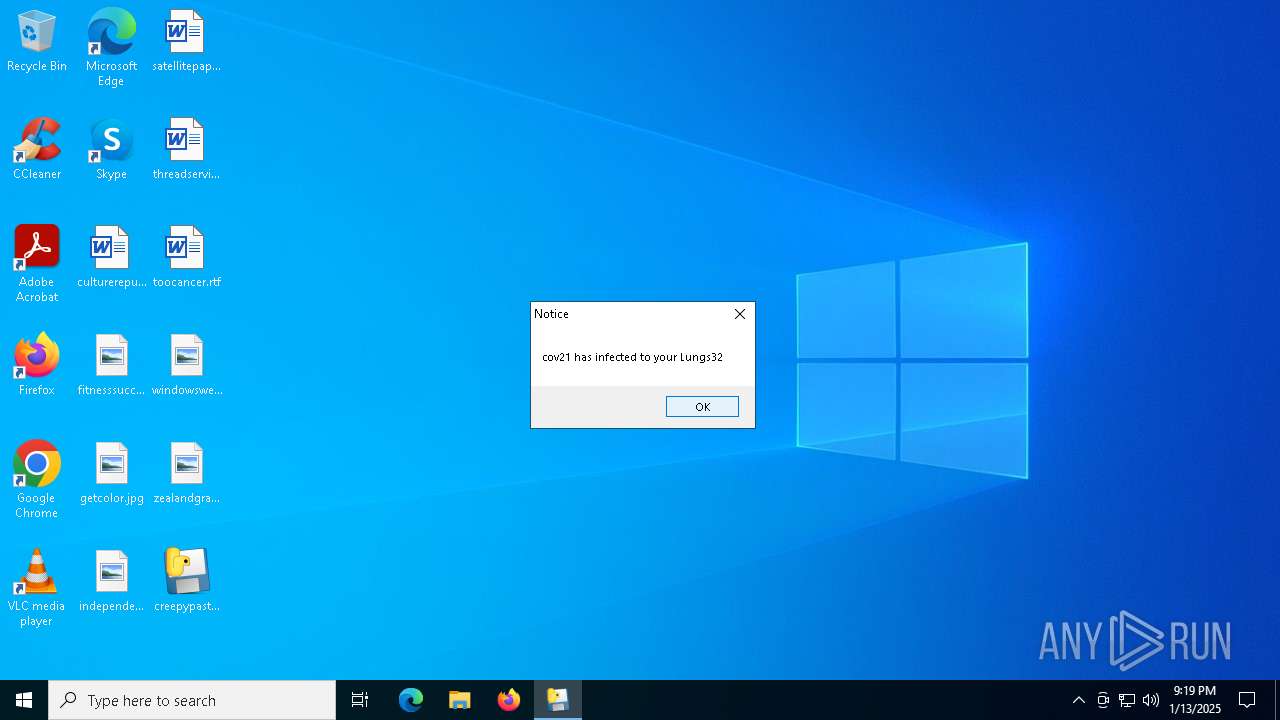
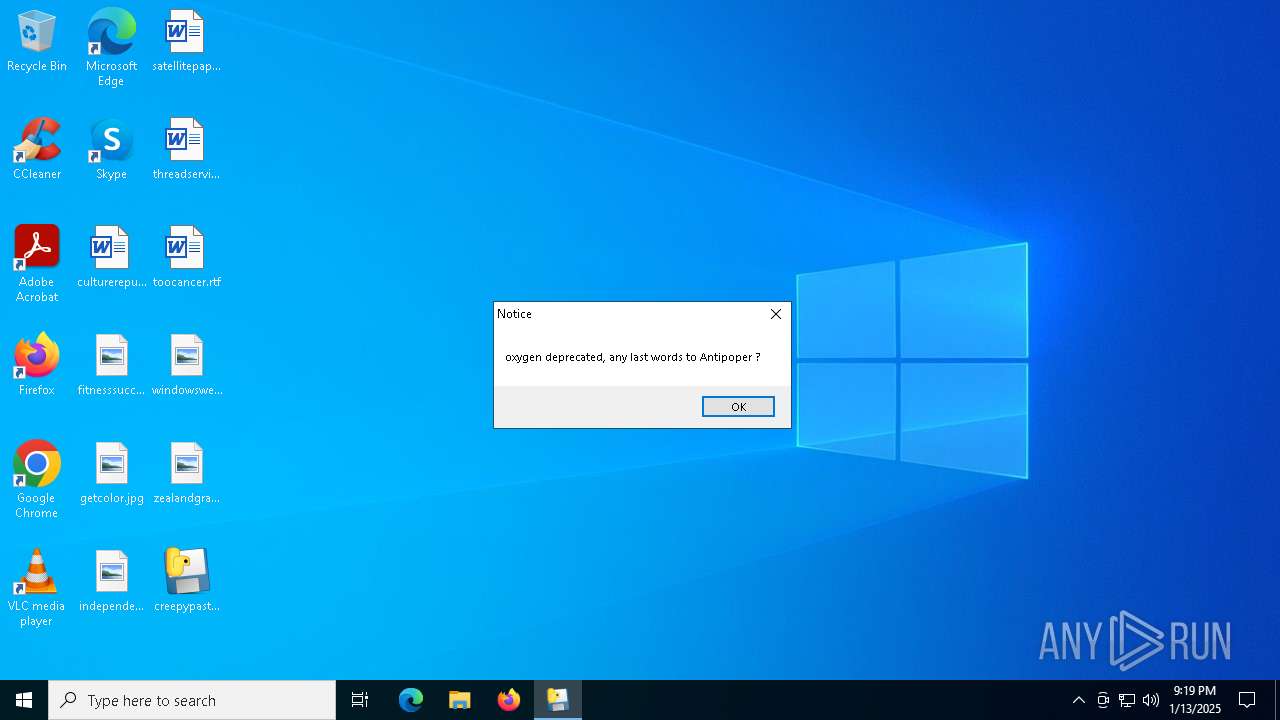
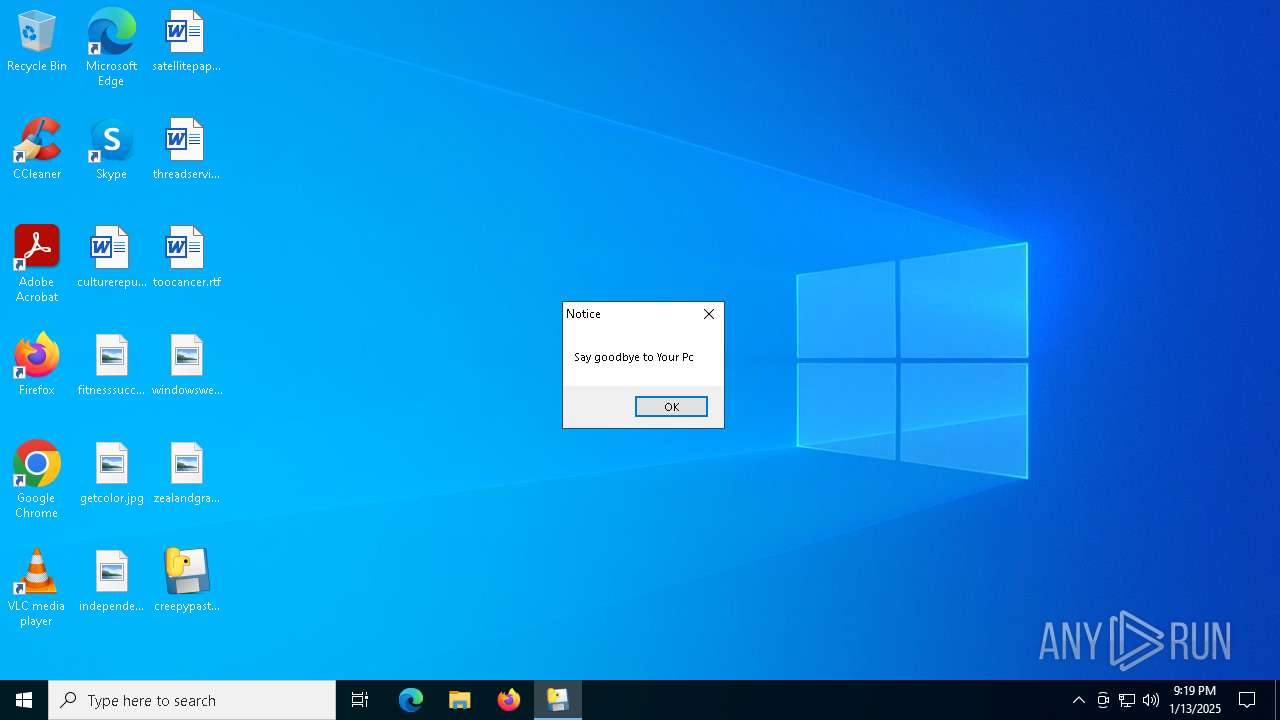
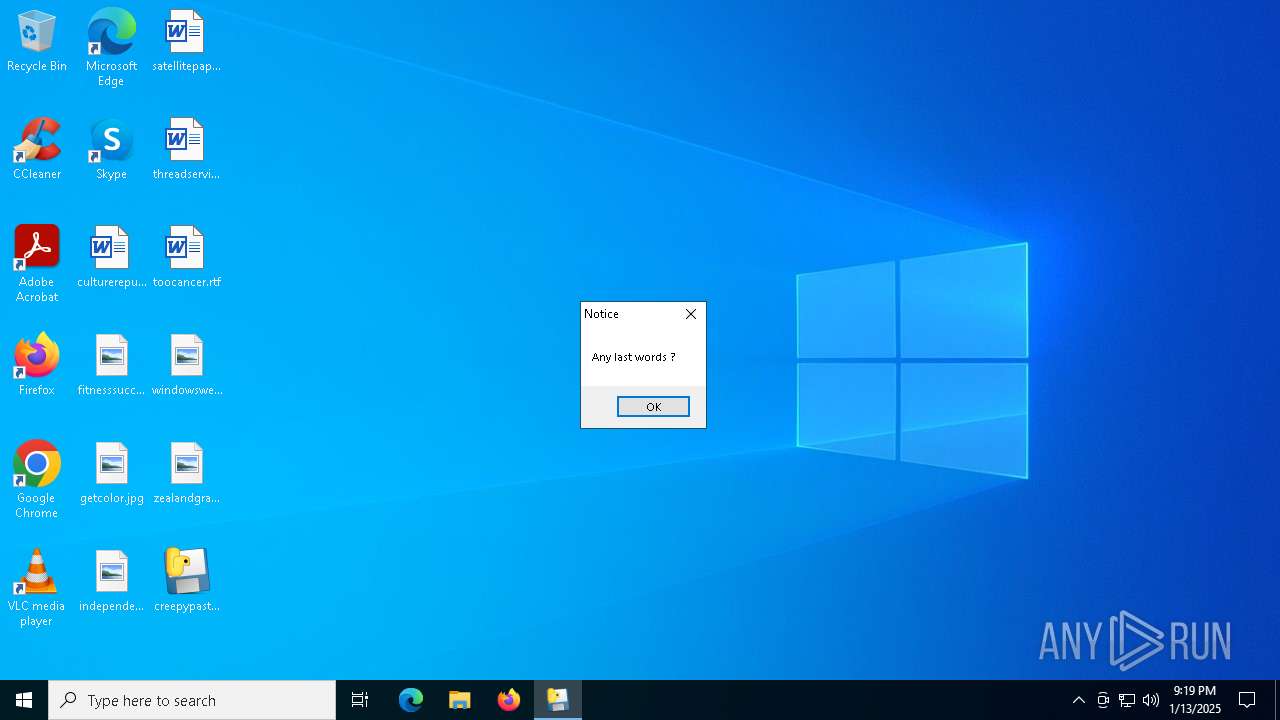
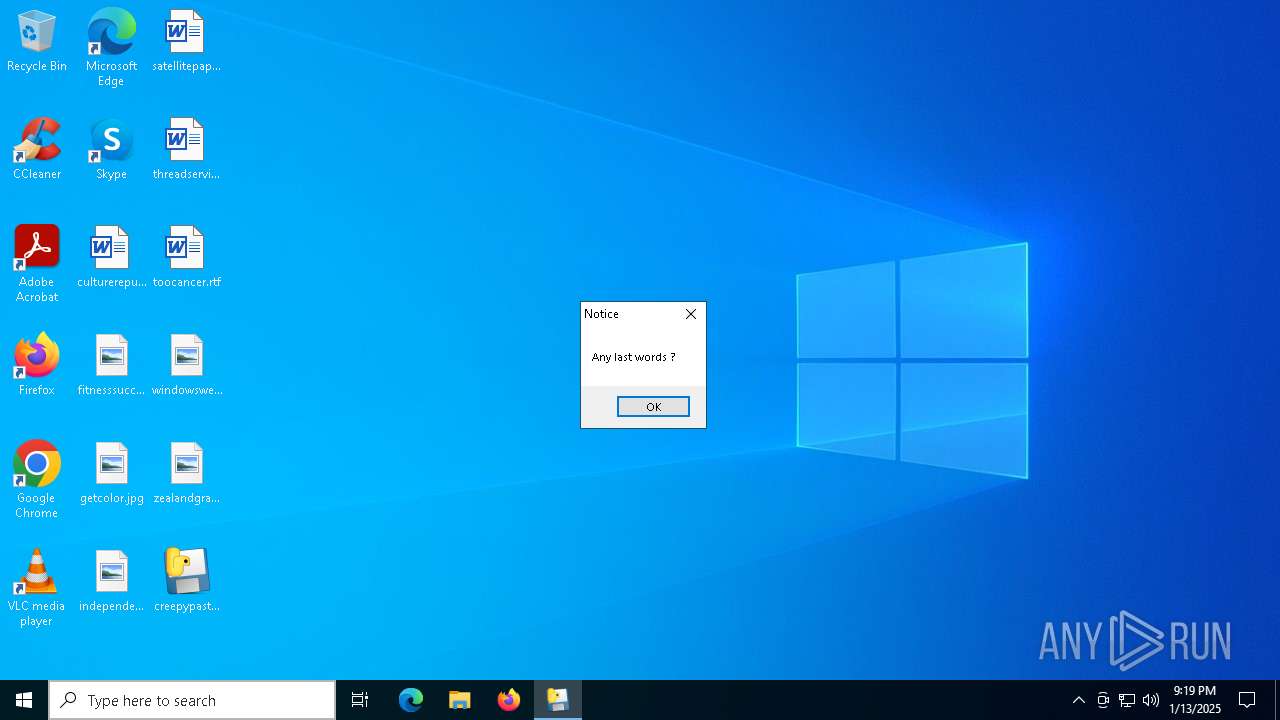
| File name: | creepypasta.exe |
| Full analysis: | https://app.any.run/tasks/532f4cae-4058-49ce-a945-90317471a01a |
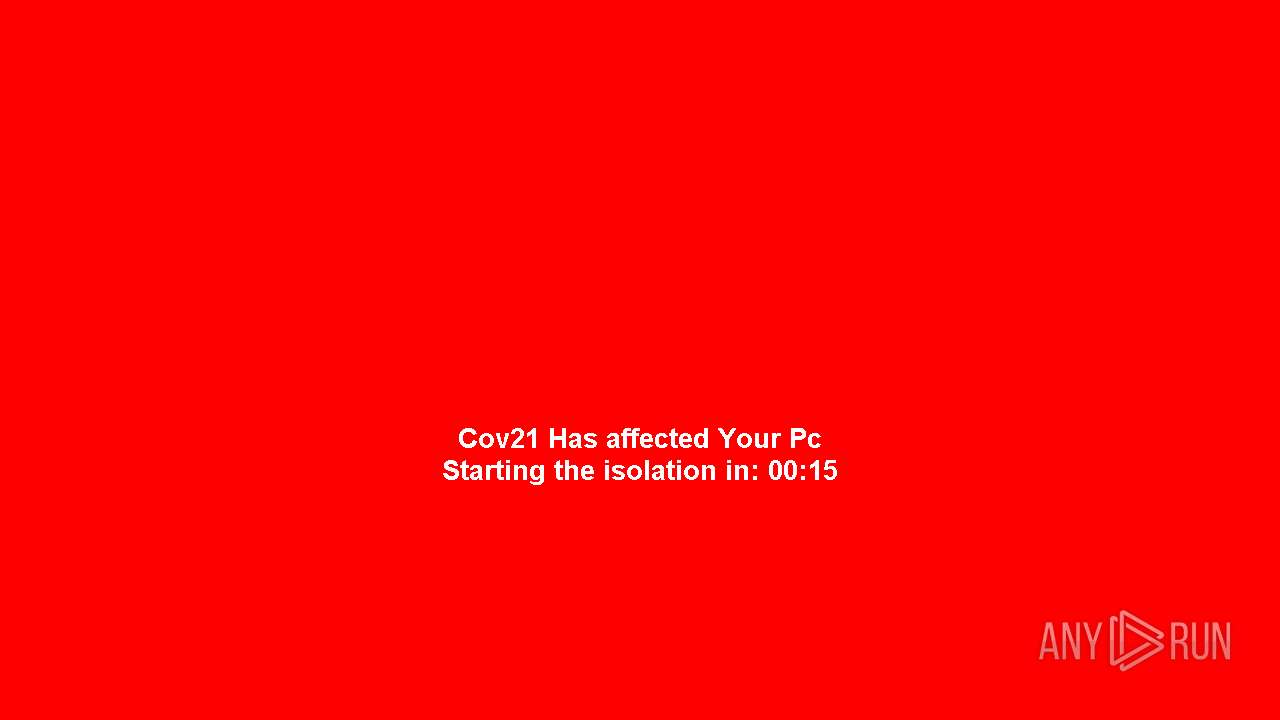
| Verdict: | Malicious activity |
| Analysis date: | January 13, 2025, 21:18:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 505472ACE48A3DF4C510587B56EFED4D |
| SHA1: | 0A9CE66C86A9C4EB50EFB9463361DD3AE961CFB7 |
| SHA256: | E97B5B5B2BE90D65601948B54EFE7813778C4E8E6D28680FB668BE796888F13A |
| SSDEEP: | 98304:tFsOgE8onYwv4qO5GgeuwVZ55gKGHOGh9wv2WsUbUdw35f31Ezd5hb02BtZT4Z+B:S9aEZ/FtnqxPC7A |
MALICIOUS
No malicious indicators.SUSPICIOUS
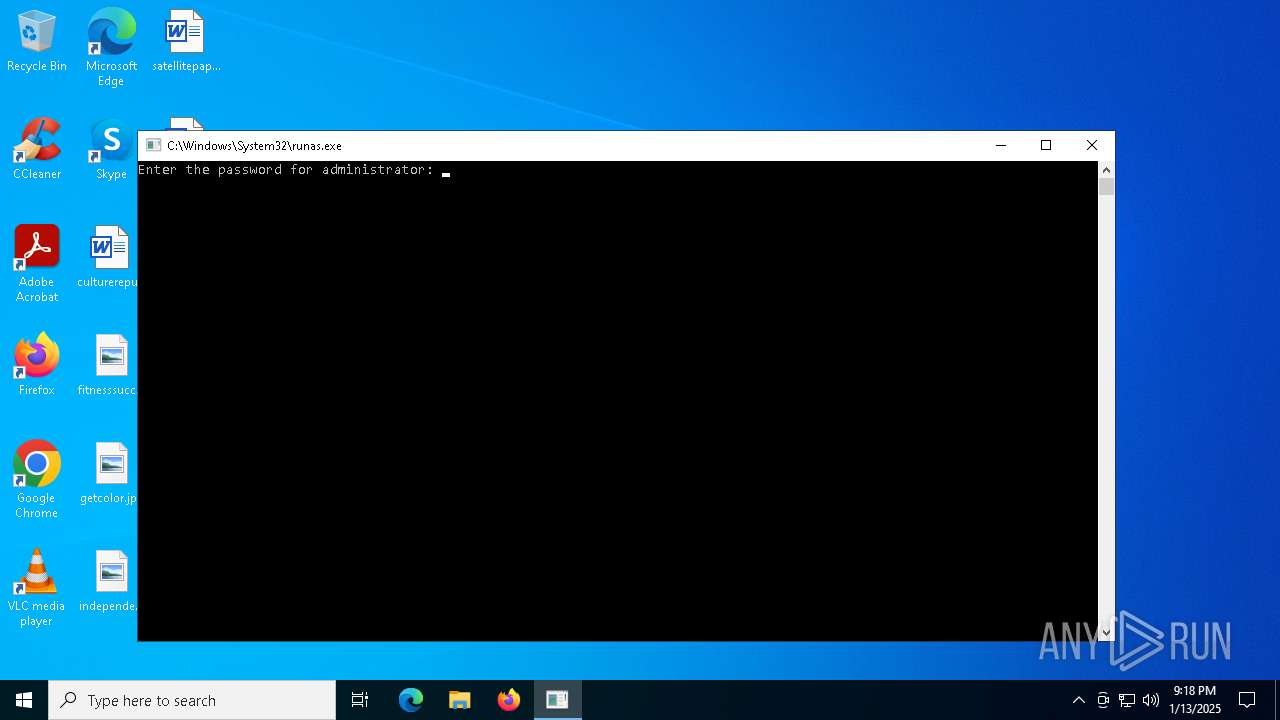
Starts another process probably with elevated privileges via RUNAS.EXE
- runas.exe (PID: 6280)
Process drops python dynamic module
- creepypasta.exe (PID: 6748)
Process drops legitimate windows executable
- creepypasta.exe (PID: 6748)
The process drops C-runtime libraries
- creepypasta.exe (PID: 6748)
Application launched itself
- creepypasta.exe (PID: 6748)
Executable content was dropped or overwritten
- creepypasta.exe (PID: 6748)
Loads Python modules
- creepypasta.exe (PID: 6980)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7036)
- cmd.exe (PID: 7128)
Starts CMD.EXE for commands execution
- creepypasta.exe (PID: 6980)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 364)
INFO
The sample compiled with english language support
- creepypasta.exe (PID: 6748)
Reads the machine GUID from the registry
- creepypasta.exe (PID: 6980)
Reads the computer name
- creepypasta.exe (PID: 6748)
- creepypasta.exe (PID: 6980)
Checks supported languages
- creepypasta.exe (PID: 6980)
- creepypasta.exe (PID: 6748)
PyInstaller has been detected (YARA)
- creepypasta.exe (PID: 6748)
- creepypasta.exe (PID: 6980)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (50.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (32.2) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.6) |
| .exe | | | Win32 Executable (generic) (5.2) |
| .exe | | | Generic Win/DOS Executable (2.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:01:05 12:16:35+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 126976 |
| InitializedDataSize: | 173568 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x7cd3 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
134
Monitored processes
13
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 364 | C:\WINDOWS\system32\cmd.exe /c "takeown /f C:\Windows\System32\drivers\disk.sys && icacls C:\Windows\System32\drivers\disk.sys /grant %username%:F" | C:\Windows\SysWOW64\cmd.exe | — | creepypasta.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1684 | REG add HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System /v DisableRegistryTools /t REG_DWORD /d 1 /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3812 | takeown /f C:\Windows\System32\drivers\disk.sys | C:\Windows\SysWOW64\takeown.exe | — | cmd.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4428 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6280 | "C:\Windows\System32\runas.exe" /user:administrator C:\Users\admin\Desktop\creepypasta.exe | C:\Windows\System32\runas.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Run As Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6288 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | runas.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6748 | C:\Users\admin\Desktop\creepypasta.exe | C:\Users\admin\Desktop\creepypasta.exe | runas.exe | ||||||||||||
User: Administrator Integrity Level: HIGH Modules
| |||||||||||||||
| 6980 | C:\Users\admin\Desktop\creepypasta.exe | C:\Users\admin\Desktop\creepypasta.exe | — | creepypasta.exe | |||||||||||
User: Administrator Integrity Level: HIGH Modules
| |||||||||||||||
| 7036 | C:\WINDOWS\system32\cmd.exe /c "REG add HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System /v DisableTaskMgr /t REG_DWORD /d 1 /f" | C:\Windows\SysWOW64\cmd.exe | — | creepypasta.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7044 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
321
Read events
319
Write events
2
Delete events
0
Modification events
| (PID) Process: | (7096) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableTaskMgr |
Value: 1 | |||
| (PID) Process: | (1684) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableRegistryTools |
Value: 1 | |||
Executable files
22
Suspicious files
3
Text files
912
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6748 | creepypasta.exe | C:\Users\Administrator\AppData\Local\Temp\_MEI67482\_asyncio.pyd | executable | |
MD5:E88C7D616749054FEFAA13602CBE2947 | SHA256:F8552B6290A91A8BC4D6C86B537C00FA2F25B1DEE2D2D2EB95D1F458179B4EFB | |||
| 6748 | creepypasta.exe | C:\Users\Administrator\AppData\Local\Temp\_MEI67482\_ctypes.pyd | executable | |
MD5:36BF6FFD59C04075D50F245EF5DE2AB9 | SHA256:7C11A5B8CBAEB0CD34544A7E4949C1B2A61CC78392C0155C0156306E6FF602E0 | |||
| 6748 | creepypasta.exe | C:\Users\Administrator\AppData\Local\Temp\_MEI67482\_hashlib.pyd | executable | |
MD5:9AA769EFAC1446DB1D2E4E1C39500A20 | SHA256:DE7C71C90C7F58DCDC3DA159D08DDA7DC297E39C5F309849290238BAED7E230F | |||
| 6748 | creepypasta.exe | C:\Users\Administrator\AppData\Local\Temp\_MEI67482\_bz2.pyd | executable | |
MD5:852CAC1AC7232C5788CBA284C3122347 | SHA256:94D02CBCFAC3141CA0107253050D7B9D809FEA04B42964142BED3F090783A26A | |||
| 6748 | creepypasta.exe | C:\Users\Administrator\AppData\Local\Temp\_MEI67482\_queue.pyd | executable | |
MD5:BCF5440A884EF33DF02CE124557D0C2C | SHA256:2F2F30A6B697B7BA7C09DB16EC04517C85CDFAB13F142B9C810FDF9983522129 | |||
| 6748 | creepypasta.exe | C:\Users\Administrator\AppData\Local\Temp\_MEI67482\_lzma.pyd | executable | |
MD5:52E990DA9F33D0EF2B83A0B52D42DCD6 | SHA256:17FD3A2750E61FB164F3A9E8E021A0A3B5DE107A3CC4C798E127618034E09D6F | |||
| 6748 | creepypasta.exe | C:\Users\Administrator\AppData\Local\Temp\_MEI67482\_overlapped.pyd | executable | |
MD5:BAFA4F39AE519192EA8D3274986A6187 | SHA256:342BDAF83A0046F786D38E1DC1215FB4113472D8E99BF14F48F61E0574BBE1B4 | |||
| 6748 | creepypasta.exe | C:\Users\Administrator\AppData\Local\Temp\_MEI67482\VCRUNTIME140.dll | executable | |
MD5:AE96651CFBD18991D186A029CBECB30C | SHA256:1B372F064EACB455A0351863706E6326CA31B08E779A70DE5DE986B5BE8069A1 | |||
| 6748 | creepypasta.exe | C:\Users\Administrator\AppData\Local\Temp\_MEI67482\libffi-7.dll | executable | |
MD5:64FD05751201BBE3E29FA3A8AA600B5E | SHA256:8F88C66FD8E046A57DEB7D263EFB9D79092B1A55FD7F08DF7F430654B47ACE09 | |||
| 6748 | creepypasta.exe | C:\Users\Administrator\AppData\Local\Temp\_MEI67482\libcrypto-1_1.dll | executable | |
MD5:67C1EA1B655DBB8989A55E146761C202 | SHA256:541ADBC9654D967491D11359A0E4AD4972D2BD25F260476DD7576C576478698A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
32
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
876 | svchost.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
876 | svchost.exe | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4708 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6836 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6836 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
876 | svchost.exe | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
876 | svchost.exe | 23.218.209.163:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.218.209.163:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.128:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |