| File name: | gmer.exe |
| Full analysis: | https://app.any.run/tasks/b0efcd3d-4b27-4132-9c96-45f0c6297209 |
| Verdict: | Malicious activity |
| Analysis date: | November 02, 2020, 02:12:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | E9DC058440D321AA17D0600B3CA0AB04 |
| SHA1: | 539C228B6B332F5AA523E5CE358C16647D8BBE57 |
| SHA256: | E8A3E804A96C716A3E9B69195DB6FFB0D33E2433AF871E4D4E1EAB3097237173 |
| SSDEEP: | 6144:wW3dQfk45aQOVusKHL7G0FJ6KbJLor/XqNjHtBfLptTksD0c2PMM40:FgkOZHvNJ6KbJE/qNBJT/h2PM |
MALICIOUS
Loads dropped or rewritten executable
- gmer.exe (PID: 3180)
Changes settings of System certificates
- gmer.exe (PID: 3180)
SUSPICIOUS
Creates or modifies windows services
- gmer.exe (PID: 3180)
Adds / modifies Windows certificates
- gmer.exe (PID: 3180)
Executable content was dropped or overwritten
- gmer.exe (PID: 3180)
Low-level read access rights to disk partition
- gmer.exe (PID: 3180)
INFO
Reads settings of System Certificates
- gmer.exe (PID: 3180)
Dropped object may contain Bitcoin addresses
- gmer.exe (PID: 3180)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (43.5) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (42.7) |
| .exe | | | Win32 Executable (generic) (7.2) |
| .exe | | | Generic Win/DOS Executable (3.2) |
| .exe | | | DOS Executable Generic (3.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:03:11 14:53:14+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 376832 |
| InitializedDataSize: | 8192 |
| UninitializedDataSize: | 520192 |
| EntryPoint: | 0xdb470 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.2.19882.0 |
| ProductVersionNumber: | 2.2.19882.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | Polish |
| CharacterSet: | Unicode |
| FileVersion: | 2, 2, 19882 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 11-Mar-2016 13:53:14 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000118 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 11-Mar-2016 13:53:14 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
UPX0 | 0x00001000 | 0x0007F000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
UPX1 | 0x00080000 | 0x0005C000 | 0x0005B800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.92656 |
.rsrc | 0x000DC000 | 0x00002000 | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.47048 |
Imports
KERNEL32.DLL |
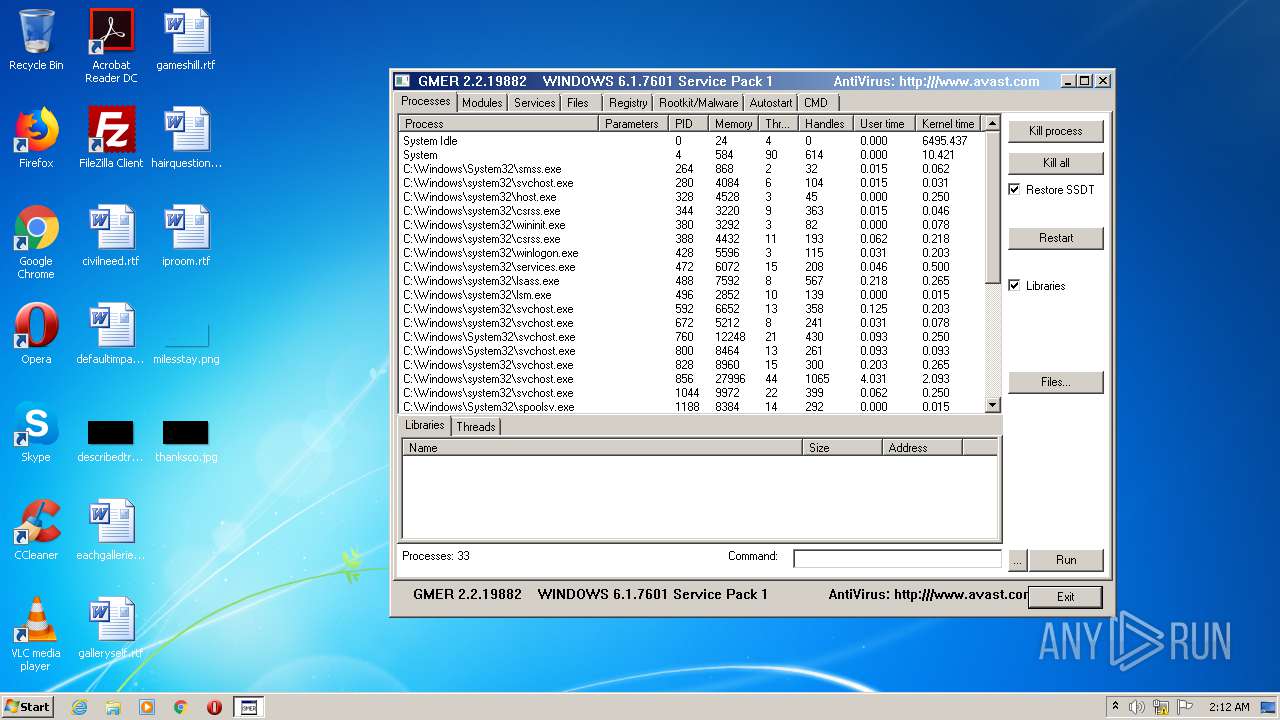
Total processes
38
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2568 | "C:\Users\admin\AppData\Local\Temp\gmer.exe" | C:\Users\admin\AppData\Local\Temp\gmer.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 2, 2, 19882 Modules
| |||||||||||||||
| 3180 | "C:\Users\admin\AppData\Local\Temp\gmer.exe" | C:\Users\admin\AppData\Local\Temp\gmer.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 2, 2, 19882 Modules
| |||||||||||||||
Total events
159
Read events
132
Write events
27
Delete events
0
Modification events
| (PID) Process: | (3180) gmer.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\kxldapob |
| Operation: | write | Name: | Type |
Value: 1 | |||
| (PID) Process: | (3180) gmer.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\kxldapob |
| Operation: | write | Name: | ErrorControl |
