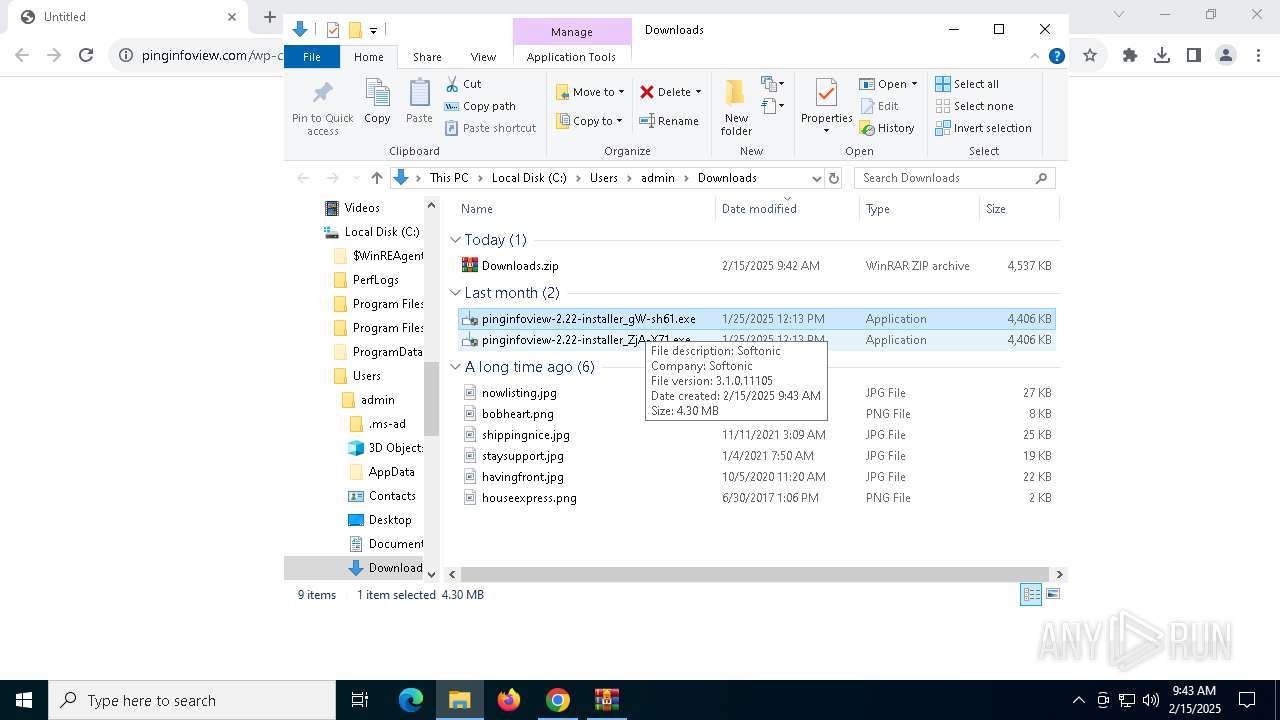
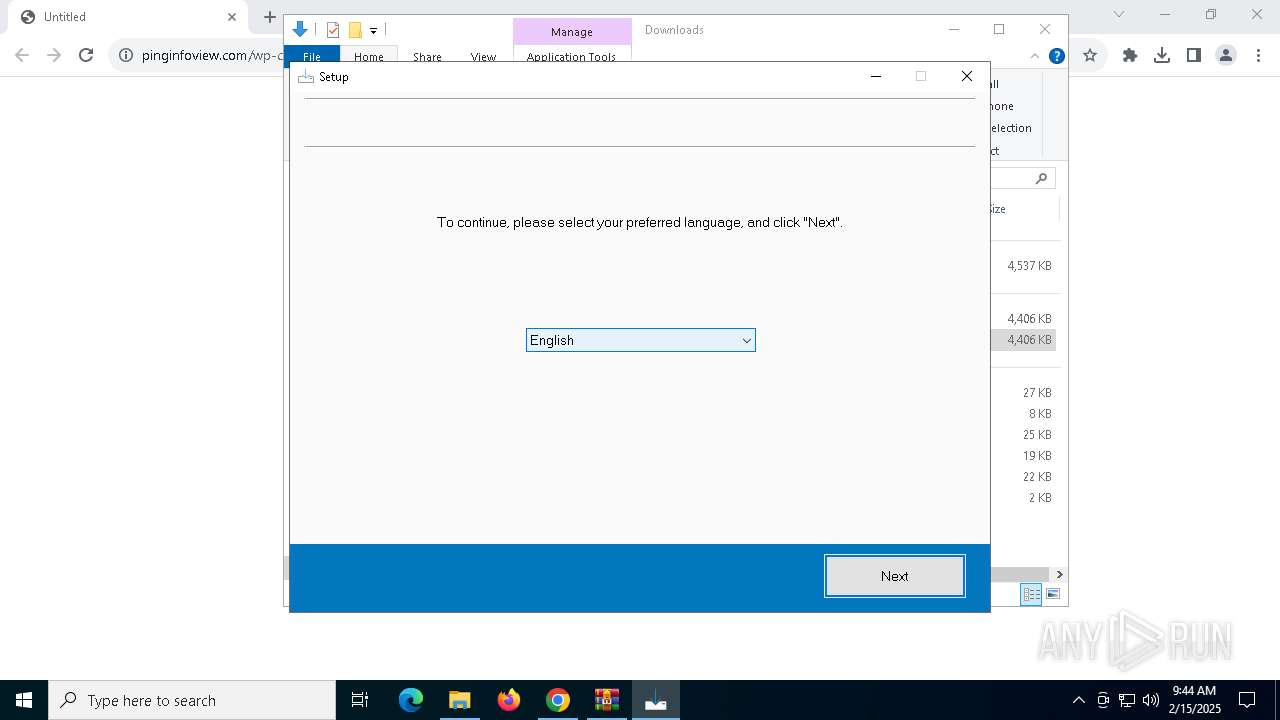
| URL: | https://pinginfoview.com/wp-content/uploads/2025/01/Downloads.zip |
| Full analysis: | https://app.any.run/tasks/b01ce11d-5c65-4a71-aff4-dd6f32ff633d |
| Verdict: | Malicious activity |
| Analysis date: | February 15, 2025, 09:42:03 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 05302F5C1A9D99EC9D97A7C39E59755C |
| SHA1: | B8F4C55F0C8EBCCC2DEB121031FFF43D761C5A84 |
| SHA256: | E9C14397354A53B069288DA06106780F040054E640A23A82CA812BBE9B6071D6 |
| SSDEEP: | 3:N8I2M2SZ2OlAQyXZ+6zgLcn:2ISLOlAZpvLn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
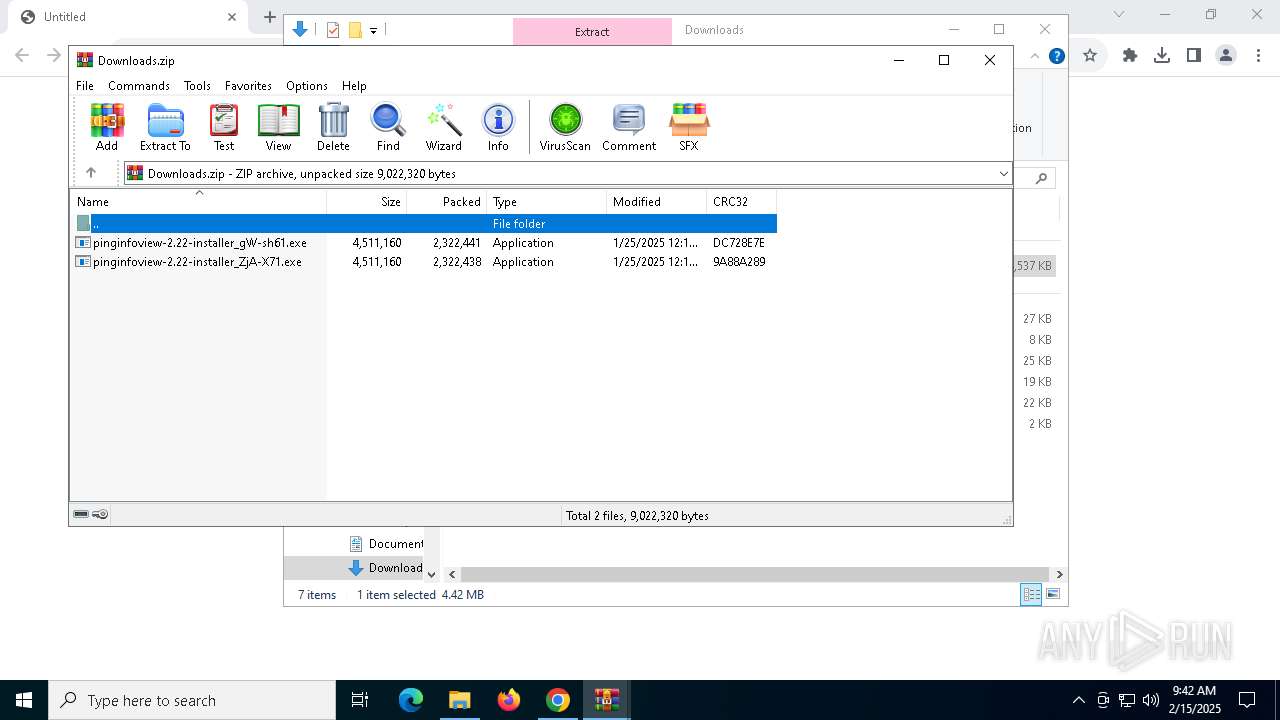
- pinginfoview-2.22-installer_gW-sh61.exe (PID: 6984)
- pinginfoview-2.22-installer_ZjA-X71.exe (PID: 3488)
Checks Windows Trust Settings
- pinginfoview-2.22-installer_gW-sh61.exe (PID: 6984)
- pinginfoview-2.22-installer_ZjA-X71.exe (PID: 3488)
Executable content was dropped or overwritten
- pinginfoview-2.22-installer_gW-sh61.exe (PID: 6984)
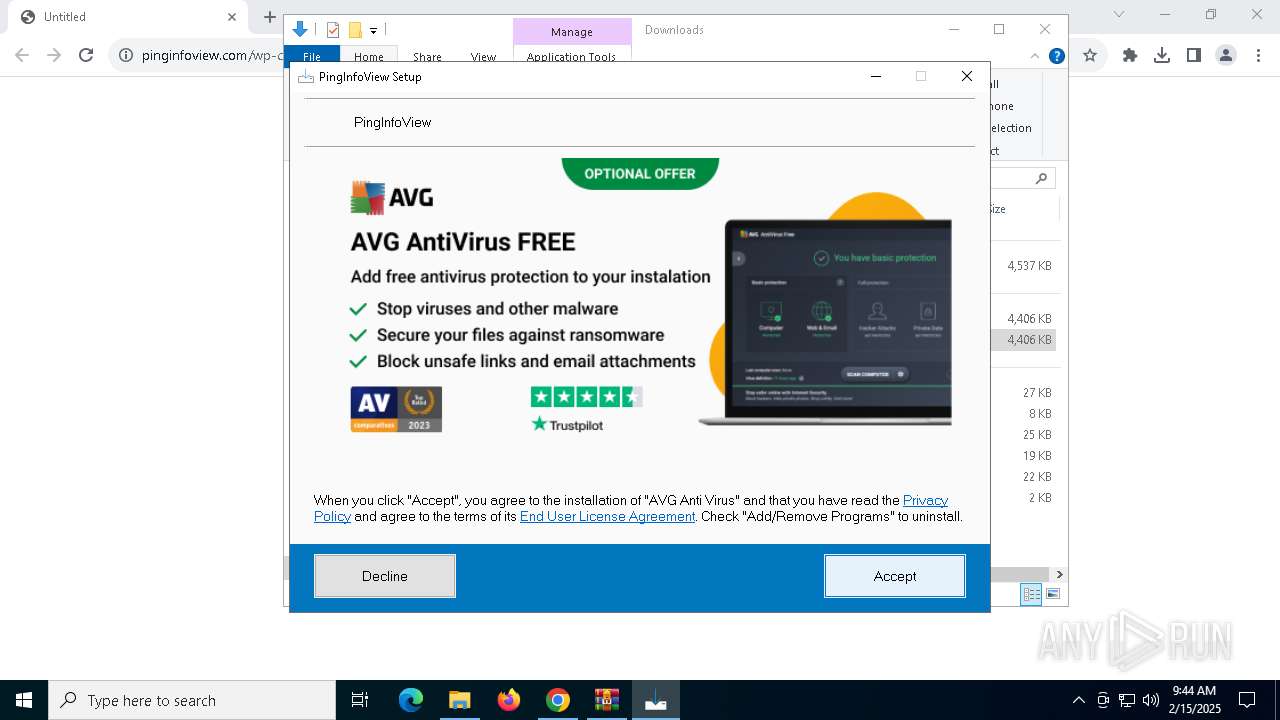
- avg_antivirus_free_setup.exe (PID: 2356)
- avg_antivirus_free_online_setup.exe (PID: 1296)
- icarus.exe (PID: 7068)
- icarus.exe (PID: 1304)
- pinginfoview-2.22-installer_ZjA-X71.exe (PID: 3488)
Starts itself from another location
- icarus.exe (PID: 7068)
The process creates files with name similar to system file names
- icarus.exe (PID: 1304)
Process drops legitimate windows executable
- icarus.exe (PID: 1304)
The process drops C-runtime libraries
- icarus.exe (PID: 1304)
The process verifies whether the antivirus software is installed
- icarus.exe (PID: 1304)
INFO
The sample compiled with english language support
- chrome.exe (PID: 6248)
- chrome.exe (PID: 640)
- chrome.exe (PID: 6304)
- pinginfoview-2.22-installer_gW-sh61.exe (PID: 6984)
- avg_antivirus_free_setup.exe (PID: 2356)
- avg_antivirus_free_online_setup.exe (PID: 1296)
- icarus.exe (PID: 7068)
- icarus.exe (PID: 1304)
- pinginfoview-2.22-installer_ZjA-X71.exe (PID: 3488)
- WinRAR.exe (PID: 1616)
Checks supported languages
- pinginfoview-2.22-installer_gW-sh61.exe (PID: 6984)
- avg_antivirus_free_setup.exe (PID: 2356)
- avg_antivirus_free_online_setup.exe (PID: 1296)
- icarus.exe (PID: 7068)
- icarus.exe (PID: 1304)
- icarus.exe (PID: 3780)
- pinginfoview-2.22-installer_ZjA-X71.exe (PID: 3488)
- avg_antivirus_free_setup.exe (PID: 2008)
Reads the computer name
- pinginfoview-2.22-installer_gW-sh61.exe (PID: 6984)
- avg_antivirus_free_setup.exe (PID: 2356)
- avg_antivirus_free_online_setup.exe (PID: 1296)
- icarus.exe (PID: 7068)
- icarus.exe (PID: 1304)
- icarus.exe (PID: 3780)
- pinginfoview-2.22-installer_ZjA-X71.exe (PID: 3488)
- avg_antivirus_free_setup.exe (PID: 2008)
Checks proxy server information
- pinginfoview-2.22-installer_gW-sh61.exe (PID: 6984)
- avg_antivirus_free_online_setup.exe (PID: 1296)
- pinginfoview-2.22-installer_ZjA-X71.exe (PID: 3488)
Creates files or folders in the user directory
- pinginfoview-2.22-installer_gW-sh61.exe (PID: 6984)
- pinginfoview-2.22-installer_ZjA-X71.exe (PID: 3488)
Reads the machine GUID from the registry
- pinginfoview-2.22-installer_gW-sh61.exe (PID: 6984)
- avg_antivirus_free_setup.exe (PID: 2356)
- avg_antivirus_free_online_setup.exe (PID: 1296)
- icarus.exe (PID: 7068)
- icarus.exe (PID: 3780)
- icarus.exe (PID: 1304)
- pinginfoview-2.22-installer_ZjA-X71.exe (PID: 3488)
Executable content was dropped or overwritten
- chrome.exe (PID: 640)
- chrome.exe (PID: 6248)
- WinRAR.exe (PID: 1616)
Reads Microsoft Office registry keys
- chrome.exe (PID: 6304)
Application launched itself
- chrome.exe (PID: 6304)
Create files in a temporary directory
- pinginfoview-2.22-installer_gW-sh61.exe (PID: 6984)
- avg_antivirus_free_online_setup.exe (PID: 1296)
- pinginfoview-2.22-installer_ZjA-X71.exe (PID: 3488)
Reads the software policy settings
- avg_antivirus_free_setup.exe (PID: 2356)
- avg_antivirus_free_online_setup.exe (PID: 1296)
- pinginfoview-2.22-installer_ZjA-X71.exe (PID: 3488)
- pinginfoview-2.22-installer_gW-sh61.exe (PID: 6984)
Creates files in the program directory
- avg_antivirus_free_online_setup.exe (PID: 1296)
- icarus.exe (PID: 7068)
- icarus.exe (PID: 1304)
Reads CPU info
- icarus.exe (PID: 7068)
- icarus.exe (PID: 3780)
- icarus.exe (PID: 1304)
Reads Environment values
- icarus.exe (PID: 1304)
Manual execution by a user
- pinginfoview-2.22-installer_ZjA-X71.exe (PID: 5240)
- pinginfoview-2.22-installer_ZjA-X71.exe (PID: 3488)
- WinRAR.exe (PID: 1616)
- pinginfoview-2.22-installer_gW-sh61.exe (PID: 188)
- pinginfoview-2.22-installer_gW-sh61.exe (PID: 6984)
The sample compiled with czech language support
- icarus.exe (PID: 1304)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
165
Monitored processes
30
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Users\admin\Downloads\pinginfoview-2.22-installer_gW-sh61.exe" | C:\Users\admin\Downloads\pinginfoview-2.22-installer_gW-sh61.exe | — | explorer.exe | |||||||||||
User: admin Company: Softonic Integrity Level: MEDIUM Description: Softonic Exit code: 3221226540 Version: 3.1.0.11108 Modules
| |||||||||||||||
| 244 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4208 --field-trial-handle=1872,i,891494011401052871,14656622943705102501,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 640 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5668 --field-trial-handle=1872,i,891494011401052871,14656622943705102501,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1296 | "C:\WINDOWS\Temp\asw.b19783736225456d\avg_antivirus_free_online_setup.exe" /silent /ws /psh:hIA7qv6y4LnyhZ8uUg5ES7NJSv5xFxjsl6RHqJGR35jKfB2LkrE9eOjWN5xgM0llSpYRPzJTV6kNeF /cookie:mmm_irs_ppi_902_451_o /ga_clientid:1561a6e1-9b32-48f4-8755-40cfd78589cc /edat_dir:C:\WINDOWS\Temp\asw.b19783736225456d | C:\Windows\Temp\asw.b19783736225456d\avg_antivirus_free_online_setup.exe | avg_antivirus_free_setup.exe | ||||||||||||
User: admin Company: Gen Digital Inc. Integrity Level: HIGH Description: AVG Self-Extract Package Version: 25.1.8538.0 Modules
| |||||||||||||||
| 1304 | C:\WINDOWS\Temp\asw-72434755-b9c2-47d9-a7dc-6a1ad4956cfb\avg-av\icarus.exe /silent /ws /psh:hIA7qv6y4LnyhZ8uUg5ES7NJSv5xFxjsl6RHqJGR35jKfB2LkrE9eOjWN5xgM0llSpYRPzJTV6kNeF /cookie:mmm_irs_ppi_902_451_o /edat_dir:C:\WINDOWS\Temp\asw.b19783736225456d /track-guid:1561a6e1-9b32-48f4-8755-40cfd78589cc /er_master:master_ep_eee8e5c3-2785-420c-9a6e-a2c8051c0db9 /er_ui:ui_ep_a1552e60-538a-4471-901e-760df3538238 /er_slave:avg-av_slave_ep_aa304259-5ec6-4036-a9a6-9f36334e34f8 /slave:avg-av | C:\Windows\Temp\asw-72434755-b9c2-47d9-a7dc-6a1ad4956cfb\avg-av\icarus.exe | icarus.exe | ||||||||||||
User: admin Company: Gen Digital Inc. Integrity Level: HIGH Description: AVG Installer Version: 25.1.8538.0 Modules
| |||||||||||||||
| 1416 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5464 --field-trial-handle=1872,i,891494011401052871,14656622943705102501,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1616 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Downloads.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2008 | "C:\Users\admin\AppData\Local\Temp\ISV2C59.tmp\avg\avg_antivirus_free_setup.exe" /silent /ws /psh:hIA7qv6y4LnyhZ8uUg5ES7NJSv5xFxjsl6RHqJGR35jKfB2LkrE9eOjWN5xgM0llSpYRPzJTV6l41h | C:\Users\admin\AppData\Local\Temp\ISV2C59.tmp\avg\avg_antivirus_free_setup.exe | pinginfoview-2.22-installer_ZjA-X71.exe | ||||||||||||
User: admin Company: AVG Technologies CZ, s.r.o. Integrity Level: HIGH Description: AVG Installer Exit code: 1056 Version: 2.1.99.0 Modules
| |||||||||||||||
| 2356 | "C:\Users\admin\AppData\Local\Temp\ISVCC28.tmp\avg\avg_antivirus_free_setup.exe" /silent /ws /psh:hIA7qv6y4LnyhZ8uUg5ES7NJSv5xFxjsl6RHqJGR35jKfB2LkrE9eOjWN5xgM0llSpYRPzJTV6kNeF | C:\Users\admin\AppData\Local\Temp\ISVCC28.tmp\avg\avg_antivirus_free_setup.exe | pinginfoview-2.22-installer_gW-sh61.exe | ||||||||||||
User: admin Company: AVG Technologies CZ, s.r.o. Integrity Level: HIGH Description: AVG Installer Version: 2.1.99.0 Modules
| |||||||||||||||
| 3488 | "C:\Users\admin\Downloads\pinginfoview-2.22-installer_ZjA-X71.exe" | C:\Users\admin\Downloads\pinginfoview-2.22-installer_ZjA-X71.exe | explorer.exe | ||||||||||||
User: admin Company: Softonic Integrity Level: HIGH Description: Softonic Exit code: 0 Version: 3.1.0.11105 Modules
| |||||||||||||||
Total events
16 776
Read events
16 685
Write events
70
Delete events
21
Modification events
| (PID) Process: | (6304) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6304) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6304) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6304) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6304) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3808) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 010000000000000086548EEC8D7FDB01 | |||
| (PID) Process: | (6304) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithProgids |
| Operation: | write | Name: | WinRAR.ZIP |
Value: | |||
| (PID) Process: | (5112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
Executable files
260
Suspicious files
662
Text files
131
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF13864a.TMP | — | |
MD5:— | SHA256:— | |||
| 6304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF13864a.TMP | — | |
MD5:— | SHA256:— | |||
| 6304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF13864a.TMP | — | |
MD5:— | SHA256:— | |||
| 6304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF13864a.TMP | — | |
MD5:— | SHA256:— | |||
| 6304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF138679.TMP | — | |
MD5:— | SHA256:— | |||
| 6304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
88
DNS requests
75
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
488 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
488 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6056 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6056 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6248 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AMpg5-cnrANo_2018.8.8.0/2018.8.8.0_win64_win_third_party_module_list.crx3 | unknown | — | — | whitelisted |
6248 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AMpg5-cnrANo_2018.8.8.0/2018.8.8.0_win64_win_third_party_module_list.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.16.110.136:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
488 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
488 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
6572 | chrome.exe | 172.217.218.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
6304 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
pinginfoview.com |
| unknown |
accounts.google.com |
| whitelisted |
login.live.com |
| whitelisted |
www.google.com |
| whitelisted |
Threats
Process | Message |
|---|---|
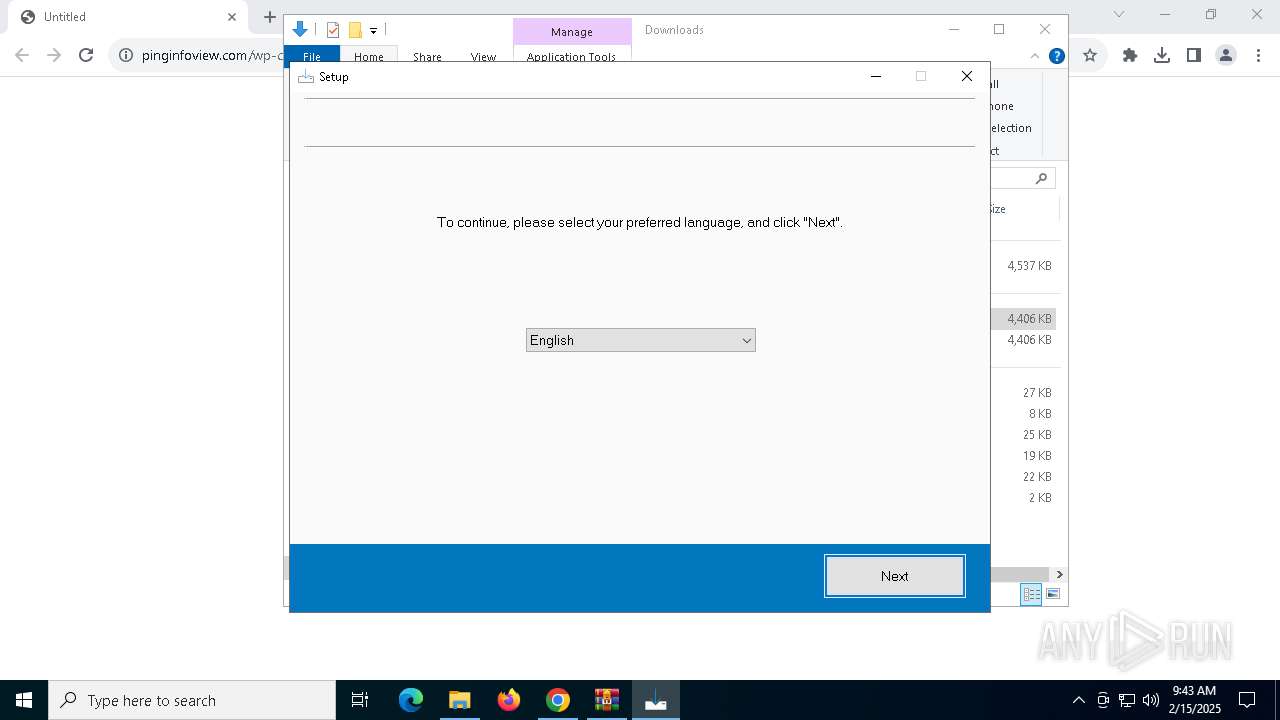
pinginfoview-2.22-installer_gW-sh61.exe | LoadingPage
|
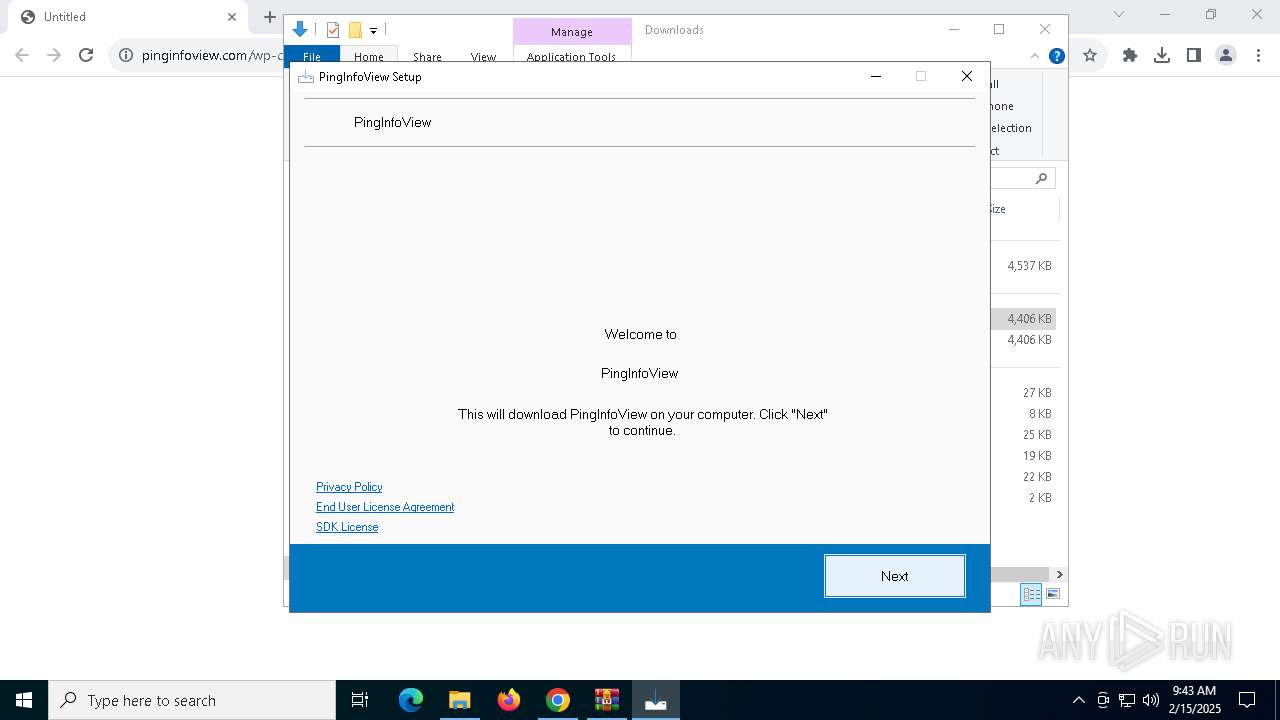
pinginfoview-2.22-installer_gW-sh61.exe | WelcomePage
|
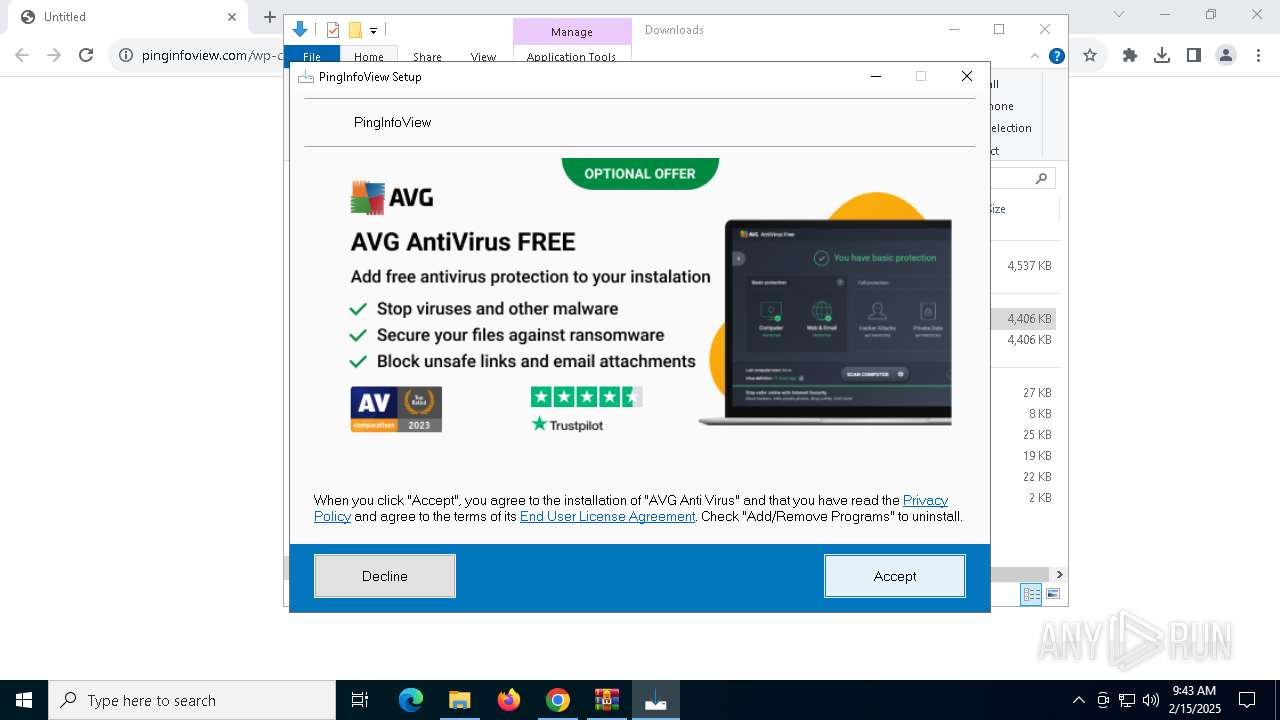
pinginfoview-2.22-installer_gW-sh61.exe | ProductPage
|
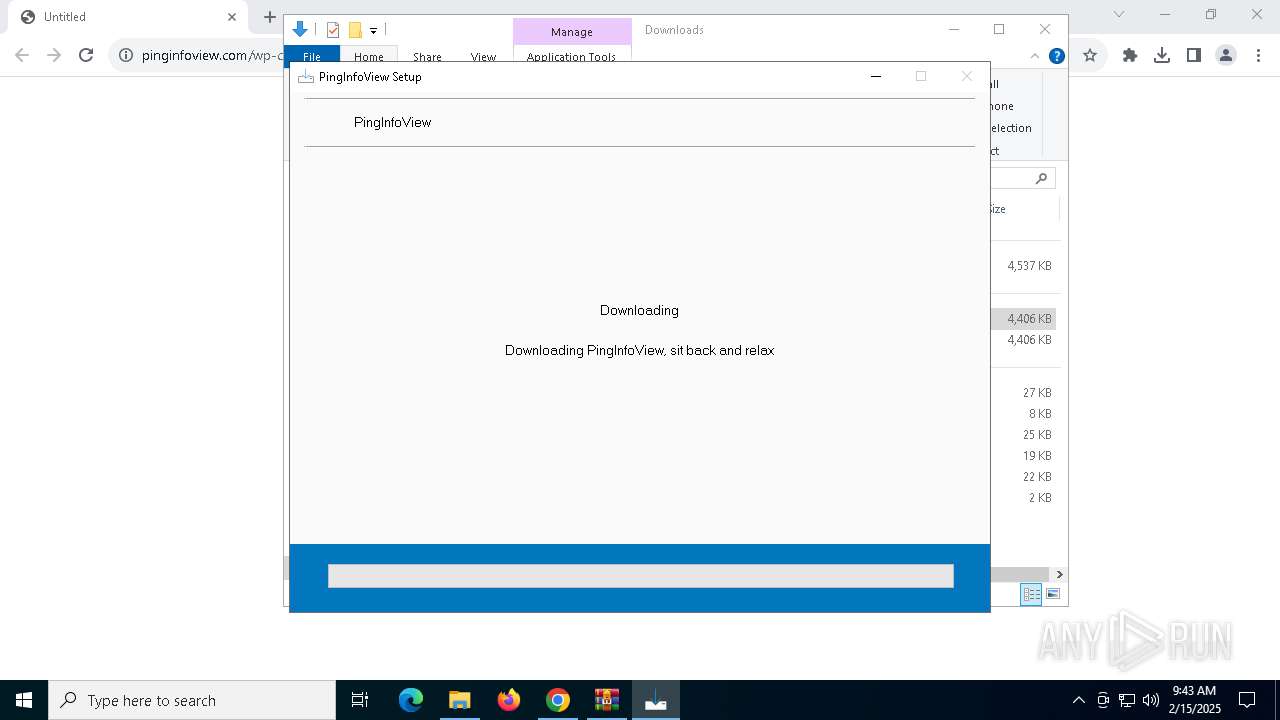
pinginfoview-2.22-installer_gW-sh61.exe | DownloadPageDLM
|
pinginfoview-2.22-installer_ZjA-X71.exe | LoadingPage
|
pinginfoview-2.22-installer_ZjA-X71.exe | WelcomePage
|
pinginfoview-2.22-installer_ZjA-X71.exe | ProductPage
|
pinginfoview-2.22-installer_ZjA-X71.exe | DownloadPageDLM
|