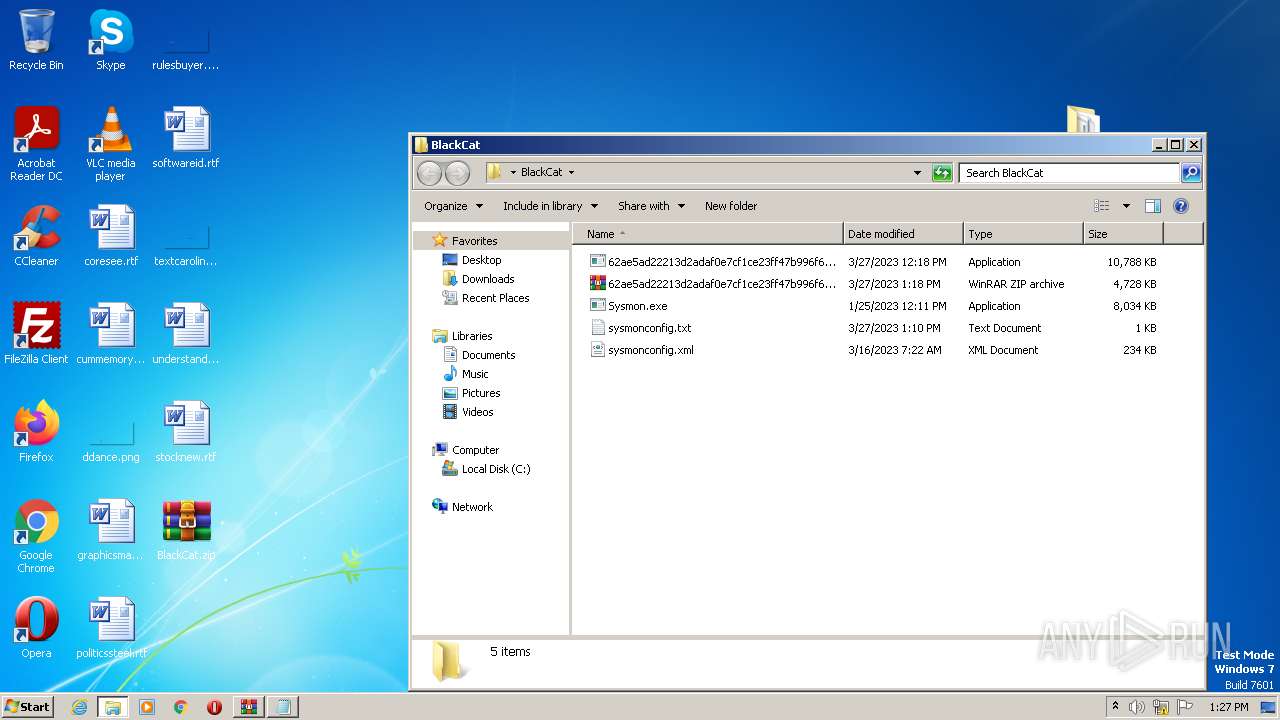
| File name: | BlackCat.zip |
| Full analysis: | https://app.any.run/tasks/c4b5375c-fb01-42cf-9a60-e7d054cf4de2 |
| Verdict: | Malicious activity |
| Analysis date: | March 27, 2023, 12:26:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | BB810D8D2197D1B9AD032E44A75B8FCC |
| SHA1: | 536D2D38B2730CD246151F51E421DFD1B251E1AB |
| SHA256: | E8EA99B5BAA6016A7E48B82D4A656BF64C5BE95D7CD4CB18FC2E3A604B6FFD03 |
| SSDEEP: | 98304:FArtD0jSGJ4LzVwyOYAwouKGaakRUGqJwYxfNCN1H8s254GIZe9ai+UFA/6B5lsh:qlGJpoTmasqyYhQNh8ae8iNA/ash |
MALICIOUS
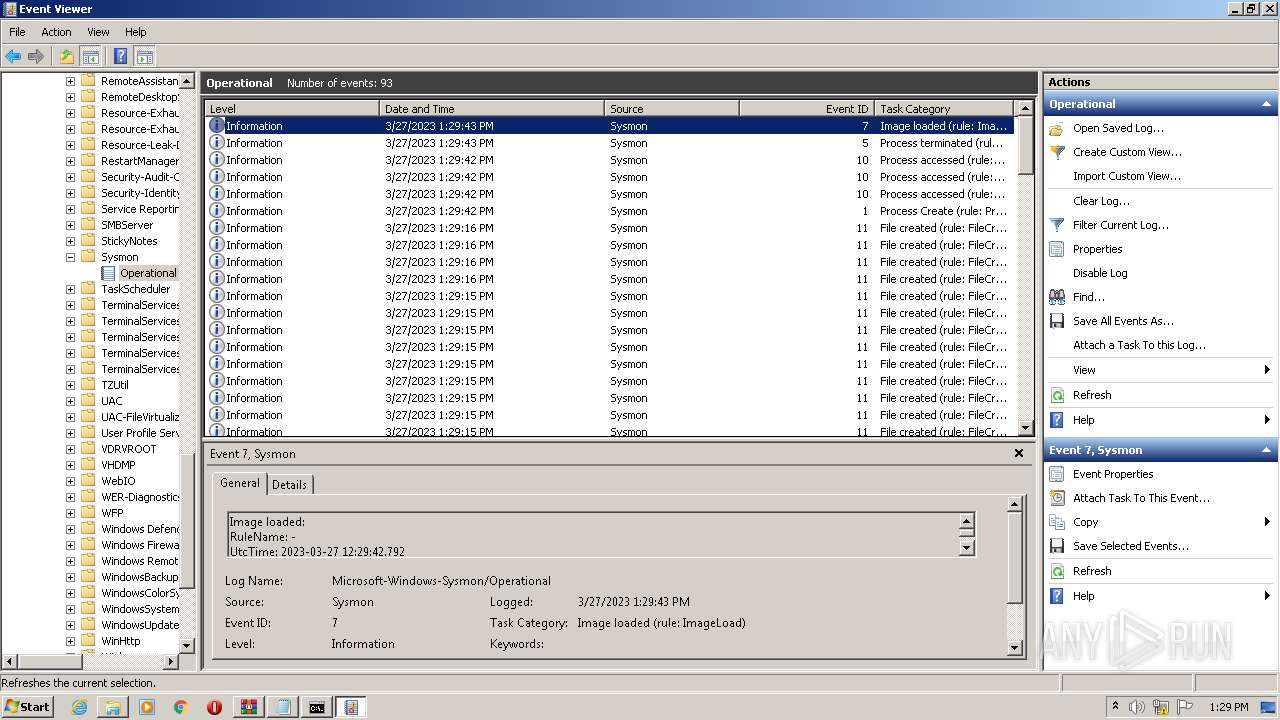
Application was dropped or rewritten from another process
- Sysmon.exe (PID: 3940)
- Sysmon.exe (PID: 2540)
- Sysmon.exe (PID: 3212)
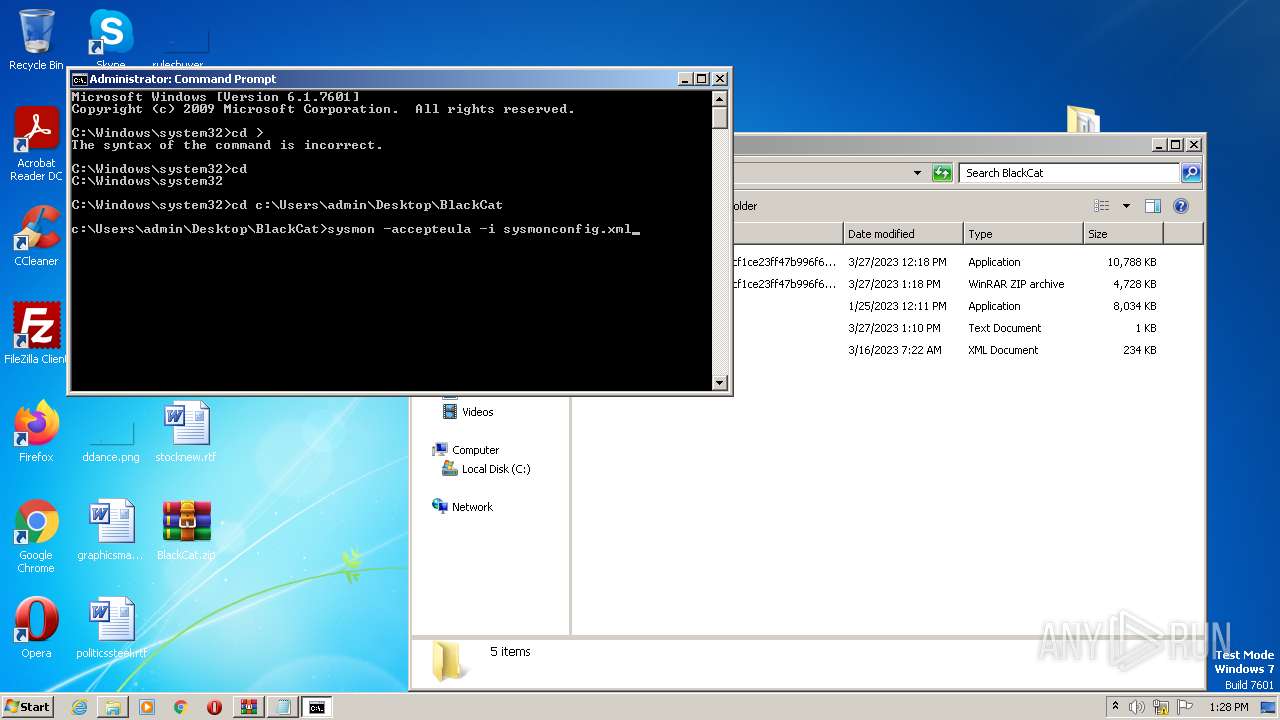
- 62ae5ad22213d2adaf0e7cf1ce23ff47b996f60065244b63f361a22daed2bdda.exe (PID: 3012)
Application was injected by another process
- svchost.exe (PID: 860)
- svchost.exe (PID: 1372)
- spoolsv.exe (PID: 1228)
- svchost.exe (PID: 1076)
- svchost.exe (PID: 832)
- lsass.exe (PID: 484)
- svchost.exe (PID: 756)
Runs injected code in another process
- Sysmon.exe (PID: 3212)
Creates a writable file the system directory
- svchost.exe (PID: 756)
SUSPICIOUS
Reads the Internet Settings
- wevtutil.exe (PID: 2000)
- wevtutil.exe (PID: 1164)
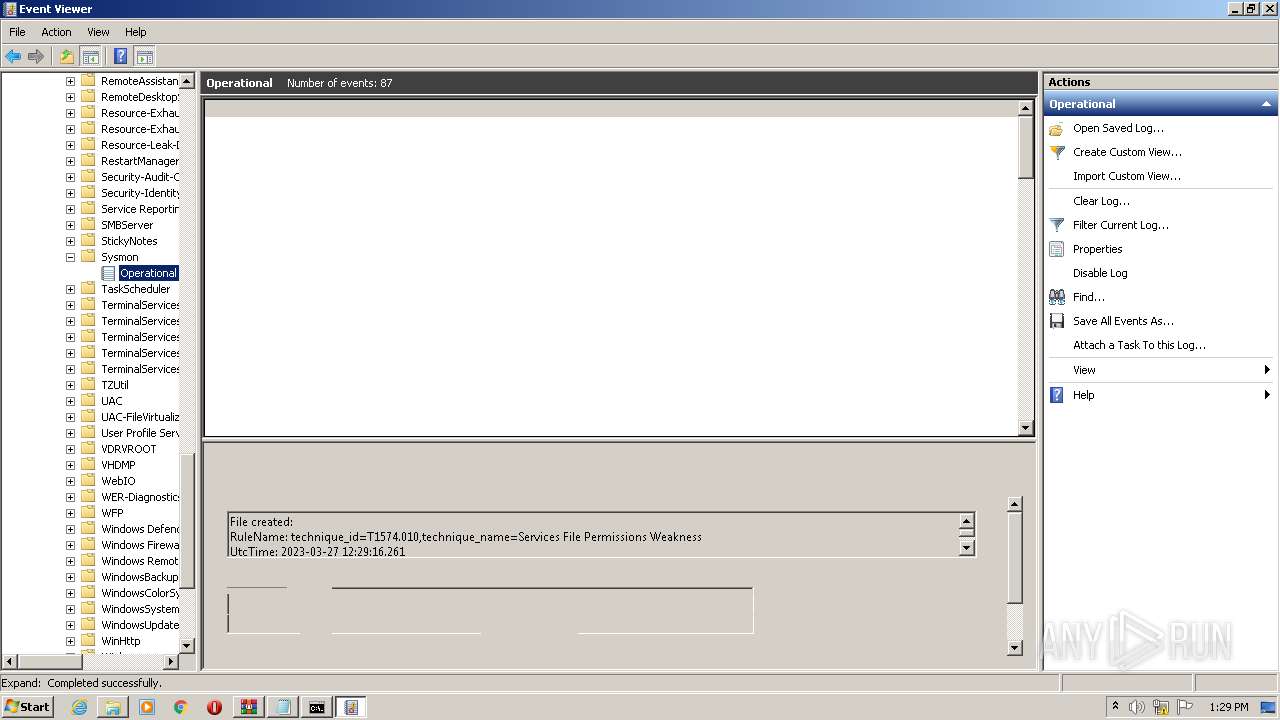
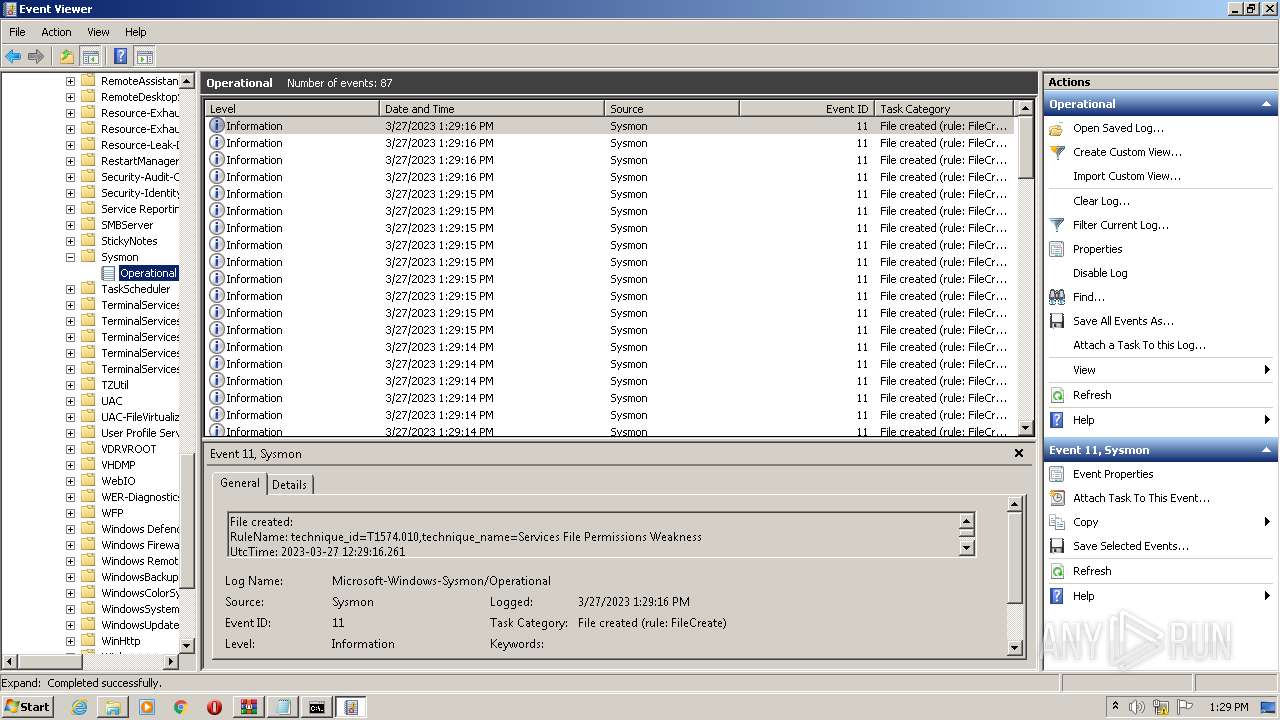
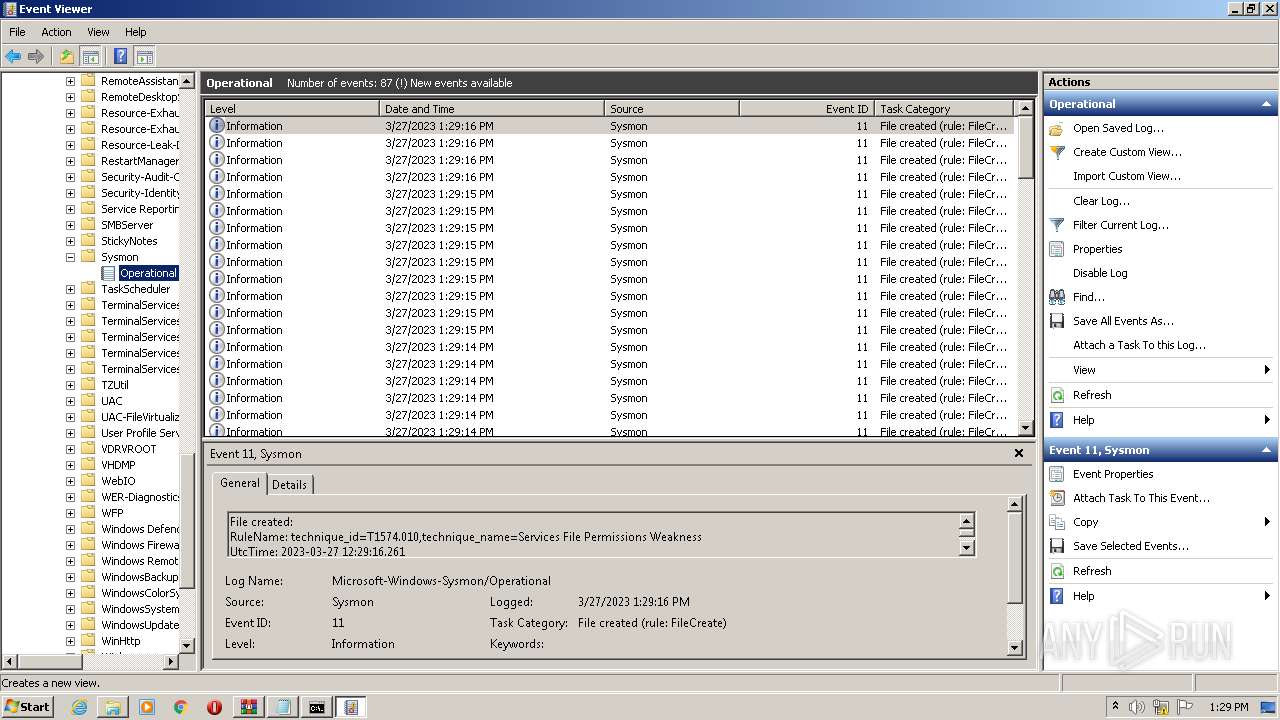
Uses WEVTUTIL.EXE to install publishers and event logs from the manifest
- Sysmon.exe (PID: 2540)
Executable content was dropped or overwritten
- Sysmon.exe (PID: 3940)
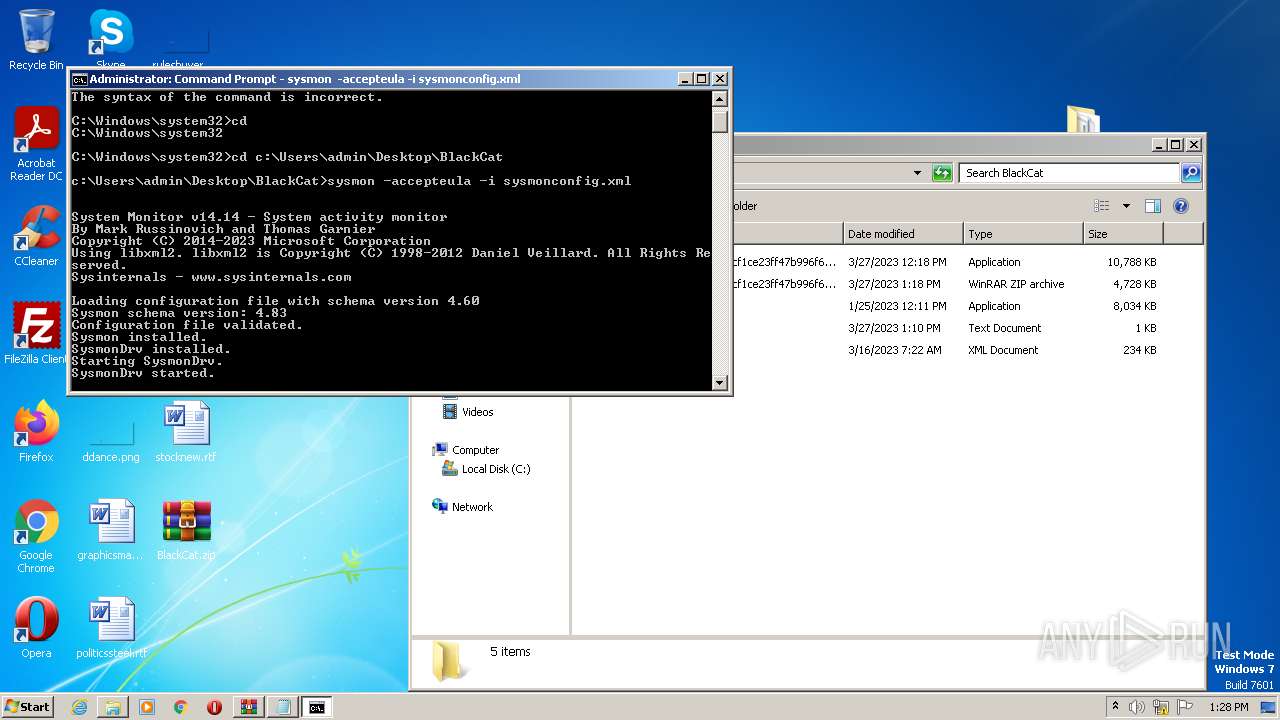
Drops a system driver (possible attempt to evade defenses)
- Sysmon.exe (PID: 3940)
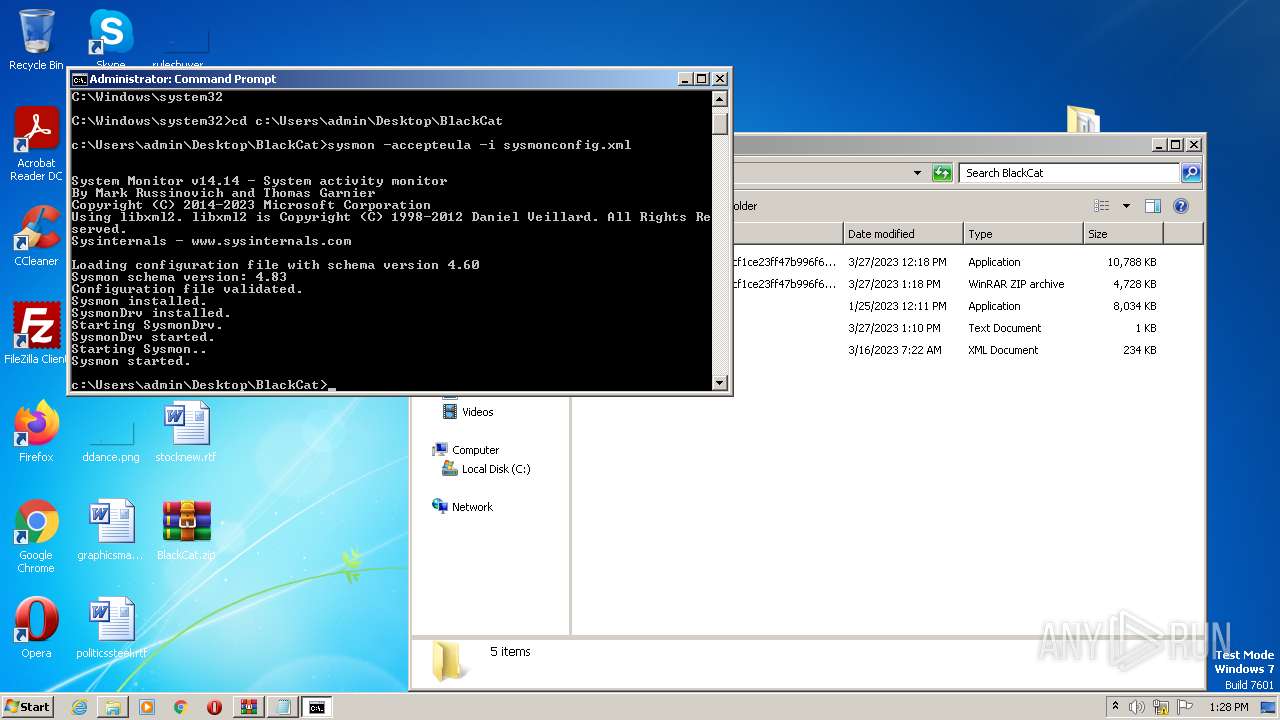
Executes as Windows Service
- Sysmon.exe (PID: 3212)
Reads settings of System Certificates
- Sysmon.exe (PID: 3212)
Uses WEVTUTIL.EXE to remove publishers and event logs from the manifest
- Sysmon.exe (PID: 2540)
Starts itself from another location
- Sysmon.exe (PID: 3940)
Checks Windows Trust Settings
- Sysmon.exe (PID: 3212)
INFO
Creates files or folders in the user directory
- lsass.exe (PID: 484)
The process checks LSA protection
- lsass.exe (PID: 484)
- Sysmon.exe (PID: 3940)
- Sysmon.exe (PID: 3212)
- unsecapp.exe (PID: 1356)
- mmc.exe (PID: 2268)
Manual execution by a user
- cmd.exe (PID: 2460)
- cmd.exe (PID: 1112)
- notepad.exe (PID: 2944)
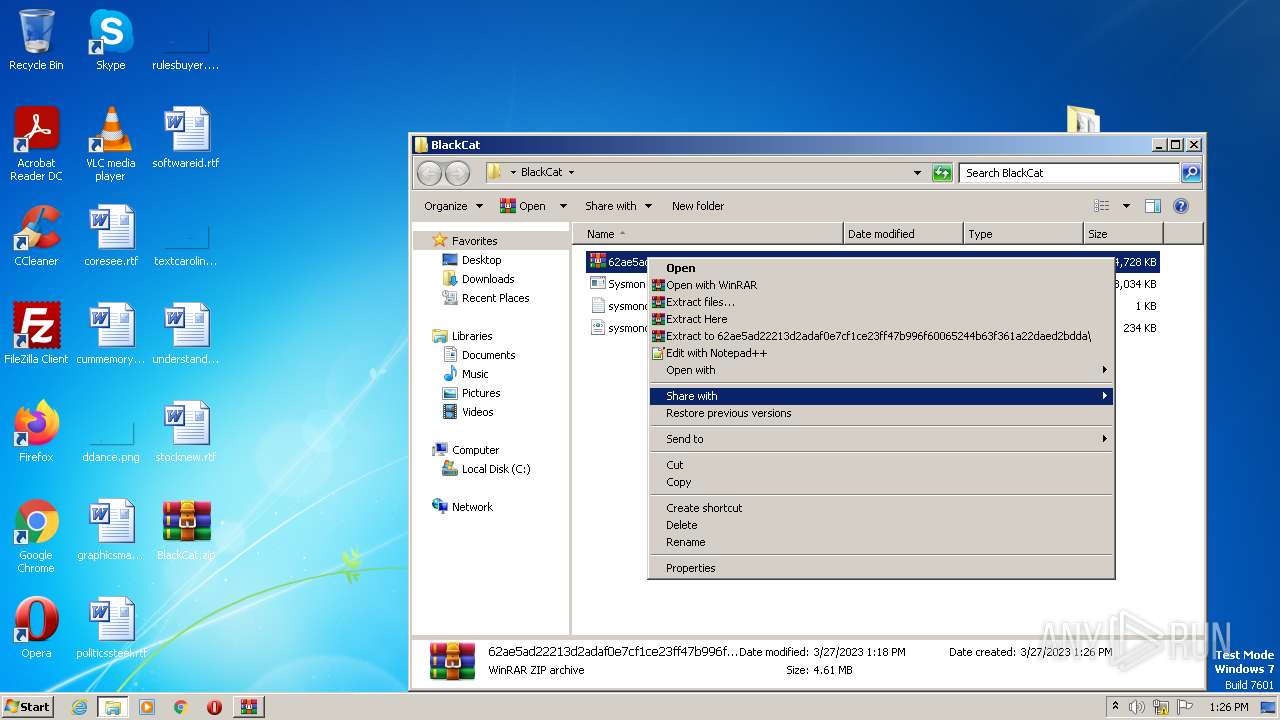
- WinRAR.exe (PID: 2872)
- mmc.exe (PID: 1032)
- mmc.exe (PID: 2268)
- 62ae5ad22213d2adaf0e7cf1ce23ff47b996f60065244b63f361a22daed2bdda.exe (PID: 3012)
- chrome.exe (PID: 2472)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2872)
- WinRAR.exe (PID: 852)
Checks supported languages
- Sysmon.exe (PID: 3940)
- Sysmon.exe (PID: 2540)
- Sysmon.exe (PID: 3212)
Reads the machine GUID from the registry
- Sysmon.exe (PID: 3940)
- Sysmon.exe (PID: 3212)
- Sysmon.exe (PID: 2540)
Reads the time zone
- svchost.exe (PID: 756)
- Sysmon.exe (PID: 3212)
Reads the computer name
- Sysmon.exe (PID: 3212)
- Sysmon.exe (PID: 3940)
- Sysmon.exe (PID: 2540)
Reads CPU info
- Sysmon.exe (PID: 3212)
Creates files in the program directory
- mmc.exe (PID: 2268)
Application launched itself
- chrome.exe (PID: 2472)
Create files in a temporary directory
- Sysmon.exe (PID: 2540)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | BlackCat/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2023:03:27 18:18:34 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
84
Monitored processes
31
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1024,12240322902341856067,12941116706727338374,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1044 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | |||||||||||||||
| 484 | C:\Windows\system32\lsass.exe | C:\Windows\System32\lsass.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Security Authority Process Exit code: 0 Version: 6.1.7601.24545 (win7sp1_ldr_escrow.200102-1707) Modules
| |||||||||||||||
| 756 | C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 832 | C:\Windows\system32\svchost.exe -k LocalService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
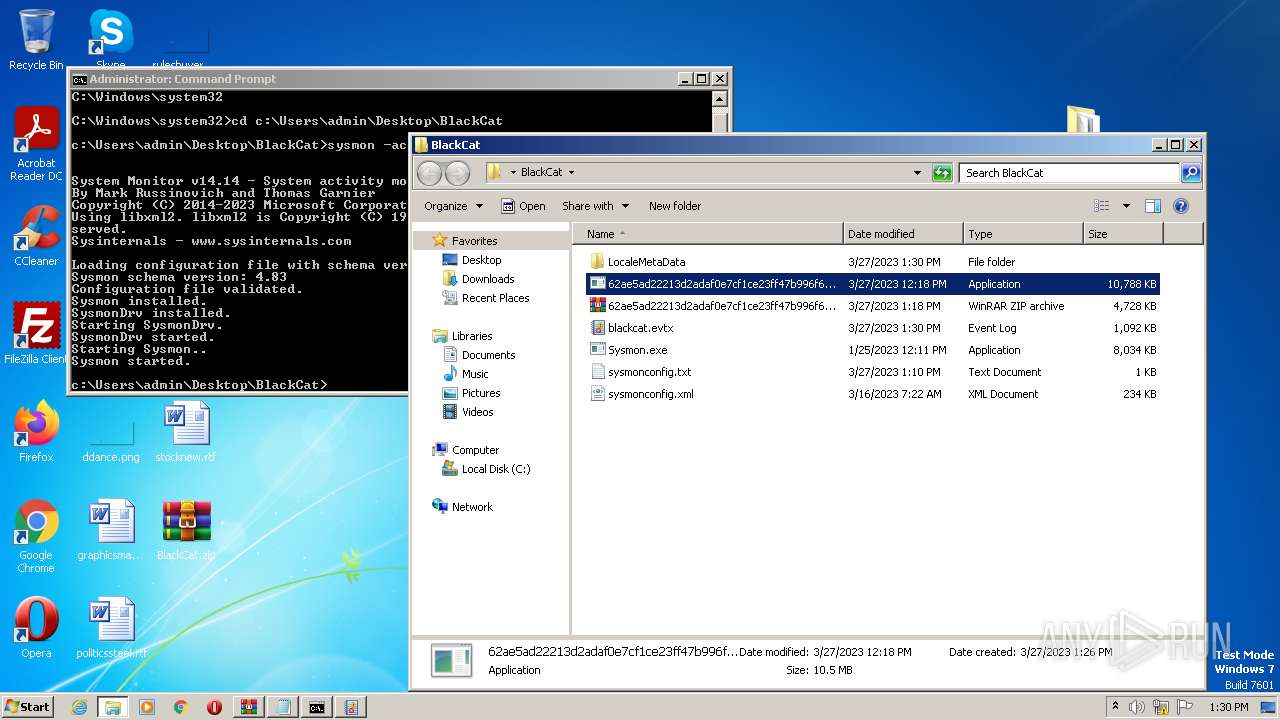
| 852 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\BlackCat.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 860 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 912 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1024,12240322902341856067,12941116706727338374,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2960 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | |||||||||||||||
| 1032 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\eventvwr.msc" /s | C:\Windows\System32\mmc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1076 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1112 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
295 322
Read events
295 240
Write events
82
Delete events
0
Modification events
| (PID) Process: | (852) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
8
Suspicious files
28
Text files
54
Unknown types
138
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 484 | lsass.exe | C:\Users\admin\AppData\Roaming\Microsoft\Protect\S-1-5-21-1302019708-1500728564-335382590-1000\Preferred | vc | |
MD5:— | SHA256:— | |||
| 852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa852.48375\BlackCat\62ae5ad22213d2adaf0e7cf1ce23ff47b996f60065244b63f361a22daed2bdda.zip | compressed | |
MD5:— | SHA256:— | |||
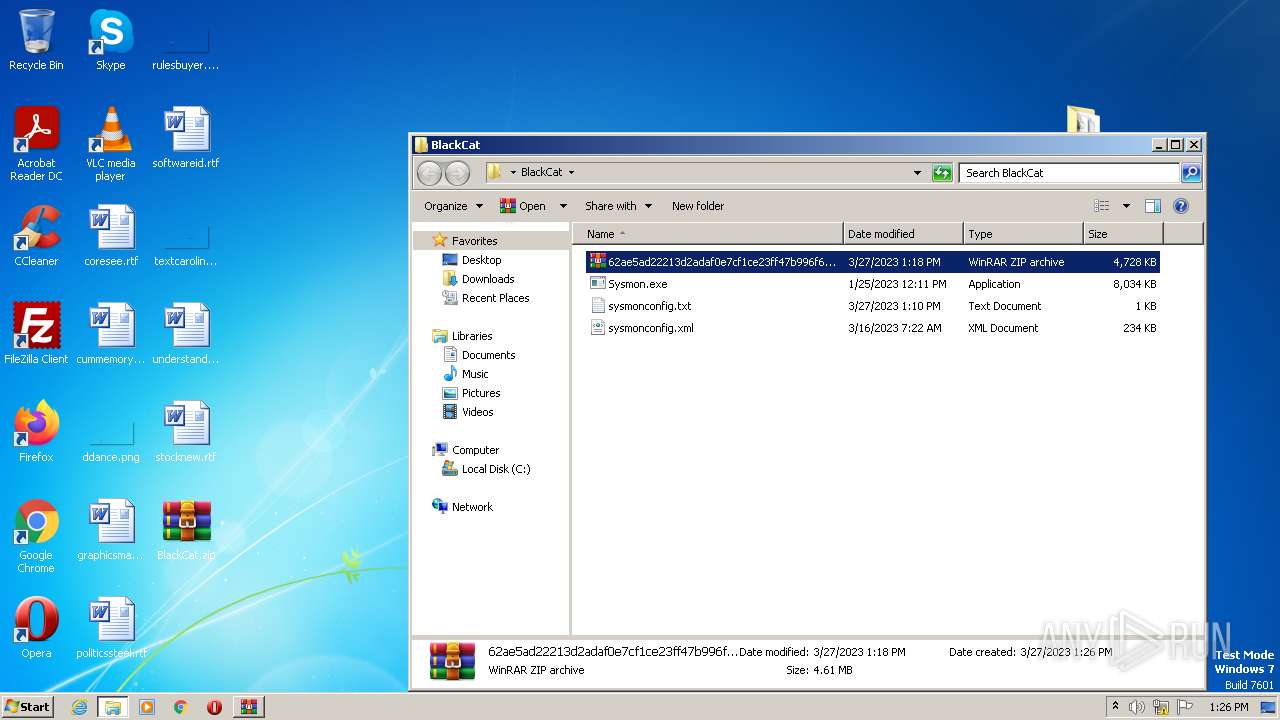
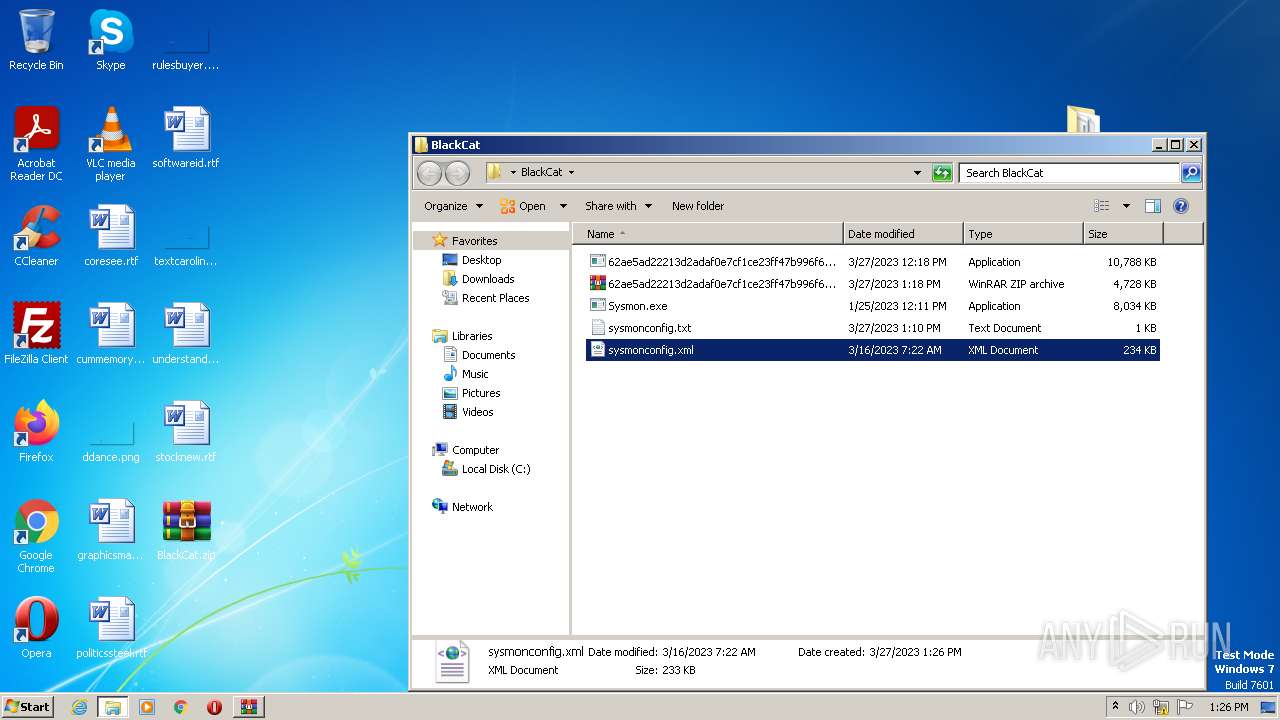
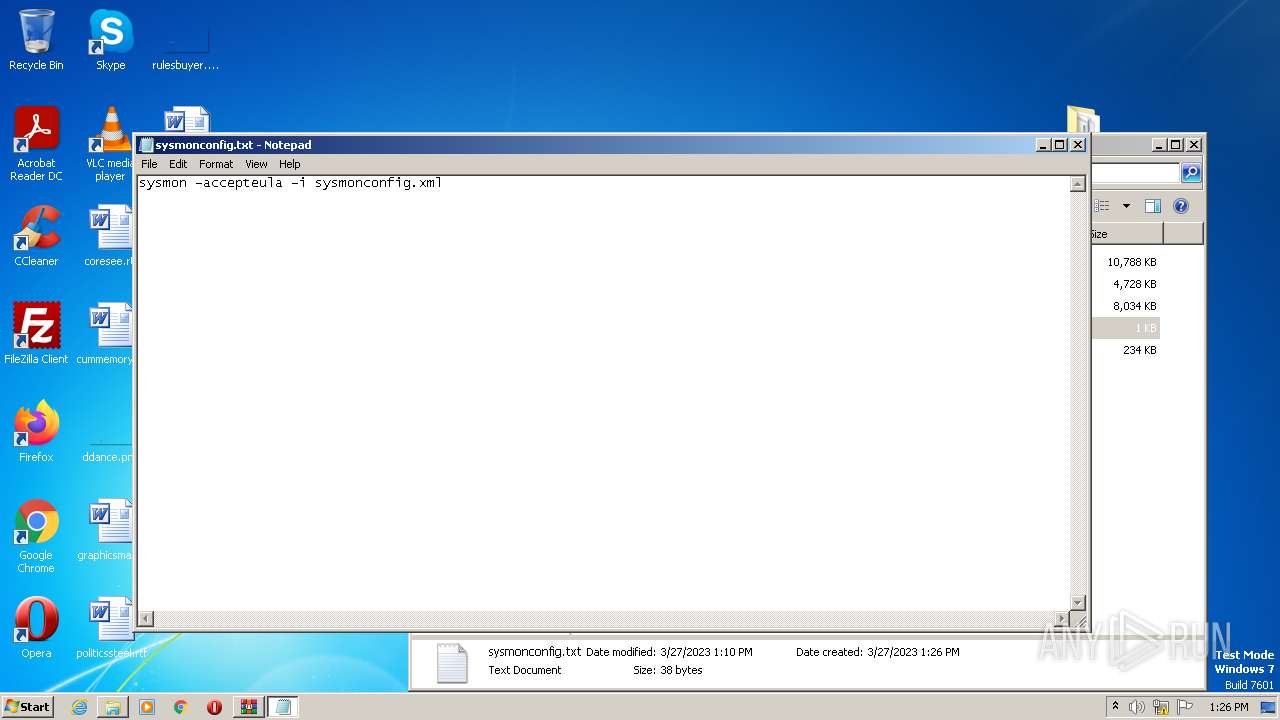
| 852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa852.48375\BlackCat\sysmonconfig.xml | text | |
MD5:— | SHA256:— | |||
| 852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa852.48375\BlackCat\sysmonconfig.txt | text | |
MD5:— | SHA256:— | |||
| 860 | svchost.exe | C:\Windows\appcompat\programs\RecentFileCache.bcf | txt | |
MD5:— | SHA256:— | |||
| 852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa852.48375\BlackCat\Sysmon.exe | executable | |
MD5:A6048861CEF42D7BE2A35367425ACD91 | SHA256:29917A051BCC99DBA2ED9B073CE838CEC9CF858DD6EED9AEE0C464D29B629FB2 | |||
| 756 | svchost.exe | C:\Windows\System32\Winevt\Logs\Microsoft-Windows-AppLocker%4MSI and Script.evtx | evtx | |
MD5:— | SHA256:— | |||
| 756 | svchost.exe | C:\Windows\System32\Winevt\Logs\Microsoft-Windows-Authentication User Interface%4Operational.evtx | evtx | |
MD5:— | SHA256:— | |||
| 756 | svchost.exe | C:\Windows\System32\Winevt\Logs\Microsoft-Windows-API-Tracing%4Operational.evtx | evtx | |
MD5:— | SHA256:— | |||
| 756 | svchost.exe | C:\Windows\System32\Winevt\Logs\Microsoft-Windows-Audio%4Operational.evtx | evtx | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
10
DNS requests
9
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 142.250.186.77:443 | accounts.google.com | GOOGLE | US | suspicious |
— | — | 142.250.186.174:443 | clients2.google.com | GOOGLE | US | whitelisted |
— | — | 142.250.185.100:443 | www.google.com | GOOGLE | US | whitelisted |
— | — | 142.250.181.225:443 | clients2.googleusercontent.com | GOOGLE | US | whitelisted |
— | — | 142.250.186.42:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
— | — | 142.250.186.67:443 | www.gstatic.com | GOOGLE | US | whitelisted |
— | — | 142.250.186.99:443 | fonts.gstatic.com | GOOGLE | US | whitelisted |
— | — | 142.250.184.227:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| malicious |
accounts.google.com |
| shared |
clients2.google.com |
| whitelisted |
clients2.googleusercontent.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
Threats
Process | Message |
|---|---|
mmc.exe | ViewerConfigPath = 'C:\ProgramData\Microsoft\Event Viewer': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerAdminViewsPath = 'C:\ProgramData\Microsoft\Event Viewer\Views\ApplicationViewsRootNode': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerExternalLogsPath = 'C:\ProgramData\Microsoft\Event Viewer\ExternalLogs': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerViewsFolderPath = 'C:\ProgramData\Microsoft\Event Viewer\Views': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerViewsFolderPath = 'C:\ProgramData\Microsoft\Event Viewer\Views': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerAdminViewsPath = 'C:\ProgramData\Microsoft\Event Viewer\Views\ApplicationViewsRootNode': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerExternalLogsPath = 'C:\ProgramData\Microsoft\Event Viewer\ExternalLogs': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerConfigPath = 'C:\ProgramData\Microsoft\Event Viewer': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | Failed to get ChannelConfigOwningPublisher -122-The data area passed to a system call is too small
|
mmc.exe | Failed to get ChannelConfigOwningPublisher -122-The data area passed to a system call is too small
|