| File name: | iCal-201972.ics |
| Full analysis: | https://app.any.run/tasks/b321d34d-8a58-4041-b463-72fb48d37307 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2019, 15:36:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | text/calendar |
| File info: | vCalendar calendar file |
| MD5: | FB0F5257D9BBB60BF5DC2ED7FBC4481C |
| SHA1: | 5DEC6C33CA13FE0052E70D1B748F45B329E2C401 |
| SHA256: | E976AB28340AB965E1E1A6EE8015B94FD8E33D6EA249F84B64E8392909EF7CDB |
| SSDEEP: | 48:Egfo6ej19yn1l6b1d4Z1lN41dm8Cj1ILNKb13fE1+M/QK1lZs1hdI1woIWvn1tdb:Egf2jenubUZN4d8CNO5Ef/QKdstIKQvt |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3384)
Reads internet explorer settings
- OUTLOOK.EXE (PID: 3384)
Creates files in the user directory
- OUTLOOK.EXE (PID: 3384)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .ics/vcs | | | iCalendar - vCalendar (100) |
|---|
EXIF
VCard
| Software: | -//CALENDARSERVER.ORG//NONSGML Version 1//EN |
|---|---|
| Method: | REQUEST |
| VCalendarVersion: | 2 |
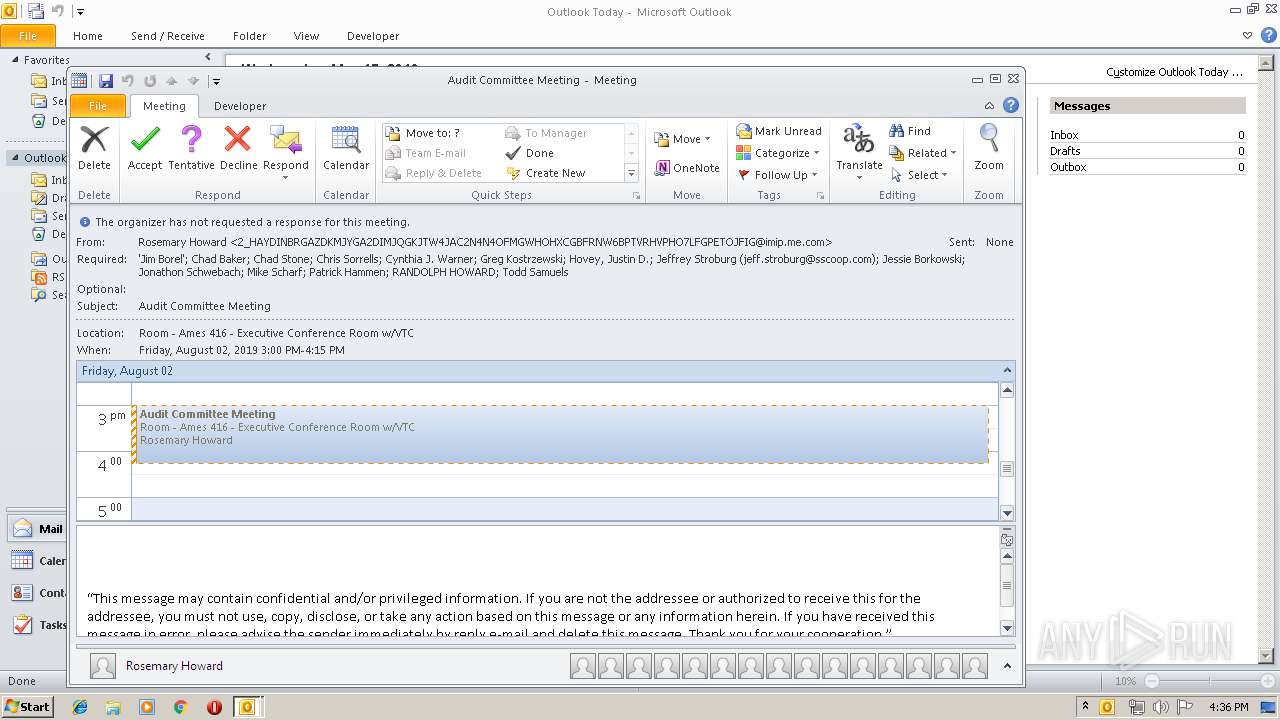
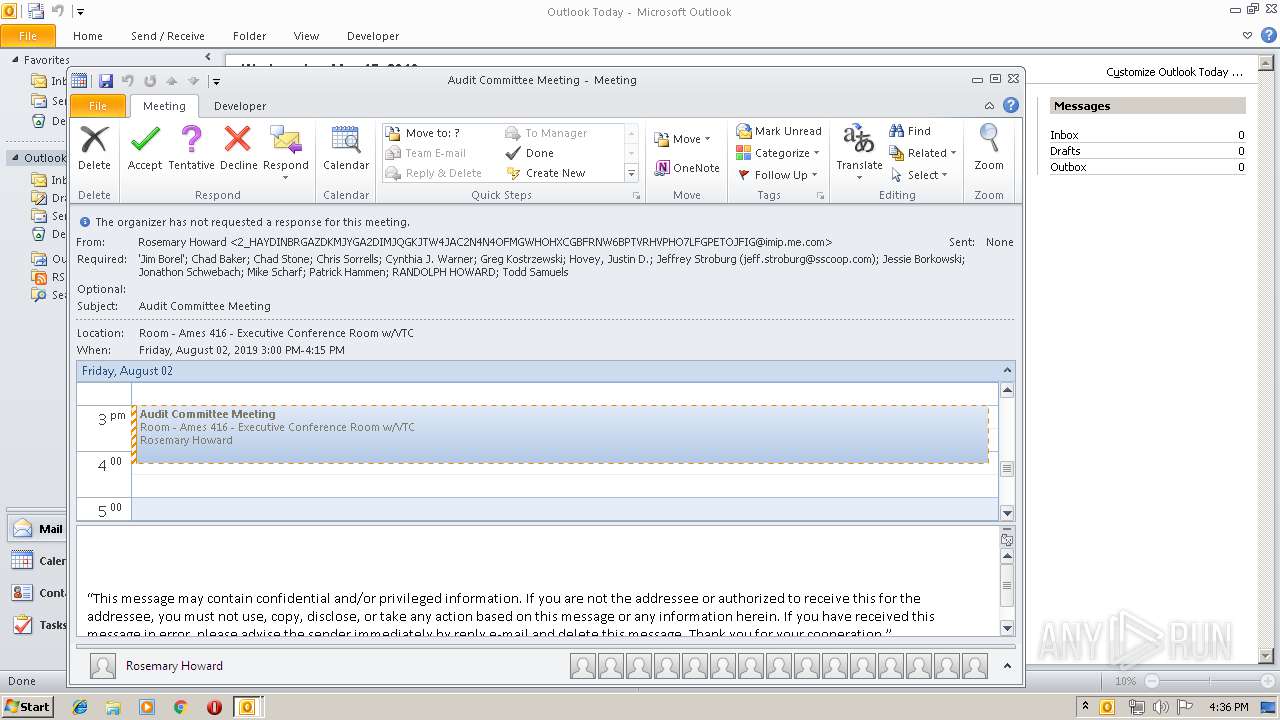
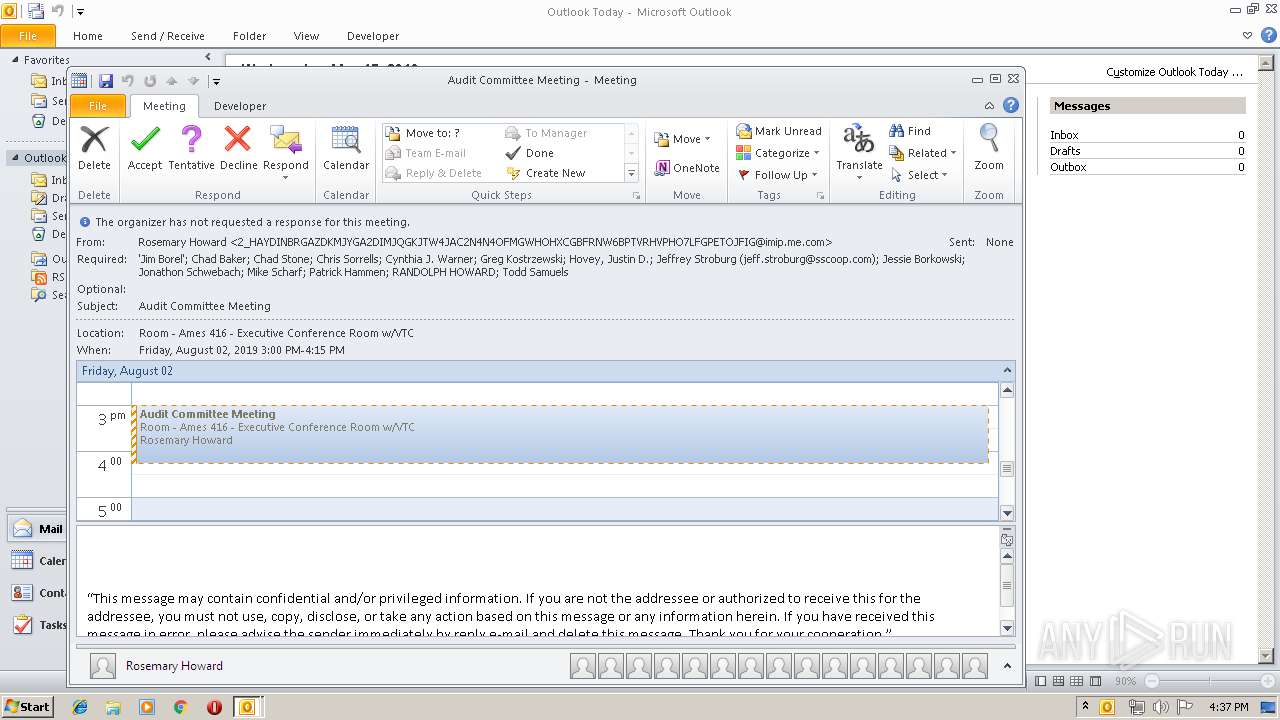
| Attendee: | mailto:todd.samuels@regi.com |
| DateCreated: | 2019:05:08 13:23:11Z |
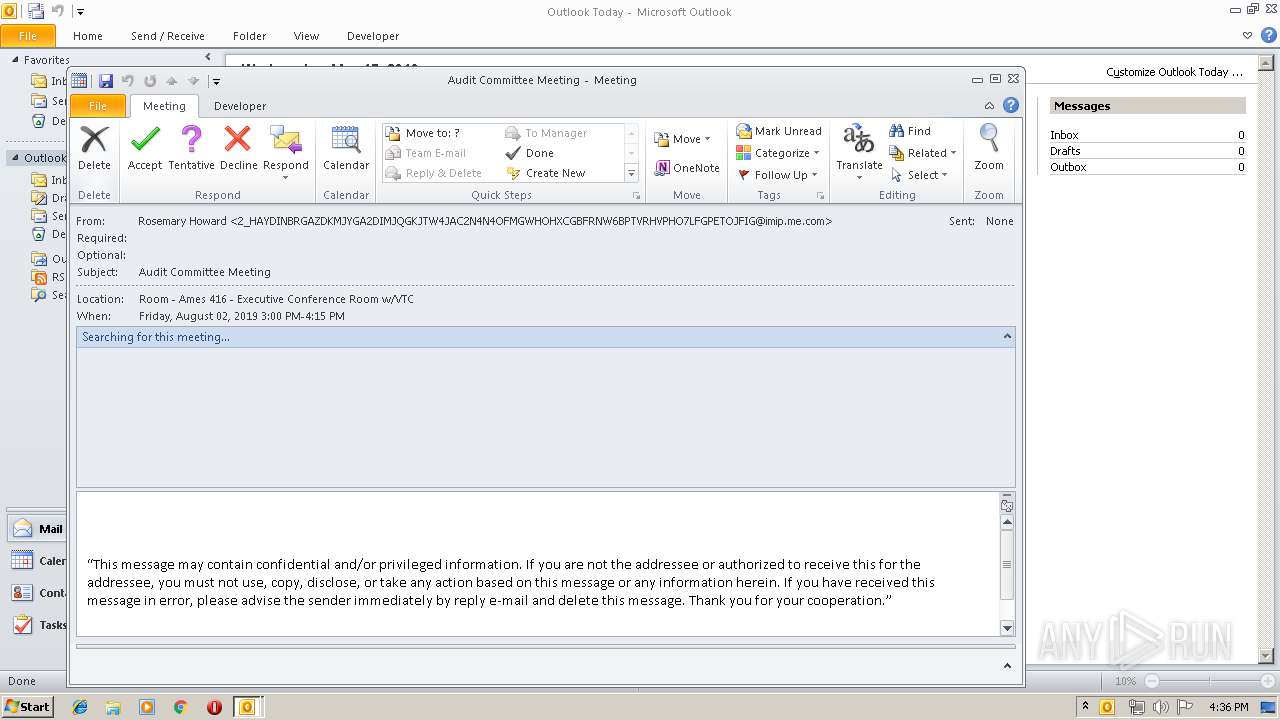
| Description: | "This message may contain confidential and/or privileged information. If you are not the addressee or authorized to receive this for the addressee, you must not use, copy, disclose, or take any action based on this message or any information herein. If you have received this message in error, please advise the sender immediately by reply e-mail and delete this message. Thank you for your cooperation." |
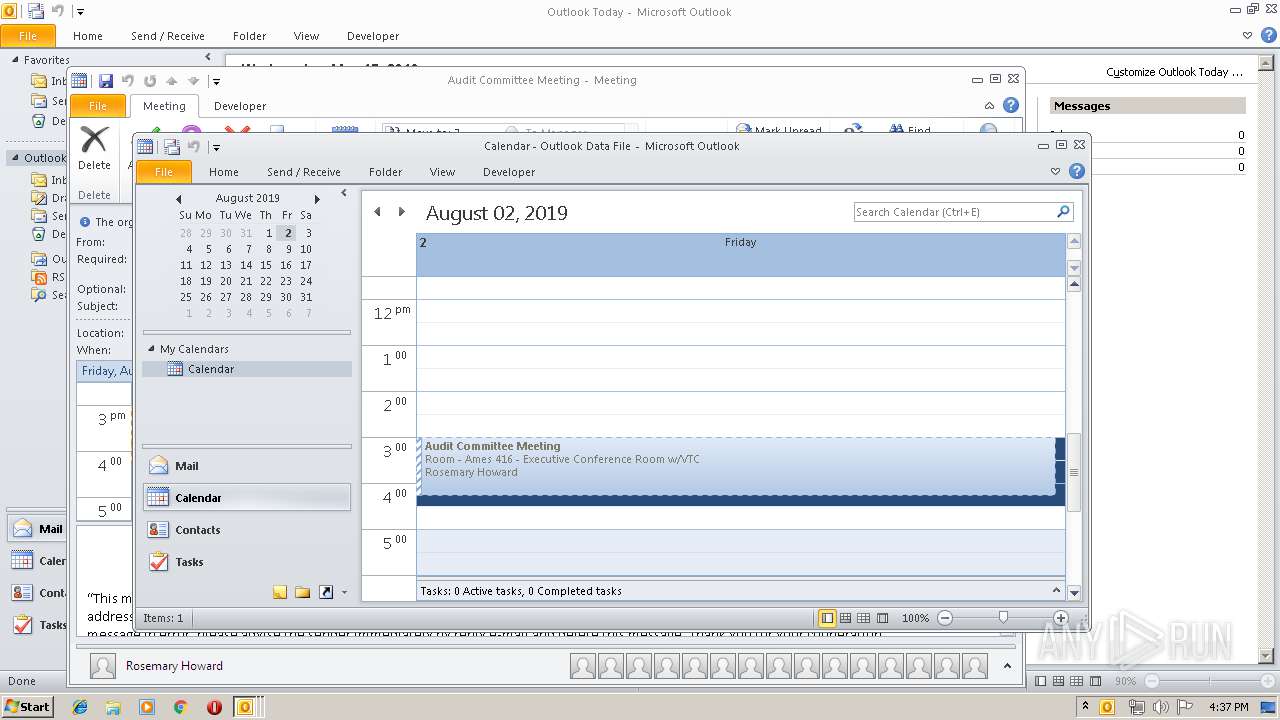
| DateTimeEnd: | 2019:08:02 09:15:00 |
| DateTimeEndTimezoneID: | America/Chicago |
| DateTimeStamp: | 2019:05:09 00:33:48Z |
| DateTimeStart: | 2019:08:02 08:00:00 |
| DateTimeStartTimezoneID: | America/Chicago |
| ModifyDate: | 2019:05:08 13:23:11Z |
| Location: | Room - Ames 416 - Executive Conference Room w/VTC |
| Organizer: | mailto:2_HAYDINBRGAZDKMJYGA2DIMJQGKJTW4JAC2N4N4OFMGWHOHXCGBFRNW6BPTVRHVPHO7LFGPETOJFIG@imip.me.com |
| SequenceNumber: | - |
| Summary: | Audit Committee Meeting |
| UID: | 7F1AD3AB-9A08-4DB9-9DAC-4B4603C0BBB2 |
| URL: | - |
Total processes
35
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3384 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /ical "C:\Users\admin\AppData\Local\Temp\iCal-201972.ics" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
Total events
1 640
Read events
1 157
Write events
446
Delete events
37
Modification events
| (PID) Process: | (3384) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3384) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3384) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | `:= |
Value: 603A3D00380D0000010000000000000000000000 | |||
| (PID) Process: | (3384) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: 380D0000489DB1F8330BD50100000000 | |||
| (PID) Process: | (3384) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (3384) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 220039200 | |||
| (PID) Process: | (3384) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (3384) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (3384) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (3384) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1320091669 | |||
Executable files
0
Suspicious files
1
Text files
27
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3384 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRE40.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3384 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DFF4D2E5F643F96353.TMP | — | |
MD5:— | SHA256:— | |||
| 3384 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF20C11039AB99564D.TMP | — | |
MD5:— | SHA256:— | |||
| 3384 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{D1EFD586-25E6-4E99-AF85-C81F2A4F49A9}.tmp | — | |
MD5:— | SHA256:— | |||
| 3384 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:48DD6CAE43CE26B992C35799FCD76898 | SHA256:7BFE1F3691E2B4FB4D61FBF5E9F7782FBE49DA1342DBD32201C2CC8E540DBD1A | |||
| 3384 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\History\History.IE5\MSHist012019051520190516\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3384 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3384 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Outlook\NoMail.srs | srs | |
MD5:— | SHA256:— | |||
| 3384 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Outlook\NoMail.xml | xml | |
MD5:— | SHA256:— | |||
| 3384 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\~Outlook Data File - NoMail.pst.tmp | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3384 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3384 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |