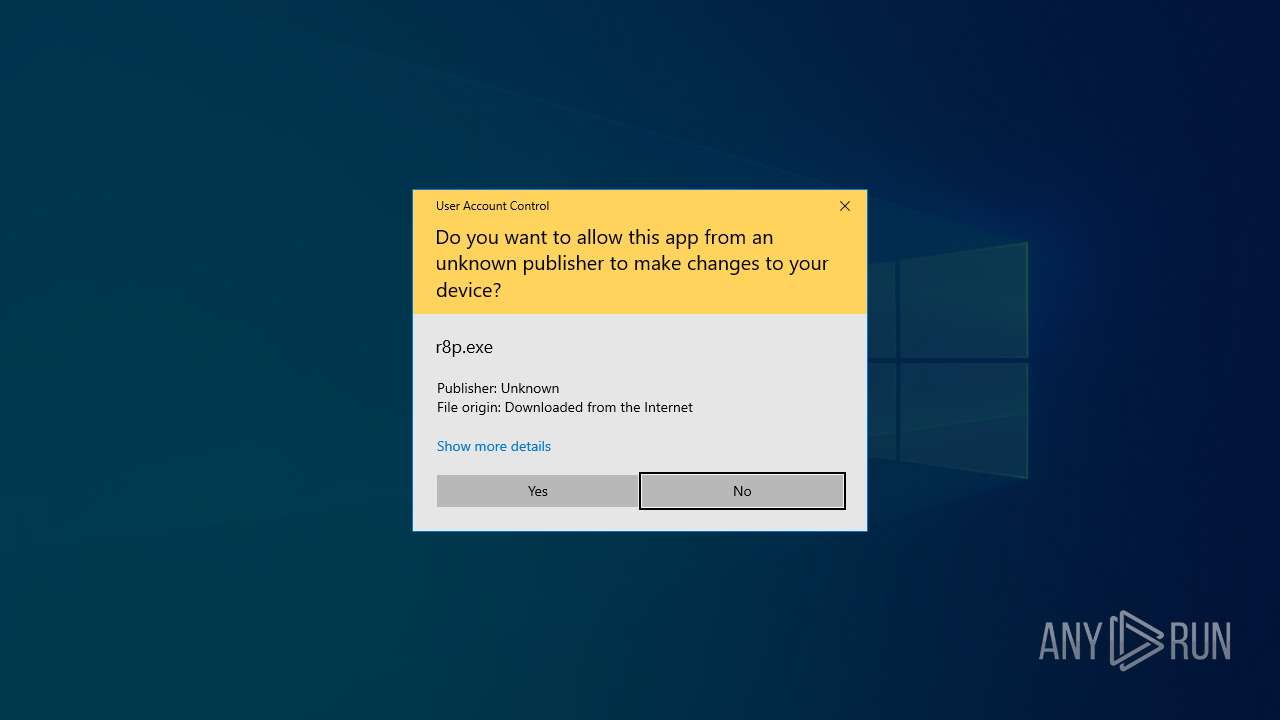
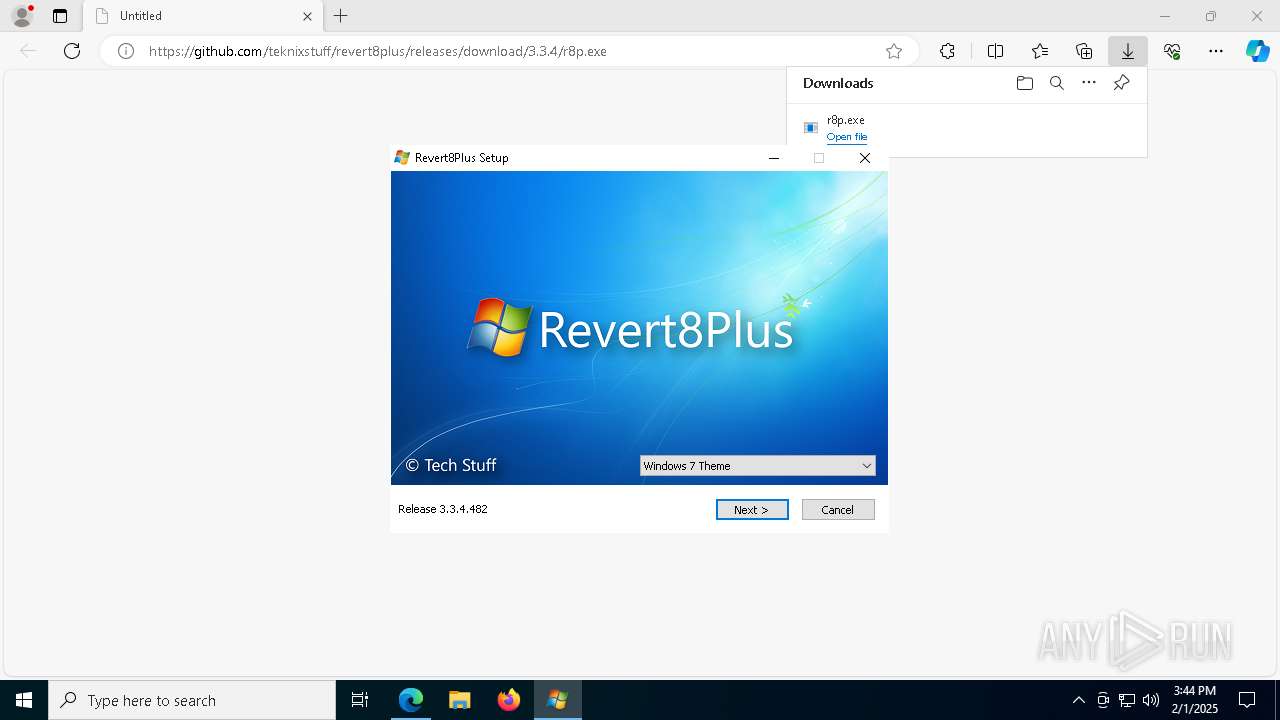
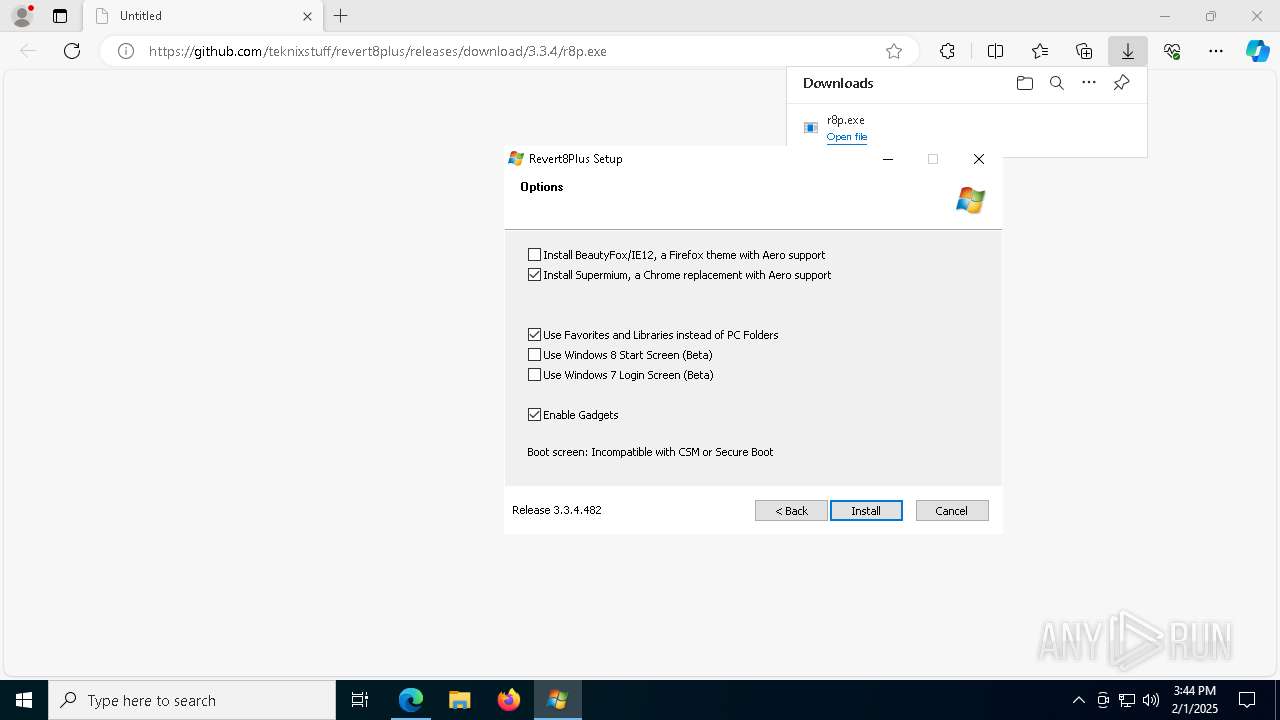
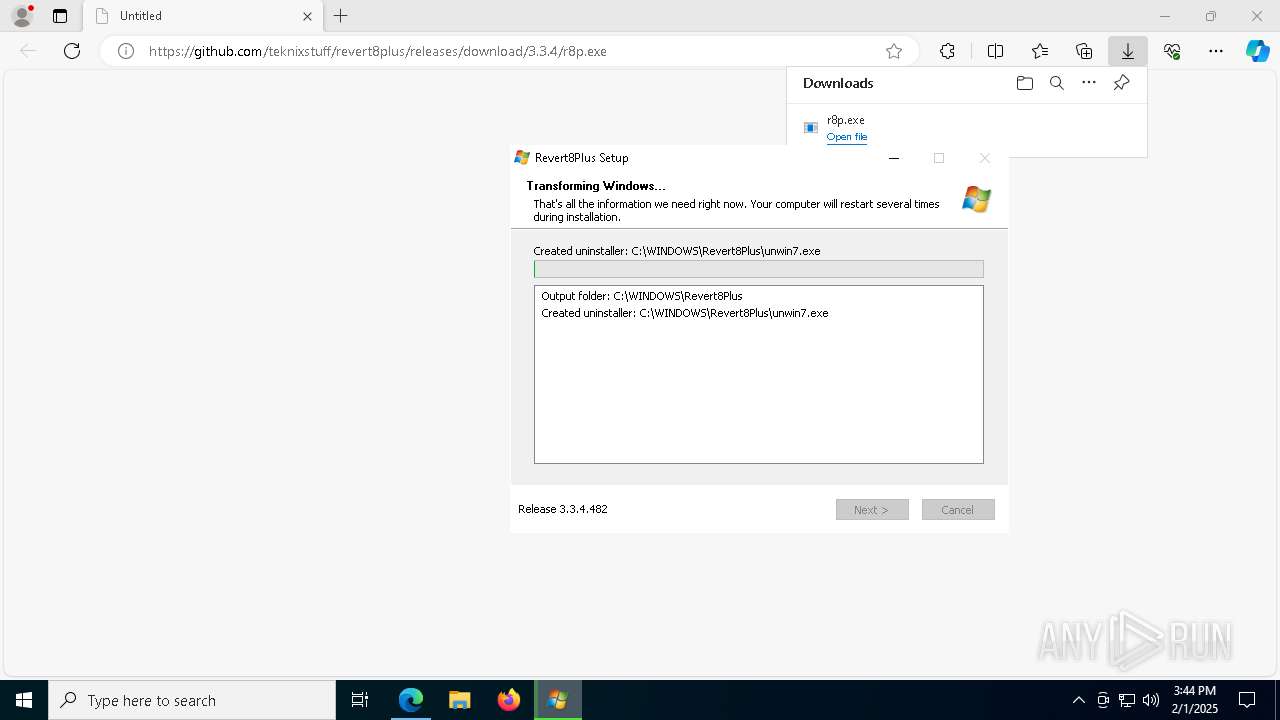
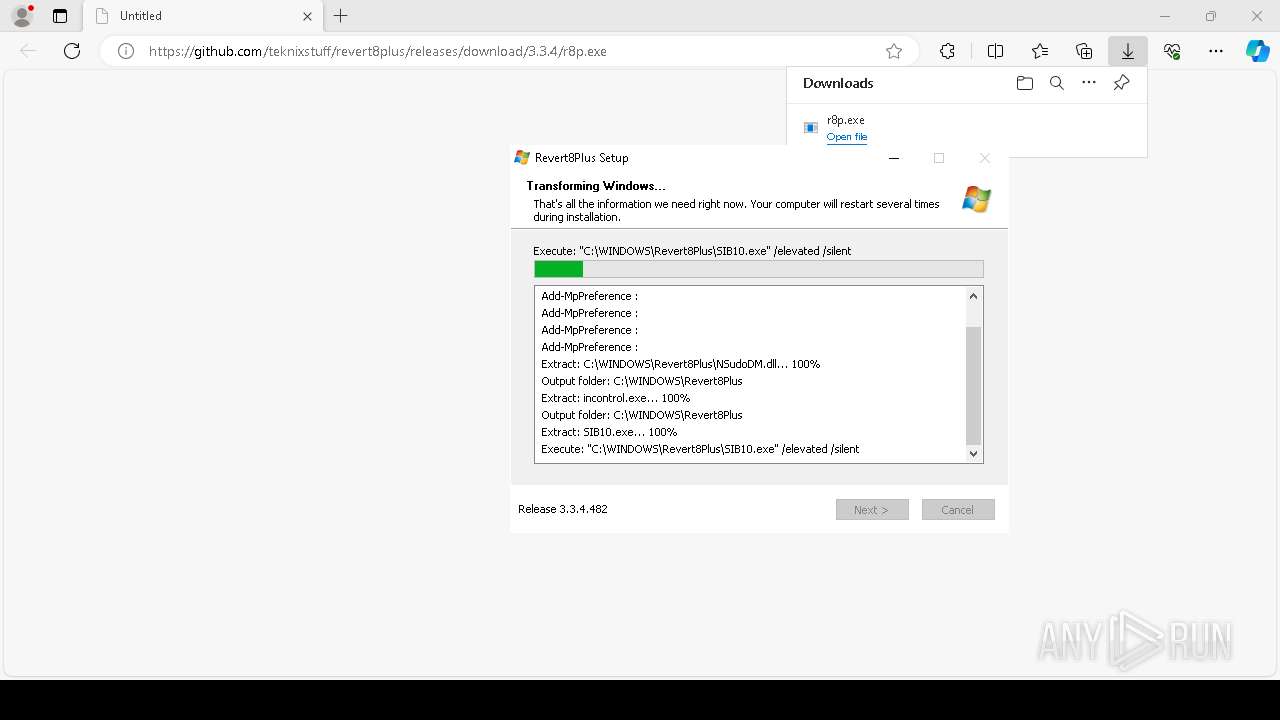
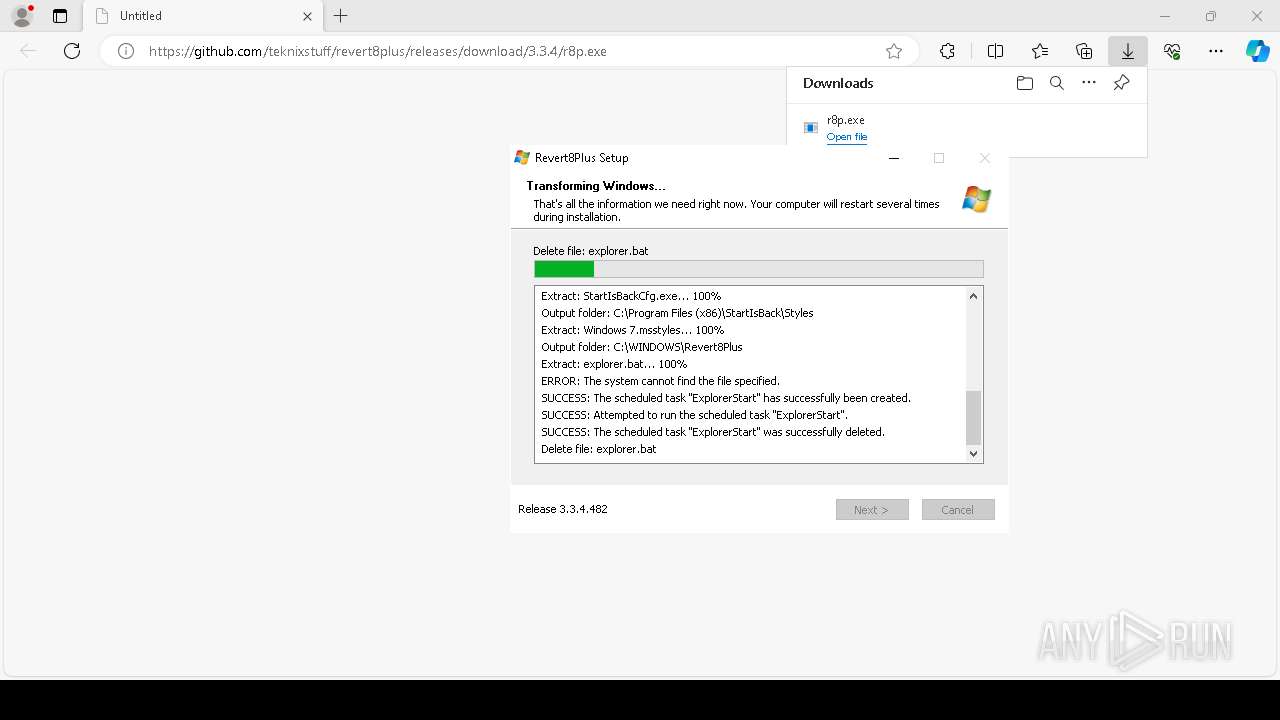
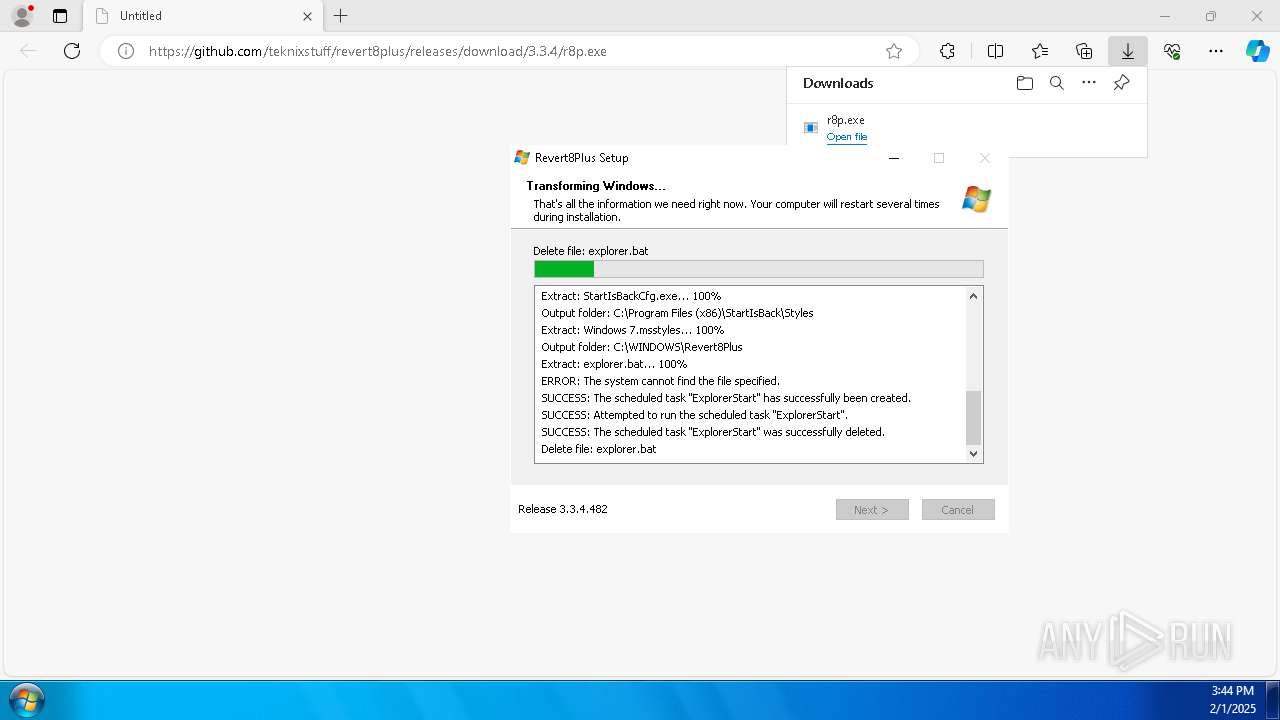
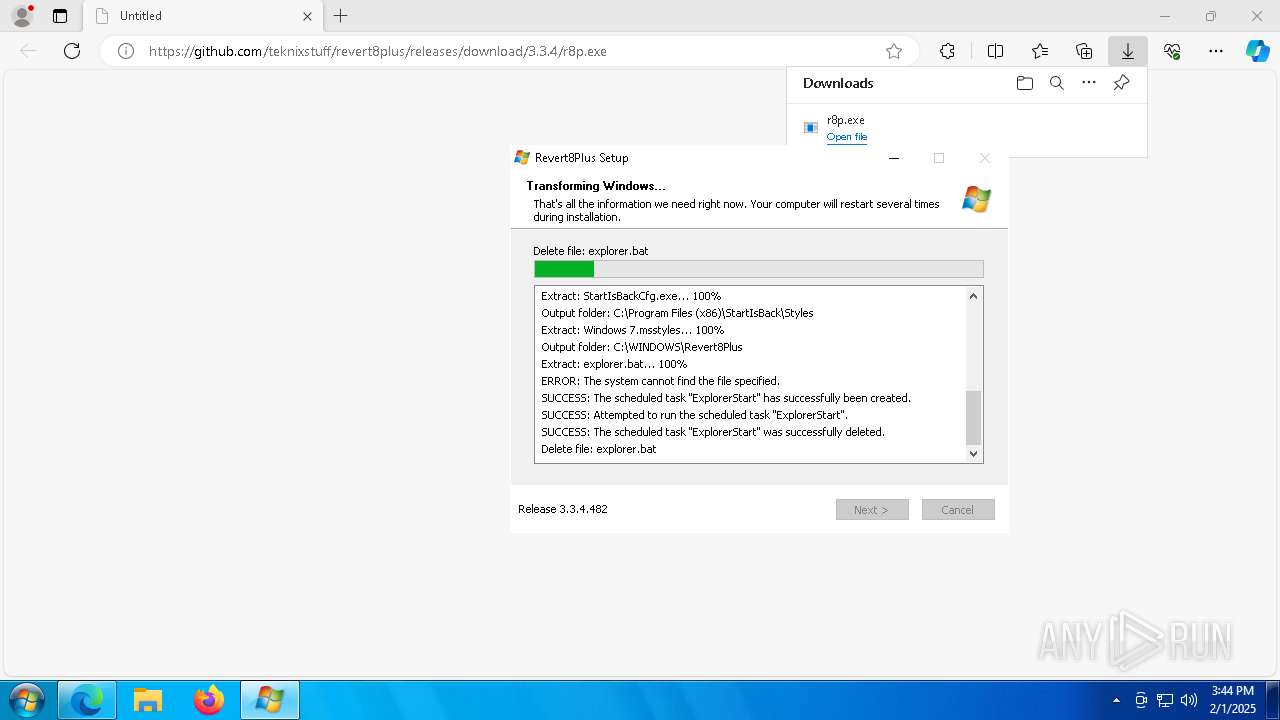
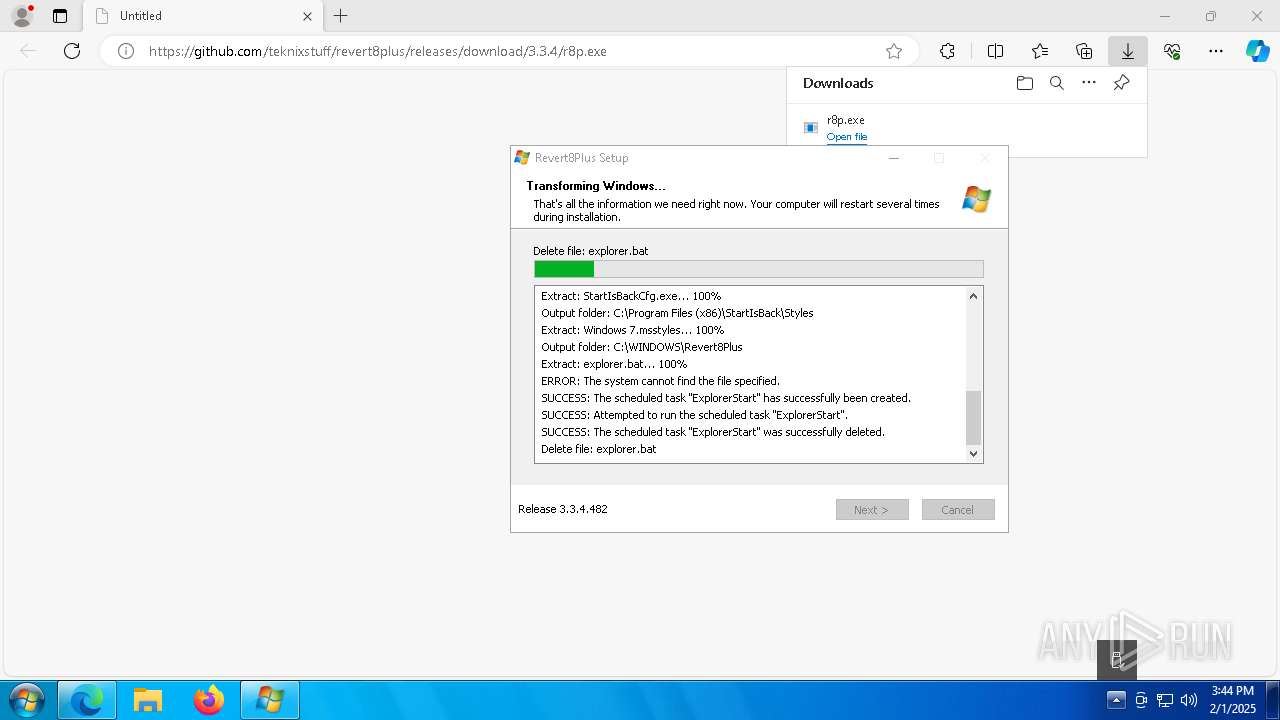
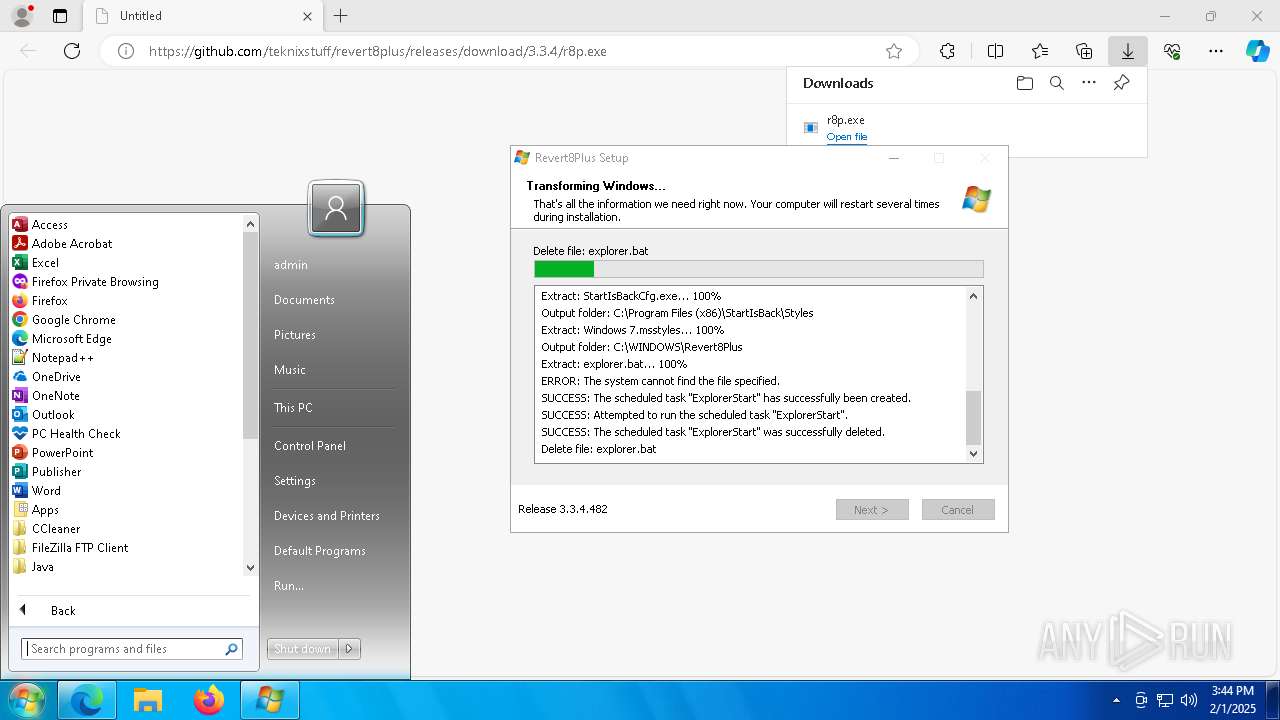
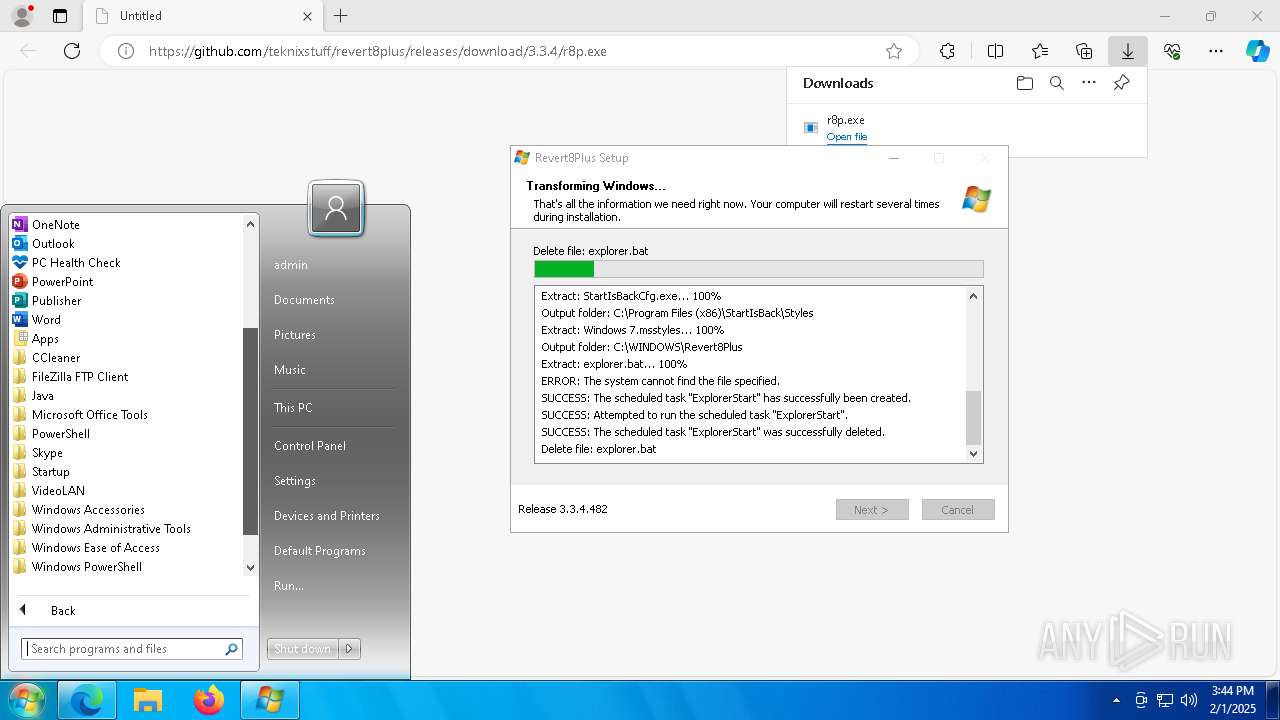
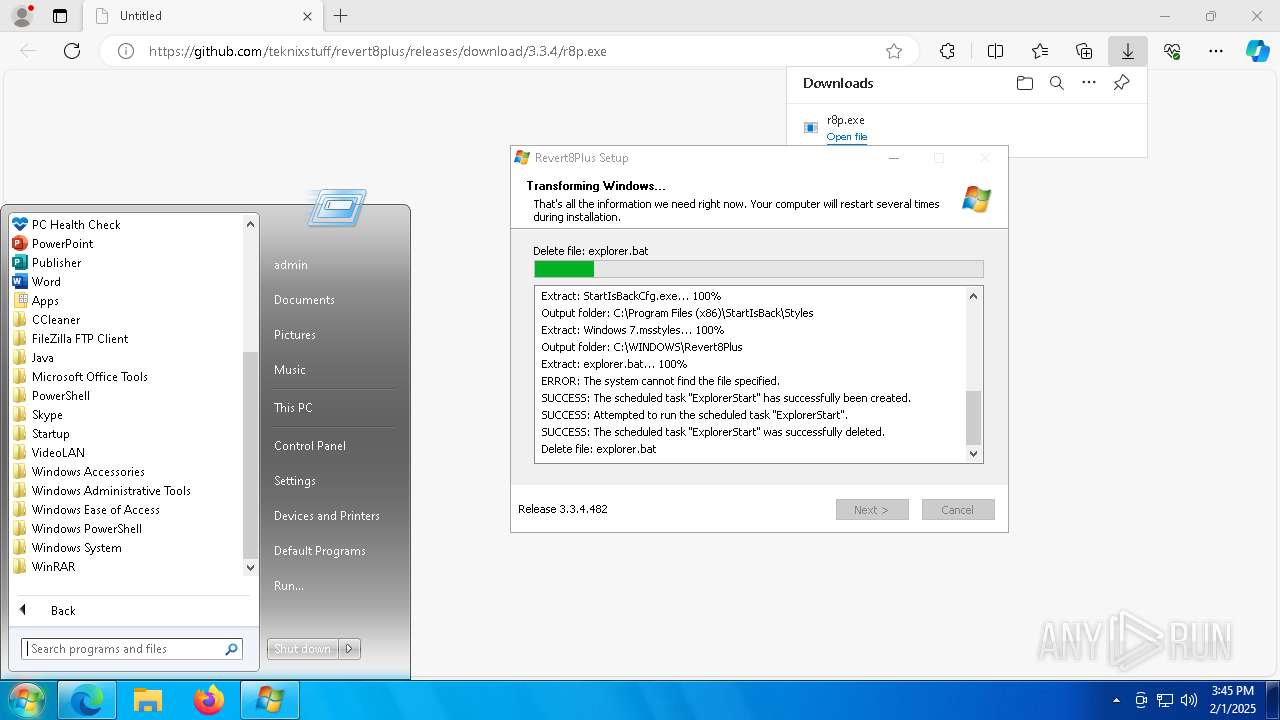
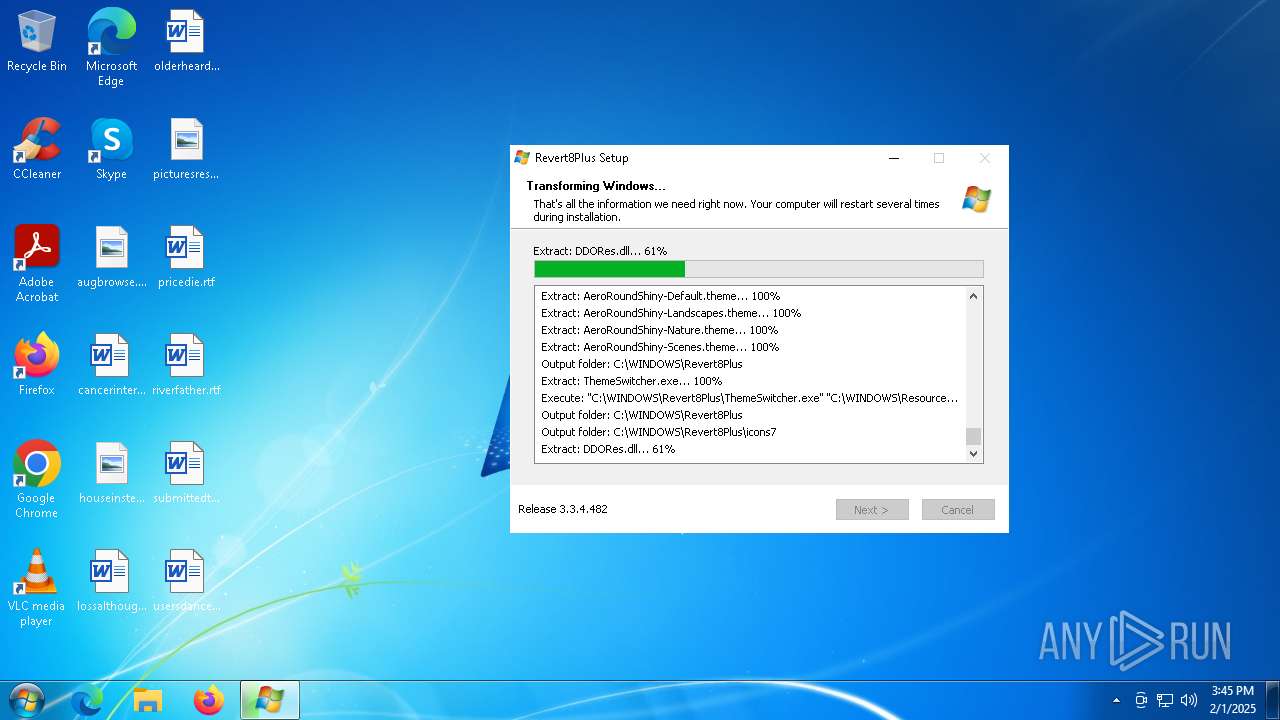
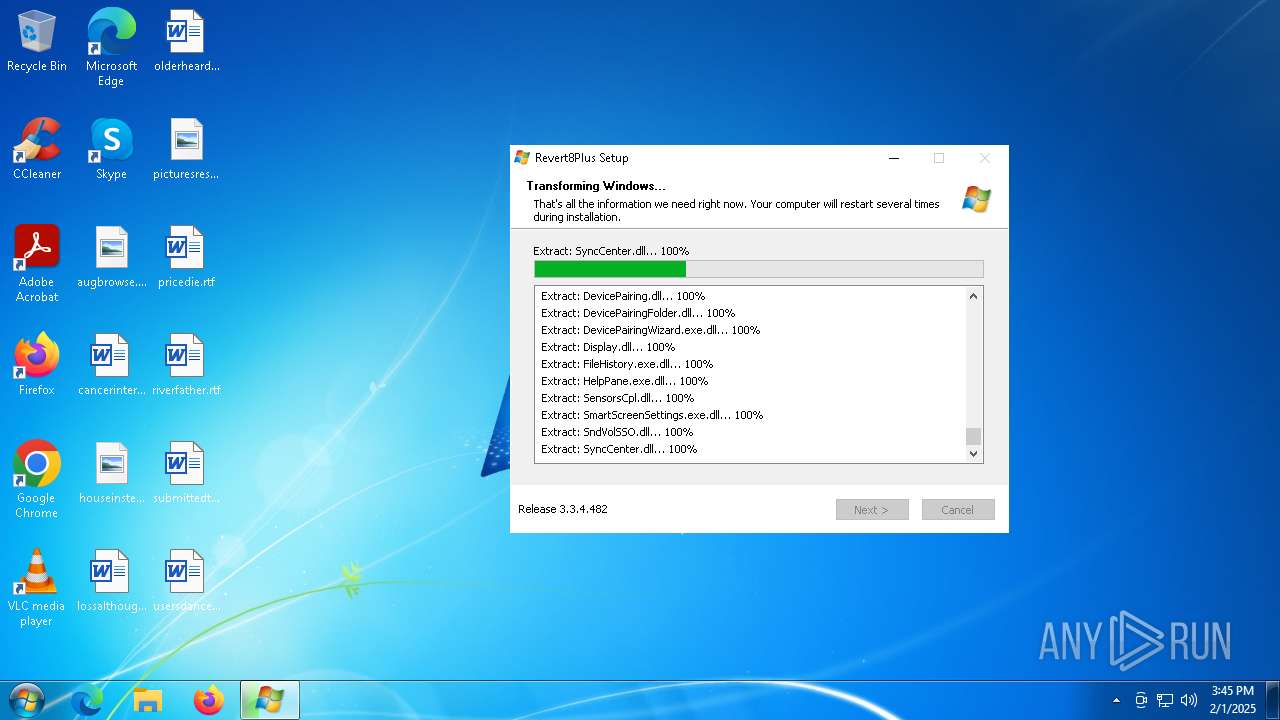
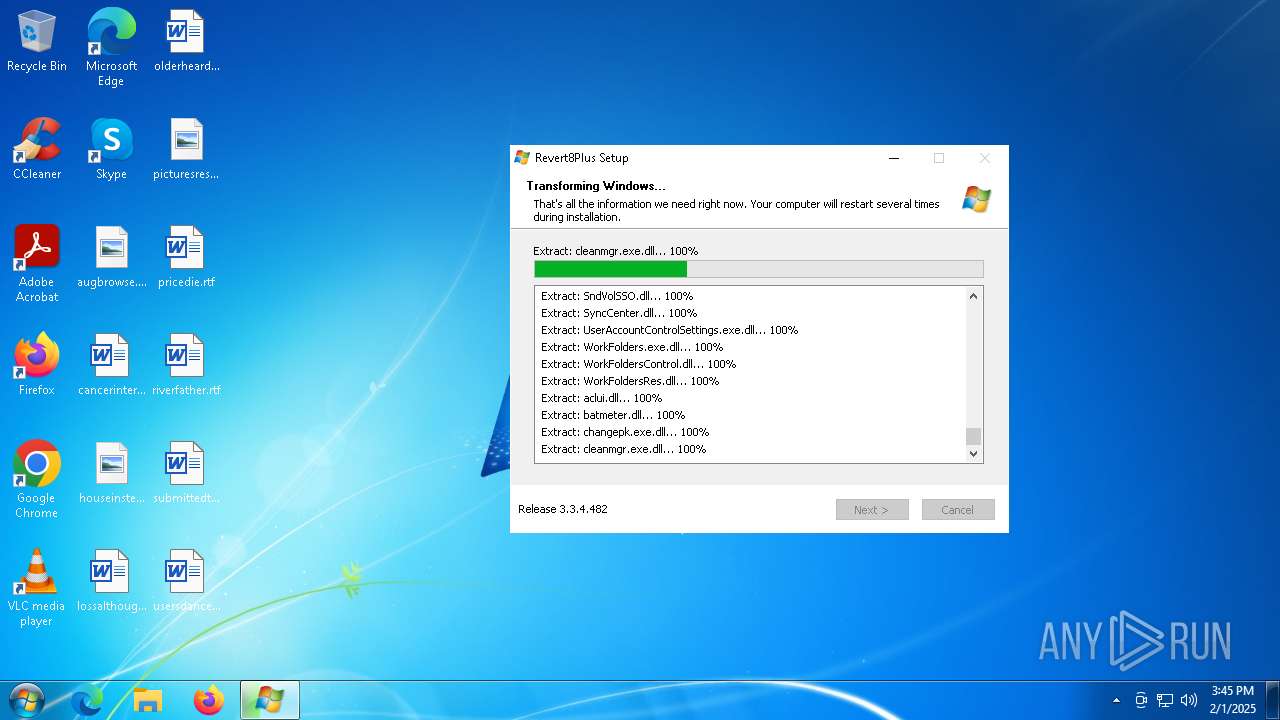
| URL: | https://github.com/teknixstuff/revert8plus/releases/download/3.3.4/r8p.exe |
| Full analysis: | https://app.any.run/tasks/4c6ff021-7798-491a-b2cc-356b8f2e641b |
| Verdict: | Malicious activity |
| Analysis date: | February 01, 2025, 15:40:39 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | DDA4B9084C433DCFA0456E3C872E0A7C |
| SHA1: | 3EE715561F9818E7DE2265B5973979D9629781BF |
| SHA256: | EA02C97D036BDB10980DE28C87C42D9A955B4CE63975026AA2B7F73549068432 |
| SSDEEP: | 3:N8tEdhAXfMAW7VeiArkCWilcaA:2uwX0XIiM4ilcaA |
MALICIOUS
Adds path to the Windows Defender exclusion list
- r8p.exe (PID: 7332)
Changes image file execution options
- r8p.exe (PID: 7332)
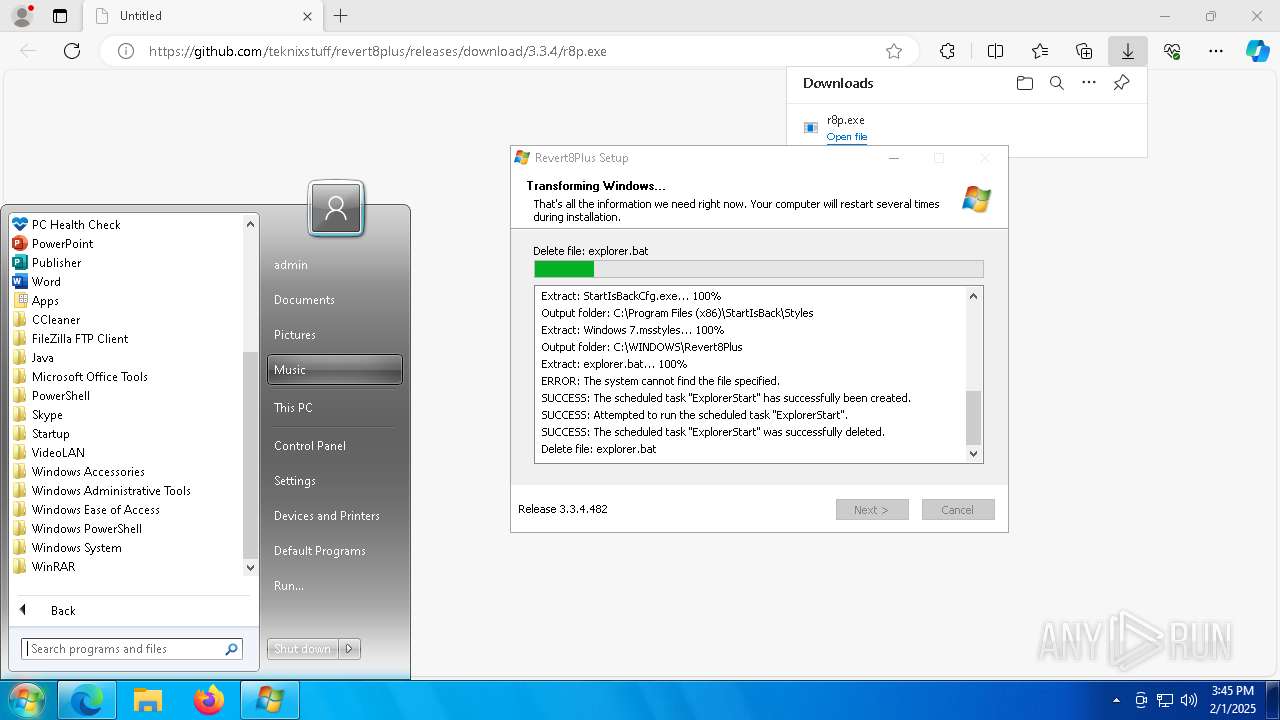
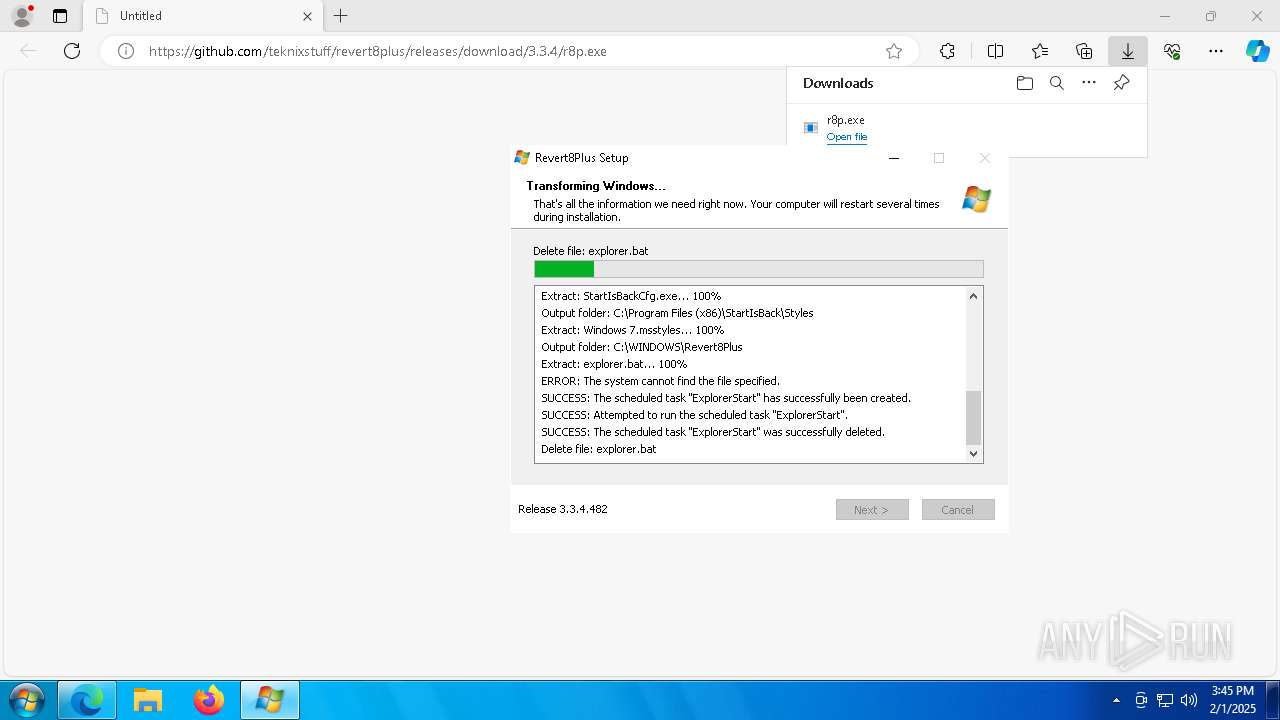
Uses Task Scheduler to run other applications
- StartIsBackCfg.exe (PID: 2424)
