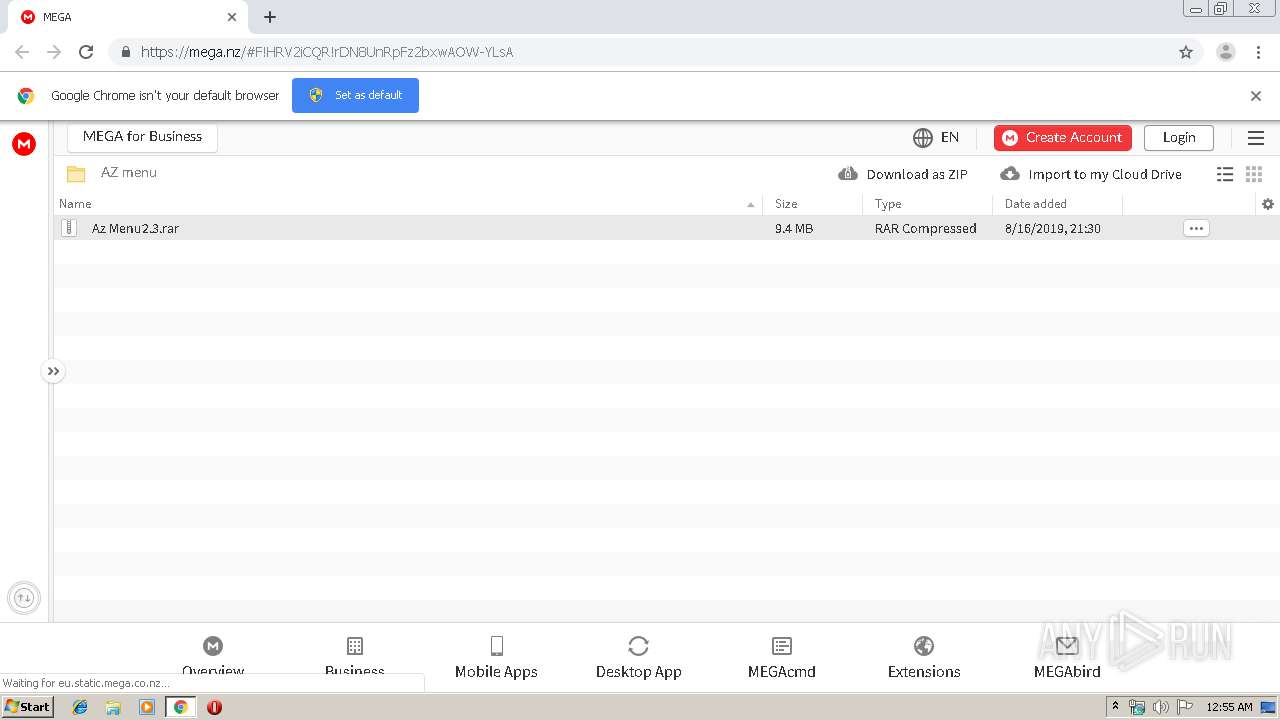
| URL: | https://mega.nz/#F!HRV2iCQR!rDN8UnRpFz2bxwAOW-YLsA?aItgiCIJ |
| Full analysis: | https://app.any.run/tasks/92328d37-3707-42ad-9f1b-08113fd8b330 |
| Verdict: | Malicious activity |
| Analysis date: | August 16, 2019, 23:54:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 718D4DEF4D87F4378B4B128618946CDB |
| SHA1: | 9CB160FC3AAE4FAC0E0672BB4AD1174BB6E7498B |
| SHA256: | E9D55ED1F3CB57FA3DFA9884FF712AF954CE15C99EAFF43A1D3572A78A44047E |
| SSDEEP: | 3:N8X/iG4Zn0lhR0TSO:29pATSO |
MALICIOUS
Changes the autorun value in the registry
- Az Menu.exe (PID: 3744)
Application was dropped or rewritten from another process
- SetupUtility.exe (PID: 3592)
- Az Menu.exe (PID: 3744)
- SetupUtility.exe (PID: 2732)
- Setup.exe (PID: 3028)
- aspnet_regiis.exe (PID: 2796)
- ngen.exe (PID: 528)
- ngen.exe (PID: 3696)
- ngen.exe (PID: 2288)
- mscorsvw.exe (PID: 3852)
- mscorsvw.exe (PID: 3448)
- mscorsvw.exe (PID: 2492)
- mscorsvw.exe (PID: 996)
- mscorsvw.exe (PID: 2828)
- mscorsvw.exe (PID: 3768)
- mscorsvw.exe (PID: 1944)
- mscorsvw.exe (PID: 2276)
- mscorsvw.exe (PID: 3212)
- mscorsvw.exe (PID: 3932)
- mscorsvw.exe (PID: 2984)
- mscorsvw.exe (PID: 1524)
- mscorsvw.exe (PID: 3836)
- mscorsvw.exe (PID: 3144)
- mscorsvw.exe (PID: 3968)
- mscorsvw.exe (PID: 2888)
- mscorsvw.exe (PID: 3420)
- mscorsvw.exe (PID: 2844)
- mscorsvw.exe (PID: 1680)
- mscorsvw.exe (PID: 2008)
- mscorsvw.exe (PID: 560)
- mscorsvw.exe (PID: 2244)
- mscorsvw.exe (PID: 3964)
- mscorsvw.exe (PID: 3544)
- mscorsvw.exe (PID: 2072)
- mscorsvw.exe (PID: 2544)
- mscorsvw.exe (PID: 3628)
- mscorsvw.exe (PID: 1348)
- mscorsvw.exe (PID: 4048)
- mscorsvw.exe (PID: 3240)
- mscorsvw.exe (PID: 3460)
- mscorsvw.exe (PID: 4016)
- mscorsvw.exe (PID: 1828)
- mscorsvw.exe (PID: 912)
- mscorsvw.exe (PID: 3440)
- mscorsvw.exe (PID: 3836)
- mscorsvw.exe (PID: 2708)
- mscorsvw.exe (PID: 4012)
- mscorsvw.exe (PID: 2380)
- mscorsvw.exe (PID: 2708)
- mscorsvw.exe (PID: 3912)
- mscorsvw.exe (PID: 3528)
- mscorsvw.exe (PID: 2872)
- mscorsvw.exe (PID: 2424)
- mscorsvw.exe (PID: 912)
- mscorsvw.exe (PID: 1528)
- mscorsvw.exe (PID: 3784)
- mscorsvw.exe (PID: 2308)
- mscorsvw.exe (PID: 3164)
- mscorsvw.exe (PID: 1720)
- mscorsvw.exe (PID: 2784)
- mscorsvw.exe (PID: 2804)
- mscorsvw.exe (PID: 3508)
- mscorsvw.exe (PID: 3060)
- mscorsvw.exe (PID: 772)
- mscorsvw.exe (PID: 1632)
- mscorsvw.exe (PID: 2344)
- mscorsvw.exe (PID: 2140)
- mscorsvw.exe (PID: 1420)
- mscorsvw.exe (PID: 3592)
- mscorsvw.exe (PID: 3572)
- mscorsvw.exe (PID: 3536)
- mscorsvw.exe (PID: 2968)
- mscorsvw.exe (PID: 3232)
- mscorsvw.exe (PID: 3596)
- mscorsvw.exe (PID: 3792)
- mscorsvw.exe (PID: 3240)
- mscorsvw.exe (PID: 3984)
- mscorsvw.exe (PID: 3404)
- mscorsvw.exe (PID: 3848)
- mscorsvw.exe (PID: 2568)
- mscorsvw.exe (PID: 1636)
- mscorsvw.exe (PID: 1020)
- mscorsvw.exe (PID: 3484)
- mscorsvw.exe (PID: 3436)
- mscorsvw.exe (PID: 2644)
- mscorsvw.exe (PID: 2376)
- mscorsvw.exe (PID: 2352)
- mscorsvw.exe (PID: 3544)
- mscorsvw.exe (PID: 2424)
- mscorsvw.exe (PID: 4028)
- mscorsvw.exe (PID: 3184)
- mscorsvw.exe (PID: 3236)
- mscorsvw.exe (PID: 3068)
- mscorsvw.exe (PID: 3076)
- mscorsvw.exe (PID: 3820)
- mscorsvw.exe (PID: 2664)
- mscorsvw.exe (PID: 3452)
- mscorsvw.exe (PID: 3156)
- mscorsvw.exe (PID: 2060)
- mscorsvw.exe (PID: 2444)
- mscorsvw.exe (PID: 2468)
- mscorsvw.exe (PID: 2820)
- mscorsvw.exe (PID: 2200)
- mscorsvw.exe (PID: 2760)
- mscorsvw.exe (PID: 2736)
- mscorsvw.exe (PID: 2064)
- mscorsvw.exe (PID: 2360)
Loads dropped or rewritten executable
- Setup.exe (PID: 3028)
- wmiprvse.exe (PID: 3712)
- Az Menu.exe (PID: 3744)
- svchost.exe (PID: 784)
- mscorsvw.exe (PID: 3448)
- ngen.exe (PID: 528)
- mscorsvw.exe (PID: 2828)
- ngen.exe (PID: 3696)
- ngen.exe (PID: 2288)
- mscorsvw.exe (PID: 996)
- mscorsvw.exe (PID: 3852)
- mscorsvw.exe (PID: 2492)
- mscorsvw.exe (PID: 1944)
- mscorsvw.exe (PID: 3768)
- mscorsvw.exe (PID: 3420)
- mscorsvw.exe (PID: 2276)
- mscorsvw.exe (PID: 3212)
- mscorsvw.exe (PID: 3932)
- mscorsvw.exe (PID: 2984)
- mscorsvw.exe (PID: 3836)
- mscorsvw.exe (PID: 1680)
- mscorsvw.exe (PID: 3968)
- mscorsvw.exe (PID: 3144)
- mscorsvw.exe (PID: 2844)
- mscorsvw.exe (PID: 1524)
- mscorsvw.exe (PID: 2888)
- mscorsvw.exe (PID: 2244)
- mscorsvw.exe (PID: 2544)
- mscorsvw.exe (PID: 2008)
- mscorsvw.exe (PID: 3964)
- mscorsvw.exe (PID: 560)
- mscorsvw.exe (PID: 3544)
- mscorsvw.exe (PID: 3628)
- mscorsvw.exe (PID: 3460)
- mscorsvw.exe (PID: 4016)
- mscorsvw.exe (PID: 4048)
- mscorsvw.exe (PID: 2072)
- mscorsvw.exe (PID: 3164)
- mscorsvw.exe (PID: 1828)
- mscorsvw.exe (PID: 2708)
- mscorsvw.exe (PID: 3836)
- mscorsvw.exe (PID: 912)
- mscorsvw.exe (PID: 3440)
- mscorsvw.exe (PID: 2708)
- mscorsvw.exe (PID: 1348)
- mscorsvw.exe (PID: 3240)
- mscorsvw.exe (PID: 4012)
- mscorsvw.exe (PID: 2380)
- mscorsvw.exe (PID: 2872)
- mscorsvw.exe (PID: 2424)
- mscorsvw.exe (PID: 3528)
- mscorsvw.exe (PID: 1528)
- mscorsvw.exe (PID: 912)
- mscorsvw.exe (PID: 3912)
- mscorsvw.exe (PID: 1632)
- mscorsvw.exe (PID: 2784)
- mscorsvw.exe (PID: 1720)
- mscorsvw.exe (PID: 2804)
- mscorsvw.exe (PID: 3508)
- mscorsvw.exe (PID: 3784)
- mscorsvw.exe (PID: 2308)
- mscorsvw.exe (PID: 772)
- mscorsvw.exe (PID: 3536)
- mscorsvw.exe (PID: 2968)
- mscorsvw.exe (PID: 2140)
- mscorsvw.exe (PID: 1420)
- mscorsvw.exe (PID: 2344)
- mscorsvw.exe (PID: 3060)
- mscorsvw.exe (PID: 3592)
- mscorsvw.exe (PID: 3232)
- mscorsvw.exe (PID: 3240)
- mscorsvw.exe (PID: 3984)
- mscorsvw.exe (PID: 3572)
- mscorsvw.exe (PID: 3596)
- mscorsvw.exe (PID: 3484)
- mscorsvw.exe (PID: 3404)
- mscorsvw.exe (PID: 2568)
- mscorsvw.exe (PID: 3848)
- mscorsvw.exe (PID: 3792)
- mscorsvw.exe (PID: 1020)
- mscorsvw.exe (PID: 1636)
- mscorsvw.exe (PID: 3436)
- mscorsvw.exe (PID: 2644)
- mscorsvw.exe (PID: 2352)
- mscorsvw.exe (PID: 2376)
- mscorsvw.exe (PID: 3236)
- mscorsvw.exe (PID: 4028)
- mscorsvw.exe (PID: 2424)
- mscorsvw.exe (PID: 3544)
- mscorsvw.exe (PID: 3068)
- mscorsvw.exe (PID: 2060)
- mscorsvw.exe (PID: 3076)
- mscorsvw.exe (PID: 3820)
- mscorsvw.exe (PID: 2664)
- mscorsvw.exe (PID: 3452)
- mscorsvw.exe (PID: 3184)
- mscorsvw.exe (PID: 3156)
- mscorsvw.exe (PID: 2760)
- mscorsvw.exe (PID: 2444)
- mscorsvw.exe (PID: 2468)
- mscorsvw.exe (PID: 2200)
- mscorsvw.exe (PID: 2360)
- mscorsvw.exe (PID: 2736)
- mscorsvw.exe (PID: 2820)
- mscorsvw.exe (PID: 2064)
Loads the Task Scheduler DLL interface
- Az Menu.exe (PID: 3744)
Loads the Task Scheduler COM API
- ngen.exe (PID: 528)
- mscorsvw.exe (PID: 3448)
- ngen.exe (PID: 3696)
- ngen.exe (PID: 2288)
SUSPICIOUS
Executable content was dropped or overwritten
- ndp48-x86-x64-allos-enu.exe (PID: 2216)
- Az Menu.exe (PID: 3744)
- WinRAR.exe (PID: 2960)
- msiexec.exe (PID: 2412)
- mscorsvw.exe (PID: 996)
- mscorsvw.exe (PID: 3628)
- mscorsvw.exe (PID: 4016)
- mscorsvw.exe (PID: 1348)
- mscorsvw.exe (PID: 3060)
- mscorsvw.exe (PID: 2344)
- mscorsvw.exe (PID: 3240)
- mscorsvw.exe (PID: 3232)
- mscorsvw.exe (PID: 1720)
- mscorsvw.exe (PID: 3404)
- mscorsvw.exe (PID: 3596)
- mscorsvw.exe (PID: 3848)
- mscorsvw.exe (PID: 1636)
- mscorsvw.exe (PID: 1020)
- mscorsvw.exe (PID: 2352)
- mscorsvw.exe (PID: 3544)
- mscorsvw.exe (PID: 3236)
- mscorsvw.exe (PID: 2760)
- mscorsvw.exe (PID: 3184)
- mscorsvw.exe (PID: 2468)
Creates files in the Windows directory
- Az Menu.exe (PID: 3744)
- lodctr.exe (PID: 560)
- aspnet_regiis.exe (PID: 2796)
- lodctr.exe (PID: 3764)
- ngen.exe (PID: 528)
- lodctr.exe (PID: 1484)
- lodctr.exe (PID: 3324)
- lodctr.exe (PID: 2188)
- ngen.exe (PID: 3696)
- ngen.exe (PID: 2288)
- msiexec.exe (PID: 2412)
- mscorsvw.exe (PID: 3448)
- mscorsvw.exe (PID: 996)
- mscorsvw.exe (PID: 3628)
- mscorsvw.exe (PID: 4016)
- mscorsvw.exe (PID: 1348)
- mscorsvw.exe (PID: 3060)
- mscorsvw.exe (PID: 2344)
- mscorsvw.exe (PID: 3240)
- mscorsvw.exe (PID: 3232)
- mscorsvw.exe (PID: 3596)
- mscorsvw.exe (PID: 1720)
- mscorsvw.exe (PID: 3404)
- mscorsvw.exe (PID: 1636)
- mscorsvw.exe (PID: 3848)
- mscorsvw.exe (PID: 3544)
- mscorsvw.exe (PID: 1020)
- mscorsvw.exe (PID: 3236)
- mscorsvw.exe (PID: 2352)
- mscorsvw.exe (PID: 2760)
- mscorsvw.exe (PID: 3184)
- mscorsvw.exe (PID: 3156)
- mscorsvw.exe (PID: 3076)
- mscorsvw.exe (PID: 2468)
Removes files from Windows directory
- Az Menu.exe (PID: 3744)
- lodctr.exe (PID: 560)
- msiexec.exe (PID: 2412)
- lodctr.exe (PID: 3764)
- lodctr.exe (PID: 1484)
- lodctr.exe (PID: 2188)
- lodctr.exe (PID: 3324)
- aspnet_regiis.exe (PID: 2796)
- mscorsvw.exe (PID: 996)
- mscorsvw.exe (PID: 3628)
- mscorsvw.exe (PID: 4016)
- mscorsvw.exe (PID: 1348)
- mscorsvw.exe (PID: 3060)
- mscorsvw.exe (PID: 2344)
- mscorsvw.exe (PID: 3240)
- mscorsvw.exe (PID: 3232)
- mscorsvw.exe (PID: 3404)
- mscorsvw.exe (PID: 3596)
- mscorsvw.exe (PID: 1720)
- mscorsvw.exe (PID: 3848)
- mscorsvw.exe (PID: 1636)
- mscorsvw.exe (PID: 1020)
- mscorsvw.exe (PID: 3236)
- mscorsvw.exe (PID: 3544)
- mscorsvw.exe (PID: 2352)
- mscorsvw.exe (PID: 3184)
- mscorsvw.exe (PID: 2760)
- mscorsvw.exe (PID: 2468)
- mscorsvw.exe (PID: 3076)
- mscorsvw.exe (PID: 3156)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3548)
Reads Internet Cache Settings
- Az Menu.exe (PID: 3744)
Creates files in the user directory
- Az Menu.exe (PID: 3744)
Creates COM task schedule object
- msiexec.exe (PID: 2412)
- aspnet_regiis.exe (PID: 2796)
Changes the autorun value in the registry
- msiexec.exe (PID: 2412)
INFO
Loads dropped or rewritten executable
- MsiExec.exe (PID: 3444)
- MsiExec.exe (PID: 3540)
- MsiExec.exe (PID: 3752)
- msiexec.exe (PID: 2412)
Dropped object may contain Bitcoin addresses
- ndp48-x86-x64-allos-enu.exe (PID: 2216)
- msiexec.exe (PID: 2412)
- mscorsvw.exe (PID: 3448)
Reads settings of System Certificates
- chrome.exe (PID: 2840)
Application launched itself
- chrome.exe (PID: 3548)
- msiexec.exe (PID: 2412)
Creates or modifies windows services
- msiexec.exe (PID: 2412)
Creates a software uninstall entry
- msiexec.exe (PID: 2412)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
217
Monitored processes
158
Malicious processes
113
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 528 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngen.exe update /queue | C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngen.exe | — | MsiExec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Common Language Runtime native compiler Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 560 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -StartupEvent 1fc -InterruptEvent 0 -NGENProcess 1f4 -Pipe 1f0 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe | — | ngen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 560 | "C:\Windows\system32\lodctr.exe" "C:\Windows\Microsoft.NET\Framework\v4.0.30319\netmemorycache.ini" | C:\Windows\system32\lodctr.exe | — | MsiExec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Load PerfMon Counters Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 772 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -StartupEvent 2b0 -InterruptEvent 0 -NGENProcess 2ac -Pipe 29c -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe | — | ngen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 784 | C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 912 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -StartupEvent 264 -InterruptEvent 0 -NGENProcess 23c -Pipe 184 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe | — | ngen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 912 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -StartupEvent 2a0 -InterruptEvent 0 -NGENProcess 29c -Pipe 28c -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe | — | ngen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 996 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -StartupEvent 100 -InterruptEvent 0 -NGENProcess f4 -Pipe ec -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe | ngen.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 1008 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\regtlibv12.exe" "C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorlib.tlb" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\regtlibv12.exe | — | MsiExec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: RegTLib Exit code: 0 Version: 14.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 1020 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -StartupEvent 2f4 -InterruptEvent 0 -NGENProcess 2f0 -Pipe 310 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe | ngen.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
Total events
29 073
Read events
14 112
Write events
12 696
Delete events
2 265
Modification events
| (PID) Process: | (3396) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3548-13210473312816375 |
Value: 259 | |||
| (PID) Process: | (3548) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3548) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3548) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3548) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3548) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3548) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3548) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3548) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 1512-13197841398593750 |
Value: 0 | |||
| (PID) Process: | (3548) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
1 382
Suspicious files
99
Text files
706
Unknown types
29
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3548 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\52bb4de5-20a8-4872-9c1a-445052295fab.tmp | — | |
MD5:— | SHA256:— | |||
| 3548 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000020.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3548 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\AvailabilityDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3548 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\AvailabilityDB\LOG.old~RF169ca2.TMP | text | |
MD5:— | SHA256:— | |||
| 3548 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3548 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF169be7.TMP | text | |
MD5:— | SHA256:— | |||
| 3548 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3548 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 3548 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old~RF169c44.TMP | text | |
MD5:— | SHA256:— | |||
| 3548 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RF169c25.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
41
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2840 | chrome.exe | GET | 302 | 172.217.18.174:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 512 b | whitelisted |
3028 | Setup.exe | GET | 200 | 2.16.186.120:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | der | 550 b | whitelisted |
3028 | Setup.exe | GET | 200 | 2.16.186.120:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | der | 555 b | whitelisted |
2840 | chrome.exe | GET | 200 | 172.217.130.70:80 | http://r1---sn-2gb7sn7r.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=185.76.9.67&mm=28&mn=sn-2gb7sn7r&ms=nvh&mt=1565999653&mv=m&mvi=0&pl=24&shardbypass=yes | US | crx | 862 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3744 | Az Menu.exe | 68.232.34.200:443 | download.visualstudio.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
— | — | 172.217.22.110:443 | clients1.google.com | Google Inc. | US | whitelisted |
2840 | chrome.exe | 172.217.22.35:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2840 | chrome.exe | 172.217.23.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2840 | chrome.exe | 89.44.169.135:443 | mega.nz | Datacenter Luxembourg S.A. | LU | suspicious |
2840 | chrome.exe | 172.217.22.45:443 | accounts.google.com | Google Inc. | US | whitelisted |
2840 | chrome.exe | 172.217.23.170:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
2840 | chrome.exe | 172.217.22.110:443 | clients1.google.com | Google Inc. | US | whitelisted |
2840 | chrome.exe | 89.44.169.132:443 | eu.static.mega.co.nz | Datacenter Luxembourg S.A. | LU | suspicious |
2840 | chrome.exe | 172.217.18.164:443 | www.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
mega.nz |
| whitelisted |
accounts.google.com |
| shared |
safebrowsing.googleapis.com |
| whitelisted |
clients1.google.com |
| whitelisted |
eu.static.mega.co.nz |
| shared |
www.google.com |
| malicious |
g.api.mega.co.nz |
| shared |
clients2.google.com |
| whitelisted |
clients2.googleusercontent.com |
| whitelisted |