823-78bf-457f-8e88-b8c405478a78}\Jun2010_D3DCompiler_43_x86.cab | compressed | |
MD5:F7F554AA613ECCF065575B8C69717EF7 | SHA256:417EEBD5B19F45C67C94C2D2BA8B774C0FC6D958B896D7B1AC12CF5A0EA06E0E | |||
| 1672 | installpolyboard.exe | C:\Users\admin\AppData\Local\Temp\boole_{e2a60823-78bf-457f-8e88-b8c405478a78}\dxupdate.cab | compressed | |
MD5:8ADF5A3C4BD187052BFA92B34220F4E7 | SHA256:13393A91201E69E70A9F68D21428453FFF3951535DEC88F879270269CFE54D6F | |||
| 1672 | installpolyboard.exe | C:\Users\admin\AppData\Local\Temp\boole_{e2a60823-78bf-457f-8e88-b8c405478a78}\Jun2010_d3dx9_43_x86.cab | compressed | |
MD5:7749862C307E527366B6868326DB8198 | SHA256:FCC6CF0966B4853D6FA3D32AB299CDE5A9824FEAECB0D4F34EA452FB9FD1C867 | |||
| 1672 | installpolyboard.exe | C:\ProgramData\Boole & Partners\Textures\PolyBoard 6\Birch.jpg | image | |
MD5:D7C65D3FAD68A279AFE66B395FFB0BF4 | SHA256:893248AFED8CC6D5573E5E8CD7CCE01A28B40E595F8AD2B5EE0FCCAD15FDE388 | |||
| 1672 | installpolyboard.exe | C:\ProgramData\Boole & Partners\Textures\PolyBoard 6\Chene4.jpg | image | |
MD5:0EC1F708089EF8DE1FDF7D52E068499D | SHA256:4916640E908F9F6DC6011FEE5B66DC9A06B2400D5AE2980DAEDC9E41E6A17FD7 | |||
| 1672 | installpolyboard.exe | C:\ProgramData\Boole & Partners\Textures\PolyBoard 6\Beech.jpg | image | |
MD5:B218CAE9E84AE0CFAE75D3BA8ACDE091 | SHA256:ED7AABABC9308000802EDF3FE3B6562A1333AFCB97932769F2A6588B6E969274 | |||
| 1672 | installpolyboard.exe | C:\ProgramData\Boole & Partners\Textures\PolyBoard 6\Chataignier.jpg | image | |
MD5:13681D01B50F1B73E0CB5B9327E8E72B | SHA256:E687C202687C845A2D941A9FBCDA4CD8BFCB6090AC8372D665E61BB79C55FF49 | |||
| 1672 | installpolyboard.exe | C:\ProgramData\Boole & Partners\Textures\PolyBoard 6\Bois1.jpg | image | |
MD5:AF1AF8747900F207E21C6BF45FBA73B7 | SHA256:389803BF6EFE61CC19D09E9A7E568226BC8AFA24EC2DC869B840A715140895C9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
installpolyboard.exe | DLL_PROCESS_ATTACH |
installpolyboard.exe | DLL_PROCESS_ATTACH |
installpolyboard.exe | DLL_PROCESS_DETACH |
installpolyboard.exe | DLL_PROCESS_DETACH |