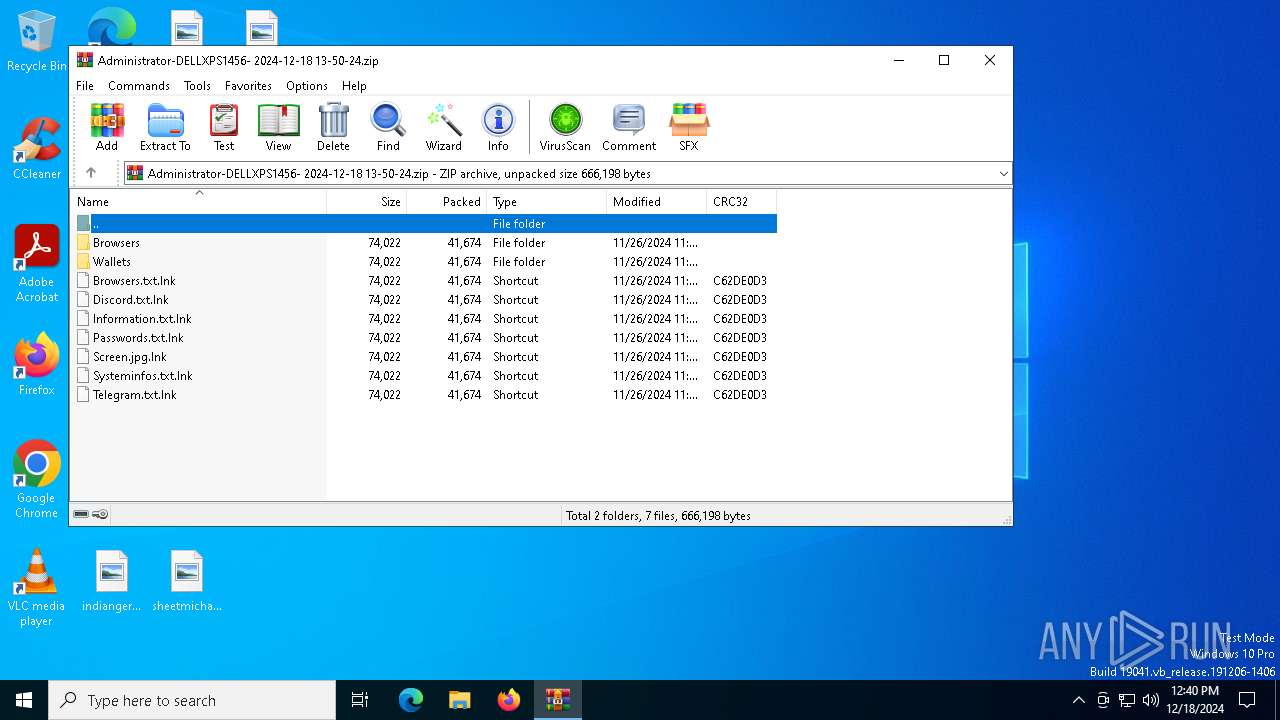
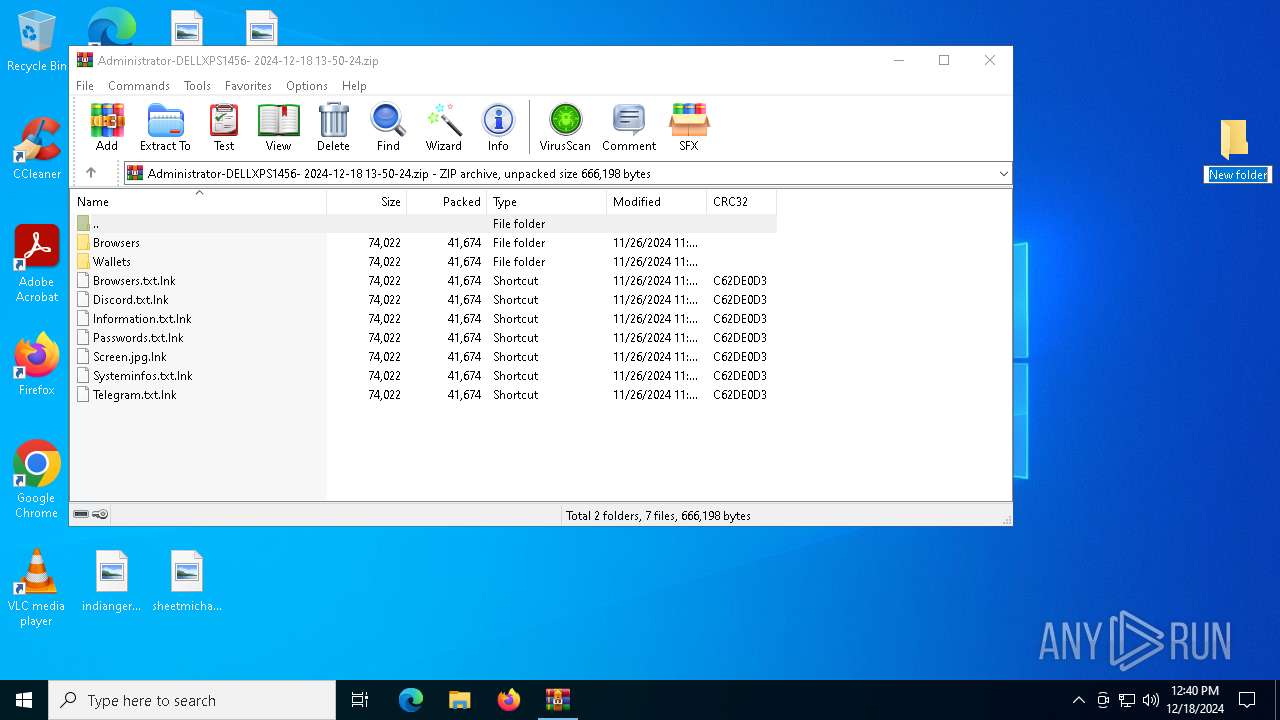
| File name: | Administrator-DELLXPS1456- 2024-12-18 13-50-24.zip |
| Full analysis: | https://app.any.run/tasks/8495e3de-4540-420f-94c8-09ae26ffff08 |
| Verdict: | Malicious activity |
| Analysis date: | December 18, 2024, 12:40:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | EC70B1CD3D3BCA7303B23E344AAFB78E |
| SHA1: | 8D4268DDEA54F15AF5415C39FE7EA0DAB8E2A228 |
| SHA256: | E8EDB03673135993012B78BCA85FFB75829F7FB432B61C49242C84E7F41F638A |
| SSDEEP: | 12288:554RCI854RCIU54RCIe54RCI454RCIg54RCIi54RCIK54RCIR54RCIV:5540I8540IU540Ie540I4540Ig540IiH |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6304)
Run PowerShell with an invisible window
- powershell.exe (PID: 6820)
- powershell.exe (PID: 5300)
Uses Task Scheduler to run other applications
- tmp256575502.exe (PID: 6712)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6232)
- cmd.exe (PID: 6816)
Executable content was dropped or overwritten
- powershell.exe (PID: 6820)
- powershell.exe (PID: 5300)
Lists all scheduled tasks
