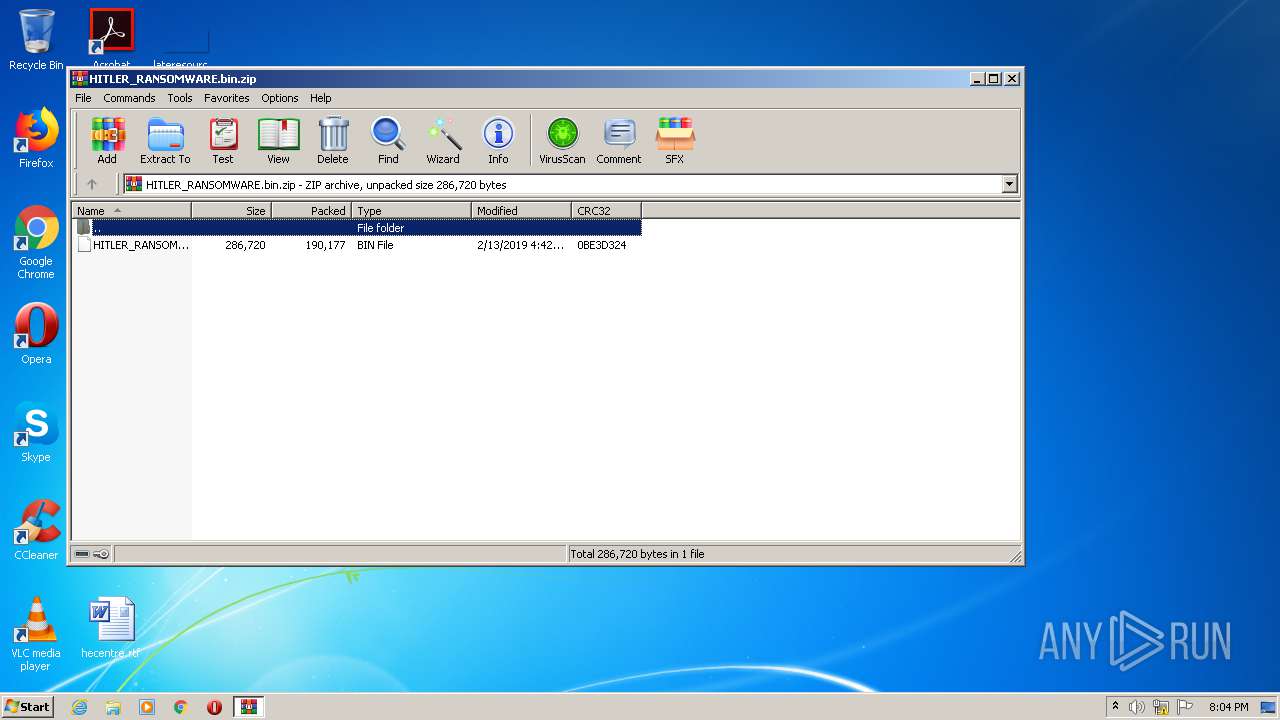
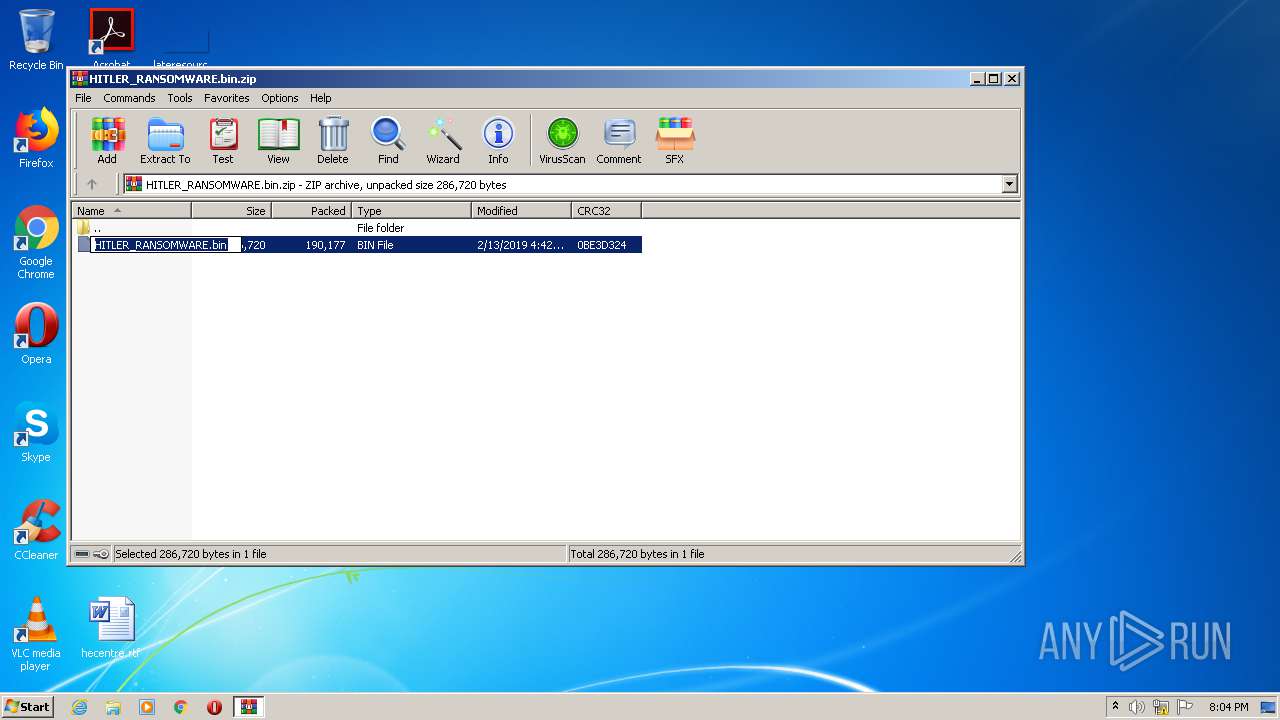
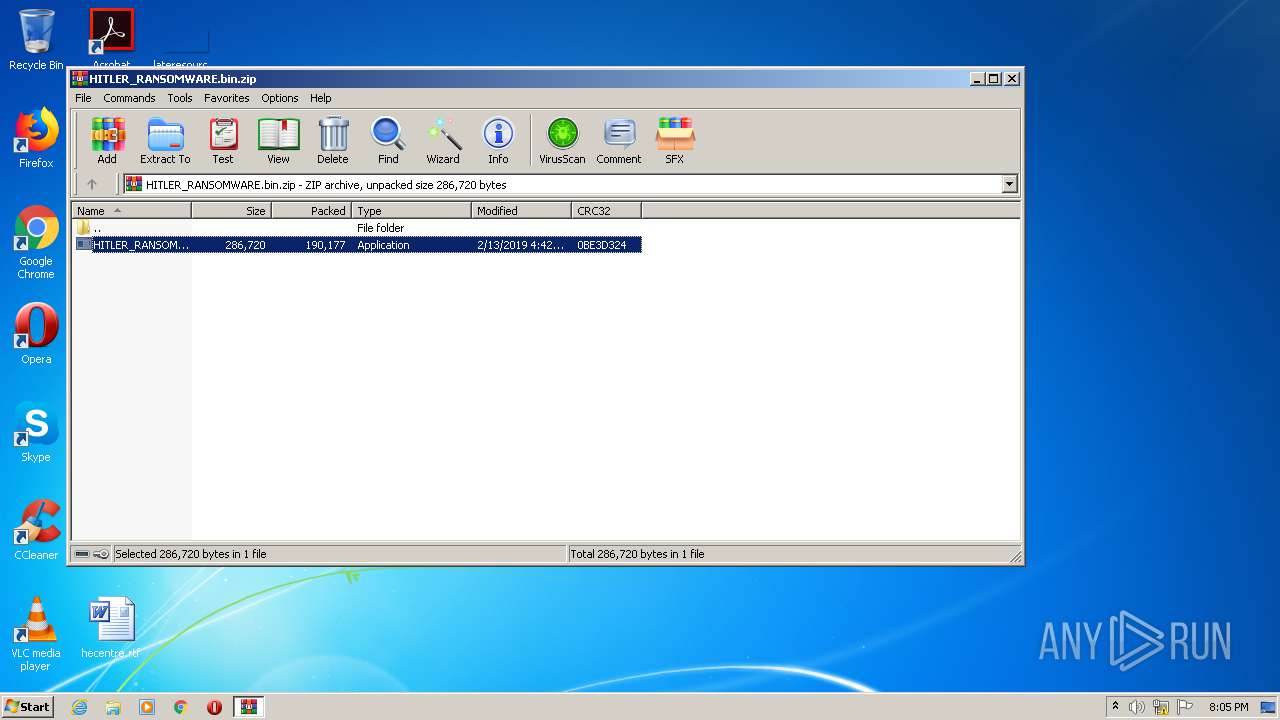
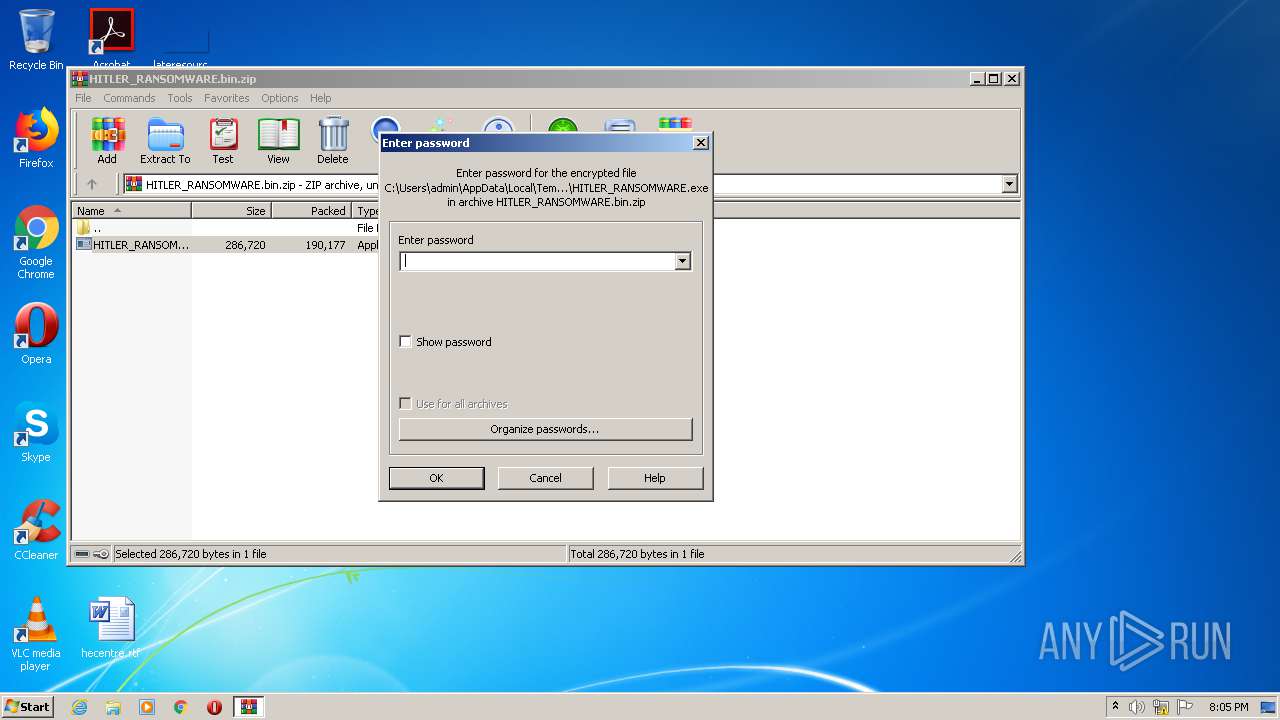
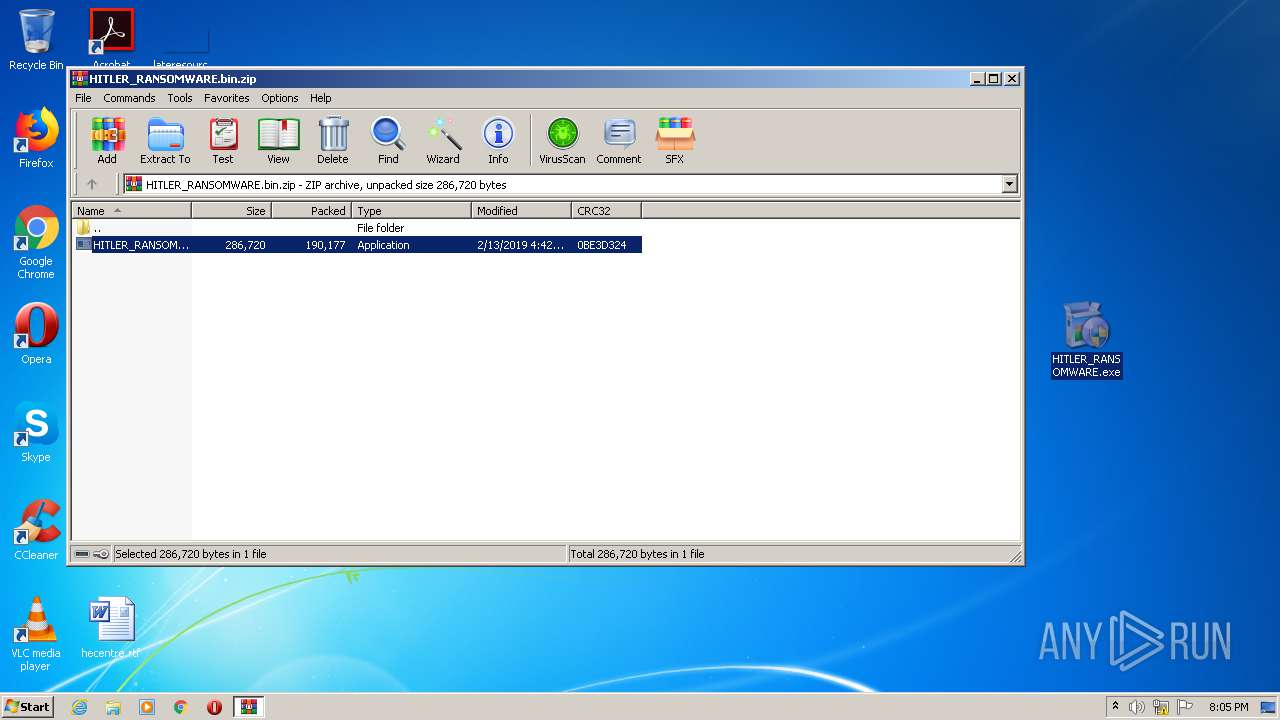
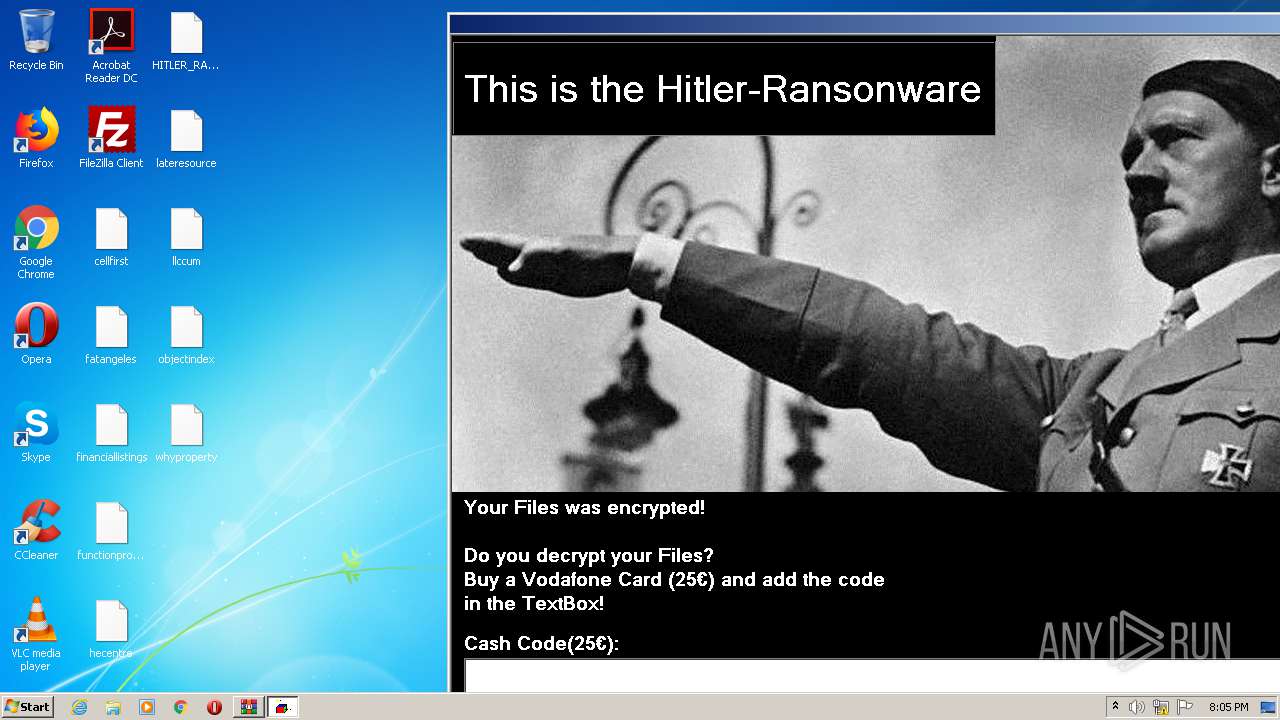
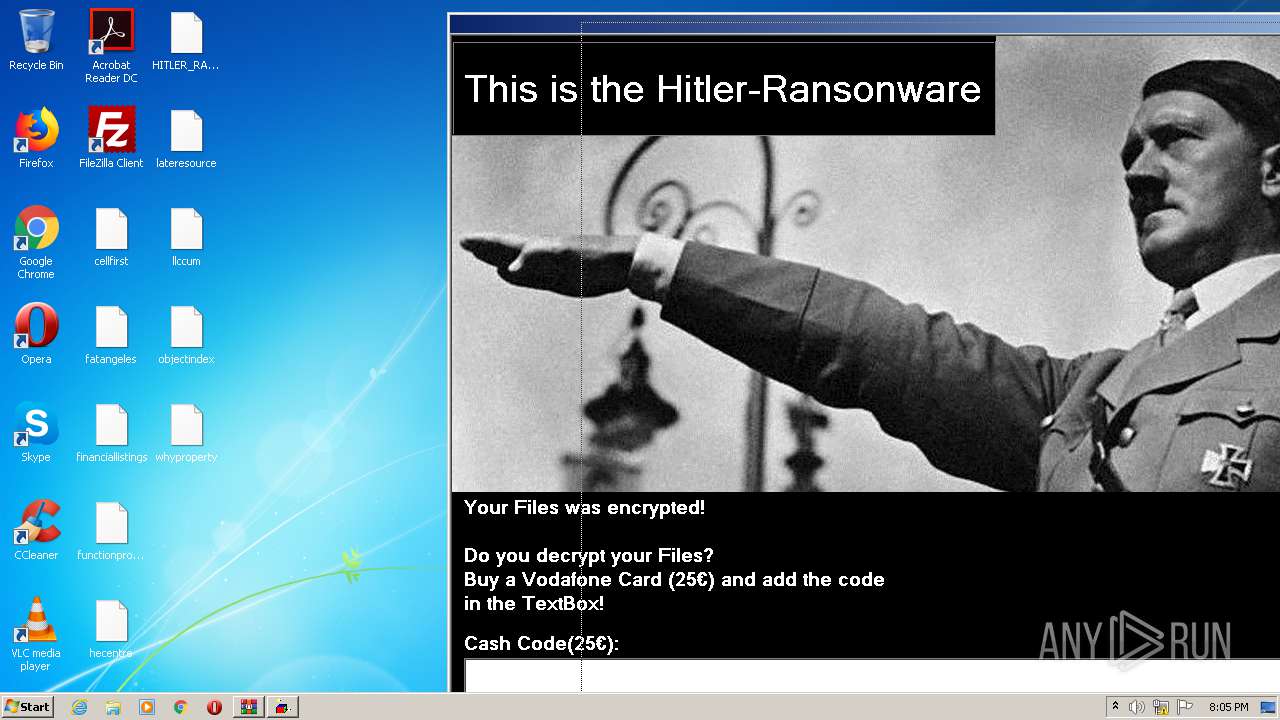
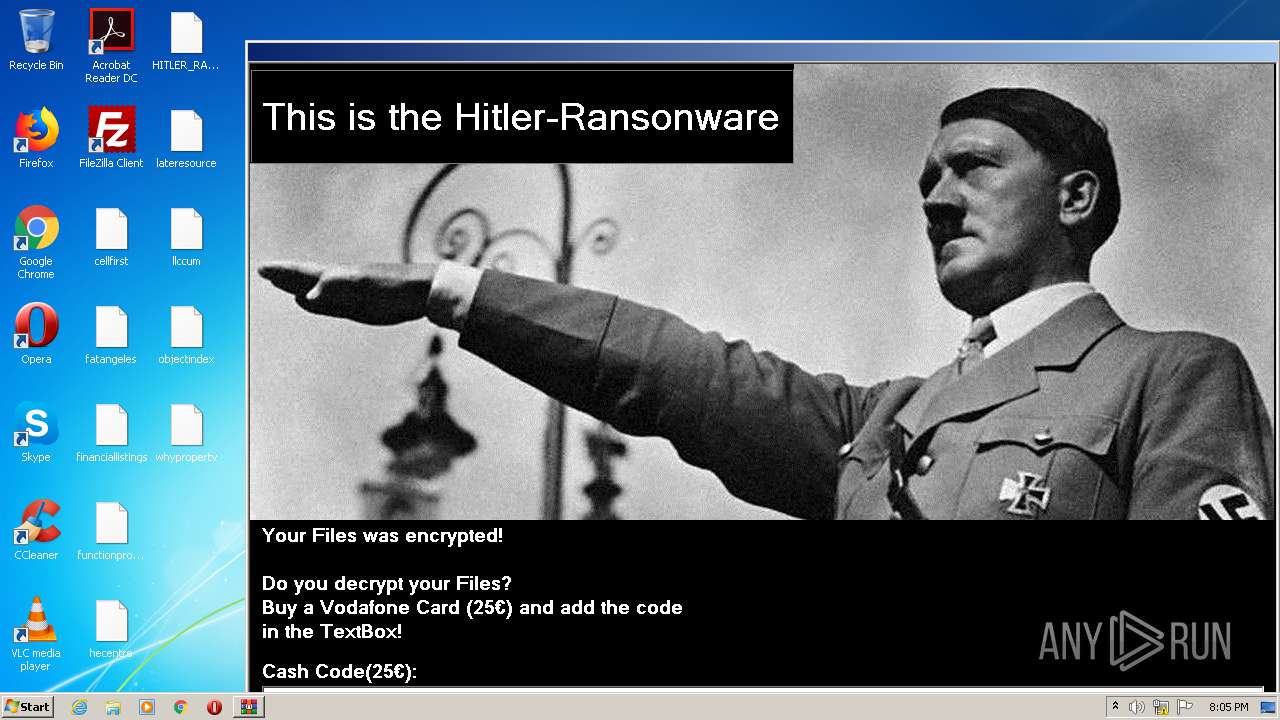
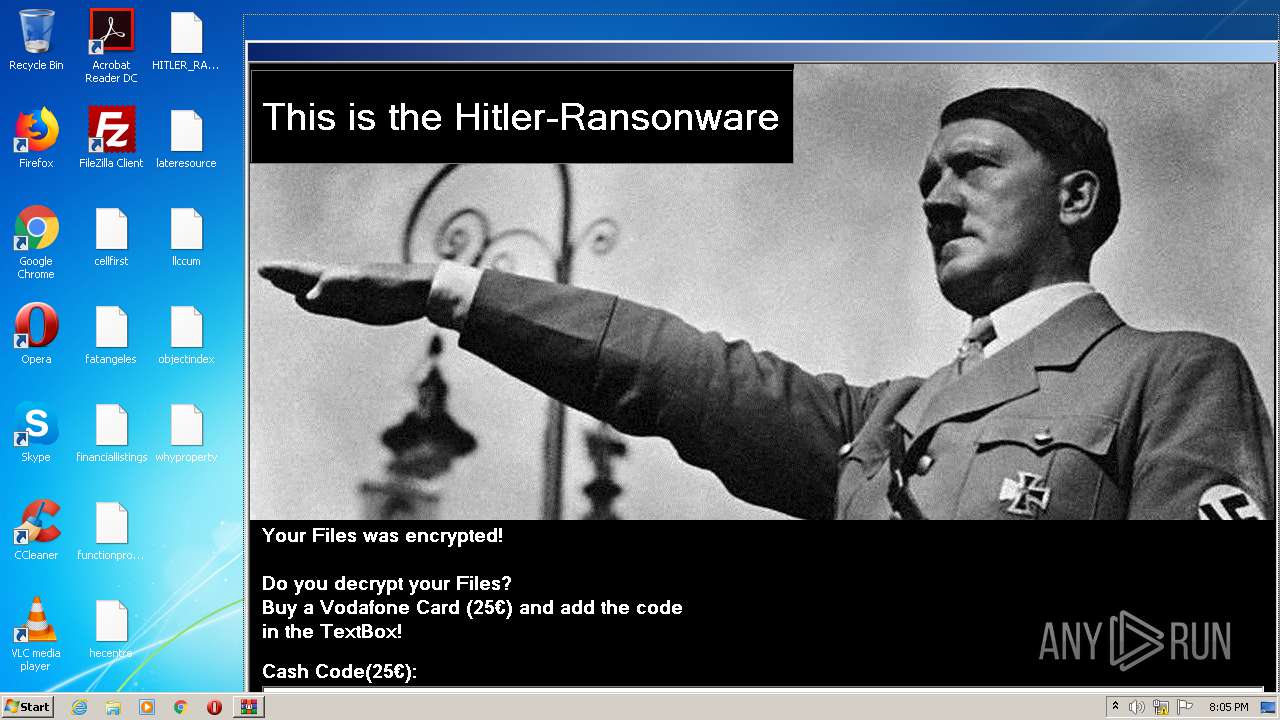
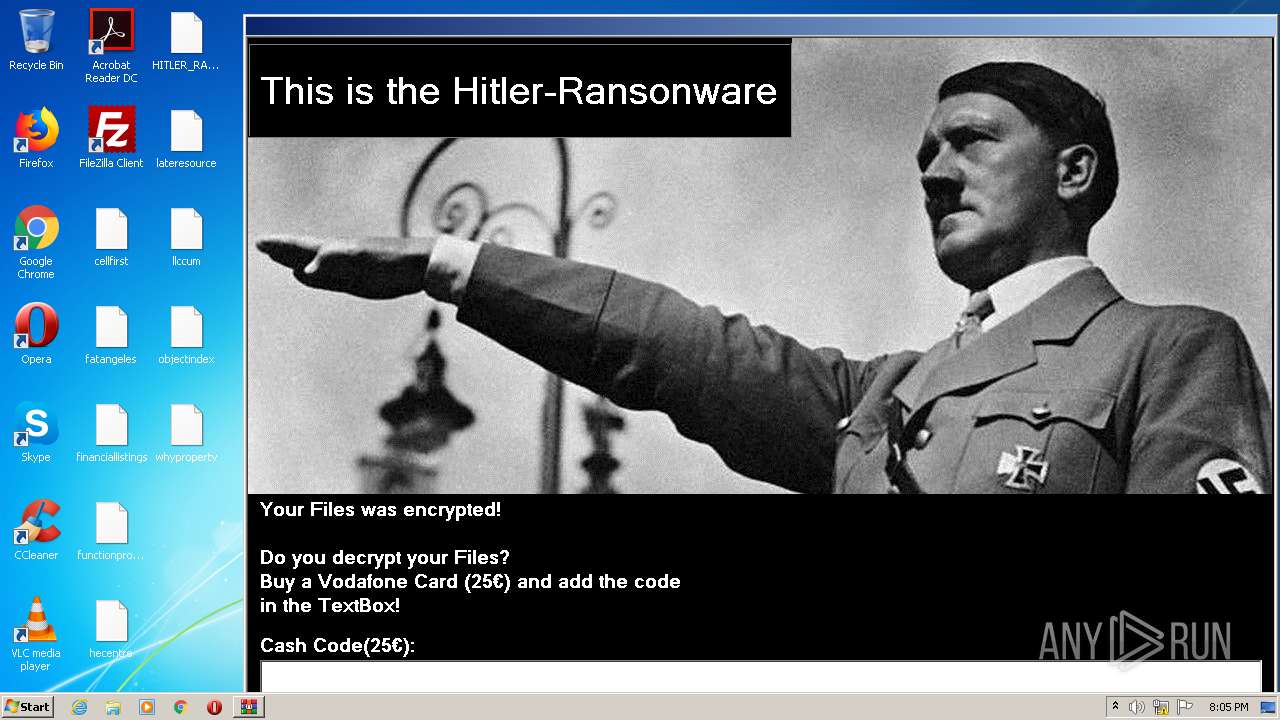
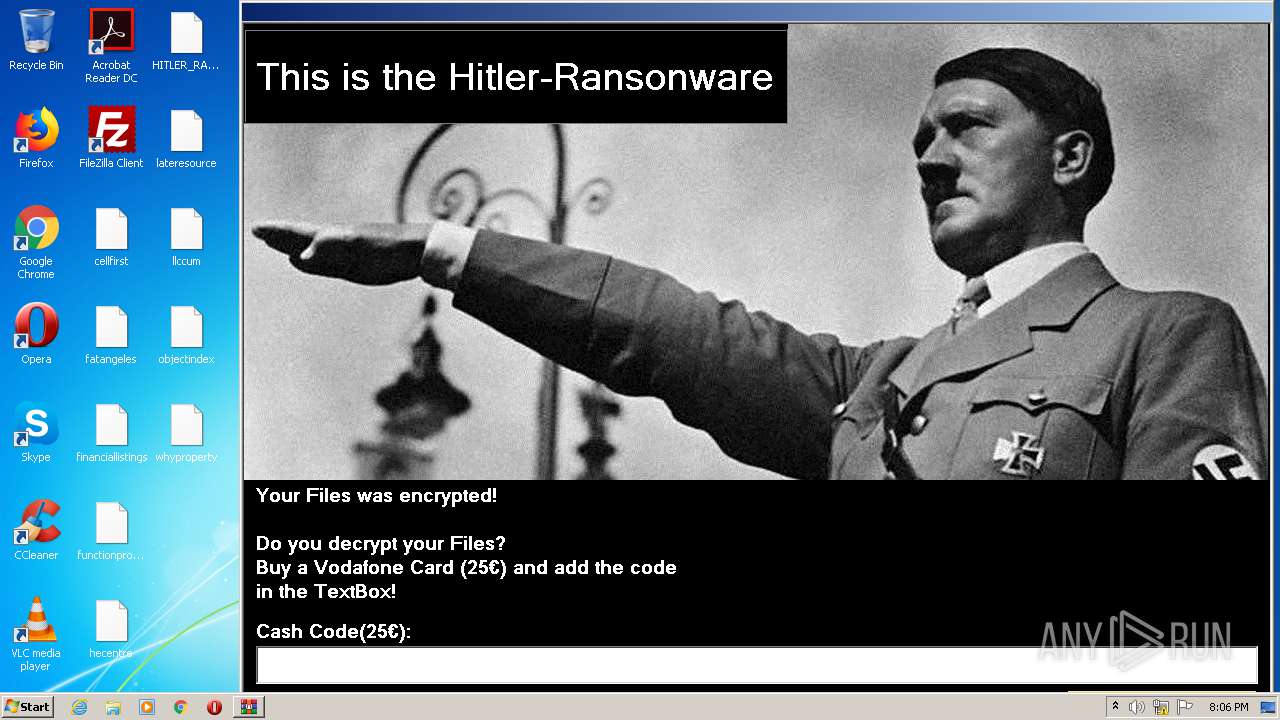
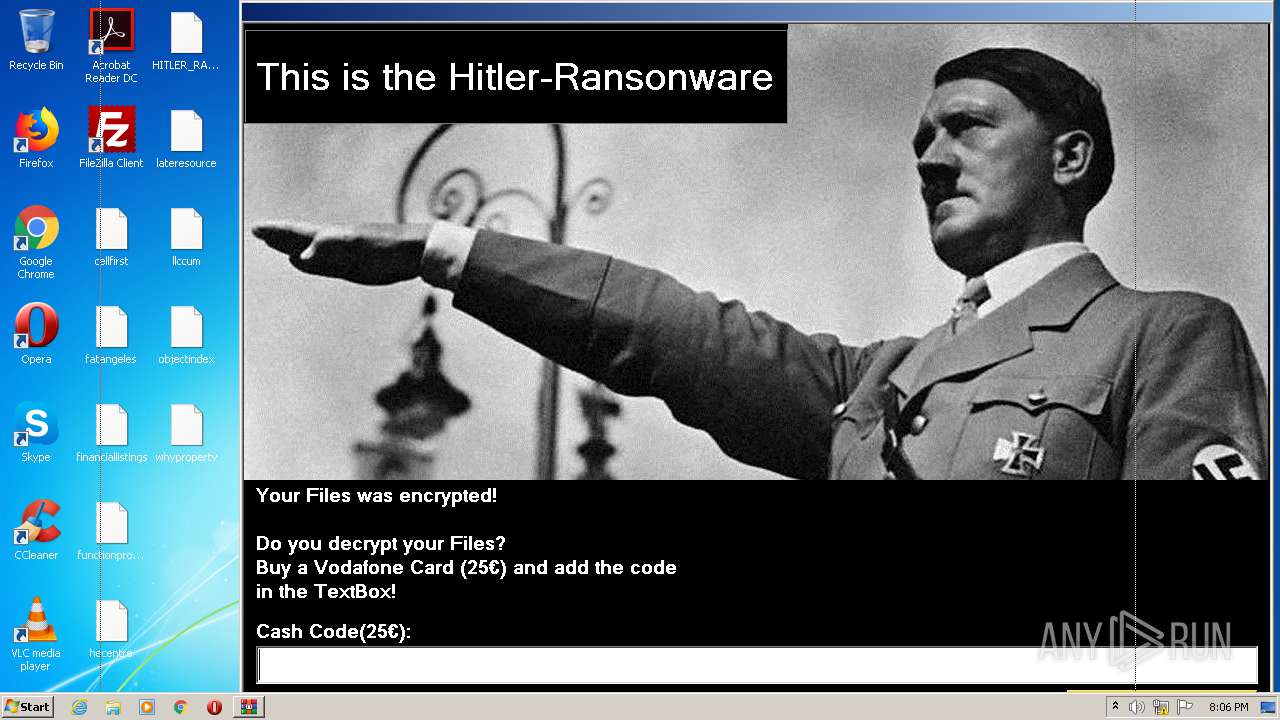
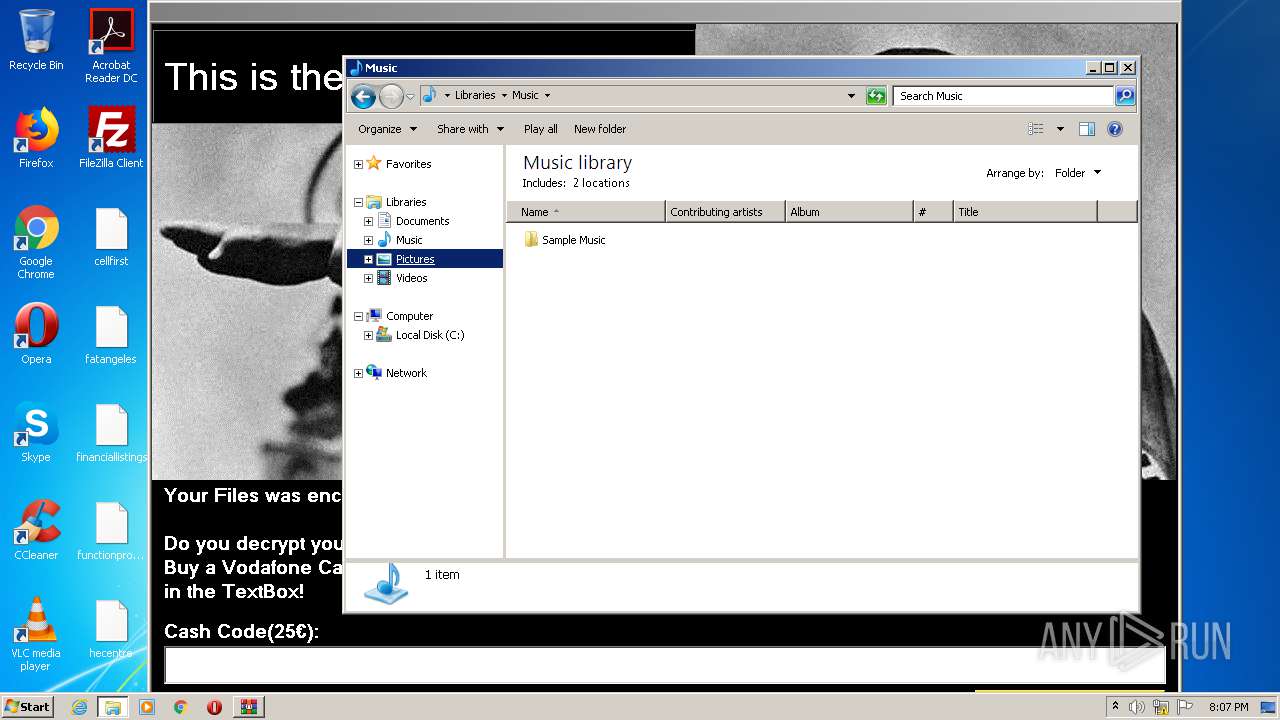
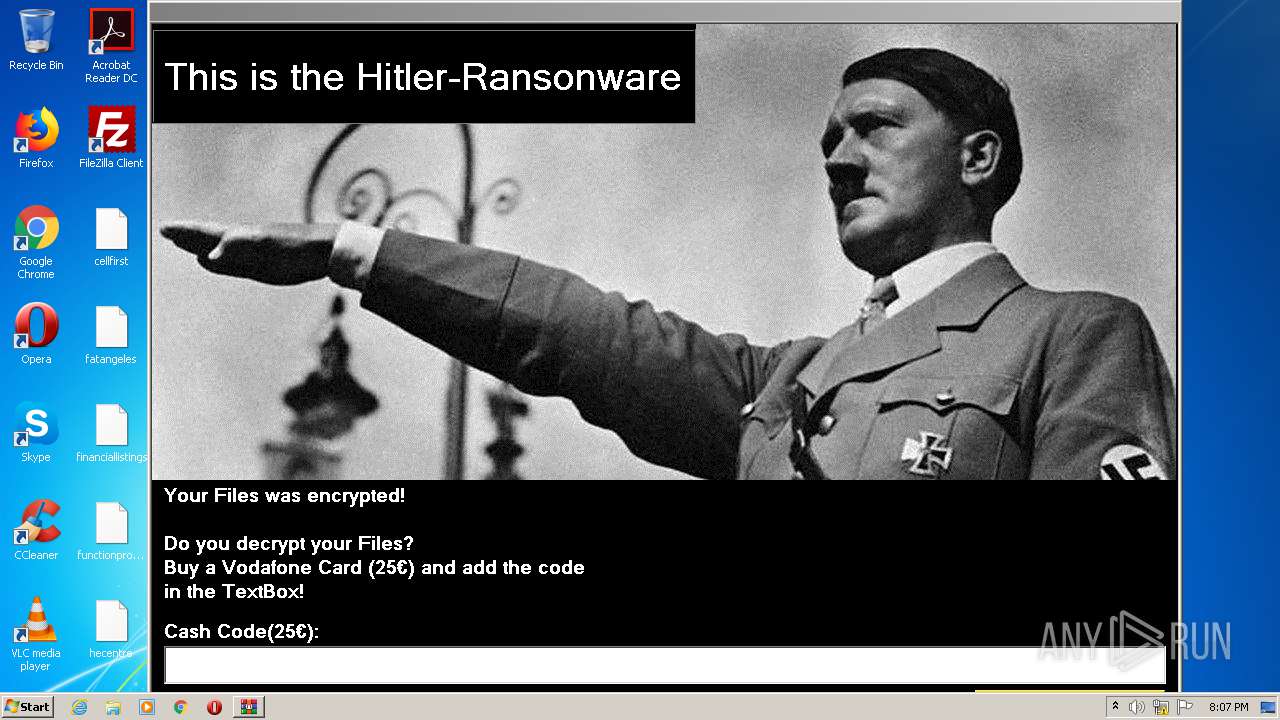
| File name: | HITLER_RANSOMWARE.bin.zip |
| Full analysis: | https://app.any.run/tasks/89efe362-a297-4797-a350-820a8a8c6c33 |
| Verdict: | Malicious activity |
| Analysis date: | February 20, 2021, 20:04:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 0A0C2DBC58C6F973ABDFC9B33AA2752B |
| SHA1: | A210804D64BC5D8685F822871B1F295A8F4A1C56 |
| SHA256: | EA0F481AC317D20954FA66DE7AEB1B05DAB4AB76A7871D76F168096F2D9369BF |
| SSDEEP: | 3072:k5prT8UlK8LMpAkAoE8kuTAV6O137SpaD5nzKSyMiH/dPoWbO1exu:k5VQU5MKk5Cu0V34paDfyM4/dQWqc4 |
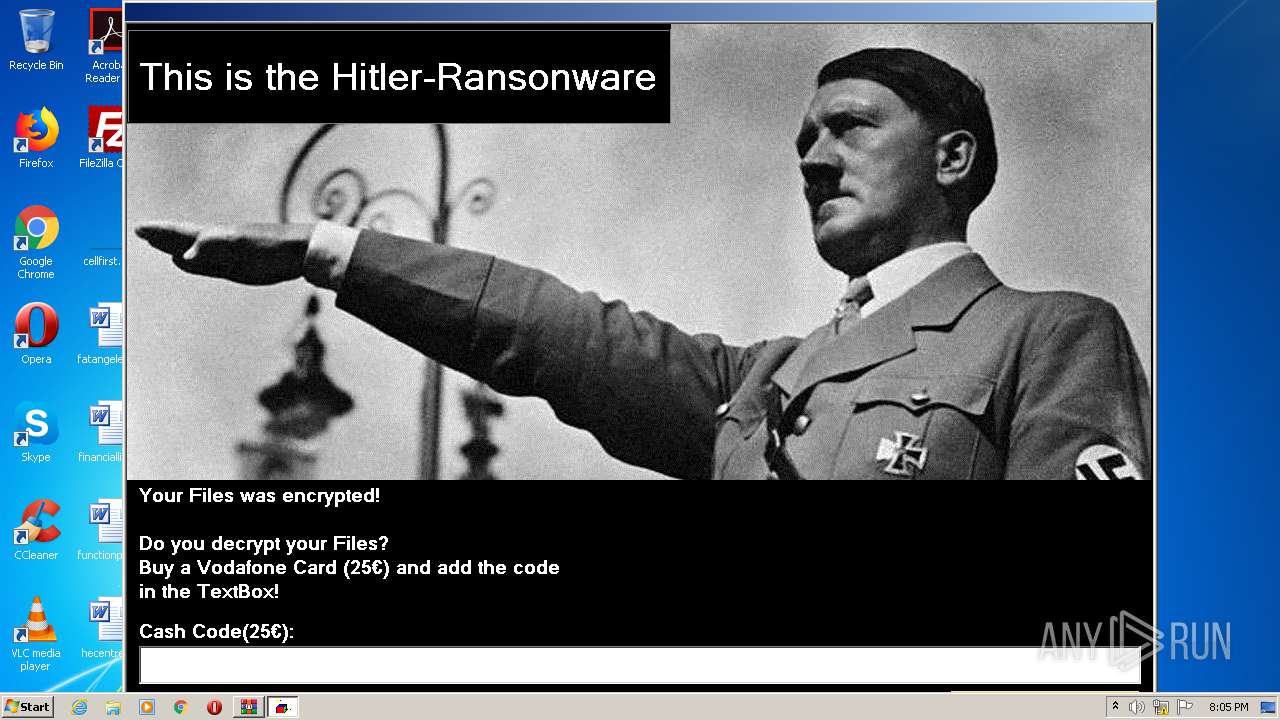
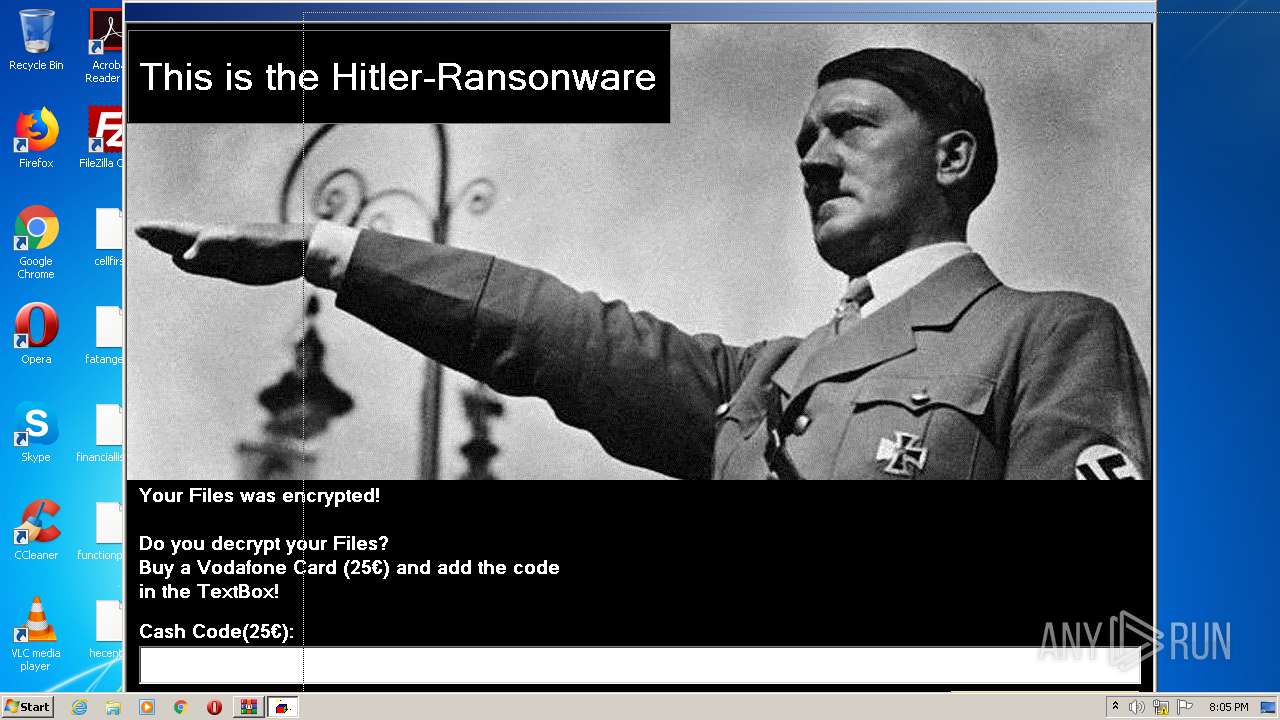
MALICIOUS
Application was dropped or rewritten from another process
- HITLER_RANSOMWARE.exe (PID: 3976)
- HITLER_RANSOMWARE.exe (PID: 1236)
- chrst.exe (PID: 3152)
Drops executable file immediately after starts
- HITLER_RANSOMWARE.exe (PID: 1236)
Writes to a start menu file
- cmd.exe (PID: 3324)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2964)
- HITLER_RANSOMWARE.exe (PID: 1236)
- cmd.exe (PID: 3324)
Starts CMD.EXE for commands execution
- HITLER_RANSOMWARE.exe (PID: 1236)
Drops a file that was compiled in debug mode
- HITLER_RANSOMWARE.exe (PID: 1236)
Executes scripts
- cmd.exe (PID: 3324)
Creates files in the program directory
- cmd.exe (PID: 3324)
INFO
Manual execution by user
- HITLER_RANSOMWARE.exe (PID: 3976)
- HITLER_RANSOMWARE.exe (PID: 1236)
- explorer.exe (PID: 2544)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:02:13 17:42:05 |
| ZipCRC: | 0x0be3d324 |
| ZipCompressedSize: | 190177 |
| ZipUncompressedSize: | 286720 |
| ZipFileName: | HITLER_RANSOMWARE.bin |
Total processes
51
Monitored processes
7
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1236 | "C:\Users\admin\Desktop\HITLER_RANSOMWARE.exe" | C:\Users\admin\Desktop\HITLER_RANSOMWARE.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2544 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2900 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\1710.tmp\ErOne.vbs" | C:\Windows\System32\WScript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2964 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\HITLER_RANSOMWARE.bin.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3152 | chrst.exe | C:\Users\admin\AppData\Local\Temp\1710.tmp\chrst.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: HIGH Description: chrst Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3324 | "C:\Windows\System32\cmd.exe" /c "C:\Users\admin\AppData\Local\Temp\1710.tmp\ExtraTools.bat "C:\Users\admin\Desktop\HITLER_RANSOMWARE.exe"" | C:\Windows\System32\cmd.exe | HITLER_RANSOMWARE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3976 | "C:\Users\admin\Desktop\HITLER_RANSOMWARE.exe" | C:\Users\admin\Desktop\HITLER_RANSOMWARE.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
934
Read events
909
Write events
25
Delete events
0
Modification events
| (PID) Process: | (2964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2964) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2964) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\HITLER_RANSOMWARE.bin.zip | |||
| (PID) Process: | (2964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
Executable files
5
Suspicious files
1
Text files
37
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2964 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\__rzi_2964.33305 | — | |
MD5:— | SHA256:— | |||
| 2964 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\HITLER_RANSOMWARE.bin.zip | compressed | |
MD5:— | SHA256:— | |||
| 1236 | HITLER_RANSOMWARE.exe | C:\Users\admin\AppData\Local\Temp\1710.tmp\ErOne.vbs | text | |
MD5:A764FE63C6CC48C851F0D2A8BA73C2B7 | SHA256:8C4D90A5343CEA107FAD96E842404522AADFC416E7CF84ADC58FE2BA72BBC919 | |||
| 1236 | HITLER_RANSOMWARE.exe | C:\Users\admin\AppData\Local\Temp\1710.tmp\ExtraTools.bat | text | |
MD5:8F07FA594D84C6E234B336DEF0B47CDC | SHA256:DD79D7A80A9087E1FCED76ADE08394843EAB01A8CE263DC2306F46435B451F77 | |||
| 2964 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2964.33790\HITLER_RANSOMWARE.exe | executable | |
MD5:0210D88F1A9C5A5A7EFF5C44CF4F7FBC | SHA256:06C8E0F6FA2616F4FA92C610A1FAEA23887AC31DB8FA78CEDE49B6B8C80EC22F | |||
| 3324 | cmd.exe | C:\Users\admin\Pictures\browseadvice | image | |
MD5:— | SHA256:— | |||
| 3324 | cmd.exe | C:\Users\Public\Pictures\Sample Pictures\Desert | image | |
MD5:BA45C8F60456A672E003A875E469D0EB | SHA256:010F60D2927A35D0235490136EF9F4953B7EE453073794BCAF153D20A64544EA | |||
| 1236 | HITLER_RANSOMWARE.exe | C:\Users\admin\AppData\Local\Temp\1710.tmp\firefox32.exe | executable | |
MD5:866604F3ADB9207E29505012215F203F | SHA256:978ED9B9C86653E8F10FEB9E7F93EB32F2DADEEC42CCCE498403E96B7BB3E3C9 | |||
| 3324 | cmd.exe | C:\Users\Public\Pictures\Sample Pictures\Chrysanthemum | image | |
MD5:076E3CAED758A1C18C91A0E9CAE3368F | SHA256:954F7D96502B5C5FE2E98A5045BCA7F5E9BA11E3DBF92A5C0214A6AA4C7F2208 | |||
| 1236 | HITLER_RANSOMWARE.exe | C:\Users\admin\AppData\Local\Temp\1710.tmp\chrst.exe | executable | |
MD5:C657DAF595B5D535CCC757AD837EEBE8 | SHA256:A02565EC78FA1221433E720BD57B044938345B8C65A73143BD9FF73529767526 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report