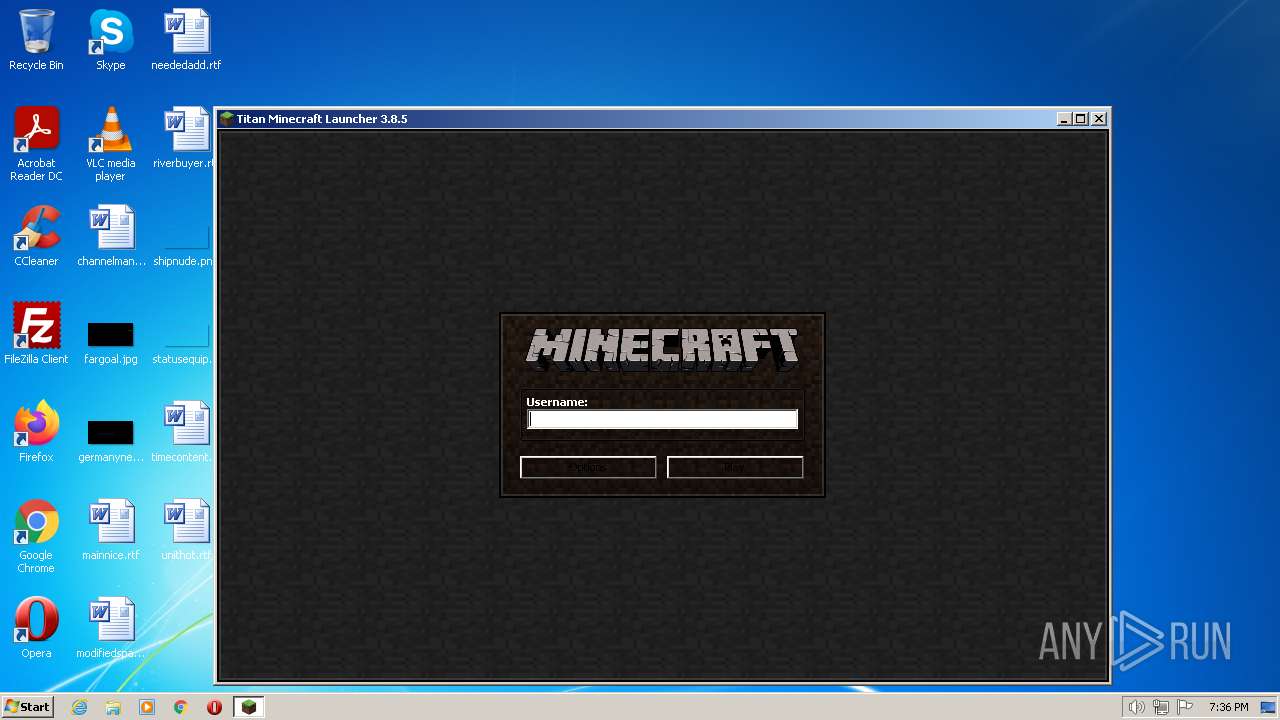
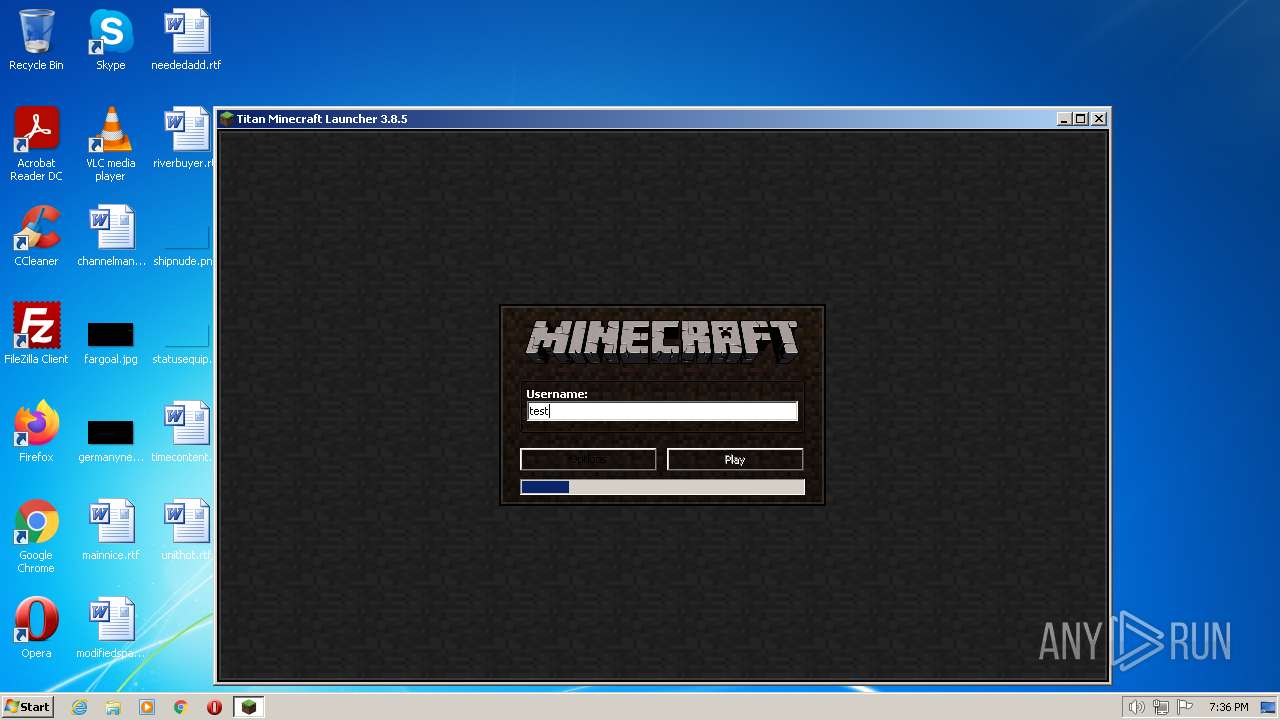
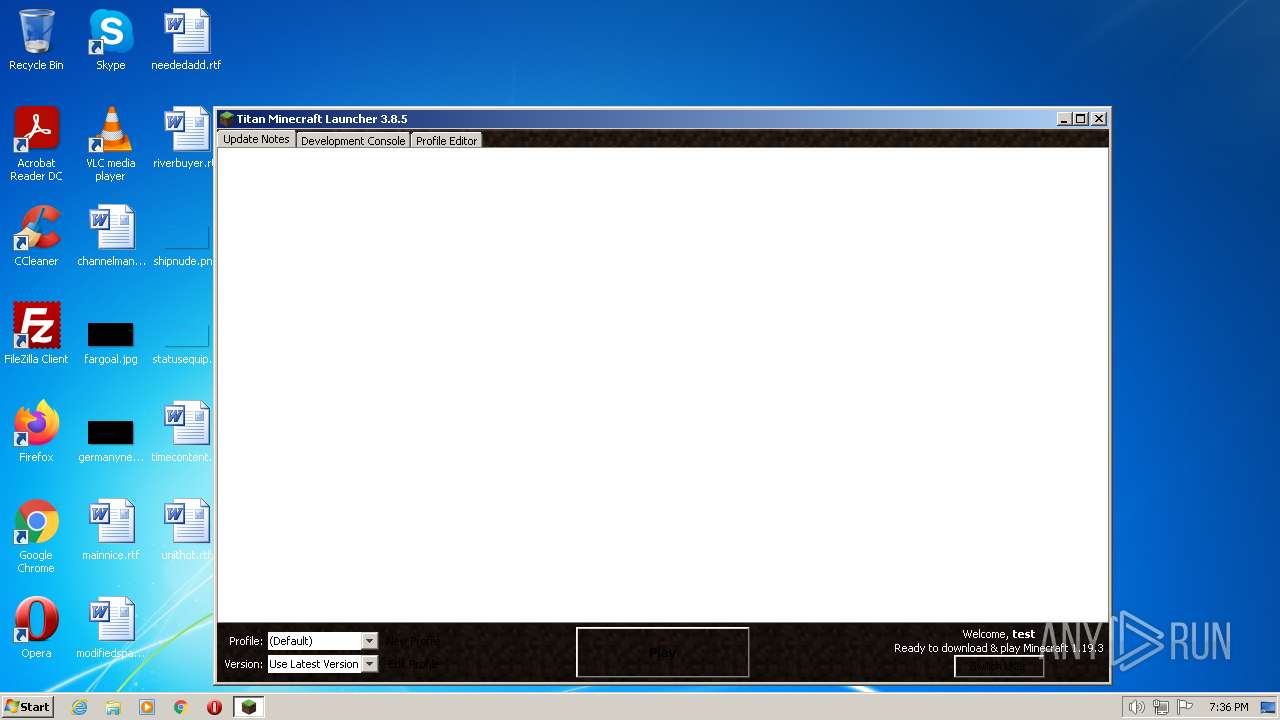
| File name: | Minecraft Launcher.exe |
| Full analysis: | https://app.any.run/tasks/065af8a3-8dbb-4fbd-ac13-1009145e1532 |
| Verdict: | Malicious activity |
| Analysis date: | January 26, 2023, 19:36:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows |
| MD5: | BE214F4374142DFA548AC39ECA507E94 |
| SHA1: | 3E2279A0EB74AE3DCF2D60CD6ED33A3FD45FA304 |
| SHA256: | EA04FA0A4191001206744C948DBF1A810A633FD760F699C16B60386C66A6B6B7 |
| SSDEEP: | 98304:XfZt4EJC5UiDvZpHMM+5rFp3tSjiZmJXbICNqI6:XxzJZiDR6M+5roOZkXbICNqI6 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks for Java to be installed
- Minecraft Launcher.exe (PID: 856)
INFO
Checks supported languages
- Minecraft Launcher.exe (PID: 856)
- javaw.exe (PID: 2284)
The process checks LSA protection
- icacls.exe (PID: 1464)
- javaw.exe (PID: 2284)
Reads the computer name
- javaw.exe (PID: 2284)
Creates files in the program directory
- javaw.exe (PID: 2284)
Reads the machine GUID from the registry
- javaw.exe (PID: 2284)
Create files in a temporary directory
- javaw.exe (PID: 2284)
Creates files or folders in the user directory
- javaw.exe (PID: 2284)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2023-Jan-16 21:52:12 |
| Detected languages: |
|
| TLS Callbacks: | 2 callback(s) detected. |
| CompanyName: | Titan Launcher |
| FileDescription: | 1.19 Minecraft Launcher |
| FileVersion: | 3.8.5 |
| InternalName: | Minecraft Launcher |
| LegalCopyright: | Titan Launcher |
| LegalTrademarks: | - |
| OriginalFilename: | Minecraft Launcher.exe |
| ProductName: | Titan Launcher |
| ProductVersion: | 3.8.5 |
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 144 |
| e_cp: | 3 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | - |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | - |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 128 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 9 |
| TimeDateStamp: | 2023-Jan-16 21:52:12 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 4096 | 43808 | 44032 | IMAGE_SCN_ALIGN_1024BYTES, IMAGE_SCN_ALIGN_16BYTES, IMAGE_SCN_ALIGN_1BYTES, IMAGE_SCN_ALIGN_2048BYTES, IMAGE_SCN_ALIGN_256BYTES, IMAGE_SCN_ALIGN_32BYTES, IMAGE_SCN_ALIGN_4096BYTES, IMAGE_SCN_ALIGN_4BYTES, IMAGE_SCN_ALIGN_64BYTES, IMAGE_SCN_ALIGN_8192BYTES, IMAGE_SCN_ALIGN_8BYTES, IMAGE_SCN_ALIGN_MASK, IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.25323 |
.data | 49152 | 40 | 512 | IMAGE_SCN_ALIGN_1024BYTES, IMAGE_SCN_ALIGN_16BYTES, IMAGE_SCN_ALIGN_1BYTES, IMAGE_SCN_ALIGN_256BYTES, IMAGE_SCN_ALIGN_2BYTES, IMAGE_SCN_ALIGN_32BYTES, IMAGE_SCN_ALIGN_4096BYTES, IMAGE_SCN_ALIGN_4BYTES, IMAGE_SCN_ALIGN_512BYTES, IMAGE_SCN_ALIGN_64BYTES, IMAGE_SCN_ALIGN_8192BYTES, IMAGE_SCN_ALIGN_MASK, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.312429 |
.rdata | 53248 | 3864 | 4096 | IMAGE_SCN_ALIGN_1024BYTES, IMAGE_SCN_ALIGN_16BYTES, IMAGE_SCN_ALIGN_2048BYTES, IMAGE_SCN_ALIGN_2BYTES, IMAGE_SCN_ALIGN_32BYTES, IMAGE_SCN_ALIGN_4096BYTES, IMAGE_SCN_ALIGN_4BYTES, IMAGE_SCN_ALIGN_512BYTES, IMAGE_SCN_ALIGN_64BYTES, IMAGE_SCN_ALIGN_8192BYTES, IMAGE_SCN_ALIGN_8BYTES, IMAGE_SCN_ALIGN_MASK, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.554 |
.eh_fram | 57344 | 7440 | 7680 | IMAGE_SCN_ALIGN_1024BYTES, IMAGE_SCN_ALIGN_16BYTES, IMAGE_SCN_ALIGN_1BYTES, IMAGE_SCN_ALIGN_256BYTES, IMAGE_SCN_ALIGN_2BYTES, IMAGE_SCN_ALIGN_32BYTES, IMAGE_SCN_ALIGN_4096BYTES, IMAGE_SCN_ALIGN_4BYTES, IMAGE_SCN_ALIGN_512BYTES, IMAGE_SCN_ALIGN_64BYTES, IMAGE_SCN_ALIGN_8192BYTES, IMAGE_SCN_ALIGN_MASK, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.88209 |
.bss | 65536 | 38520 | 0 | IMAGE_SCN_ALIGN_1024BYTES, IMAGE_SCN_ALIGN_16BYTES, IMAGE_SCN_ALIGN_2048BYTES, IMAGE_SCN_ALIGN_2BYTES, IMAGE_SCN_ALIGN_32BYTES, IMAGE_SCN_ALIGN_4096BYTES, IMAGE_SCN_ALIGN_4BYTES, IMAGE_SCN_ALIGN_512BYTES, IMAGE_SCN_ALIGN_64BYTES, IMAGE_SCN_ALIGN_8192BYTES, IMAGE_SCN_ALIGN_8BYTES, IMAGE_SCN_ALIGN_MASK, IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.idata | 106496 | 3624 | 4096 | IMAGE_SCN_ALIGN_1024BYTES, IMAGE_SCN_ALIGN_16BYTES, IMAGE_SCN_ALIGN_1BYTES, IMAGE_SCN_ALIGN_256BYTES, IMAGE_SCN_ALIGN_2BYTES, IMAGE_SCN_ALIGN_32BYTES, IMAGE_SCN_ALIGN_4096BYTES, IMAGE_SCN_ALIGN_4BYTES, IMAGE_SCN_ALIGN_512BYTES, IMAGE_SCN_ALIGN_64BYTES, IMAGE_SCN_ALIGN_8192BYTES, IMAGE_SCN_ALIGN_MASK, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.92285 |
.CRT | 110592 | 24 | 512 | IMAGE_SCN_ALIGN_1024BYTES, IMAGE_SCN_ALIGN_16BYTES, IMAGE_SCN_ALIGN_1BYTES, IMAGE_SCN_ALIGN_256BYTES, IMAGE_SCN_ALIGN_2BYTES, IMAGE_SCN_ALIGN_32BYTES, IMAGE_SCN_ALIGN_4096BYTES, IMAGE_SCN_ALIGN_4BYTES, IMAGE_SCN_ALIGN_512BYTES, IMAGE_SCN_ALIGN_64BYTES, IMAGE_SCN_ALIGN_8192BYTES, IMAGE_SCN_ALIGN_MASK, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.114463 |
.tls | 114688 | 32 | 512 | IMAGE_SCN_ALIGN_1024BYTES, IMAGE_SCN_ALIGN_16BYTES, IMAGE_SCN_ALIGN_1BYTES, IMAGE_SCN_ALIGN_256BYTES, IMAGE_SCN_ALIGN_2BYTES, IMAGE_SCN_ALIGN_32BYTES, IMAGE_SCN_ALIGN_4096BYTES, IMAGE_SCN_ALIGN_4BYTES, IMAGE_SCN_ALIGN_512BYTES, IMAGE_SCN_ALIGN_64BYTES, IMAGE_SCN_ALIGN_8192BYTES, IMAGE_SCN_ALIGN_MASK, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.204488 |
.rsrc | 118784 | 12800 | 12800 | IMAGE_SCN_ALIGN_1024BYTES, IMAGE_SCN_ALIGN_16BYTES, IMAGE_SCN_ALIGN_1BYTES, IMAGE_SCN_ALIGN_256BYTES, IMAGE_SCN_ALIGN_2BYTES, IMAGE_SCN_ALIGN_32BYTES, IMAGE_SCN_ALIGN_4096BYTES, IMAGE_SCN_ALIGN_4BYTES, IMAGE_SCN_ALIGN_512BYTES, IMAGE_SCN_ALIGN_64BYTES, IMAGE_SCN_ALIGN_8192BYTES, IMAGE_SCN_ALIGN_MASK, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.69163 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.594 | 9640 | UNKNOWN | Process Default Language | RT_ICON |
2 | 2.25163 | 6 | UNKNOWN | Process Default Language | RT_RCDATA |
17 | 2.32193 | 5 | UNKNOWN | Process Default Language | RT_RCDATA |
20 | 1.58496 | 3 | UNKNOWN | Process Default Language | RT_RCDATA |
21 | 3.78875 | 22 | UNKNOWN | Process Default Language | RT_RCDATA |
25 | 2 | 4 | UNKNOWN | Process Default Language | RT_RCDATA |
27 | 2 | 4 | UNKNOWN | Process Default Language | RT_RCDATA |
101 | 4.04307 | 50 | UNKNOWN | Process Default Language | RT_RCDATA |
102 | 4.20399 | 54 | UNKNOWN | Process Default Language | RT_RCDATA |
103 | 4.14776 | 53 | UNKNOWN | Process Default Language | RT_RCDATA |
Imports
advapi32.dll |
kernel32.dll |
msvcrt.dll |
msvcrt.dll (#2) |
shell32.dll |
user32.dll |
Total processes
37
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 856 | "C:\Users\admin\AppData\Local\Temp\Minecraft Launcher.exe" | C:\Users\admin\AppData\Local\Temp\Minecraft Launcher.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Titan Launcher Integrity Level: MEDIUM Description: 1.19 Minecraft Launcher Exit code: 0 Version: 3.8.5 Modules
| |||||||||||||||
| 1464 | C:\Windows\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\system32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2284 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -Xms256m -Xmx512m -jar "C:\Users\admin\AppData\Local\Temp\Minecraft Launcher.exe" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | Minecraft Launcher.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
Total events
1 136
Read events
1 132
Write events
4
Delete events
0
Modification events
| (PID) Process: | (2284) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: javaw.exe | |||
Executable files
0
Suspicious files
2
Text files
18
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2284 | javaw.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:— | SHA256:— | |||
| 2284 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\launcher_profiles.json | text | |
MD5:— | SHA256:— | |||
| 2284 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\servers.dat | image | |
MD5:009B730618EB922205FBB3E29BC81B9D | SHA256:517284D561F3B06BAE25F16C36B4FFDDDFC6C1234FBC4943C268EAF06D0F6403 | |||
| 2284 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio2225960178801575526.tmp | image | |
MD5:CB2666EAE03572A523CE8EAD1EB45134 | SHA256:7BC1CC5F09034D3CA71B5F23AF0E83A2B681E90F5B986DE3748D555F527251B4 | |||
| 2284 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\minecraft launcher\options.json | binary | |
MD5:B9CF32949297936C8EDE369A16865831 | SHA256:4420CB57C8D4ADB8D867534F258D16D5BB7621D04A2C710CC94CBCA9F8D4E7C1 | |||
| 2284 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio5548608394508240303.tmp | image | |
MD5:D141CC8E71A3351F1AACB88A74B45FA4 | SHA256:2788675E062E1111EAD50A9A05971A7C11FE6246A89F571CF9F59ED68C72BB17 | |||
| 2284 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio3366807310139858757.tmp | image | |
MD5:D141CC8E71A3351F1AACB88A74B45FA4 | SHA256:2788675E062E1111EAD50A9A05971A7C11FE6246A89F571CF9F59ED68C72BB17 | |||
| 2284 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio3554634379831341075.tmp | image | |
MD5:91D3708A258E5F789E2AE888CF68F66F | SHA256:0AD2672561C2BA4E86C38702682BD84D720351F3E5C4CA232F0043AAB7FA8B28 | |||
| 2284 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio1615245729233844905.tmp | image | |
MD5:D141CC8E71A3351F1AACB88A74B45FA4 | SHA256:2788675E062E1111EAD50A9A05971A7C11FE6246A89F571CF9F59ED68C72BB17 | |||
| 2284 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio8280074012490535825.tmp | image | |
MD5:E7E38B97A9FE7E0BB219AAF28BB750B7 | SHA256:99EDDE5742D3F824EB8F1EA03CCBDB969A04F94235CAE509644A442F8EBB039E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
8
DNS requests
7
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2284 | javaw.exe | GET | 410 | 3.64.163.50:80 | http://temc.xyz/failsafe/failsafe.txt | US | html | 102 b | malicious |
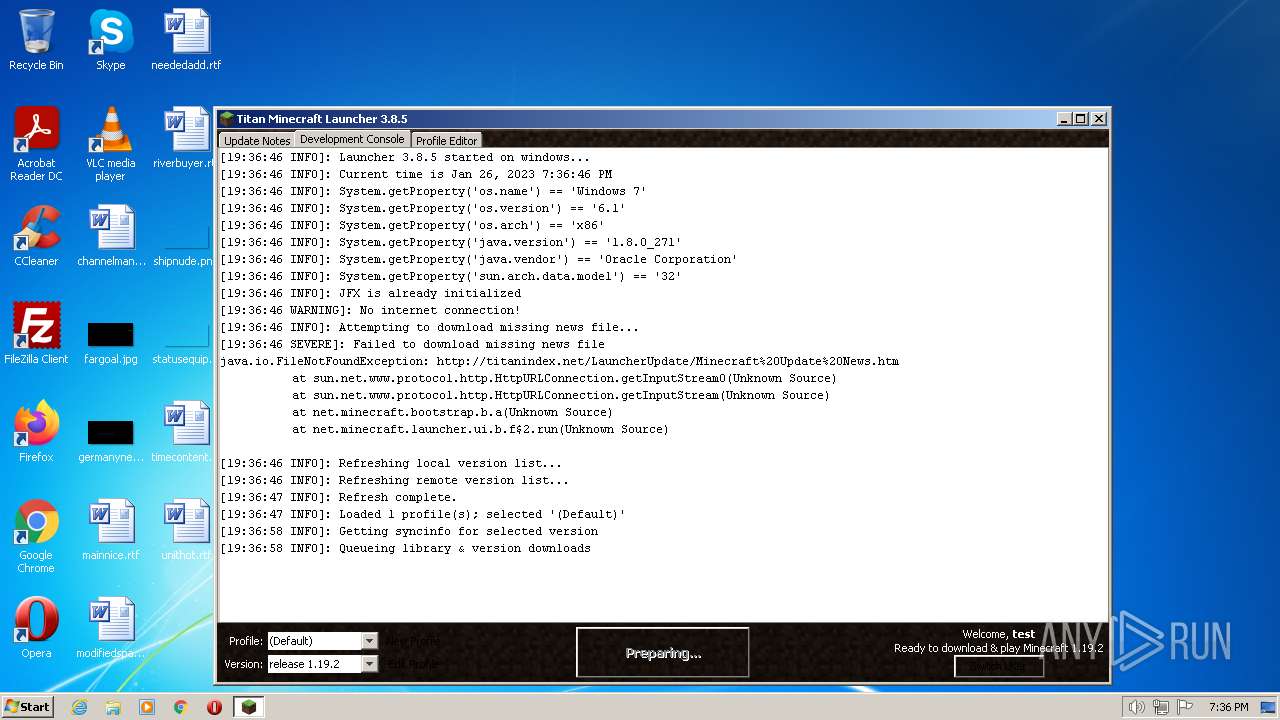
2284 | javaw.exe | GET | 410 | 3.64.163.50:80 | http://titanindex.net/LauncherUpdate/version.txt | US | html | 108 b | malicious |
2284 | javaw.exe | GET | 410 | 3.64.163.50:80 | http://titanindex.net/LauncherUpdate/Minecraft%20Update%20News.htm | US | html | 108 b | malicious |
2284 | javaw.exe | GET | 410 | 3.64.163.50:80 | http://titanindex.net/LauncherUpdate/Minecraft%20Update%20News.htm | US | html | 108 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2284 | javaw.exe | 188.114.96.3:80 | titan.mythicmc.org | CLOUDFLARENET | NL | malicious |
2284 | javaw.exe | 198.54.115.64:80 | teamextrememc.com | NAMECHEAP-NET | US | malicious |
2284 | javaw.exe | 3.64.163.50:80 | titanindex.net | AMAZON-02 | DE | malicious |
2284 | javaw.exe | 13.107.237.40:443 | launchermeta.mojang.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2284 | javaw.exe | 13.107.238.45:443 | piston-meta.mojang.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
titan.mythicmc.org |
| malicious |
teamextrememc.com |
| malicious |
titanindex.net |
| malicious |
temc.xyz |
| malicious |
launchermeta.mojang.com |
| whitelisted |
piston-meta.mojang.com |
| suspicious |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2284 | javaw.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
2284 | javaw.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2284 | javaw.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
2284 | javaw.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2284 | javaw.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |