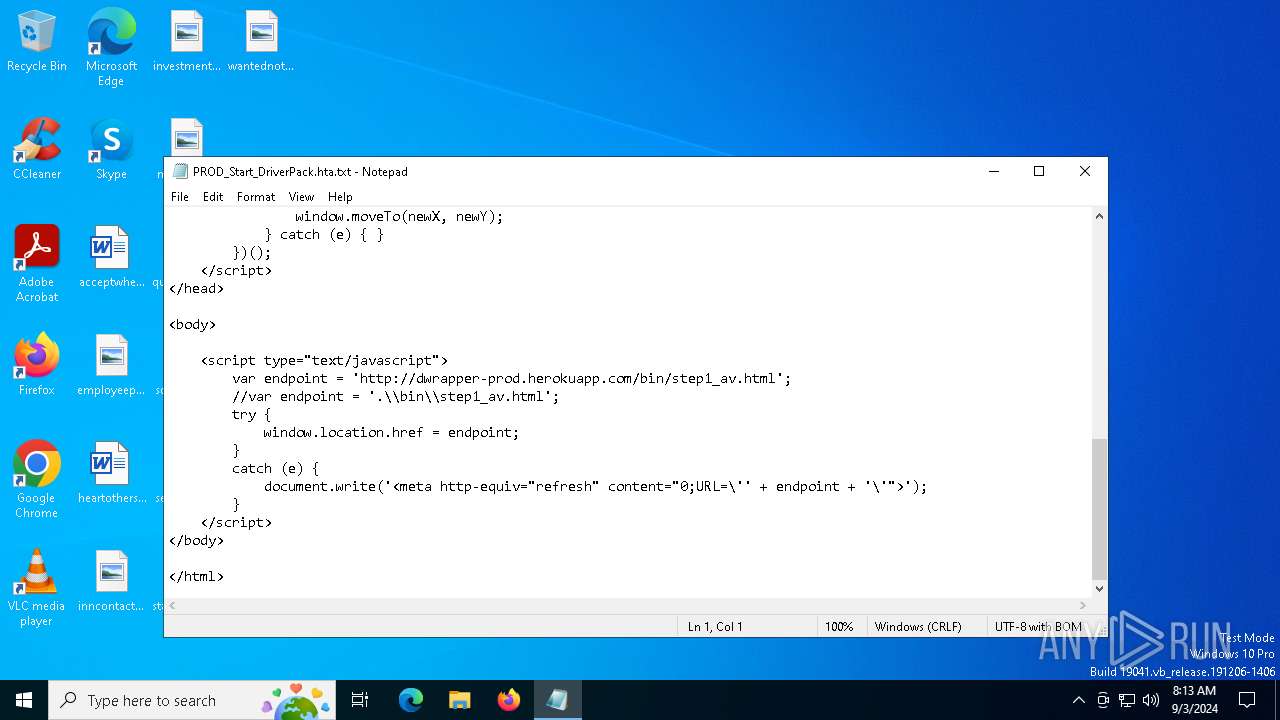
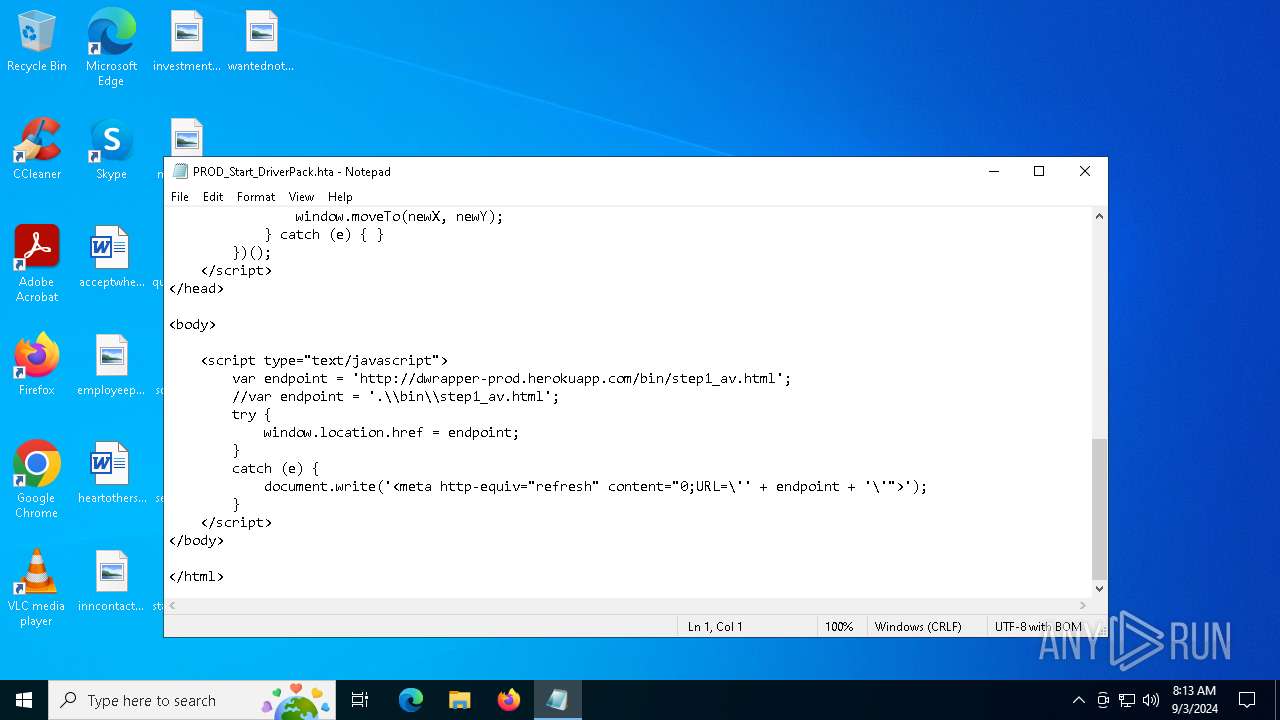
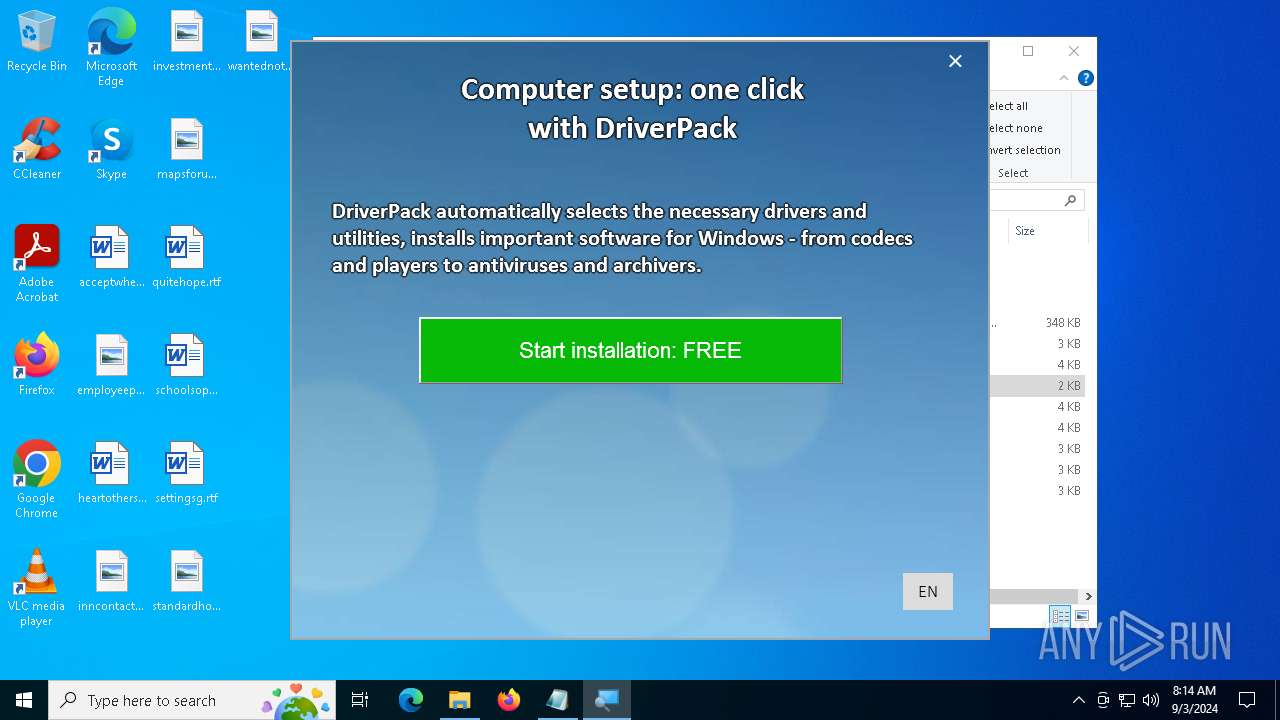
| File name: | PROD_Start_DriverPack.hta |
| Full analysis: | https://app.any.run/tasks/a0182b4b-a71d-4098-913f-52ec4f21d5a2 |
| Verdict: | Malicious activity |
| Analysis date: | September 03, 2024, 08:13:15 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, Unicode text, UTF-8 (with BOM) text, with CRLF line terminators |
| MD5: | DDA846A4704EFC2A03E1F8392E6F1FFC |
| SHA1: | 387171A06EEE5A76AAEDC3664385BB89703CF6DF |
| SHA256: | E9DC9648D8FB7D943431459F49A7D9926197C2D60B3C2B6A58294FD75B672B25 |
| SSDEEP: | 48:uzK1vpKljUYpuqgs1pxXzOSRByHCpmF50bxxdW6kI:qiIT3BjNOSOGmF50tKA |
MALICIOUS
Scans artifacts that could help determine the target
- mshta.exe (PID: 236)
Downloads files via BITSADMIN.EXE
- cmd.exe (PID: 7024)
SUSPICIOUS
Query Microsoft Defender status
- cmd.exe (PID: 448)
- mshta.exe (PID: 236)
Found strings related to reading or modifying Windows Defender settings
- mshta.exe (PID: 236)
Process requests binary or script from the Internet
- mshta.exe (PID: 236)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7024)
- cmd.exe (PID: 2324)
- cmd.exe (PID: 3852)
- cmd.exe (PID: 6280)
- cmd.exe (PID: 6336)
- cmd.exe (PID: 5104)
- cmd.exe (PID: 1116)
- cmd.exe (PID: 1164)
- cmd.exe (PID: 6016)
- cmd.exe (PID: 1712)
- cmd.exe (PID: 5064)
- cmd.exe (PID: 5040)
- cmd.exe (PID: 1640)
- cmd.exe (PID: 6384)
- cmd.exe (PID: 1184)
- cmd.exe (PID: 2128)
- cmd.exe (PID: 6432)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 448)
Cmdlet gets the status of antimalware software installed on the computer
- cmd.exe (PID: 448)
Starts CMD.EXE for commands execution
- mshta.exe (PID: 236)
The process verifies whether the antivirus software is installed
- mshta.exe (PID: 236)
INFO
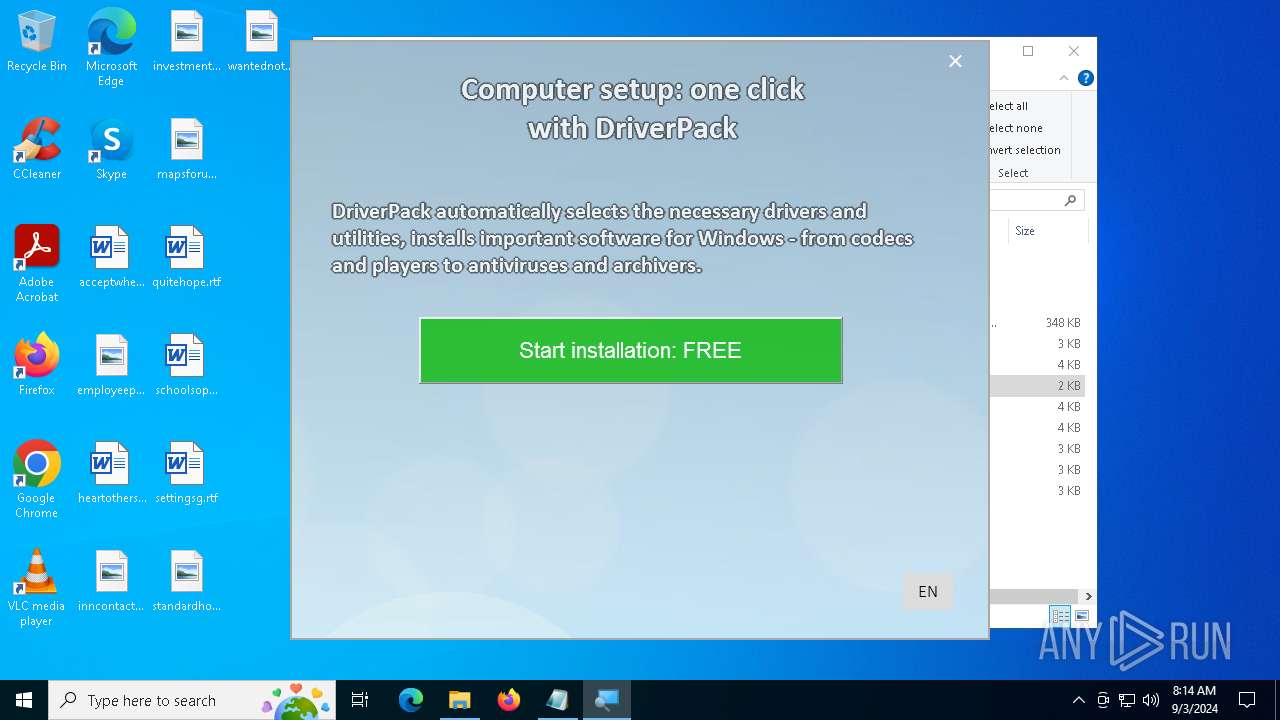
Manual execution by a user
- mshta.exe (PID: 236)
Reads security settings of Internet Explorer
- notepad.exe (PID: 420)
Checks proxy server information
- mshta.exe (PID: 236)
Reads Internet Explorer settings
- mshta.exe (PID: 236)
Uses BITSADMIN.EXE
- cmd.exe (PID: 2324)
- cmd.exe (PID: 3852)
- cmd.exe (PID: 6336)
- cmd.exe (PID: 6280)
- cmd.exe (PID: 5104)
- cmd.exe (PID: 5064)
- cmd.exe (PID: 1164)
- cmd.exe (PID: 1116)
- cmd.exe (PID: 6016)
- cmd.exe (PID: 1712)
- cmd.exe (PID: 6432)
- cmd.exe (PID: 5040)
- cmd.exe (PID: 6384)
- cmd.exe (PID: 1640)
- cmd.exe (PID: 1184)
- cmd.exe (PID: 2128)
The process uses the downloaded file
- mshta.exe (PID: 236)
- powershell.exe (PID: 6376)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6376)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-8 encoded (100) |
|---|
EXIF
HTML
| Title: | Starting... |
|---|---|
| HTTPEquivXUACompatible: | IE=7 |
Total processes
212
Monitored processes
91
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Windows\SysWOW64\mshta.exe" "C:\Users\admin\Documents\PROD_Start_DriverPack.hta" {1E460BD7-F1C3-4B2E-88BF-4E770A288AF5}{1E460BD7-F1C3-4B2E-88BF-4E770A288AF5} | C:\Windows\SysWOW64\mshta.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 420 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\PROD_Start_DriverPack.hta.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 448 | "C:\Windows\System32\cmd.exe" /c powershell Get-MpComputerStatus > "C:\Users\admin\AppData\Local\Temp\dwnl_30420\log_defenderVersionPowershell.txt" | C:\Windows\SysWOW64\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 568 | findstr /V /C:"BITSADMIN version" /C:"BITS administration" /C:"(C) Copyright" /C:"BITSAdmin is deprecated" /C:"Administrative tools" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | findstr /R /V "^f7f81a39-5f63-5b42-9efd-1f13b5431005quot; | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1084 | findstr /V /C:"BITSADMIN version" /C:"BITS administration" /C:"(C) Copyright" /C:"BITSAdmin is deprecated" /C:"Administrative tools" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | "C:\Windows\System32\cmd.exe" /c bitsadmin /info dwnl-task-30420 | findstr /V /C:"BITSADMIN version" /C:"BITS administration" /C:"(C) Copyright" /C:"BITSAdmin is deprecated" /C:"Administrative tools" | findstr /R /V "^f7f81a39-5f63-5b42-9efd-1f13b5431005quot; > "C:\Users\admin\AppData\Local\Temp\dwnl_30420\log_bits_info.txt" | C:\Windows\SysWOW64\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1148 | findstr /V /C:"BITSADMIN version" /C:"BITS administration" /C:"(C) Copyright" /C:"BITSAdmin is deprecated" /C:"Administrative tools" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | "C:\Windows\System32\cmd.exe" /c bitsadmin /info dwnl-task-30420 | findstr /V /C:"BITSADMIN version" /C:"BITS administration" /C:"(C) Copyright" /C:"BITSAdmin is deprecated" /C:"Administrative tools" | findstr /R /V "^f7f81a39-5f63-5b42-9efd-1f13b5431005quot; > "C:\Users\admin\AppData\Local\Temp\dwnl_30420\log_bits_info.txt" | C:\Windows\SysWOW64\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | "C:\Windows\System32\cmd.exe" /c bitsadmin /info dwnl-task-30420 | findstr /V /C:"BITSADMIN version" /C:"BITS administration" /C:"(C) Copyright" /C:"BITSAdmin is deprecated" /C:"Administrative tools" | findstr /R /V "^f7f81a39-5f63-5b42-9efd-1f13b5431005quot; > "C:\Users\admin\AppData\Local\Temp\dwnl_30420\log_bits_info.txt" | C:\Windows\SysWOW64\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
22 247
Read events
22 165
Write events
78
Delete events
4
Modification events
| (PID) Process: | (420) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (420) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0400000000000000030000000E0000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (420) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 040000000000000005000000020000000100000003000000FFFFFFFF | |||
| (PID) Process: | (420) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Documents | |||
| (PID) Process: | (420) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 93 | |||
| (PID) Process: | (420) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 3BC5D66600000000 | |||
| (PID) Process: | (420) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (420) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (420) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (420) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
1
Text files
47
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 236 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\3[1].js | text | |
MD5:CC9E168614A8D567352E24F970CA21E0 | SHA256:578820B83CD0244FFC068665C531A8C7D633F890A927A682A1708B84B7A08702 | |||
| 236 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\client_ip[1].js | text | |
MD5:24D1F2CFBC8884A75CDE629904E25A89 | SHA256:A5173EFFF9E3C5B7DF3DA89A3ED1EDFBD34F16F9C3DACF4804FAF0FCB85B935B | |||
| 236 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\missing-scripts-detector[1].js | text | |
MD5:5BB70933199563BD95A85E9D58D0920B | SHA256:915A03DDD5D887CE43185A21FD9927FFCFC6E8F373D80D6FB0BFE96E65C029CD | |||
| 420 | notepad.exe | C:\Users\admin\Documents\PROD_Start_DriverPack.hta | html | |
MD5:DDA846A4704EFC2A03E1F8392E6F1FFC | SHA256:E9DC9648D8FB7D943431459F49A7D9926197C2D60B3C2B6A58294FD75B672B25 | |||
| 236 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\4[1].js | text | |
MD5:B21247B2428E6D9F72405EB1A2F5F75C | SHA256:9DDF298484BD63F71CFF04DD81E00913266FA8D71793E2C26F3B7B215067812C | |||
| 236 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\style[1].css | text | |
MD5:CE40483E494B033AA4A204080ABB54DA | SHA256:1FC4501622BAFC4560C28442D01F708579F26AFBB88229328B2CE7E83A2D36A8 | |||
| 236 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\matomo[1].htm | text | |
MD5:51C8E2EC2D4A042736B88F1BE1BE5B7E | SHA256:481BEEA6F83C5C784276DF3BFB8693CC60C0CE8EF0A2CB8F47D624E2D6C9B076 | |||
| 236 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\matomo[1].htm | text | |
MD5:51C8E2EC2D4A042736B88F1BE1BE5B7E | SHA256:481BEEA6F83C5C784276DF3BFB8693CC60C0CE8EF0A2CB8F47D624E2D6C9B076 | |||
| 236 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\style[1].css | text | |
MD5:CE40483E494B033AA4A204080ABB54DA | SHA256:1FC4501622BAFC4560C28442D01F708579F26AFBB88229328B2CE7E83A2D36A8 | |||
| 236 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\lang[1].js | html | |
MD5:3B196A2A5E0875A186EFA1A6101B775D | SHA256:B6EF0302FB7FE71577D6B6AFE104B4C890FC6419FB9A9C4EC359A0CC25EA8885 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
42
TCP/UDP connections
26
DNS requests
14
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3296 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
236 | mshta.exe | GET | 200 | 46.137.15.86:80 | http://dwrapper-prod.herokuapp.com/bin/step1_av.html | unknown | — | — | whitelisted |
4444 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
236 | mshta.exe | GET | 200 | 46.137.15.86:80 | http://dwrapper-prod.herokuapp.com/bin/src/missing-scripts-detector.js | unknown | — | — | whitelisted |
4444 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
236 | mshta.exe | GET | 200 | 46.137.15.86:80 | http://dwrapper-prod.herokuapp.com/bin/src/style.css | unknown | — | — | whitelisted |
236 | mshta.exe | GET | 200 | 46.137.15.86:80 | http://dwrapper-prod.herokuapp.com/client_ip.js | unknown | — | — | whitelisted |
236 | mshta.exe | GET | 200 | 46.137.15.86:80 | http://dwrapper-prod.herokuapp.com/bin/src/variables/1.js | unknown | — | — | whitelisted |
236 | mshta.exe | GET | 200 | 46.137.15.86:80 | http://dwrapper-prod.herokuapp.com/bin/src/variables/3.js | unknown | — | — | whitelisted |
236 | mshta.exe | GET | 200 | 46.137.15.86:80 | http://dwrapper-prod.herokuapp.com/bin/src/variables/2.js | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6440 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3296 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3296 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4444 | SIHClient.exe | 40.127.169.103:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4444 | SIHClient.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
dwrapper-prod.herokuapp.com |
| whitelisted |
exampledd.matomo.cloud |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
236 | mshta.exe | A Network Trojan was detected | SUSPICIOUS [ANY.RUN] VBS is used to run Shell |
236 | mshta.exe | A Network Trojan was detected | SUSPICIOUS [ANY.RUN] VBS is used to run Shell |
236 | mshta.exe | Potentially Bad Traffic | ET HUNTING PowerShell DownloadFile Command Common In Powershell Stagers |
5 ETPRO signatures available at the full report