- cmd.exe (PID: 2012)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- r8p.exe (PID: 7332)
Found strings related to reading or modifying Windows Defender settings
- r8p.exe (PID: 7332)
The process creates files with name similar to system file names
- r8p.exe (PID: 7332)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 7188)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7188)
Starts CMD.EXE for commands execution
- r8p.exe (PID: 7332)
Accesses antivirus product name via WMI (SCRIPT)
- WMIC.exe (PID: 7636)
Executable content was dropped or overwritten
- r8p.exe (PID: 7332)
- StartIsBackCfg.exe (PID: 2424)
- SIB10.exe (PID: 3000)
Creates a software uninstall entry
- r8p.exe (PID: 7332)
- StartIsBackCfg.exe (PID: 2424)
Uses powercfg.exe to modify the power settings
- r8p.exe (PID: 7332)
Reads the date of Windows installation
- r8p.exe (PID: 7332)
- SearchApp.exe (PID: 7980)
Executes script without checking the security policy
- powershell.exe (PID: 5980)
The process bypasses the loading of PowerShell profile settings
- r8p.exe (PID: 7332)
Starts POWERSHELL.EXE for commands execution
- r8p.exe (PID: 7332)
There is functionality for taking screenshot (YARA)
- r8p.exe (PID: 7332)
Reads security settings of Internet Explorer
- StartIsBackCfg.exe (PID: 2424)
- SIB10.exe (PID: 3000)
Uses TASKKILL.EXE to kill process
- StartIsBackCfg.exe (PID: 2424)
Creates/Modifies COM task schedule object
- StartIsBackCfg.exe (PID: 2424)
Changes default file association
- StartIsBackCfg.exe (PID: 2424)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 4132)
- schtasks.exe (PID: 1304)
The process executes via Task Scheduler
- explorer.exe (PID: 1292)
Executing commands from a ".bat" file
- r8p.exe (PID: 7332)
Write to the desktop.ini file (may be used to cloak folders)
- r8p.exe (PID: 7332)
Process drops legitimate windows executable
- r8p.exe (PID: 7332)
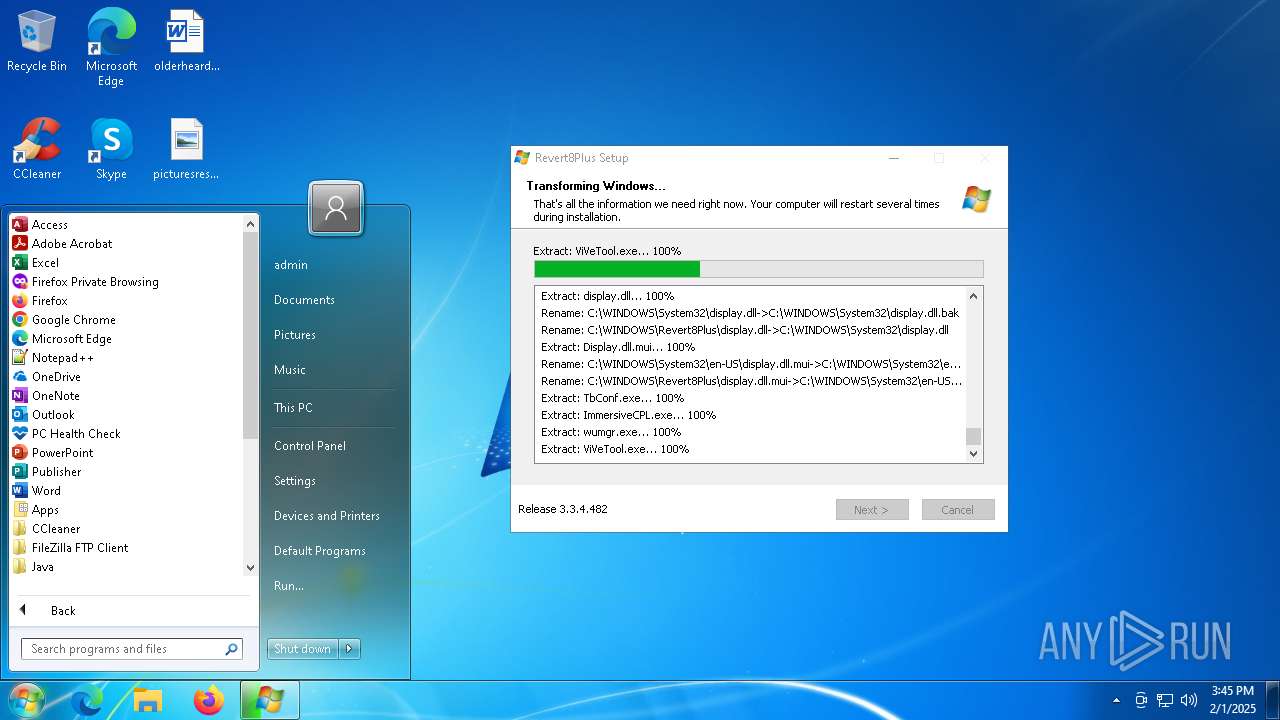
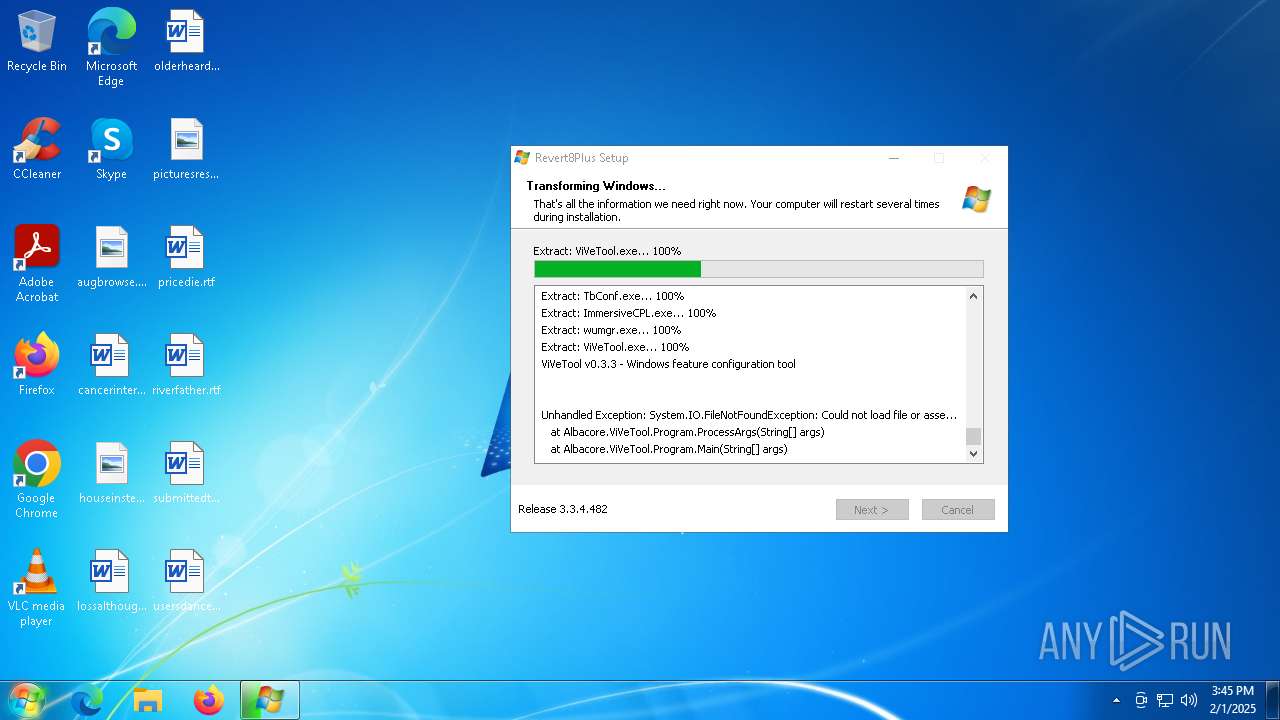
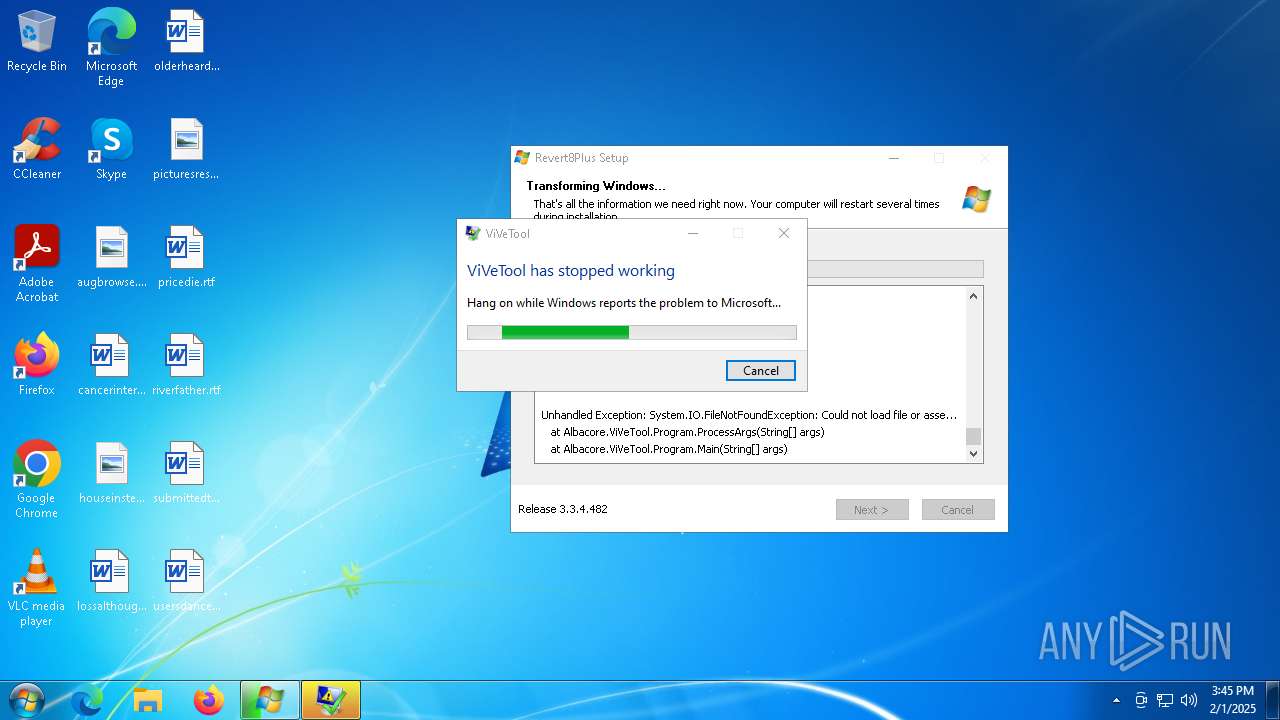
Executes application which crashes
- ViVeTool.exe (PID: 7756)
INFO
Reads the computer name
- identity_helper.exe (PID: 7608)
- r8p.exe (PID: 7332)
- SIB10.exe (PID: 3000)
- StartIsBackCfg.exe (PID: 2424)
- TextInputHost.exe (PID: 900)
- SearchApp.exe (PID: 7980)
- UpdateCheck.exe (PID: 3124)
- ThemeSwitcher.exe (PID: 6380)
- identity_helper.exe (PID: 4672)
- ViVeTool.exe (PID: 7756)
Checks supported languages
- identity_helper.exe (PID: 7608)
- r8p.exe (PID: 7332)
- incontrol.exe (PID: 4944)
- SIB10.exe (PID: 3000)
- startscreen.exe (PID: 3836)
- StartIsBackCfg.exe (PID: 2424)
- StartScreen.exe (PID: 772)
- UpdateCheck.exe (PID: 3124)
- TextInputHost.exe (PID: 900)
- SearchApp.exe (PID: 7980)
- identity_helper.exe (PID: 4672)
- ThemeSwitcher.exe (PID: 6380)
- ViVeTool.exe (PID: 7756)
Executable content was dropped or overwritten
- msedge.exe (PID: 6364)
- msedge.exe (PID: 3080)
Reads Environment values
- identity_helper.exe (PID: 7608)
- r8p.exe (PID: 7332)
- identity_helper.exe (PID: 4672)
The sample compiled with english language support
- msedge.exe (PID: 3080)
- r8p.exe (PID: 7332)
- StartIsBackCfg.exe (PID: 2424)
- SIB10.exe (PID: 3000)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 7636)
- powershell.exe (PID: 6308)
- explorer.exe (PID: 1292)
Application launched itself
- msedge.exe (PID: 6364)
- msedge.exe (PID: 5632)
Create files in a temporary directory
- r8p.exe (PID: 7332)
- powershell.exe (PID: 6308)
- SIB10.exe (PID: 3000)
- StartIsBackCfg.exe (PID: 2424)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6308)
Reads the software policy settings
- powershell.exe (PID: 6308)
- UpdateCheck.exe (PID: 3124)
- WerFault.exe (PID: 5076)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6308)
- powershell.exe (PID: 5980)
The sample compiled with russian language support
- SIB10.exe (PID: 3000)
- StartIsBackCfg.exe (PID: 2424)
Process checks computer location settings
- SIB10.exe (PID: 3000)
- SearchApp.exe (PID: 7980)
Creates files in the program directory
- StartIsBackCfg.exe (PID: 2424)
- r8p.exe (PID: 7332)
Creates files or folders in the user directory
- explorer.exe (PID: 1292)
- ThemeSwitcher.exe (PID: 6380)
- WerFault.exe (PID: 5076)
Checks proxy server information
- explorer.exe (PID: 1292)
- SearchApp.exe (PID: 7980)
- WerFault.exe (PID: 5076)
Reads the machine GUID from the registry
- ThemeSwitcher.exe (PID: 6380)
- ViVeTool.exe (PID: 7756)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
278
Monitored processes
132
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 424 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=4832 --field-trial-handle=2336,i,2133342066911448129,17871025872968044048,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 524 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5428 --field-trial-handle=2336,i,2282725711073534892,2648164946067219329,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 644 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=1500 --field-trial-handle=2336,i,2282725711073534892,2648164946067219329,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 772 | "C:\Program Files (x86)\StartIsBack\StartScreen.exe" /purge | C:\Program Files (x86)\StartIsBack\StartScreen.exe | explorer.exe | ||||||||||||
User: admin Company: www.startisback.com Integrity Level: MEDIUM Description: StartIsBack Helper Tool Exit code: 0 Version: 5.9.8 Modules
| |||||||||||||||
| 836 | taskkill.exe /F /IM explorer* | C:\Windows\SysWOW64\taskkill.exe | — | StartIsBackCfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 848 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 1064 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6992 --field-trial-handle=2336,i,2282725711073534892,2648164946067219329,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1292 | "C:\WINDOWS\explorer.EXE" | C:\Windows\explorer.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1304 | schtasks /Delete /TN "ExplorerStart" /F | C:\Windows\SysWOW64\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
49 219
Read events
48 656
Write events
506
Delete events
57
Modification events
| (PID) Process: | (5464) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5464) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5464) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5464) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (5464) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (5464) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | DisableFirstRunCustomize |
Value: 1 | |||
| (PID) Process: | (6364) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6364) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6364) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6364) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
Executable files
182
Suspicious files
753
Text files
213
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6364 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF13596e.TMP | — | |
MD5:— | SHA256:— | |||
| 6364 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6364 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF13597d.TMP | — | |
MD5:— | SHA256:— | |||
| 6364 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6364 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF13597d.TMP | — | |
MD5:— | SHA256:— | |||
| 6364 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF13597d.TMP | — | |
MD5:— | SHA256:— | |||
| 6364 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6364 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6364 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF13597d.TMP | — | |
MD5:— | SHA256:— | |||
| 6364 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
60
TCP/UDP connections
63
DNS requests
73
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1738720099&P2=404&P3=2&P4=UCRaW4YNx3Lc4%2f7IfNdw2MkUHNajHVjkvIhINEojRdKkdPTZR4EoyYXjz62taLxWbsSPLTliN7%2fGU8ST8LaEeA%3d%3d | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2324 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2324 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6260 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7920 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1738720099&P2=404&P3=2&P4=UCRaW4YNx3Lc4%2f7IfNdw2MkUHNajHVjkvIhINEojRdKkdPTZR4EoyYXjz62taLxWbsSPLTliN7%2fGU8ST8LaEeA%3d%3d | unknown | — | — | whitelisted |
7920 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1738720099&P2=404&P3=2&P4=UCRaW4YNx3Lc4%2f7IfNdw2MkUHNajHVjkvIhINEojRdKkdPTZR4EoyYXjz62taLxWbsSPLTliN7%2fGU8ST8LaEeA%3d%3d | unknown | — | — | whitelisted |
7920 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1738720099&P2=404&P3=2&P4=UCRaW4YNx3Lc4%2f7IfNdw2MkUHNajHVjkvIhINEojRdKkdPTZR4EoyYXjz62taLxWbsSPLTliN7%2fGU8ST8LaEeA%3d%3d | unknown | — | — | whitelisted |
