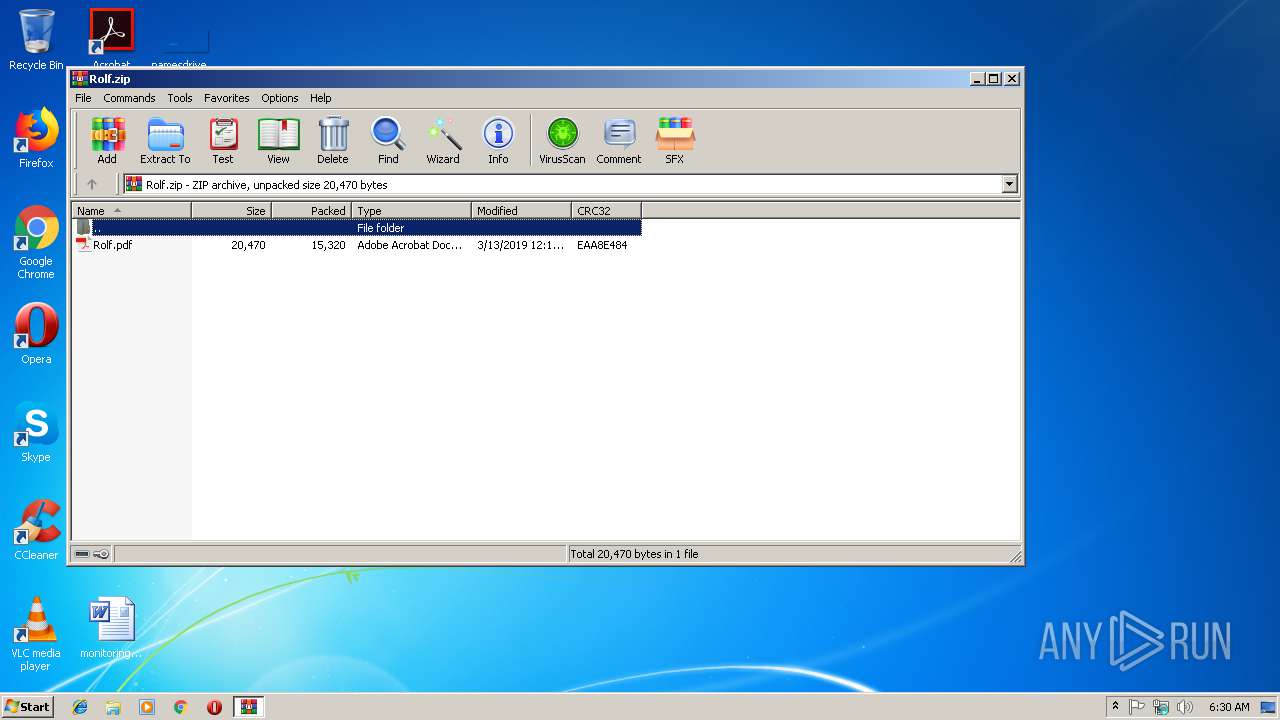
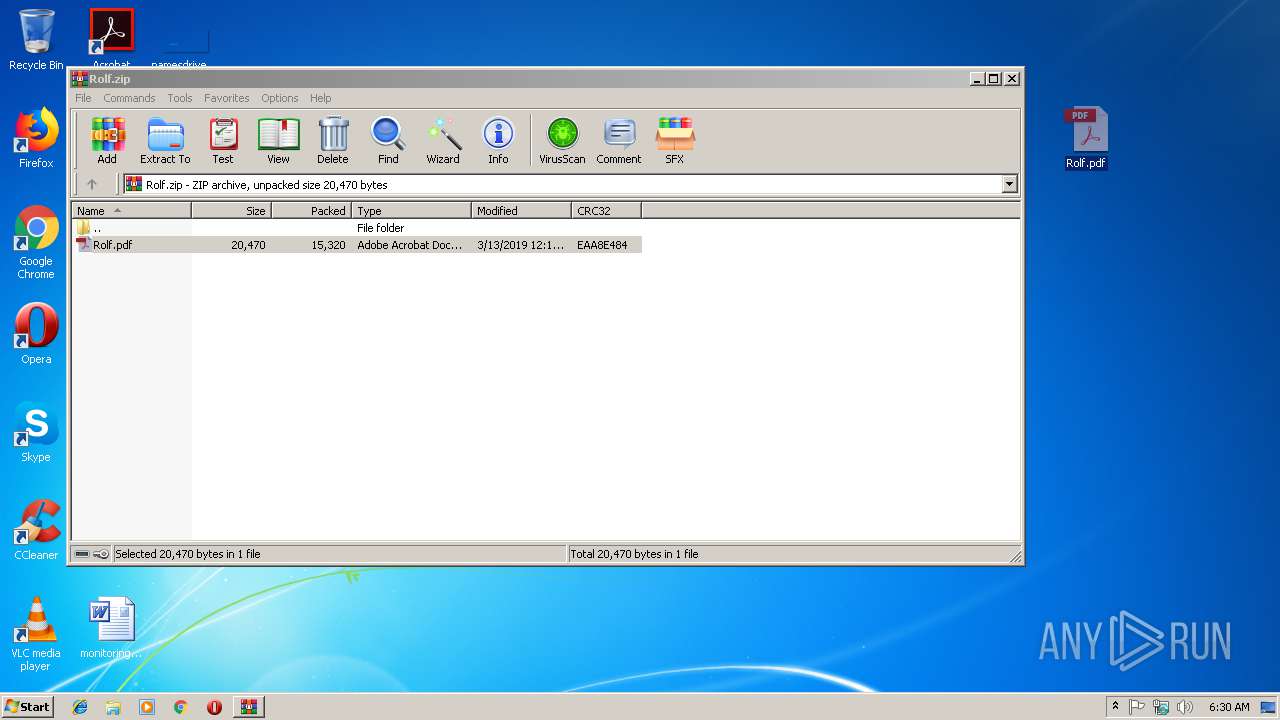
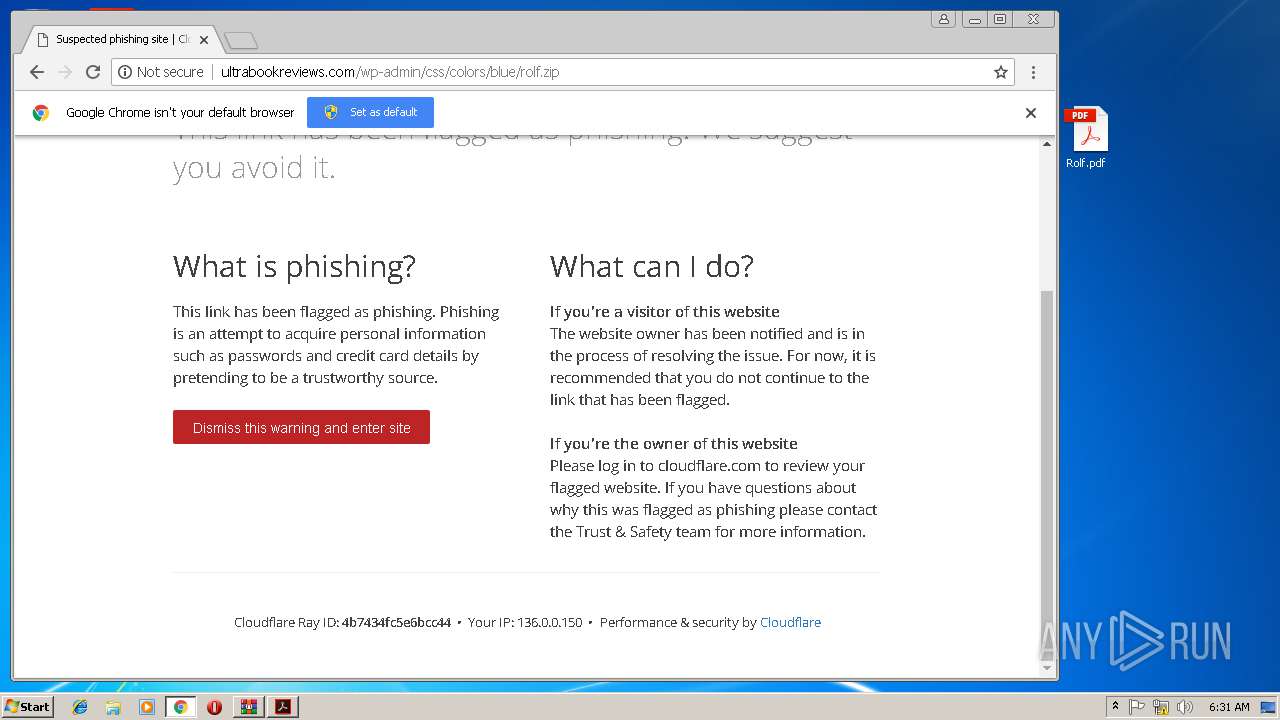
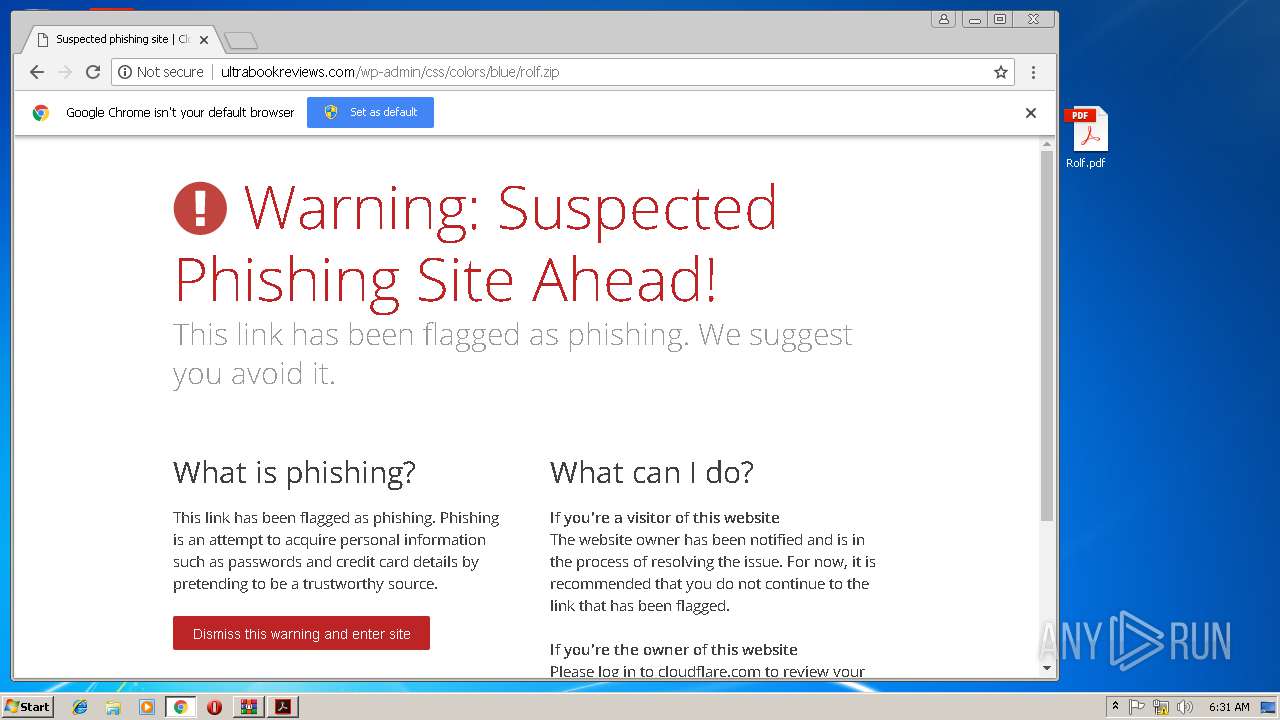
| File name: | Rolf.zip |
| Full analysis: | https://app.any.run/tasks/b2dc78d9-ec2f-4d0d-b6a0-75acecd56864 |
| Verdict: | Malicious activity |
| Analysis date: | March 14, 2019, 06:30:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 3715512504DFA3BC16886EDD79D51A1A |
| SHA1: | 45A4B3E3338F27ED9D7D32B9E47D8146E6E76E42 |
| SHA256: | E9340F2A6DCACAD19E5896BEB5D12947B4E6AD13EB9C921395BDA644A297F6BC |
| SSDEEP: | 384:tMAmIZmszLwVzA+a3NJXJ0UfoUj0ff4DFEvs0E37hC/qiaG8bb+LU:OA2o9pJrN0fwDFV0eESia7qA |
MALICIOUS
No malicious indicators.SUSPICIOUS
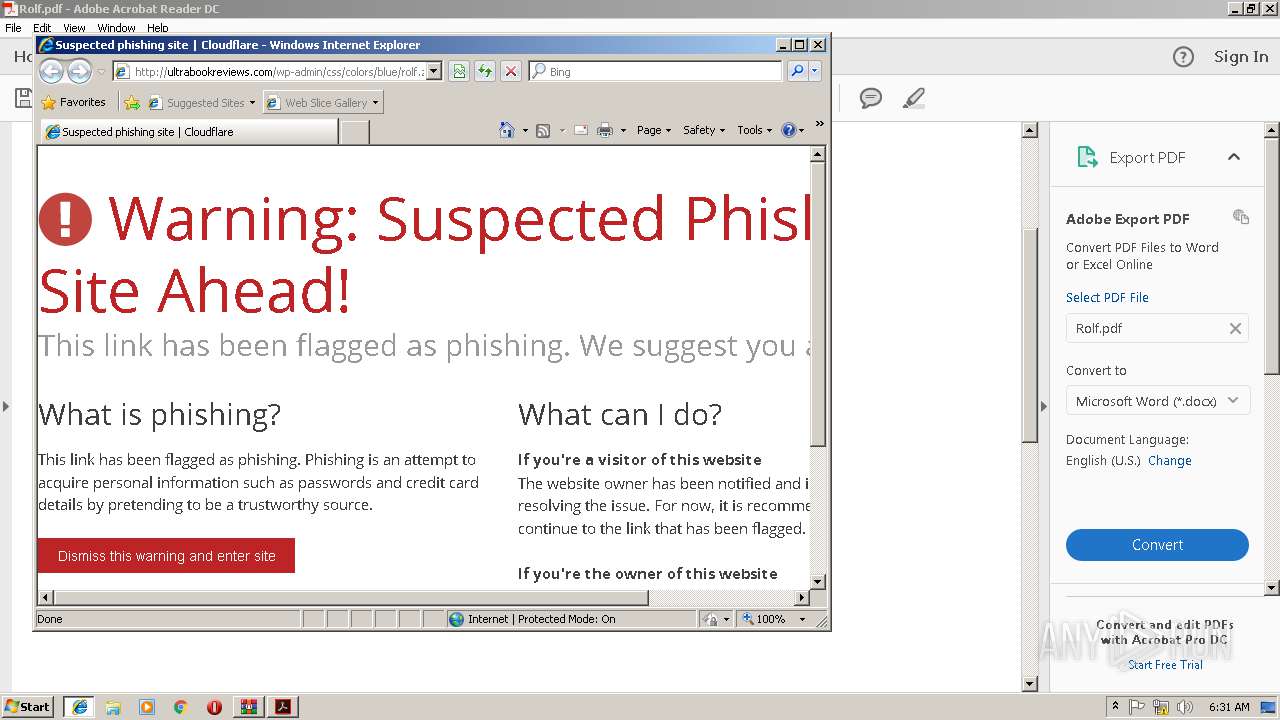
Starts Internet Explorer
- AcroRd32.exe (PID: 3664)
Creates files in the program directory
- AdobeARM.exe (PID: 1488)
Executable content was dropped or overwritten
- AdobeARM.exe (PID: 1488)
INFO
Application launched itself
- AcroRd32.exe (PID: 3664)
- chrome.exe (PID: 2972)
- iexplore.exe (PID: 2840)
- RdrCEF.exe (PID: 3128)
Reads Internet Cache Settings
- iexplore.exe (PID: 3660)
- iexplore.exe (PID: 3620)
Creates files in the user directory
- iexplore.exe (PID: 3660)
- iexplore.exe (PID: 2840)
Changes internet zones settings
- iexplore.exe (PID: 2840)
- iexplore.exe (PID: 2796)
Reads internet explorer settings
- iexplore.exe (PID: 3660)
- iexplore.exe (PID: 3620)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:03:13 12:14:02 |
| ZipCRC: | 0xeaa8e484 |
| ZipCompressedSize: | 15320 |
| ZipUncompressedSize: | 20470 |
| ZipFileName: | Rolf.pdf |
Total processes
55
Monitored processes
23
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 560 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=916,8567100111887030192,16938160832286420175,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=2BAF9D1D9F42DE6FA6861624CB396F59 --mojo-platform-channel-handle=512 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1424 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=916,8567100111887030192,16938160832286420175,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=3F3E08F93A7A06DE8156850C2DD7CD09 --mojo-platform-channel-handle=2384 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1488 | "C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" /PRODUCT:Reader /VERSION:15.0 /MODE:3 | C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Reader and Acrobat Manager Exit code: 0 Version: 1.824.27.2646 Modules
| |||||||||||||||
| 2092 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=68.0.3440.106 --initial-client-data=0x78,0x7c,0x80,0x74,0x84,0x6d6a00b0,0x6d6a00c0,0x6d6a00cc | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2372 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=916,8567100111887030192,16938160832286420175,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=CAFF865DD87C6D59A645389A715F040C --mojo-platform-channel-handle=988 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2796 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2840 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2940 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=916,8567100111887030192,16938160832286420175,131072 --enable-features=PasswordImport --service-pipe-token=AFB4D28F15EF9AB2E779C69EE7ADEBE4 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=AFB4D28F15EF9AB2E779C69EE7ADEBE4 --renderer-client-id=5 --mojo-platform-channel-handle=1900 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2972 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3032 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Rolf.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
1 846
Read events
1 642
Write events
197
Delete events
7
Modification events
| (PID) Process: | (3032) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3032) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3032) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3032) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Rolf.zip | |||
| (PID) Process: | (3032) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3032) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3032) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3032) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3180) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (3180) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | bExpandRHPInViewer |
Value: 1 | |||
Executable files
2
Suspicious files
56
Text files
103
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3180 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages-journal | — | |
MD5:— | SHA256:— | |||
| 3180 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9Rtiuasz_9kqhbz_2gc.tmp | — | |
MD5:— | SHA256:— | |||
| 3180 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9Rye3yt4_9kqhby_2gc.tmp | — | |
MD5:— | SHA256:— | |||
| 3180 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R1pxl2f_9kqhbx_2gc.tmp | — | |
MD5:— | SHA256:— | |||
| 3180 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R1gb24oy_9kqhc0_2gc.tmp | — | |
MD5:— | SHA256:— | |||
| 3180 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R16b17lk_9kqhc1_2gc.tmp | — | |
MD5:— | SHA256:— | |||
| 2840 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2840 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3660 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\rolf[1].zip | — | |
MD5:— | SHA256:— | |||
| 2840 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\favicon[1].htm | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
35
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3664 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/message.zip | unknown | — | — | whitelisted |
3664 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/278_15_23_20070.zip | unknown | — | — | whitelisted |
3664 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/280_15_23_20070.zip | unknown | — | — | whitelisted |
3664 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/281_15_23_20070.zip | unknown | — | — | whitelisted |
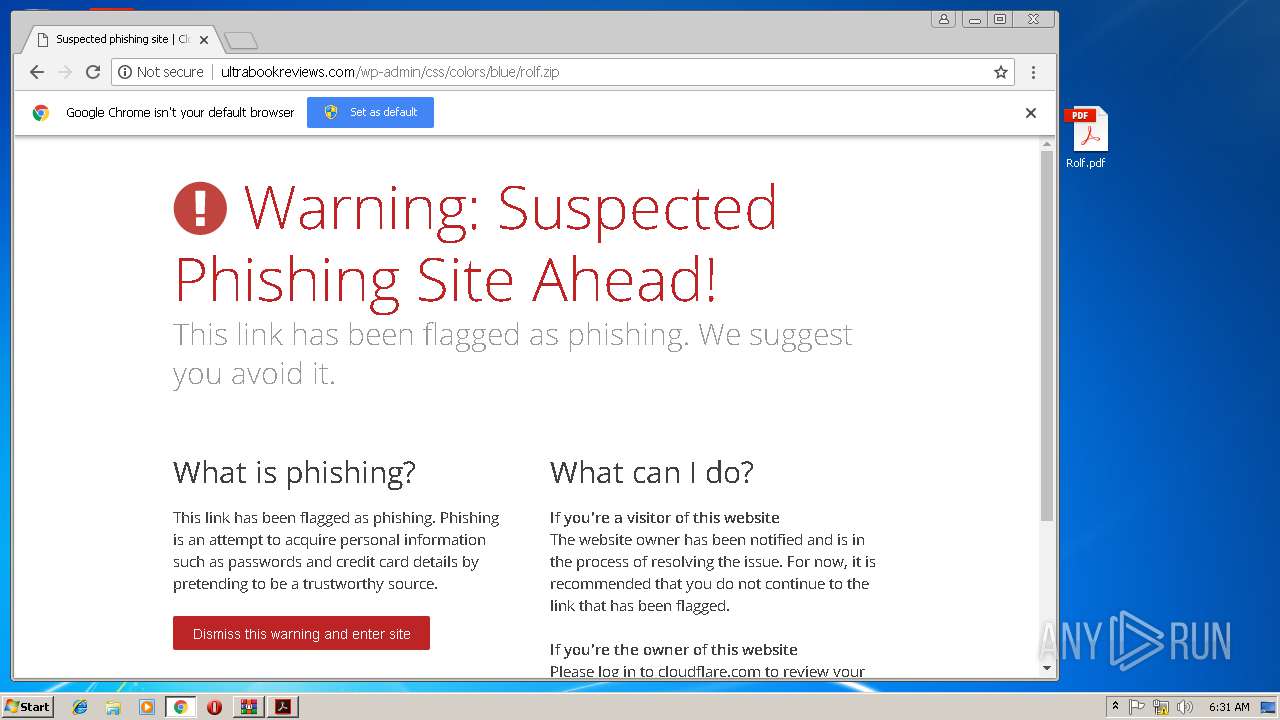
3660 | iexplore.exe | GET | 200 | 104.27.188.104:80 | http://ultrabookreviews.com/cdn-cgi/styles/fonts/opensans-600.eot | US | eot | 18.8 Kb | shared |
3660 | iexplore.exe | GET | 200 | 104.27.188.104:80 | http://ultrabookreviews.com/cdn-cgi/styles/fonts/opensans-700.eot | US | eot | 19.3 Kb | shared |
3660 | iexplore.exe | GET | 200 | 104.27.188.104:80 | http://ultrabookreviews.com/cdn-cgi/styles/fonts/opensans-300i.eot | US | eot | 20.9 Kb | shared |
3660 | iexplore.exe | GET | 200 | 104.27.188.104:80 | http://ultrabookreviews.com/cdn-cgi/styles/fonts/opensans-400i.eot | US | eot | 20.7 Kb | shared |
3660 | iexplore.exe | GET | 200 | 104.27.188.104:80 | http://ultrabookreviews.com/cdn-cgi/images/icon-exclamation.png?1376755637 | US | image | 512 b | shared |
2796 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3664 | AcroRd32.exe | 2.16.186.33:80 | acroipm2.adobe.com | Akamai International B.V. | — | whitelisted |
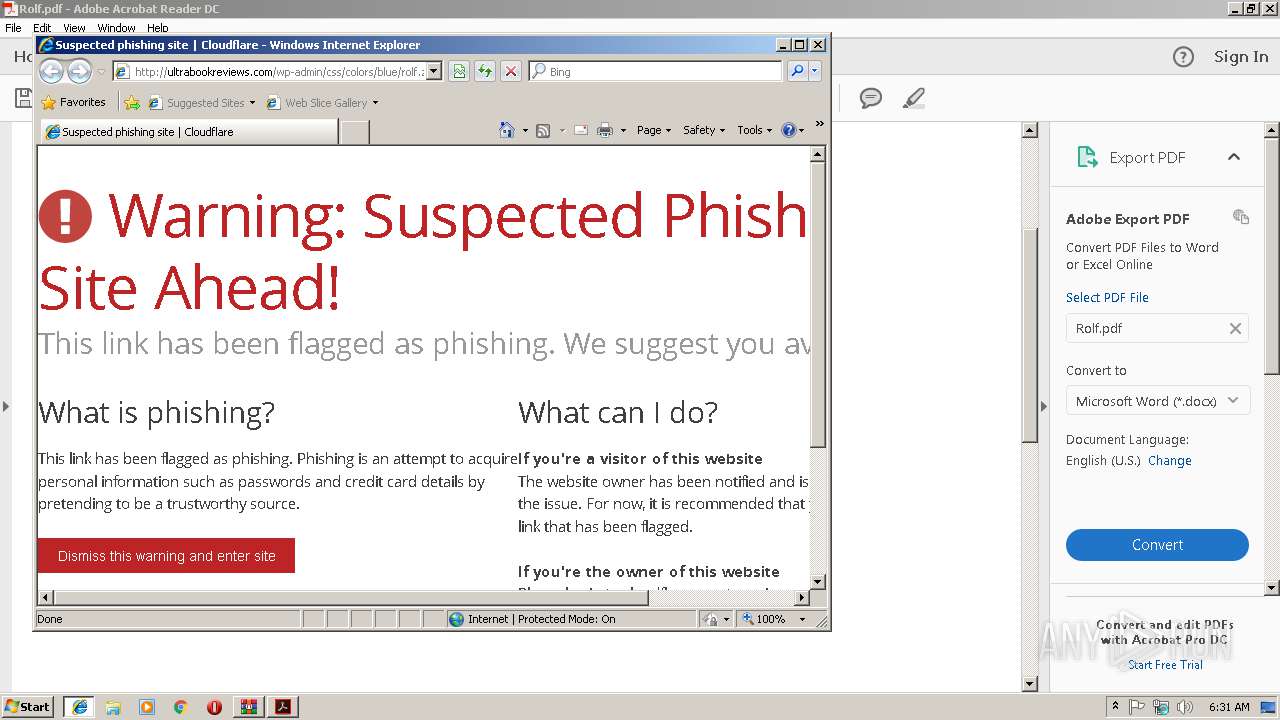
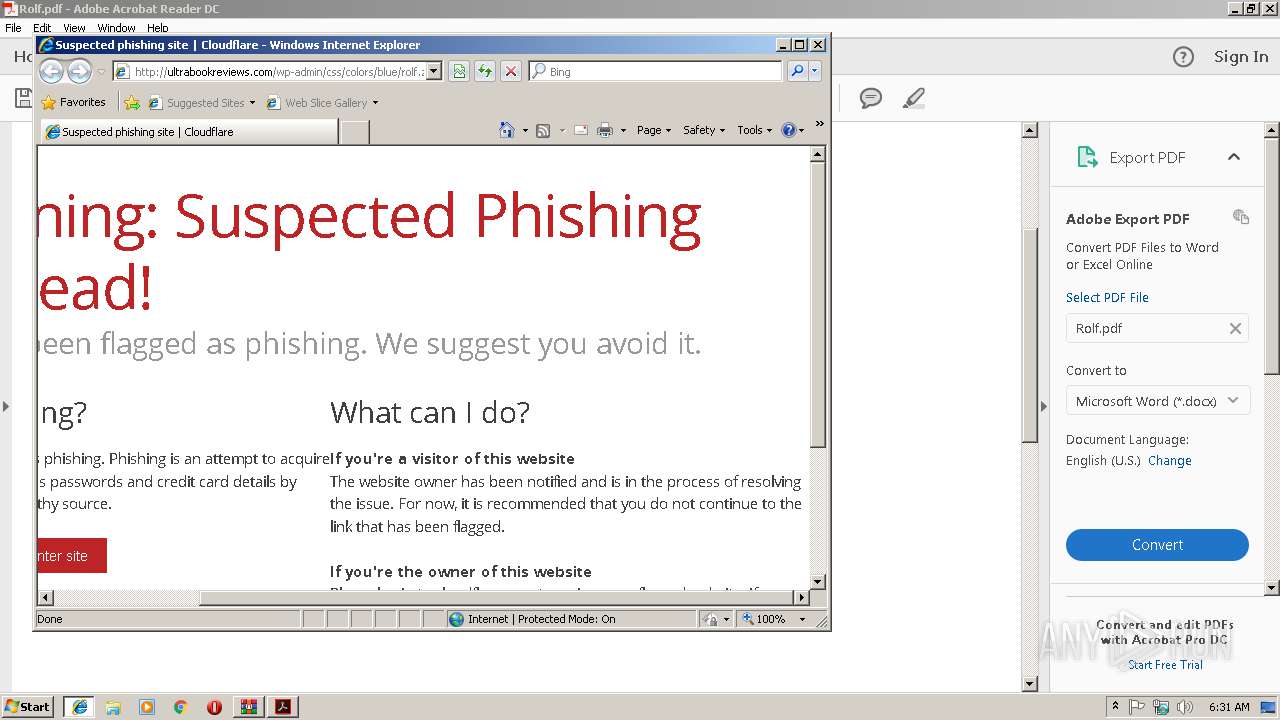
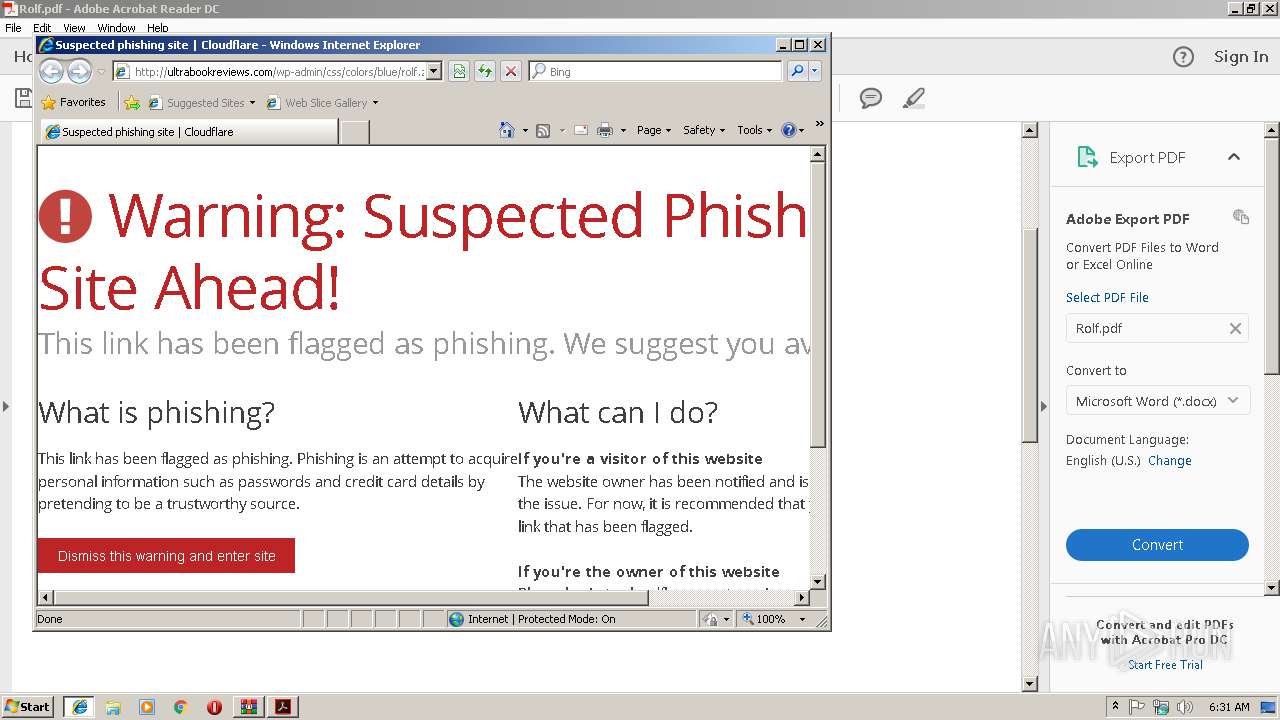
3660 | iexplore.exe | 104.27.188.104:80 | ultrabookreviews.com | Cloudflare Inc | US | shared |
2840 | iexplore.exe | 104.27.188.104:80 | ultrabookreviews.com | Cloudflare Inc | US | shared |
— | — | 2.18.233.74:443 | armmf.adobe.com | Akamai International B.V. | — | whitelisted |
3620 | iexplore.exe | 104.27.188.104:80 | ultrabookreviews.com | Cloudflare Inc | US | shared |
2972 | chrome.exe | 172.217.22.67:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2796 | iexplore.exe | 104.27.188.104:80 | ultrabookreviews.com | Cloudflare Inc | US | shared |
2972 | chrome.exe | 216.58.205.237:443 | accounts.google.com | Google Inc. | US | whitelisted |
2972 | chrome.exe | 172.217.22.46:443 | clients1.google.com | Google Inc. | US | whitelisted |
2972 | chrome.exe | 216.58.208.35:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
acroipm2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
www.bing.com |
| whitelisted |
ultrabookreviews.com |
| unknown |
ardownload2.adobe.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
www.google.de |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |