| File name: | word.exe |
| Full analysis: | https://app.any.run/tasks/ec98bba4-dae4-4f82-8d57-d525f22bdd32 |
| Verdict: | Malicious activity |
| Analysis date: | June 06, 2025, 22:11:46 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 19 sections |
| MD5: | DB8A70D9D0863093469D2DCC41E6A775 |
| SHA1: | 9EE89DACC64EECEA75C1D93A0DC8C0FBF0721C33 |
| SHA256: | E9C03A71D46C7F16356F81E0027CDF5D9F12803D89AF30163FFE9AD0A97AFFA5 |
| SSDEEP: | 393216:YtW+qtHmup15w3/kHmUyPczvm95qbavh9A0t9AfAB/E/eRrC4jAQn8JJCFn5LTA/:YtW+qtHmup15w3/kHmUyPczvm95qbavk |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process drops C-runtime libraries
- word.exe (PID: 7316)
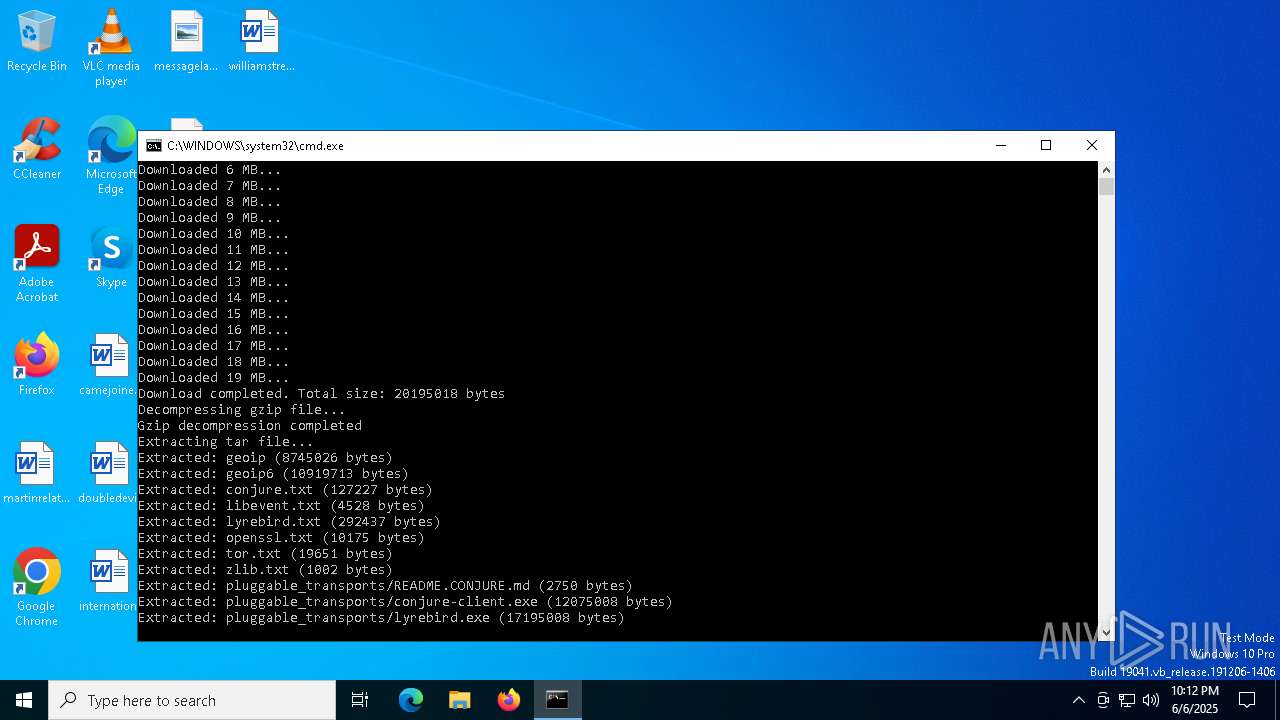
Process drops legitimate windows executable
- word.exe (PID: 7316)
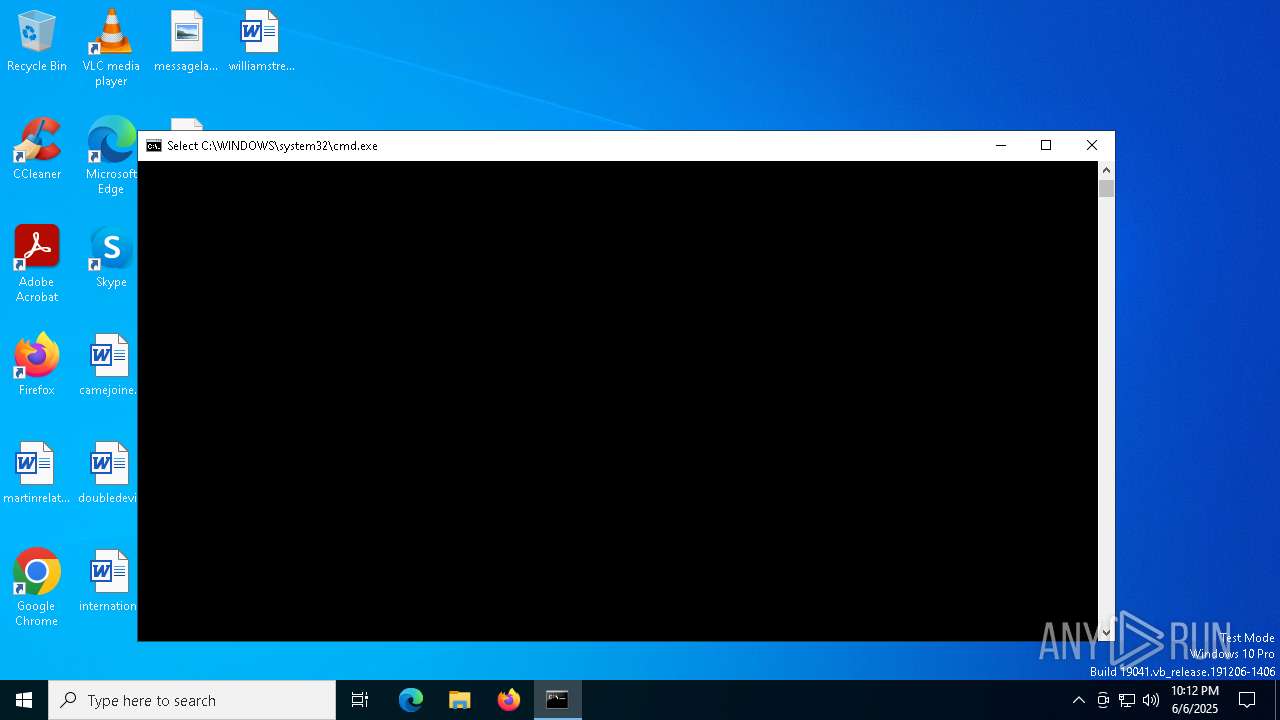
The executable file from the user directory is run by the CMD process
- java.exe (PID: 1244)
Executable content was dropped or overwritten
- java.exe (PID: 1244)
- word.exe (PID: 7316)
The process checks if it is being run in the virtual environment
- java.exe (PID: 1244)
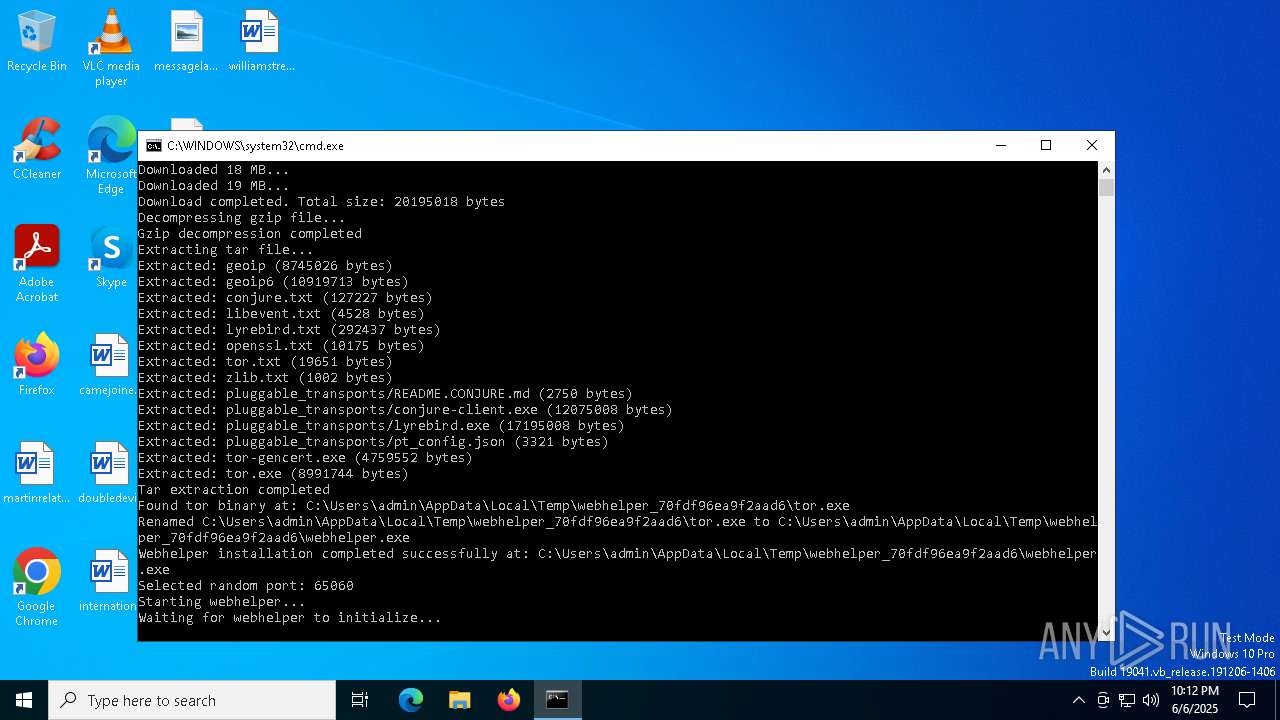
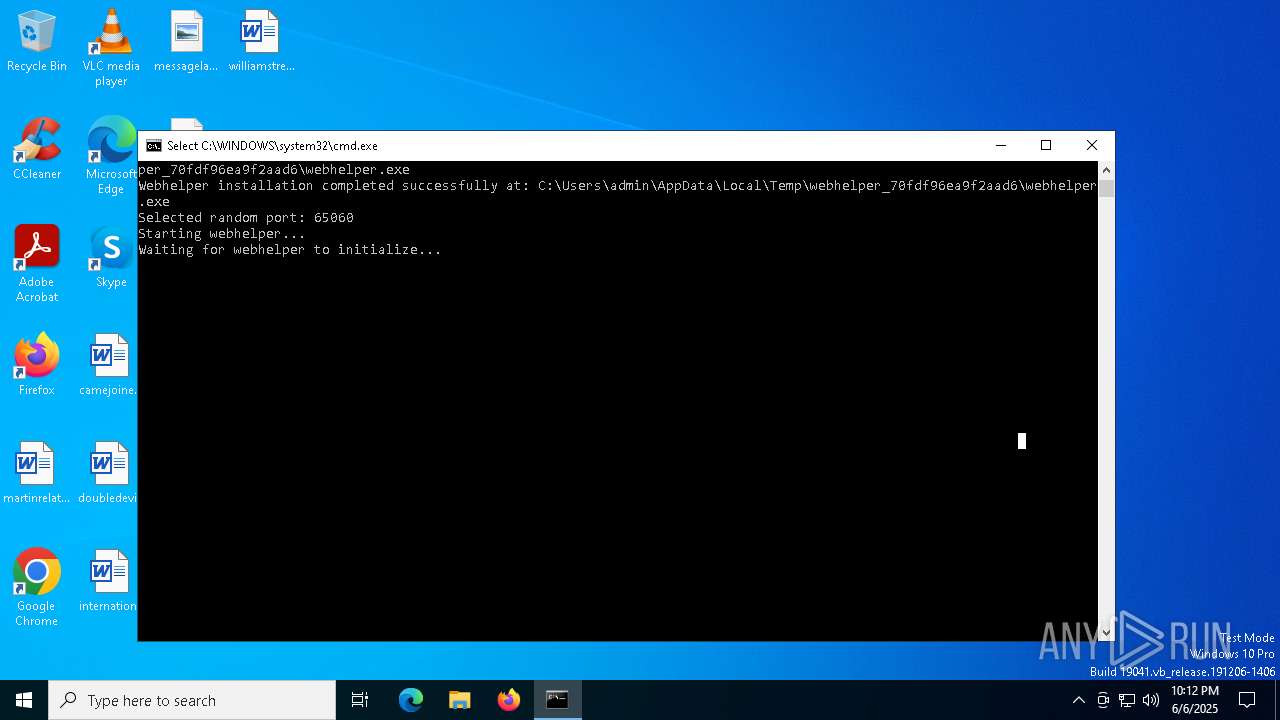
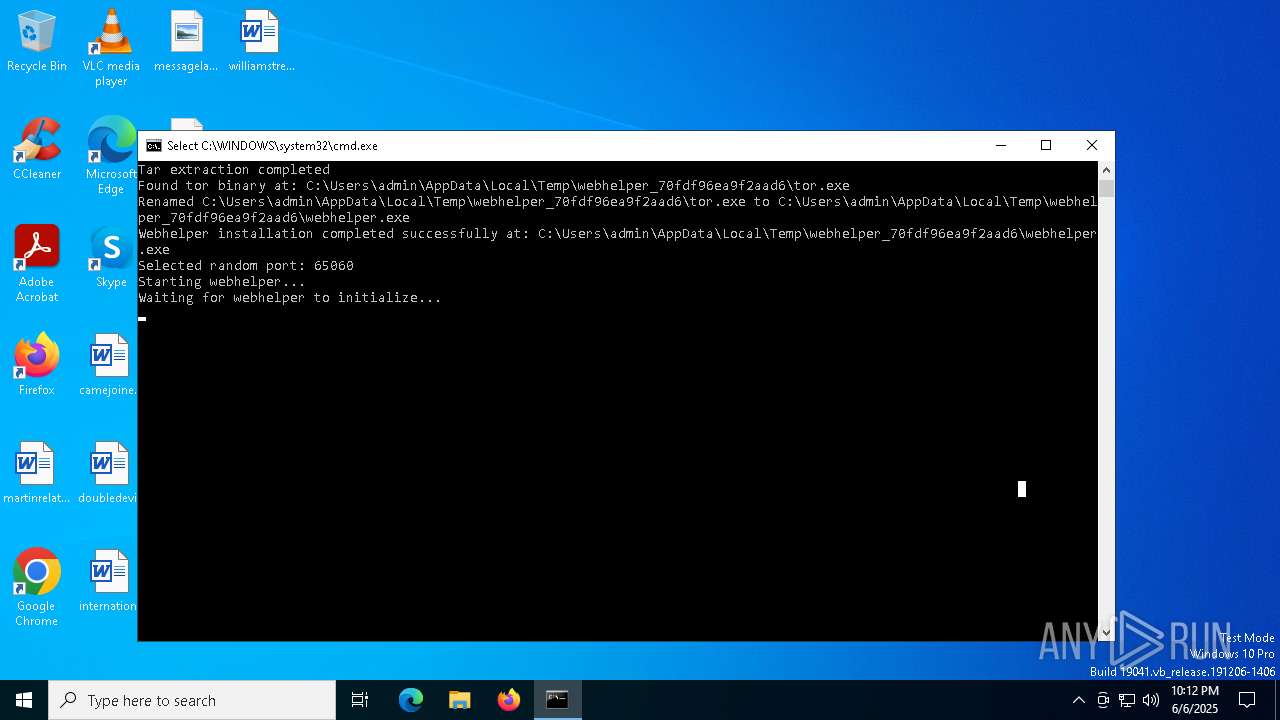
Connects to unusual port
- webhelper.exe (PID: 2568)
Starts CMD.EXE for commands execution
- word.exe (PID: 7316)
Reads security settings of Internet Explorer
- java.exe (PID: 1244)
INFO
Creates files or folders in the user directory
- java.exe (PID: 1244)
Checks supported languages
- word.exe (PID: 7316)
- webhelper.exe (PID: 2568)
- java.exe (PID: 1244)
Reads Environment values
- java.exe (PID: 1244)
Reads the computer name
- java.exe (PID: 1244)
- word.exe (PID: 7316)
- webhelper.exe (PID: 2568)
The sample compiled with english language support
- word.exe (PID: 7316)
Create files in a temporary directory
- word.exe (PID: 7316)
- webhelper.exe (PID: 2568)
- java.exe (PID: 1244)
Checks proxy server information
- java.exe (PID: 1244)
Reads the machine GUID from the registry
- java.exe (PID: 1244)
- webhelper.exe (PID: 2568)
Reads the software policy settings
- java.exe (PID: 1244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:06 22:09:55+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 2.4 |
| CodeSize: | 1818624 |
| InitializedDataSize: | 3701248 |
| UninitializedDataSize: | 4096 |
| EntryPoint: | 0x10f6 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
129
Monitored processes
7
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 644 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | webhelper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1244 | "C:\Users\admin\AppData\Local\Temp\runtime\jvm\bin\java.exe" -Djava.library.path="C:\Users\admin\AppData\Local\Temp\runtime" -cp . JNILoader | C:\Users\admin\AppData\Local\Temp\runtime\jvm\bin\java.exe | cmd.exe | ||||||||||||
User: admin Company: IBM Corporation Integrity Level: MEDIUM Description: IBM Semeru Runtime binary Version: 21.0.7.0 Modules
| |||||||||||||||
| 2568 | "C:\Users\admin\AppData\Local\Temp\webhelper_70fdf96ea9f2aad6\webhelper.exe" -f "C:\Users\admin\AppData\Local\Temp\webhelper_70fdf96ea9f2aad6\torrc" | C:\Users\admin\AppData\Local\Temp\webhelper_70fdf96ea9f2aad6\webhelper.exe | java.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5728 | C:\WINDOWS\system32\cmd.exe /c set PATH=C:\Users\admin\AppData\Local\Temp\runtime;%PATH% && cd "C:\Users\admin\AppData\Local\Temp\runtime" && "C:\Users\admin\AppData\Local\Temp\runtime\jvm\bin\java.exe" -Djava.library.path="C:\Users\admin\AppData\Local\Temp\runtime" -cp . JNILoader | C:\Windows\System32\cmd.exe | — | word.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6248 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7316 | "C:\Users\admin\AppData\Local\Temp\word.exe" | C:\Users\admin\AppData\Local\Temp\word.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 7852 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 230
Read events
2 227
Write events
3
Delete events
0
Modification events
| (PID) Process: | (1244) java.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1244) java.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1244) java.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
136
Suspicious files
13
Text files
275
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7316 | word.exe | C:\Users\admin\AppData\Local\Temp\runtime\jvm.tar.gz | — | |
MD5:— | SHA256:— | |||
| 7316 | word.exe | C:\Users\admin\AppData\Local\Temp\runtime\jdk-21.0.7+6-jre\bin\api-ms-win-core-errorhandling-l1-1-0.dll | executable | |
MD5:257DD7F0FCD0D44D250B137A768A088E | SHA256:8AFF0BBC8148317C91DFF126FD346266EE1763E86C17FF7152E561005C876FE3 | |||
| 7316 | word.exe | C:\Users\admin\AppData\Local\Temp\runtime\JNILoader.class | binary | |
MD5:01EF331C79582C5F6EC1B438186FA709 | SHA256:600023E3A93ACF0C2103AE42B3DE7802CB55EF6FEBDDC92AE99606025C998C13 | |||
| 7316 | word.exe | C:\Users\admin\AppData\Local\Temp\runtime\jdk-21.0.7+6-jre\bin\api-ms-win-core-datetime-l1-1-0.dll | executable | |
MD5:BE69F5B751F68B767F6DE67C6031EE1D | SHA256:BF09558A8675EC3F6293A978C9E1646B544D1E7CCEB6F50BB60D0D2884127DDA | |||
| 7316 | word.exe | C:\Users\admin\AppData\Local\Temp\runtime\jdk-21.0.7+6-jre\bin\api-ms-win-core-console-l1-1-0.dll | executable | |
MD5:5B59567B0C75089B88A855740D039BD8 | SHA256:B6998B3568735638795585044ABE39D98E5CCB75BF693152F9CDEEA34B8EF2EA | |||
| 7316 | word.exe | C:\Users\admin\AppData\Local\Temp\runtime\jdk-21.0.7+6-jre\bin\api-ms-win-core-handle-l1-1-0.dll | executable | |
MD5:5A7F590FD08D06CC8298837DCDEDB2BE | SHA256:C81EEAD0E8681AC16298AAED8F203D126C9EB19CAF8FA183179FADE8C0AF165A | |||
| 7316 | word.exe | C:\Users\admin\AppData\Local\Temp\runtime\jdk-21.0.7+6-jre\bin\api-ms-win-core-interlocked-l1-1-0.dll | executable | |
MD5:A307921604527116C69FF1E839F066DB | SHA256:07FC8BABCB8F092EB2A180183CC06BE181B9BFA432B1ED3CCFA6F4B355F469B6 | |||
| 7316 | word.exe | C:\Users\admin\AppData\Local\Temp\runtime\jdk-21.0.7+6-jre\bin\api-ms-win-core-file-l1-2-0.dll | executable | |
MD5:FB3BD208799D3ADF88954EE5A066AC5A | SHA256:42ACC4086C60FB958B6CC0FA4B0C89AD75D3CA933B3ABB6BD11536308C942F14 | |||
| 7316 | word.exe | C:\Users\admin\AppData\Local\Temp\runtime\jdk-21.0.7+6-jre\bin\api-ms-win-core-file-l2-1-0.dll | executable | |
MD5:DA124D272E1EEEA56E446FEC95AFADA1 | SHA256:2CA25EA0322D32CCEE119C32D604C39FCDA254A140FADA57374D523265BE8DBB | |||
| 7316 | word.exe | C:\Users\admin\AppData\Local\Temp\runtime\jdk-21.0.7+6-jre\bin\api-ms-win-core-console-l1-2-0.dll | executable | |
MD5:1307FF6815D39C2B6E1B67832BA34B6B | SHA256:DCB1DDFA6283118C0D9B8104D5FAA3F1866D756101D791EA75E558E04126B6C1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
33
DNS requests
21
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
756 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1244 | java.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTPlNxcMEqnlIVyH5VuZ4lawhZX3QQU9oUKOxGG4QR9DqoLLNLuzGR7e64CEQCrZoa1YnvoBZaCEzAShkn1 | unknown | — | — | whitelisted |
4452 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4452 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6960 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3760 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7316 | word.exe | 140.82.121.3:443 | github.com | GITHUB | US | whitelisted |
756 | lsass.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | whitelisted |
756 | lsass.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
github.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
objects.githubusercontent.com |
| whitelisted |
archive.torproject.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2568 | webhelper.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 90 |
2568 | webhelper.exe | Misc Attack | ET TOR Known Tor Exit Node Traffic group 89 |
2568 | webhelper.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 250 |
2568 | webhelper.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 704 |