| File name: | setup.exe |
| Full analysis: | https://app.any.run/tasks/b493ba2c-cff1-4c8a-844c-5fe72f6d7cd4 |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2022, 00:55:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | D2EA92875A1B9A5BDCCF966F17C545B7 |
| SHA1: | 40D18FCEBC8105512369910D9F30C95C24B53CFD |
| SHA256: | E94A49E237EC3C99ABEAB49A8A676073D31F9BE841D4A38AFC555EC90893EFCF |
| SSDEEP: | 49152:MDyo7MklXa+1NI9ZTSTIlqBbjbETbmjCg4:DOMklq+1NIoNj+byCj |
MALICIOUS
Drops executable file immediately after starts
- msiexec.exe (PID: 2824)
Loads dropped or rewritten executable
- GCloud.exe (PID: 2668)
Application was dropped or rewritten from another process
- GCloud.exe (PID: 2668)
SUSPICIOUS
Checks supported languages
- setup.exe (PID: 3904)
- msiexec.exe (PID: 2824)
- GCloud.exe (PID: 2668)
- MsiExec.exe (PID: 3848)
Reads the computer name
- setup.exe (PID: 3904)
- msiexec.exe (PID: 2824)
- GCloud.exe (PID: 2668)
- MsiExec.exe (PID: 3848)
Executable content was dropped or overwritten
- setup.exe (PID: 3904)
- msiexec.exe (PID: 2824)
Executed as Windows Service
- vssvc.exe (PID: 1388)
- GCloud.exe (PID: 2668)
Reads Windows owner or organization settings
- MSIEXEC.EXE (PID: 2880)
- msiexec.exe (PID: 2824)
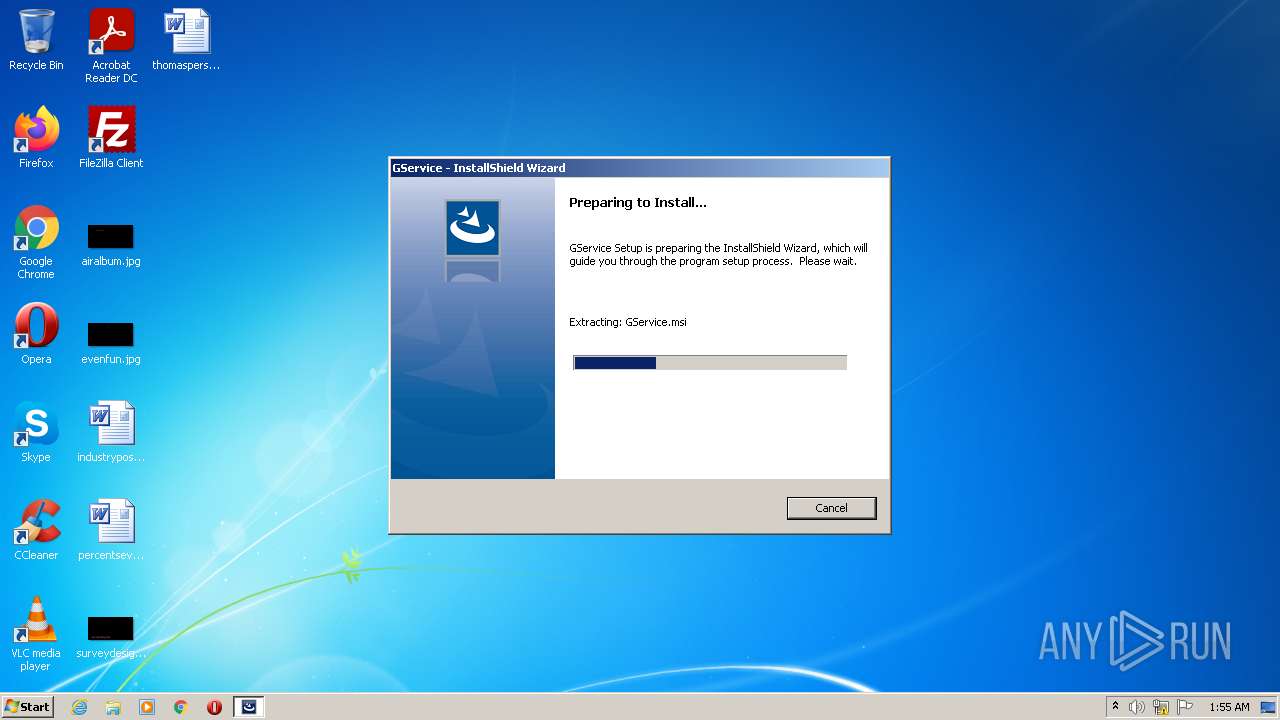
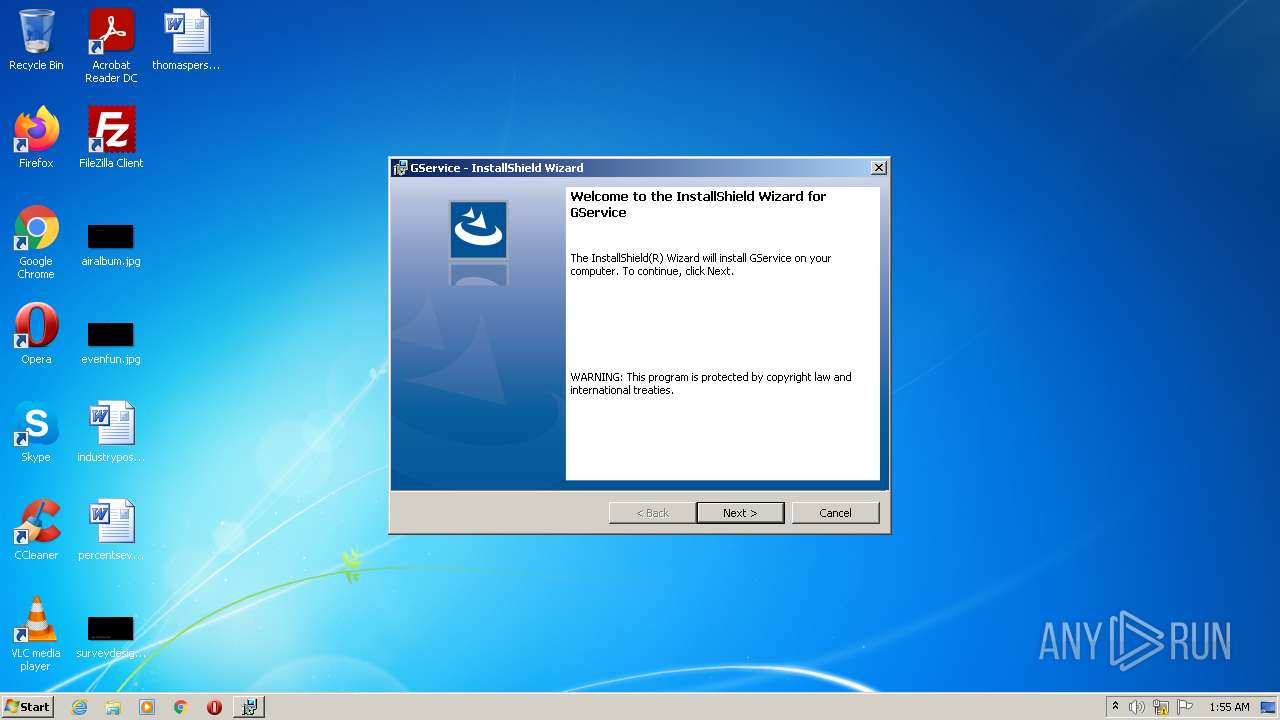
Starts Microsoft Installer
- setup.exe (PID: 3904)
Reads the Windows organization settings
- MSIEXEC.EXE (PID: 2880)
- msiexec.exe (PID: 2824)
Creates a directory in Program Files
- msiexec.exe (PID: 2824)
Drops a file with a compile date too recent
- msiexec.exe (PID: 2824)
Uses NETSH.EXE for network configuration
- GCloud.exe (PID: 2668)
Reads Environment values
- Netsh.exe (PID: 2768)
- GCloud.exe (PID: 2668)
- vssvc.exe (PID: 1388)
INFO
Checks supported languages
- vssvc.exe (PID: 1388)
- MSIEXEC.EXE (PID: 2880)
- Netsh.exe (PID: 2768)
Reads the computer name
- vssvc.exe (PID: 1388)
- MSIEXEC.EXE (PID: 2880)
- Netsh.exe (PID: 2768)
Creates files in the program directory
- msiexec.exe (PID: 2824)
Creates a software uninstall entry
- msiexec.exe (PID: 2824)
Searches for installed software
- msiexec.exe (PID: 2824)
Application launched itself
- msiexec.exe (PID: 2824)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (56.1) |
|---|---|---|
| .scr | | | Windows screen saver (26.6) |
| .exe | | | Win32 Executable (generic) (9.1) |
| .exe | | | Generic Win/DOS Executable (4) |
| .exe | | | DOS Executable Generic (4) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2015-Sep-09 05:59:06 |
| Detected languages: |
|
| Debug artifacts: |
|
| CompanyName: | GIGABYTE |
| FileDescription: | Setup Launcher Unicode |
| FileVersion: | 1.19.0624.1 |
| InternalName: | Setup |
| LegalCopyright: | Copyright (c) 2015 Flexera Software LLC. All Rights Reserved. |
| OriginalFilename: | InstallShield Setup.exe |
| ProductName: | GService |
| ProductVersion: | 1.19.0624.1 |
| Internal Build Number: | 158438 |
| ISInternalVersion: | 22.0.347 |
| ISInternalDescription: | Setup Launcher Unicode |