Value: 1 | |||
| (PID) Process: | (3180) gmer.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\kxldapob |
| Operation: | write | Name: | Start |
Value: 3 | |||
| (PID) Process: | (3180) gmer.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\kxldapob |
| Operation: | write | Name: | ImagePath |
Value: \??\C:\Users\admin\AppData\Local\Temp\kxldapob.sys | |||
| (PID) Process: | (3180) gmer.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\kxldapob |
| Operation: | write | Name: | Group |
Value: Base | |||
| (PID) Process: | (3180) gmer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3180) gmer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\4EB6D578499B1CCF5F581EAD56BE3D9B6744A5E5 |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000CB17E431673EE209FE455793F30AFA1C0F0000000100000014000000E91E1E972B8F467AB4E0598FA92285387DEE94C90300000001000000140000004EB6D578499B1CCF5F581EAD56BE3D9B6744A5E57E00000001000000080000000040D0D1B0FFD4017F000000010000000C000000300A06082B060105050703011D0000000100000010000000C6CBCAFA17955C4CFD41ECA0C654C3610B000000010000001200000056006500720069005300690067006E0000001400000001000000140000007FD365A7C2DDECBBF03009F34339FA02AF3331336200000001000000200000009ACFAB7E43C8D880D06B262A94DEEEE4B4659989C3D0CAF19BAF6405E41AB7DF09000000010000002A000000302806082B0601050507030106082B0601050507030206082B0601050507030406082B0601050507030353000000010000004600000030443021060B6086480186F8450107170630123010060A2B0601040182373C0101030200C0301F06096086480186FD6C020130123010060A2B0601040182373C0101030200C0190000000100000010000000D8B5FB368468620275D142FFD2AADE372000000001000000D7040000308204D3308203BBA003020102021018DAD19E267DE8BB4A2158CDCC6B3B4A300D06092A864886F70D01010505003081CA310B300906035504061302555331173015060355040A130E566572695369676E2C20496E632E311F301D060355040B1316566572695369676E205472757374204E6574776F726B313A3038060355040B1331286329203230303620566572695369676E2C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79314530430603550403133C566572695369676E20436C6173732033205075626C6963205072696D6172792043657274696669636174696F6E20417574686F72697479202D204735301E170D3036313130383030303030305A170D3336303731363233353935395A3081CA310B300906035504061302555331173015060355040A130E566572695369676E2C20496E632E311F301D060355040B1316566572695369676E205472757374204E6574776F726B313A3038060355040B1331286329203230303620566572695369676E2C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79314530430603550403133C566572695369676E20436C6173732033205075626C6963205072696D6172792043657274696669636174696F6E20417574686F72697479202D20473530820122300D06092A864886F70D01010105000382010F003082010A0282010100AF240808297A359E600CAAE74B3B4EDC7CBC3C451CBB2BE0FE2902F95708A364851527F5F1ADC831895D22E82AAAA642B38FF8B955B7B1B74BB3FE8F7E0757ECEF43DB66621561CF600DA4D8DEF8E0C362083D5413EB49CA59548526E52B8F1B9FEBF5A191C23349D843636A524BD28FE870514DD189697BC770F6B3DC1274DB7B5D4B56D396BF1577A1B0F4A225F2AF1C926718E5F40604EF90B9E400E4DD3AB519FF02BAF43CEEE08BEB378BECF4D7ACF2F6F03DAFDD759133191D1C40CB7424192193D914FEAC2A52C78FD50449E48D6347883C6983CBFE47BD2B7E4FC595AE0E9DD4D143C06773E314087EE53F9F73B8330ACF5D3F3487968AEE53E825150203010001A381B23081AF300F0603551D130101FF040530030101FF300E0603551D0F0101FF040403020106306D06082B0601050507010C0461305FA15DA05B3059305730551609696D6167652F6769663021301F300706052B0E03021A04148FE5D31A86AC8D8E6BC3CF806AD448182C7B192E30251623687474703A2F2F6C6F676F2E766572697369676E2E636F6D2F76736C6F676F2E676966301D0603551D0E041604147FD365A7C2DDECBBF03009F34339FA02AF333133300D06092A864886F70D0101050500038201010093244A305F62CFD81A982F3DEADC992DBD77F6A5792238ECC4A7A07812AD620E457064C5E797662D98097E5FAFD6CC2865F201AA081A47DEF9F97C925A0869200DD93E6D6E3C0D6ED8E606914018B9F8C1EDDFDB41AAE09620C9CD64153881C994EEA284290B136F8EDB0CDD2502DBA48B1944D2417A05694A584F60CA7E826A0B02AA251739B5DB7FE784652A958ABD86DE5E8116832D10CCDEFDA8822A6D281F0D0BC4E5E71A2619E1F4116F10B595FCE7420532DBCE9D515E28B69E85D35BEFA57D4540728EB70E6B0E06FB33354871B89D278BC4655F0D86769C447AF6955CF65D320833A454B6183F685CF2424A853854835FD1E82CF2AC11D6A8ED636A | |||
| (PID) Process: | (3180) gmer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\3B1EFD3A66EA28B16697394703A72CA340A05BD5 |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000A266BB7DCC38A562631361BBF61DD11B140000000100000014000000D5F656CB8FE8A25C6268D13D94905BD7CE9A18C40300000001000000140000003B1EFD3A66EA28B16697394703A72CA340A05BD50B00000001000000540000004D006900630072006F0073006F0066007400200052006F006F007400200043006500720074006900660069006300610074006500200041007500740068006F00720069007400790020003200300031003000000069000000010000000E000000300C060A2B0601040182373C03020F000000010000002000000008FBA831C08544208F5208686B991CA1B2CFC510E7301784DDF1EB5BF03932391900000001000000100000003C70FAEA25600CE3B2CC5F0B222ED6292000000001000000F1050000308205ED308203D5A003020102021028CC3A25BFBA44AC449A9B586B4339AA300D06092A864886F70D01010B0500308188310B3009060355040613025553311330110603550408130A57617368696E67746F6E3110300E060355040713075265646D6F6E64311E301C060355040A13154D6963726F736F667420436F72706F726174696F6E31323030060355040313294D6963726F736F667420526F6F7420436572746966696361746520417574686F726974792032303130301E170D3130303632333231353732345A170D3335303632333232303430315A308188310B3009060355040613025553311330110603550408130A57617368696E67746F6E3110300E060355040713075265646D6F6E64311E301C060355040A13154D6963726F736F667420436F72706F726174696F6E31323030060355040313294D6963726F736F667420526F6F7420436572746966696361746520417574686F72697479203230313030820222300D06092A864886F70D01010105000382020F003082020A0282020100B9089E28E4E4EC064E5068B341C57BEBAEB68EAF81BA22441F6534694CBE704017F2167BE279FD86ED0D39F41BA8AD92901ECB3D768F5AD9B591102E3C058D8A6D2454E71FED56AD83B4509C15A51774885920FC08C58476D368D46F2878CE5CB8F3509044FFE3635FBEA19A2C961504D607FE1E8421E0423111C4283694CF50A4629EC9D6AB7100B25B0CE696D40A2496F5FFC6D5B71BD7CBB72162AF12DCA15D37E31AFB1A4698C09BC0E7631F2A0893027E1E6A8EF29F1889E42285A2B1845740FFF50ED86F9CEDE2453101CD17E97FB08145E3AA214026A172AAA74F3C01057EEE8358B15E06639962917882B70D930C246AB41BDB27EC5F95043F934A30F59718B3A7F919A793331D01C8DB22525CD725C946F9A2FB875943BE9B62B18D2D86441A46AC78617E3009FAAE89C4412A2266039139459CC78B0CA8CA0D2FFB52EA0CF76333239DFEB01FAD67D6A75003C6047063B52CB1865A43B7FBAEF96E296E21214126068CC9C3EEB0C28593A1B985D9E6326C4B4C3FD65DA3E5B59D77C39CC055B77400E3B838AB839750E19A42241DC6C0A330D11A5AC85234F773F1C7181F33AD7AECCB4160F3239420C24845AC5C51C62E80C2E27715BD8587ED369D9691EE00B5A370EC9FE38D80688376BAAF5D70522216E266FBBAB3C5C2F73E2F77A6CADEC1A6C6484CC3375123D327D7B84E7096F0A14476AF78CF9AE166130203010001A351304F300B0603551D0F040403020186300F0603551D130101FF040530030101FF301D0603551D0E04160414D5F656CB8FE8A25C6268D13D94905BD7CE9A18C4301006092B06010401823715010403020100300D06092A864886F70D01010B05000382020100ACA5968CBFBBAEA6F6D7718743315688FD1C32715B35B7D4F091F2AF37E214F1F30226053E16147F14BAB84FFB89B2B2E7D409CC6DB95B3B64657066B7F2B15ADF1A02F3F551B8676D79F3BF567BE484B92B1E9B409C2634F947189869D81CD7B6D1BF8F61C267C4B5EF60438E101B3649E420CAADA7C1B1276509F8CDF55B2AD08433F3EF1FF2F59C0B589337A075A0DE72DE6C752A6622F58C0630569F40B930AA40771582D78BECC0D3B2BD83C5770C1EAEAF1953A04D79719F0FAF30CE67F9D62CCC22417A07F2974218CE59791055DE6F10E4B8DA836640160968235B972E269A02BB578CC5B8BA69623280899EA1FDC0927C7B2B3319842A63C5006862FA9F478D997A453AA7E9EDEE6942B5F3819B4756107BFC7036841873EAEFF9974D9E3323DD260BBA2AB73F44DC8327FFBD61592B11B7CA4FDBC58B0C1C31AE32F8F8B942F77FDC619A76B15A04E1113D6645B71871BEC92485D6F3D4BA41345D122D25B98DA613486D4BB0077D99930961817457268AAB69E3E4D9C788CC24D8EC52245C1EBC9114E296DEEB0ADA9EDD5FB35BDBD482ECC620508725403AFBC7EECDFE33E56EC3840955032539C0E9355D6531A8F6BFA009CD29C7B336322EDC95F383C15ACF8B8DF6EAB321F8A4ED1E310EB64C11AB600BA412232217A3366482910412E0AB6F1ECB500561B440FF598671D1D533697CA9738A38D7640CF169 | |||
| (PID) Process: | (3180) gmer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\BE36A4562FB2EE05DBB3D32323ADF445084ED656 |
| Operation: | write | Name: | Blob |
Value: 0400000001000000100000007F667A71D3EB6978209A51149D83DA200F0000000100000010000000E8A598BE84828EFEAE701115013576B2030000000100000014000000BE36A4562FB2EE05DBB3D32323ADF445084ED65609000000010000000C000000300A06082B060105050703080B000000010000000E00000074006800610077007400650000001D00000001000000100000006454A4AA36F9B5CC8338E5A67FABFF17140000000100000014000000DDBCBD869C3F07ED40E31B08EFCEC4D188CD3B156200000001000000200000006B6C1E01F590F5AFC5FCF85CD0B9396884048659FC2C6D1170D68B045216C3FD190000000100000010000000181C2BE05851F96993E196F279954B232000000001000000A5020000308202A13082020AA003020102020100300D06092A864886F70D010104050030818B310B3009060355040613025A41311530130603550408130C5765737465726E2043617065311430120603550407130B44757262616E76696C6C65310F300D060355040A1306546861777465311D301B060355040B13145468617774652043657274696669636174696F6E311F301D060355040313165468617774652054696D657374616D70696E67204341301E170D3937303130313030303030305A170D3230313233313233353935395A30818B310B3009060355040613025A41311530130603550408130C5765737465726E2043617065311430120603550407130B44757262616E76696C6C65310F300D060355040A1306546861777465311D301B060355040B13145468617774652043657274696669636174696F6E311F301D060355040313165468617774652054696D657374616D70696E6720434130819F300D06092A864886F70D010101050003818D0030818902818100D62B587861458653EA347B519CEDB0E62E180EFEE05FA827D3B4C9E07C594E160E735460C17FF69F2EE93A8524153CDB470463C39EC4941A5ADF4C7AF3D9431D3C107A7925DB90FEF051E730D64100FD9F28DF79BE94BB9DB614E32385D7A941E04CA479B02B1A8BF2F83B8A3E45AC719200B4904198FB5FEDFAB72E8AF888370203010001A3133011300F0603551D130101FF040530030101FF300D06092A864886F70D01010405000381810067DBE2C2E6873D40838637357D1FCE9AC30C6620A8BAAA048986C2F510080DBFCBA2058AD04D363EF4D7EF69C65EE4B0946F4AB9E7DE5B88B67BDBE327E576C3F035C1CBB5279B3379DC90A6009E77FAFCCD279442169CD31C68ECBF5CDDE5A97B100A32745413318B85038491B75801301438AF28CAFCB150191909AC8949D3 | |||
| (PID) Process: | (3180) gmer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\742C3192E607E424EB4549542BE1BBC53E6174E2 |
| Operation: | write | Name: | Blob |
Value: 04000000010000001000000010FC635DF6263E0DF325BE5F79CD67670F0000000100000010000000D7C63BE0837DBABF881D4FBF5F986AD8030000000100000014000000742C3192E607E424EB4549542BE1BBC53E6174E27E0000000100000008000000000010C51E92D2017A000000010000000E000000300C060A2B0601040182375E01021D000000010000001000000027B3517667331CE2C1E74002B5FF2298140000000100000014000000E27F7BD877D5DF9E0A3F9EB4CB0E2EA9EFDB6977620000000100000020000000E7685634EFACF69ACE939A6B255B7B4FABEF42935B50A265ACB5CB6027E44E7053000000010000002400000030223020060A2B0601040182375E010130123010060A2B0601040182373C0101030200C009000000010000002A000000302806082B0601050507030106082B0601050507030206082B0601050507030406082B060105050703030B000000010000004600000056006500720069005300690067006E00200043006C006100730073002000330020005000750062006C006900630020005000720069006D00610072007900200043004100000019000000010000001000000091161B894B117ECDC257628DB460CC042000000001000000400200003082023C308201A5021070BAE41D10D92934B638CA7B03CCBABF300D06092A864886F70D0101020500305F310B300906035504061302555331173015060355040A130E566572695369676E2C20496E632E31373035060355040B132E436C6173732033205075626C6963205072696D6172792043657274696669636174696F6E20417574686F72697479301E170D3936303132393030303030305A170D3238303830313233353935395A305F310B300906035504061302555331173015060355040A130E566572695369676E2C20496E632E31373035060355040B132E436C6173732033205075626C6963205072696D6172792043657274696669636174696F6E20417574686F7269747930819F300D06092A864886F70D010101050003818D0030818902818100C95C599EF21B8A0114B410DF0440DBE357AF6A45408F840C0BD133D9D911CFEE02581F25F72AA84405AAEC031F787F9E93B99A00AA237DD6AC85A26345C77227CCF44CC67571D239EF4F42F075DF0A90C68E206F980FF8AC235F702936A4C986E7B19A20CB53A585E73DBE7D9AFE244533DC7615ED0FA271644C652E816845A70203010001300D06092A864886F70D010102050003818100BB4C122BCF2C26004F1413DDA6FBFC0A11848CF3281C67922F7CB6C5FADFF0E895BC1D8F6C2CA851CC73D8A4C053F04ED626C076015781925E21F1D1B1FFE7D02158CD6917E3441C9C194439895CDC9C000F568D0299EDA290454CE4BB10A43DF032030EF1CEF8E8C9518CE6629FE69FC07DB7729CC9363A6B9F4EA8FF640D64 | |||
Executable files
58
Suspicious files
29
Text files
0
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3180 | gmer.exe | C:\Users\admin\AppData\Local\Temp\CabAF66.tmp | — | |
MD5:— | SHA256:— | |||
| 3180 | gmer.exe | C:\Users\admin\AppData\Local\Temp\TarAF67.tmp | — | |
MD5:— | SHA256:— | |||
| 3180 | gmer.exe | C:\Users\admin\AppData\Local\Temp\tmpB024.tmp | — | |
MD5:— | SHA256:— | |||
| 3180 | gmer.exe | C:\Users\admin\AppData\Local\Temp\tmpB044.tmp | — | |
MD5:— | SHA256:— | |||
| 3180 | gmer.exe | C:\Users\admin\AppData\Local\Temp\tmpB074.tmp | — | |
MD5:— | SHA256:— | |||
| 3180 | gmer.exe | C:\Users\admin\AppData\Local\Temp\tmpB0C3.tmp | — | |
MD5:— | SHA256:— | |||
| 3180 | gmer.exe | C:\Users\admin\AppData\Local\Temp\tmpB102.tmp | — | |
MD5:— | SHA256:— | |||
| 3180 | gmer.exe | C:\Users\admin\AppData\Local\Temp\tmpB132.tmp | — | |
MD5:— | SHA256:— | |||
| 3180 | gmer.exe | C:\Users\admin\AppData\Local\Temp\tmp93B4.tmp | — | |
MD5:— | SHA256:— | |||
| 3180 | gmer.exe | C:\Users\admin\AppData\Local\Temp\tmp9412.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
7
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3180 | gmer.exe | GET | 200 | 23.51.123.27:80 | http://sf.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTSqZMG5M8TA9rdzkbCnNwuMAd5VgQUz5mp6nsm9EvJjo%2FX8AUm7%2BPSp50CEFbG0met4H9y7rRgO7%2BEzqU%3D | NL | der | 1.62 Kb | whitelisted |
3180 | gmer.exe | GET | 200 | 23.51.123.27:80 | http://ocsp.verisign.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEFIA5aolVvwahu2WydRLM8c%3D | NL | der | 1.71 Kb | whitelisted |
3180 | gmer.exe | GET | 200 | 23.51.123.27:80 | http://ocsp.thawte.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQJ1TBLBrQ9OnPHXPVaWb87MxkNlgQUwu79F9f%2Btw%2FGciJ7fvbA4gIz7D4CEH6T6%2Ft8xk5Z6kuad9QG%2FDs%3D | NL | der | 1.30 Kb | whitelisted |
3180 | gmer.exe | GET | 200 | 23.51.123.27:80 | http://ts-ocsp.ws.symantec.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRi82PVYYKWGJWdgVNyePy5kYTdqQQUX5r1blzMzHSa1N197z%2Fb7EyALt0CEA7P9DjI%2Fr81bgTYapgbGlA%3D | NL | der | 1.43 Kb | whitelisted |
3180 | gmer.exe | GET | 200 | 23.51.123.27:80 | http://ocsp.verisign.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQJ1TBLBrQ9OnPHXPVaWb87MxkNlgQUwu79F9f%2Btw%2FGciJ7fvbA4gIz7D4CEEe%2FGZXfjVJGQ%2FfbbUgNMaQ%3D | NL | der | 1.30 Kb | whitelisted |
3180 | gmer.exe | GET | 200 | 2.16.186.74:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | der | 781 b | whitelisted |
3180 | gmer.exe | GET | 200 | 67.26.137.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.5 Kb | whitelisted |
3180 | gmer.exe | GET | 304 | 67.26.137.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.5 Kb | whitelisted |
3180 | gmer.exe | GET | 304 | 67.26.137.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.5 Kb | whitelisted |
3180 | gmer.exe | GET | 200 | 23.51.123.27:80 | http://ocsp.verisign.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTO3jAJoCaQZUo7%2B2qJhdK4D6wpuQQUqkwAvoiA5mAvIL8uAwdOcMH2iFUCEDgl1%2Fr4Ya%2Be9JDnJrXWWtU%3D | NL | binary | 5 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3180 | gmer.exe | 2.16.186.74:80 | crl.microsoft.com | Akamai International B.V. | — | whitelisted |
3180 | gmer.exe | 67.26.137.254:80 | www.download.windowsupdate.com | Level 3 Communications, Inc. | US | malicious |
3180 | gmer.exe | 23.51.123.27:80 | ocsp.verisign.com | Akamai Technologies, Inc. | NL | whitelisted |
3180 | gmer.exe | 93.184.220.29:80 | crl.verisign.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
ocsp.verisign.com |
| whitelisted |
sf.symcd.com |
| whitelisted |
ocsp.thawte.com |
| whitelisted |
ts-ocsp.ws.symantec.com |
| whitelisted |
crl.verisign.com |
| whitelisted |