7920 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/e74ec02c-7f50-4b67-9a51-6cc67399bc04?P1=1738720101&P2=404&P3=2&P4=ZRqhjct6MAQsQDKEziOhfJQuLRoZ0odWb3Hio3Wz8kx0JubBEqUOUEbI5Poag23LQcSsgFRwaI4z9czlIqGyjg%3d%3d | unknown | — | — | whitelisted |
7920 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/e74ec02c-7f50-4b67-9a51-6cc67399bc04?P1=1738720101&P2=404&P3=2&P4=ZRqhjct6MAQsQDKEziOhfJQuLRoZ0odWb3Hio3Wz8kx0JubBEqUOUEbI5Poag23LQcSsgFRwaI4z9czlIqGyjg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6072 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6364 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6608 | msedge.exe | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
6608 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6608 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6608 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6608 | msedge.exe | 13.107.246.61:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6608 | msedge.exe | 2.19.126.145:443 | bzib.nelreports.net | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
objects.githubusercontent.com |
| shared |
go.microsoft.com |
| whitelisted |
edgeservices.bing.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
Threats
Process | Message |
|---|---|
explorer.exe | Purging StartIsBack cache directory |
StartScreen.exe | No HKCU installation to purge |
StartScreen.exe | Performing StartIsBack healthy purge |
explorer.exe | StartIsBack: forbiding XAML launcher to start |
explorer.exe | SIBActivation: mismatch; expected '' decrypted ' ' |