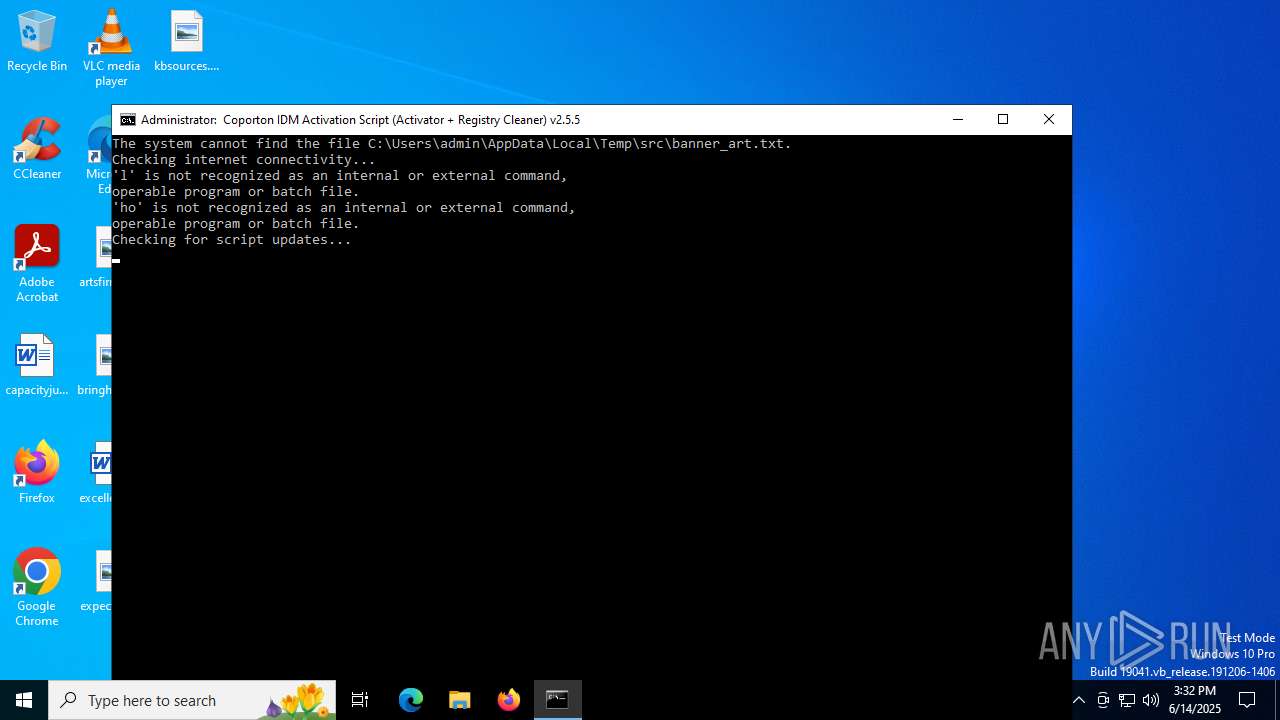
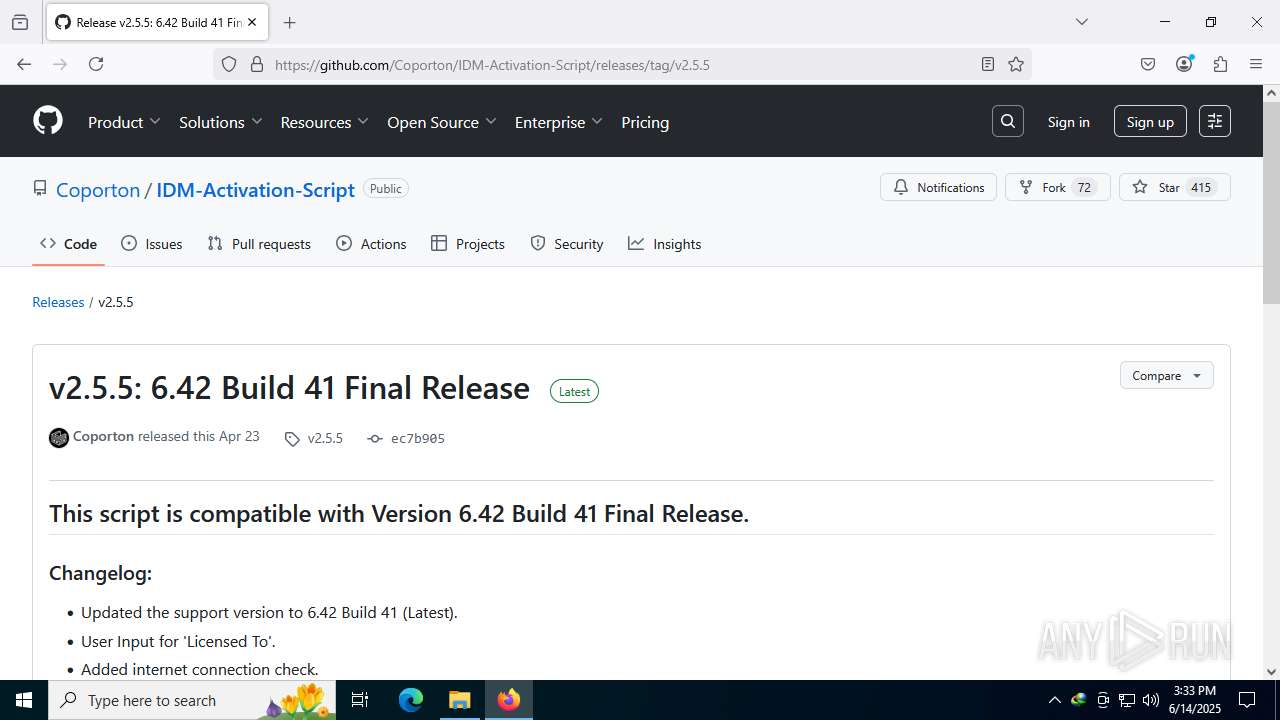
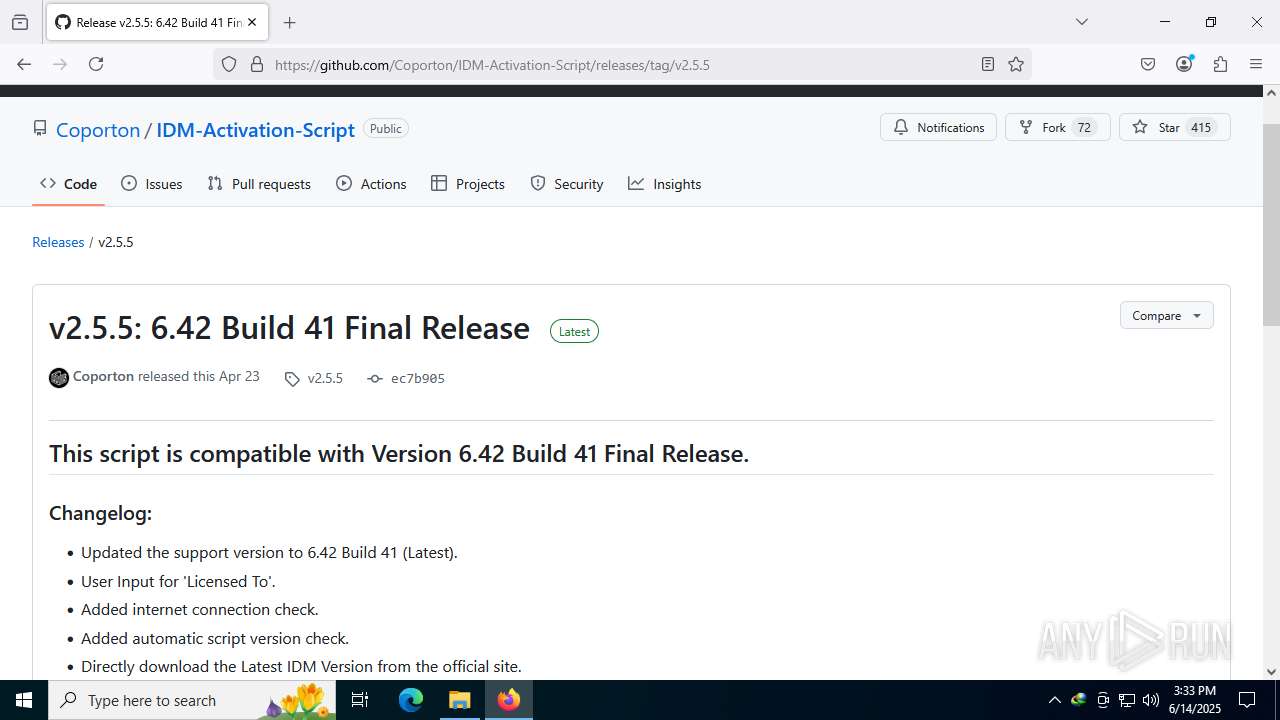
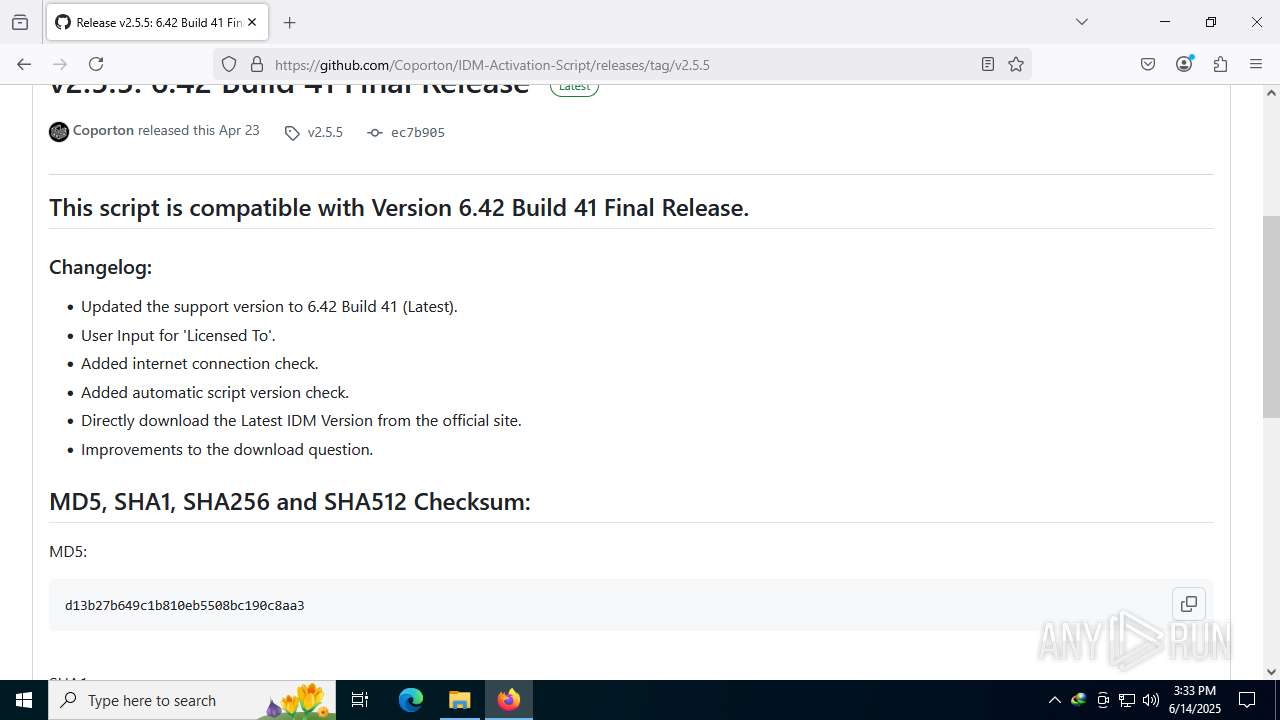
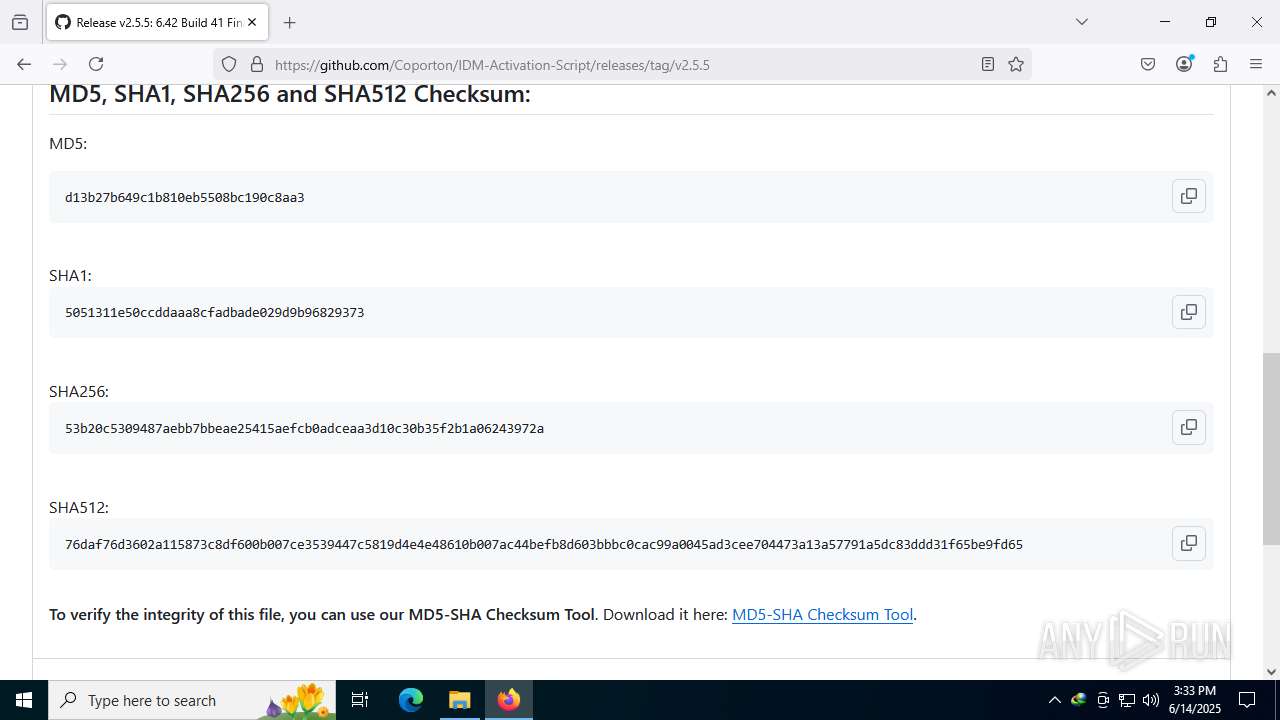
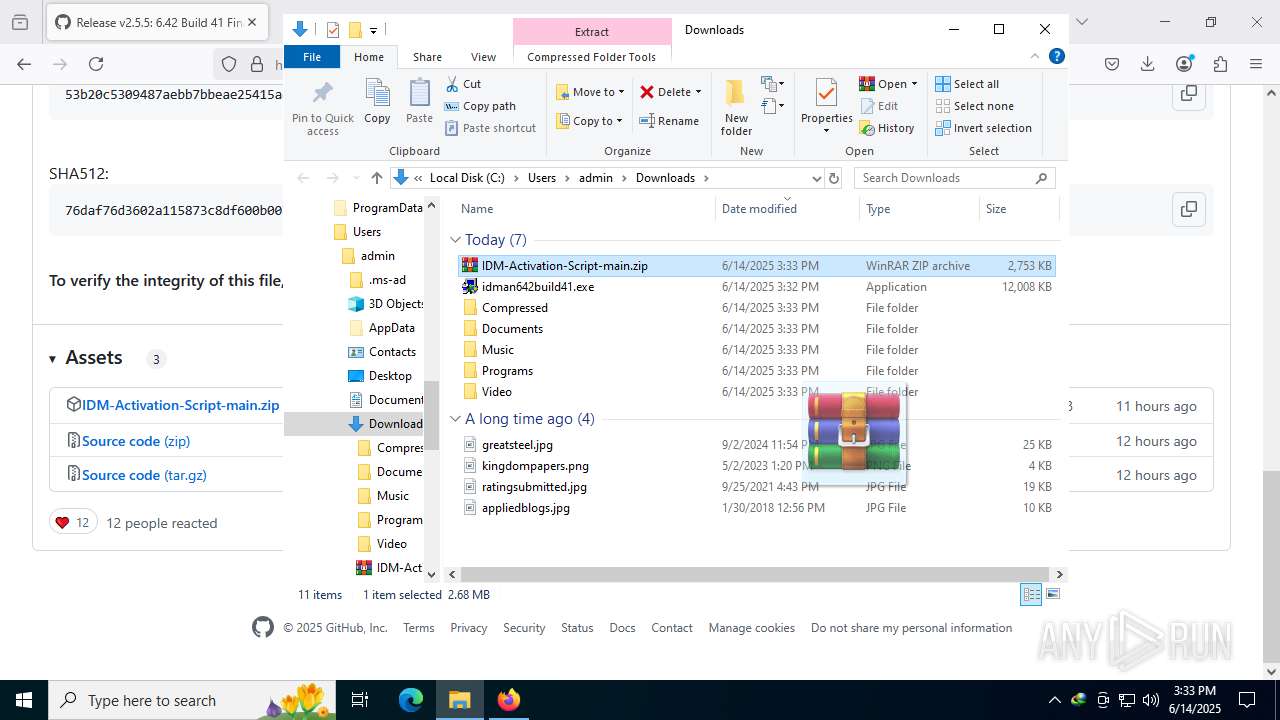
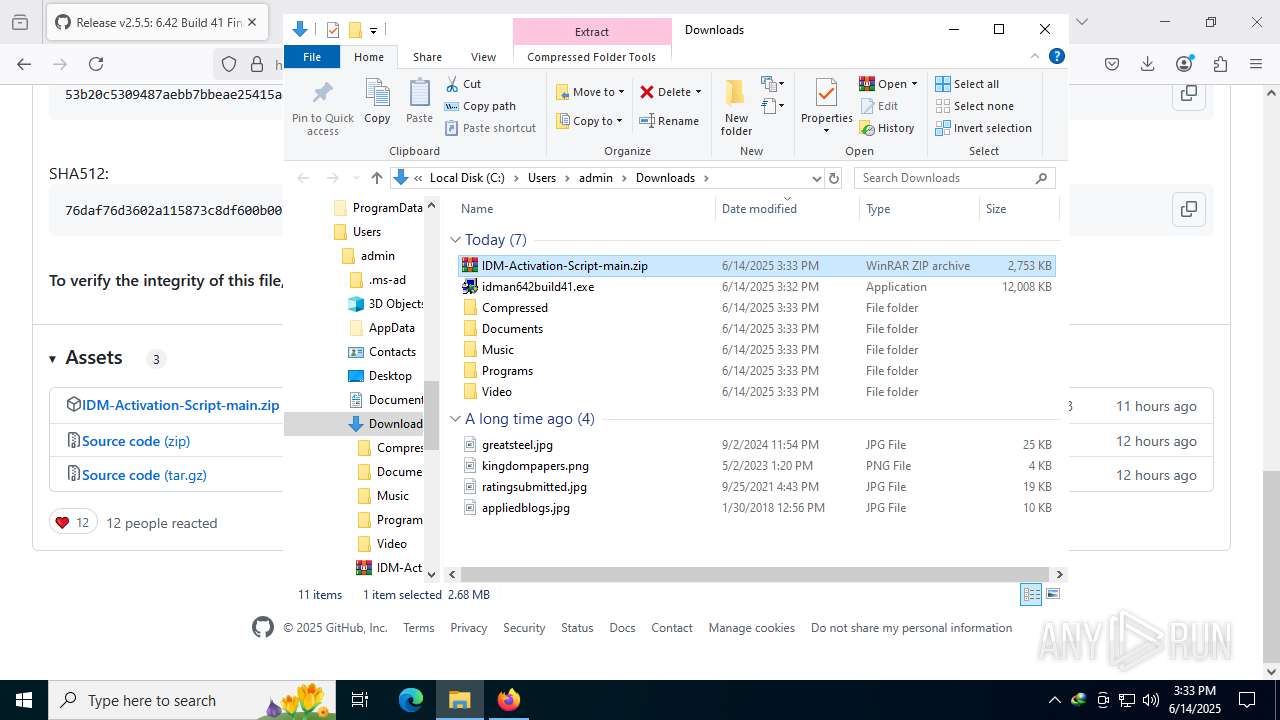
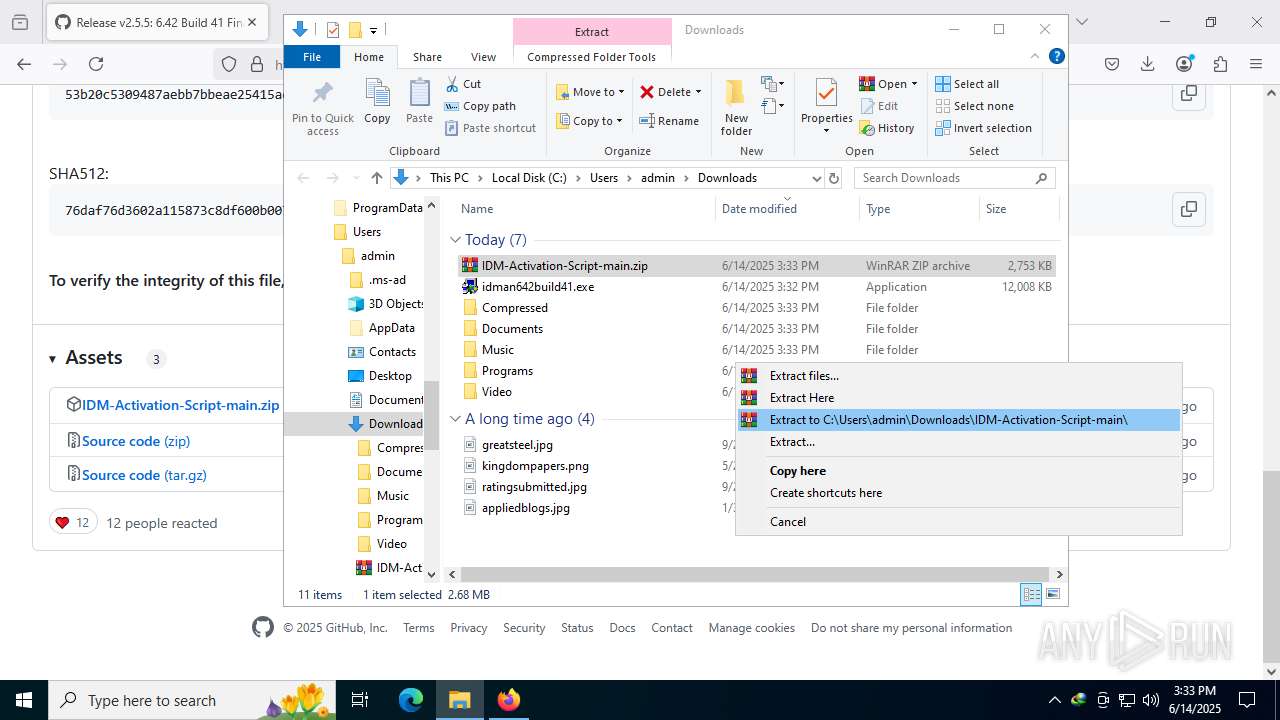
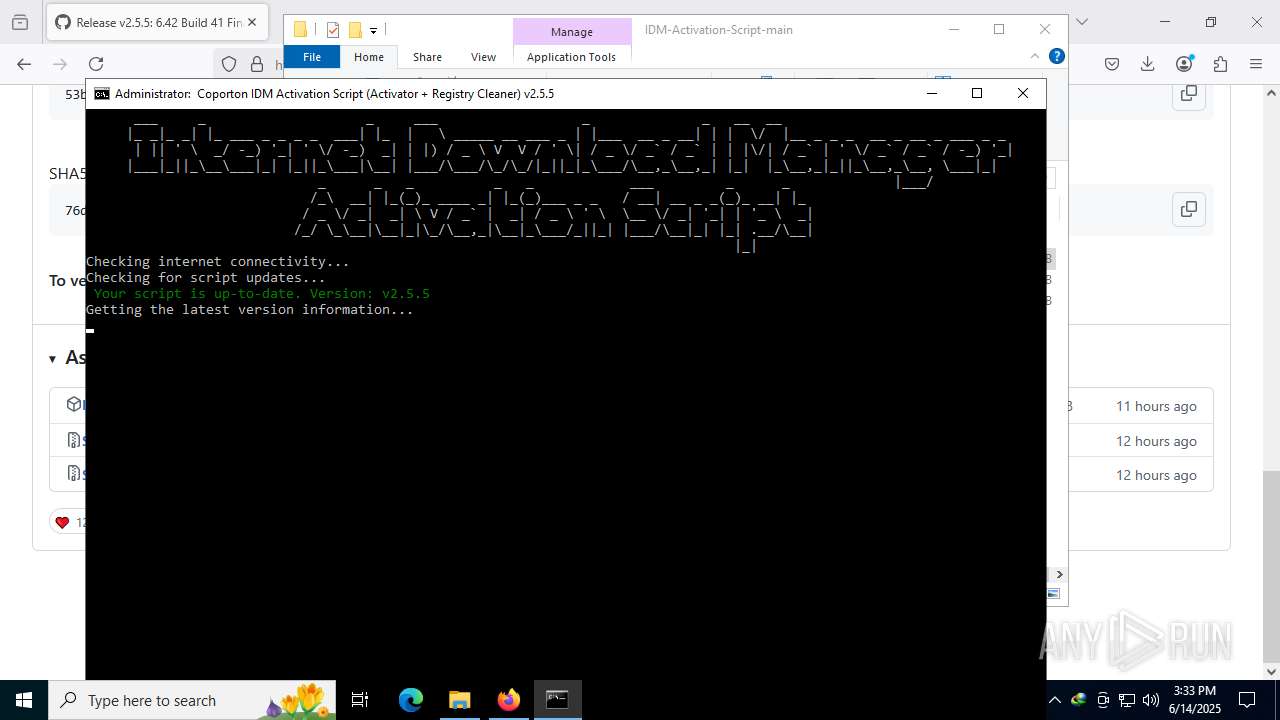
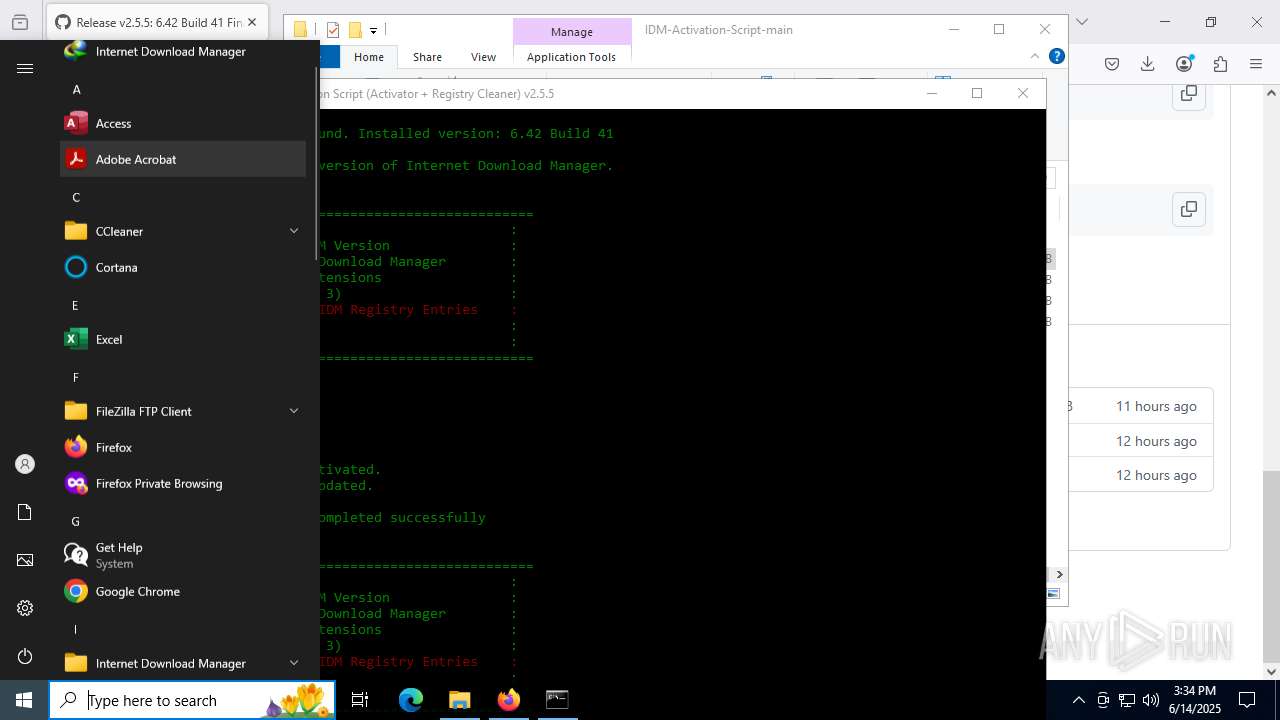
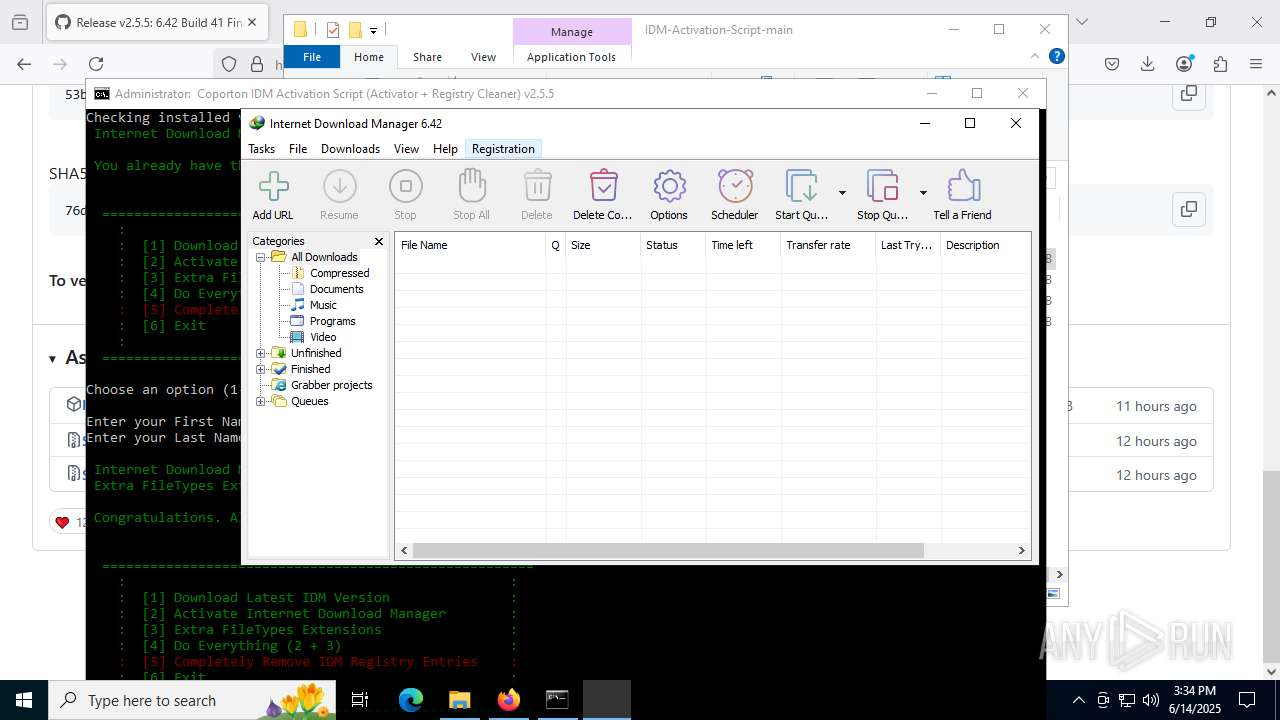
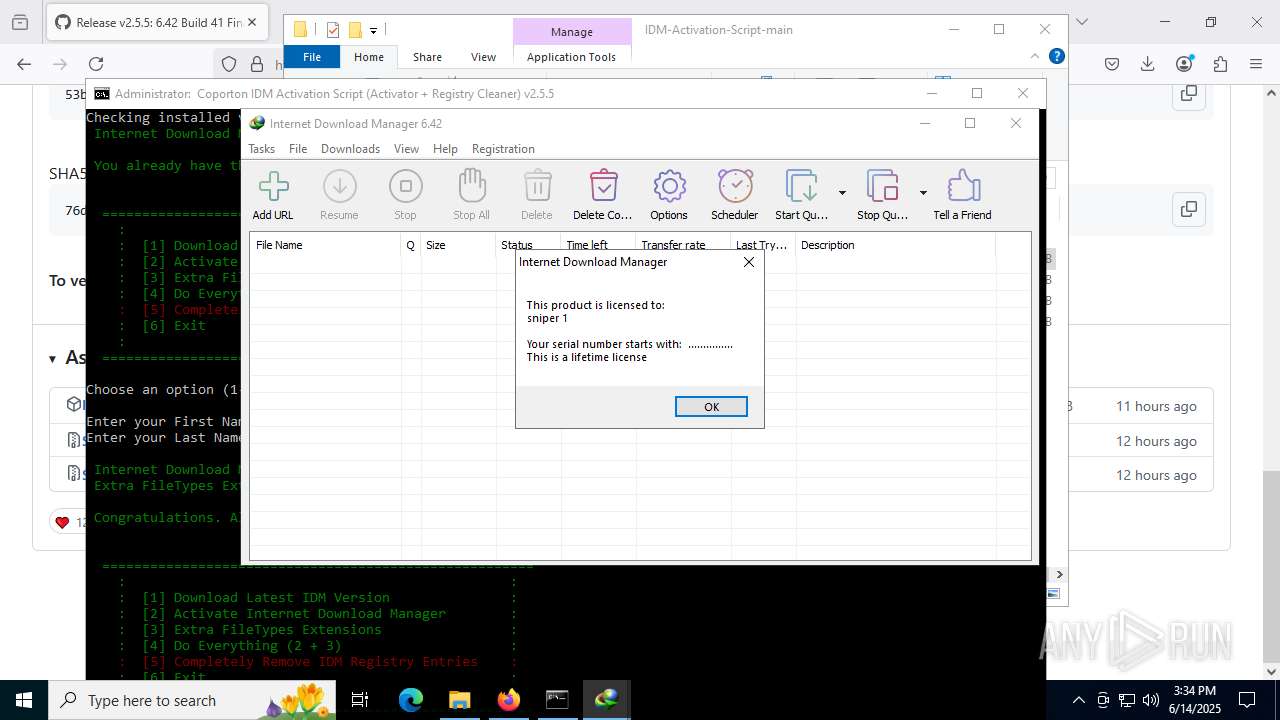
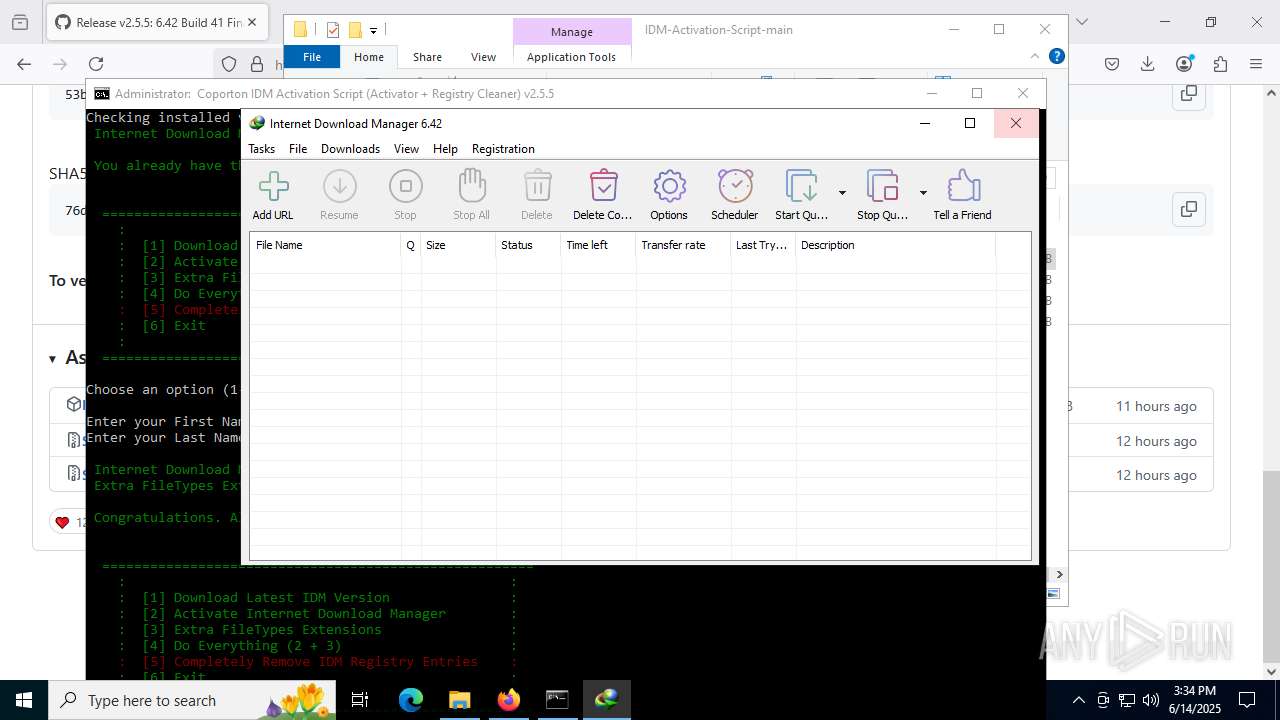
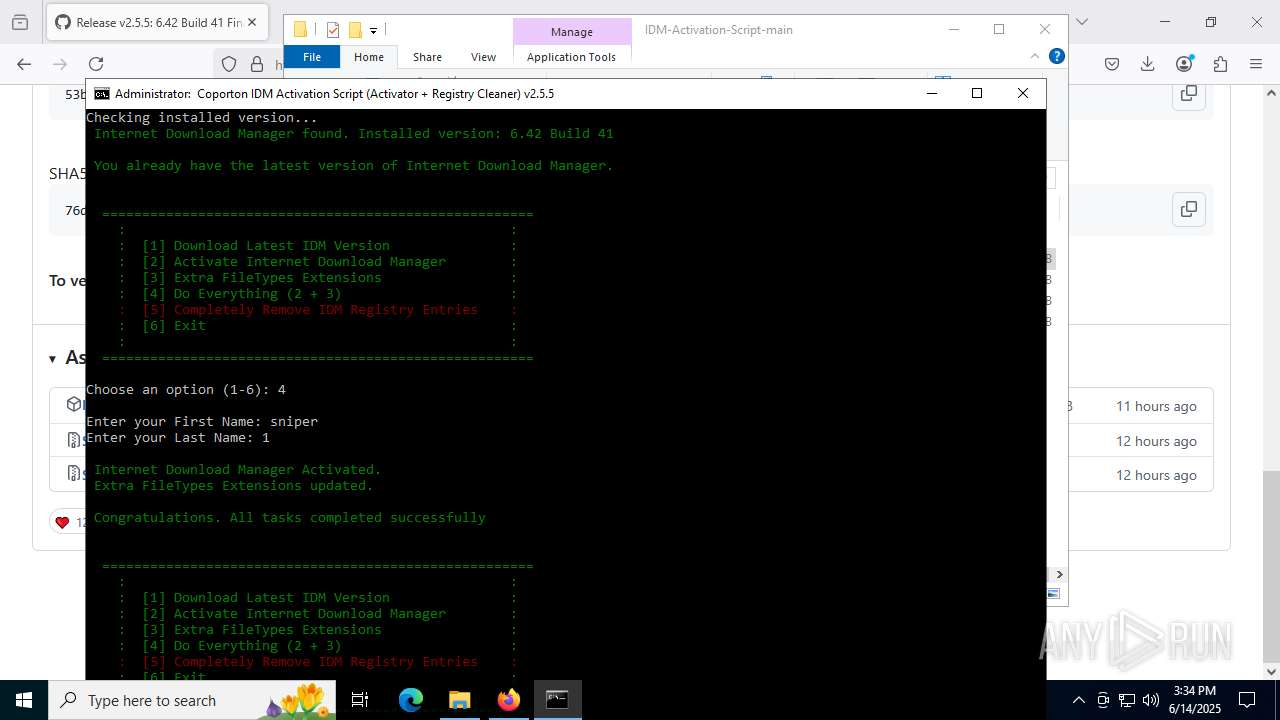
| File name: | IASL.cmd |
| Full analysis: | https://app.any.run/tasks/0e05d252-096c-4c35-94cb-2b9e781f6367 |
| Verdict: | Malicious activity |
| Analysis date: | June 14, 2025, 15:32:03 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, Unicode text, UTF-8 text, with escape sequences |
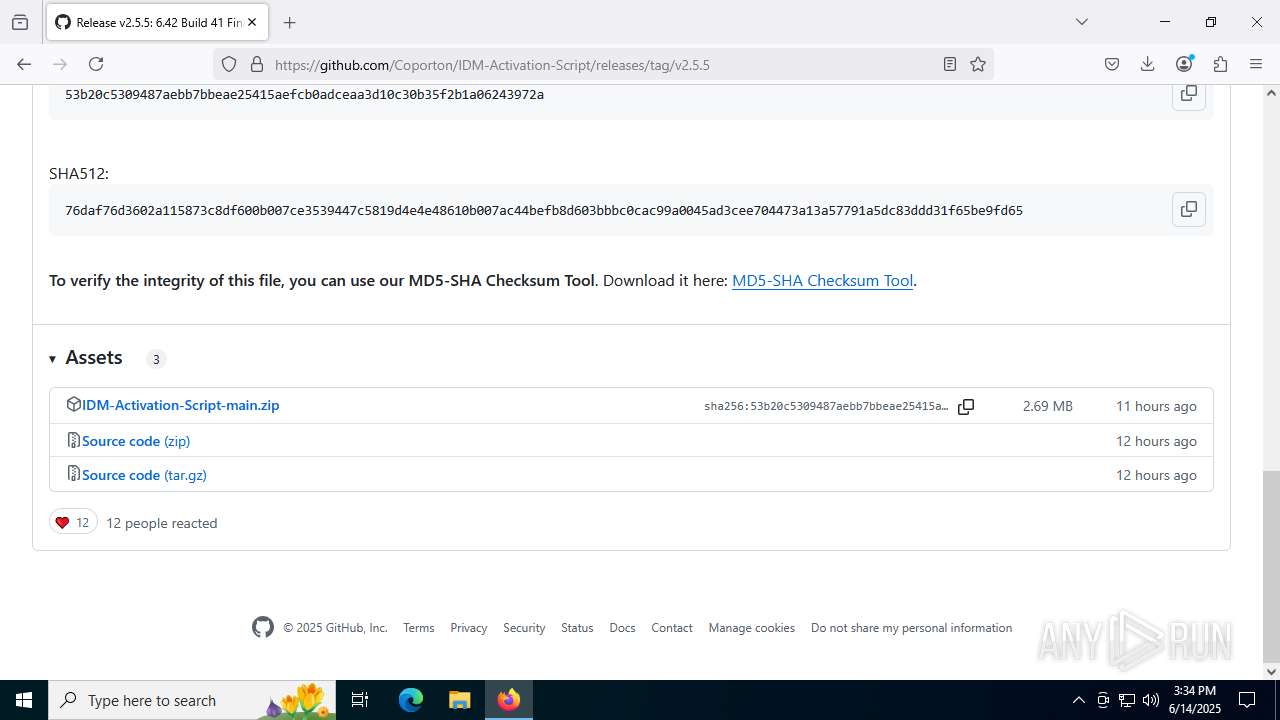
| MD5: | F9D919EB7BE54B65D3D1AB64E3259AC1 |
| SHA1: | 7573683B1C4FA0735FBEC66952074C27EA9ADC95 |
| SHA256: | E9404D07F95003F1A3E2A2F3EB37455529C9B3CC2A383FC3194B941DCFB0EAD6 |
| SSDEEP: | 192:HPlIGDENw3gLVODRqzXlWpYBZdSiNdLvZC1SzUG6BmtPJnt2vC96veoA6jeBOrCF:HPrQw3gLVO1qopY7dSsZC1X49Iyk8 |
MALICIOUS
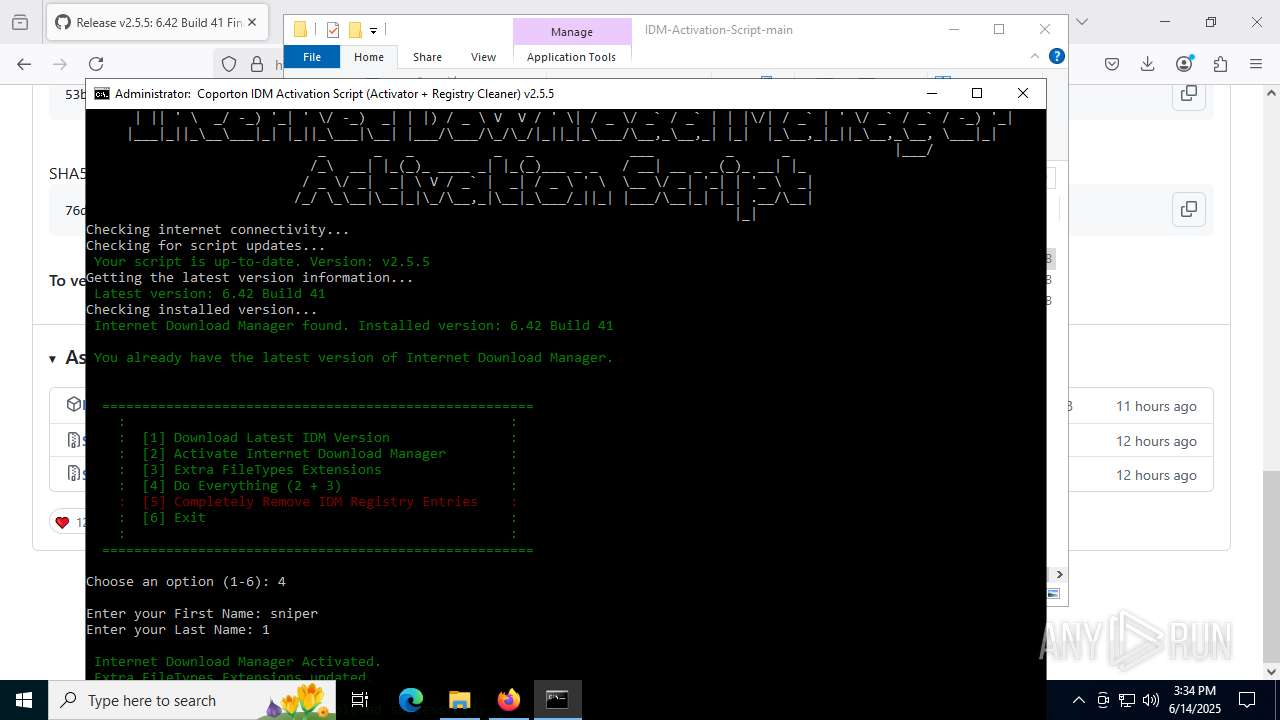
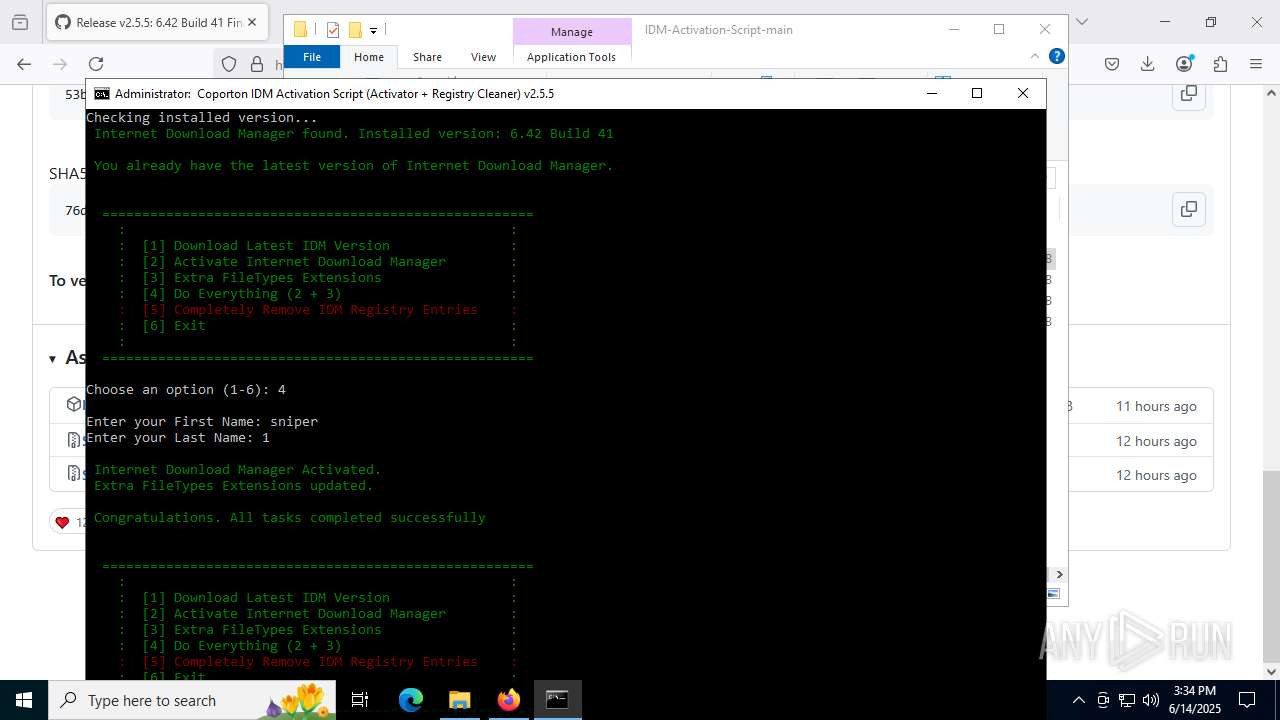
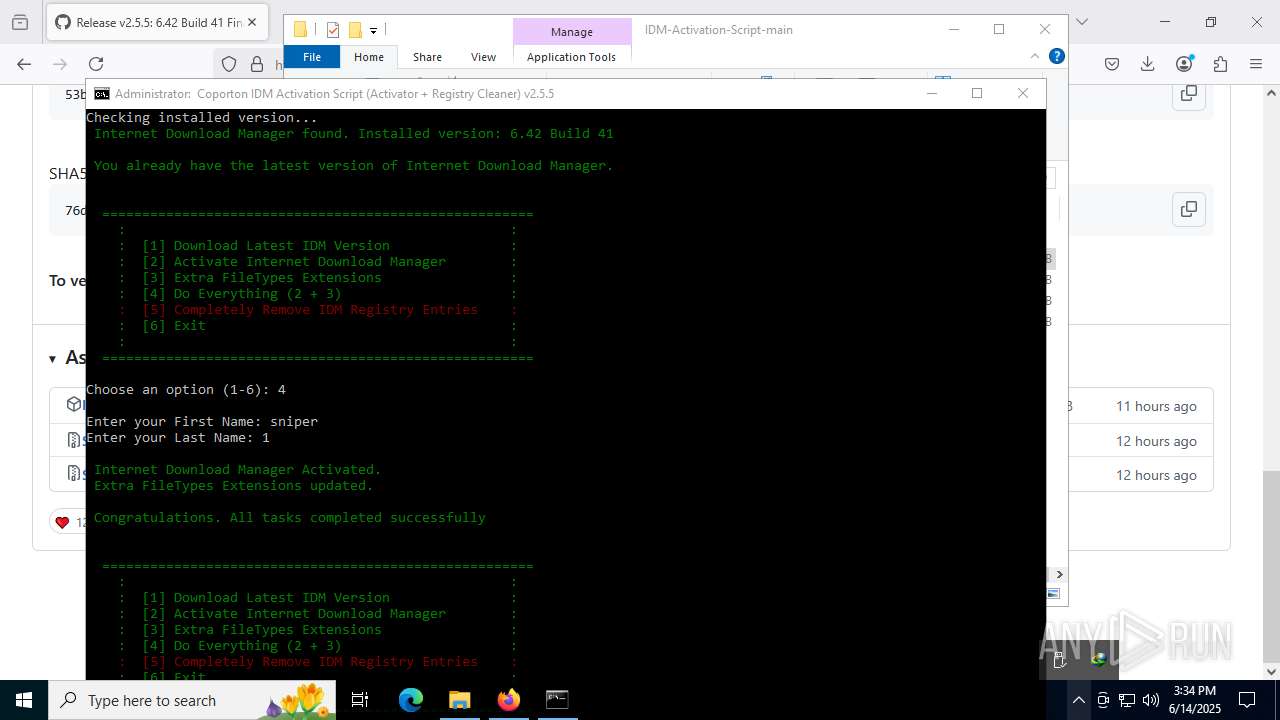
Registers / Runs the DLL via REGSVR32.EXE
- IDMan.exe (PID: 7472)
- IDM1.tmp (PID: 7892)
- Uninstall.exe (PID: 8152)
- IDMan.exe (PID: 8112)
GENERIC has been found (auto)
- rundll32.exe (PID: 4648)
- drvinst.exe (PID: 3620)
Starts NET.EXE for service management
- Uninstall.exe (PID: 8152)
- net.exe (PID: 416)
SUSPICIOUS
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 6684)
- cmd.exe (PID: 2032)
- cmd.exe (PID: 536)
- cmd.exe (PID: 6016)
The process executes VB scripts
- cmd.exe (PID: 6684)
- cmd.exe (PID: 6016)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 6896)
- cmd.exe (PID: 2032)
- wscript.exe (PID: 6540)
- cmd.exe (PID: 536)
Executing commands from a ".bat" file
- wscript.exe (PID: 6896)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6896)
Starts application with an unusual extension
- cmd.exe (PID: 2032)
- idman642build41.exe (PID: 7904)
- cmd.exe (PID: 536)
Application launched itself
- cmd.exe (PID: 2032)
- cmd.exe (PID: 536)
- WinRAR.exe (PID: 6700)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 640)
- cmd.exe (PID: 3768)
- cmd.exe (PID: 1200)
Executable content was dropped or overwritten
- drvinst.exe (PID: 3620)
- IDMan.exe (PID: 7472)
- rundll32.exe (PID: 4648)
- cmd.exe (PID: 536)
Drops a system driver (possible attempt to evade defenses)
- drvinst.exe (PID: 3620)
- rundll32.exe (PID: 4648)
Uses RUNDLL32.EXE to load library
- Uninstall.exe (PID: 8152)
Executing commands from ".cmd" file
- wscript.exe (PID: 6540)
Hides command output
- cmd.exe (PID: 4048)
- cmd.exe (PID: 4832)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 536)
- cmd.exe (PID: 4832)
- cmd.exe (PID: 4048)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 536)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 536)
INFO
Checks supported languages
- mode.com (PID: 4968)
- mode.com (PID: 3888)
- chcp.com (PID: 3028)
- curl.exe (PID: 4968)
- idman642build41.exe (PID: 7904)
- IDM1.tmp (PID: 7892)
Starts MODE.COM to configure console settings
- mode.com (PID: 4968)
- mode.com (PID: 3888)
- mode.com (PID: 6172)
- mode.com (PID: 7244)
Manual execution by a user
- firefox.exe (PID: 432)
- idman642build41.exe (PID: 7904)
- firefox.exe (PID: 7900)
- idman642build41.exe (PID: 7364)
- firefox.exe (PID: 5012)
- cmd.exe (PID: 6016)
- WinRAR.exe (PID: 3924)
- IDMan.exe (PID: 7732)
- WinRAR.exe (PID: 6700)
- msedge.exe (PID: 4768)
Application launched itself
- firefox.exe (PID: 432)
- firefox.exe (PID: 536)
- firefox.exe (PID: 7900)
- firefox.exe (PID: 5012)
- firefox.exe (PID: 6312)
- msedge.exe (PID: 4768)
Changes the display of characters in the console
- cmd.exe (PID: 2032)
- cmd.exe (PID: 536)
Execution of CURL command
- cmd.exe (PID: 2032)
- cmd.exe (PID: 536)
Reads the computer name
- curl.exe (PID: 4968)
- idman642build41.exe (PID: 7904)
Create files in a temporary directory
- curl.exe (PID: 4968)
- idman642build41.exe (PID: 7904)
Executable content was dropped or overwritten
- firefox.exe (PID: 536)
- WinRAR.exe (PID: 3924)
Launching a file from the Downloads directory
- firefox.exe (PID: 536)
- firefox.exe (PID: 6312)
The sample compiled with english language support
- IDMan.exe (PID: 7472)
- firefox.exe (PID: 536)
- rundll32.exe (PID: 4648)
- drvinst.exe (PID: 3620)
- WinRAR.exe (PID: 3924)
- firefox.exe (PID: 6312)
- cmd.exe (PID: 536)
Reads Microsoft Office registry keys
- firefox.exe (PID: 536)
INTERNETDOWNLOADMANAGER mutex has been found
- idman642build41.exe (PID: 7904)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
318
Monitored processes
161
Malicious processes
10
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 416 | "C:\Windows\System32\net.exe" start IDMWFP | C:\Windows\SysWOW64\net.exe | — | Uninstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 432 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 136.0 Modules
| |||||||||||||||
| 536 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 136.0 Modules
| |||||||||||||||
| 536 | "C:\WINDOWS\System32\cmd.exe" /C "C:\Users\admin\DOWNLO~1\IDM-AC~1\IDM-AC~1\IASL.cmd" | C:\Windows\System32\cmd.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | C:\WINDOWS\system32\cmd.exe /c findstr /i "tag_name" "C:\Users\admin\AppData\Local\Temp\latest_release.json" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=8084,i,4756552329492556014,9324361560597647220,262144 --variations-seed-version --mojo-platform-channel-handle=8128 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1200 | C:\WINDOWS\system32\cmd.exe /c findstr /i "<H3>What's new in version" "C:\Users\admin\AppData\Local\Temp\idm_news.html" | findstr /r /c:"Build [0-9]*" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1204 | regedit /s "C:\Users\admin\DOWNLO~1\IDM-AC~1\IDM-AC~1\src\extensions.bin" | C:\Windows\regedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1208 | "C:\Windows\System32\grpconv.exe" -o | C:\Windows\System32\grpconv.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1268 | findstr /i "tag_name" "C:\Users\admin\AppData\Local\Temp\latest_release.json" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
82 480
Read events
81 319
Write events
977
Delete events
184
Modification events
| (PID) Process: | (6684) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (6684) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6684) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6684) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6684) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6896) wscript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.FriendlyAppName |
Value: Windows Command Processor | |||
| (PID) Process: | (6896) wscript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.ApplicationCompany |
Value: Microsoft Corporation | |||
| (PID) Process: | (536) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (7892) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Internet Download Manager |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files (x86)\Internet Download Manager\Uninstall.exe | |||
| (PID) Process: | (7892) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Internet Download Manager |
| Operation: | write | Name: | DisplayName |
Value: Internet Download Manager | |||
Executable files
63
Suspicious files
1 413
Text files
427
Unknown types
31
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6684 | cmd.exe | C:\Users\admin\AppData\Local\Temp\getadmin.vbs | text | |
MD5:D14A6C18536B08C2D91CC10129CEC2CA | SHA256:88F0E55BE41422957E8F4FEC8CAF0F9ED4E68D1F0290171BA8F4BD26C19FA17D | |||
| 4968 | curl.exe | C:\Users\admin\AppData\Local\Temp\latest_release.json | binary | |
MD5:6991101047722B7E191CB89318D52D77 | SHA256:C9B32693A953A9FACD52BCF12047870848F04566ED7CF2896B350B4B57742389 | |||
| 536 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:3134ED3F12E4F4F8643DB90043B0FD7B | SHA256:26E4F122034D7A03F6DA0E707799B09CBEEBDAF8D7A3133A1F7BD894AC72EEA1 | |||
| 536 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:57979E33510BB12EFCB06B9FC83E939F | SHA256:0D3E6E5B0BEF63512826FF39DC39D1BA7B1DBAB7763B482D2B5E2BDA5A9743FF | |||
| 536 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 536 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 536 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 536 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\bounce-tracking-protection.sqlite-journal | binary | |
MD5:D674EBB4200B6103D81557DFF6B026B7 | SHA256:2AD459F52E681D96BC6C20460F9ECD0CCCB9BE90ABAD968C246B49E7CFA8C79B | |||
| 536 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:57979E33510BB12EFCB06B9FC83E939F | SHA256:0D3E6E5B0BEF63512826FF39DC39D1BA7B1DBAB7763B482D2B5E2BDA5A9743FF | |||
| 536 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
88
TCP/UDP connections
331
DNS requests
407
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
764 | lsass.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | — | — | whitelisted |
764 | lsass.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPlNxcMEqnlIVyH5VuZ4lawhZX3QQU9oUKOxGG4QR9DqoLLNLuzGR7e64CECoW9cIBGAf3CpJj3Tw5qfI%3D | unknown | — | — | whitelisted |
764 | lsass.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | unknown | — | — | whitelisted |
536 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
536 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
536 | firefox.exe | POST | 200 | 142.250.186.99:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
536 | firefox.exe | POST | 200 | 216.58.206.67:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
536 | firefox.exe | POST | 200 | 2.16.168.113:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
536 | firefox.exe | POST | 200 | 2.16.168.113:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
536 | firefox.exe | POST | 200 | 216.58.206.67:80 | http://o.pki.goog/s/wr3/3H4 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6216 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4968 | curl.exe | 140.82.121.6:443 | api.github.com | GITHUB | US | whitelisted |
764 | lsass.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
536 | firefox.exe | 34.160.144.191:443 | content-signature-2.cdn.mozilla.net | GOOGLE | US | whitelisted |
536 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
536 | firefox.exe | 34.36.137.203:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
api.github.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
content-signature-2.cdn.mozilla.net |
| whitelisted |
content-signature-chains.prod.autograph.services.mozaws.net |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
8052 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
8052 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
8052 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
8052 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
8052 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
8052 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
8052 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |