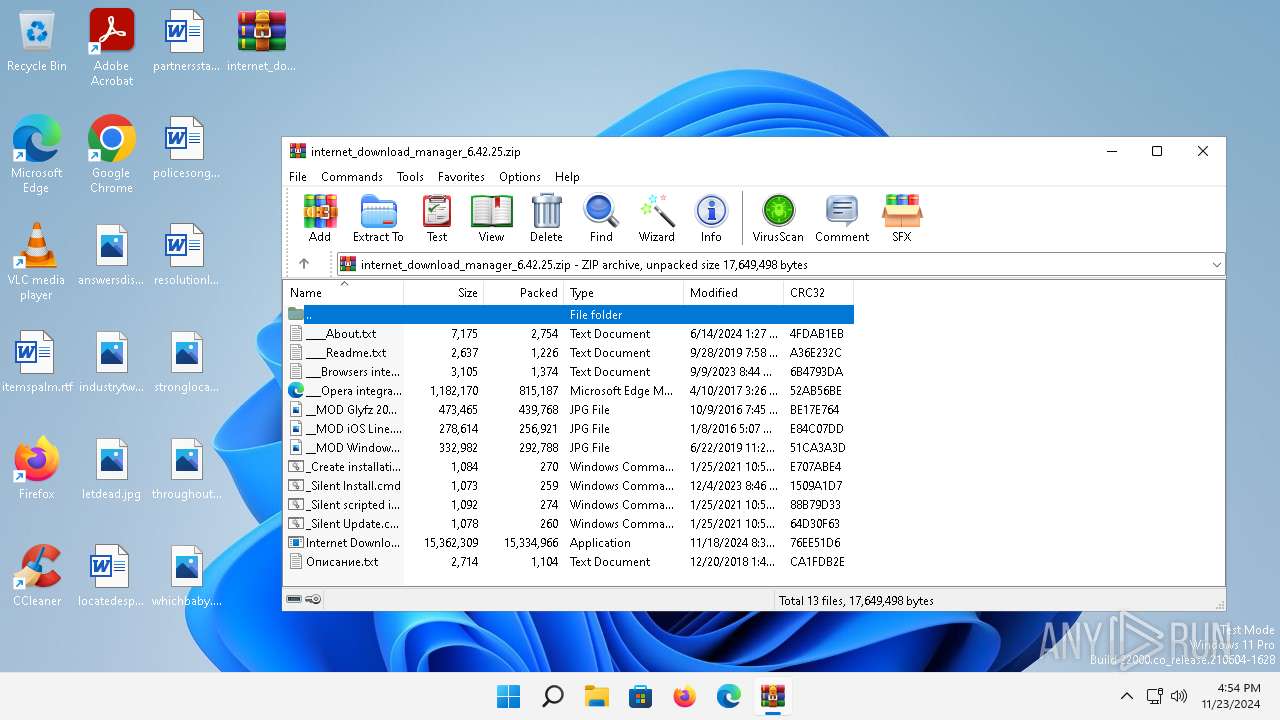
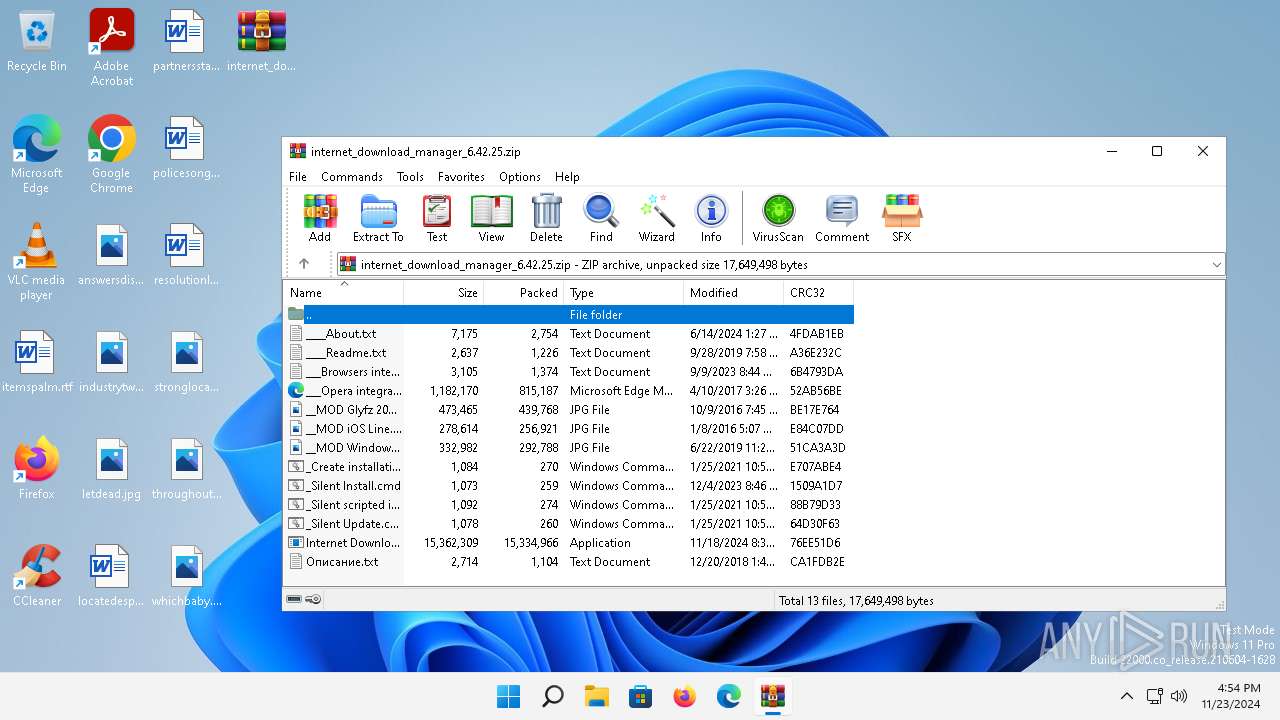
| File name: | internet_download_manager_6.42.25.zip |
| Full analysis: | https://app.any.run/tasks/ddde13c9-8180-4270-a442-9195c226d42d |
| Verdict: | Malicious activity |
| Analysis date: | November 23, 2024, 16:54:31 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 6E477E05A33AC4AC475FEC8674746AB5 |
| SHA1: | E46C96F8D6364BF27BE619854E996B8BED609516 |
| SHA256: | E982C59B70FAE4D269DD4C34B502A81F26668BAD00F7DCCD372D50EC71D939AE |
| SSDEEP: | 98304:rgPwpz5ti/jnbRzBn31+JhrLmlN5LMkepk0l4k+hzxsZsCelyrREnamtdzTSrzXh:mMuDLZGla9jmYxNhxz0xWAbCbulT |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6468)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6468)
- Notepad.exe (PID: 6136)
- Notepad.exe (PID: 452)
- Notepad.exe (PID: 3220)
- Notepad.exe (PID: 1808)
Reads the Internet Settings
- Notepad.exe (PID: 6136)
- Notepad.exe (PID: 452)
- Notepad.exe (PID: 3220)
- Notepad.exe (PID: 1808)
- rundll32.exe (PID: 3868)
INFO
Manual execution by a user
- cmd.exe (PID: 2132)
- Notepad.exe (PID: 6136)
- cmd.exe (PID: 4292)
- cmd.exe (PID: 5664)
- cmd.exe (PID: 2808)
- Notepad.exe (PID: 452)
- Notepad.exe (PID: 3220)
- Notepad.exe (PID: 1808)
- rundll32.exe (PID: 3868)
- rundll32.exe (PID: 1564)
Reads the computer name
- Notepad.exe (PID: 6136)
- Notepad.exe (PID: 452)
- Notepad.exe (PID: 3220)
- Notepad.exe (PID: 1808)
Checks supported languages
- Notepad.exe (PID: 6136)
- Notepad.exe (PID: 452)
- Notepad.exe (PID: 3220)
- Notepad.exe (PID: 1808)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 3868)
Reads Microsoft Office registry keys
- rundll32.exe (PID: 3868)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2016:10:09 22:45:54 |
| ZipCRC: | 0xbe17e764 |
| ZipCompressedSize: | 439768 |
| ZipUncompressedSize: | 473465 |
| ZipFileName: | __MOD Glyfz 2016.jpg |
Total processes
132
Monitored processes
15
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
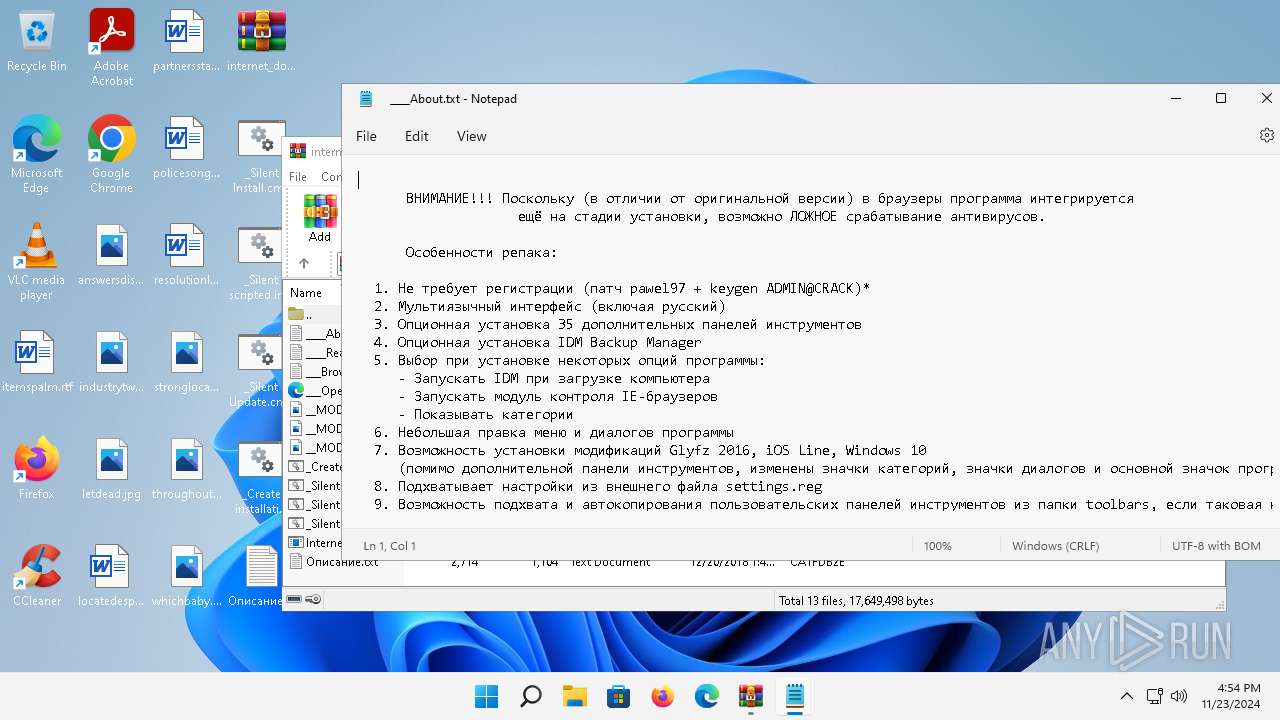
| 452 | "C:\Windows\system32\notepad.exe" C:\Users\admin\Desktop\____About.txt | C:\Program Files\WindowsApps\Microsoft.WindowsNotepad_11.2205.11.0_x64__8wekyb3d8bbwe\Notepad\Notepad.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
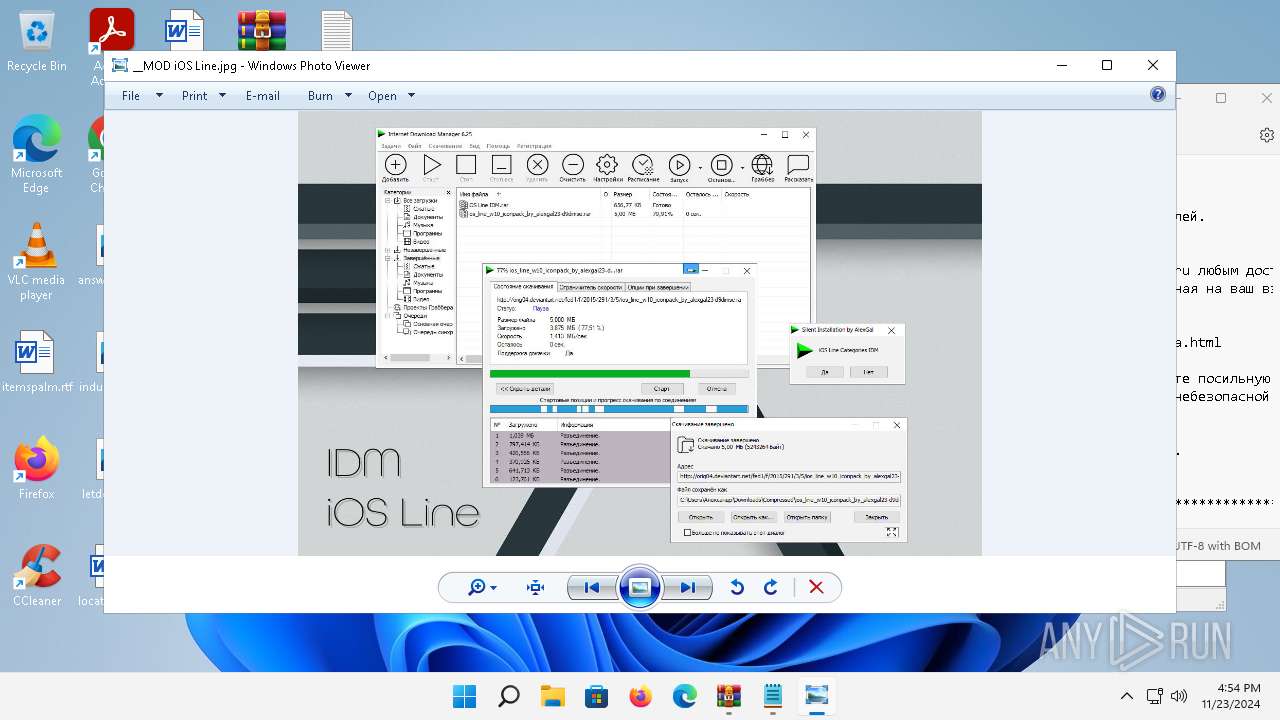
| 1564 | "C:\Windows\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\Desktop\__MOD iOS Line.jpg | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
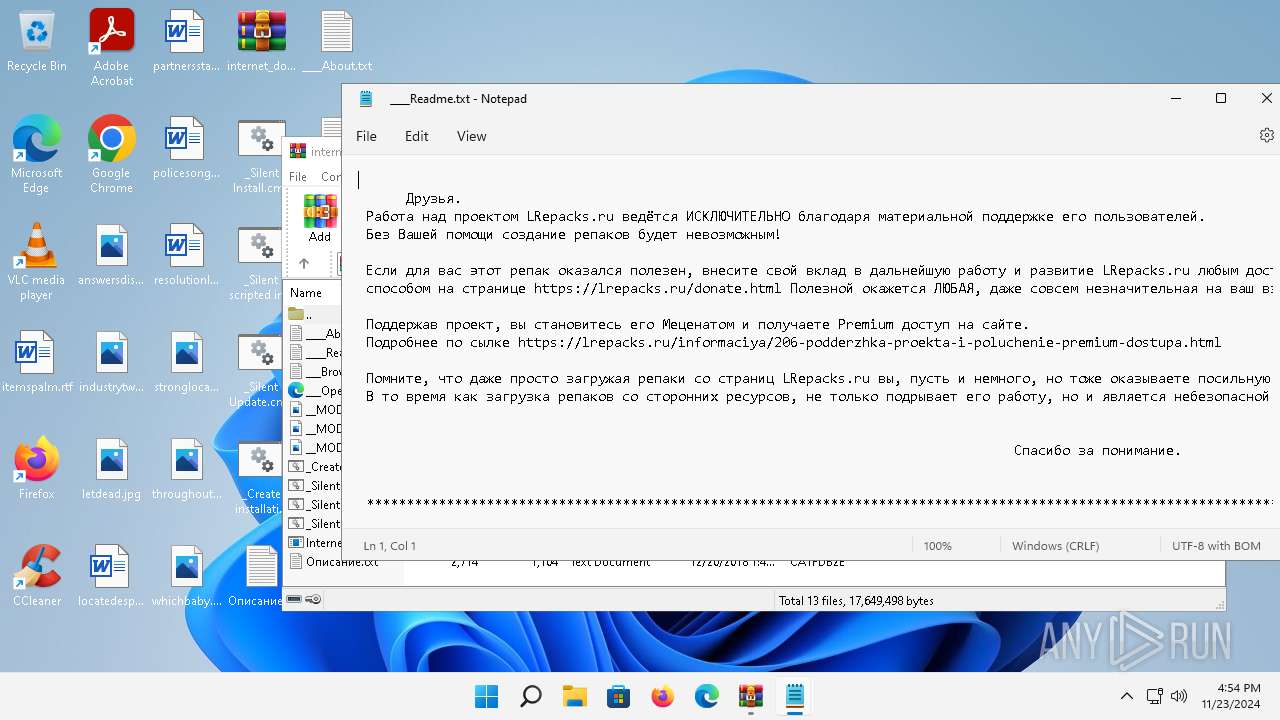
| 1808 | "C:\Windows\system32\notepad.exe" C:\Users\admin\Desktop\____Readme.txt | C:\Program Files\WindowsApps\Microsoft.WindowsNotepad_11.2205.11.0_x64__8wekyb3d8bbwe\Notepad\Notepad.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2132 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\_Silent Update.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2808 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\_Silent Install.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
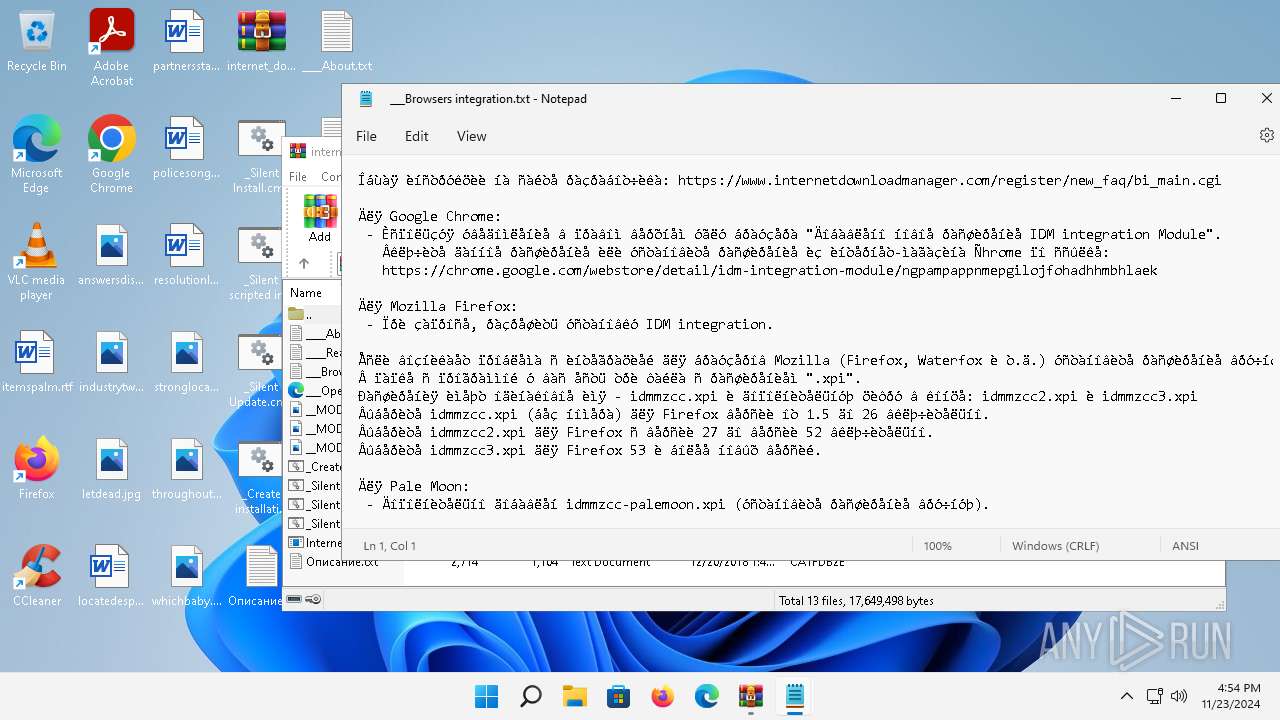
| 3220 | "C:\Windows\system32\notepad.exe" "C:\Users\admin\Desktop\___Browsers integration.txt" | C:\Program Files\WindowsApps\Microsoft.WindowsNotepad_11.2205.11.0_x64__8wekyb3d8bbwe\Notepad\Notepad.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 3828 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3868 | "C:\Windows\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\Desktop\__MOD Windows 10.jpg | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4292 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\_Create installation script.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5664 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\_Silent scripted installation.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 623
Read events
15 604
Write events
19
Delete events
0
Modification events
| (PID) Process: | (6468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\internet_download_manager_6.42.25.zip | |||
| (PID) Process: | (6468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6468) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\4c\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\acppage.dll,-6003 |
Value: Windows Command Script | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
35
DNS requests
32
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4368 | firefox.exe | POST | 200 | 184.24.77.56:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
6956 | MoUsoCoreWorker.exe | GET | 304 | 23.50.131.205:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e62ea634f0bfd038 | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.55.161.191:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
4368 | firefox.exe | POST | 200 | 184.24.77.56:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
3420 | rundll32.exe | GET | 304 | 23.50.131.205:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1ef392ec4b03121e | unknown | — | — | whitelisted |
4368 | firefox.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | — | — | whitelisted |
4368 | firefox.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | — | — | whitelisted |
4368 | firefox.exe | POST | 200 | 184.24.77.56:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
2860 | svchost.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?0b3de69d37a33f41 | unknown | — | — | whitelisted |
2860 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?a32176130b135011 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3420 | rundll32.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3840 | OfficeC2RClient.exe | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
4368 | firefox.exe | 34.149.100.209:443 | firefox.settings.services.mozilla.com | GOOGLE | US | whitelisted |
4368 | firefox.exe | 34.120.208.123:443 | incoming.telemetry.mozilla.org | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
— | — | 23.55.161.191:80 | — | Akamai International B.V. | DE | unknown |
5552 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6956 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6956 | MoUsoCoreWorker.exe | 23.50.131.205:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
4368 | firefox.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
firefox.settings.services.mozilla.com |
| whitelisted |
incoming.telemetry.mozilla.org |
| whitelisted |
prod.remote-settings.prod.webservices.mozgcp.net |
| whitelisted |
telemetry-incoming.r53-2.services.mozilla.com |
| whitelisted |
google.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r10.o.lencr.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Microsoft Connection Test |