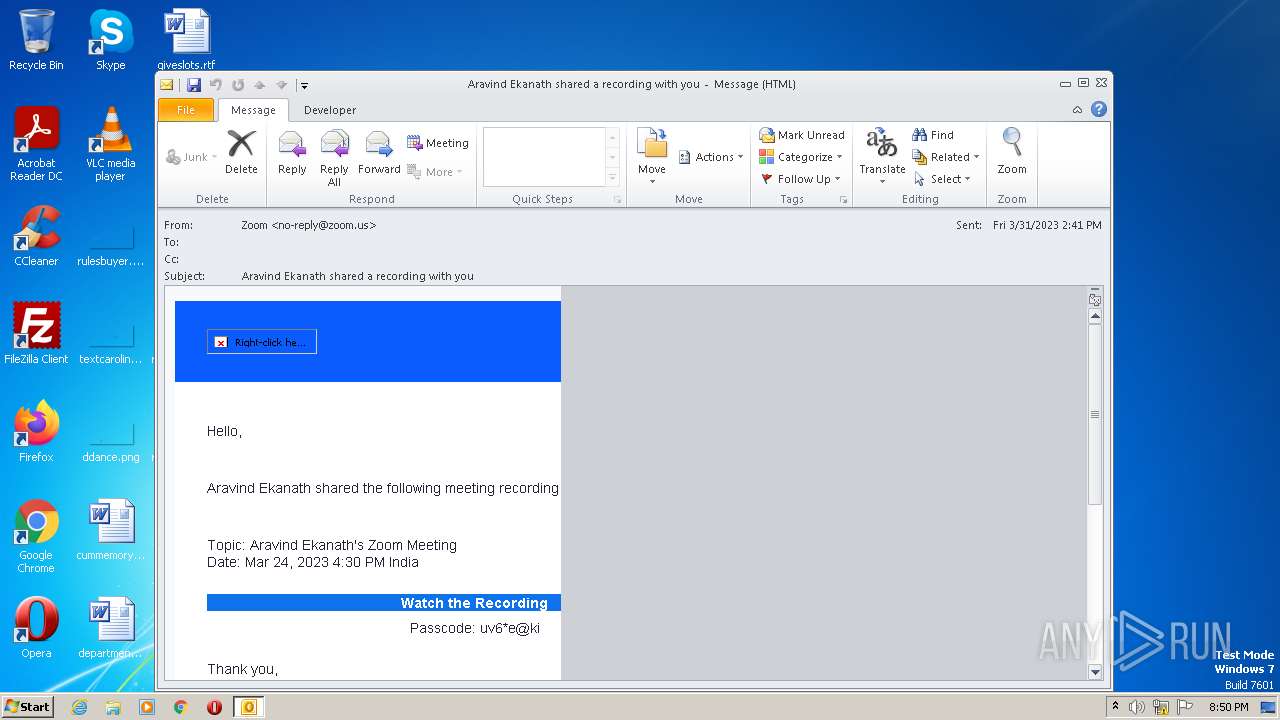
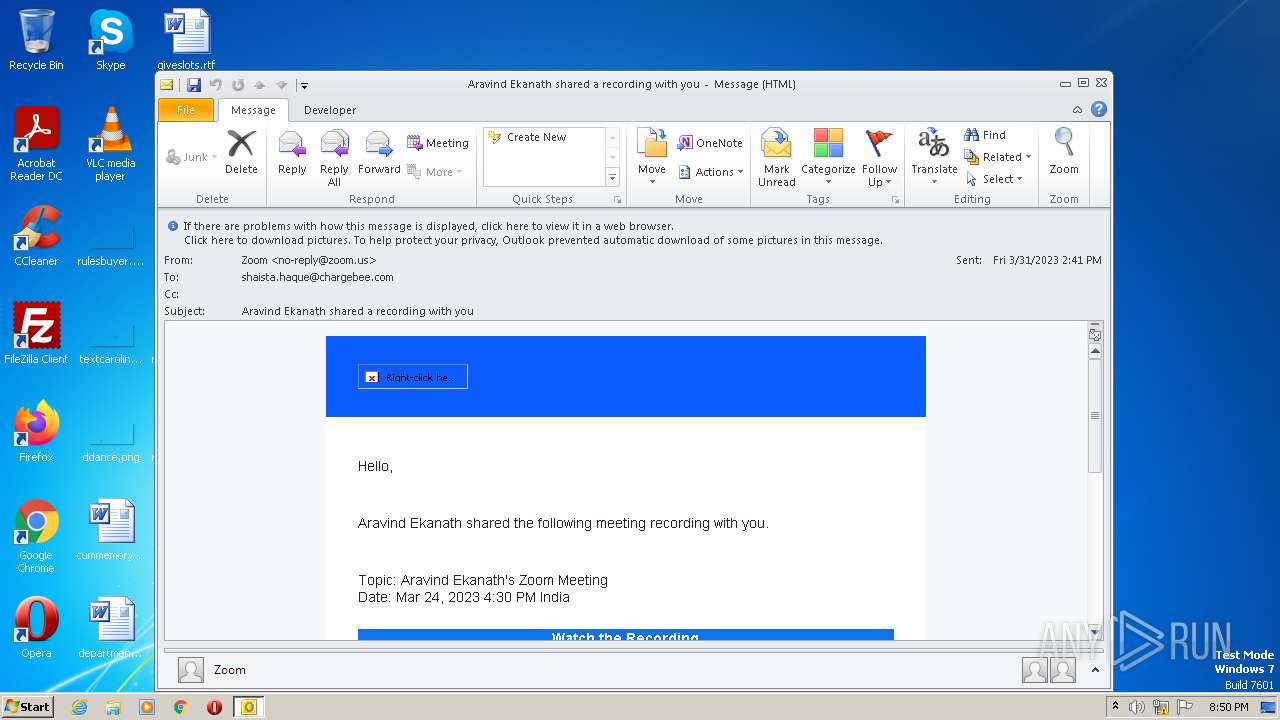
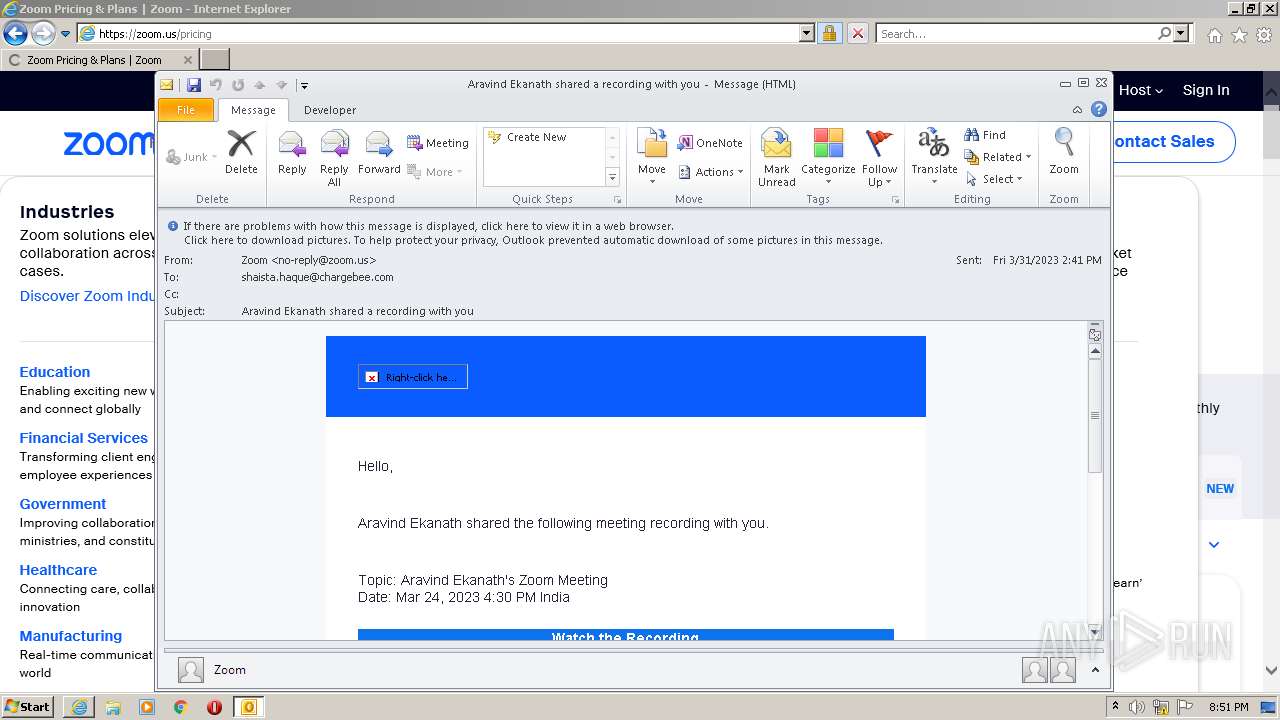
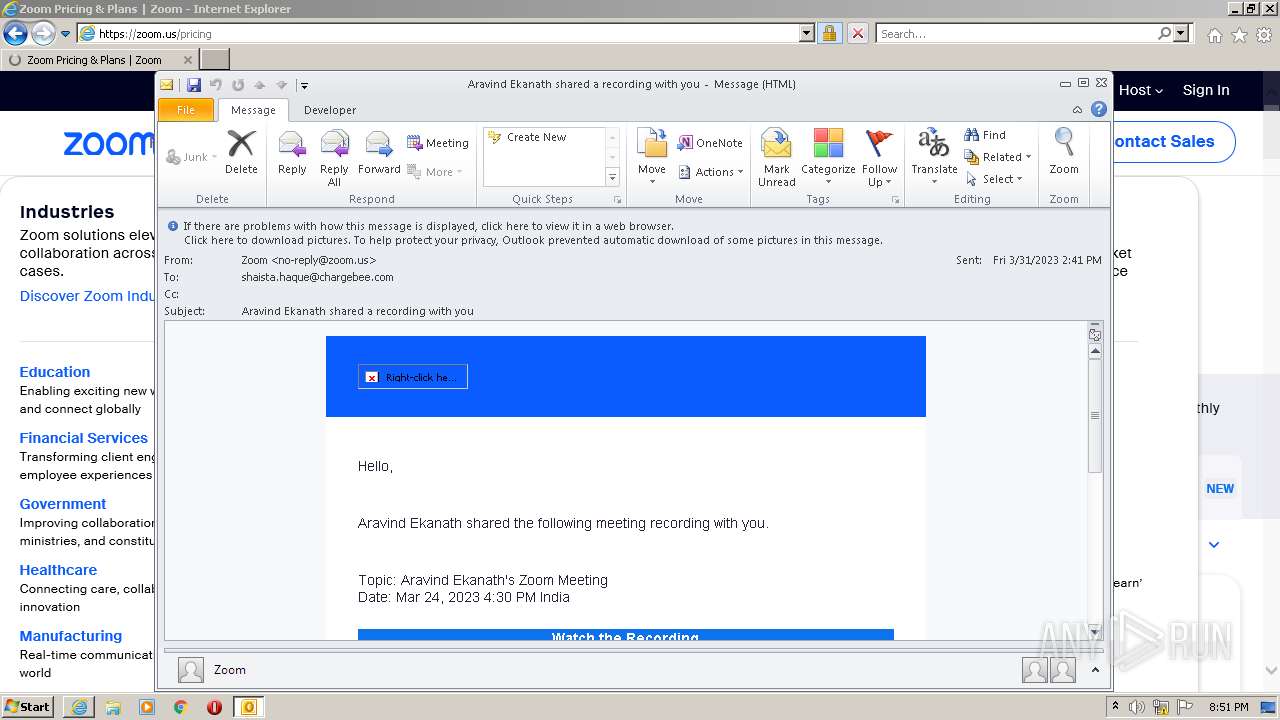
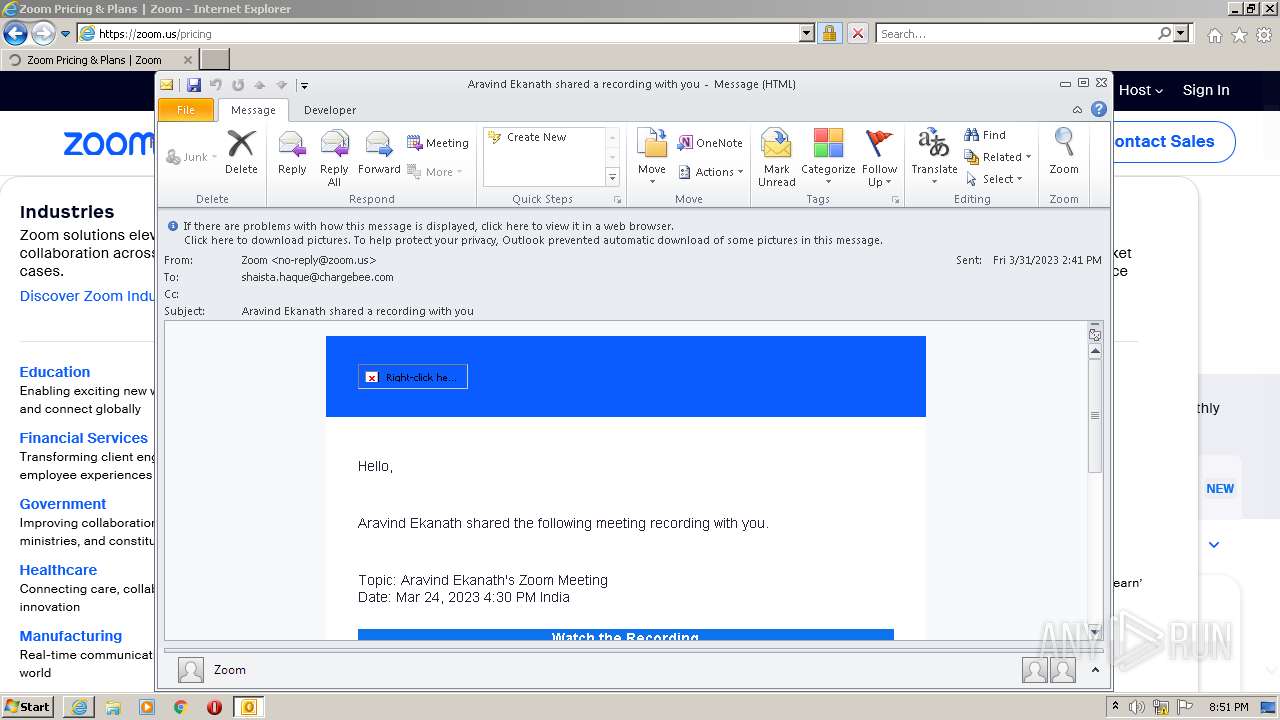
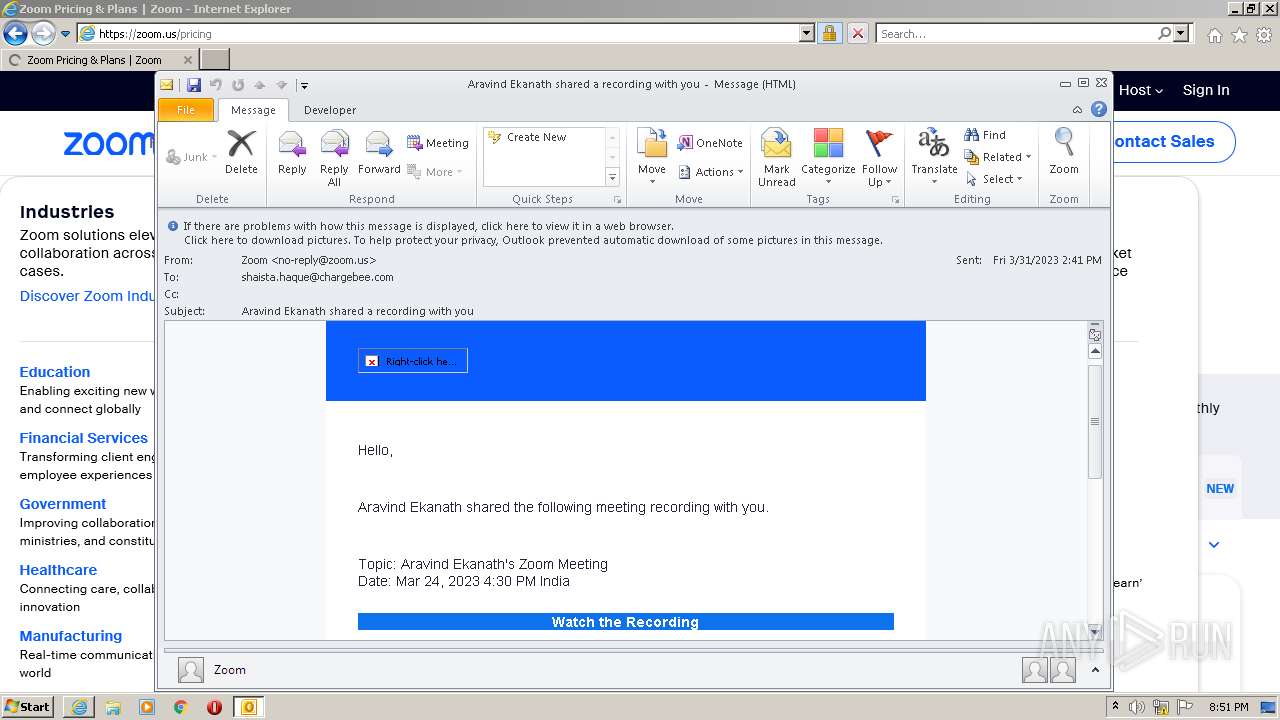
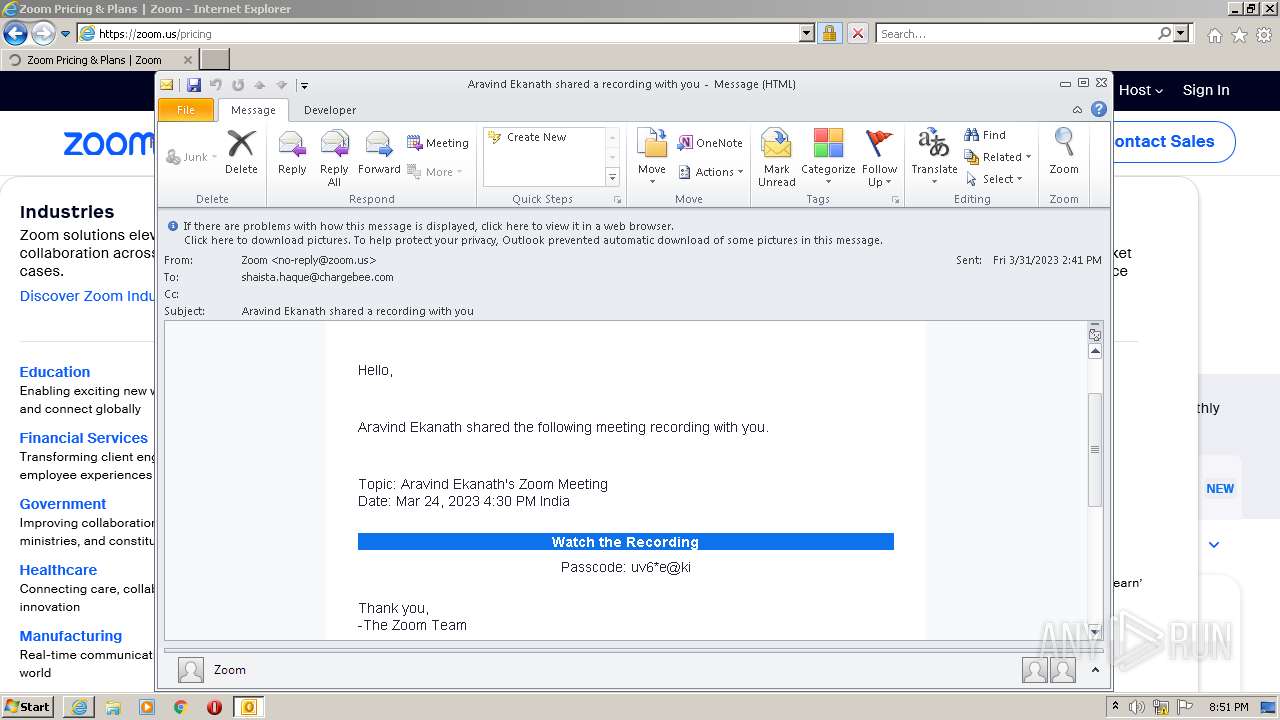
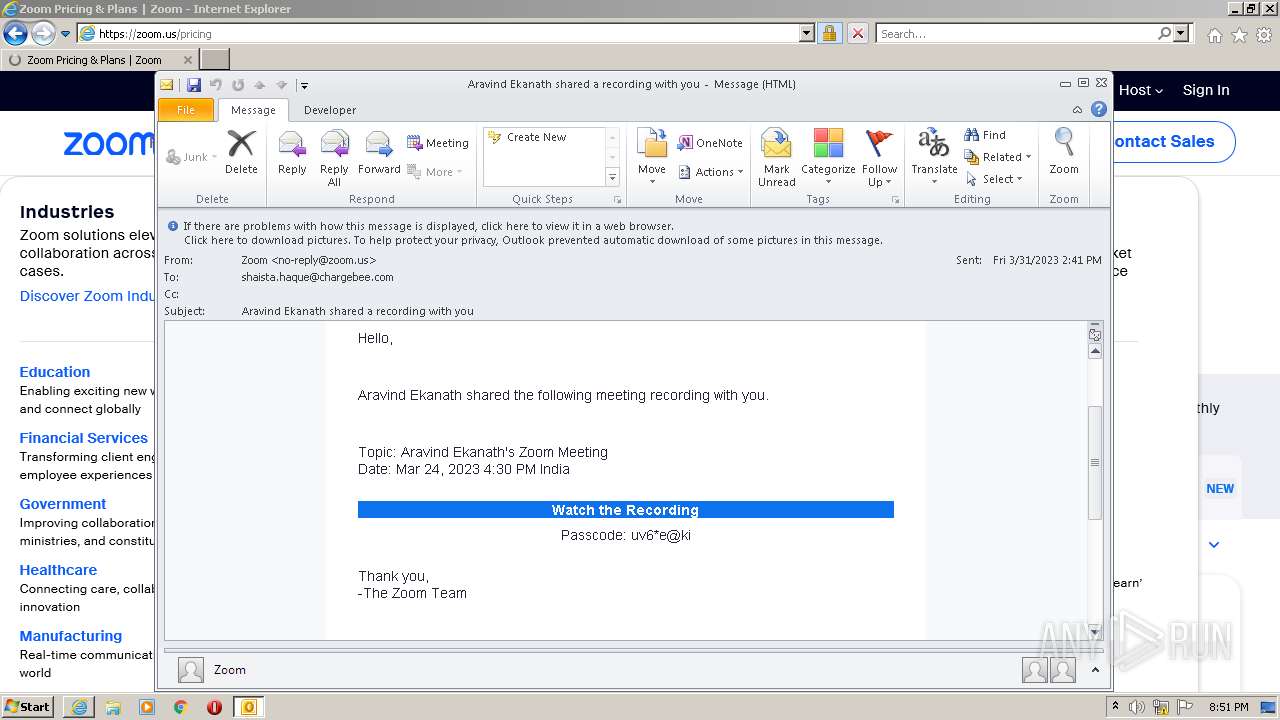
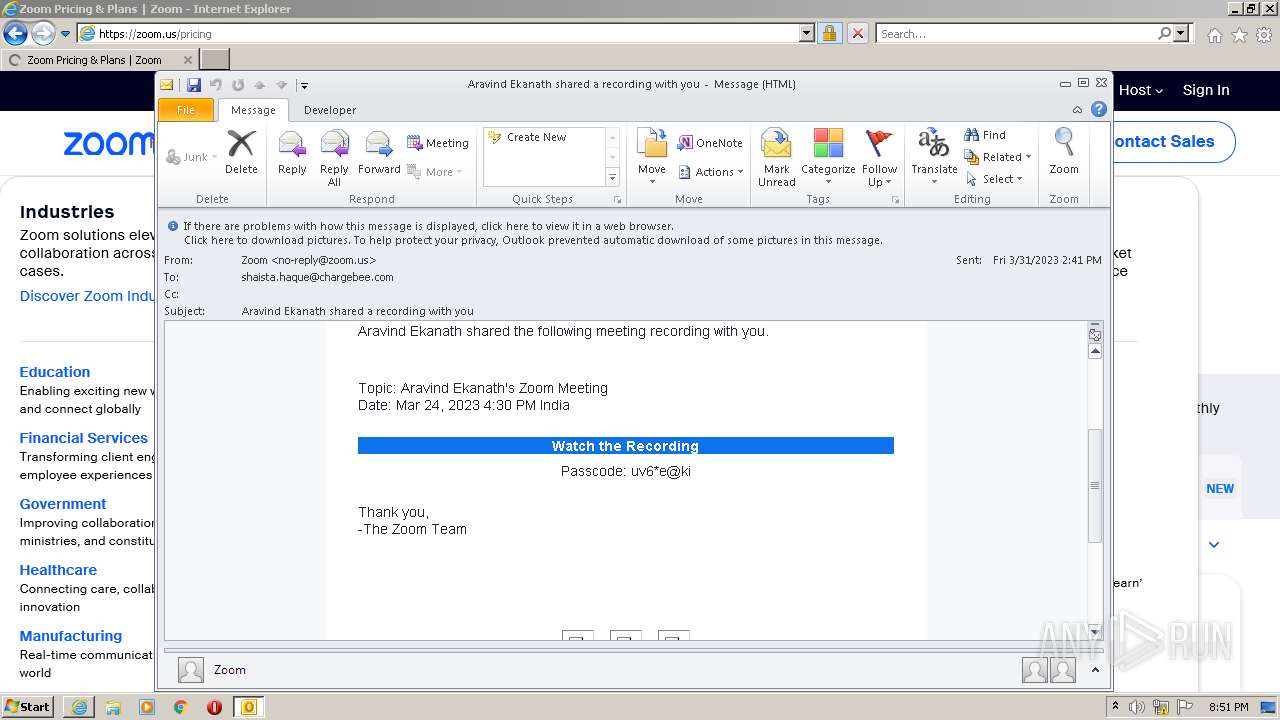
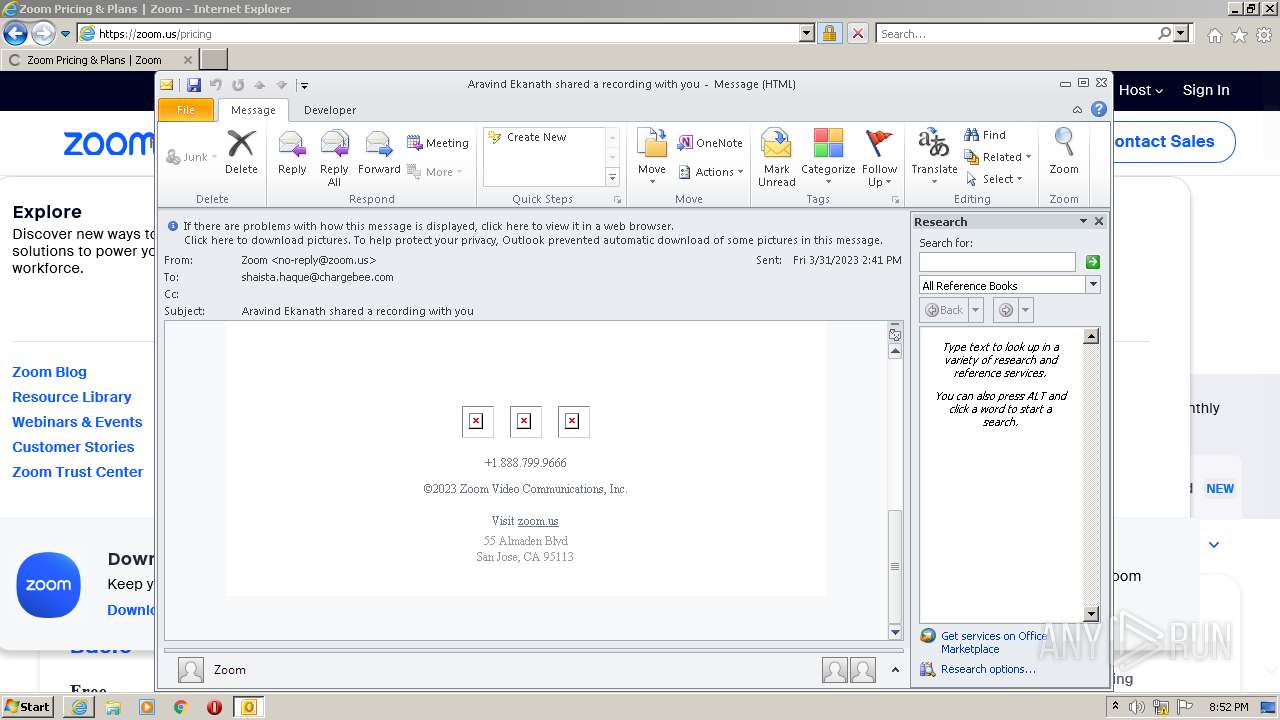
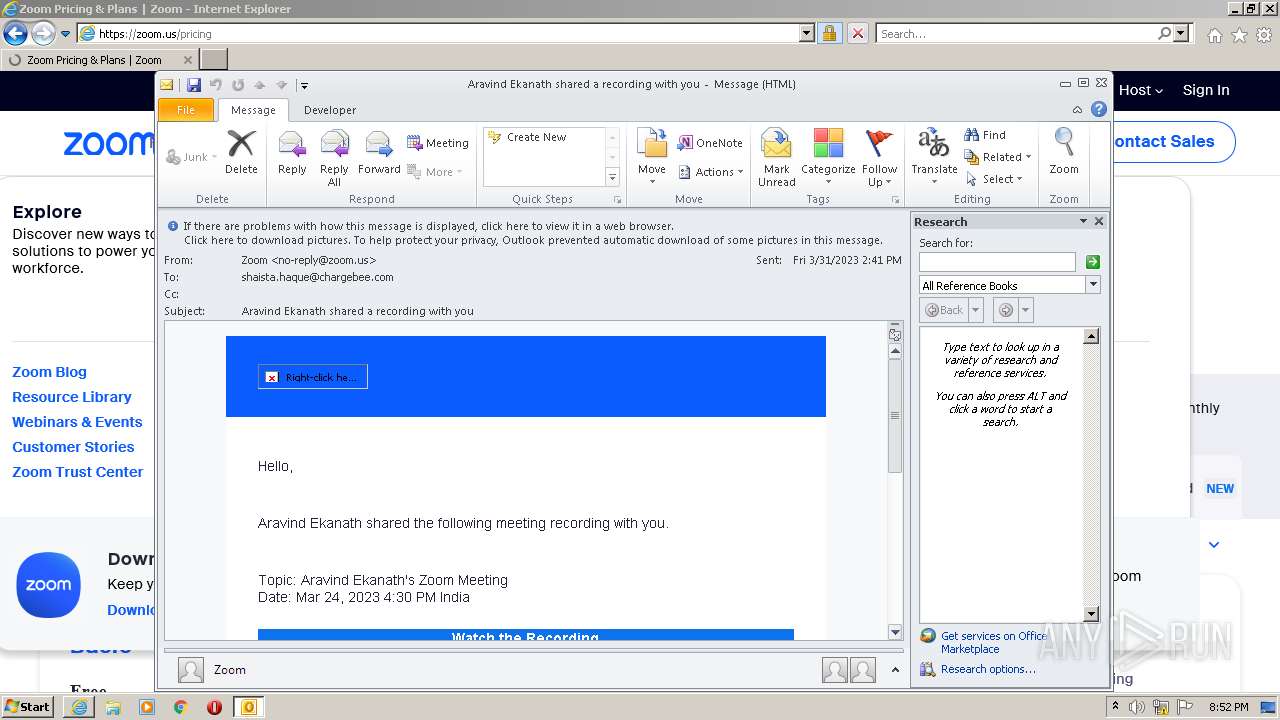
| File name: | Aravind Ekanath shared a recording with you.eml |
| Full analysis: | https://app.any.run/tasks/ae67e594-cad9-436d-8541-fd1b2f9e4998 |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2023, 19:50:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | SMTP mail, ASCII text, with CRLF line terminators |
| MD5: | 8B9C21D1371F6852B41C4251F45889C3 |
| SHA1: | 8DF73735BBE38874A146814CD11CA605E1DE57DF |
| SHA256: | E8FAFED4DBE6AB6CCDBD7D973C606358B3C1D1DB70A3803466E88A18B1CDE1ED |
| SSDEEP: | 384:hjmLxTn5aBLofyGQfN+CWxo/8OfzGEy4+pba:hCLx1ado6qsfqJa |
MALICIOUS
No malicious indicators.SUSPICIOUS
Searches for installed software
- OUTLOOK.EXE (PID: 1048)
Reads the Internet Settings
- OUTLOOK.EXE (PID: 1048)
Reads settings of System Certificates
- OUTLOOK.EXE (PID: 1048)
Checks Windows Trust Settings
- OUTLOOK.EXE (PID: 1048)
Reads security settings of Internet Explorer
- OUTLOOK.EXE (PID: 1048)
INFO
Checks supported languages
- OUTLOOK.EXE (PID: 1048)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 1048)
The process checks LSA protection
- OUTLOOK.EXE (PID: 1048)
Reads the computer name
- OUTLOOK.EXE (PID: 1048)
Reads the machine GUID from the registry
- OUTLOOK.EXE (PID: 1048)
Create files in a temporary directory
- OUTLOOK.EXE (PID: 1048)
- iexplore.exe (PID: 2996)
- iexplore.exe (PID: 3000)
Checks proxy server information
- OUTLOOK.EXE (PID: 1048)
Process checks computer location settings
- OUTLOOK.EXE (PID: 1048)
Application launched itself
- iexplore.exe (PID: 2996)
Creates files or folders in the user directory
- OUTLOOK.EXE (PID: 1048)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 7) (100) |
|---|
Total processes
44
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1048 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\Aravind Ekanath shared a recording with you.eml" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
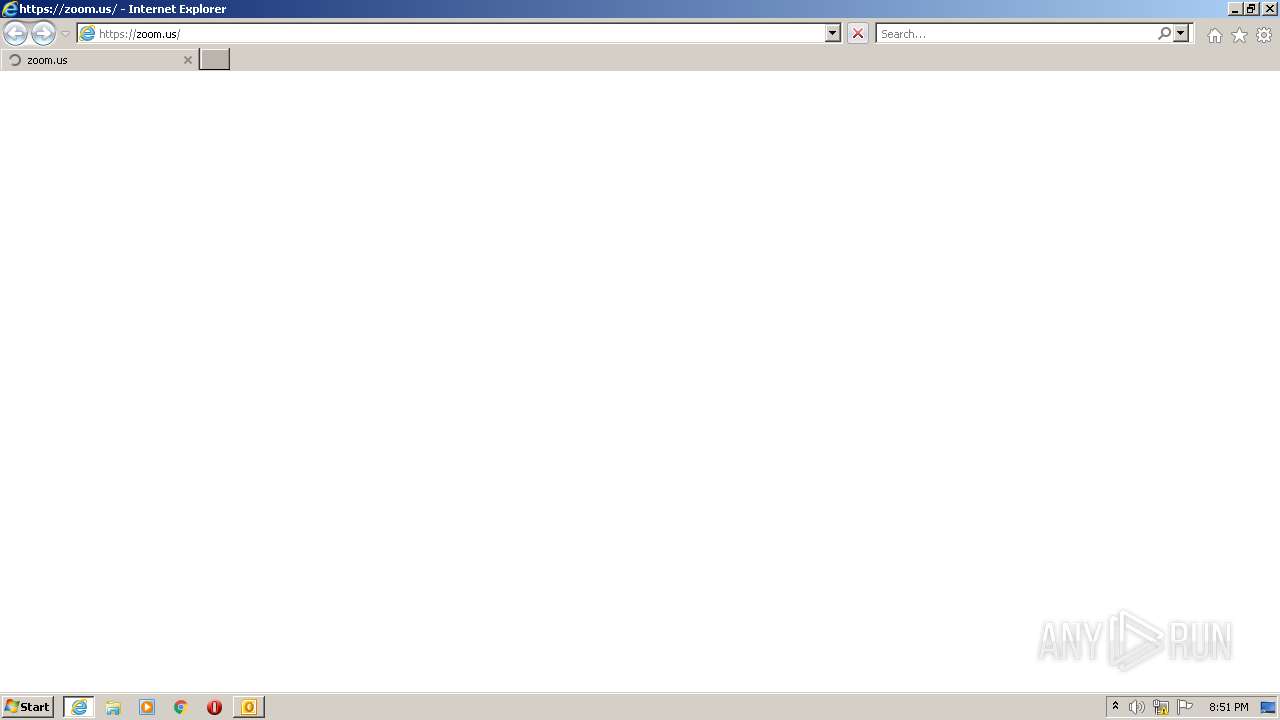
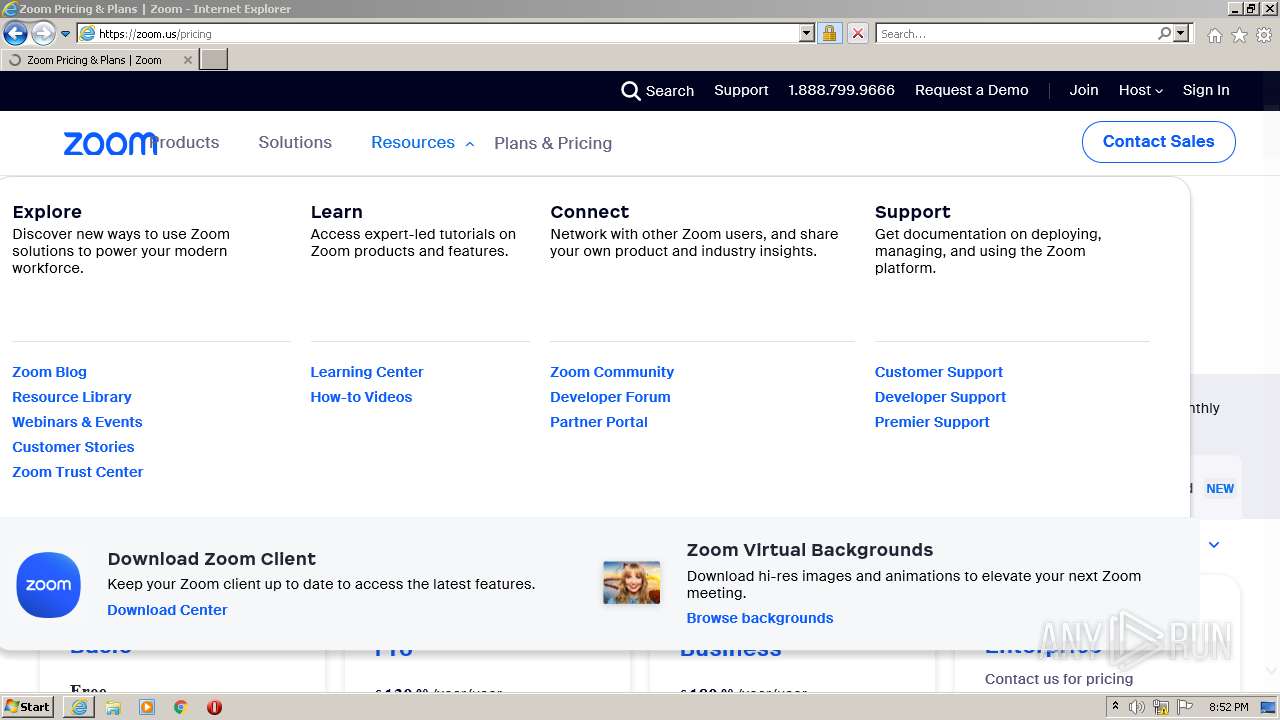
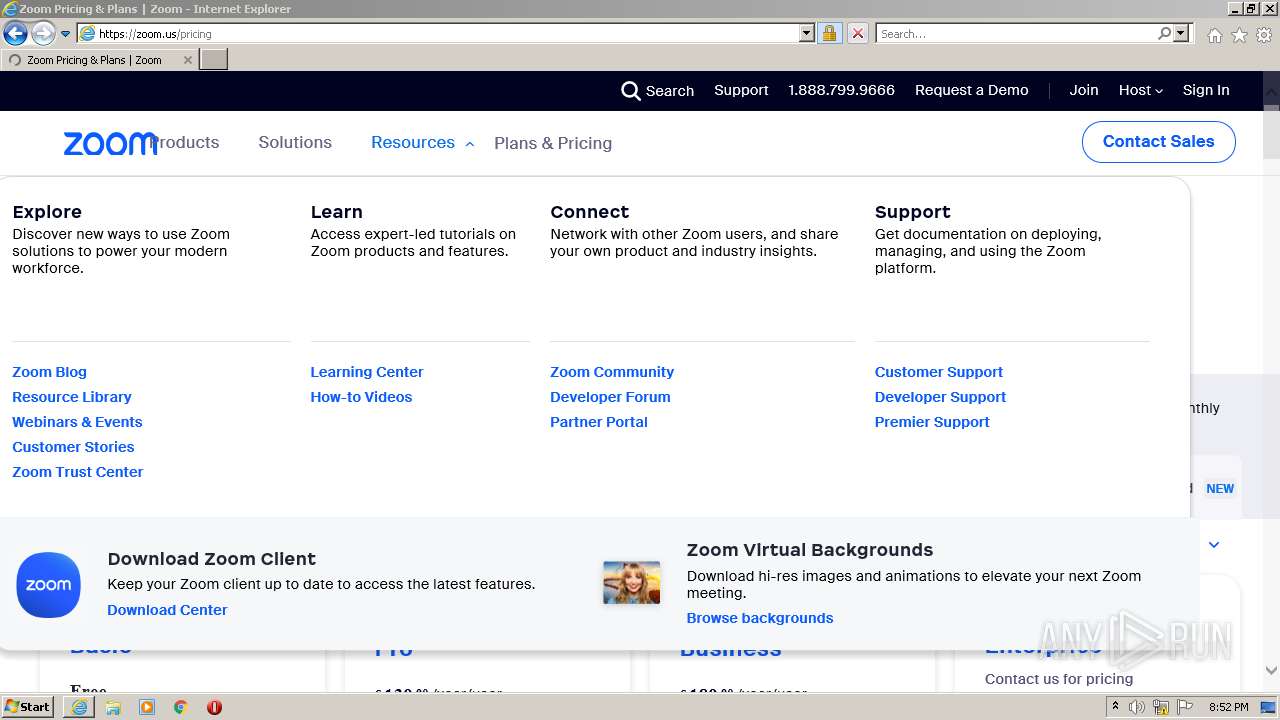
| 2996 | "C:\Program Files\Internet Explorer\iexplore.exe" https://zoom.us/ | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3000 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2996 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3164 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2996 CREDAT:2430230 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
110 510
Read events
90 188
Write events
20 276
Delete events
46
Modification events
| (PID) Process: | (1048) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (1048) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (1048) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (1048) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (1048) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (1048) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (1048) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (1048) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (1048) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (1048) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
0
Suspicious files
94
Text files
348
Unknown types
80
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1048 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRF657.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1048 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 1048 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 3000 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:— | SHA256:— | |||
| 3000 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | der | |
MD5:— | SHA256:— | |||
| 3000 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\327BDKJ4.txt | text | |
MD5:— | SHA256:— | |||
| 3000 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\LDVYCKUK.txt | text | |
MD5:— | SHA256:— | |||
| 3000 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\1UKHRFM3.txt | text | |
MD5:— | SHA256:— | |||
| 3000 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3000 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\9CHE5VV9.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
86
DNS requests
36
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3000 | iexplore.exe | GET | — | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | — | — | whitelisted |
3000 | iexplore.exe | GET | — | 108.138.2.173:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | — | — | whitelisted |
3000 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAhflMAthXvozBT%2FU%2B2iPio%3D | US | der | 471 b | whitelisted |
3000 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | US | der | 1.47 Kb | whitelisted |
3000 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSnxLiz3Fu1WB6n1%2FE6xWn1b0jXiQQUdIWAwGbH3zfez70pN6oDHb7tzRcCEAbCsehAv%2FkAxBfkV5KvfLI%3D | US | der | 471 b | whitelisted |
2996 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
3000 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?f6c84cee3fddff75 | US | compressed | 61.1 Kb | whitelisted |
3000 | iexplore.exe | GET | 200 | 23.37.41.57:80 | http://x1.c.lencr.org/ | NL | der | 717 b | whitelisted |
3000 | iexplore.exe | GET | 200 | 52.84.193.138:80 | http://crl.rootg2.amazontrust.com/rootg2.crl | US | der | 660 b | whitelisted |
3000 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3000 | iexplore.exe | 18.66.130.242:443 | st3.zoom.us | AMAZON-02 | US | unknown |
3000 | iexplore.exe | 52.84.151.14:443 | file-paa.zoom.us | AMAZON-02 | US | unknown |
3000 | iexplore.exe | 18.66.147.113:443 | static.ada.support | AMAZON-02 | US | suspicious |
3000 | iexplore.exe | 34.98.108.207:443 | cdn.solvvy.com | GOOGLE | US | unknown |
3000 | iexplore.exe | 108.138.2.173:80 | o.ss2.us | AMAZON-02 | US | unknown |
3000 | iexplore.exe | 44.199.16.116:443 | rewards.zoom.us | AMAZON-AES | US | unknown |
3000 | iexplore.exe | 143.204.14.3:80 | ocsp.rootg2.amazontrust.com | AMAZON-02 | US | whitelisted |
3000 | iexplore.exe | 13.32.216.250:443 | explore.zoom.us | AMAZON-02 | US | unknown |
3000 | iexplore.exe | 104.19.187.97:443 | cdn.cookielaw.org | CLOUDFLARENET | — | whitelisted |
3000 | iexplore.exe | 23.37.41.57:80 | x1.c.lencr.org | AKAMAI-AS | DE | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
zoom.us |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
st3.zoom.us |
| whitelisted |
explore.zoom.us |
| whitelisted |
st1.zoom.us |
| whitelisted |
st2.zoom.us |
| whitelisted |
cdn.cookielaw.org |
| whitelisted |
file-paa.zoom.us |
| suspicious |