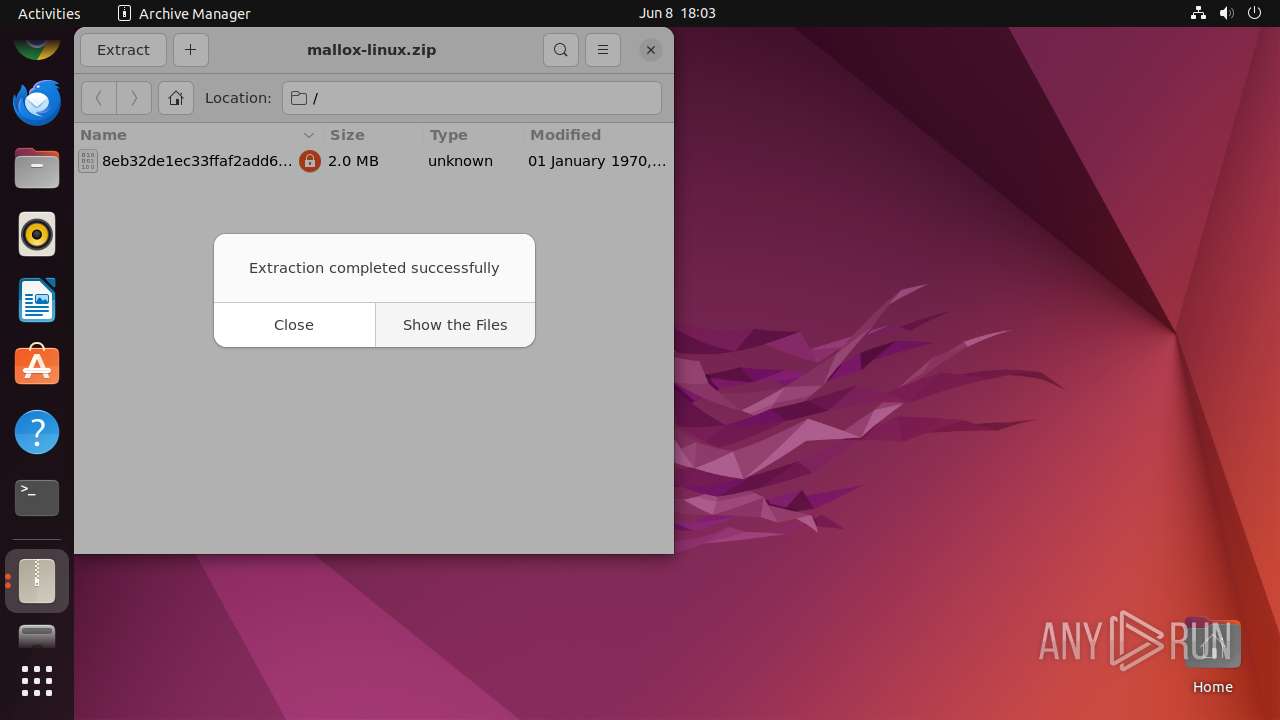
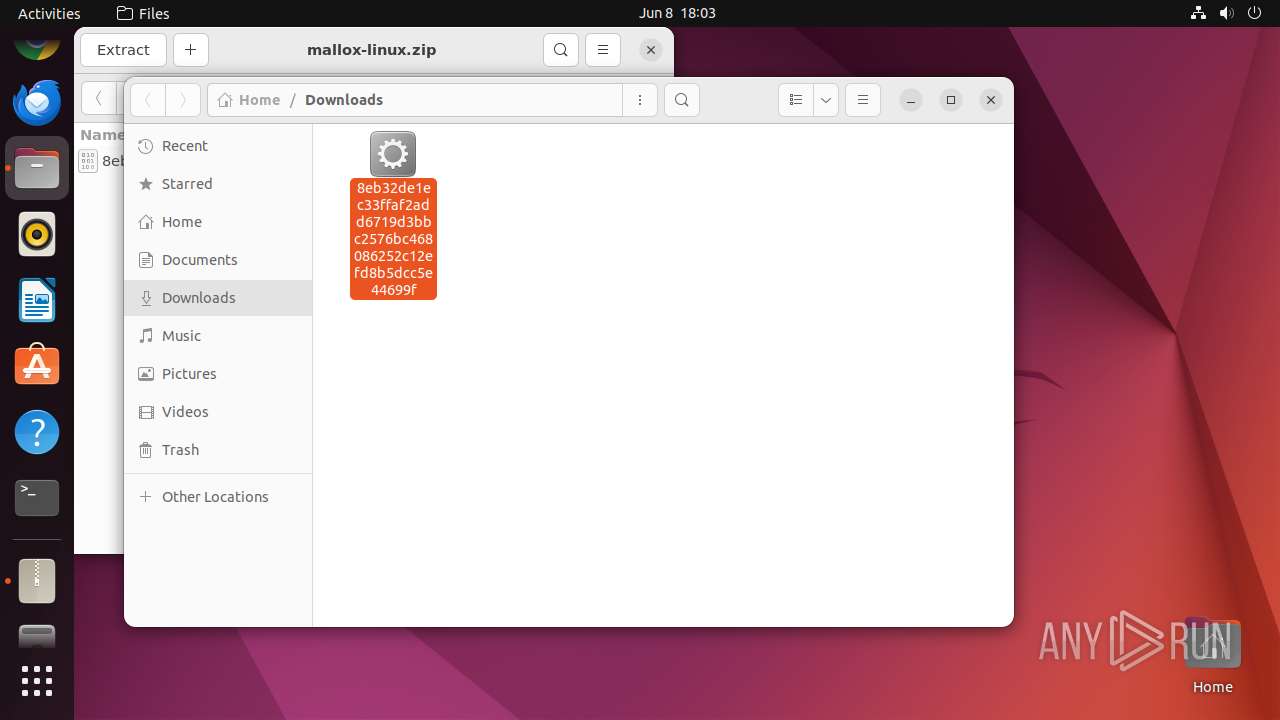
| File name: | mallox-linux.zip |
| Full analysis: | https://app.any.run/tasks/235daed6-9631-4659-9fd9-662cd98f4fd0 |
| Verdict: | Malicious activity |
| Analysis date: | June 08, 2024, 17:02:46 |
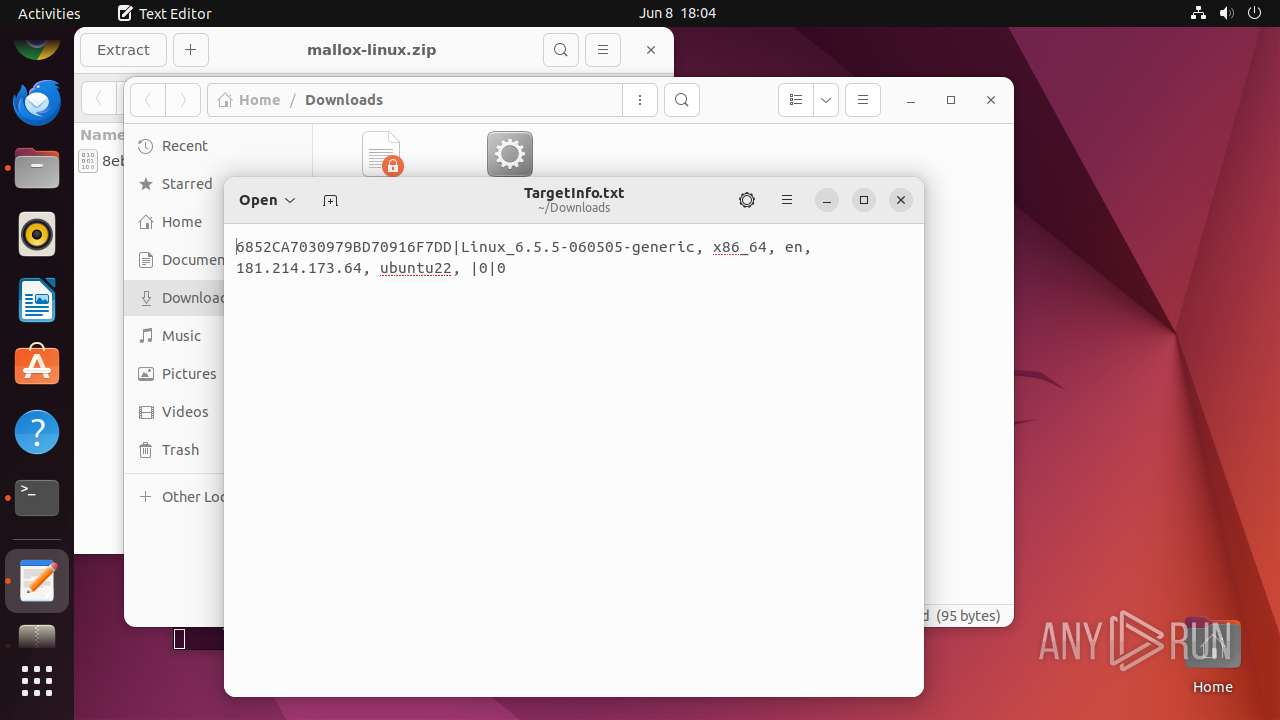
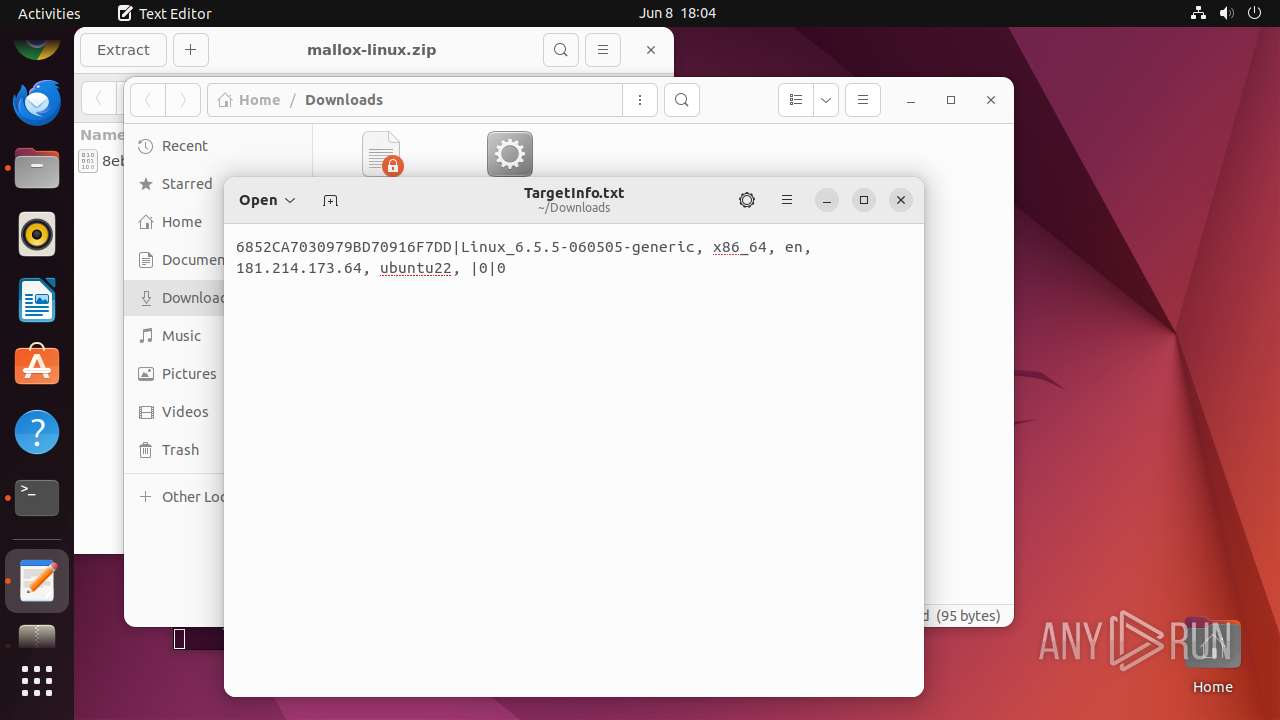
| OS: | Ubuntu 22.04.2 |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 9F41AB9D1E98C63872CB681C31FE1953 |
| SHA1: | AA56EE683F841614959930C711BB38E342D77061 |
| SHA256: | E98B35F3D400BA5A8042C3C24EC8B048A4F39E663C2E1A3FB58CC301DA6E87CB |
| SSDEEP: | 49152:n06CkRSLPrBg7k1C+Bkf3ndbTSkpSUz5SdjrwtH3hyxgm+TdRszha+j19I7K2cSp:ukQzKA1RBQ3tpPgVWIxoTdC1d1z2gJn2 |
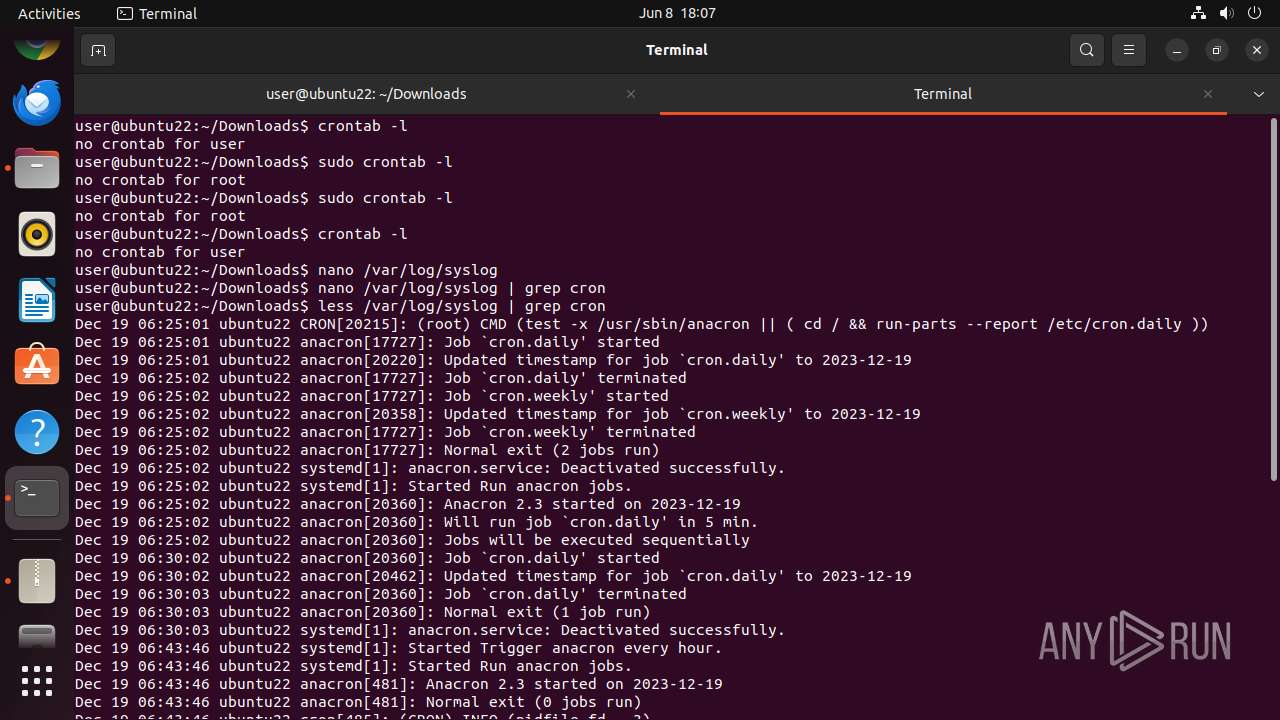
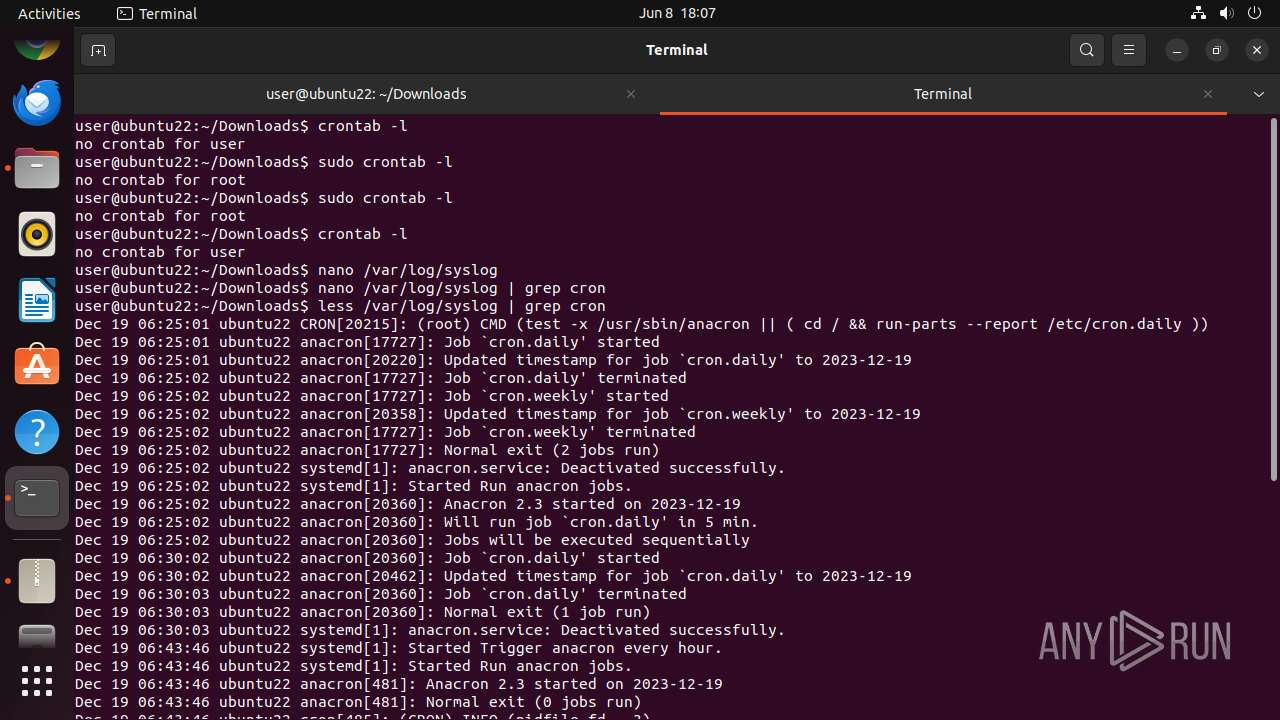
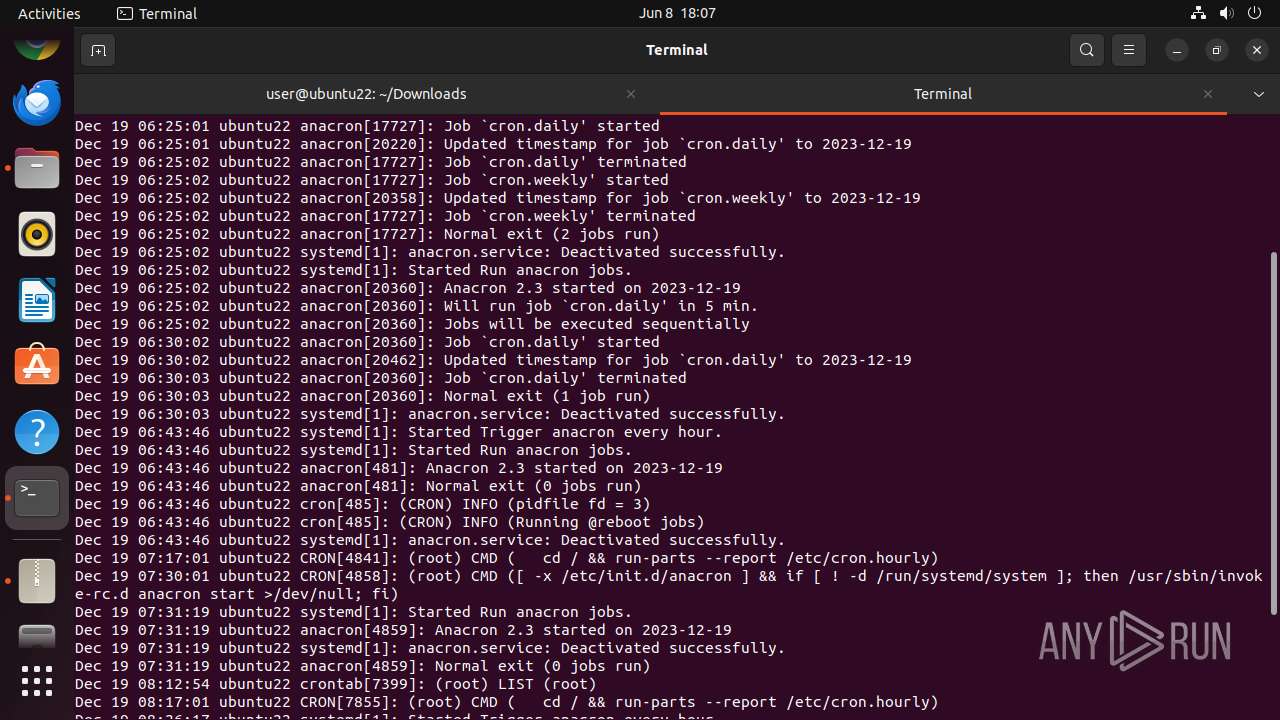
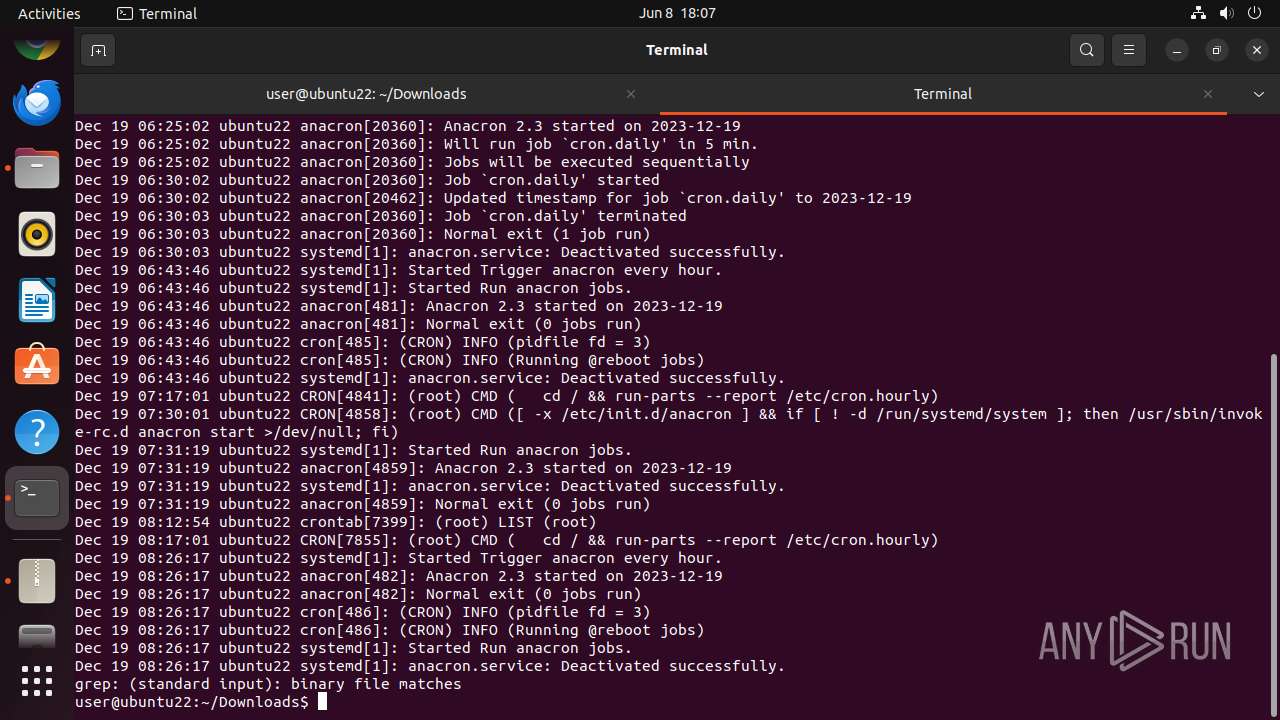
MALICIOUS
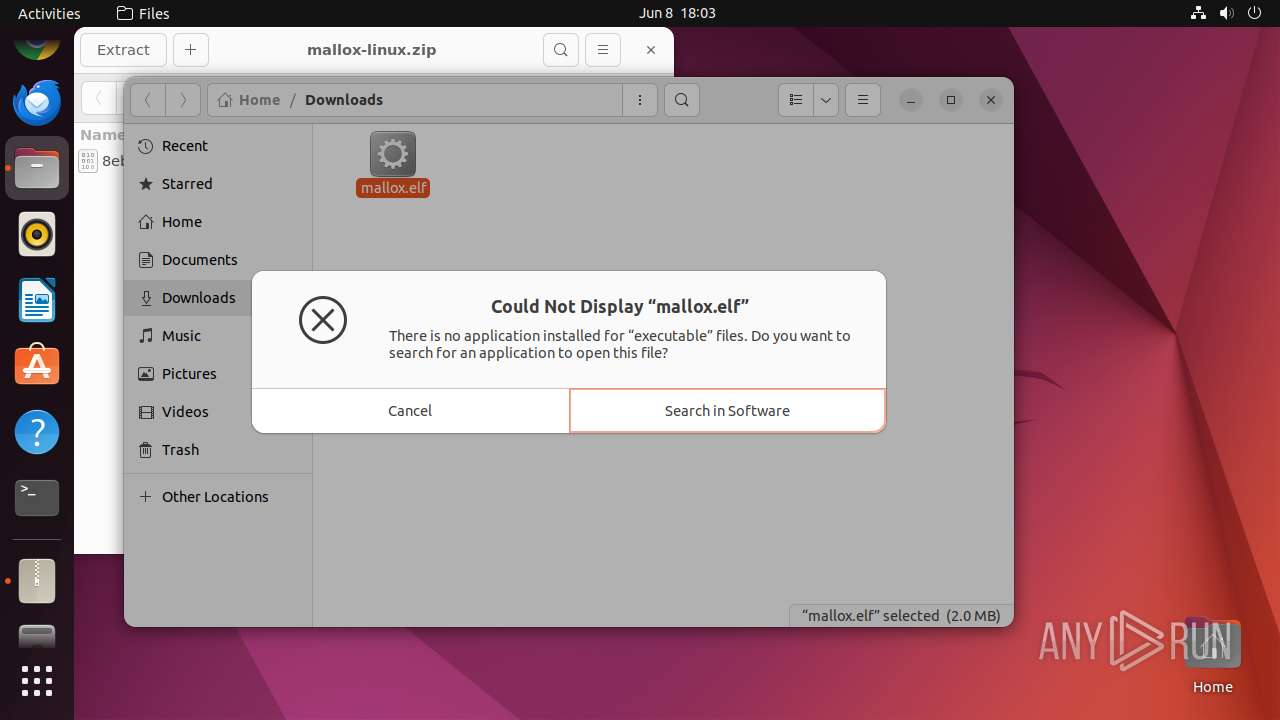
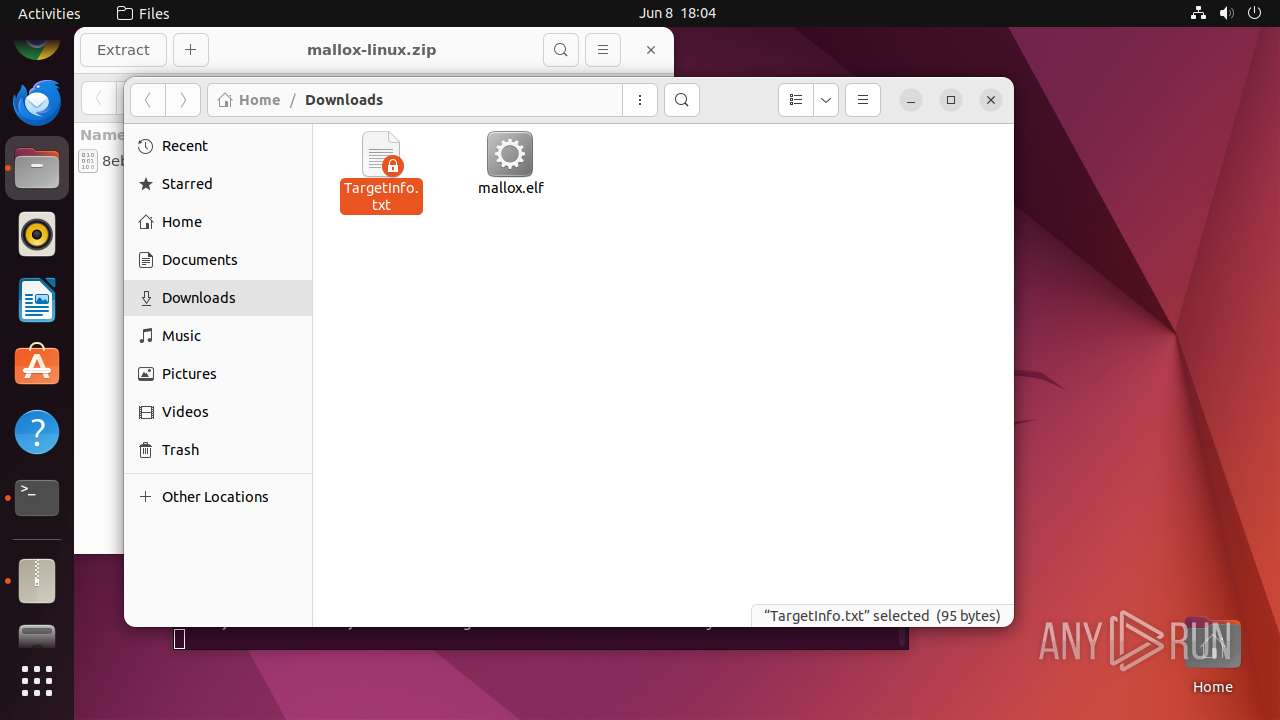
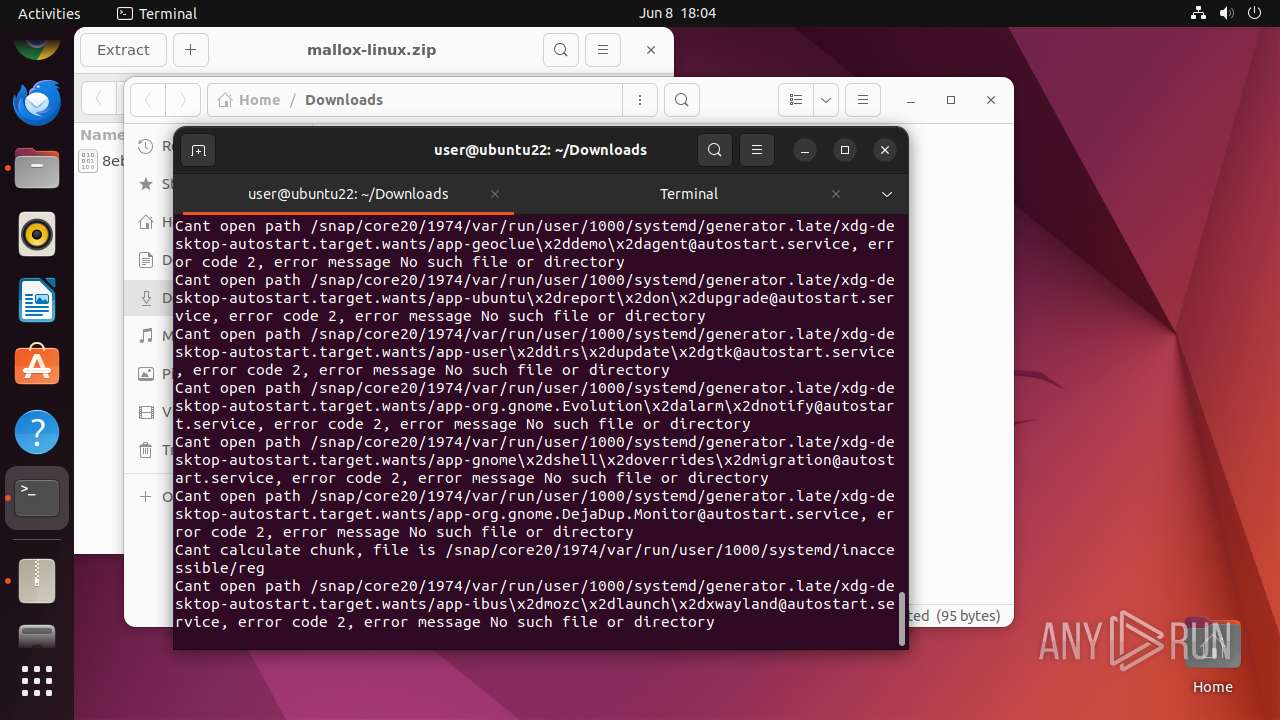
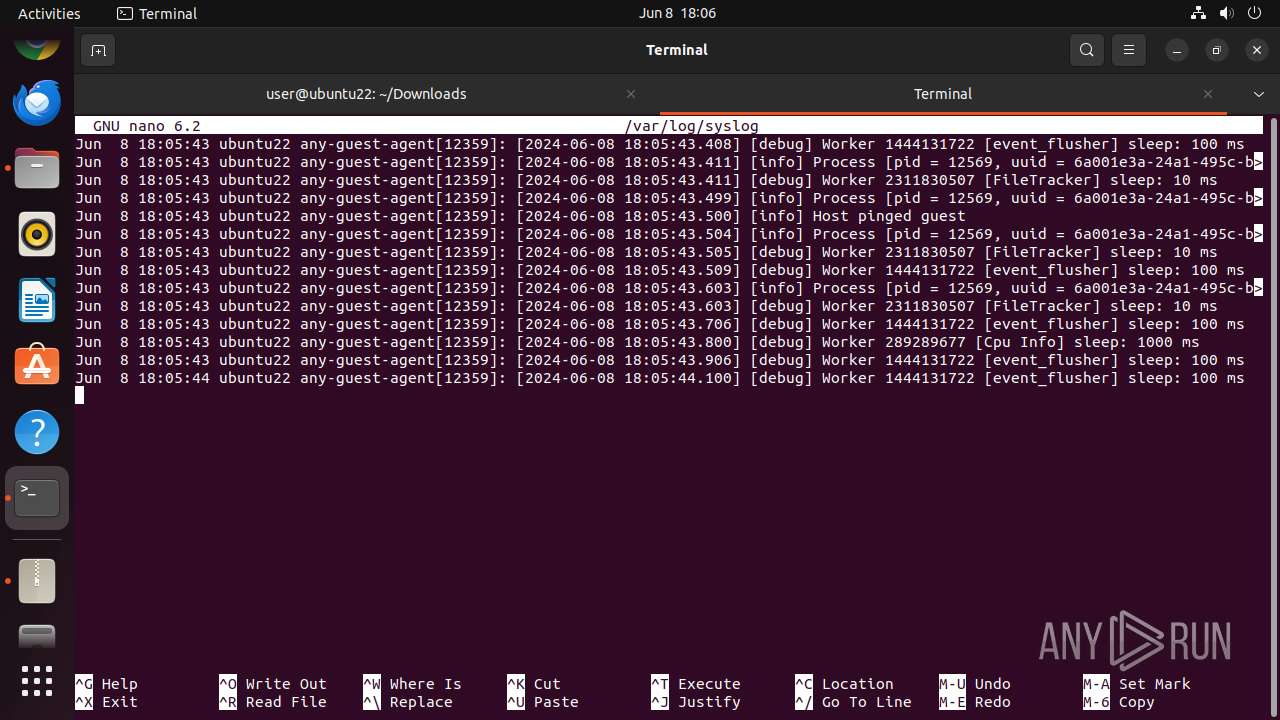
Drops the executable file immediately after the start
- mallox.elf (PID: 12569)
SUSPICIOUS
Checks DMI information (probably VM detection)
- systemd-hostnamed (PID: 12465)
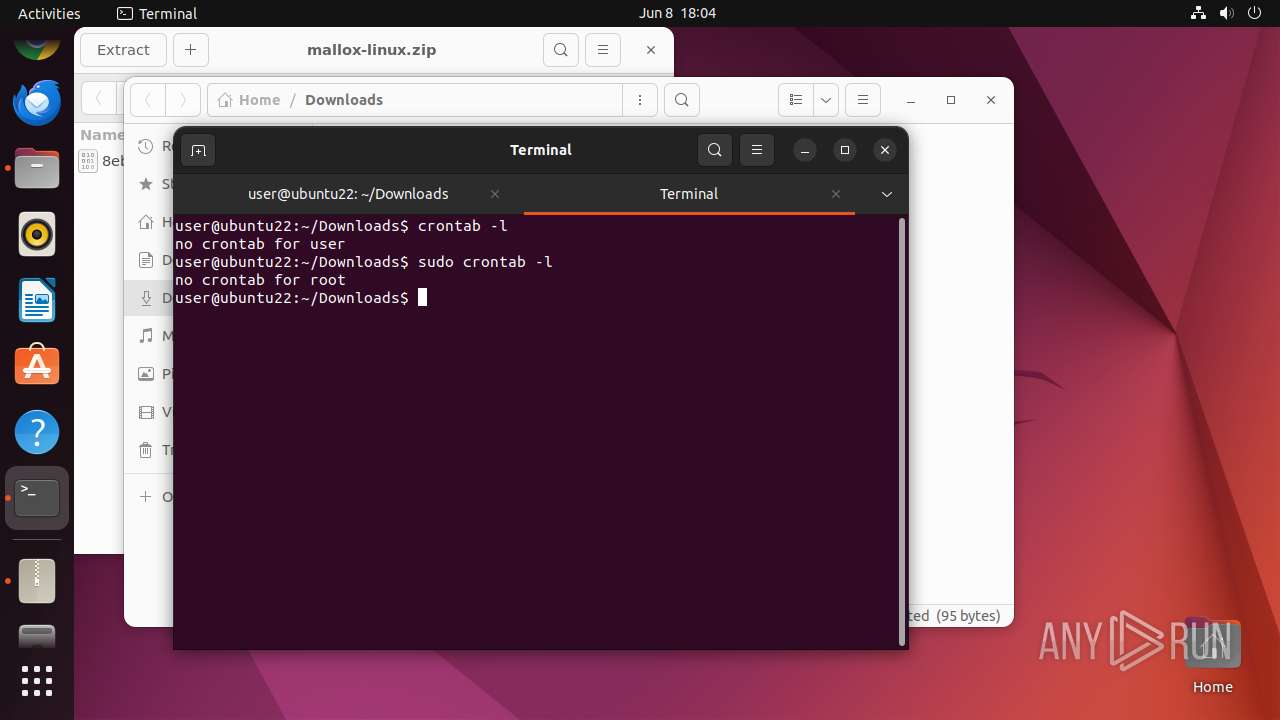
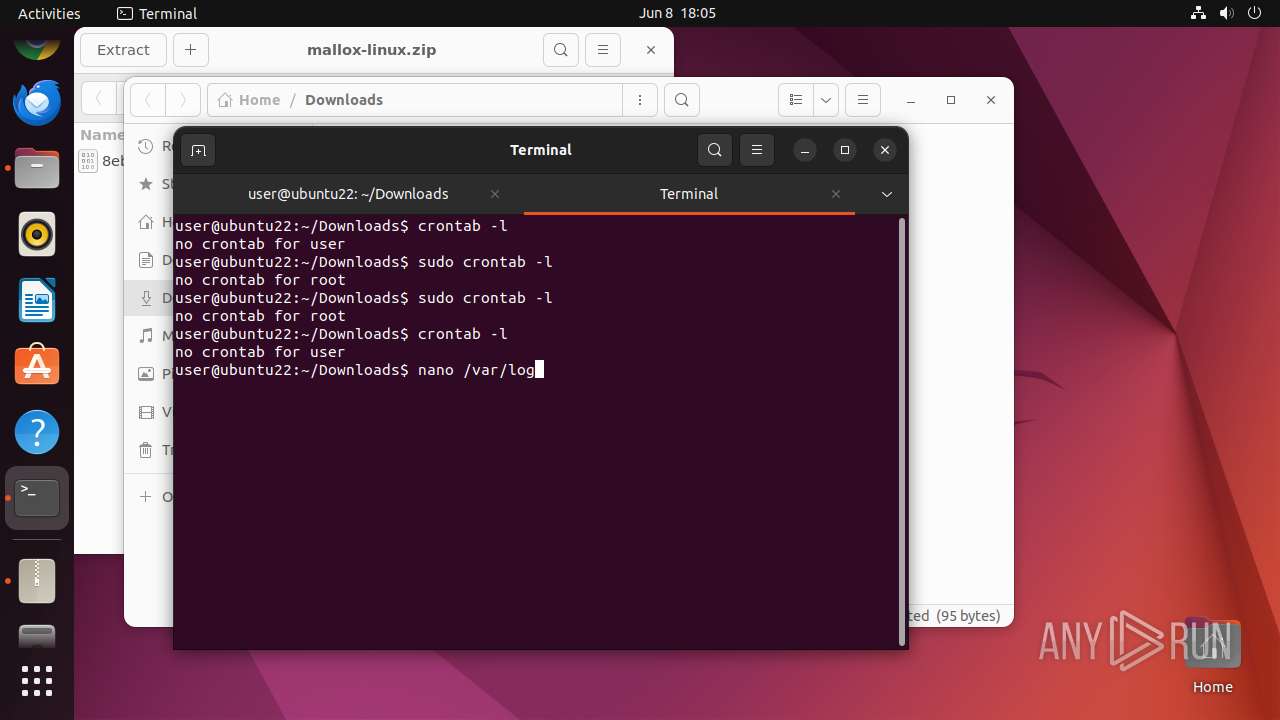
Executes commands using command-line interpreter
- gnome-terminal-server (PID: 12528)
Modifies bash configuration script
- mallox.elf (PID: 12569)
INFO
The dropped object may contain a URL to Tor Browser
- mallox.elf (PID: 12569)
Dropped object may contain TOR URL's
- mallox.elf (PID: 12569)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x144fe78c |
| ZipCompressedSize: | 869349 |
| ZipUncompressedSize: | 1991784 |
| ZipFileName: | 8eb32de1ec33ffaf2add6719d3bbc2576bc468086252c12efd8b5dcc5e44699f |
Total processes
247
Monitored processes
34
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 12434 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 12435 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 12436 | sh -c "file --mime-type /tmp/mallox-linux\.zip" | /bin/sh | — | any-guest-agent |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 12437 | file --mime-type /tmp/mallox-linux.zip | /usr/bin/file | — | sh |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 12438 | /bin/sh -c "DISPLAY=:0 sudo -iu user file-roller /tmp/mallox-linux\.zip " | /bin/sh | — | any-guest-agent |
User: root Integrity Level: UNKNOWN | ||||
| 12439 | sudo -iu user file-roller /tmp/mallox-linux.zip | /usr/bin/sudo | — | sh |
User: root Integrity Level: UNKNOWN | ||||
| 12440 | file-roller /tmp/mallox-linux.zip | /usr/bin/file-roller | — | sudo |
User: user Integrity Level: UNKNOWN | ||||
| 12441 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | file-roller |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 12446 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 485 | ||||
| 12458 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 12440 | ||||
Executable files
0
Suspicious files
741
Text files
316
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 12440 | file-roller | /home/user/.local/share/recently-used.xbel | xml | |
MD5:— | SHA256:— | |||
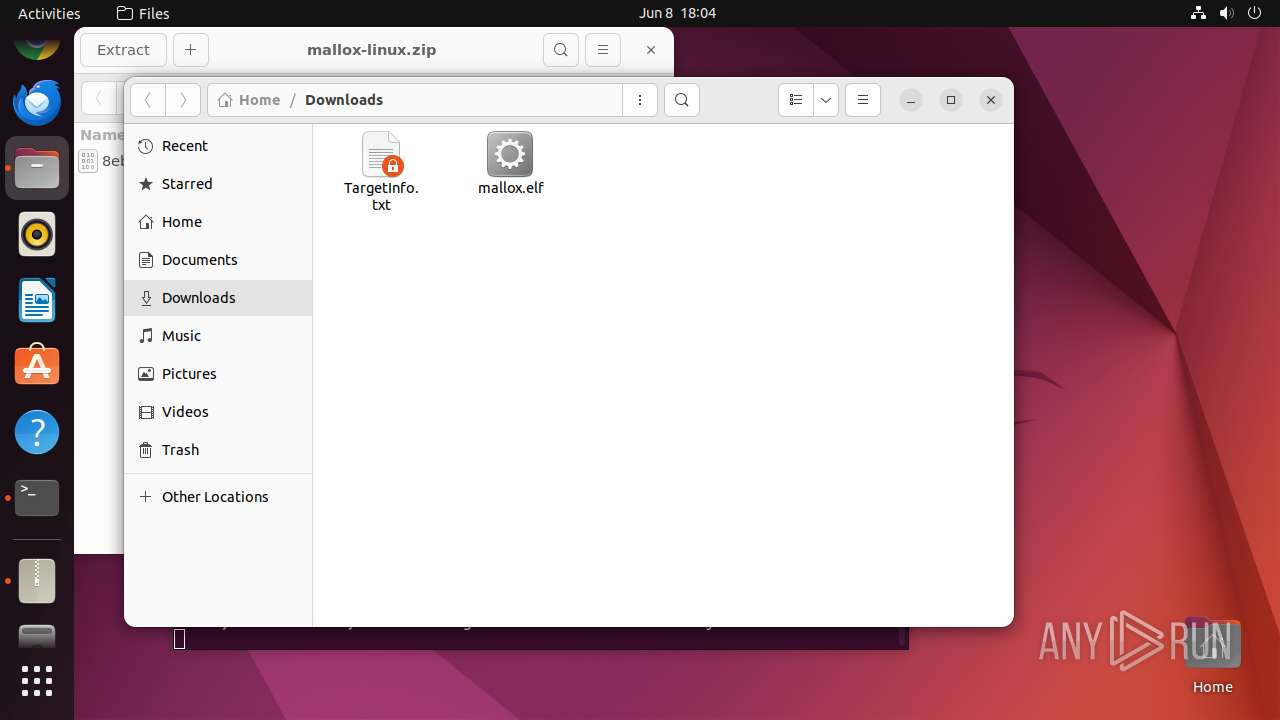
| 12569 | mallox.elf | /home/user/Downloads/TargetInfo.txt | text | |
MD5:— | SHA256:— | |||
| 12569 | mallox.elf | /home/user/test_files/HOW TO DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 12569 | mallox.elf | /home/user/.pki/nssdb/HOW TO DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 12569 | mallox.elf | /home/user/.cache/ubuntu-report/HOW TO DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 12569 | mallox.elf | /home/user/.cache/gnome-desktop-thumbnailer/gstreamer-1.0/HOW TO DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 12569 | mallox.elf | /home/user/.cache/gnome-software/screenshots/624x351/HOW TO DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 12569 | mallox.elf | /home/user/.cache/gnome-software/icons/HOW TO DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 12569 | mallox.elf | /home/user/.cache/gnome-software/odrs/HOW TO DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 12569 | mallox.elf | /home/user/.cache/gnome-software/appstream/HOW TO DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
17
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 185.125.190.96:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | unknown |
— | — | GET | 204 | 185.125.190.96:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | unknown |
12569 | mallox.elf | GET | 200 | 172.67.74.152:80 | http://api.ipify.org/ | unknown | — | — | unknown |
12569 | mallox.elf | GET | 200 | 172.67.74.152:80 | http://api.ipify.org/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 185.125.190.96:80 | connectivity-check.ubuntu.com | Canonical Group Limited | GB | unknown |
470 | avahi-daemon | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 91.189.91.97:80 | connectivity-check.ubuntu.com | Canonical Group Limited | US | unknown |
— | — | 156.146.33.141:443 | odrs.gnome.org | Datacamp Limited | DE | unknown |
— | — | 185.125.188.55:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
485 | snapd | 185.125.188.54:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
485 | snapd | 185.125.188.58:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
12476 | gvfsd-smb-browse | 192.168.100.255:137 | — | — | — | whitelisted |
12569 | mallox.elf | 172.67.74.152:80 | api.ipify.org | CLOUDFLARENET | US | unknown |
12569 | mallox.elf | 91.215.85.142:80 | — | — | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
odrs.gnome.org |
| unknown |
api.snapcraft.io |
| unknown |
192.100.168.192.in-addr.arpa |
| unknown |
connectivity-check.ubuntu.com |
| unknown |
api.ipify.org |
| shared |