| URL: | https://apc01.safelinks.protection.outlook.com/?url=https%3A%2F%2Fortus-dot-yamm-track.appspot.com%2F1mZ-tGDOOVaTXdQJZFtuQJHSef4ErlGk3IcxmBVqB9fqJGHEgfwEY4PErZytu6UVUU1m6gmxVi1TA6bEIpCa3aMiuwhx-5_hMV9BXh8zd_-2qHp1BN_0a2B9jsr2-_MHol-IqoriKJgOCVoWPCsWmo-fGgsnMupLCQdXvlxwrWPmF56s7vKXa5c4yLl8HeoJtY4wzFkNVZCbFjMOFAVtpanRMON2orFZyhn4PSWkuoYAsqZmXndCH5BXBuPAhHFnK&data=04%7C01%7C%7C1f4439b044e84f800a0408d9f5d93cc3%7C7007305e26644e6bb9a4c4d5ccfd1524%7C0%7C0%7C637811137518660321%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C3000&sdata=UjnY6HpXkh6iR0ZeTdql2DoR2QMsKDCDzbA3FdU60L0%3D&reserved=0 |
| Full analysis: | https://app.any.run/tasks/cd4c3e82-a2c6-4130-9c2f-3e17d2833896 |
| Verdict: | Malicious activity |
| Analysis date: | February 23, 2022, 00:11:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 081D3EC04308F9686E9B734BD237D661 |
| SHA1: | 0400C7BCD876F1A53B776CDB8931801B34EB775B |
| SHA256: | E91EAB52D7667ECE6AFC1052F4626D1671CF4ACB727AB4BE7A89EC9E974CC03F |
| SSDEEP: | 12:2byqxpteL+UgAqWNsVxVjmeXEA3EHcVgoUBKxKP7RDgJUbwiW:2byqzkKH1WUjREcTyoU8wP7ia5W |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3096)
INFO
Reads the computer name
- iexplore.exe (PID: 2824)
- iexplore.exe (PID: 3096)
Application launched itself
- iexplore.exe (PID: 2824)
Checks Windows Trust Settings
- iexplore.exe (PID: 2824)
- iexplore.exe (PID: 3096)
Checks supported languages
- iexplore.exe (PID: 3096)
- iexplore.exe (PID: 2824)
Changes internet zones settings
- iexplore.exe (PID: 2824)
Reads settings of System Certificates
- iexplore.exe (PID: 3096)
- iexplore.exe (PID: 2824)
Reads internet explorer settings
- iexplore.exe (PID: 3096)
Creates files in the user directory
- iexplore.exe (PID: 3096)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2824 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://apc01.safelinks.protection.outlook.com/?url=https%3A%2F%2Fortus-dot-yamm-track.appspot.com%2F1mZ-tGDOOVaTXdQJZFtuQJHSef4ErlGk3IcxmBVqB9fqJGHEgfwEY4PErZytu6UVUU1m6gmxVi1TA6bEIpCa3aMiuwhx-5_hMV9BXh8zd_-2qHp1BN_0a2B9jsr2-_MHol-IqoriKJgOCVoWPCsWmo-fGgsnMupLCQdXvlxwrWPmF56s7vKXa5c4yLl8HeoJtY4wzFkNVZCbFjMOFAVtpanRMON2orFZyhn4PSWkuoYAsqZmXndCH5BXBuPAhHFnK&data=04%7C01%7C%7C1f4439b044e84f800a0408d9f5d93cc3%7C7007305e26644e6bb9a4c4d5ccfd1524%7C0%7C0%7C637811137518660321%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C3000&sdata=UjnY6HpXkh6iR0ZeTdql2DoR2QMsKDCDzbA3FdU60L0%3D&reserved=0" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3096 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2824 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
23 508
Read events
23 345
Write events
163
Delete events
0
Modification events
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30943305 | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30943305 | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
29
Text files
114
Unknown types
38
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2824 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 2824 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 2824 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2824 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:— | SHA256:— | |||
| 2824 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:— | SHA256:— | |||
| 3096 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:— | SHA256:— | |||
| 3096 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\2F23D0F5E4D72862517E1CB26A329742_F6FACC49395CFA949BCE851E73323C49 | der | |
MD5:— | SHA256:— | |||
| 3096 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:— | SHA256:— | |||
| 3096 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | der | |
MD5:— | SHA256:— | |||
| 3096 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\265C0DEB29181DD1891051371C5F863A_20543FC7EB7901B83C465108C81E9629 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
103
DNS requests
39
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3096 | iexplore.exe | GET | — | 92.123.195.57:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?5f7cf339ac077724 | unknown | — | — | whitelisted |
3096 | iexplore.exe | GET | — | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?d4348fe0c13b7613 | US | — | — | whitelisted |
3096 | iexplore.exe | GET | — | 92.123.195.57:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?1b6fa1f8c5cb0ea6 | unknown | — | — | whitelisted |
2824 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2824 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
3096 | iexplore.exe | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
3096 | iexplore.exe | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
3096 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
3096 | iexplore.exe | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDjl5xPKHVBuQoAAAABM%2Fjo | US | der | 472 b | whitelisted |
3096 | iexplore.exe | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCYyccBU%2BO5JwoAAAABM%2FlK | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3096 | iexplore.exe | 104.47.124.28:443 | apc01.safelinks.protection.outlook.com | Microsoft Corporation | US | whitelisted |
2824 | iexplore.exe | 92.123.195.41:80 | ctldl.windowsupdate.com | Akamai International B.V. | — | whitelisted |
2824 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3096 | iexplore.exe | 104.47.110.28:443 | apc01.safelinks.protection.outlook.com | Microsoft Corporation | US | suspicious |
2824 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2824 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2824 | iexplore.exe | 92.123.195.57:80 | ctldl.windowsupdate.com | Akamai International B.V. | — | whitelisted |
3096 | iexplore.exe | 92.123.195.57:80 | ctldl.windowsupdate.com | Akamai International B.V. | — | whitelisted |
3096 | iexplore.exe | 142.250.186.116:443 | ortus-dot-yamm-track.appspot.com | Google Inc. | US | suspicious |
3096 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
apc01.safelinks.protection.outlook.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
ortus-dot-yamm-track.appspot.com |
| malicious |
ocsp.pki.goog |
| whitelisted |
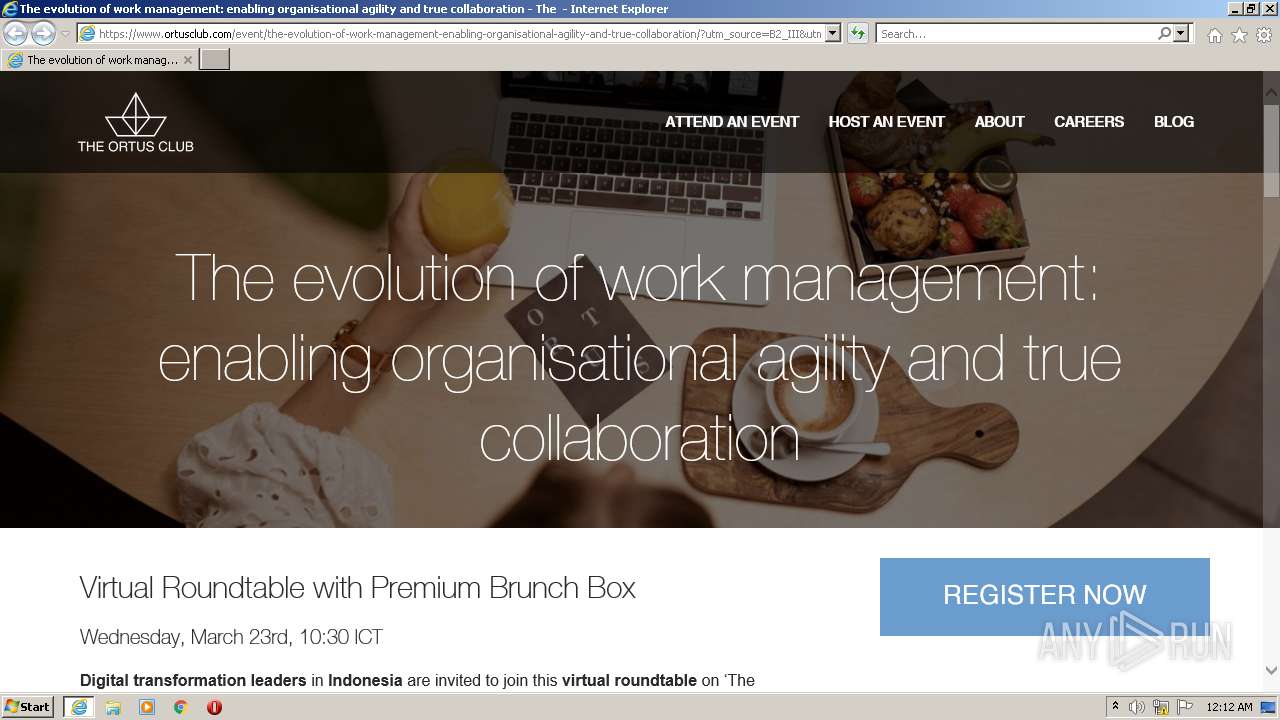
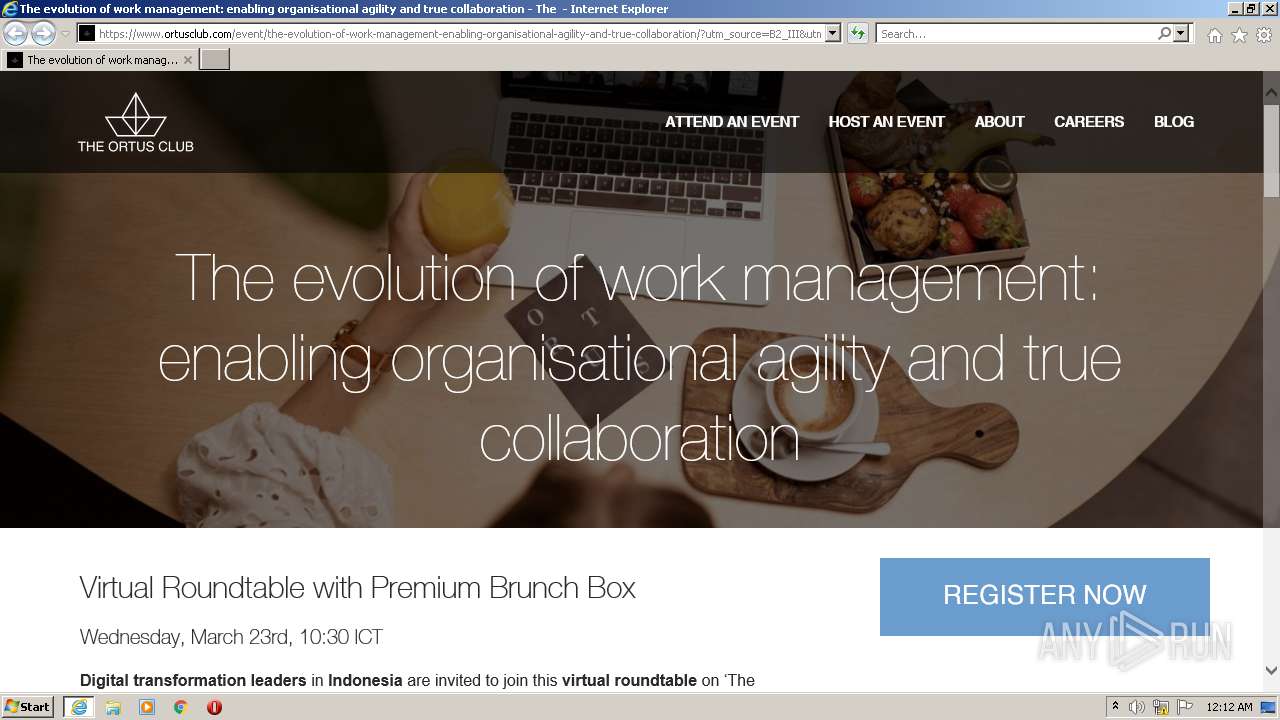
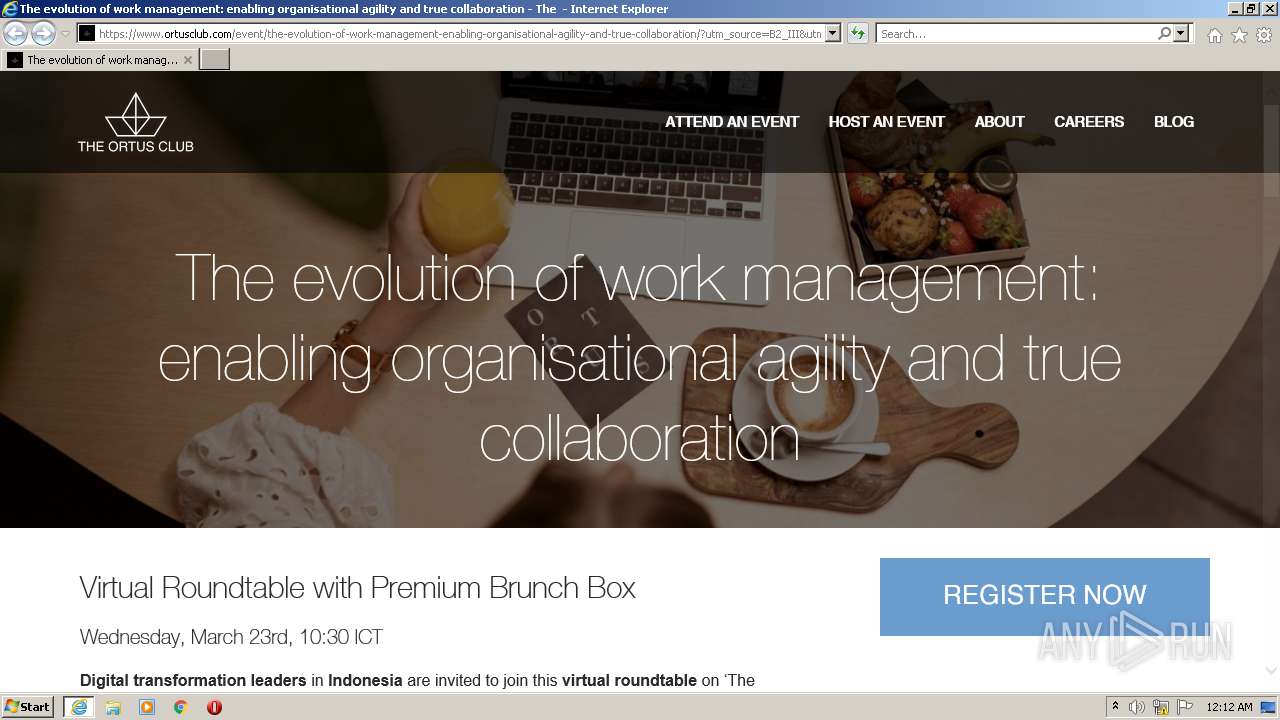
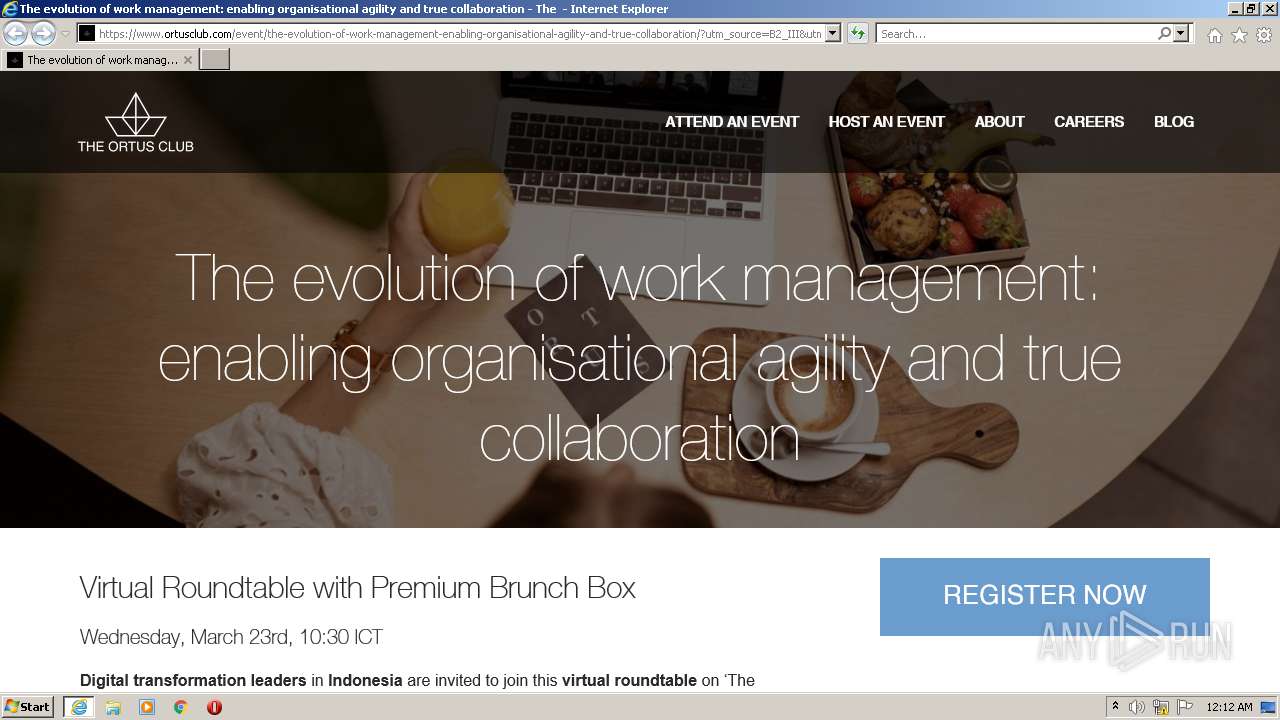
www.ortusclub.com |
| malicious |