- schtasks.exe (PID: 4984)
- schtasks.exe (PID: 6004)
- schtasks.exe (PID: 7072)
- schtasks.exe (PID: 6720)
Connects to the server without a host name
- tmp256575502.exe (PID: 6712)
- tmp97186975.exe (PID: 6772)
Reads the date of Windows installation
- tmp256575502.exe (PID: 6712)
Reads security settings of Internet Explorer
- tmp97186975.exe (PID: 6772)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 6304)
- tmp256575502.exe (PID: 6712)
Manual execution by a user
- cmd.exe (PID: 6232)
- mspaint.exe (PID: 5604)
- cmd.exe (PID: 6816)
The executable file from the user directory is run by the Powershell process
- tmp256575502.exe (PID: 6712)
- tmp97186975.exe (PID: 6772)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6820)
- powershell.exe (PID: 5300)
Checks supported languages
- tmp256575502.exe (PID: 6712)
- identity_helper.exe (PID: 6804)
- tmp97186975.exe (PID: 6772)
- identity_helper.exe (PID: 4244)
Reads the machine GUID from the registry
- tmp256575502.exe (PID: 6712)
- tmp97186975.exe (PID: 6772)
Disables trace logs
- tmp256575502.exe (PID: 6712)
- tmp97186975.exe (PID: 6772)
Reads Microsoft Office registry keys
- tmp256575502.exe (PID: 6712)
Process checks computer location settings
- tmp256575502.exe (PID: 6712)
Reads CPU info
- tmp97186975.exe (PID: 6772)
- tmp256575502.exe (PID: 6712)
Reads Environment values
- tmp97186975.exe (PID: 6772)
- identity_helper.exe (PID: 4244)
Create files in a temporary directory
- tmp256575502.exe (PID: 6712)
- tmp97186975.exe (PID: 6772)
Checks proxy server information
- tmp256575502.exe (PID: 6712)
- tmp97186975.exe (PID: 6772)
Application launched itself
- msedge.exe (PID: 6548)
- msedge.exe (PID: 5240)
Reads the computer name
- identity_helper.exe (PID: 4244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:11:26 12:20:54 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Browsers/ |
Total processes
197
Monitored processes
67
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 420 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5188 --field-trial-handle=2472,i,16921214151388469978,12280372649986867823,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 648 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5984 --field-trial-handle=2012,i,10466132883116656062,1117037340498361166,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1076 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5068 --field-trial-handle=2472,i,16921214151388469978,12280372649986867823,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1140 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1140 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1296 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=136 --field-trial-handle=2472,i,16921214151388469978,12280372649986867823,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1460 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=23 --mojo-platform-channel-handle=4052 --field-trial-handle=2012,i,10466132883116656062,1117037340498361166,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1488 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2468 --field-trial-handle=2472,i,16921214151388469978,12280372649986867823,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1704 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=4008 --field-trial-handle=2012,i,10466132883116656062,1117037340498361166,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1740 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4612 --field-trial-handle=2012,i,10466132883116656062,1117037340498361166,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
21 944
Read events
21 868
Write events
76
Delete events
0
Modification events
| (PID) Process: | (6304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Administrator-DELLXPS1456- 2024-12-18 13-50-24.zip | |||
| (PID) Process: | (6304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | crc |
Value: 70 | |||
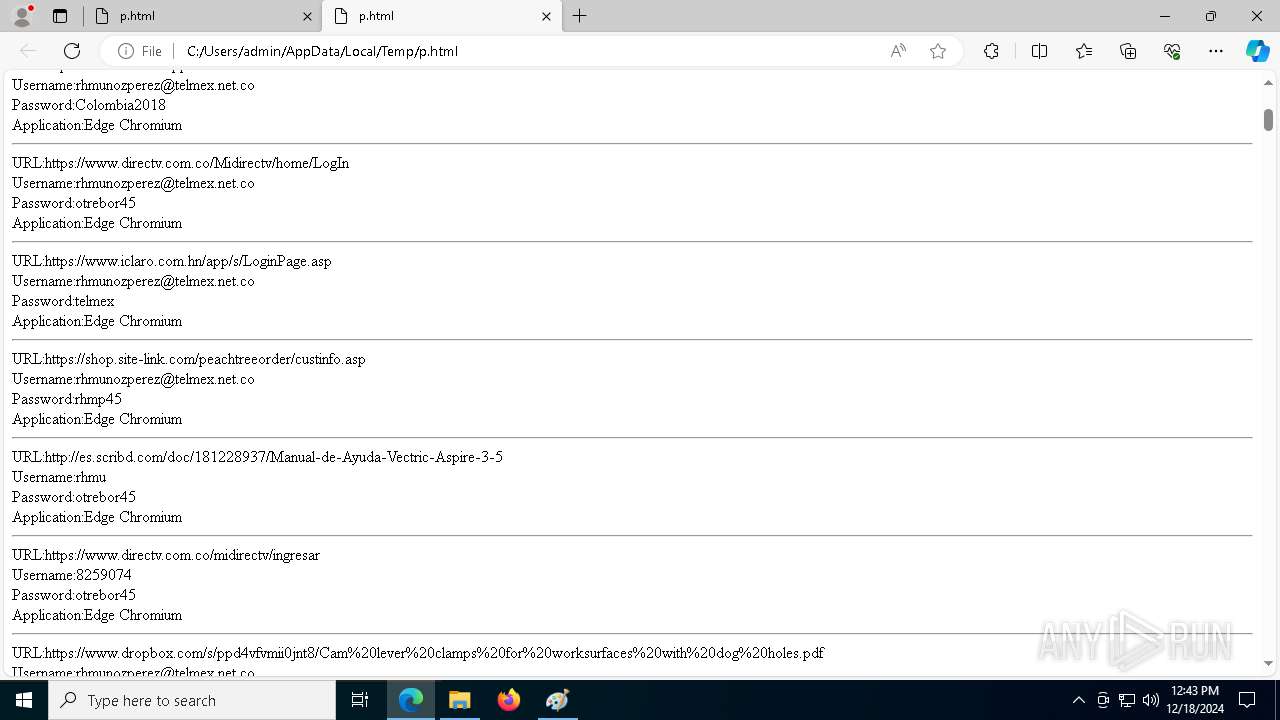
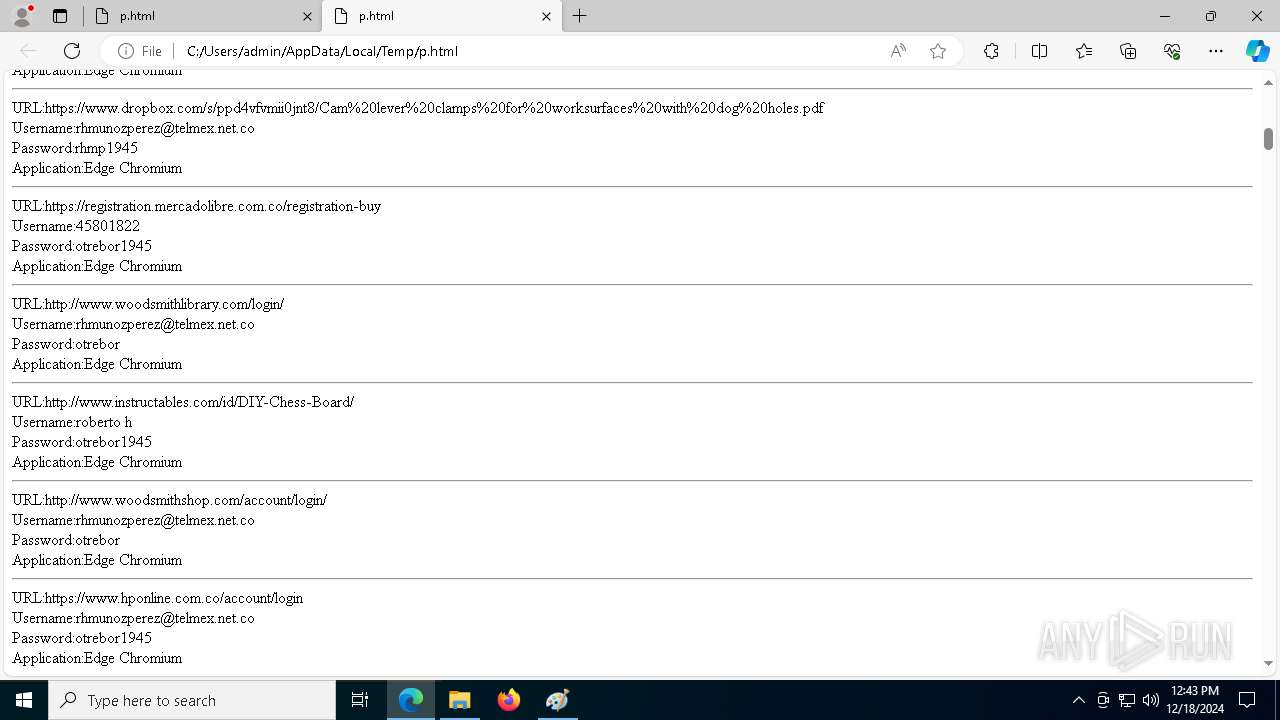
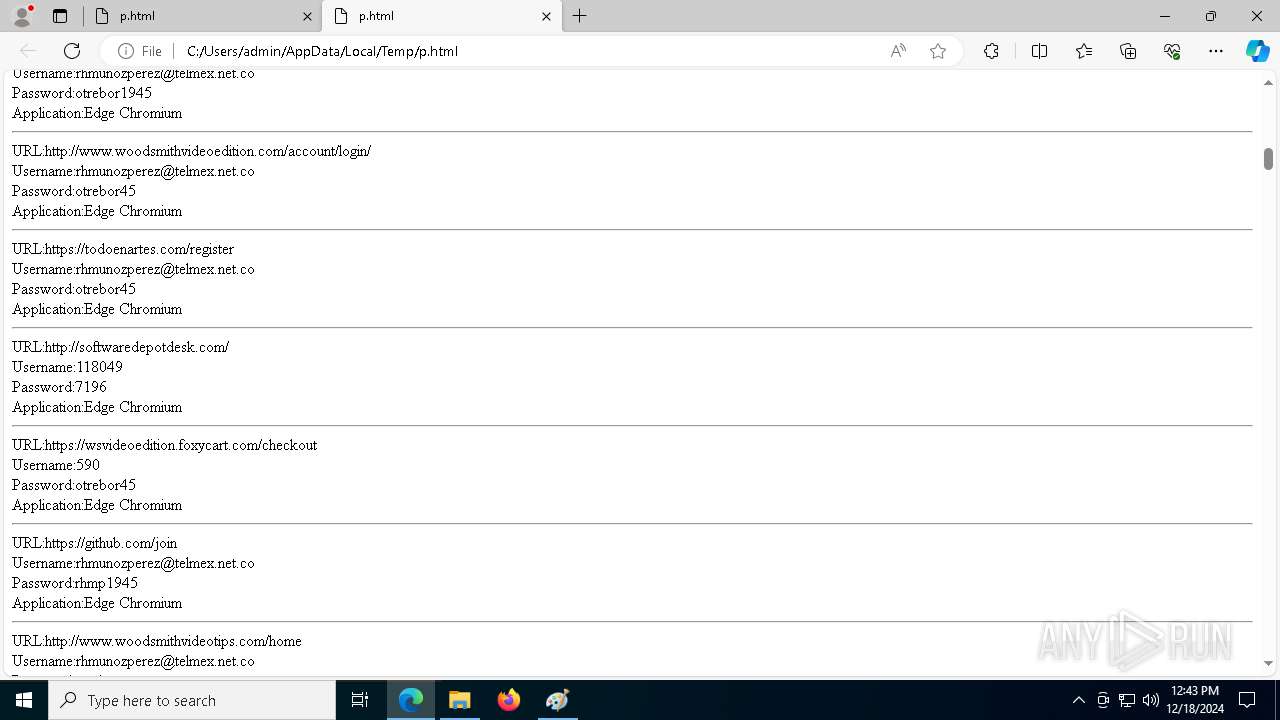
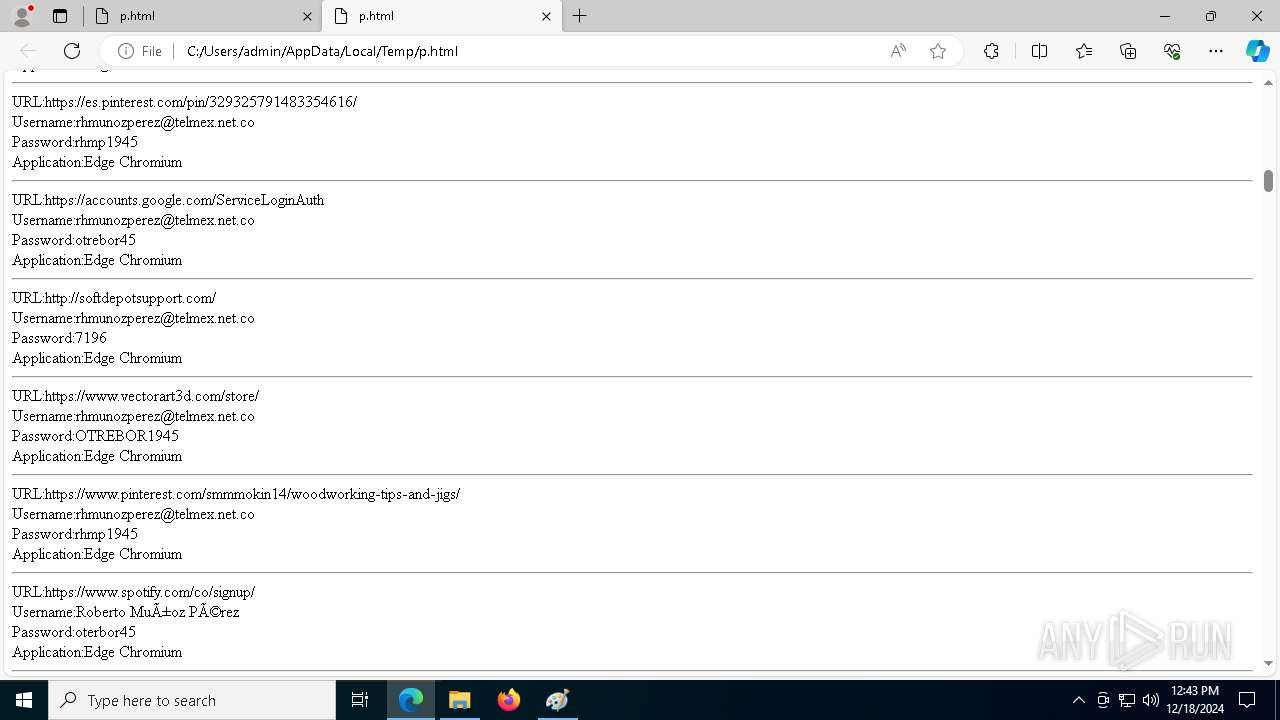
Executable files
7
Suspicious files
276
Text files
79
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6304 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6304.47079\Screen.jpg.lnk | lnk | |
MD5:DBF4819FD016C532DB4313B9748ED879 | SHA256:2932DFC97050720A10F6B41F2C765D6200C64ED418A7058126965E827953323D | |||
| 6304 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6304.47079\Browsers.txt.lnk | lnk | |
MD5:DBF4819FD016C532DB4313B9748ED879 | SHA256:2932DFC97050720A10F6B41F2C765D6200C64ED418A7058126965E827953323D | |||
| 6304 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6304.47079\Information.txt.lnk | binary | |
MD5:DBF4819FD016C532DB4313B9748ED879 | SHA256:2932DFC97050720A10F6B41F2C765D6200C64ED418A7058126965E827953323D | |||
| 6304 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6304.47079\Telegram.txt.lnk | binary | |
MD5:DBF4819FD016C532DB4313B9748ED879 | SHA256:2932DFC97050720A10F6B41F2C765D6200C64ED418A7058126965E827953323D | |||
| 6820 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_bl1qas2q.iob.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6304 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6304.47079\Wallets\Excodus.txt.lnk | lnk | |
MD5:DBF4819FD016C532DB4313B9748ED879 | SHA256:2932DFC97050720A10F6B41F2C765D6200C64ED418A7058126965E827953323D | |||
| 6548 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:1E9E15EF6E531C4557100F20C9C76F01 | SHA256:46CB063CC268B69B172660F166C4394D5B4EDD802388B3EC16766DEBDB9F86C3 | |||
| 6548 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF14bfc4.TMP | — | |
MD5:— | SHA256:— | |||
| 6548 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6548 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF14bfc4.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
64
DNS requests
55
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2548 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
624 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
624 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
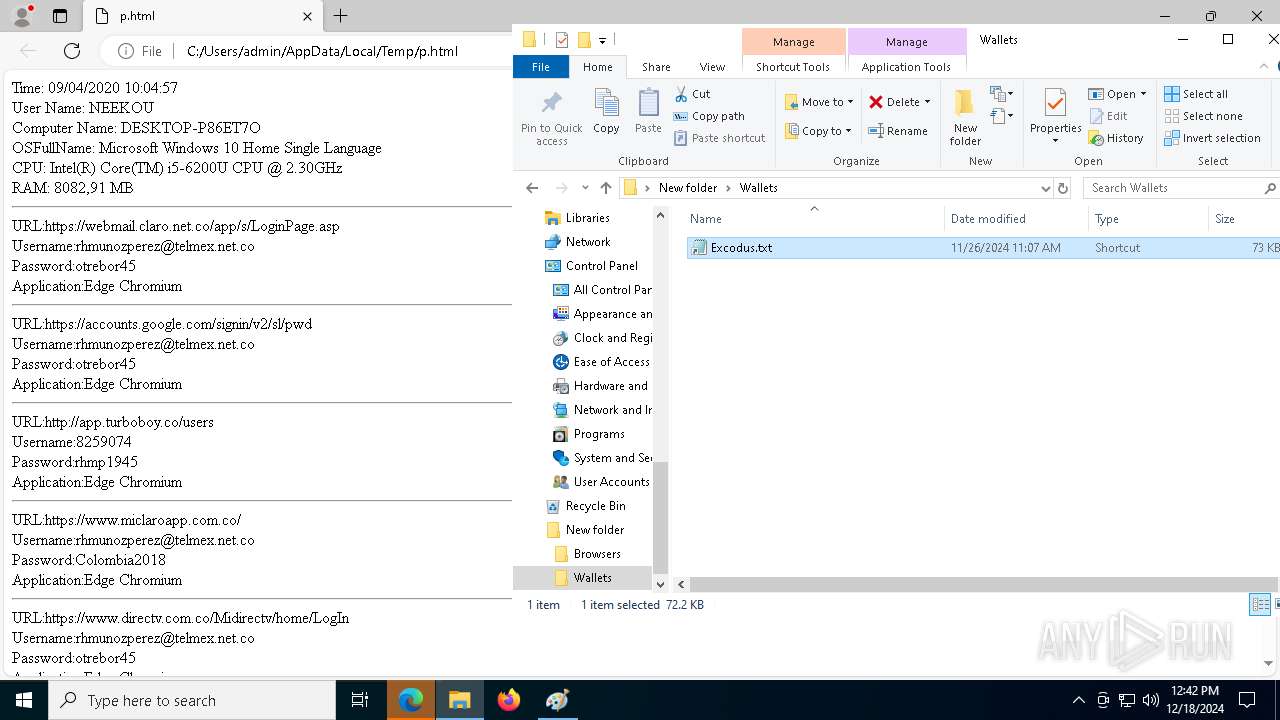
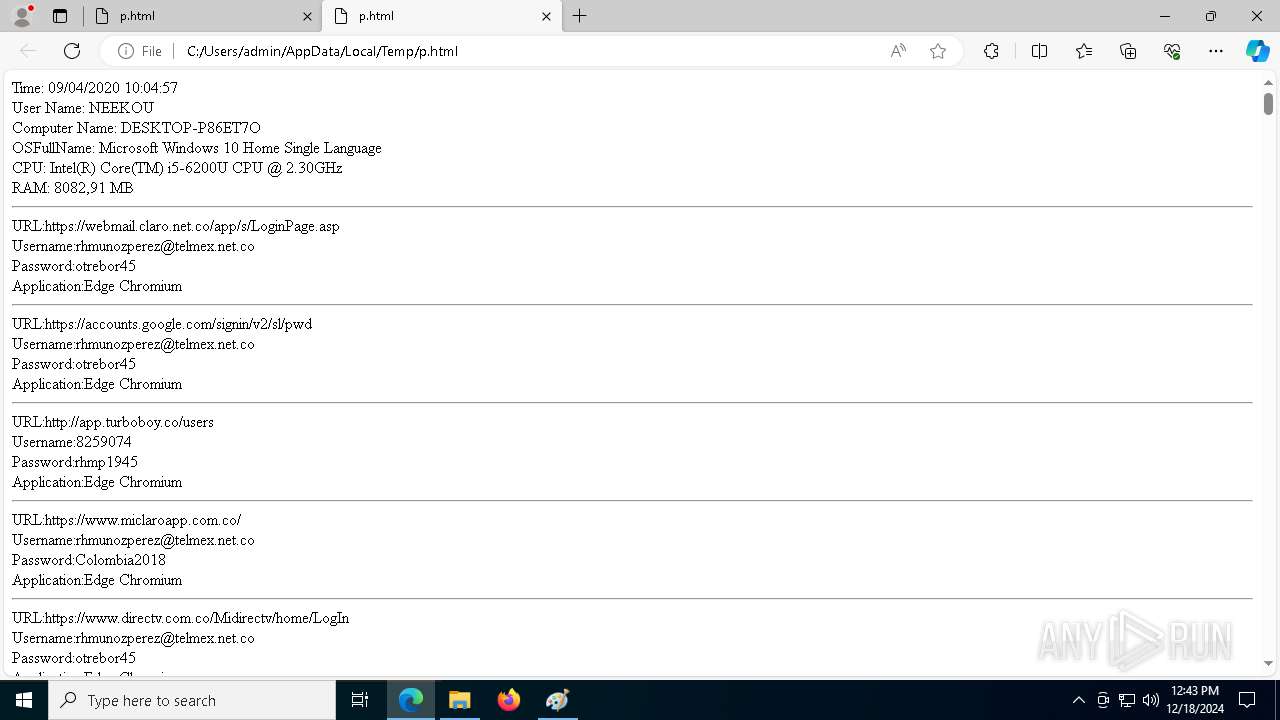
6772 | tmp97186975.exe | POST | 200 | 128.199.113.162:80 | http://128.199.113.162/XtfcshEgt/upwawsfrg.php | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6072 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.162:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |