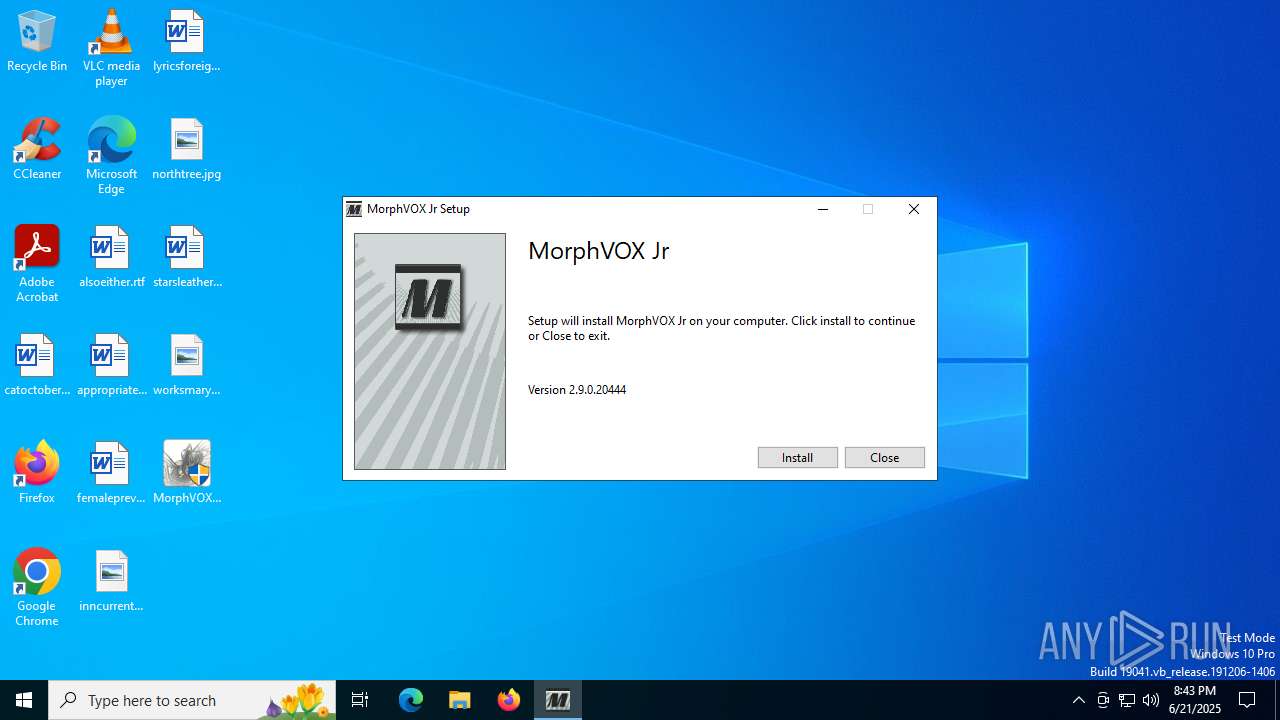
| File name: | MorphVOXJunior_Install-1.exe |
| Full analysis: | https://app.any.run/tasks/ee4a366d-bbde-4483-932d-1c912aa42697 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 20:43:10 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 5BE92593F6D10F118AA536AF777D7386 |
| SHA1: | 66D81144FEA29FE34EEF1FDB6B49590E91A40C01 |
| SHA256: | E884995DB0D8A8EDC614D12D86846DBD454DD368DA12A93E1E3FFF18F17B0718 |
| SSDEEP: | 98304:uFtUT57p97RshhTlddrXdmQLUeQ761IR79gaLONyXFNiTXK3VRTEgsrpmQFkBoIg:GZ6vZM |
MALICIOUS
Changes the autorun value in the registry
- mvsetup.exe (PID: 5780)
SUSPICIOUS
Reads security settings of Internet Explorer
- mvsetup.exe (PID: 2368)
- MorphVOXJunior_Install-1.exe (PID: 2356)
- mvsetup.exe (PID: 5780)
- msiexec.exe (PID: 6368)
Executable content was dropped or overwritten
- mvsetup.exe (PID: 3676)
- MorphVOXJunior_Install-1.exe (PID: 2356)
- mvsetup.exe (PID: 5780)
- mvsetup.exe (PID: 7008)
- mvsetup.exe (PID: 2368)
- drvinst.exe (PID: 4868)
- drvinst.exe (PID: 1472)
Starts itself from another location
- mvsetup.exe (PID: 2368)
- mvsetup.exe (PID: 3676)
Executes as Windows Service
- VSSVC.exe (PID: 3724)
Creates a software uninstall entry
- mvsetup.exe (PID: 5780)
Searches for installed software
- dllhost.exe (PID: 4824)
- mvsetup.exe (PID: 4832)
- mvsetup.exe (PID: 2368)
- mvsetup.exe (PID: 7008)
There is functionality for taking screenshot (YARA)
- mvsetup.exe (PID: 3676)
- mvsetup.exe (PID: 2368)
- mvsetup.exe (PID: 5780)
- mvsetup.exe (PID: 7008)
- mvsetup.exe (PID: 5692)
Process drops legitimate windows executable
- mvsetup.exe (PID: 5780)
- msiexec.exe (PID: 5928)
Application launched itself
- mvsetup.exe (PID: 4832)
- mvsetup.exe (PID: 5692)
Reads the Windows owner or organization settings
- mvsetup.exe (PID: 5780)
- msiexec.exe (PID: 5928)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 5928)
- drvinst.exe (PID: 4868)
- drvinst.exe (PID: 1472)
Creates files in the driver directory
- drvinst.exe (PID: 4868)
- SBAudioInstallx64.exe (PID: 1604)
- drvinst.exe (PID: 1472)
Creates or modifies Windows services
- drvinst.exe (PID: 1472)
INFO
Reads the computer name
- MorphVOXJunior_Install-1.exe (PID: 2356)
- mvsetup.exe (PID: 5780)
- msiexec.exe (PID: 5928)
- mvsetup.exe (PID: 2368)
- msiexec.exe (PID: 5008)
- msiexec.exe (PID: 4164)
- msiexec.exe (PID: 6368)
- SBAudioInstallx64.exe (PID: 1604)
- drvinst.exe (PID: 4868)
- drvinst.exe (PID: 1472)
- MorphVOXJr.exe (PID: 5252)
- mvsetup.exe (PID: 7008)
Create files in a temporary directory
- mvsetup.exe (PID: 2368)
- mvsetup.exe (PID: 3676)
- MorphVOXJunior_Install-1.exe (PID: 2356)
- mvsetup.exe (PID: 5780)
- msiexec.exe (PID: 5008)
- mvsetup.exe (PID: 7008)
- msiexec.exe (PID: 4164)
Process checks computer location settings
- mvsetup.exe (PID: 2368)
- MorphVOXJunior_Install-1.exe (PID: 2356)
- msiexec.exe (PID: 6368)
Checks supported languages
- MorphVOXJunior_Install-1.exe (PID: 2356)
- mvsetup.exe (PID: 3676)
- mvsetup.exe (PID: 5780)
- msiexec.exe (PID: 5008)
- msiexec.exe (PID: 5928)
- mvsetup.exe (PID: 4832)
- mvsetup.exe (PID: 5692)
- mvsetup.exe (PID: 7008)
- mvsetup.exe (PID: 2368)
- msiexec.exe (PID: 4164)
- msiexec.exe (PID: 6368)
- SBDriverInstaller.exe (PID: 5960)
- SBAudioInstallx64.exe (PID: 1604)
- drvinst.exe (PID: 4868)
- drvinst.exe (PID: 1472)
- MorphVOXJr.exe (PID: 5252)
The sample compiled with english language support
- mvsetup.exe (PID: 3676)
- MorphVOXJunior_Install-1.exe (PID: 2356)
- mvsetup.exe (PID: 5780)
- mvsetup.exe (PID: 2368)
- msiexec.exe (PID: 5928)
- drvinst.exe (PID: 4868)
- drvinst.exe (PID: 1472)
- mvsetup.exe (PID: 7008)
Manages system restore points
- SrTasks.exe (PID: 2976)
Creates files in the program directory
- mvsetup.exe (PID: 5780)
Launching a file from a Registry key
- mvsetup.exe (PID: 5780)
Reads the machine GUID from the registry
- mvsetup.exe (PID: 5780)
- msiexec.exe (PID: 5928)
- msiexec.exe (PID: 6368)
- SBAudioInstallx64.exe (PID: 1604)
- drvinst.exe (PID: 4868)
- MorphVOXJr.exe (PID: 5252)
Checks proxy server information
- mvsetup.exe (PID: 5780)
- slui.exe (PID: 1128)
Reads the software policy settings
- mvsetup.exe (PID: 5780)
- msiexec.exe (PID: 5928)
- SBAudioInstallx64.exe (PID: 1604)
- drvinst.exe (PID: 4868)
- slui.exe (PID: 1128)
Creates files or folders in the user directory
- mvsetup.exe (PID: 5780)
Manual execution by a user
- mvsetup.exe (PID: 4832)
Executable content was dropped or overwritten
- msiexec.exe (PID: 5928)
Creates a software uninstall entry
- msiexec.exe (PID: 5928)
Disables trace logs
- MorphVOXJr.exe (PID: 5252)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:09:29 17:05:58+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 68096 |
| InitializedDataSize: | 54784 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x7cde |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
156
Monitored processes
23
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1128 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1472 | DrvInst.exe "2" "211" "ROOT\MEDIA\0000" "C:\WINDOWS\INF\oem1.inf" "oem1.inf:c14ce88487927c7b:SBEE_Audio.NTamd64:3.0.0.1:*screamingbaudio," "4892a7cef" "0000000000000190" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1496 | "C:\Users\admin\Desktop\MorphVOXJunior_Install-1.exe" | C:\Users\admin\Desktop\MorphVOXJunior_Install-1.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1604 | "C:\Program Files (x86)\Screaming Bee\MorphVOX Junior\Drivers\SBAudioInstallx64.exe" i "C:\Program Files (x86)\Screaming Bee\MorphVOX Junior\Drivers\x64\W10\SBAudio.inf" "*ScreamingBAudio" | C:\Program Files (x86)\Screaming Bee\MorphVOX Junior\drivers\SBAudioInstallx64.exe | — | SBDriverInstaller.exe | |||||||||||
User: SYSTEM Company: Screaming Bee Inc Integrity Level: SYSTEM Description: Screaming Bee Driver Installer Exit code: 0 Version: 3.0.1.0 Modules
| |||||||||||||||
| 2356 | "C:\Users\admin\Desktop\MorphVOXJunior_Install-1.exe" | C:\Users\admin\Desktop\MorphVOXJunior_Install-1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2368 | "C:\Users\admin\AppData\Local\Temp\{F456A9CF-CDD8-4957-A516-78A0B8EAF526}\.cr\mvsetup.exe" -burn.clean.room="C:\Users\admin\AppData\Local\Temp\lui73F7.tmp\mvsetup.exe" -burn.filehandle.attached=684 -burn.filehandle.self=712 | C:\Users\admin\AppData\Local\Temp\{F456A9CF-CDD8-4957-A516-78A0B8EAF526}\.cr\mvsetup.exe | mvsetup.exe | ||||||||||||
User: admin Company: Screaming Bee Integrity Level: HIGH Description: MorphVOX Jr Version: 2.9.0.20444 Modules
| |||||||||||||||
| 2976 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3540 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SBDriverInstaller.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3676 | "C:\Users\admin\AppData\Local\Temp\lui73F7.tmp\mvsetup.exe" | C:\Users\admin\AppData\Local\Temp\lui73F7.tmp\mvsetup.exe | MorphVOXJunior_Install-1.exe | ||||||||||||
User: admin Company: Screaming Bee Integrity Level: HIGH Description: MorphVOX Jr Version: 2.9.0.20444 Modules
| |||||||||||||||
| 3724 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
24 940
Read events
23 941
Write events
960
Delete events
39
Modification events
| (PID) Process: | (2356) MorphVOXJunior_Install-1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Screaming Bee\InstallInfo |
| Operation: | write | Name: | InstallFile |
Value: C:\Users\admin\Desktop\MorphVOXJunior_Install-1.exe | |||
| (PID) Process: | (5780) mvsetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000799AD322EDE2DB01941600006C110000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4824) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000002538F022EDE2DB01D8120000BC040000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4824) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000002538F022EDE2DB01D8120000BC040000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3724) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3724) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 480000000000000045994F23EDE2DB018C0E0000C4130000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3724) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
| (PID) Process: | (3724) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3724) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | write | Name: | Element |
Value: \EFI\Microsoft\Boot\bootmgfw.efi | |||
| (PID) Process: | (3724) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
33
Suspicious files
40
Text files
18
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4824 | dllhost.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3676 | mvsetup.exe | C:\Users\admin\AppData\Local\Temp\{F456A9CF-CDD8-4957-A516-78A0B8EAF526}\.cr\mvsetup.exe | executable | |
MD5:DEAC15B4E72C622313F95AF1FE14E8B7 | SHA256:CDC0A9E6C5C1967AA9AAF777B1F1084B5A318FEBD0E16C79290F4A1C6095388A | |||
| 2368 | mvsetup.exe | C:\Users\admin\AppData\Local\Temp\{887CE6A0-4CBD-426B-9078-34419AD619AF}\.ba\wixextba.dll | executable | |
MD5:EA77FCD3A62FFB0433F353D006627ED1 | SHA256:EC415A95ED87C62B67566CAE3C9DAD2E0842238E39FFDE8D168DA98D9E7D7BB3 | |||
| 2368 | mvsetup.exe | C:\Users\admin\AppData\Local\Temp\{887CE6A0-4CBD-426B-9078-34419AD619AF}\.ba\LogoSide2.png | image | |
MD5:C73219FBF25D5FF3B15B8BA5AA3E4421 | SHA256:91A51952D64AE032158A400F5BCEABA326AE29940388867BE6B31B11A98D51C2 | |||
| 2368 | mvsetup.exe | C:\Users\admin\AppData\Local\Temp\{887CE6A0-4CBD-426B-9078-34419AD619AF}\.ba\thm.wxl | xml | |
MD5:2A38F6A71B86336B2C86AC4DA98FFC22 | SHA256:C9867635942686DA64BBDE3153D1DB06ECA861DD506A5334CB528D93343ED5FE | |||
| 2368 | mvsetup.exe | C:\Users\admin\AppData\Local\Temp\{887CE6A0-4CBD-426B-9078-34419AD619AF}\.ba\thm.xml | xml | |
MD5:06512DA9FC91BC938295A5DA0CC65C19 | SHA256:BA3CA00D8E8A418E831325D7D74B37434C014B909EF0CA64DD0FE5C8D95CBAA7 | |||
| 2368 | mvsetup.exe | C:\Users\admin\AppData\Local\Temp\{887CE6A0-4CBD-426B-9078-34419AD619AF}\.ba\BootstrapperApplicationData.xml | xml | |
MD5:18D199599B26C780B035C6B42FC53433 | SHA256:16ADD71A6B41528B4F84C2F07A0D35753B7BCFBF97B220B9D2ECE33F8502FCAF | |||
| 2356 | MorphVOXJunior_Install-1.exe | C:\Users\admin\AppData\Local\Temp\lui73F7.tmp\mvsetup.exe | executable | |
MD5:DEAC15B4E72C622313F95AF1FE14E8B7 | SHA256:CDC0A9E6C5C1967AA9AAF777B1F1084B5A318FEBD0E16C79290F4A1C6095388A | |||
| 2368 | mvsetup.exe | C:\Users\admin\AppData\Local\Temp\{887CE6A0-4CBD-426B-9078-34419AD619AF}\.ba\Logo.png | image | |
MD5:78880F10A90D15F087A5742544E7BAC5 | SHA256:E7FC090A659A619F1CE94AF48F5208051BE5907CA1857B43E59FAF02151AF0C8 | |||
| 2368 | mvsetup.exe | C:\Users\admin\AppData\Local\Temp\{887CE6A0-4CBD-426B-9078-34419AD619AF}\MVJRMSI | executable | |
MD5:A4C8ABC13AB6693328A5E72A19827270 | SHA256:D715255AA092171C21BD66A6AA6FDB3DC62B29190C5842B7F6523EE4CFBC227E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
44
TCP/UDP connections
54
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 184.25.50.10:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.25.50.10:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 400 | 20.190.160.22:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | GET | 200 | 184.25.50.10:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.160.22:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.160.20:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 16.7 Kb | whitelisted |
— | — | POST | 200 | 40.126.32.134:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 184.25.50.10:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 184.25.50.10:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.25.50.10:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |