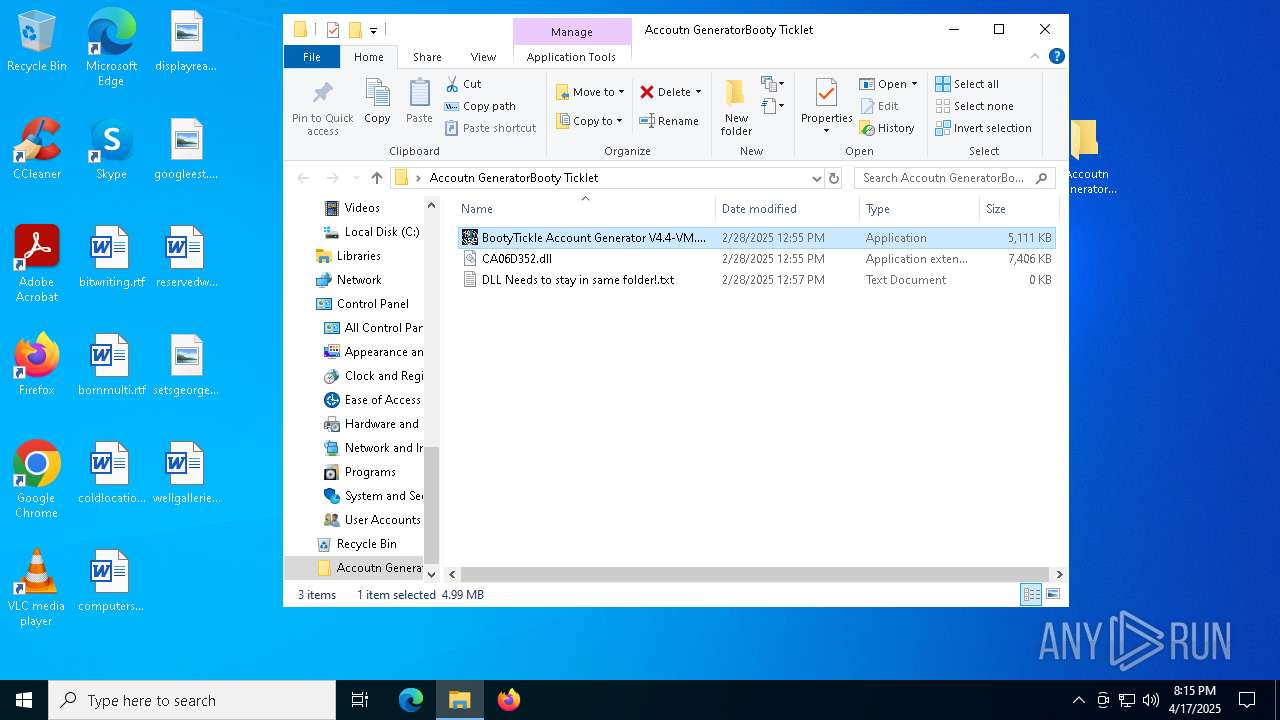
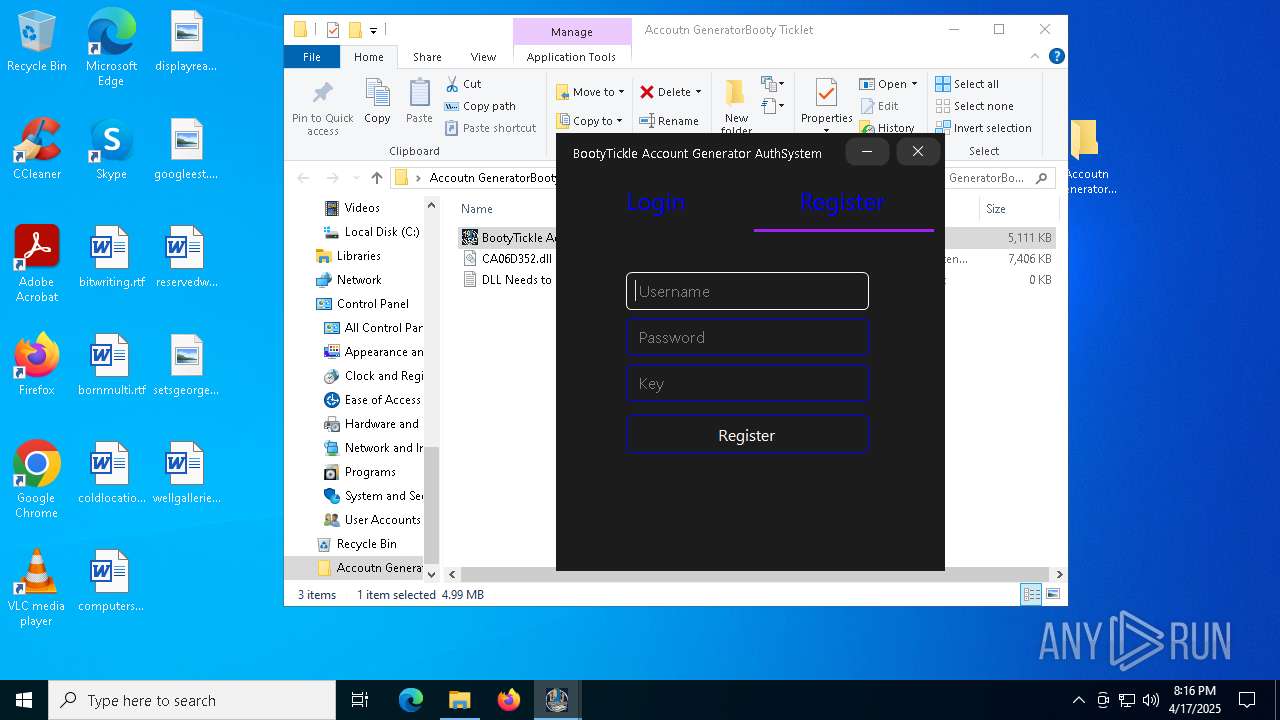
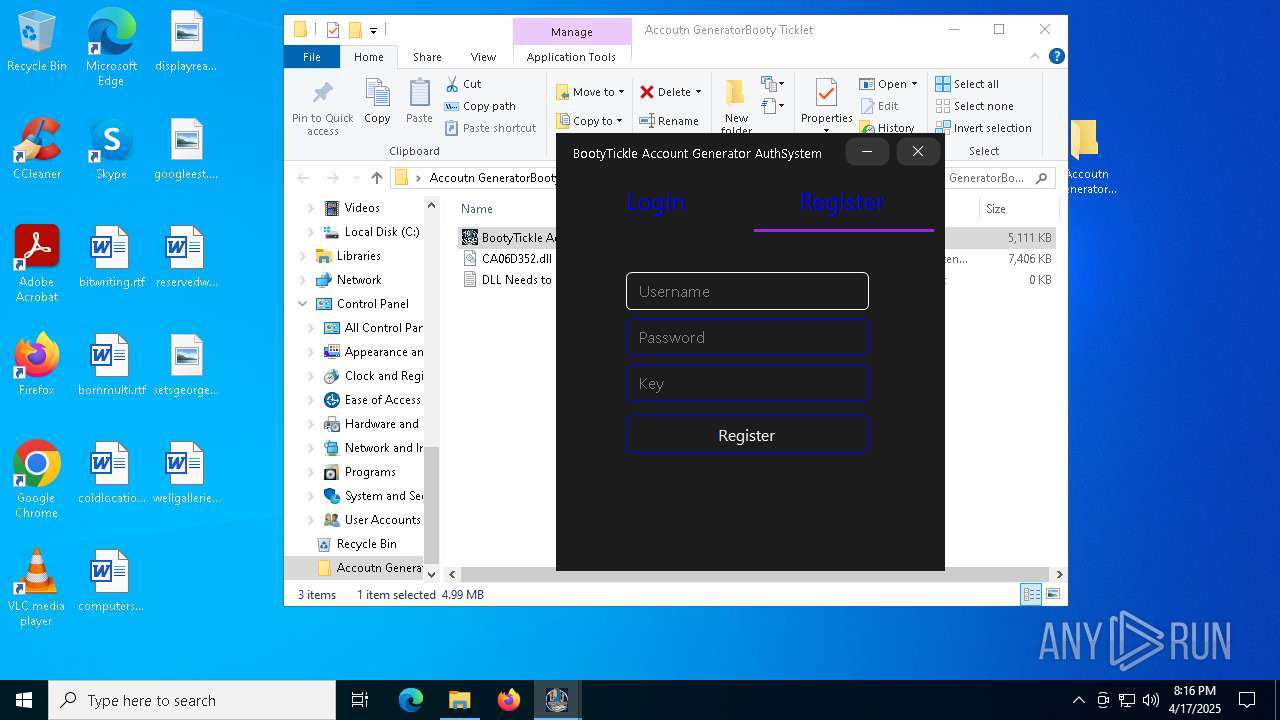
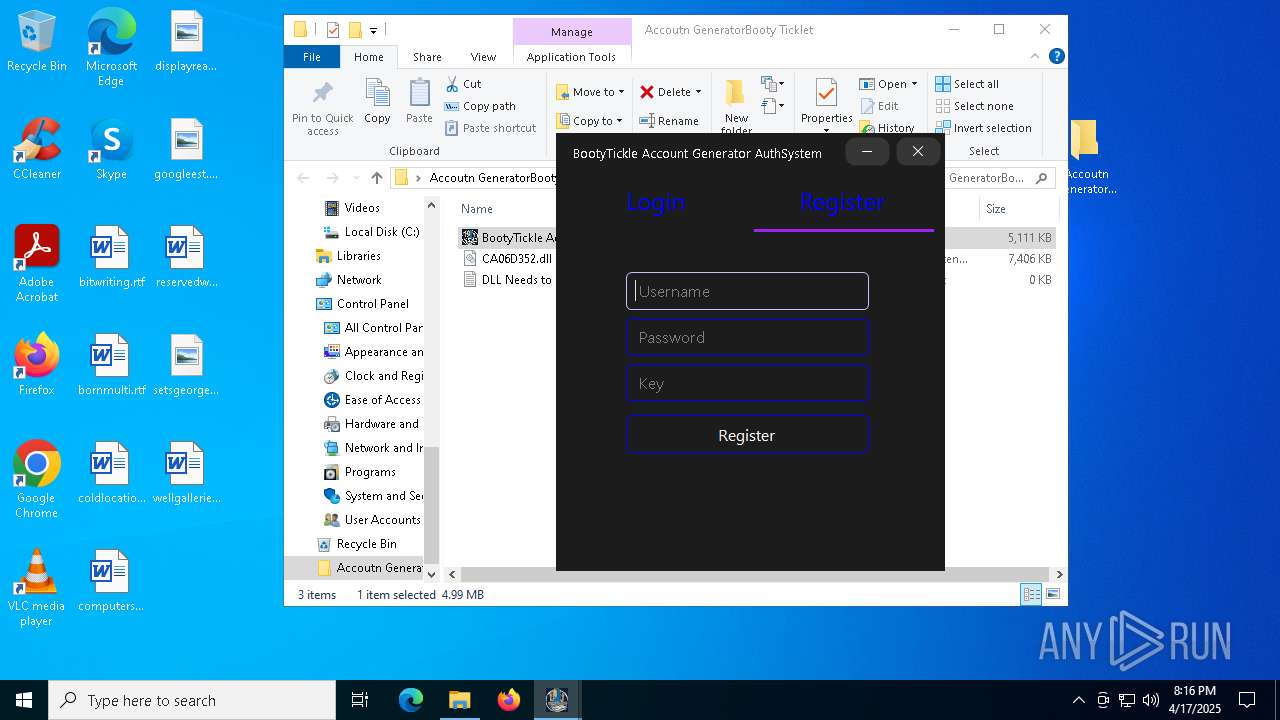
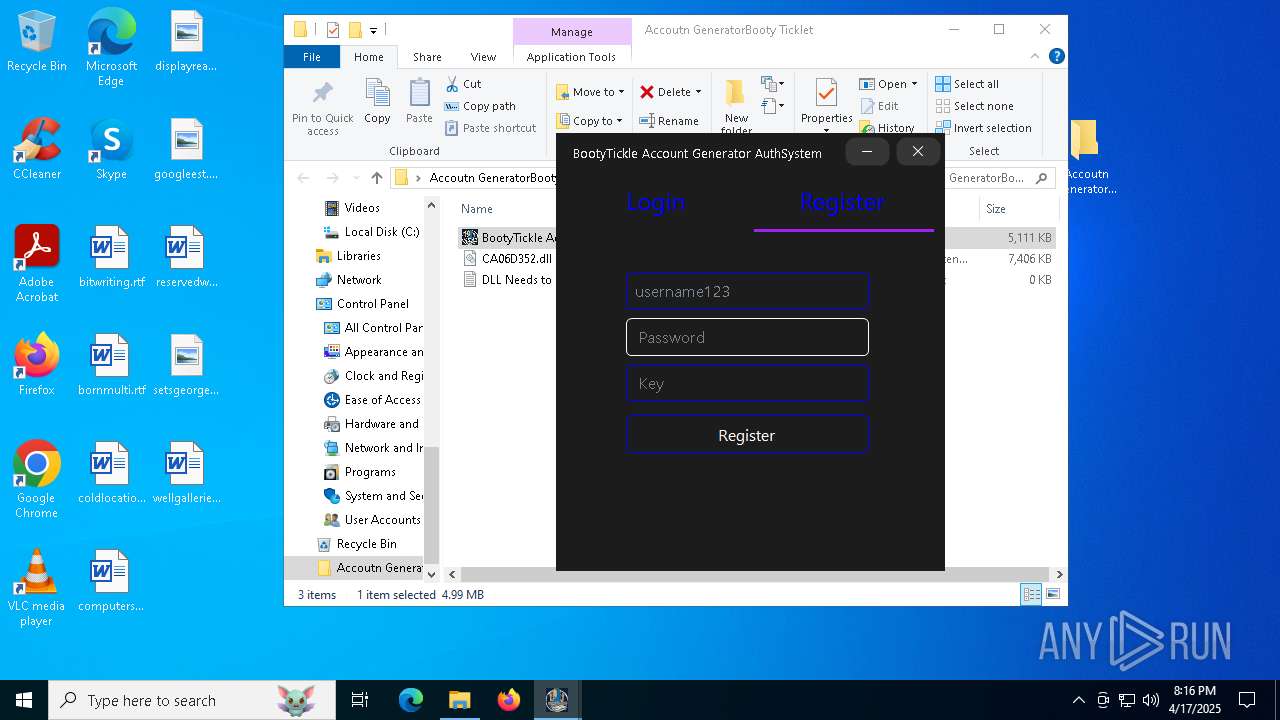
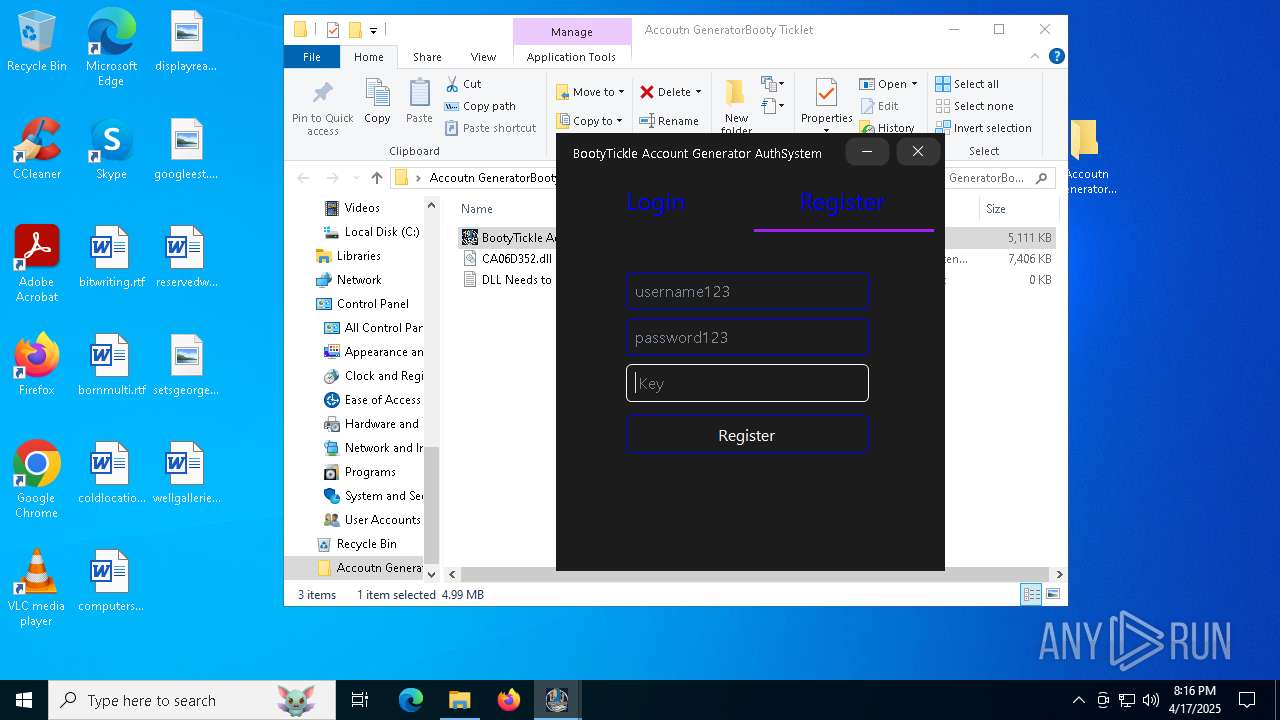
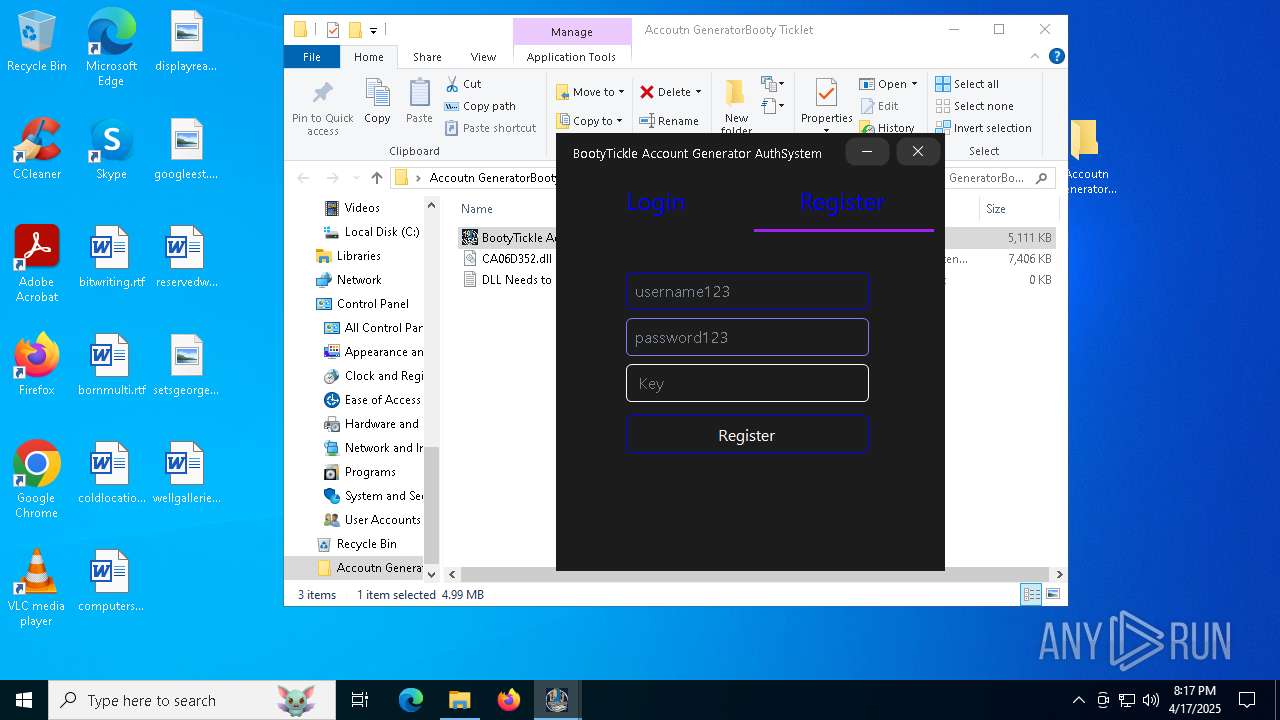
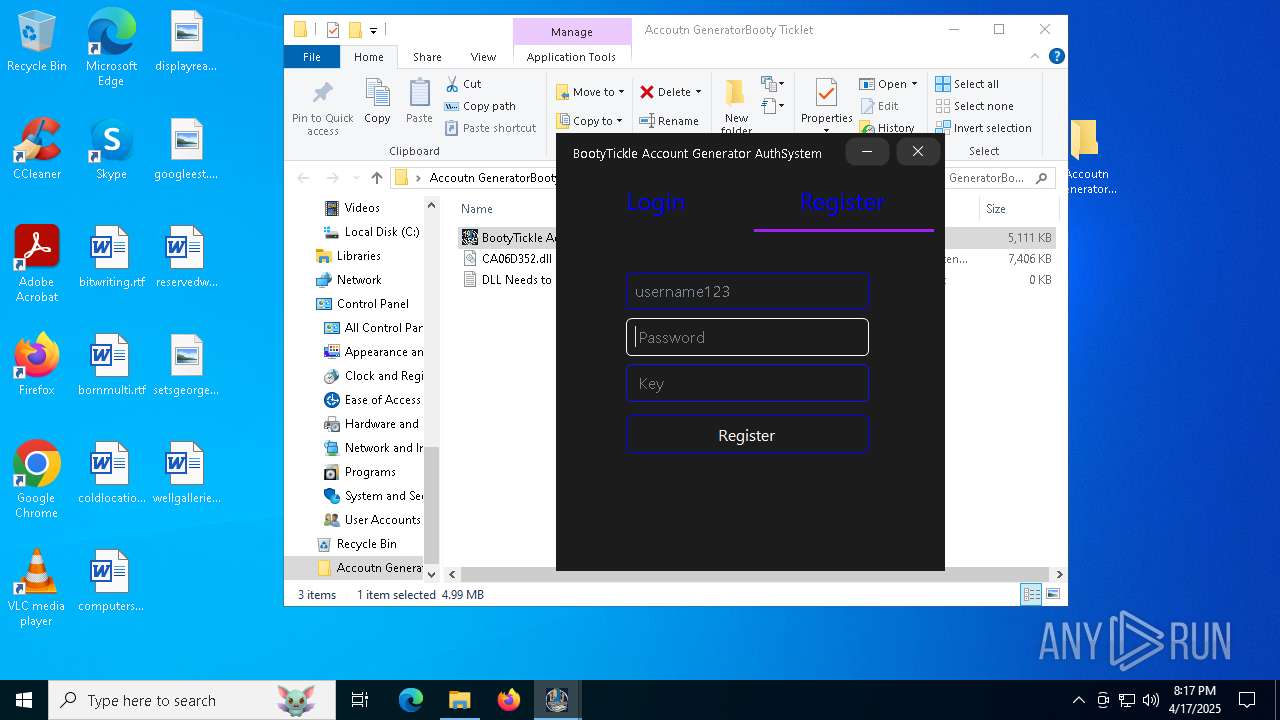
| File name: | Accoutn GeneratorBooty Ticklet.rar |
| Full analysis: | https://app.any.run/tasks/12980177-7809-4cba-bf5b-f57618b53891 |
| Verdict: | Malicious activity |
| Analysis date: | April 17, 2025, 20:13:49 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 2D9CC5E1D9F9B48645189E664B5F3C73 |
| SHA1: | B0D013EDFBAC23205E8502921D45C54ACAD89AC0 |
| SHA256: | E9DC12CEBAA917571CD72741C4702B6490BDC10BC164D424BBF71C53EF37C234 |
| SSDEEP: | 98304:oclDJ8i7+NsH90CrhhaG+TVd8xbxxn7Z2CTqO6A2eiG75WYRDAmaAHz/s7NoBQR1:x84QSKOXHL8eptqCoT1 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the BIOS version
- BootyTickle Account Generator V4.4-VM.exe (PID: 7984)
- BootyTickle Account Generator V4.4-VM.exe (PID: 5048)
- BootyTickle Account Generator V4.4-VM.exe (PID: 5204)
- BootyTickle Account Generator V4.4-VM.exe (PID: 664)
- BootyTickle Account Generator V4.4-VM.exe (PID: 7380)
The process checks if it is being run in the virtual environment
- BootyTickle Account Generator V4.4-VM.exe (PID: 7984)
- BootyTickle Account Generator V4.4-VM.exe (PID: 5048)
- BootyTickle Account Generator V4.4-VM.exe (PID: 5204)
- BootyTickle Account Generator V4.4-VM.exe (PID: 664)
- BootyTickle Account Generator V4.4-VM.exe (PID: 7380)
Read disk information to detect sandboxing environments
- BootyTickle Account Generator V4.4-VM.exe (PID: 7984)
- BootyTickle Account Generator V4.4-VM.exe (PID: 5048)
- BootyTickle Account Generator V4.4-VM.exe (PID: 5204)
- BootyTickle Account Generator V4.4-VM.exe (PID: 664)
- BootyTickle Account Generator V4.4-VM.exe (PID: 7380)
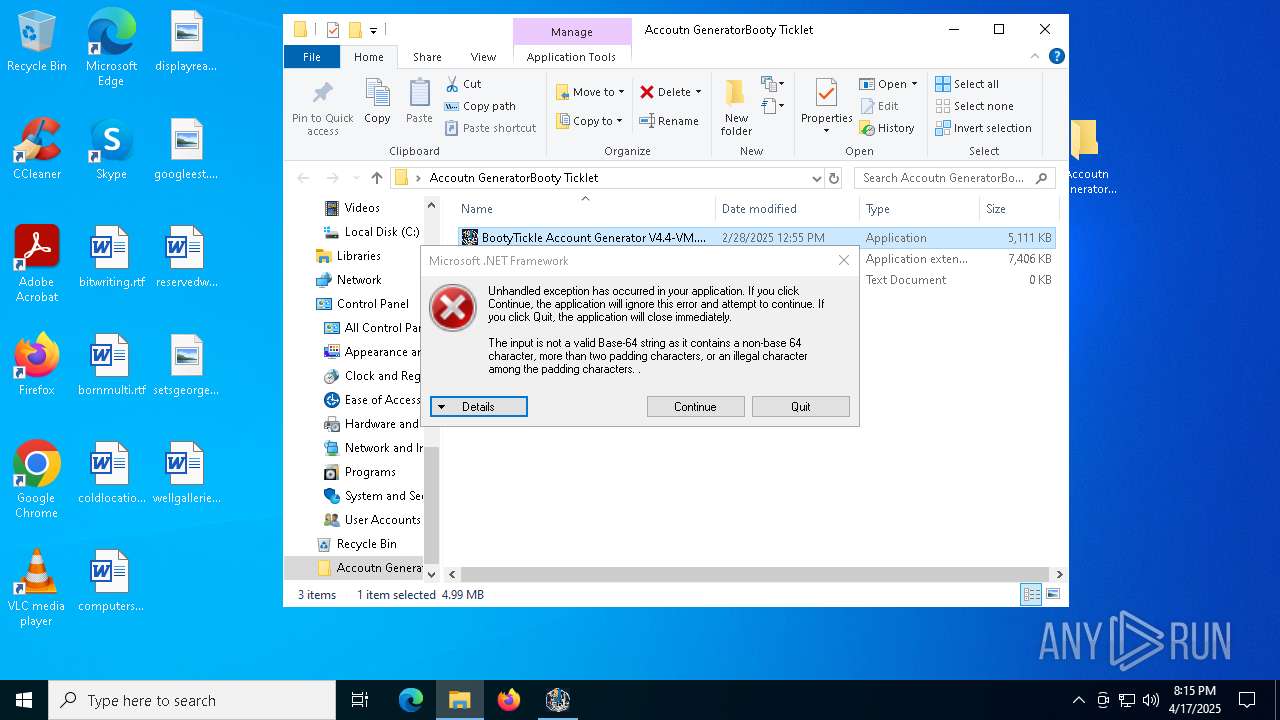
Executes application which crashes
- BootyTickle Account Generator V4.4-VM.exe (PID: 7984)
- BootyTickle Account Generator V4.4-VM.exe (PID: 5048)
There is functionality for taking screenshot (YARA)
- BootyTickle Account Generator V4.4-VM.exe (PID: 664)
- BootyTickle Account Generator V4.4-VM.exe (PID: 7380)
INFO
Manual execution by a user
- BootyTickle Account Generator V4.4-VM.exe (PID: 7984)
- BootyTickle Account Generator V4.4-VM.exe (PID: 5048)
- BootyTickle Account Generator V4.4-VM.exe (PID: 664)
- BootyTickle Account Generator V4.4-VM.exe (PID: 5204)
- BootyTickle Account Generator V4.4-VM.exe (PID: 7380)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7216)
Reads the computer name
- BootyTickle Account Generator V4.4-VM.exe (PID: 7984)
- BootyTickle Account Generator V4.4-VM.exe (PID: 5048)
- BootyTickle Account Generator V4.4-VM.exe (PID: 5204)
- BootyTickle Account Generator V4.4-VM.exe (PID: 664)
- BootyTickle Account Generator V4.4-VM.exe (PID: 7380)
Checks supported languages
- BootyTickle Account Generator V4.4-VM.exe (PID: 7984)
- BootyTickle Account Generator V4.4-VM.exe (PID: 5048)
- BootyTickle Account Generator V4.4-VM.exe (PID: 5204)
- BootyTickle Account Generator V4.4-VM.exe (PID: 664)
- BootyTickle Account Generator V4.4-VM.exe (PID: 7380)
Reads the machine GUID from the registry
- BootyTickle Account Generator V4.4-VM.exe (PID: 7984)
- BootyTickle Account Generator V4.4-VM.exe (PID: 5048)
- BootyTickle Account Generator V4.4-VM.exe (PID: 5204)
- BootyTickle Account Generator V4.4-VM.exe (PID: 664)
- BootyTickle Account Generator V4.4-VM.exe (PID: 7380)
Creates files or folders in the user directory
- WerFault.exe (PID: 8124)
- WerFault.exe (PID: 5892)
Disables trace logs
- BootyTickle Account Generator V4.4-VM.exe (PID: 664)
Checks proxy server information
- BootyTickle Account Generator V4.4-VM.exe (PID: 664)
- slui.exe (PID: 6148)
Reads the software policy settings
- slui.exe (PID: 6148)
- BootyTickle Account Generator V4.4-VM.exe (PID: 664)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 4936073 |
| UncompressedSize: | 5233152 |
| OperatingSystem: | Win32 |
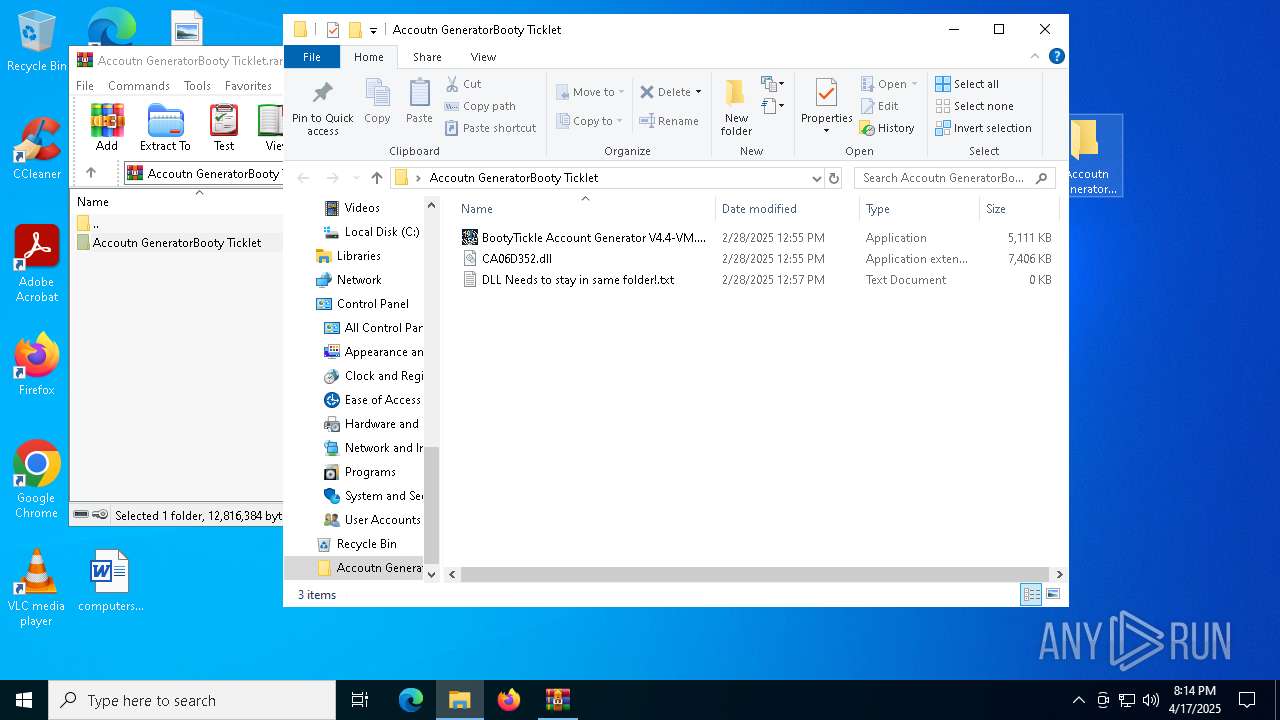
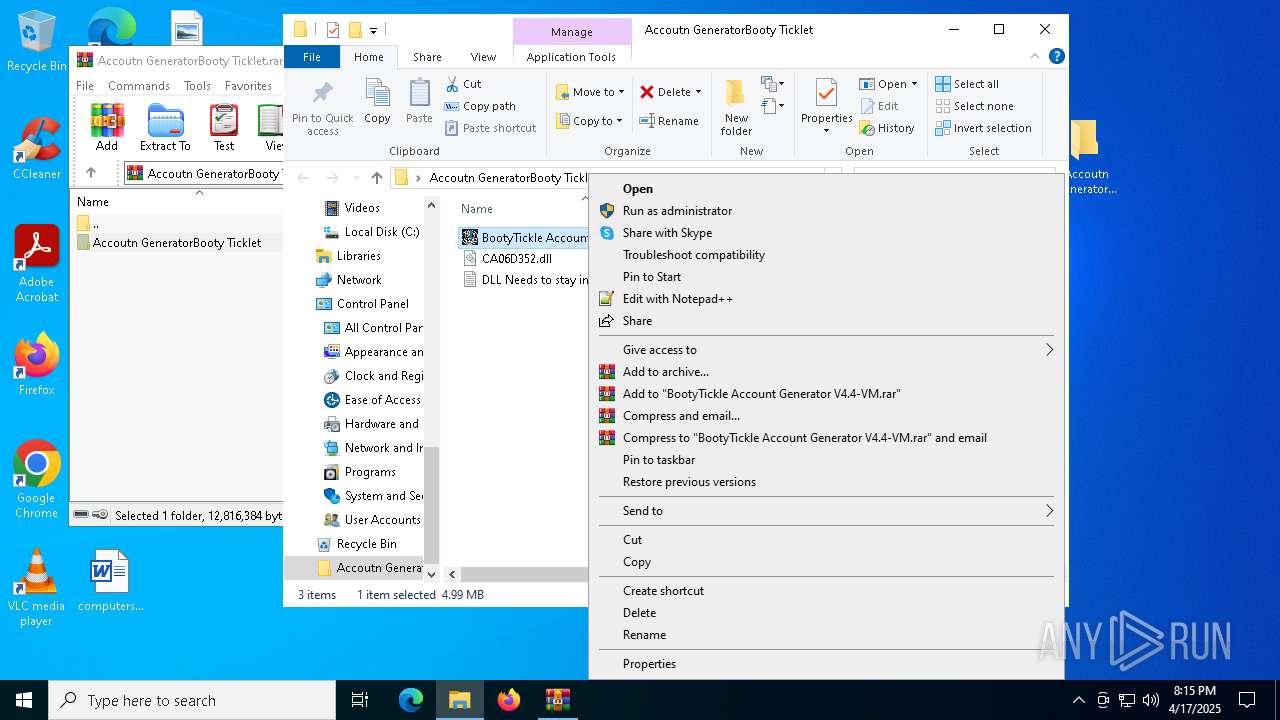
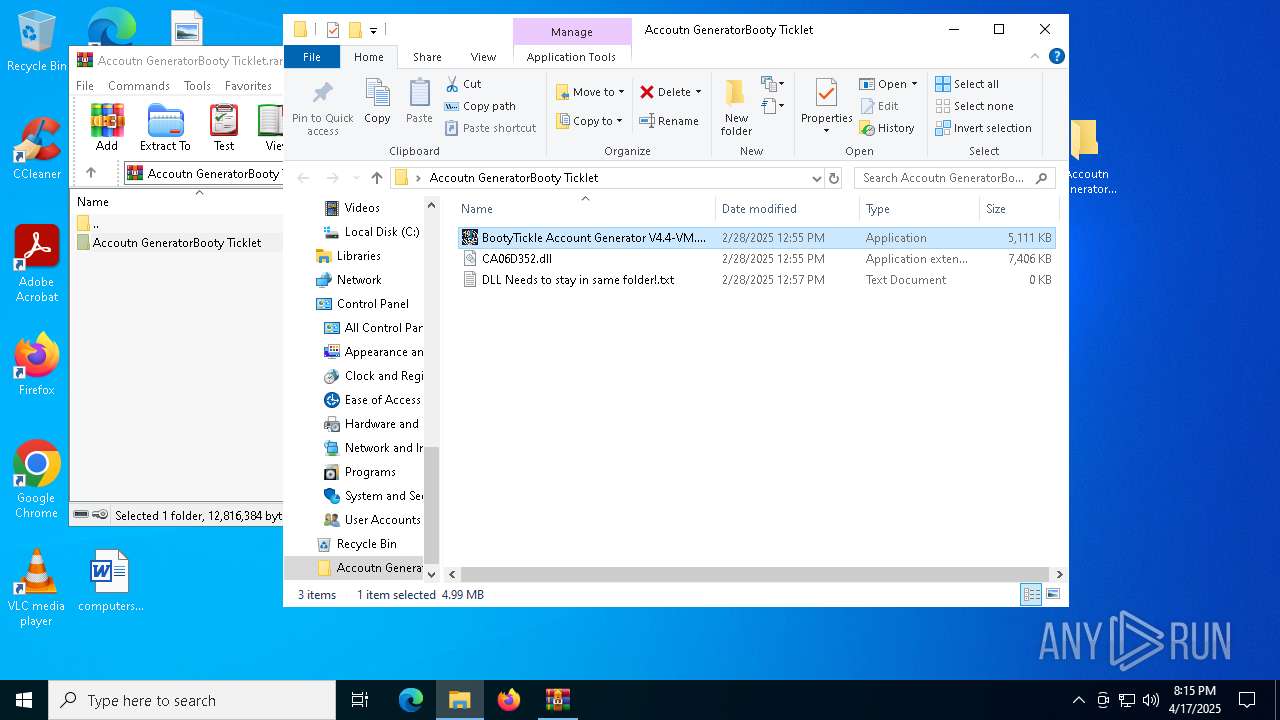
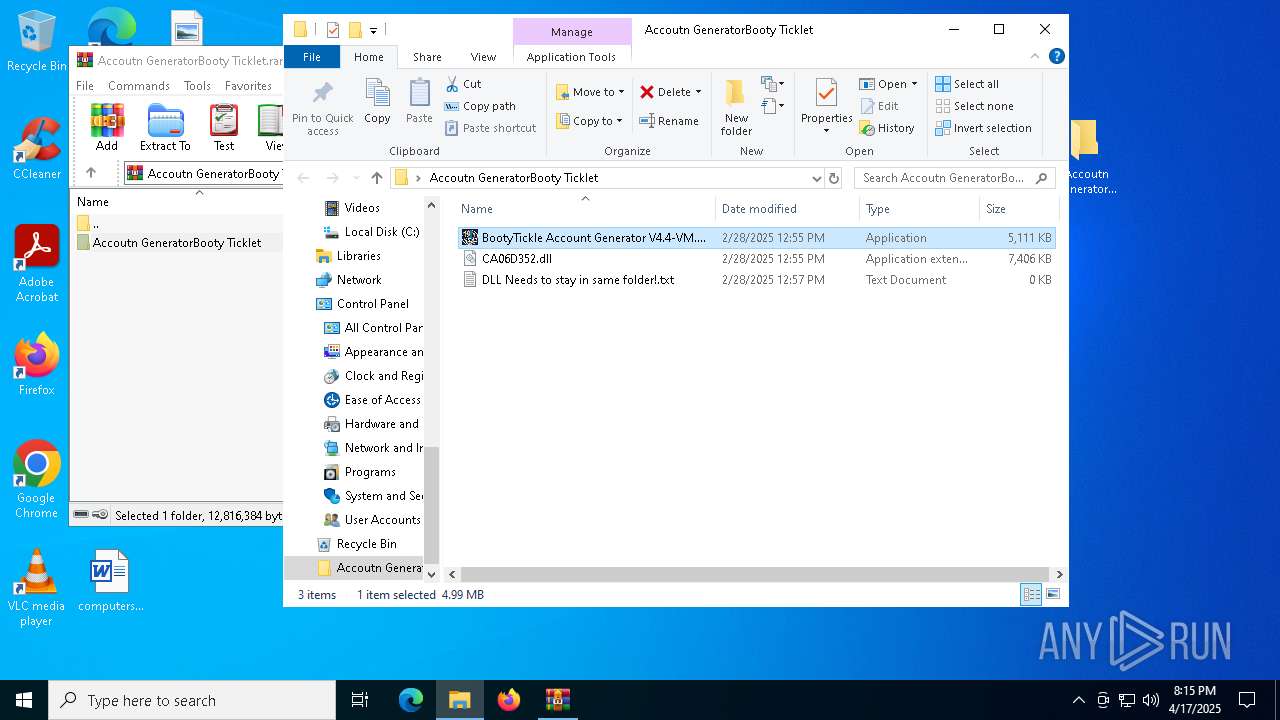
| ArchivedFileName: | Accoutn GeneratorBooty Ticklet/BootyTickle Account Generator V4.4-VM.exe |
Total processes
148
Monitored processes
11
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | "C:\Users\admin\Desktop\Accoutn GeneratorBooty Ticklet\BootyTickle Account Generator V4.4-VM.exe" | C:\Users\admin\Desktop\Accoutn GeneratorBooty Ticklet\BootyTickle Account Generator V4.4-VM.exe | explorer.exe | ||||||||||||
User: admin Company: Arxvestiys Service Integrity Level: MEDIUM Description: Account Generator V4.4 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5048 | "C:\Users\admin\Desktop\Accoutn GeneratorBooty Ticklet\BootyTickle Account Generator V4.4-VM.exe" | C:\Users\admin\Desktop\Accoutn GeneratorBooty Ticklet\BootyTickle Account Generator V4.4-VM.exe | explorer.exe | ||||||||||||
User: admin Company: Arxvestiys Service Integrity Level: MEDIUM Description: Account Generator V4.4 Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 5204 | "C:\Users\admin\Desktop\Accoutn GeneratorBooty Ticklet\BootyTickle Account Generator V4.4-VM.exe" | C:\Users\admin\Desktop\Accoutn GeneratorBooty Ticklet\BootyTickle Account Generator V4.4-VM.exe | — | explorer.exe | |||||||||||
User: admin Company: Arxvestiys Service Integrity Level: MEDIUM Description: Account Generator V4.4 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 5892 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 5048 -s 6608 | C:\Windows\SysWOW64\WerFault.exe | — | BootyTickle Account Generator V4.4-VM.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6148 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7216 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Accoutn GeneratorBooty Ticklet.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7380 | "C:\Users\admin\Desktop\Accoutn GeneratorBooty Ticklet\BootyTickle Account Generator V4.4-VM.exe" | C:\Users\admin\Desktop\Accoutn GeneratorBooty Ticklet\BootyTickle Account Generator V4.4-VM.exe | — | explorer.exe | |||||||||||
User: admin Company: Arxvestiys Service Integrity Level: MEDIUM Description: Account Generator V4.4 Version: 1.0.0.0 Modules
| |||||||||||||||
| 7932 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7984 | "C:\Users\admin\Desktop\Accoutn GeneratorBooty Ticklet\BootyTickle Account Generator V4.4-VM.exe" | C:\Users\admin\Desktop\Accoutn GeneratorBooty Ticklet\BootyTickle Account Generator V4.4-VM.exe | explorer.exe | ||||||||||||
User: admin Company: Arxvestiys Service Integrity Level: MEDIUM Description: Account Generator V4.4 Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
9 629
Read events
9 597
Write events
32
Delete events
0
Modification events
| (PID) Process: | (7216) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7216) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7216) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7216) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Accoutn GeneratorBooty Ticklet.rar | |||
| (PID) Process: | (7216) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7216) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7216) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7216) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7216) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (7216) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
2
Suspicious files
4
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 8124 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_QEI3OC35JESVXQAB_3e961deb232a41dcd97918c14a42c2560914144_399df6ad_5978400f-e12e-4465-b62c-9d3206c324ed\Report.wer | — | |
MD5:— | SHA256:— | |||
| 8124 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\BootyTickle Account Generator V4.4-VM.exe.7984.dmp | — | |
MD5:— | SHA256:— | |||
| 5892 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_QEI3OC35JESVXQAB_3e961deb232a41dcd97918c14a42c2560914144_399df6ad_996a070d-36e3-43eb-bb87-351a6bd17a95\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5892 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\BootyTickle Account Generator V4.4-VM.exe.5048.dmp | — | |
MD5:— | SHA256:— | |||
| 8124 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER53BA.tmp.dmp | binary | |
MD5:742C3EF573990E3CF363FE1D9E674E71 | SHA256:9AFFFF3A90CF769F58570F731BB5B3D5262E128B6DB4F795828EC6504FD8B674 | |||
| 5892 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERF8B5.tmp.dmp | binary | |
MD5:E1A7F4A6AFABE58F674E3AE2FE5DE50F | SHA256:FC5B0A051623AFF3FE248E98D7C83C888CDB6BFF047B111DAFCEFBEF4D4FA35E | |||
| 8124 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER561E.tmp.xml | xml | |
MD5:92CFE2B20C358B849A845FBCBD07F3B4 | SHA256:3141B40F30BFC00D70BE3A58887C9A452968E628F626AC2B30F02E43A1F1A645 | |||
| 8124 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER55DE.tmp.WERInternalMetadata.xml | binary | |
MD5:BF00EACC0D180C93AC40149276D3617E | SHA256:6DF99F06C0C380CD8DA7A55014AF1C04AA75C20F24CDDBEBA9C42905174CF68A | |||
| 7216 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7216.17663\Accoutn GeneratorBooty Ticklet\BootyTickle Account Generator V4.4-VM.exe | executable | |
MD5:A115B6BE0F1C126AB9BD0C189FA27D92 | SHA256:BC24B6C62CFF50172D2F81C72CEAF27E82D2A764EAE7E9618E35582770C1C73D | |||
| 7216 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7216.17663\Accoutn GeneratorBooty Ticklet\CA06D352.dll | executable | |
MD5:92B3B4A2E337FD9A51F604DBF43A94F2 | SHA256:8C3E7B19782A8C96A357B47C0AC432BA592BC30A69A593BD75622E71E73A165B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
34
DNS requests
20
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.29:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7740 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7740 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.216.77.29:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
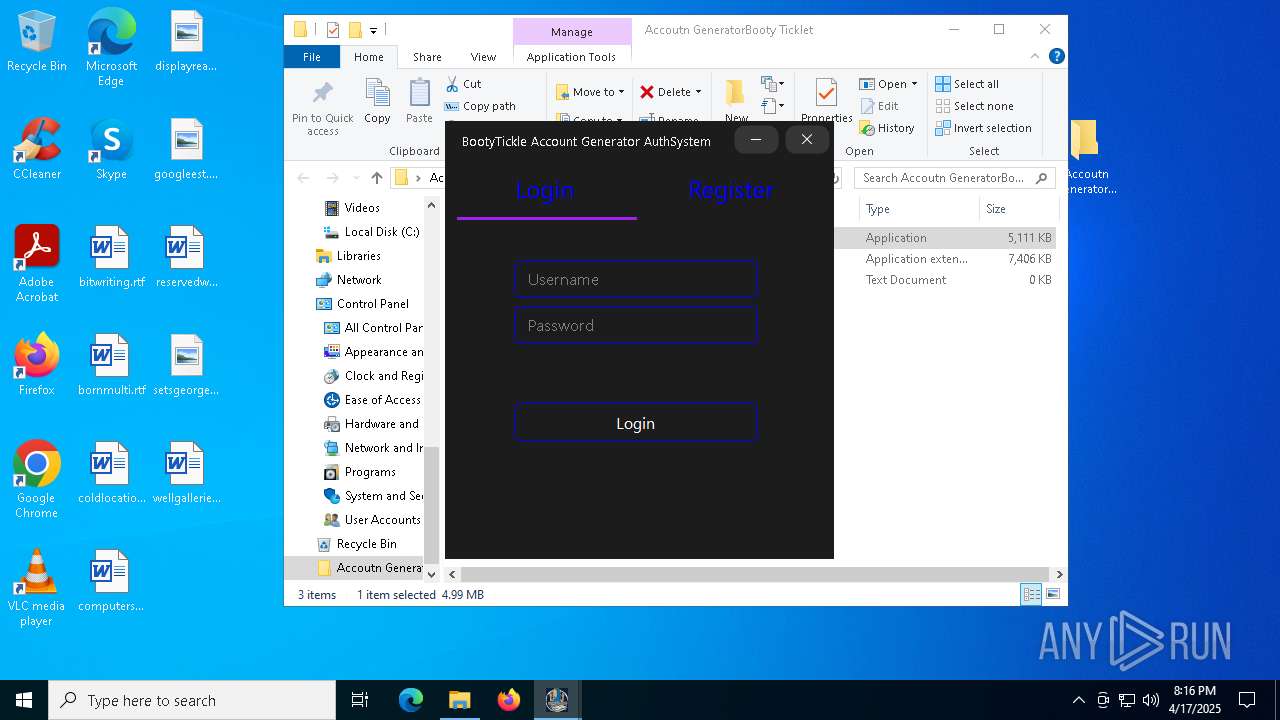
keyauth.win |
| malicious |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain in DNS Lookup (keyauth .win) |
664 | BootyTickle Account Generator V4.4-VM.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain (keyauth .win) in TLS SNI |