| File name: | e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe |
| Full analysis: | https://app.any.run/tasks/df0b6b3b-528c-413d-a32e-86a81faaa1ac |
| Verdict: | Malicious activity |
| Analysis date: | August 26, 2025, 20:45:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | 4CEB21B9A6093AB9F033C39294E376AE |
| SHA1: | 305AE88C2F8F0028251F1557EF9456474F9720C1 |
| SHA256: | E96C334F57835EB579789875FDA70800A5947955D420BABBF482A39E7AFBB3DF |
| SSDEEP: | 196608:PFxFm6LTvg/tRg4IWGnPqIo9yxA6vYoqLjObhmURg3qU:PFHHYtR/vgPlw6v4kmURUf |
MALICIOUS
JEEFO has been detected
- e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe (PID: 5616)
SUSPICIOUS
Executable content was dropped or overwritten
- e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe (PID: 5616)
- e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe (PID: 1100)
- e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe (PID: 436)
Starts application with an unusual extension
- e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe (PID: 5616)
- e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe (PID: 1100)
Searches for installed software
- e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe (PID: 436)
There is functionality for taking screenshot (YARA)
- e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe (PID: 1100)
- e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe (PID: 436)
INFO
Failed to create an executable file in Windows directory
- e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe (PID: 5616)
Checks supported languages
- e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe (PID: 5616)
- e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe (PID: 1100)
- e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe (PID: 436)
The sample compiled with english language support
- e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe (PID: 5616)
- e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe (PID: 1100)
- e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe (PID: 436)
Create files in a temporary directory
- e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe (PID: 1100)
- e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe (PID: 5616)
- e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe (PID: 436)
Reads the computer name
- e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe (PID: 436)
Reads the machine GUID from the registry
- e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe (PID: 436)
UPX packer has been detected
- e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe (PID: 5616)
Checks proxy server information
- slui.exe (PID: 5188)
Reads the software policy settings
- slui.exe (PID: 5188)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Microsoft Visual Basic 6 (47.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (16) |
| .exe | | | UPX compressed Win32 Executable (15.7) |
| .exe | | | Win32 EXE Yoda's Crypter (15.4) |
| .exe | | | Win32 Executable (generic) (2.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:04:01 07:08:22+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 36864 |
| InitializedDataSize: | 8192 |
| UninitializedDataSize: | 90112 |
| EntryPoint: | 0x1f1a0 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| ProductName: | Project1 |
| FileVersion: | 1 |
| ProductVersion: | 1 |
| InternalName: | TJprojMain |
| OriginalFileName: | TJprojMain.exe |
Total processes
135
Monitored processes
4
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 436 | "C:\Users\admin\AppData\Local\Temp\{5A929E10-C5AA-4087-9BE5-F7754BF37C81}\.cr\e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe " -burn.clean.room="c:\users\admin\desktop\e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe " -burn.filehandle.attached=596 -burn.filehandle.self=604 | C:\Users\admin\AppData\Local\Temp\{5A929E10-C5AA-4087-9BE5-F7754BF37C81}\.cr\e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe | e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe | ||||||||||||
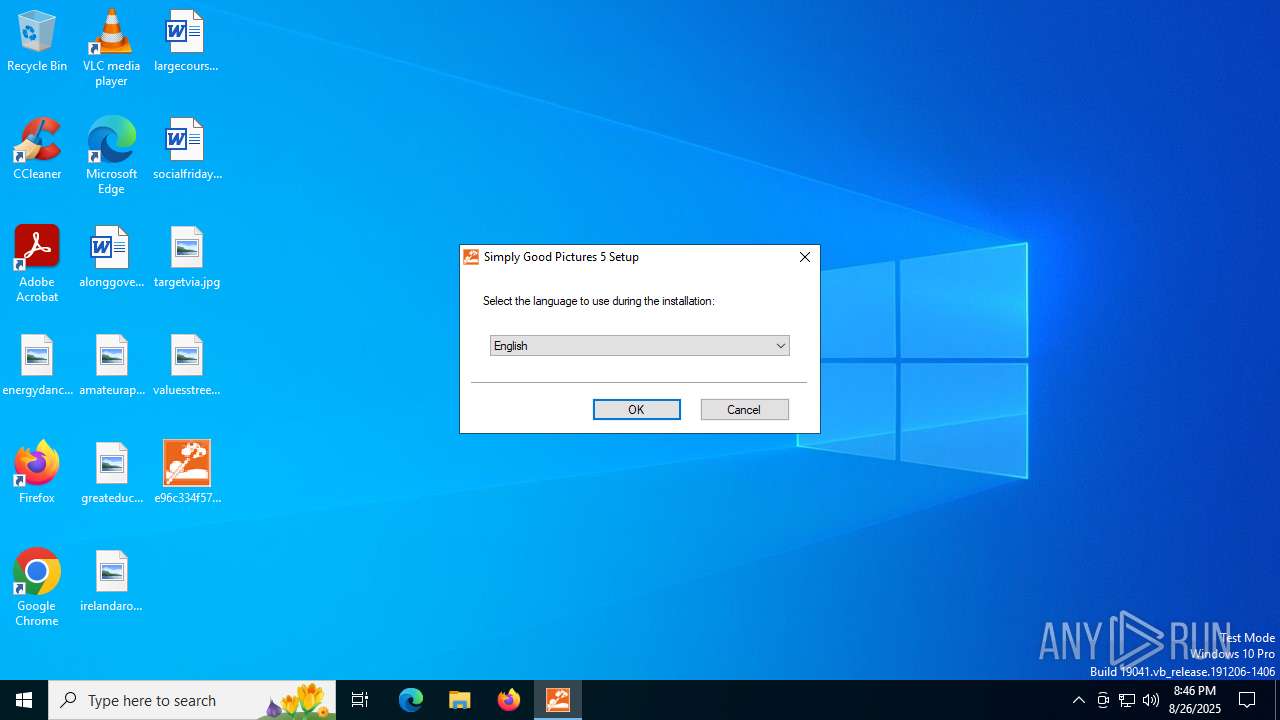
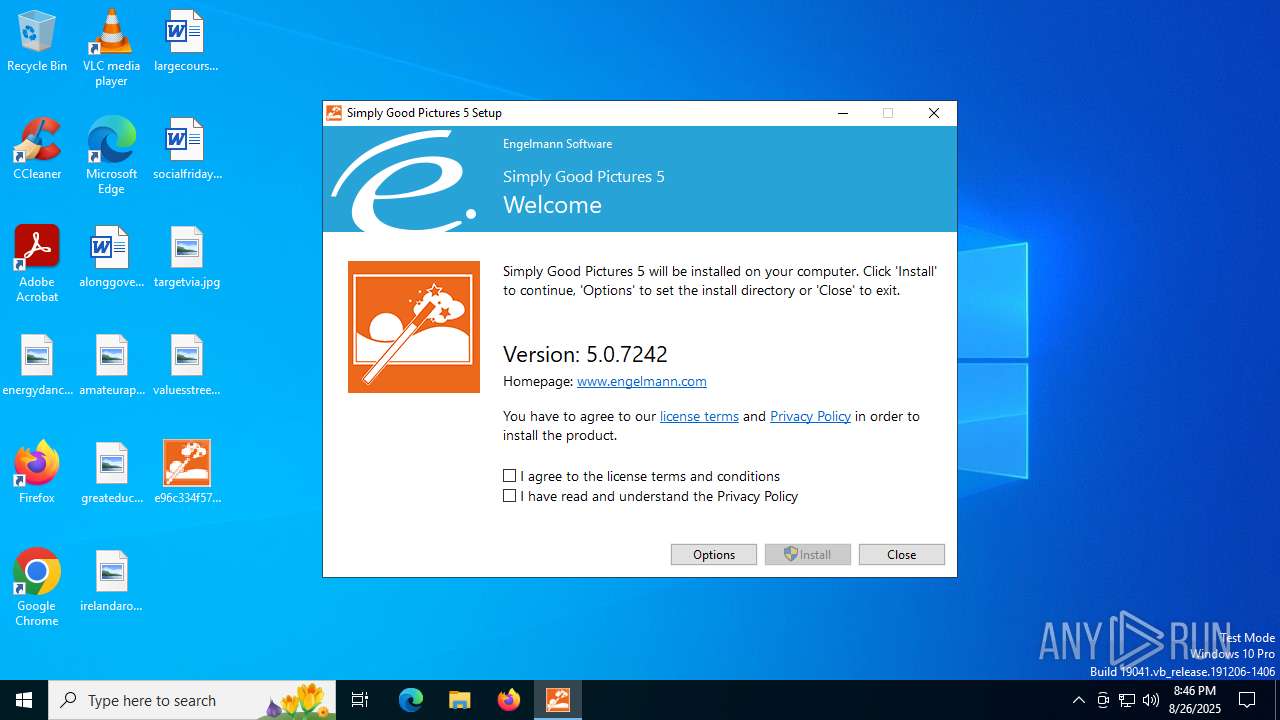
User: admin Company: Engelmann Software Integrity Level: MEDIUM Description: Simply Good Pictures 5 Version: 5.0.7242.24775 Modules
| |||||||||||||||
| 1100 | c:\users\admin\desktop\e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe | C:\Users\admin\Desktop\e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe | e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe | ||||||||||||
User: admin Company: Engelmann Software Integrity Level: MEDIUM Description: Simply Good Pictures 5 Version: 5.0.7242.24775 Modules
| |||||||||||||||
| 5188 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5616 | "C:\Users\admin\Desktop\e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe" | C:\Users\admin\Desktop\e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
Total events
3 591
Read events
3 589
Write events
2
Delete events
0
Modification events
| (PID) Process: | (5616) e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (436) e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Installer\Languages |
| Operation: | write | Name: | {14FFF7BE-3649-452B-AA82-508577F97F25} |
Value: 1033 | |||
Executable files
3
Suspicious files
1
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 436 | e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe | C:\Users\admin\AppData\Local\Temp\{F3BC3CC2-5D4C-438A-A857-DFEEAD708BCC}\.ba\UpdateSearch02.png | image | |
MD5:D4F84E6375D03EC926B5A79D42E848B1 | SHA256:400AE9C91DBB6AADC360080B4E4A928C65FDC5027533DE5A294EB075B45B5ACB | |||
| 436 | e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe | C:\Users\admin\AppData\Local\Temp\{F3BC3CC2-5D4C-438A-A857-DFEEAD708BCC}\.ba\wixextba.dll | executable | |
MD5:13FE36F0F07B31D2302EE553A38E8F43 | SHA256:02DFAAEAB46F66300389ECC2BDC83B608AAB6FD945DE87AA2F1083D25D79D6BC | |||
| 436 | e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe | C:\Users\admin\AppData\Local\Temp\{F3BC3CC2-5D4C-438A-A857-DFEEAD708BCC}\.ba\LogoSide.png | image | |
MD5:CD17AD0CC34945EF4DEA29742CD89C84 | SHA256:DC915FBF7F10969759F7735C5337F705AE2D4BABF36D00917DBD2CCBAD2A1842 | |||
| 436 | e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe | C:\Users\admin\AppData\Local\Temp\{F3BC3CC2-5D4C-438A-A857-DFEEAD708BCC}\.ba\thm.xml | xml | |
MD5:45EFF24261980E2911FCB3166F72E12A | SHA256:D5CB4A6CA3176AF9051C2516E5E69F0133DF79E9B06408B03AA24D761B7507DA | |||
| 436 | e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe | C:\Users\admin\AppData\Local\Temp\{F3BC3CC2-5D4C-438A-A857-DFEEAD708BCC}\.ba\UpdateSearch01.png | image | |
MD5:03A616090EB820D53D26286F7F44F675 | SHA256:ECEFF7AFA3D34E06AF8681B807CC1630ADFEB061DEE255298B63BA4F7EF41763 | |||
| 5616 | e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe | C:\Users\admin\Desktop\e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe | executable | |
MD5:70B6CB1B8D28F0E0925DA38CAEBEAD2E | SHA256:96762056835703225DE0452A289896814E1F22AB85479CA83A0E9C7C02606FE7 | |||
| 1100 | e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe | C:\Users\admin\AppData\Local\Temp\{5A929E10-C5AA-4087-9BE5-F7754BF37C81}\.cr\e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe | executable | |
MD5:B38B30AAC5F68EBB297DF9990C3470AB | SHA256:128E4F7356E9D0B91343F0E22C0B2239FD23C8D94BF0BBB054DE7F42A98873EB | |||
| 436 | e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe | C:\Users\admin\AppData\Local\Temp\{F3BC3CC2-5D4C-438A-A857-DFEEAD708BCC}\.ba\Logo.png | image | |
MD5:DC9AA2F0AA432B799876F966855FC496 | SHA256:3D838B049D85442167B056143EFF5BB798D43328C5FAC6CD208937EEC5F43D5E | |||
| 436 | e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe | C:\Users\admin\AppData\Local\Temp\{F3BC3CC2-5D4C-438A-A857-DFEEAD708BCC}\.ba\thm.wxl | xml | |
MD5:5DCADCD2E10BDAE82C651A6C966ED3A2 | SHA256:CF4BAC461F70AD0B60F12F35EAD1FD9BBE184C497EDEE3ACBFF82A5D23B26E1C | |||
| 5616 | e96c334f57835eb579789875fda70800a5947955d420babbf482a39e7afbb3df.exe | C:\Users\admin\AppData\Local\Temp\~DFBE1064C29674F2EA.TMP | binary | |
MD5:22CB87760D6AC56D9B029BFDD351FB4C | SHA256:0DBF3FCA834EF1A1D1A34B3FE666FD1772AE41DC5827FB5854A0745464D92F33 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
50
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.160.17:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | unknown |
— | — | POST | 400 | 20.190.160.131:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | unknown |
— | — | POST | 400 | 20.190.160.5:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | unknown |
— | — | GET | 200 | 20.165.94.63:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
1268 | svchost.exe | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
1268 | svchost.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |