| File name: | truecrypt_setup_7.1a.exe |
| Full analysis: | https://app.any.run/tasks/cef1b173-b344-4a55-8f9e-94434a7f19ec |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2020, 00:10:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 7A23AC83A0856C352025A6F7C9CC1526 |
| SHA1: | 7689D038C76BD1DF695D295C026961E50E4A62EA |
| SHA256: | E95ECA399DFE95500C4DE569EFC4CC77B75E2B66A864D467DF37733EC06A0FF2 |
| SSDEEP: | 98304:cYoVF1jLBam4KBcDxJhL2+fZAwwjaJ2mLsn:IRLIgwxzLRfOoJ2mQ |
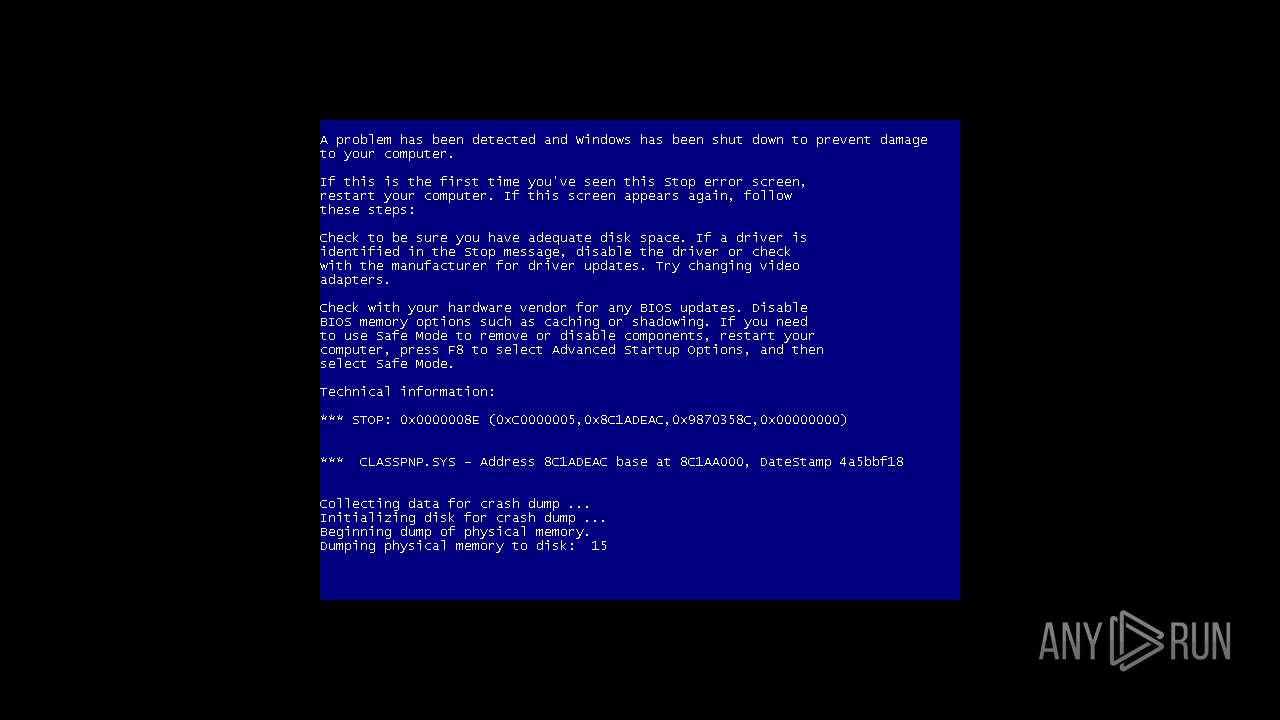
MALICIOUS
Application was dropped or rewritten from another process
- TrueCrypt Format.exe (PID: 3228)
- TrueCrypt.exe (PID: 2068)
SUSPICIOUS
Searches for installed software
- truecrypt_setup_7.1a.exe (PID: 628)
Executed as Windows Service
- vssvc.exe (PID: 4056)
Executed via COM
- DllHost.exe (PID: 740)
Creates files in the Windows directory
- truecrypt_setup_7.1a.exe (PID: 628)
Creates files in the driver directory
- truecrypt_setup_7.1a.exe (PID: 628)
Creates a software uninstall entry
- truecrypt_setup_7.1a.exe (PID: 628)
Creates files in the program directory
- truecrypt_setup_7.1a.exe (PID: 628)
Executable content was dropped or overwritten
- truecrypt_setup_7.1a.exe (PID: 628)
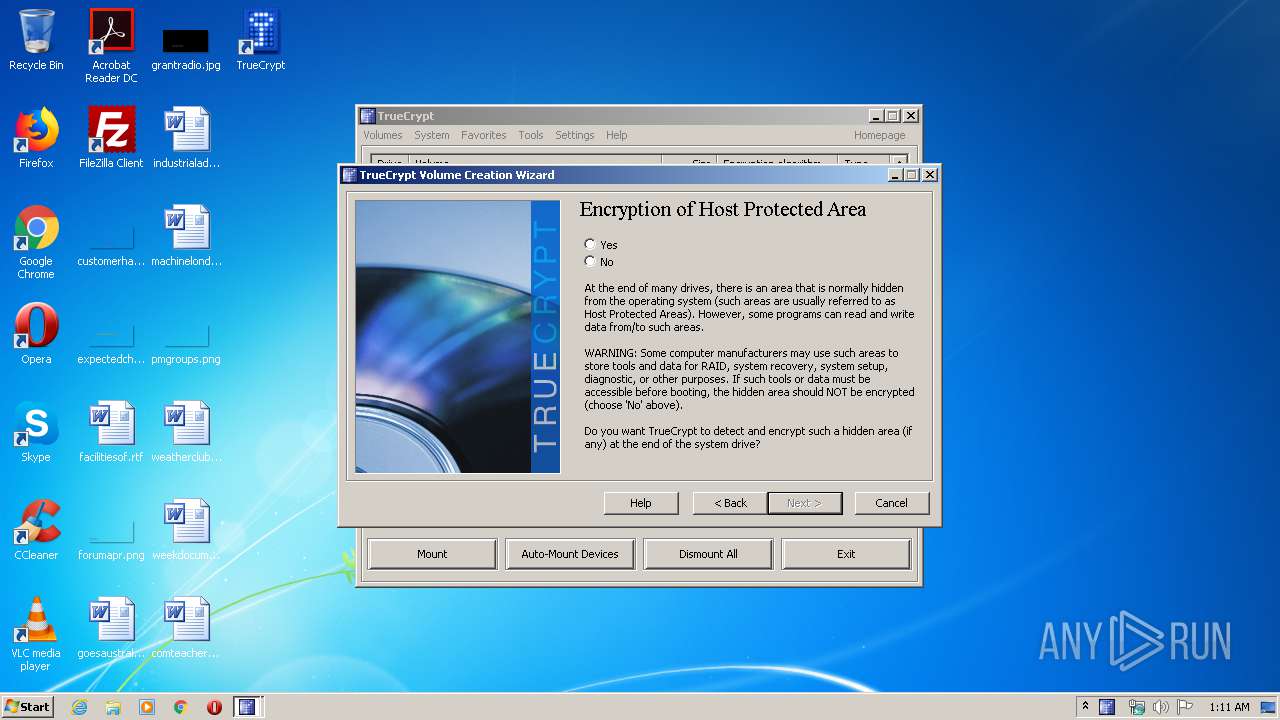
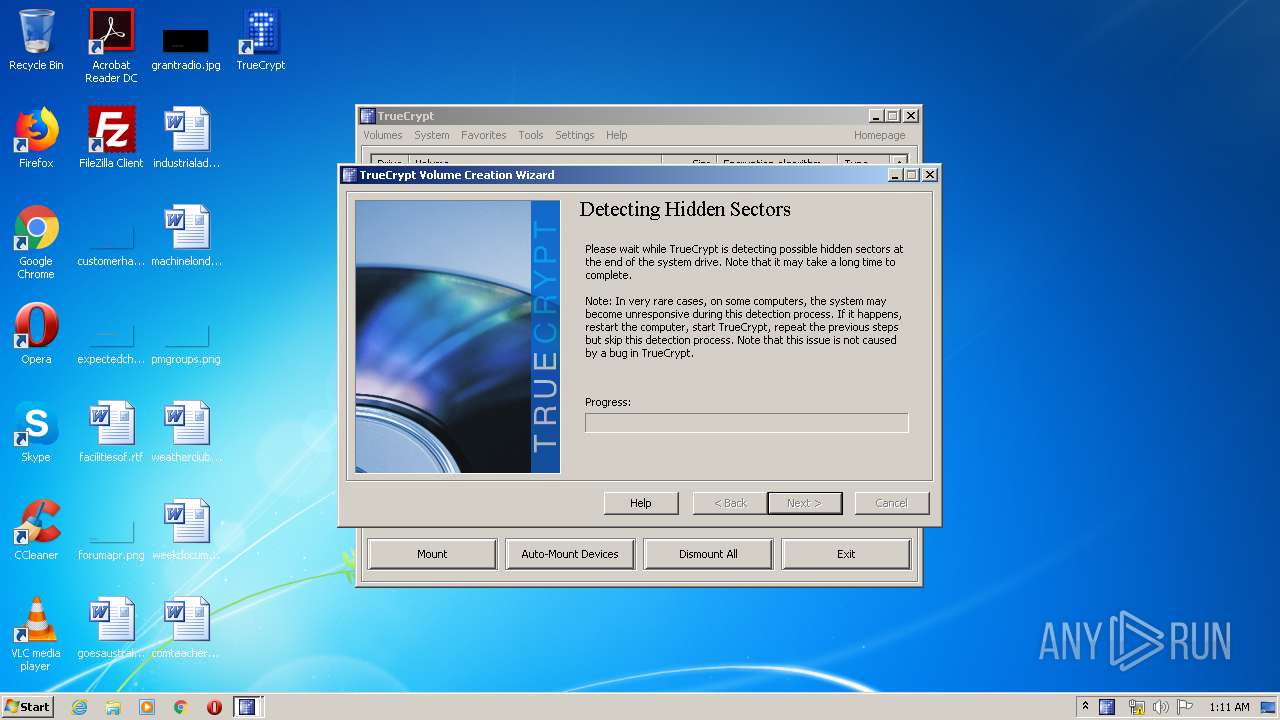
Low-level read access rights to disk partition
- TrueCrypt Format.exe (PID: 3228)
Modifies the open verb of a shell class
- truecrypt_setup_7.1a.exe (PID: 628)
INFO
Low-level read access rights to disk partition
- vssvc.exe (PID: 4056)
Manual execution by user
- TrueCrypt.exe (PID: 2068)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:02:07 10:09:48+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 265216 |
| InitializedDataSize: | 792576 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x28653 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.1.1.0 |
| ProductVersionNumber: | 7.1.1.0 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | TrueCrypt Foundation |
| FileDescription: | TrueCrypt Setup |
| FileVersion: | 7.1a |
| LegalTrademarks: | TrueCrypt |
| OriginalFileName: | TrueCrypt Setup.exe |
| ProductName: | TrueCrypt |
| ProductVersion: | 7.1a |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 07-Feb-2012 09:09:48 |
| Detected languages: |
|
| CompanyName: | TrueCrypt Foundation |
| FileDescription: | TrueCrypt Setup |
| FileVersion: | 7.1a |
| LegalTrademarks: | TrueCrypt |
| OriginalFilename: | TrueCrypt Setup.exe |
| ProductName: | TrueCrypt |
| ProductVersion: | 7.1a |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000E8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 07-Feb-2012 09:09:48 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00040BAA | 0x00040C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.60783 |
.rdata | 0x00042000 | 0x0000BC52 | 0x0000BE00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.2184 |
.data | 0x0004E000 | 0x0002E058 | 0x00002400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.78324 |
.rsrc | 0x0007D000 | 0x000B354C | 0x000B3600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.17759 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.15561 | 892 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 6.15135 | 1864 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 6.17923 | 3240 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 5.67704 | 7336 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 2.9303 | 296 | Latin 1 / Western European | English - United States | RT_ICON |
6 | 7.22346 | 872 | Latin 1 / Western European | English - United States | RT_ICON |
7 | 6.48494 | 1864 | Latin 1 / Western European | English - United States | RT_ICON |
8 | 6.54975 | 3240 | Latin 1 / Western European | English - United States | RT_ICON |
9 | 5.94405 | 7336 | Latin 1 / Western European | English - United States | RT_ICON |
10 | 6.35582 | 872 | Latin 1 / Western European | English - United States | RT_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
OLEAUT32.dll |
SETUPAPI.dll |
SHELL32.dll |
SHLWAPI.dll |
USER32.dll |
ole32.dll |
Total processes
45
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 628 | "C:\Users\admin\AppData\Local\Temp\truecrypt_setup_7.1a.exe" | C:\Users\admin\AppData\Local\Temp\truecrypt_setup_7.1a.exe | explorer.exe | ||||||||||||
User: admin Company: TrueCrypt Foundation Integrity Level: HIGH Description: TrueCrypt Setup Exit code: 0 Version: 7.1a Modules
| |||||||||||||||
| 740 | C:\Windows\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2068 | "C:\Program Files\TrueCrypt\TrueCrypt.exe" | C:\Program Files\TrueCrypt\TrueCrypt.exe | — | explorer.exe | |||||||||||
User: admin Company: TrueCrypt Foundation Integrity Level: MEDIUM Description: TrueCrypt Exit code: 0 Version: 7.1a Modules
| |||||||||||||||
| 3228 | "C:\Program Files\TrueCrypt\TrueCrypt Format.exe" /sysenc | C:\Program Files\TrueCrypt\TrueCrypt Format.exe | — | TrueCrypt.exe | |||||||||||
User: admin Company: TrueCrypt Foundation Integrity Level: MEDIUM Description: TrueCrypt Format Exit code: 0 Version: 7.1a Modules
| |||||||||||||||
| 3420 | "C:\Users\admin\AppData\Local\Temp\truecrypt_setup_7.1a.exe" | C:\Users\admin\AppData\Local\Temp\truecrypt_setup_7.1a.exe | — | explorer.exe | |||||||||||
User: admin Company: TrueCrypt Foundation Integrity Level: MEDIUM Description: TrueCrypt Setup Exit code: 3221226540 Version: 7.1a Modules
| |||||||||||||||
| 4056 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
551
Read events
325
Write events
226
Delete events
0
Modification events
| (PID) Process: | (628) truecrypt_setup_7.1a.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 400000000000000038DA8ED5F006D60174020000680D0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (628) truecrypt_setup_7.1a.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 400000000000000038DA8ED5F006D60174020000680D0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (628) truecrypt_setup_7.1a.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 34 | |||
| (PID) Process: | (628) truecrypt_setup_7.1a.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4000000000000000109CD1D5F006D60174020000680D0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (628) truecrypt_setup_7.1a.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000109CD1D5F006D60174020000000A0000E8030000010000000000000000000000BD4EBDF496675A429C9CF838DD645D8E0000000000000000 | |||
| (PID) Process: | (628) truecrypt_setup_7.1a.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4000000000000000E0AEE4D5F006D60174020000000A0000E8030000000000000000000000000000BD4EBDF496675A429C9CF838DD645D8E0000000000000000 | |||
| (PID) Process: | (628) truecrypt_setup_7.1a.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Leave) |
Value: 40000000000000003A11E7D5F006D60174020000680D0000D3070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (628) truecrypt_setup_7.1a.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Leave) |
Value: 40000000000000003A11E7D5F006D60174020000680D0000D007000001000000000000000A010081BD4EBDF496675A429C9CF838DD645D8E0000000000000000 | |||
| (PID) Process: | (628) truecrypt_setup_7.1a.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Leave) |
Value: 40000000000000003A11E7D5F006D60174020000680D0000D507000001000000000000000A010081000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (628) truecrypt_setup_7.1a.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000003A11E7D5F006D60174020000680D0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
6
Suspicious files
3
Text files
2
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 740 | DllHost.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 4056 | vssvc.exe | C: | — | |
MD5:— | SHA256:— | |||
| 740 | DllHost.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{71eb9e4a-7515-43c1-ae69-a17e9912fc3b}_OnDiskSnapshotProp | binary | |
MD5:— | SHA256:— | |||
| 740 | DllHost.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:— | SHA256:— | |||
| 628 | truecrypt_setup_7.1a.exe | C:\Users\Public\Desktop\TrueCrypt.lnk | lnk | |
MD5:— | SHA256:— | |||
| 628 | truecrypt_setup_7.1a.exe | C:\Program Files\TrueCrypt\TrueCrypt User Guide.pdf | ||
MD5:60B1EA96C0DCB7238DA39844F0C11910 | SHA256:739D7A00489395F516239A506F2E0B614052401CD9F692B4F8CDE0CBF55B3C0A | |||
| 628 | truecrypt_setup_7.1a.exe | C:\Program Files\TrueCrypt\truecrypt-x64.sys | executable | |
MD5:370A6907DDF79532A39319492B1FA38A | SHA256:46AECC5160F04FC3FFE4D37B404CCBBD1C5DC1501C2CEEE8284FF544DBDF10F8 | |||
| 628 | truecrypt_setup_7.1a.exe | C:\Program Files\TrueCrypt\TrueCrypt Setup.exe | executable | |
MD5:7A23AC83A0856C352025A6F7C9CC1526 | SHA256:E95ECA399DFE95500C4DE569EFC4CC77B75E2B66A864D467DF37733EC06A0FF2 | |||
| 628 | truecrypt_setup_7.1a.exe | C:\Program Files\TrueCrypt\truecrypt.sys | executable | |
MD5:ED5E4CE36C54F55E7698642E94D32EC7 | SHA256:07BD324083D1784F8F716C528D530003369E6D87EFC7B79BCAA1767F80DA4FDC | |||
| 628 | truecrypt_setup_7.1a.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\TrueCrypt\TrueCrypt Website.url | text | |
MD5:9CDA3A91CF04824781BBEBF415FE5211 | SHA256:8CE38040F962B921742AB9C657E81E0AB8565C5DDE26B0D4C709E92FB0ADA057 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report