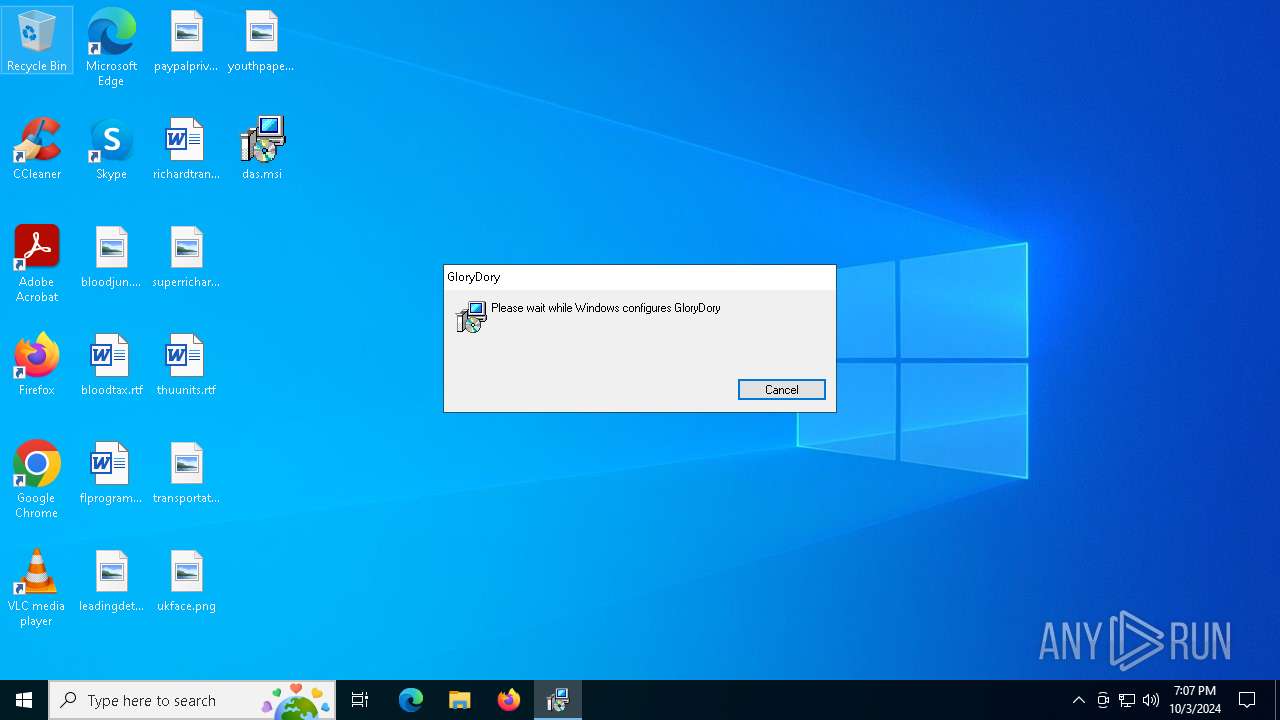
| download: | /das.msi |
| Full analysis: | https://app.any.run/tasks/83b449af-f71c-41b9-bef6-59a3520eab19 |
| Verdict: | Malicious activity |
| Analysis date: | October 03, 2024, 19:07:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Last Printed: Fri Dec 11 11:47:44 2009, Create Time/Date: Fri Dec 11 11:47:44 2009, Last Saved Time/Date: Fri Sep 18 14:06:51 2020, Security: 0, Code page: 1252, Revision Number: {26C6701E-5BA5-48FD-87C5-16BC3575B429}, Number of Words: 10, Subject: GloryDory, Author: OrbitalMast LLC, Name of Creating Application: GloryDory, Template: ;1033, Comments: This installer database contains the logic and data required to install GloryDory., Title: Installation Database, Keywords: Installer, MSI, Database, Number of Pages: 200 |
| MD5: | 3CB6B99B20930AC0DBADC10899DC511E |
| SHA1: | 570C4AB78CF4BB22B78AAC215A4A79189D4FA9ED |
| SHA256: | EA1792F689BFE5AD3597C7F877B66F9FCF80D732E5233293D52D374D50CAB991 |
| SSDEEP: | 49152:5Pz9IfHgoPxmbqD+/GKIikt698ta5Q1aTeor8trZeOq6VaRHwHpRh3P2jr8oOFBx:59IIoPWkt698tYTeoroq6oQHpr3O8oOz |
MALICIOUS
Runs injected code in another process
- rundll32.exe (PID: 512)
Application was injected by another process
- explorer.exe (PID: 4552)
SUSPICIOUS
Uses RUNDLL32.EXE to load library
- rundll32.exe (PID: 6208)
Executes as Windows Service
- VSSVC.exe (PID: 4120)
Connects to unusual port
- rundll32.exe (PID: 512)
INFO
Reads security settings of Internet Explorer
- explorer.exe (PID: 4552)
The process uses the downloaded file
- explorer.exe (PID: 4552)
Checks supported languages
- msiexec.exe (PID: 2956)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2956)
Reads the computer name
- msiexec.exe (PID: 2956)
Starts application with an unusual extension
- msiexec.exe (PID: 2956)
Manages system restore points
- SrTasks.exe (PID: 3728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (81.9) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.2) |
| .msp | | | Windows Installer Patch (7.6) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| LastPrinted: | 2009:12:11 11:47:44 |
|---|---|
| CreateDate: | 2009:12:11 11:47:44 |
| ModifyDate: | 2020:09:18 14:06:51 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {26C6701E-5BA5-48FD-87C5-16BC3575B429} |
| Words: | 10 |
| Subject: | GloryDory |
| Author: | OrbitalMast LLC |
| LastModifiedBy: | - |
| Software: | GloryDory |
| Template: | ;1033 |
| Comments: | This installer database contains the logic and data required to install GloryDory. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| Pages: | 200 |
Total processes
138
Monitored processes
10
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 512 | "C:\Windows\SysWOW64\rundll32.exe" C:\Users\admin\AppData\Roaming\vierm_soft_x64.dll, GetDeepDVCState | C:\Windows\System32\rundll32.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1940 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\Desktop\das.msi | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2480 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2776 | C:\Windows\syswow64\MsiExec.exe -Embedding 3A91BFAE1E5A7FF448FCD9DE720CF570 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2956 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3728 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4120 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4552 | C:\WINDOWS\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5328 | "C:\WINDOWS\Installer\MSIA9FE.tmp" /DontWait C:/Windows/SysWOW64/rundll32.exe C:\Users\admin\AppData\Roaming\vierm_soft_x64.dll, GetDeepDVCState | C:\Windows\Installer\MSIA9FE.tmp | — | msiexec.exe | |||||||||||
User: admin Company: Caphyon LTD Integrity Level: MEDIUM Description: File that launches another file Exit code: 0 Version: 19.1.0.0 Modules
| |||||||||||||||
| 6208 | "C:\Windows\SysWOW64\rundll32.exe" C:\Users\admin\AppData\Roaming\vierm_soft_x64.dll, GetDeepDVCState | C:\Windows\SysWOW64\rundll32.exe | — | MSIA9FE.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 443
Read events
4 233
Write events
191
Delete events
19
Modification events
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010014000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C000000100000000000000062006C006F006F0064006A0075006E002E0070006E0067003E00200020000000100000000000000062006C006F006F0064007400610078002E007200740066003E00200020000000150000000000000066006C00700072006F006700720061006D006D0069006E0067002E007200740066003E0020002000000018000000000000006C0065006100640069006E006700640065007400650072006D0069006E0065002E0070006E0067003E002000200000001500000000000000700061007900700061006C0070007200690076006100630079002E0070006E0067003E00200020000000170000000000000072006900630068006100720064007400720061006E0073006600650072002E007200740066003E0020002000000014000000000000007300750070006500720072006900630068006100720064002E0070006E0067003E00200020000000100000000000000074006800750075006E006900740073002E007200740066003E002000200000001D000000000000007400720061006E00730070006F00720074006100740069006F006E006F0076006500720061006C006C002E0070006E0067003E002000200000000E0000000000000075006B0066006100630065002E0070006E0067003E00200020000000130000000000000079006F007500740068007000610070006500720073002E0070006E0067003E002000200000000B000000000000006400610073002E006D00730069003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001400000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E0000000040000040400F0000000040000080401000000000400000A040110000004040000000001200000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F0700000040400000803F1300 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconNameVersion |
Value: 1 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 78EBFE6600000000 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Security and Maintenance\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 23004100430042006C006F00620000000000000000000000010000000000000000000000 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:000000000013024A |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456033BCEE44DE41B4E8AEC331E84F566D2 | |||
| (PID) Process: | (2956) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 48000000000000005DB6CE83C715DB018C0B000018160000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2956) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000005DB6CE83C715DB018C0B000018160000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2956) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000005D5C2984C715DB018C0B000018160000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2956) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000005D5C2984C715DB018C0B000018160000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2956) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000FCAB2B84C715DB018C0B000018160000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
7
Suspicious files
19
Text files
0
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2956 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2956 | msiexec.exe | C:\Windows\Installer\MSIA67E.tmp | executable | |
MD5:475D20C0EA477A35660E3F67ECF0A1DF | SHA256:426E6CF199A8268E8A7763EC3A4DD7ADD982B28C51D89EBEA90CA792CBAE14DD | |||
| 2956 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{d2c22647-bbdc-4609-ba82-7ab985f28b1d}_OnDiskSnapshotProp | binary | |
MD5:ED79D932903F2B51CDD1D492A289C08C | SHA256:A8F756ABD663957F4FD7914F7660CEA8C64C2DF6EF52A0B29F33D42D8E323E5A | |||
| 2956 | msiexec.exe | C:\Windows\Installer\MSIA9FE.tmp | executable | |
MD5:B9545ED17695A32FACE8C3408A6A3553 | SHA256:1E0E63B446EECF6C9781C7D1CAE1F46A3BB31654A70612F71F31538FB4F4729A | |||
| 2956 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:1A073CE68F62A880CF46BAA9CCEF326E | SHA256:079548E7978D80BB6E7B85CA23D41846022499215DA8675FE9B45F8236578A99 | |||
| 2956 | msiexec.exe | C:\Windows\Installer\MSIA98F.tmp | binary | |
MD5:CBF11F7DC03C843C24AC7840658ABD0B | SHA256:08950EFEE7D64CA3F6C17DF13A1F08EFF83355FA8322494BF187801E10AF5B4A | |||
| 2956 | msiexec.exe | C:\Windows\Temp\~DF391D8B2E947857FD.TMP | gmc | |
MD5:DFC9B5741A0924E1DD12D9A16FBEE03B | SHA256:3F48AD558A640289F2C5C6E354FDC536C9720A93CBAC3FA9AA96C982D3012D9A | |||
| 2956 | msiexec.exe | C:\Windows\Temp\~DFEABBF1E7315A1B6D.TMP | binary | |
MD5:1A073CE68F62A880CF46BAA9CCEF326E | SHA256:079548E7978D80BB6E7B85CA23D41846022499215DA8675FE9B45F8236578A99 | |||
| 2956 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:ED79D932903F2B51CDD1D492A289C08C | SHA256:A8F756ABD663957F4FD7914F7660CEA8C64C2DF6EF52A0B29F33D42D8E323E5A | |||
| 2956 | msiexec.exe | C:\Config.Msi\3fa5d4.rbs | binary | |
MD5:40EADD8A5F1777C32C0CD4EF3E0B57FA | SHA256:93F0085167FEB86337B59C5506ECE9EBCB5453D1A91F6EC255C21E10DFED9FD7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
103
DNS requests
21
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6168 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3212 | SIHClient.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
512 | rundll32.exe | GET | 200 | 23.32.238.82:80 | http://r10.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRpD%2BQVZ%2B1vf7U0RGQGBm8JZwdxcgQUdKR2KRcYVIUxN75n5gZYwLzFBXICEgPwXByFcml3jW44ijNKERozTw%3D%3D | unknown | — | — | whitelisted |
2968 | svchost.exe | GET | 304 | 23.192.153.142:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
3212 | SIHClient.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5996 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 23.218.209.163:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.218.209.163:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5152 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4324 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5152 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6168 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
greshunka.com |
| malicious |
r10.o.lencr.org |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
512 | rundll32.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 8 |