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 144 |
| e_cp: | 3 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | - |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | - |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 256 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 4 |
| TimeDateStamp: | 2015-Sep-09 05:59:06 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 4096 | 734341 | 734720 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.58334 |
.rdata | 741376 | 221704 | 222208 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.10399 |
.data | 966656 | 35896 | 9728 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.50984 |
.rsrc | 1003520 | 324916 | 325120 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.62524 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.27303 | 1640 | Latin 1 / Western European | UNKNOWN | RT_ICON |
2 | 3.835 | 744 | Latin 1 / Western European | UNKNOWN | RT_ICON |
3 | 3.35696 | 296 | Latin 1 / Western European | UNKNOWN | RT_ICON |
4 | 6.14965 | 3752 | Latin 1 / Western European | UNKNOWN | RT_ICON |
5 | 6.18448 | 2216 | Latin 1 / Western European | UNKNOWN | RT_ICON |
6 | 4.85842 | 1384 | Latin 1 / Western European | UNKNOWN | RT_ICON |
7 | 5.57777 | 9640 | Latin 1 / Western European | UNKNOWN | RT_ICON |
8 | 5.81004 | 4264 | Latin 1 / Western European | UNKNOWN | RT_ICON |
9 | 6.06596 | 1128 | Latin 1 / Western European | UNKNOWN | RT_ICON |
10 | 3.22977 | 744 | Latin 1 / Western European | UNKNOWN | RT_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
CRYPT32.dll |
GDI32.dll |
KERNEL32.dll |
OLEAUT32.dll |
RPCRT4.dll |
SHELL32.dll |
USER32.dll |
VERSION.dll |
Total processes
46
Monitored processes
8
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1388 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1968 | "C:\Users\admin\AppData\Local\Temp\setup.exe" | C:\Users\admin\AppData\Local\Temp\setup.exe | — | Explorer.EXE | |||||||||||
User: admin Company: GIGABYTE Integrity Level: MEDIUM Description: Setup Launcher Unicode Exit code: 3221226540 Version: 1.19.0624.1 Modules
| |||||||||||||||
| 2668 | "C:\Program Files\GIGABYTE\GService\GCloud.exe" | C:\Program Files\GIGABYTE\GService\GCloud.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Integrity Level: SYSTEM Description: GCloud Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2768 | "Netsh.exe" advfirewall firewall add rule name="allow 9009" protocol=TCP dir=in localport=9009 action=allow | C:\Windows\system32\Netsh.exe | — | GCloud.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2824 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2880 | MSIEXEC.EXE /i "C:\Users\admin\AppData\Local\Downloaded Installations\{89481967-8BEF-4362-BA5A-D05CF787E272}\GService.msi" SETUPEXEDIR="C:\Users\admin\AppData\Local\Temp" SETUPEXENAME="setup.exe" | C:\Windows\system32\MSIEXEC.EXE | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3848 | C:\Windows\system32\MsiExec.exe -Embedding 74D05718AD9689AA712B56A42EB285F8 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3904 | "C:\Users\admin\AppData\Local\Temp\setup.exe" | C:\Users\admin\AppData\Local\Temp\setup.exe | Explorer.EXE | ||||||||||||
User: admin Company: GIGABYTE Integrity Level: HIGH Description: Setup Launcher Unicode Exit code: 0 Version: 1.19.0624.1 Modules
| |||||||||||||||
Total events
11 484
Read events
11 181
Write events
291
Delete events
12
Modification events
| (PID) Process: | (2824) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000001CB4A82E55D8D801080B0000F0050000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2824) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 40000000000000001CB4A82E55D8D801080B0000F0050000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2824) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 69 | |||
| (PID) Process: | (2824) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000009A13E92E55D8D801080B0000F0050000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2824) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000F475EB2E55D8D801080B0000800C0000E803000001000000000000000000000042A179B64970064E94A30410F1BC18760000000000000000 | |||
| (PID) Process: | (1388) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000B661F72E55D8D8016C050000380D0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1388) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000B661F72E55D8D8016C050000B40E0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1388) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000B661F72E55D8D8016C0500000C0D0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1388) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000B661F72E55D8D8016C050000140F0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1388) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4000000000000000C488FE2E55D8D8016C0500000C0D0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
11
Suspicious files
6
Text files
10
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2824 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3904 | setup.exe | C:\Users\admin\AppData\Local\Temp\{C03AD033-C676-4914-94AC-981C80F00D28}\GService.msi | executable | |
MD5:— | SHA256:— | |||
| 3904 | setup.exe | C:\Users\admin\AppData\Local\Temp\{C03AD033-C676-4914-94AC-981C80F00D28}\_ISMSIDEL.INI | text | |
MD5:— | SHA256:— | |||
| 2824 | msiexec.exe | C:\Windows\Installer\dc8af.msi | executable | |
MD5:— | SHA256:— | |||
| 2824 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:— | SHA256:— | |||
| 3904 | setup.exe | C:\Users\admin\AppData\Local\Temp\~9A7C.tmp | text | |
MD5:— | SHA256:— | |||
| 2824 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF352D05B47C385612.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2824 | msiexec.exe | C:\Windows\Installer\dc8b0.ipi | binary | |
MD5:— | SHA256:— | |||
| 2824 | msiexec.exe | C:\Windows\Installer\MSICA47.tmp | binary | |
MD5:— | SHA256:— | |||
| 2824 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{b679a142-7049-4e06-94a3-0410f1bc1876}_OnDiskSnapshotProp | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report